DOI:10.32604/cmc.2020.013854

| Computers, Materials & Continua DOI:10.32604/cmc.2020.013854 |  |
| Article |
Managing Security-Risks for Improving Security-Durability of Institutional Web-Applications: Design Perspective
1Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, Saudi Arabia
2Department of Information Technology, Babasaheb Bhimrao Ambedkar University, Lucknow, Uttar Pradesh, India
*Corresponding Author: Raees Ahmad Khan. Email: khanraees@yahoo.com
Received: 24 August 2020; Accepted: 06 October 2020
Abstract: The advanced technological need, exacerbated by the flexible time constraints, leads to several more design level unexplored vulnerabilities. Security is an extremely vital component in software development; we must take charge of security and therefore analysis of software security risk assumes utmost significance. In order to handle the cyber-security risk of the web application and protect individuals, information and properties effectively, one must consider what needs to be secured, what are the perceived threats and the protection of assets. Security preparation plans, implements, tracks, updates and consistently develops safety risk management activities. Risk management must be interpreted as the major component for tackling security efficiently. In particular, during application development, security is considered as an add-on but not the main issue. It is important for the researchers to stress on the consideration of protection right from the earlier developmental stages of the software. This approach will help in designing software which can itself combat threats and does not depend on external security programs. Therefore, it is essential to evaluate the impact of security risks during software design. In this paper the researchers have used the hybrid Fuzzy AHP-TOPSIS method to evaluate the risks for improving security durability of different Institutional Web Applications. In addition, the e-component of security risk is measured on software durability, and vice versa. The paper’s findings will prove to be valuable for enhancing the security durability of different web applications.
Keywords: Web applications; durability; cyber-security; risk; fuzzy logic; decision-making approach
Software development team experiences multiple challenges to improve the usable security of the application. Software companies are often searching for a feasible software protection mechanism. Scientists and developers in this circumstance adjust their plans so that protection of the device can be handled. Risk is a challenge that can disrupt well-defined strategies and have specific aims [1–3]. Risk management process is used not only to minimize the risk but also to increase efficiency through safeguarding the software product. The risk management security strategy is a theoretical structure that tracks the progress of the risk mitigation security programme. Risk management process, control and management for security are interconnected processes that are incorporated into the design of protection for the safe production of software. The technology of risk management assists the whole software development process in the risk reduction activities [4,5].
The optimal risk management protection mechanism is similar to many other concepts with different features. A major study was performed in the field of risk management for security [6,7]. Software security risk management and compliance are essential to handling a variety of safety risks. All systems must be changed in order to produce better performance. The entire software product life cycle is used to define and reduce threats for managing risk strategic. Risk management and control systems have different emphasis in line with the policy and supervision included in the security evaluation, for example, it is not the consequences of criteria like costs and plans, but they are essential components of safety risk management.
In the past, this viewpoint has not been taken into consideration, but the idea of integrated protection is important to be used today. Risk identification and security management systems are a better and more streamlined security performance assessment methodology. Integrated risk assessment uses policies as well as methodologies for realistic protection. Risk management of web applications has become an important task. It computer security is crucial about everything from primary education to intrinsic engineering towards the 21st century [8,9]. Because of the apparent increase and the users reliance on software growth, software applications must be extremely safe everywhere [10].
Over the years we have been making attempts to expand the security of applications to increase transparency and to evaluate how and by what degree our improvements in technology and systems make our applications safer. ‘Design compromise’ has been found in most situations to be one of the most serious security risks. To minimize “time-to-market,” engineers prefer to hasten the design process, which ensures that protection is not built into a product but squeezed from outside. This means that the protection must be taken into account during early stage of software development. According to McGraw [11], risk management system, touch points and expertise are three pillars of application security. Therefore, risk management is one of the main issues to focus upon, if one wishes to improve security. If a threat compromises vulnerability, the risk can be described as the possibility for failure or harm. Development team normally relies on knowledge and experience for risk management without appropriate frameworks for risk management.
Quantification of the security risk factors with previous approaches is very challenging. Sodiya et al. have suggested that appropriate measurement, which itself is a very complicated process, is necessary to determine the real security of any software [12]. The comprehensive fuzzy modeling needed for safety risk evaluation has been divided into two important forms by Shamala et al. [13]: Conventional and Conceptual models based on the study of fuzzy sets. In the context of durable application development, there are few types of security risk assessment. Developers usually discuss several decision-making issues. The design of software development is influenced by enforced complexities which rely mainly on the thinking process of the individual during production about security risk management. Saleh et al. designed a security risk assessment method [14].
The researchers have measured the safety hazards of machines by using fuzzy numbers. For instance, in security risk management [15], Ming-Chang Lee has used sets. The hierarchical analysis interpretation system of safety risk was used by Shedden and others to build a software qualitative safety risk assessment [16] model. Some researchers have used the term of fuzzy inference to characterize the process of uncertainty and analytical hierarchy for structural building and thus rating the various risk factors involved in the software development process [14–16]. Some other researchers have also investigated about the protection strategies including the hierarchical characterization and acceptance. Nevertheless, authors of the present study work have not found any research that focuses on evaluating the impact of security risk for improving security durability of web applications with the help of Fuzzy based Decision-Making Process. That is why our research, in general, evaluated the impact of several security risks factors by using the Fuzzy-TOPSIS method.
The rest of this study is organized as follows: In Section 2, the paper describes the identification and assessment of software security risks at design phase. Section 3 discusses the hybrid fuzzy AHP-TOPSIS methodology and the impact of security risk analysis for web application has been evaluated. Finally, discussion and conclusions are chronicled in Section 4.
2 Identification and Assessment of Software Security Risks at Design Phase
Since the risk management in itself requires professional expertise, the design manager is not necessarily the right person to conduct risk assessment. Thorough review of risk depends heavily on a knowledge of economic impacts including knowledge of legislation and regulation and the software-supported business model. Software designers and developers construct some hypotheses about their systems and the threats they pose and, at a reasonable level, risk and protection experts help in testing the hypotheses of best practices.
Successful techniques of risk analysis have distinct benefits and drawbacks, but most of them have similar good concepts and limitations when they are implemented in advanced software design. This is the capacity to apply classic risk concepts to application design and then to establish specific mitigation criteria that distinguishes a significant risk evaluation from a merely average software evaluation. In the software development process, a high-level strategy to adaptive risk analysis would be thoroughly incorporated [4]. Software security risk management has become a critical task. Towards moving the twenty-first century, software security has become essential for everything from basic education to inherent engineering. As risks are everywhere, so software applications need to be highly secure because of enormous investment and dependency of the users on software development [11]. The following Fig. 1 shows the security risk management process for a software development project.
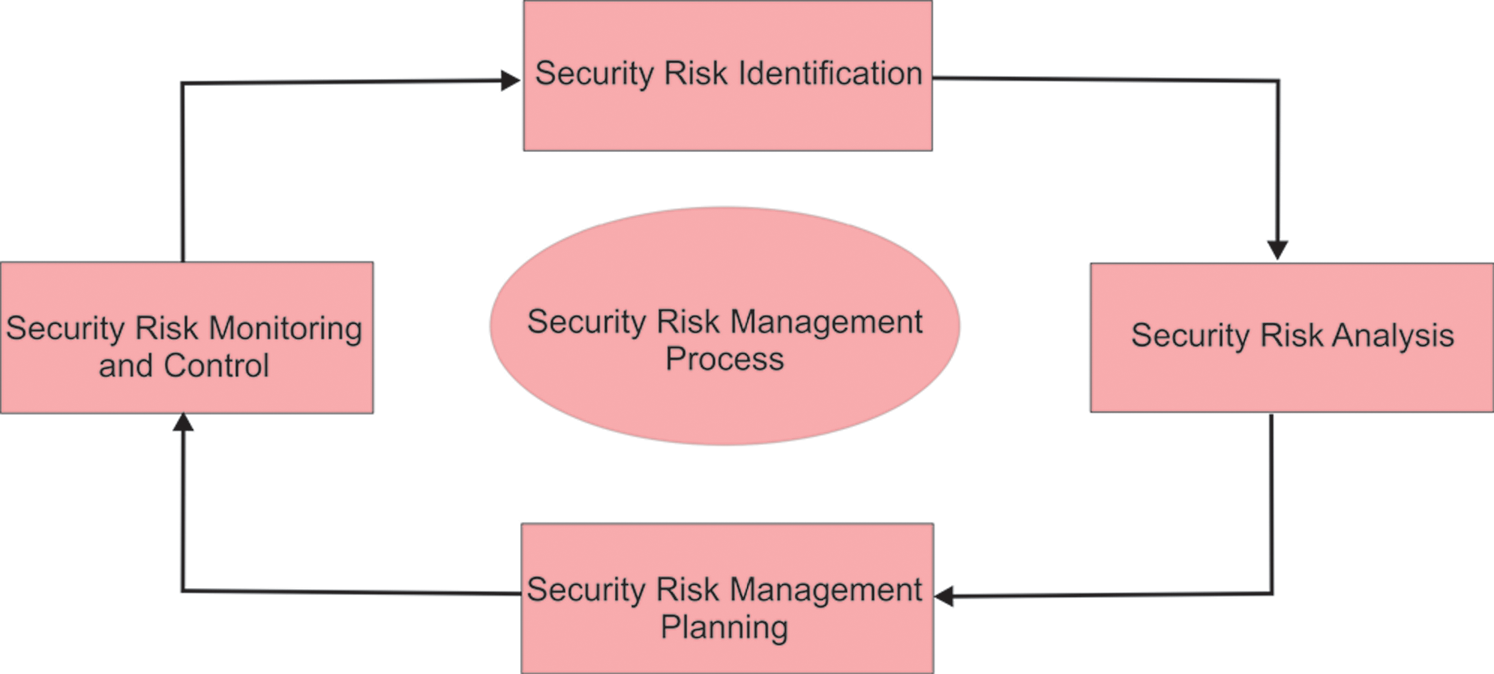
Figure 1: Security risk management process
The essence of the security threats in question should be well known to designers of software development process as they have been shown to have a significant effect on time and production costs. Recognition of security threats and their causes during development may also help developers take initial measures and necessary actions to resolve those threats. It has been found that software computing evaluation of security risks can significantly improve durable software security. The security risk elements software design was first described in this paper. In addition, the hybrid fuzzy AHP-TOPSIS technique is used to measure the impact of these security risks.
2.1 Identification of Design-Level Software Security Risks
Today most service providers are based on technology around the world. It implementation in almost every sector has increased significantly. This makes it important for security issues to be overcome as security breaches can have devastating effects on human lives. Gary McGraw pointed out earlier that protection cannot be poured on any software following its production, but must be evaluated in the development phases [17–19]. It would help develop apps that can actively defend against attack vectors, while relying on some security software application (say, antivirus) to safeguard itself from attacks [20,21]. The key explanation for the excessive breach of security is that loopholes are found in the final product. The early identification and resolution of these inconsistencies can lead to the reduction of these challenges. In general, the design process attempts to prevent errors from being implemented [22,23]. Therefore, the security vulnerabilities that arise during the design stage of the life cycle of software development have to be resolved in order to decrease the incidence of security breaches. In the initial step, recognizing the safety threats that can be addressed would help “install” protection into the program.
The concept of tackling safety problems during the early phases in the software development life cycle is now stressed upon by most researchers. Effective identification and removal of safety threats can help to fix the prevailing security concerns in the production of apps. Devanbu et al. [24] have emphasized on the consideration of security issues at every phase of development life cycle. The authors have also outlined the idea of refining the requirement and design processes so as to shift the focus on initial developmental levels. Baker et al. have dragged the focus towards the lack of valid methodology to quantify the effectiveness of the security measures. According to the authors, it is not the scarcity of security methodologies that hinders the development of secure software, but the absence of proper quantification tools [25,26].
Mehta [27] has highlighted the idea of integrating security in the development process. The author has also stated that the only thing that can help in development of secure software is modifying the development life cycle. Sandeep Gupta [28] has insisted on the application of risk management strategies in the early stages of software development. The author has also proclaimed that late risk management indirectly poses greater threats to secure software development. Steps such as identification of threats, vulnerabilities and determining the appropriate risk mitigation strategies at the design phase have also been proposed by the researcher.
2.2 Need for Design Level Security Risk Identification
Security is widely known to be a combination of two parts, viz., effective risk management and application of proper countermeasures [29,30]. Risk assessment is widely accepted as an integral part of risk management process. The risk assessment process is a complex procedure which consists of the following sub-steps: Identification of various risks; Assessment of the vulnerabilities; Establishment of threats and their countermeasures; Preparation of corrective action plan; and, Review and monitoring. As the first step itself is the identification of the risks, therefore, it becomes a prerequisite to pin them down. Also, the basic aim of risk assessment is to provide apt security levels of a system by ranking the risk on the basis of severity of its impact.
Therefore, recognizing various security threats during the software design phase helps to prevent potential lags which could pose a threat to the security of the system. When the design itself has been intended to measure security risk, it will help minimize the cost and time spent on implementation of security for software. It was found, relative to the design level, that the identification and correction of bugs after production was 100 times crucial [31–33]. Therefore, the security risks associated with software development should be discussed at an early stage.
2.3 Major Security Risks at Design Phase
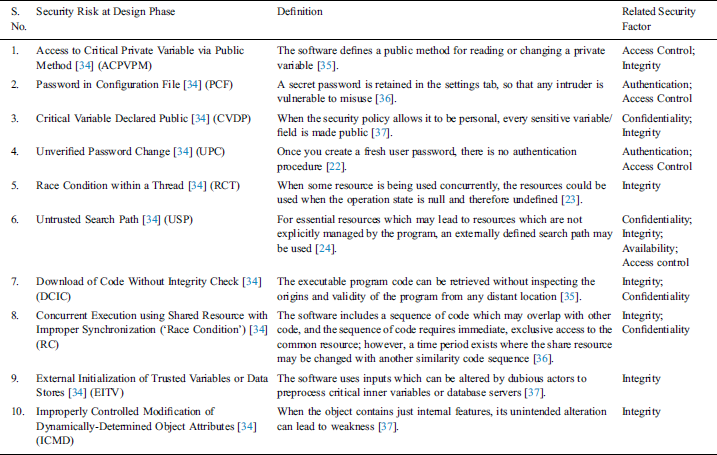
The researchers have selected the critical risks based on the related security factor. Addressing security factors such as confidentiality, access control, authentication, integrity, etc. has become a pre-requisite for secure software development. Especially today, when each and every individual is primarily concerned about the security of his data, it becomes the prime responsibility of the software developers to effectively address them. Therefore, in this proposed work, the authors have filtered the security risks that may penetrate into the software at design phase from Common Weaknesses Enumeration (CWE) list. The CWE is a community that facilitates the secure software development by providing a list of all possible weaknesses that may occur in any software. It serves as a security tool by providing a standard for identification and mitigation of various software weaknesses. The major design-level security risks, as identified by the researchers have been shown in Tab. 1 and Fig. 2 shows the relation of the security risks with the security factors along with risk-definition.
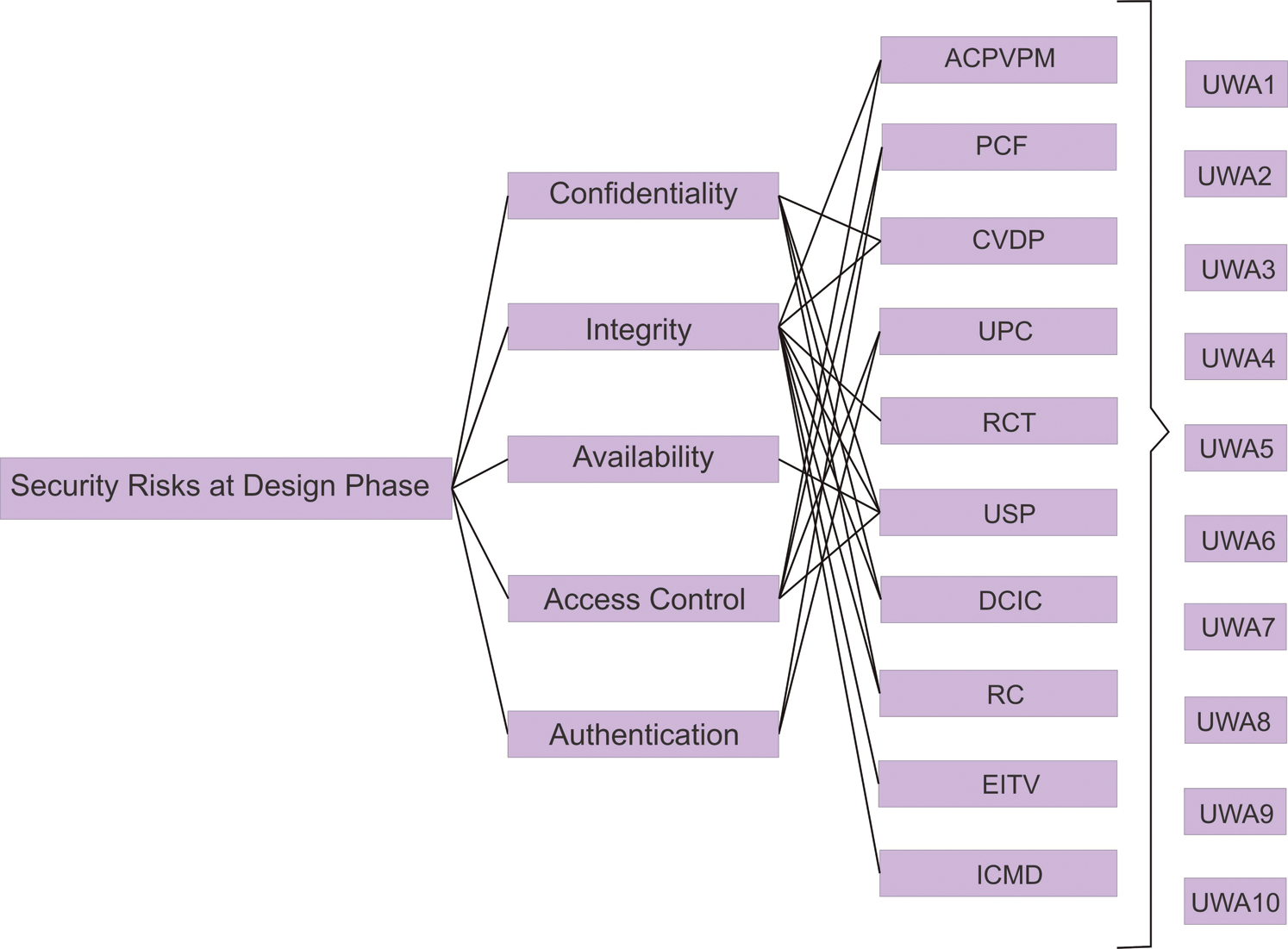
Figure 2: Software security risk attributes in a security-durability design perspective
Table 1: Security risks and related security factor
Fuzzy AHP (Analytical Hierarchy Process) is a stronger method for assessing difficult decision-making problems by evaluating a common graded target rate for any complex question. With the aid of Fuzzy-AHP, the problem is separated into a structure such as a tree. AHP is also used as a decision-making tool to measure rank statistics for different alternatives using a variety of hierarchical parameters [3]. To optimize the efficacy of Fuzzy AHP method for a more feasible perspective, the Fuzzy AHP focuses on the Fuzzy Numerical interval of triangular Fuzzy Numbers. These numbers are introduced to decide the weights of interpretative components. Saaty was the first to propose the AHP process [4]. AHP process utilizes only the matrix of the pair-wise analysis to tackle the inaccuracy in challenges of decision labeling in multi-criteria [6]. The model suggested here allows the use of the triangular fuzzy figures to define the linguistic parameters and to incorporate with AHP fuzzy procedures. Because of the inaccuracy and ambiguity, Zadeh developed the fuzzy based set theory to cope with uncertainty [5]. Fig. 2 shows the hierarchy layout for the MCDM problem. This tree layout can be designed by collating the viewpoints and responses of the domain specialists and experts through questionnaires or brainstorming. The next stage is to develop the Triangular Fuzzy Number (TFN) from the Hierarchy of the Tree. A pair-wise assessment of each category of defined goals plays a key role with the aid of one criterion’s effect on other criterion.
The Technique for Order of Preference by Similarity to Ideal Solution (TOPSIS) considers a multi-criteria decision-making issue of m alternatives like a geometric structure with m points in the n-dimensional space of component. For TOPSIS, the approach used in this research paper is based on the assumption that, for higher and lower ideal solutions, a specified alternative has the shortest and the farthest range from the positive-ideal solution as well as the negative-ideal solution simultaneously [8–15]. Professionals find difficulty in assigning a particular output ranking to an alternative with reference to factor, as shown by Kaur et al. [37]. In compatibility with the actual-world fuzzy setting, this approach applies fuzzy numbers to reflect the relative value of the factor rather than specific numbers. Furthermore, the Fuzzy AHP-TOPSIS approach is especially appropriate for finding solutions of group decision-making in fuzzy settings. Fig. 3 shows the overall weight acquisition process and the feasibility estimation of Fuzzy AHP-TOPSIS methods.
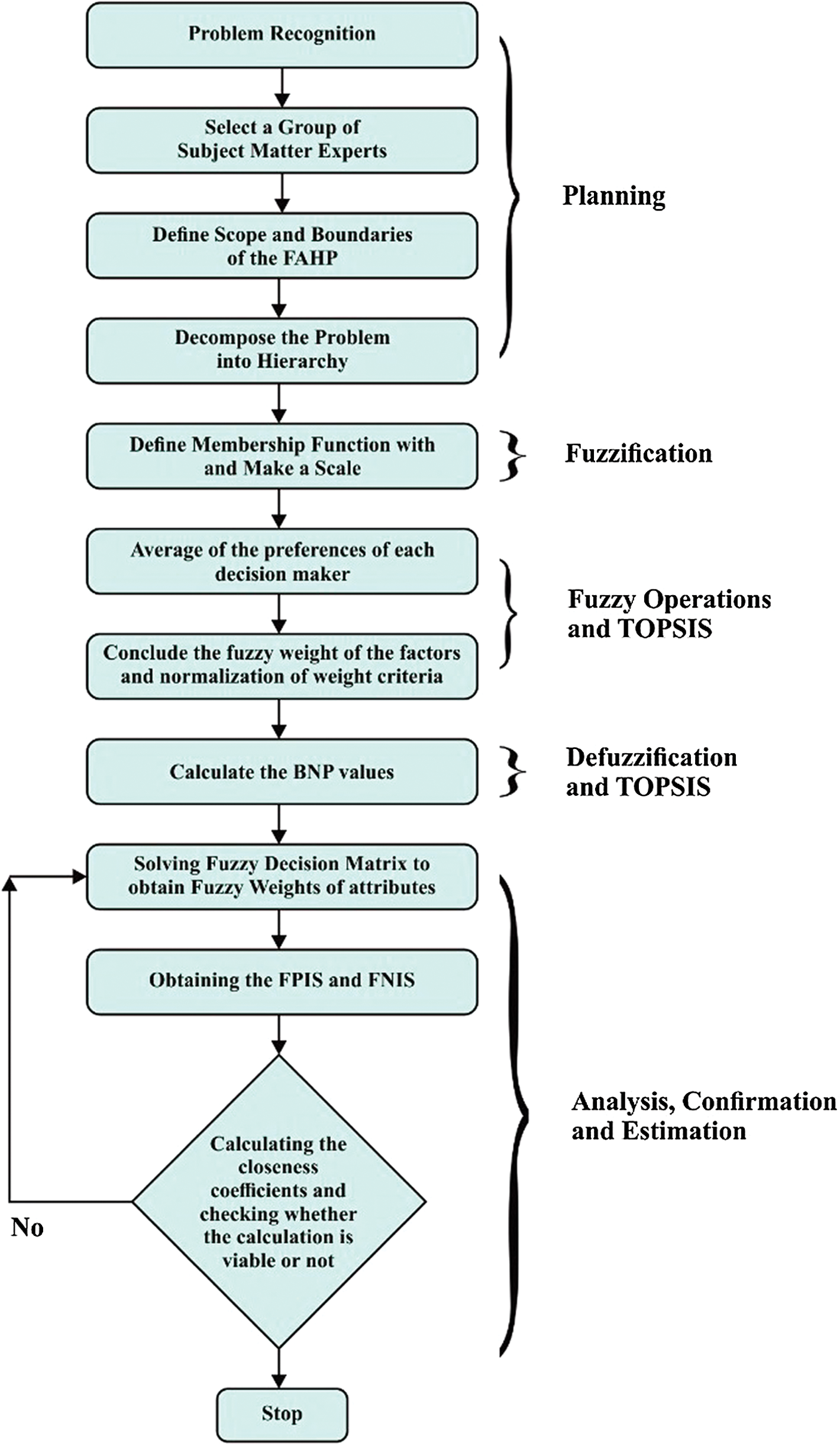
Figure 3: Flow chart of fuzzy AHP-TOPSIS method
This sub-section discusses different statistical findings of integrated fuzzy AHP-TOPSIS model implementation. Security experts usually do a behavior-based research of risks to analyze about previously identified examples of security risk or family of risk. To achieve this, it is important to identify and characterize questionable behaviors from large sets of signs of implementation. IT security experts and academicians face a complicated task of assessing the impact of risk analysis techniques numerically in current cyber-attack setting. To accomplish the objective, in our research paper, we have used an emphatically established and validated decision-making strategy, the integrated fuzzy AHP-TOPSIS. This technique is conversant for prioritizing the malware analysis techniques based on their impact evaluation in current cyber security setting. For eliciting a more convincing outcome, we took suggestions from 80 IT security experts who come from different software industries and educational backgrounds. The information outsourced from these specialists was collected for our empirical investigations. The different factors for security risk evaluation at design phase, i.e., Confidentiality, Integrity, Availability, Access Control and Authentication are represented by T1, T2, T3, T4 and T5, respectively. Systematic approach of fuzzy-AHP TOPSIS is used according to Fig. 4 to determine the impact of the mentioned security risks for different institutional web applications represented by UWA1, UWA2….UWA10.
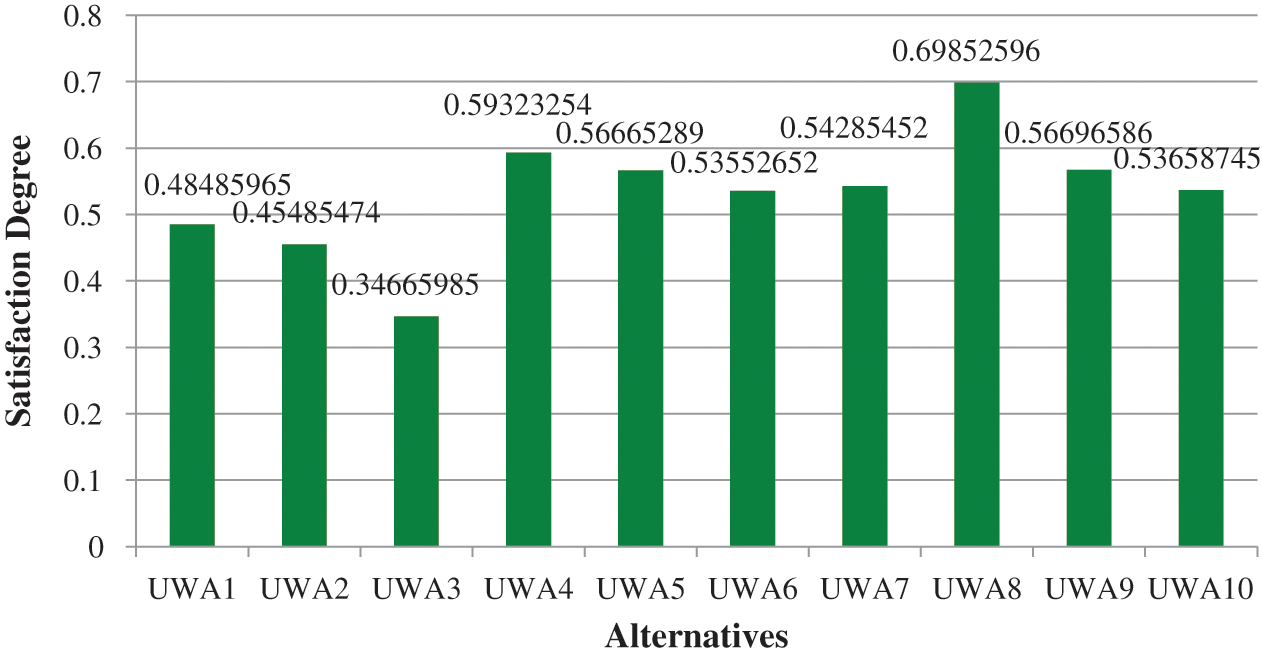
Figure 4: Graphical representation of closeness coefficients to the aspired level among the different alternatives
This was done to determine the variables and calculate the findings. Similarly, the pair-wise comparative matrix of the attributes at level 1 is developed as shown in Tab. 2. Likewise, the composite pair-wise comparative matrix for the level 2 hierarchies has been collated in Tabs. 3–11. Tab. 12 shows the summary of the results. In Tabs. 13 and 14, subjective cognition results of evaluators in linguistic terms, the normalized fuzzy-decision matrix and weighted normalized fuzzy-decision matrix respectively. To be more comprehensive, an integration to measure the weights of the factor of each point is performed. Furthermore, Tab. 15 and Fig. 4 demonstrate the Closeness coefficients to the aspired level among the different alternatives with the help of the hierarchy.
Table 2: Fuzzy-aggregated pair-wise comparison matrix at level 1
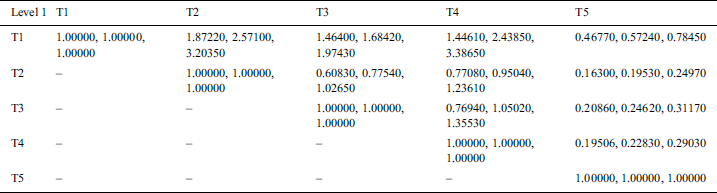
Table 3: Fuzzy aggregated pair-wise comparison matrix at level 2 for confidentiality
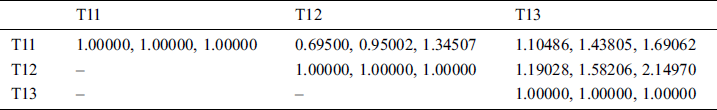
Table 4: Fuzzy aggregated pair-wise comparison matrix at level 2 for integrity
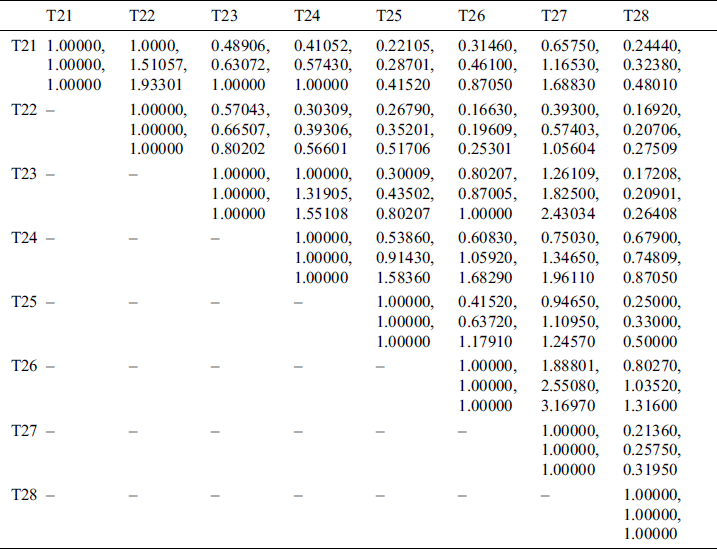
Table 5: Fuzzy aggregated pair-wise comparison matrix at level 2 for access control
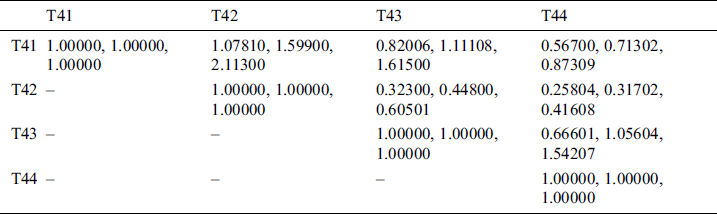
Table 6: Fuzzy aggregated pair-wise comparison matrix at level 2 for authentication

Table 7: Combined pairwise comparison matrix at level 1
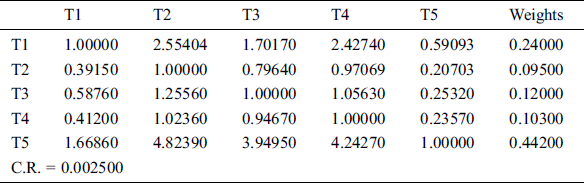
Table 8: Aggregated pair-wise comparison matrix at level 2 for confidentiality
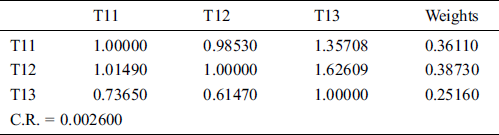
Table 9: Aggregated pair-wise comparison matrix at level 2 for integrity
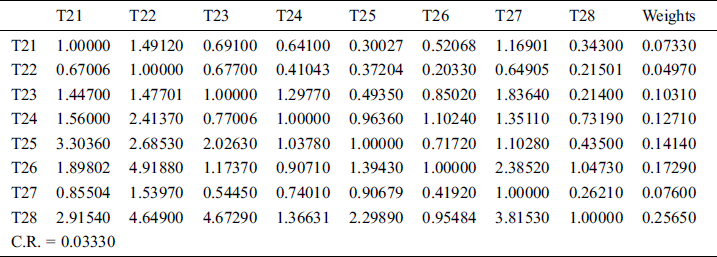
Table 10: Aggregated pair-wise comparison matrix at level 2 for availability
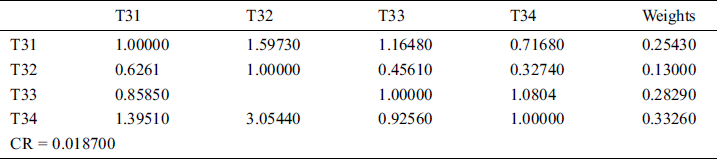
Table 11: Aggregated pair-wise comparison matrix at level 2 for access control
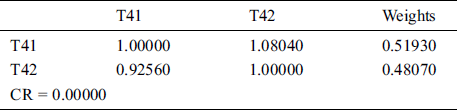
Table 12: Summary of the results
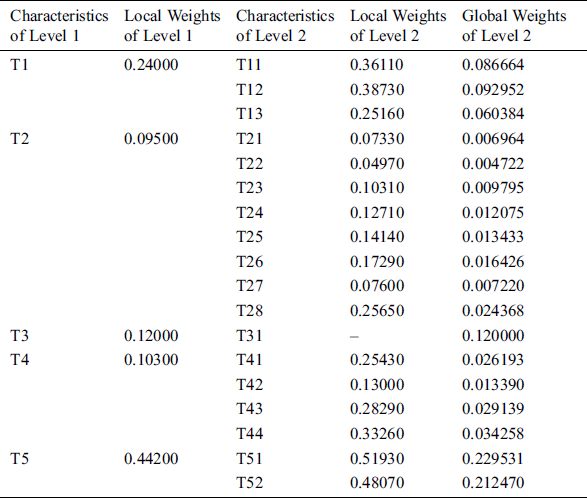
Table 13: Subjective cognition results of evaluators in linguistic terms
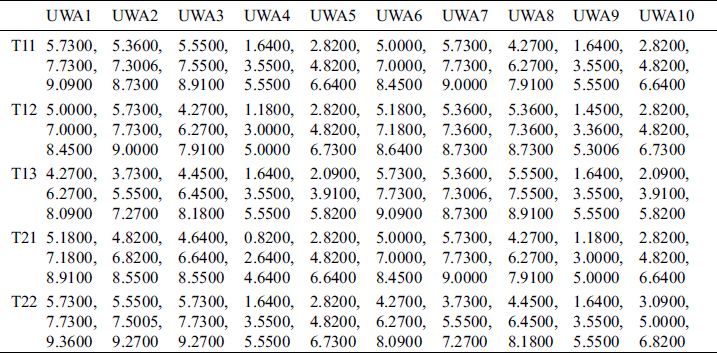
Table 14: The weighted normalized fuzzy-decision matrix
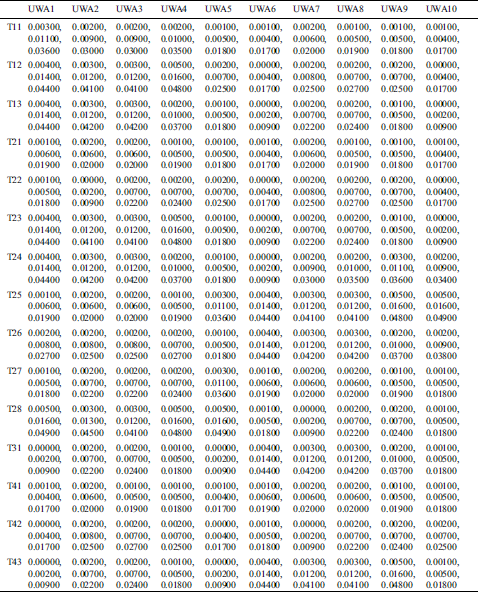
Table 15: Closeness coefficients to the aspired level among the different alternatives
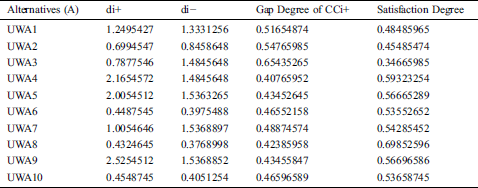
Finally the global weights of factors obtained by fuzzy-AHP are given to fuzzy-TOPSIS method as inputs to generate rank for each alternative. The performance using fuzzy-AHP-TOPSIS has been tested. The determined performance of ten institutional alternatives is as: UWA8, UWA4, UWA9, UWA5, UWA7, UWA10, UWA6, UWA1, UWA2 and UWA3. As per the assessment of this study, UWA8 provides the best security mechanism in security durability perspective among the 10 competitive alternatives.
If security problems are addressed in their evolving stages, it will help to reduce security infringements significantly. Priority should be given to the constructive approach to developing safe apps. When any lapses are found at the early stage it is supposed to result in more effective and stable applications. The use of object oriented technology continues to increase naturally in today’s world, where almost everything is done digitally. It is difficult to ignore the security factor at the same time. Therefore it can be very good for safe software creation in future if these threats of security are related to object-focused properties of design.
In order to accurately interdependence, the researchers can also quantify the relation between these risks and object-oriented design properties. An accurate, effective and reliable program can be used to establish exact mutual reliability. In this study, the Alternative (UWA8) has been determined to provide most effective and durable security framework among all 10 competing choices. With the assessment of information protection in security strategies for the university web application provides guidance and assists practitioners for designing high-quality software products that offer reliable and trustworthy frameworks for protection against both internal and outside threats and attacks.
Acknowledgement: This Project was funded by the Deanship of Scientific Research (DSR), King Abdulaziz University, Jeddah, under grant No. G-323-611-1441. The authors, therefore, gratefully acknowledge DSR technical and financial support.
Funding Statement: Deanship of Scientific Research (DSR), King Abdulaziz University, Jeddah, Kingdom of Saudi Arabia, under grant No. G-323-611-1441.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. T. J. Ansari, D. Pandey and M. Alenezi. (2018). “STORE: Security threat oriented requirements engineering methodology,” Journal of King Saud University-Computer and Information Sciences, pp. 1–17. [Google Scholar]
2. R. Kumar, S. A. Khan and R. A. Khan. (2017). “Fuzzy analytic hierarchy process for software durability: Security risks perspective,” Advances in Intelligent Systems and Computing, vol. 508, pp. 469–478. [Google Scholar]
3. S. A. Khan, M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan. (2020). “Evaluating performance of software durability through an integrated fuzzy-based symmetrical method of ANP and TOPSIS,” Symmetry, vol. 12, no. 4, pp. 1–15. [Google Scholar]
4. A. Agrawal, M. Zarour, M. Alenezi, R. Kumar and R. A. Khan. (2019). “Security durability assessment through fuzzy analytic hierarchy process,” PeerJ Computer Science vol. 8, pp. 1–43. [Google Scholar]
5. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al. (2020). , “A knowledge based integrated system of hesitant fuzzy set, AHP and TOPSIS for evaluating security-durability of web applications,” IEEE Access, vol. 8, no. 2, pp. 48870–48885. [Google Scholar]
6. M. T. J. Ansari and D. Pandey. (2018). “An integration of threat modeling with attack pattern and misuse case for effective security requirement elicitation,” International Journal of Advanced Research in Computer Science, vol. 8, no. 3, pp. 24–29. [Google Scholar]
7. R. Kumar, M. Zarour, M. Alenezi, A. Agrawal and R. A. Khan. (2019). “Measuring security-durability through fuzzy based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642. [Google Scholar]
8. M. T. J. Ansari, D. Pandey and N. A. Khan. (2019). “Comparative literature analysis on security requirements engineering,” International Journal of Engineering Sciences and Research Technology, vol. 8, no. 12, pp. 113–124. [Google Scholar]
9. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan. (2018). “Measuring the security attributes through fuzzy analytic hierarchy process: Durability perspective,” ICIC Express Letters–An International Journal of Research and Surveys, vol. 12, no. 6, pp. 615–620. [Google Scholar]
10. R. Kumar, S. A. Khan and R. A. Khan. (2016). “Durability challenges in software engineering,” CrossTalk–The Journal of Defense Software Engineering, vol. 32, no. 8, pp. 29–31. [Google Scholar]
11. G. McGraw. (2004). “Software security,” IEEE Security & Privacy Magazine, vol. 2, no. 2, pp. 80–83. [Google Scholar]
12. A. S. Sodiya, S. A. Onashoga and O. B. Ajayĩ. (2006). “Towards building secure software systems,” Issues in Informing Science and Information Technology, vol. 3, no. 12, pp. 35–42. [Google Scholar]
13. P. Shamala, R. Ahmad and M. Yusoff. (2013). “A conceptual framework of info structure for information security risk assessment (ISRA),” Journal of Information Security and Applications, vol. 18, no. 1, pp. 45–52. [Google Scholar]
14. Z. I. Saleh, H. Refai and A. Mashhour. (2011). “Proposed framework for security risk assessment,” Journal of Information Security, vol. 2, no. 2, pp. 85–90. [Google Scholar]
15. M. C. Lee. (2014). “Information security risk analysis methods and research trends: AHP and fuzzy comprehensive method,” International Journal of Computer Science and Information Technology, vol. 6, no. 1, pp. 29–35. [Google Scholar]
16. P. Shedden, R. Scheepers, W. Smith and A. Ahmad. (2011). “Incorporating a knowledge perspective into security risk assessments,” ICIC Express Letters-An International Journal of Research and Surveys, vol. 12, no. 14, pp. 4567–4573. [Google Scholar]
17. P. Kocher, R. Lee, G. McGraw and A. Raghunathan. (2004). “Security as a new dimension in embedded system design,” Proceedings of the 41st Annual Design Automation Conference IEEE, vol. 25, pp. 753–760. [Google Scholar]
18. K. Sahu, R. Shree and R. Kumar. (2014). “Risk management perspective in SDLC,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 4, no. 3, pp. 1247–1251. [Google Scholar]
19. R. Kumar, S. A. Khan and R. A. Khan. (2015). “Revisiting software security: durability perspective,” International Journal of Hybrid Information Technology, vol. 8, no. 2, pp. 311–322. [Google Scholar]
20. K. Sahu and R. K. Srivastava. (2018). “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222. [Google Scholar]
21. R. Kumar, S. A. Khan and R. A. Khan. (2014). “Software security durability,” International Journal of Computer Science and Technology, vol. 5, no. 2, pp. 23–26. [Google Scholar]
22. K. Sahu and Rajshree. (2015). “Stability: Abstract roadmap of security,” American International Journal of Research in Science, Engineering and Mathematics, vol. 2, no. 9, pp. 183–186. [Google Scholar]
23. A. Agrawal, M. Alenezi, R. Kumar and R. A. Khan. (2019). “Measuring the sustainable-security of web applications through a fuzzy-based integrated approach of AHP and TOPSIS,” IEEE Access, vol. 7, pp. 153936–153951. [Google Scholar]
24. P. T. Devanbu and S. Stubblebine. (2000). “Software engineering for security: A roadmap,” Proceedings of the Conference on the Future of Software Engineering, IEEE, vol. 254, pp. 227–239. [Google Scholar]
25. R. Kumar, S. A. Khan and R. A. Khan. (2015). “Durable security in software development: Needs and importance,” CSI Communication, vol. 39, no. 7, pp. 34–36. [Google Scholar]
26. K. Sahu and R. K. Srivastava. (2020). “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37. [Google Scholar]
27. D. M. Mehta. (2007). “Effective software security management,” Technical Report, OWASP, . [online]. Available: https://www.owasp.org/images/2/28/Effective_Software_Security_Management.pdf, last visit Aug 20, 2020. [Google Scholar]
28. J. Kaur, A. Agrawal and R. A. Khan. (2018). “Major software security risks at design phase,” ICIC Express Letters–An International Journal of Research and Surveys, vol. 12, no. 14, pp. 4578–4584. [Google Scholar]
29. K. Sahu and R. Shree. (2015). “Software security: A risk taxonomy,” International Journal of Computer Science and Engineering Technology, vol. 7, no. 3, pp. 36–41. [Google Scholar]
30. A. H. Seh, M. Zarour, M. Alenezi, A. K. Sarkar, A. Agrawal et al. (2020). , “Healthcare data breaches: Insights and implications,” Healthcare, vol. 8, no. 133, pp. 1–18. [Google Scholar]
31. K. Sahu and R. Shree. (2015). “Helpful and defending actions in software risk management: A security viewpoint,” Integrated Journal of British, vol. 4, pp. 1–7. [Google Scholar]
32. M. Alenezi, R. Kumar, A. Agrawal and R. A. Khan. (2019). “Usable-security attribute evaluation using fuzzy analytic hierarchy process,” ICIC Express Letters–An International Journal of Research and Surveys, vol. 13, no. 6, pp. 453–460. [Google Scholar]
33. K. Sahu and R. K. Srivastava. (2019). “Revisiting software reliability,” Data Management, Analytics and Innovation (Advances in Intelligent Systems and Computing). Springer, vol. 808, pp. 221–235. [Google Scholar]
34. Weaknesses introduced during design, Common Weakness Enumeration, . [online]. Available: https://cwe.mitre.org/data/definitions/701.html. [Google Scholar]
35. CWE-767: Access to critical private variable via public method, Common Weakness Enumeration, . [online]. Available: https://cwe.mitre.org/data/definitions/767.html. [Google Scholar]
36. CWE-915: Improperly controlled modification of dynamically-determined object attributes, Common Weakness Enumeration, . Available: https://cwe.mitre.org/data/definitions/915.html, last visit Aug 20, 2020. [Google Scholar]
37. J. Kaur, A. I. Khan, Y. B. Abushark, M. M. Alam, S. A. Khan et al. (2020). , “Security risk assessment of healthcare web application through adaptive neuro-fuzzy inference system: A design perspective,” Risk Management and Healthcare Policy,Dove Press, vol. 13, no. 5, pp. 355–371. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |