DOI:10.32604/cmc.2020.013104

| Computers, Materials & Continua DOI:10.32604/cmc.2020.013104 |  |
| Article |
A Novel Approach to Data Encryption Based on Matrix Computations
1Centre for Cyber Security, Faculty of Information Science and Technology, Universiti Kebangsaan Malaysia, 43600 UKM, Bangi Selangor, Malaysia
2Technical Machine School of Professional Studies, Radoja Krstića 19, Trstenik, 37240, Serbia
3University of Novi Pazar, Dimitrija Tucovića bb, Novi Pazar, 36300, Serbia
4Maulana Azad National Urdu University, Hyderabad, Telangana, 500032, India
5University of Nis, Višegradska 33, Niš, 18106, Serbia
*Corresponding Author: Khaleel Ahmad. Email: khaleelahmad@manuu.edu.in
Received: 26 July 2020; Accepted: 22 August 2020
Abstract: In this paper, we provide a new approach to data encryption using generalized inverses. Encryption is based on the implementation of weighted Moore–Penrose inverse 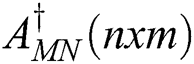 over the
over the 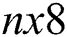 constant matrix. The square Hermitian positive definite matrix
constant matrix. The square Hermitian positive definite matrix 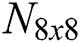 p is the key. The proposed solution represents a very strong key since the number of different variants of positive definite matrices of order 8 is huge. We have provided NIST (National Institute of Standards and Technology) quality assurance tests for a random generated Hermitian matrix (a total of 10 different tests and additional analysis with approximate entropy and random digression). In the additional testing of the quality of the random matrix generated, we can conclude that the results of our analysis satisfy the defined strict requirements. This proposed MP encryption method can be applied effectively in the encryption and decryption of images in multi-party communications. In the experimental part of this paper, we give a comparison of encryption methods between machine learning methods. Machine learning algorithms could be compared by achieved results of classification concentrating on classes. In a comparative analysis, we give results of classifying of advanced encryption standard (AES) algorithm and proposed encryption method based on Moore–Penrose inverse.
p is the key. The proposed solution represents a very strong key since the number of different variants of positive definite matrices of order 8 is huge. We have provided NIST (National Institute of Standards and Technology) quality assurance tests for a random generated Hermitian matrix (a total of 10 different tests and additional analysis with approximate entropy and random digression). In the additional testing of the quality of the random matrix generated, we can conclude that the results of our analysis satisfy the defined strict requirements. This proposed MP encryption method can be applied effectively in the encryption and decryption of images in multi-party communications. In the experimental part of this paper, we give a comparison of encryption methods between machine learning methods. Machine learning algorithms could be compared by achieved results of classification concentrating on classes. In a comparative analysis, we give results of classifying of advanced encryption standard (AES) algorithm and proposed encryption method based on Moore–Penrose inverse.
Keywords: Security; data encryption; matrix computations; cloud computing; machine learning
The level of security of data stored on the cloud is primarily based on the identification of sensitive and confidential databases, and it is necessary to apply additional protection, encryption, and monitoring. It is important to consider whether it is possible to encrypt data at all levels, where they are designed, and how encryption algorithms are tested. Data encryption became of great importance in many fields including healthcare [1], and several encryption methods have been investigated including triple data encryption [2]. The most basic way cloud providers provide data is encryption. Indeed, using clouds in order to provide data demand services is developing to be an attractive answer to services demanding scalability and cost reduction [3]. Applying encryption in a cloud environment can further protect data from theft and unauthorized use. It is important to emphasize that data security is based on an understanding of risk. Users need to be aware of the potential risks when storing their data in the cloud or using cloud applications. Therefore, they must apply different control processes and techniques to manage these risks and reduce them to an acceptable level. The dynamics of information processing in the IoT and cloud environment and the fluidity of information are the reasons. It is important to provide two types of security in the IoT and cloud environments. The first security refers to cloud providers, and the second refers to user security. Compliance of cloud providers with requirements and standards in the field of cloud security is implemented and enforced to meet security guidelines, recommendations, laws, and regulations. Some of the key challenges for IoT and cloud security are: storing data in multiple locations, storing data on media and resources shared by multiple users, availability of data after termination of the contract with the provider, in case of sale or merger companies, compliance with legal regulations, the problem of external supervision, as well as the restoration of data in the event of natural disasters or due to human error. It is especially important to take care of three aspects: data location, data control, and secure data transfer.
The major contribution of this paper regarding the issues of security and efficiency may refer to multiple different encryptions based on the random key (in form of matrix), while data encryption is based on different inversions (in this paper we have presented one of them). We present a novel method of data encryption based on matrix calculations and Weighted Moore–Penrose inverses (MP Encryption). The Moore Penrose inverses have found many applications in various areas of research. This proposed MP encryption method can be applied effectively in the encryption and decryption of images in multi-party communications.
The structure of the present paper is as follows. In the second section are exposed the similar research from the field of problems application matrices in cryptography. Also, we have presented some similar research in the field of data encryption in a cloud environment. The third section consists of the basic properties of weighted Moore–Penrose inverse (MP inverse) and presented ways to compute source matrix which can presented text or image. In the fourth section, are listed the examples for the encryption method based on weighted Moore Penrose inverse and Hermitian positive definite matrix as a cryptographic key in image encryption cases. Also, in this section, we have provided the National Institute of Standards and Technology (NIST) quality assurance tests for random generated Hermitian matrix (a total of 10 different tests and additional analysis with approximate entropy and random digression). The fifth section contains the comparative analysis of encryption methods between machine learning methods. Machine learning algorithms could be compared by achieved results of classification concentrating on classes. Sensitivity and specificity are mostly used performance measuring of complex data during classification. In this research sensitivity and specificity define achieved results of classifying Advanced Encryption Standard (AES) and MP Encryption, respectively. The sixth section lists the conclusions and suggestions for further works.
Cloud computing, a recently emerged paradigm faces major challenges in achieving the privacy of migrated data, network security, etc. Too many cryptographic technologies are raised to solve these issues based on identity, attributes, and prediction algorithms yet. These techniques are highly prone to attackers. This would raise a need for an effective encryption technique, which would ensure secure data migration [4]. Cloud computing has been investigated in many research works including the factors and the impacts of its implementation in the public sector [5], Authors in [6] present a framework with data encryption, distribution, and decryption in a cloud environment. Ensuring security for data transmission and storage is the biggest concern and challenge of the Internet of Things (IoT) [7]. Cloud services are naturally located in locations that are far from premises in which the client organization is located. As soon as data and services are accessed from a remote location, the unprotected Internet is used as an access medium, which opens a new front for a potential attacker [8]. In [9,10], new techniques are presented to provide security of data in a cloud environment. In [11], a novel encryption scheme for a concrete model (client-server architecture) has been presented. Also, authors in [12] propose a new verifiable model reduces the computational overhead of encoding and decoding. The authors in [13] deal with the topic of personal data protection with an emphasis triggering moves to unlock its insights by relocating it in the cloud. First of all, the authors survey prominent clouded data approaches such as multiparty computation, blockchain, privacy, and encryption. To achieve the goal of confidentiality of data, many encryption algorithms are available in the cloud environment. Authors in [14] proposed the first self-updatable encryption model secure against a relevant form of chosen-ciphertext security. This approach is a new kind of public-key encryption, motivated by cloud computing. In [15], the authors presented the access control model for the security of data by using attribute-based encryption in the cloud computing environment. The paper [16] proposed a security model to protect cloud data from unauthorized access using a hybrid cryptosystem. The proposed approach provides high-level security to data stored in cloud computing and ensures secure data transmission over the network. In [17] authors discussed security issues and challenges in cloud computing and study various security algorithms in this environment. In [18], a method called hyperdata encryption is proposed. The proposed solution is suitable for cloud platforms. For the secure transfer of sensitive data, the data should be encrypted before sending. Achieving the integrity goal ensures that data is not modified, damaged, or corrupted either accidentally or intentionally. The goal of data integrity is just as important as the other two main goals of computer security in a cloud environment. In [19], a multi-client universal computation model for encrypted cloud data. To achieve computer security goals on the cloud available numerous technologies. Data protection technologies, frameworks, and implementation, which achieve greater security of cloud data, are a complex and broad area, which is regularly used in the implementation of everyday activities of cloud computing.
The importance of the application of matrix computations in the encryption procedure is stated in [20–22]. Specifically, in this paper, we provided a new approach to data encryption using generalized inverses. Also, authors in [23] state some applications generalized inverses in public key cryptosystem design. In [24] authors state applications of the Drazin inverse to the Hill cryptographic system. Papers [25,26] presents secure encryption and decryption technique using generalized inverse and decimal expansion of an irrational number. Authors in [27] present a novel approach that leads in a natural manner to the Moore–Penrose’s generalized inverse between the subspaces of activation of the matrix under study. Paper [28] deals with the application of generalized inverses of matrices over finite fields and the method of least squares in linear codes. It is proven that if the Moore–Penrose inverse of a generator matrix of a linear code exists, a unique word approaching a received word near the codewords of the code can be found. Authors in [29,30] analyses about Hill cipher and public key cryptosystem using Hill secure algorithm. In [31] authors present secure communication protocols based on a computation of the MP inverse of matrices over fields of specific characteristics.
3 Preliminaries About Weighted Moore–Penrose Inverse
For any matrix 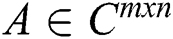 (
(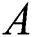 be the set of complex numbers,
be the set of complex numbers, 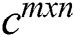 be the set of
be the set of 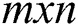 complex matrices of rank
complex matrices of rank 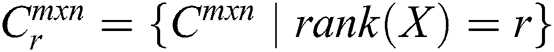 ) and positive definite Hermitian matrices
) and positive definite Hermitian matrices 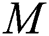 and
and 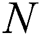 of the orders
of the orders 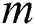 and
and 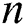 respectively, consider the four conditions in
respectively, consider the four conditions in 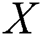 , where
, where  denotes conjugate and transpose. The first condition is AXA = A, the second condition is XAX = X, the third condition is (MAX)* = MAX and the fourth condition is (NXA)* = NXA. Moreover, this system of matrix equations has a unique solution. The matrix
denotes conjugate and transpose. The first condition is AXA = A, the second condition is XAX = X, the third condition is (MAX)* = MAX and the fourth condition is (NXA)* = NXA. Moreover, this system of matrix equations has a unique solution. The matrix 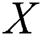 that satisfies all four conditions is called the weighted MP inverse and is denoted with
that satisfies all four conditions is called the weighted MP inverse and is denoted with 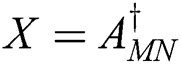 . The weighted MP inverse
. The weighted MP inverse 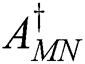 is the generalization of the MP inverse
is the generalization of the MP inverse 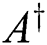 . If
. If 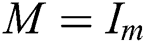 ,
, 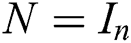 , then
, then 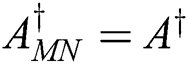 , i.e., the weighted Moore–Penrose inverse is reduced to Moore–Penrose inverse [32]. The idea for applying weighted MP inverses in cryptography came from our previous papers [33–38], where we analyzed its basic properties. Milošević in [37] generalized Greville’s method to the weighted MP inverse.
, i.e., the weighted Moore–Penrose inverse is reduced to Moore–Penrose inverse [32]. The idea for applying weighted MP inverses in cryptography came from our previous papers [33–38], where we analyzed its basic properties. Milošević in [37] generalized Greville’s method to the weighted MP inverse.
Theorem 3.1 (Wang et al. [33]) Let  and
and 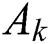 is a submatrix which consist the first
is a submatrix which consist the first 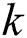 columns of matrix
columns of matrix 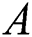 . For
. For 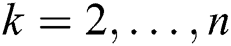 the matrix
the matrix 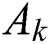 is represented with
is represented with
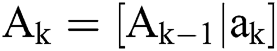
and 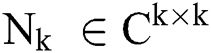 is a submatrix of the matrix
is a submatrix of the matrix 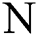 . Then the matrix
. Then the matrix 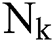 is given as
is given as
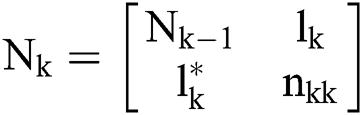
Let the matrices 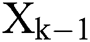 and
and 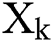 and the vectors
and the vectors 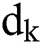 and
and 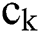 are defined as
are defined as
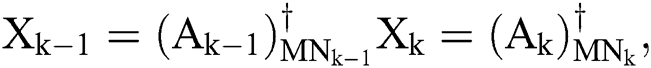

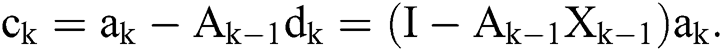
Then
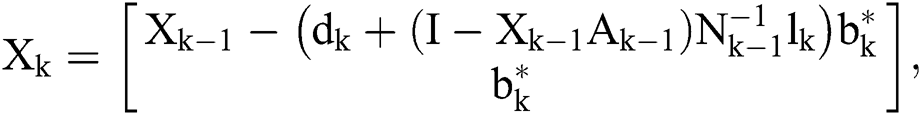
where
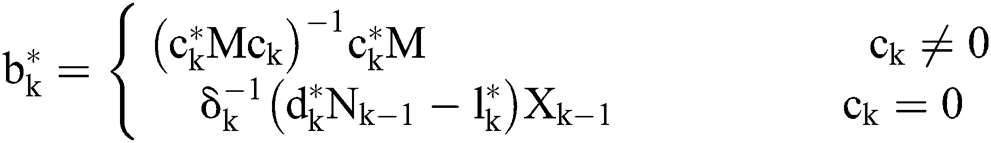
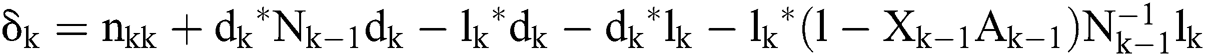
Different variants of calculation of the weighted MP inverse in combination with relational databases are given in the paper [37]. Since the number of combinations of the possible positive definite Hermitian 8 × 8 matrix is extremely large, it is clear that this type of matrix could be used in developing of the encryption algorithm and would be exceptionally strong.
Algorithm 1: Calculation of MP inverse 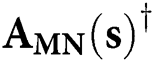 from [33]
from [33] 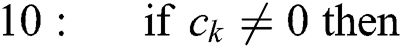

For calculation of Algorithm 1, from [33], is needed an auxiliary Algorithm 2.
Algorithm 2: Calculation of 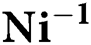 for the rational matrices
for the rational matrices
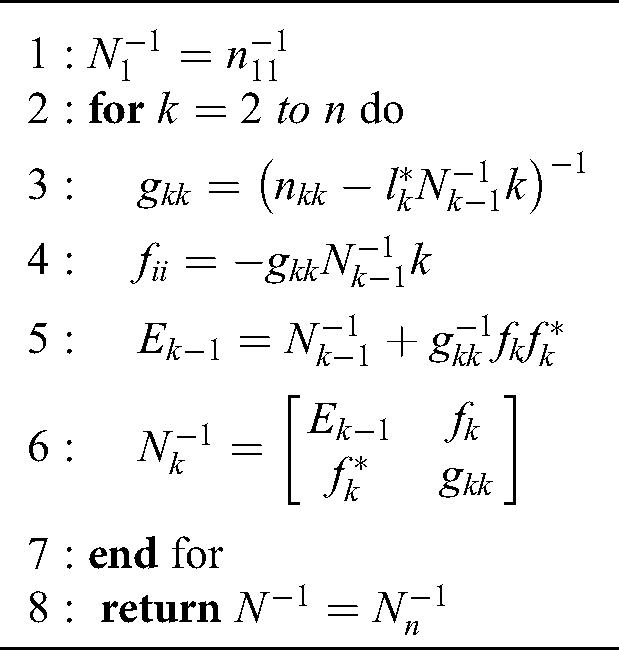
The partition method of Wang for calculation of the weighting MP inverse has been extended to a set of rational and polynomial matrices with one variable [38]. In the paper [26] is given the following equation:
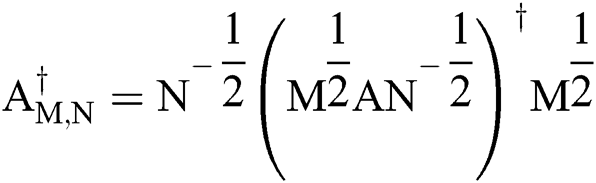
In this case, 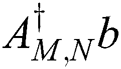 is the
is the 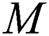 -least squares solution of
-least squares solution of 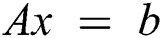 which has minimal
which has minimal 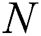 -norm. This notion can be extended where
-norm. This notion can be extended where 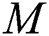 and
and 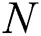 are positive semi-definite matrices, and
are positive semi-definite matrices, and 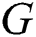 is a matrix such that
is a matrix such that 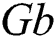 is a minimal
is a minimal 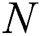 semi-norm,
semi-norm, 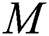 -least squares solution of
-least squares solution of 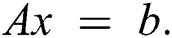 In this case,
In this case, 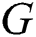 must satisfy the following four conditions [31]:
must satisfy the following four conditions [31]:
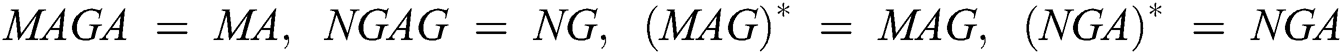 . When
. When 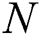 is positive definite, then there exists a unique solution for
is positive definite, then there exists a unique solution for 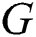 .
.
Theorem 3.2. In the set of complex matrices let 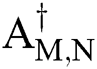 is weighted MP inverse of matrix
is weighted MP inverse of matrix 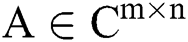 and
and 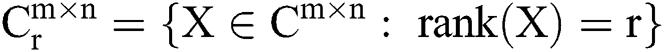 ,
,  and
and  are Hermitian, positive definite matrices with order m and n, respectively. If M is an identity matrix, then the matrix A can be represented as
are Hermitian, positive definite matrices with order m and n, respectively. If M is an identity matrix, then the matrix A can be represented as
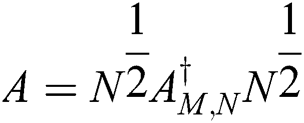
Proof. From Eq. (9) is necessary to find the value of the matrix A that is represented in the expression.
This is the process by which we will restore the encoded image value to the actual one.

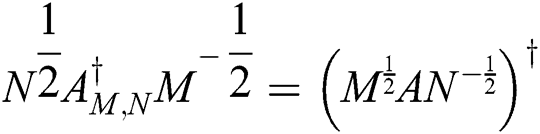
Let
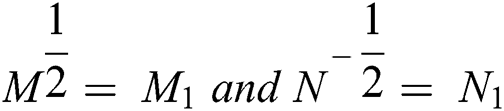
From 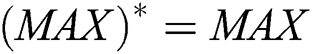 we obtain
we obtain
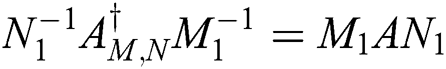
So,
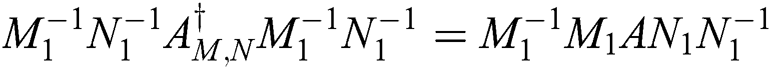
and
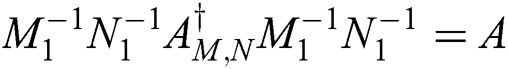
This can be rewritten as,
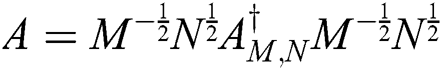
In order to simplify the expression and calculation process, without affecting the protection degree in this way we can assume that the matrix M is given as an identity matrix from order n, where n represents the number of rows of the encrypted matrix A.
Because M is the identity matrix, in this case, the expressions 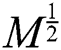 and
and 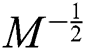 gives the identity matrix and from Eq. (16) we obtain
gives the identity matrix and from Eq. (16) we obtain
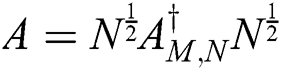
Eq. (17) allows us to obtain the original matrix, which in our case represents the image, based on the weighted MP inverse and the Hermitian positive definite matrix N which is the key.
4 Proposed Method for Data Encryption
Cloud security can be automated by a combination of a number of services available, with the goal of creating an integrated platform for monitoring, reporting, and responding to events that could compromise the security of cloud data.
The method for data encryption has four phases (see the general model framework on Fig. 1):
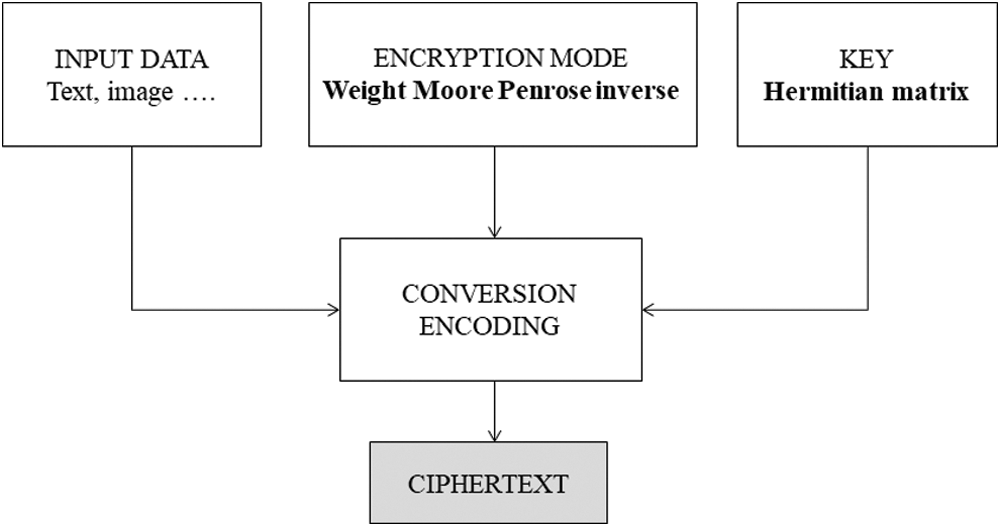
Figure 1: Proposed model framework
1. Loading data (text or image)
2. Generation of Hermitian positive definite matrix (cryptographic key)
3. Converting the input data into a binary string.
4. Application of weighted Moore Penrose inverse in data encryption.
After converting the Base64 string into a binary record, is applied the weighted MP inverse where we use the Hermitian positive definite matrix (key), where obtained a new binary string which is converted to the Base64 string, which in this case represents the cipher of the image.
Example 1. Given is the image in PNG format and the Hermitian positive definite matrix 8 × 8 which presented key.
M_8 × 8 =
{{339, −87, −110, 119, 9, −41, −20, 10},
{−87, 514, −119, 10, 48, −55, −360, 45},
{−110, −119, 395, −225, −30, 81, −16, −129},
{119, 10, −225, 392, 43, −8, 180, 109},
{9, 48, −30, 43, 473, 93, −188, 90},
{−41, −55, 81, −8, 93, 552, −3, −44},
{−20, −360, −16, 180, −188, −3, 691, 0},
{10, 45, −129, 109, 90, −44, 0, 611}}.
The first phase is loading image and application of the Base64 image encoder converting of the received Base64 string into a binary string. Then, the next phase is the generation of the Hermitian positive definite matrix (in this case order 8).
The third phase is the application of the weighted Moore Penrose inverse in image encryption where we use the Hermitian positive definite matrix as key, where we get a binary string that represents the cipher of the image (see Fig. 2).
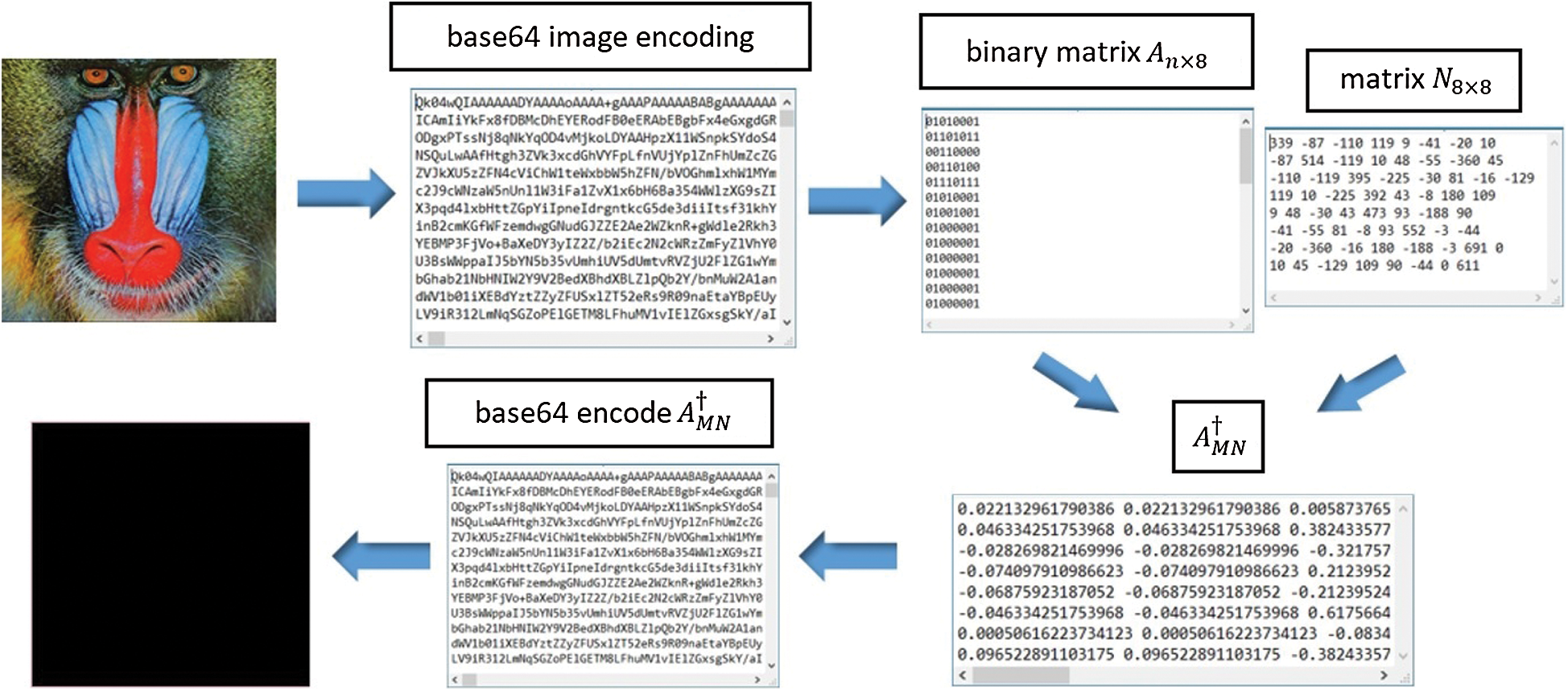
Figure 2: Image encoding procedure using weighted MP inverse
In the reverse case it is needed base64 encode  and Hermitian positive definite matrix. So, is needed loading of two input parameters: valid cryptographic key and the weighted MP inverse. If the key, or weighted MP inverse matrix
and Hermitian positive definite matrix. So, is needed loading of two input parameters: valid cryptographic key and the weighted MP inverse. If the key, or weighted MP inverse matrix  are not correct the image cannot be done (see Fig. 3).
are not correct the image cannot be done (see Fig. 3).
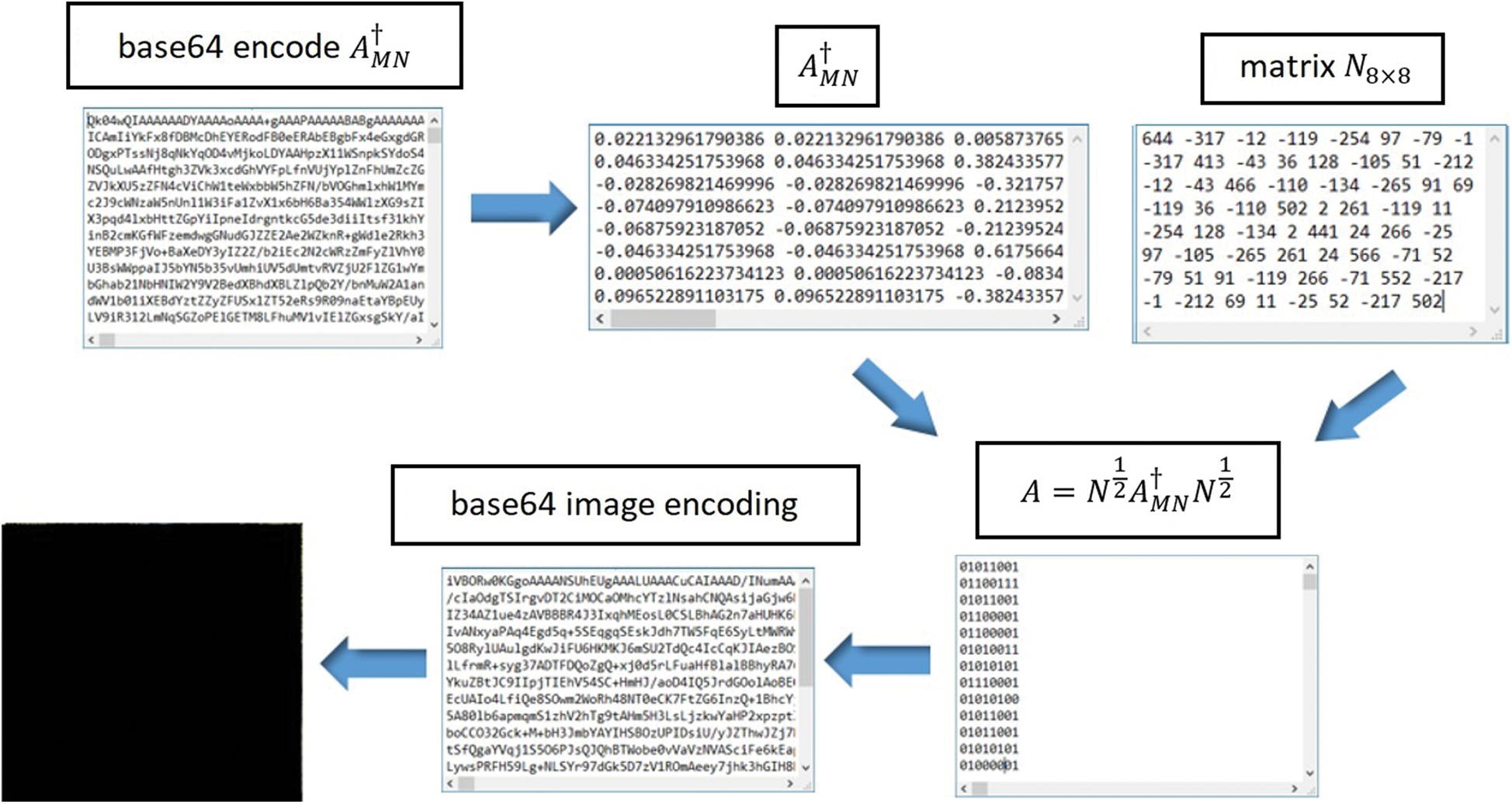
Figure 3: An example of using an invalid weighted MP inverse matrix or key
In other cases, if we use all correct parameters, then image decoding is successful (see Fig. 4).
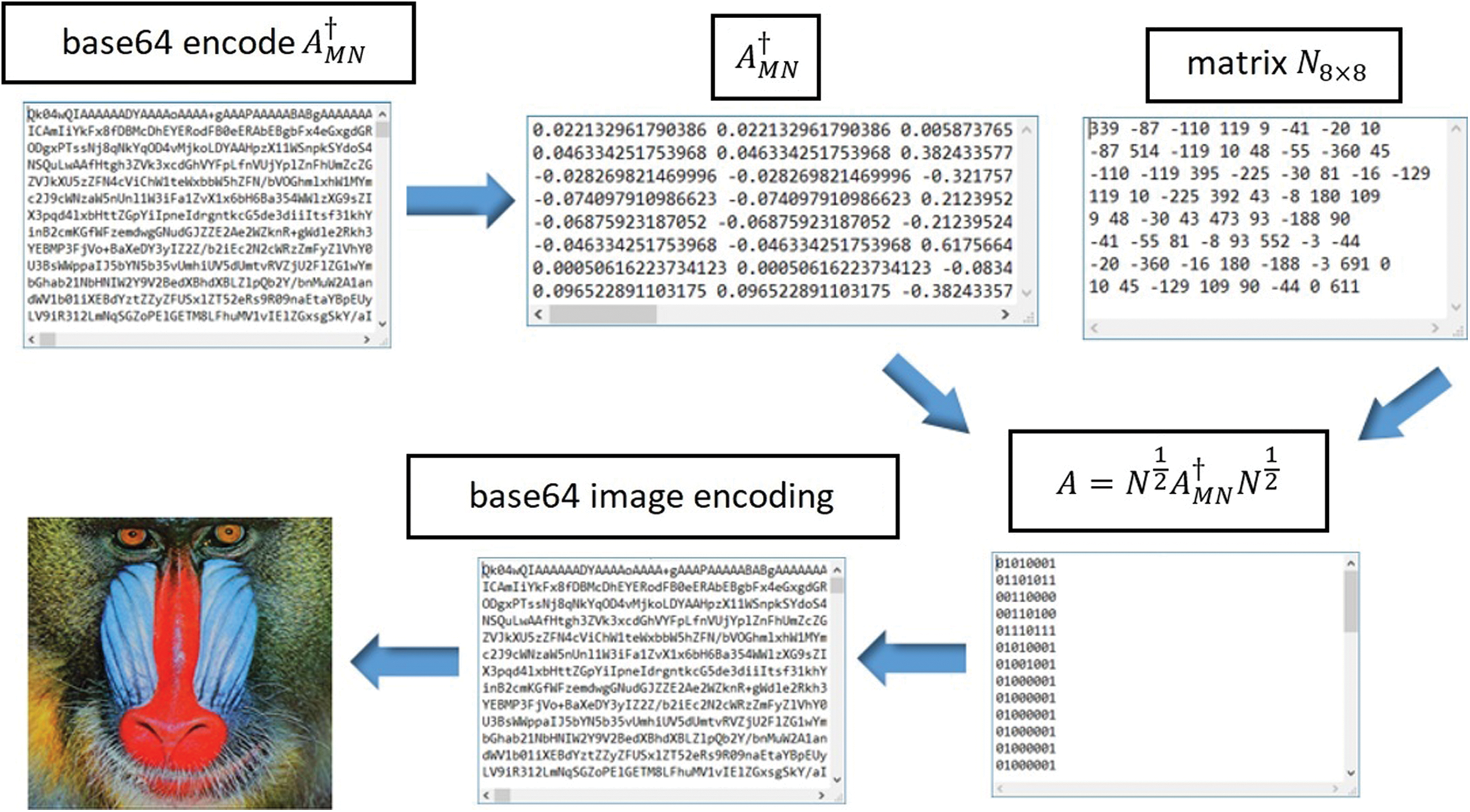
Figure 4: An example of correct using of MP inverse
In our paper [35], the weighted MP inverse and LM inverse relationship are analyzed and it shows that these are techniques that give the same result. Consequently, our proposed method for data encryption can also be used by the LM inverse. On the other hand, the key must be of type Hermitian matrix (positive definite) according to the theorem for the weight MP inverse.
In order for this encryption method to provide a high secrecy we used prescribed statistic NIST tests. NIST tests is applied only binary sequences. Therefore, in our testing, we first need to convert the cryptological key to binary (matrix from Example 1). The NIST quality assurance test results for randomly generated matrix (cryptographic key) are given in Tab. 1.
Table 1: NIST quality assurance tests for random generated Hermitian matrix
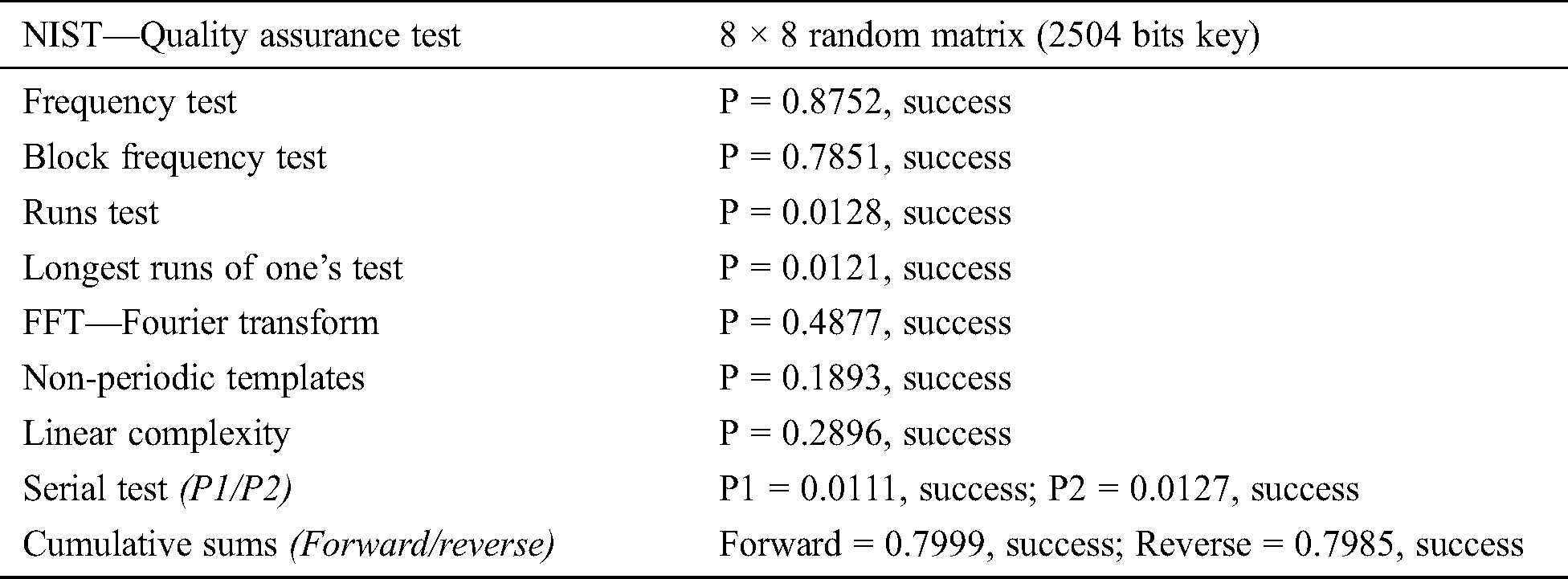
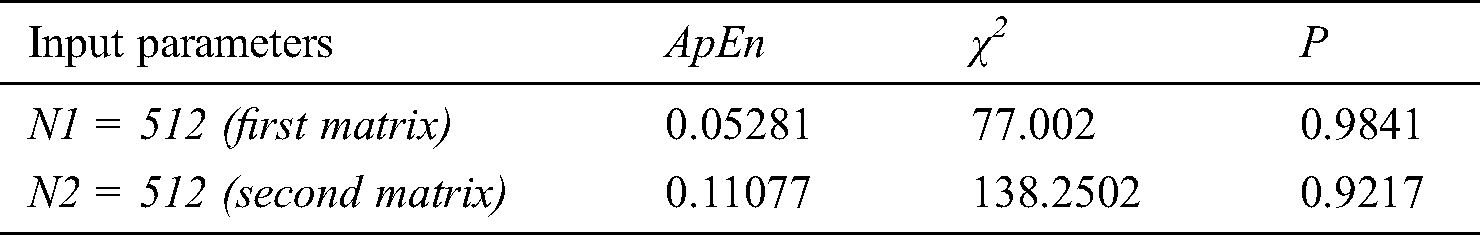
After the test, we can conclude that all tests met the condition P ≥ 0.01 (a condition for a binary sequence to be considered random, set by NIST). The fundamental terms of information theory, such as entropy, relative entropy, and mutual information are defined as probability distribution functions. These functions well describe the behavior of random variables of long sequences. We conducted additional testing for approximate entropy of a randomly generated Hermitian matrix (see Tab. 2).
Table 2: Approximate entropy for random generated Hermitian matrix
Examination of random digression test is a series of eight tests (and conclusions), i.e., one test and a conclusion for each of the states: −4, −3, −2, −1 and +1, +2, +3, +4. For seven states, is P ≥ 0.01, which leads to the conclusion that the binary sequence for the Hermitian matrix is random (see Tab. 3).
Table 3: Examination of random digression test

In the additional testing of the quality of the random matrix generated, we can conclude that the results of our advanced analysis (such as approximate entropy and random digression) satisfy the NIST requirements.
5 Performance Evaluation and Experimental Results
Machine learning algorithms could be compared by achieved results of classification concentrating on classes. Finding classification performance is a challenging part if we use inadequate data. By comparing the means of misclassified instances, we can make a comparison between machine learning methods. Several machine learning methods are used in order to distinguish two types of ciphertexts: (1) encrypted by the AES algorithm, and (2) encrypted by the proposed encryption method based on weighted MP inverse. The basic questions of the analysis are:
1. Is it possible to identify the type of encryption method by machine learning models learned only from information in encrypted text?
2. Are there significant differences between the AES and the proposed MP encryption method?
Hence, the most commonly used measure which is not focused on different classes quantity of right labels is accuracy:
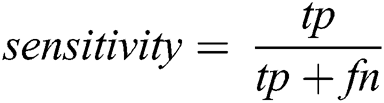
On the other hand, two measures that distinctly approximate a classifier’s presentation on diverse classes are
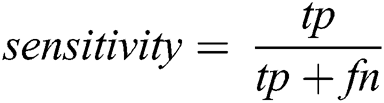 and
and 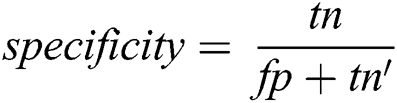
where are correctly classified: tp—true positive; tn—true negative and misclassified: fp—false positive; fn—a false negative.
Specificity and sensitivity are mostly used performance measuring of complex data during classification. In a comparative analysis, we give results of classifying of AES algorithm and encryption method based on Moore–Penrose inverse, respectively. In this study, we used two datasets which are obtained by extraction and decoding of a message in combination with different machine learning techniques. In order to produce an efficient machine learning algorithm, which will be able to satisfy all requirements, we tested both datasets on different types of machine learning methods.
5.1 Experiment Without Feature Selection
In this experiment, we used both datasets in combination with different ensemble machine learning methods. The result of this experiment is given in the following tables. We apply different machine learning techniques on both datasets without any feature extraction. Results obtained in that way are presented in Tab. 4.
Table 4: Classification result without feature selection
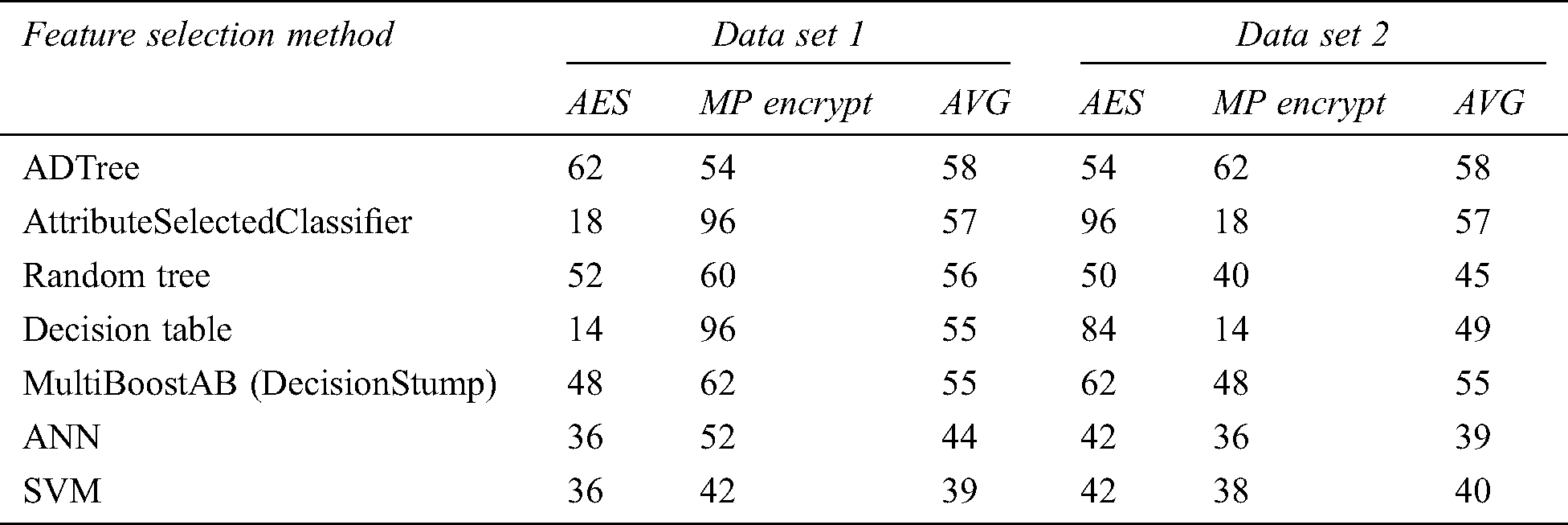
As you can see from the table, the best result with an average accuracy of 58% is achieved using the ADTree classifier. Besides that, it is obvious that tree classifiers are giving much better accuracy than other types of classifiers. Ensemble classifiers as AttributeSelectedClassifier and MultiBoost are also achieving significant accuracy. Artificial Neural Network and Support Vector Machine are giving the worst accuracy, which means that this kind of database is not suitable for this kind of classifier. Another interesting result from this experiment with dataset 1 is that the accuracy for the MP Encryption label is much greater for most classifiers. When we apply AttributeSelectedClassifier and Decision table it is 96% which is great accuracy compared to average accuracy for those classifiers. It means that some classifiers are producing much better results when they classify one class compared to another. In terms of this, AdTree and Random Tree classifiers are achieving the best-balanced accuracy for both classes.
5.2 Experiment With Feature Selection
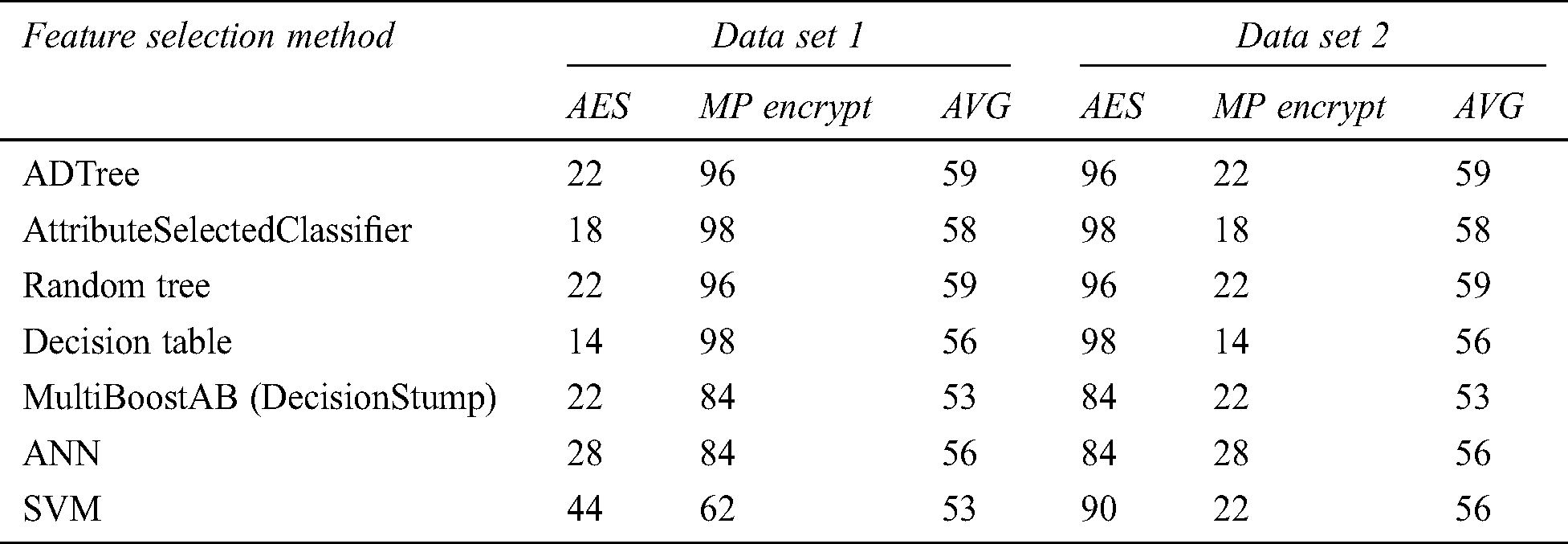
After we load data and check data distribution, we see that there is a lot of features which does not have any value for any row. So, we decided to apply some feature selection methods before we introduce classification methods. For the feature selection method, we applied AttributeSelection, which results in a much smaller number of features and at the same time slightly increase accuracy. In Tab. 5, we present a result which we achieved using the feature selection method before classification.
Table 5: Classification result with feature selection applied
In Fig. 5 we present a comparison of average accuracy between classifiers when we don’t apply feature selection on a dataset and when feature selection is applied.
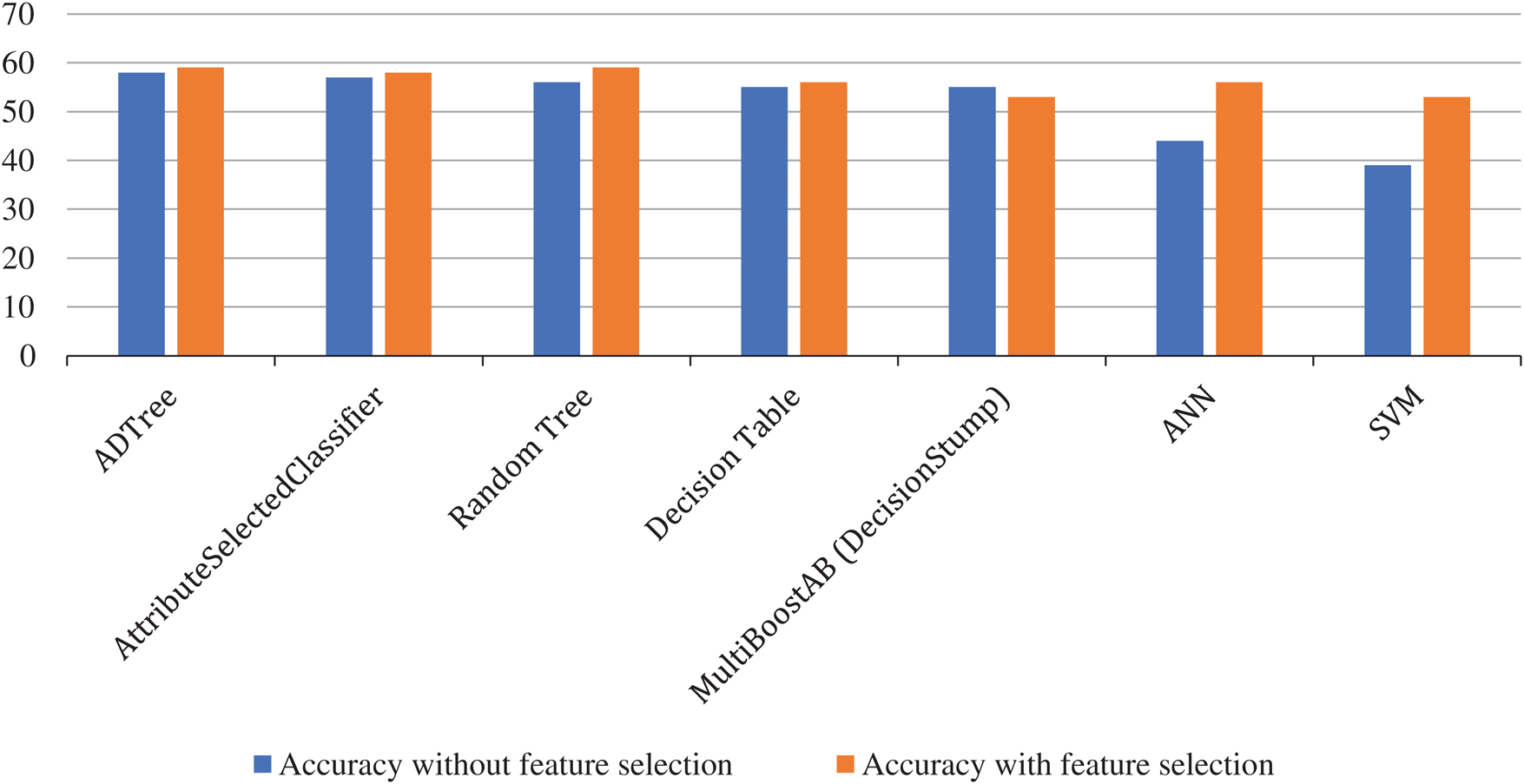
Figure 5: Comparison of accuracy between classification without and with feature selection
As you can see from the presented results, accuracy is increased for almost all machine learning methods which are applied. Some of the machine learning technologies achieved slightly better accuracy, for 1%, but for some of the methods, we achieved accuracy which is higher 14% than the previous one when we used all features. We have a similar situation in terms of accuracy distribution between classes, so again for MP Encrypt class, we have much greater accuracy in comparison with accuracy achieved for AES class.
When we use feature selected database, there are no classifiers which produce balanced accuracy for both classes. As it is obvious, all classifiers except MultiBoost are achieved better accuracy results when feature selection is applied. For some of the classifiers, we got significantly higher accuracy. When feature selection is applied, all proposed methods are achieving accuracy greater than 50% which is a great result compared with previous research on this topic. Besides that, time which is needed to build method and to test it is much smaller when we applied feature selection compared with the initial dataset.
With the development of cloud and computer technologies, tools and software are being developed that violate the security of cloud computing resources. The layered cloud storage architecture is used primarily because different types and kinds of data may have different requirements in terms of storage. It is important to point out that there are often requirements related to encryption and data security. Mathematical systems found a wide application in encryption. The calculation of the weighted MP inverse represents one of those matrix system applications in cryptography. The basic precondition for developing of cryptologic systems with the public key is the efficient generation of a parameter which generates the key.
In this paper is presented a new idea in the form of applications matrix computations and generalized inverses in cryptography. We have provided a new way of encryption of text or images, where the whole process is based on the use of weighted MP inverse over the Hermitian positive definite matrix order 8 which presented key. The number of different combinations of the Hermitian positive definite matrices order 8 is huge so this solution represents a strong and secure key. Also, it was done performed the tests for the Hermitian positive definite matrices-keys generation through several aspects. In the experimental part of this paper, we give a comparison of encryption methods between machine learning methods. Machine learning algorithms could be compared by achieved results of classification concentrating on classes. In a comparative analysis, we give results of classifying of AES algorithm and encryption method based on Moore–Penrose inverse, respectively. Security problems are one of the most important issues related to cloud technologies. Data security and physical access to the location where the equipment was located needed to be constantly improved, as security threats to data and systems are becoming more serious day by day. Progress continues and more people are turning to these technologies because security will be improved without any doubt. Cloud computing is changing the business logic in the world. Due to the transition of the company to cloud computing, the client-server life on it will improve. Larger companies will need more time to move to cloud storage. Security issues are a big problem for them, as well as control over sensitive data.
The future of clouds will be slower in large companies as well as in large urban areas. The directions of our further development of the proposed method could refer to a connection with database management systems and matrix computations using PHP and MySQL technologies [39]. In order to ensure adequate levels of cloud data protection, appropriate mechanisms for cloud data warehouse security need to be established. In this case, cloud security automation enables the storage of data that can later be used for forensic analysis. Also, our future work could go in the direction of secure computation of the Moore–Penrose pseudo-inverse and its application to secure linear algebra, modeled by Cramer et al. [40]. New applications for smartphones will also appear. People and companies will access network software applications through a remote server. It’s safe, the business will be based on applications that will be mostly accessed via cloud-enabled network devices.
Funding Statement:The authors would like to acknowledge the support of Network Communication Technology (NCT) Research Groups, FTSM, UKM in providing facilities for this research. This paper is supported under the Dana Impak Perdana UKM DIP-2018-040 and Fundamental Research Grant Scheme FRGS/1/2018/TK04/UKM/02/7.
Conflict of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. H. Muhammed, M. M. Hashim, M. S. Taha, A. H. M. Aman, A. H. A. Hashim et al. (2019). , “Securing medical data transmission systems based on integrating algorithm of encryption and steganography,” in 7th IEEE Int. Conf. on Mechatronics Engineering—ICOM’19, Putrajaya, Malaysia, pp. 1–6. [Google Scholar]
2. M. Marufuzzaman, K. Noorfazila, H. H. Fazida and B. I. R. Mamun. (2015). “Triple data encryption standard encryption engine: A hardware approach,” in Proc. of the 4th Int. Conf. on Computer Science & Computational Mathematics, Langkawi, Malaysia, pp. 53–58. [Google Scholar]
3. A. Zainalabideen, H. M. A. Azana and H. Rosilah. (2019). “Cloud query processing analysis: Encryption and decryption,” 3C Tecnologia, vol. 11, no. 3, pp. 64–75. [Google Scholar]
4. S. Hasimi, C. R. Razli, I. Mohammad, F. Ahmad and B. Rogis. (2018). “Cloud computing implementation in the public sector: Factors and impacts,” Asia-Pacific Journal of Information Technology and Multimedia, vol. 7, no. 2, pp. 27–42. [Google Scholar]
5. A. S. Ahmed, R. Hassan and N. E. Othman. (2015). “Improving security for IPv6 neighbor discovery,” in Int. Conf. on Electrical Engineering and Informatics, Denpasar, Indonesia, pp. 271–274. [Google Scholar]
6. M. G. Aruna and K. G. Mohan. (2020). “Secured cloud data migration technique by competent probabilistic public key encryption,” China Communications, vol. 17, no. 5, pp. 168–190. [Google Scholar]
7. G. Viswanath and P. V. Krishna, “Hybrid encryption framework for securing big data storage in multi-cloud environment,” Evolutionary Intelligence, vol. 13, no. 4, pp. 1–8, 2020. [Google Scholar]
8. S. Kumaresan and V. Shanmugam. (2020). “Time-variant attribute-based multitype encryption algorithm for improved cloud data security using user profile,” Journal of Supercomputing, vol. 76, no. 1, pp. 6094–6112. [Google Scholar]
9. H. Deng, Z. Qin, Q. Wu, Z. Guan, R. Deng. (2020). et al., “Identity-based encryption transformation for flexible sharing of encrypted data in public cloud,” IEEE Transactions on Information Forensics and Security, vol. 15, no. 1, pp. 3168–3180. [Google Scholar]
10. G. S. Kumar and A. S. Krishna. (2019). “Data security for cloud datasets with bloom filters on ciphertext policy attribute based encryption,” International Journal of Information Security and Privacy, vol. 13, no. 4, pp. 2–27. [Google Scholar]
11. S. Tahir, S. Ruj, Y. Rahulamathavan, M. Rajarajan and C. Glackin. (2019). “A new secure and lightweight searchable encryption scheme over encrypted cloud data,” IEEE Transactions on Emerging Topics in Computing, vol. 7, no. 4, pp. 530–544. [Google Scholar]
12. P. K. Premkamal, S. K. Pasupuleti and P. J. A. Alphonse. (2019). “A new verifiable outsourced ciphertext-policy attribute based encryption for big data privacy and access control in cloud,” Journal of Ambient Intelligence and Humanized Computing, vol. 10, no. 7, pp. 2693–2707. [Google Scholar]
13. L. Munn, T. Hristova and L. Magee. (2019). “Clouded data: Privacy and the promise of encryption,” Big Data & Society, vol. 6, no. 1, pp. 1–14. [Google Scholar]
14. K. Lee, D. H. Lee, J. H. Park and M. Yung. (2019). “CCA security for self-updatable encryption: Protecting cloud data when clients read/write ciphertexts,” Computer Journal, vol. 62, no. 4, pp. 545–562. [Google Scholar]
15. S. Namasudra, “An improved attribute-based encryption technique towards the data security in cloud computing,” Concurrency and Computation—Practice & Experience, vol. 31, no. 3, pp. 1–15, 2019. [Google Scholar]
16. O. Zibouh, A. Dalli and H. Drissi. (2019). “A hybrid model encryption for enhancing data security in cloud computing,” in 33rd IBIMA Conf., Granada, Spain, pp. 3840–3849. [Google Scholar]
17. K. Rithvik, S. Kaur, S. Sejwal, P. Narwal and P. Jain. (2019). “Cloud computing data security using encryption algorithms,” IIOAB Journal, vol. 10, no. 2, pp. 75–82. [Google Scholar]
18. B. S. Al-Attab, H. S. Fadewar and M. E. Hodeish. (2019). “Lightweight effective encryption algorithm for securing data in cloud computing,” Advances in Intelligent Systems and Computing, vol. 810, no. 1, pp. 105–121. [Google Scholar]
19. W. Liu, Y. Xu, W. Liu, H. Wang and Z. Lei. (2019). “Quantum searchable encryption for cloud data based on full-blind quantum computation,” IEEE Access, vol. 7, no. 1, pp. 186284–186295. [Google Scholar]
20. M. Alsaedi. (2020). “Novel scheme for image encryption and decryption based on a Hermite-Gaussian matrix,” Advances in Intelligent Systems and Computing, vol. 943, pp. 222–236. [Google Scholar]
21. D. P. Jha, R. Kohli and A. Gupta. (2016). “Proposed encryption algorithm for data security using matrix properties,” in Int. Conf. on Innovation and Challenges in Cyber Security (ICICCS-INBUSHNoida, India, pp. 86–90.
22. M. Es-Sabry, N. El Akkad, M. Merras, A. Saaidi and K. Satori. (2020). “A new image encryption algorithm using random numbers generation of two matrices and bit-shift operators,” Soft Computing, vol. 24, no. 5, pp. 3829–3848. [Google Scholar]
23. W. Chuan-Kun and E. Dawson. (1998). “Generalized inverses in public key cryptosystem design,” IEEE Proceedings: Computers and Digital Techniques, vol. 14, no. 5, pp. 321–326. [Google Scholar]
24. R. E. Hartwig and J. Levine. (1981). “Applications of the Drazin inverse to the Hill cryptographic system,” Cryptologia, vol. 5, no. 4, pp. 213–228. [Google Scholar]
25. R. M. Kumar and S. S. Pradeep Kumar. (2015). “A secure encryption/decryption technique using transcendental number,” International Journal of Computer Trends and Technology, vol. 29, no. 3, pp. 14–18. [Google Scholar]
26. M. K. Viswanath and M. Ranjith Kumar. (2015). “A secure cryptosystem using the decimal expansion of an irrational number,” Applied Mathematical Sciences, vol. 9, no. 106, pp. 5293–5303. [Google Scholar]
27. B. G. Thapa, P. Lam-Estrada and J. López-Bonilla. (2018). “On the Moore–Penrose generalized inverse matrix,” World Scientific News, vol. 9, no. 1, pp. 100–110. [Google Scholar]
28. M. Güllüsaç. (2016). “Generalized inverses of matrices and applications to coding theory, Ph.D. Dissertation,” Dokuz Eylül University, Turkey. [Google Scholar]
29. B. Acharya, G. S. Rath and P. S. Kumar. (2008). “Novel modified Hill cipher algorithm,” in Proc. of ICETAETS, Gujarat, India, pp. 1–7. [Google Scholar]
30. M. K. Viswanath and M. Ranjith Kumar. (2015). “A public key cryptosystem using Hiil’s cipher,” Journal of Discrete Mathematical Sciences and Cryptography, vol. 18, no. 2, pp. 129–138. [Google Scholar]
31. V. Katsikis and D. Pappas. (2011). “The restricted weighted generalized inverse of a matrix,” Electronic Journal of Linear Algebra, vol. 22, no. 1, pp. 1156–1167. [Google Scholar]
32. A. Ben-Israel and T. N. Greville. (2003). Generalized Inverses: Theory and Applications, 2nd ed. New York, USA: Springer-Verlag, pp. 71–84. [Google Scholar]
33. G. R. Wang and Y. L. Chen. (1984). “A recursive algorithm for computing the weighted Moore–Penrose inverse A+MN,” Journal of Computational Mathematics, vol. 4, no. 1, pp. 74–85. [Google Scholar]
34. M. B. Tasić and P. S. Stanimirović. (2008). “Symbolic and recursive computation of different types of generalized inverses,” Applied Mathematics and Computation, vol. 199, no. 1, pp. 349–367.
35. M. B. Tasić, P. S. Stanimirović and S. H. Pepić. (2010). “About the generalized LM inverses and the Weighted Moore Penrose inverse,” Applied Mathematics and Computation, vol. 216, no. 1, pp. 114–124. [Google Scholar]
36. S. H. Pepić. (2020). “Weighted Moore–Penrose inverse: PHP vs. MATHEMATICA,” Facta Universitatis, Series: Mathematics and Informatics, vol. 25, no. 1, pp. 35–45.
37. D. Milošević, S. H. Pepić, M. Saračević and M. Tasić. (2016). “Weighted Moore–Penrose generalized matrix inverse: MySQL vs. Cassandra database storage system,” Sadhana: Academy Proceedings in Engineering Sciences, vol. 41, no. 8, pp. 837–846. [Google Scholar]
38. M. B. Tasić, P. S. Stanimirović and M. D. Petković. (2007). “Symbolic computation of weighted Moore–Penrose inverse using partitioning method,” Applied Mathematics and Computation, vol. 189, no. 3, pp. 1317–1331. [Google Scholar]
39. M. B. Tasić, P. S. Stanimirović and S. H. Pepić. (2011). “Computation of generalized inverses using PHP/MySQL environment,” International Journal of Computer Mathematics, vol. 88, no. 11, pp. 2429–2446. [Google Scholar]
40. R. Cramer, E. Kiltz and C. Padró. (2007). “A note on secure computation of the Moore–Penrose pseudoinverse and its application to secure linear algebra,” in Annual Int. Cryptology Conf. CRYPTO, Santa Barbara, CA, USA, pp. 613–630. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |