DOI:10.32604/cmc.2021.013034

| Computers, Materials & Continua DOI:10.32604/cmc.2021.013034 |  |
| Article |
Metaheuristic Clustering Protocol for Healthcare Data Collection in Mobile Wireless Multimedia Sensor Networks
1Department of Computer Science, Pondicherry University, Puducherry, 605014, India
2Department of Information Technology, M.Kumarasamy College of Engineering, Karur, 639113, India
3Faculty of Computers and Information, Mansoura University, Egypt
4Department of Entrepreneurship and Logistics, Plekhanov Russian University of Economics, Moscow, 117997, Russia
5Department of Logistics, State University of Management, Moscow, 109542, Russia
6Department of Computer Applications, Alagappa University, Karaikudi, India
*Corresponding Author: K. Shankar. Email: drkshankar@ieee.org
Received: 22 July 2020; Accepted: 23 October 2020
Abstract: Nowadays, healthcare applications necessitate maximum volume of medical data to be fed to help the physicians, academicians, pathologists, doctors and other healthcare professionals. Advancements in the domain of Wireless Sensor Networks (WSN) and Multimedia Wireless Sensor Networks (MWSN) are tremendous. M-WMSN is an advanced form of conventional Wireless Sensor Networks (WSN) to networks that use multimedia devices. When compared with traditional WSN, the quantity of data transmission in M-WMSN is significantly high due to the presence of multimedia content. Hence, clustering techniques are deployed to achieve low amount of energy utilization. The current research work aims at introducing a new Density Based Clustering (DBC) technique to achieve energy efficiency in WMSN. The DBC technique is mainly employed for data collection in healthcare environment which primarily depends on three input parameters namely remaining energy level, distance, and node centrality. In addition, two static data collector points called Super Cluster Head (SCH) are placed, which collects the data from normal CHs and forwards it to the Base Station (BS) directly. SCH supports multi-hop data transmission that assists in effectively balancing the available energy. A detailed simulation analysis was conducted to showcase the superior performance of DBC technique and the results were examined under diverse aspects. The simulation outcomes concluded that the proposed DBC technique improved the network lifetime to a maximum of 16,500 rounds, which is significantly higher compared to existing methods.
Keywords: Smart sensor environment; healthcare data; multimedia; big data processing; clustering; mobility; energy efficiency
In the recent days, the communication of information through multimedia data such as images, audio, videos, etc. becomes essential in different domains, especially hospitals and healthcare institutions. For smart healthcare environment, Mobile-Wireless Multimedia Sensor Networks (M-WMSNs) is a better choice which comprises of a number of mobile sensor nodes with multimedia devices that can capture the details of the patients. M-WMSNs are highly versatile compared to traditional WSNs in which the sensor nodes undergo deployment in various scenarios and deal with frequent topology modifications. The mobile sensor node comprises of a processing unit, sensor array (temperature, humidity, pressure, mobility, etc.) and communication unit for which the energy is supplied from batteries. Furthermore, additional elements such as cameras and microphones are available for capturing multimedia data [1]. The process of capturing multimedia data is useful to properly analyze the environment.
M-WMSNs have a wide range of applications such as environment monitoring, mining, weather prediction, acoustic detection, hospital management, underwater surveillance, border monitoring, etc. [2]. There are two issues in M-WMSN, i.e., hardware and platform. The important limitations in hardware are inbuilt power source and cost-effective installation cost. Here, the nodes should operate using the energy available and further low complex techniques are needed for processing the data [3]. Mobility model defines the direction of motion of sensor nodes and the way to determine its location, speed and upcoming locations. The important characteristics of M-WMSN are shared communication medium and frequent topology changes. The communication media indicate that the channel access should be controlled. Hence, network topology is a significant responsibility when it comes to designing the routing protocols since it selects the optimal routes between two nodes [4,5]. Since the nodes are mobile, the effectiveness of the available network topologies cannot be applied in case of large scale M-WMSN.
To overcome these challenges, hybridized topology is a good solution and the best choice for implementation in large-scale environment [6–8]. In addition, the routing protocol decides an effective and reliable data transmission route. Based on the resource availability of nodes in M-WMSN, these are categorized into homogeneous and heterogeneous M-WMSNs. In homogeneous M-WMSNs, all the sensor networks possess similar properties such as residual energy, computation and processing capabilities. However, heterogeneous M-WMSN comprises of mobile sensor nodes with different capabilities such as battery capacity, storage, processing capability, mobility speed, and so on. The process of deploying nodes in heterogeneous type is a challenge when compared to homogeneous M-WMSN [9,10].
Out of the existing diverse set of solutions available, cluster-based routing protocol is the most-commonly employed solution to achieve effective data collection and energy efficiency. Though various clustering techniques have been developed for M-WMSN, a need exists to further improve the energy efficiency by considering different perspectives. Most of the existing works concentrated only on energy efficiency. However, in the current research, the authors incorporated energy efficient clustering technique while at the same time included a concept of utilizing super CH (SCH) for inter-cluster data transmission. The adoption of SCH is an added advantage to achieve energy efficiency and network lifetime. In this paper, the authors attempted to derive a Density Based Clustering (DBC) technique to select CHs on the basis of three input variables which include remaining energy level, distance and node centrality. The proposed method is mainly employed for data collection and communication in healthcare environment. In addition, two static data collector points called SCH are placed to collect the data from CHs and then forwards it to the BS directly. The use of SCH supports multi-hop communication which helps balance the available energy efficiency. The proposed method was validated experimentally and the results are verified in terms of network lifetime, energy efficiency and throughput. A detailed investigation of the obtained results is made and compared with other methods such as Low Energy Adaptive Clustering Hierarchy (LEACH), Threshold-based Energy Efficient Network (TEEN) and mobile LEACH (M-LEACH).
In short, the contributions of the present paper are listed as follows:
• Introduction of a new DBC technique for energy efficient clustering
• Utilization of three parameters namely remaining energy level, distance and node centrality for effective CH selection
• Incorporation of two static data collector points i.e., SCH for effective load balancing
• A detailed simulation analysis conducted to ensure the superior performance of DBC technique
The arrangement of the research is given as follows: Sections 2 and 3 explain the related works, DBC method in brief and also details about the experimental analysis part. The final section concludes the work with future scope.
The author [11] discussed the usage of mobility nature in sensor nodes and reported possible applications such as habitat monitoring of birds and animals, glacier observation, disaster management, military vehicle tracking, locating snipers, and so on. Among these different possible applications, some of the nodes are completely mobile while few others move partially. So, the mobile sensor node plays a vital part in real time applications [12]. The challenges associated with the design of M-WMSN are installation cost, system model, deployment structure, storage, inbuilt battery capacity, energy utilization, data aggregation, fault tolerant, connectivity [13–15] and security [16–22]. The complete structure of a mobile sensor node is similar to typical sensor node with few extra components such as location finder, mobile unit, and power generator [23]. The location finder identifies the exact position of the sensor node, while the mobile unit provides mobility to the attached node. The battery unit is connected in every other unit present in the node which supplies the energy for sensing, processing and communication operations. The outcome from the power generator is provided as input to the power unit, which acts as a source to recharge the power unit in exceptional cases. The network topology is useful to transmit the data from nodes to the BS, whereas the latter is linked with internet. Large scale M-WMSN functions occur solely based on data gathering or topology control method. So, the topology provides a highly reliable network with efficient QoS based on mobility, traffic, dedicated link, and so on. Additionally, the topology defines the sensing area, addition or deletion of members in the group. After considering different dimensions in the network topology, efficient data collection can be achieved with low energy consumption, while at the same time better M-WMSN can be produced.
The routing techniques, available for M-WMSN, are centralized, distributed or hybrid. A new effective routing technique is designed for M-WMSN by considering the network topology, node’s mobility, power utilization, coverage, and so on. In Reference [24], a mobility-based protocol called Mobile LEACH was presented for M-WMSN. The process of mobile LEACH was similar to that of the traditional LEACH [25]. However, such a method enabled the process of including mobile nodes like normal nodes in the setup phase and rearranged the clusters in terms of energy utilization. When the cluster gets organized, the Cluster Head (CH) allocates a time slot for all the nodes in the cluster. In addition, the cluster members can switch off the radio, excluding the transmission time, in order to diminish the energy utilization of every sensor node. The attained results verified that the Mobile LEACH was superior to LEACH in terms of reducing packet loss. In WMSN, massive amount of data transmission occurs compared to traditional WSN. Hence, clustering techniques can be deployed to reduce energy utilization. Clustering, a process in which the clusters are formed using the nearby nodes with similar properties, is one of the predominantly-used energy efficient techniques. Cluster contains a CH and cluster members. The cluster members sense the data and forward it to BS. In some cases, the data collector node is also placed. This data collector node possesses the capability to collect data from CHs and forward it to BS. The overall clustering process in M-WMSN is displayed in Fig. 1.

Figure 1: The architecture of M-WMSN
For WSN, researchers [26] proposed a Distributed Uniform Clustering Algorithm (DUCA) earlier. However, DUCA is not suitable for M-WMSN since it is modeled for static WSN as uniform distribution of nodes and grids. In the study conducted earlier [27], a cluster-based routing technique called LEACH-Mobile (LEACHM) was proposed. For CH election, LEACH-M would not assume any factors for mobility. During steady phase, it attains information reliability by broadcasting supplementary control packets and reduces its energy consumption. The authors [28] proposed a routing technique called LEACH-Mobile Enhanced (LEACH-ME). In this method, CH is selected in LEACH depending on energy and mobility factors. However, its energy efficacy remained low and the count of control packets is decided based on the estimation of mobility [29]. Based on LEACH, the researchers [30] projected a mobility-based Cluster Based Routing protocol (CBR-Mobile). For new nodes, CBR-Mobile dynamically assigned information to transfer the slots in CBR-Mobile Time Division Multiple Access (TDMA). The major disadvantage in this method is that mobility factor is not assumed. In radio transmitter over-to-aid traffic and mobility adaption, the reliability in CBR-Mobile is attained at higher energy absorption rate by nodes.
Clusters are developed by segmenting the whole field into grids in the protocol i.e., Efficient Clustering and Routing Protocol (EECRP) which was proposed in [31]. Grid-head is a node which contains higher energy and communication range. As a precinct, each and every node is considered to be 1-hop away. To transmit information to the nodes outside the cluster, the paths are selected depending upon the maximum nodal energy in Inter-cluster reactive routing. The studies conducted earlier [32] and [33] projected grid-based routing techniques, where the mobile sinks are placed in the network. By employing grids, both protocols recognize the ‘activity’ as well as ‘searching path.’ For data collection, it does not include any clustering. The authors [34] presented a mobile direct and multihop LEACH to improve the network lifetime of M-WMSN. In direct type, the sensor node transmits the data straight away to BS, whereas the multi-hop LEACH follows multi-hop communication. To improve the lifetime of M-WMSN, MSRP [35] was introduced. Here, mobile BS was used instead of static BS. The mobile BS gathers the data with regards to remaining energy level about the CHS and shifts it to high energy CHs.
In the study [36], a new Artificial Bee Colony (ABC) based algorithm was developed using mobile BS to identify the optimal route for data collection in M-WMSN. The study [37] designed a Mobility-Based Clustering (MBC) technique to improve the efficiency of M-WMSN. The operation of MBC is similar to that of LEACH. MBC takes some connection time to form clusters during when it constructs a reliable path using stability or availability of every connection among the cluster members and CHs. Since the energy utilization of transmitting images and videos is a main concern in M-WMSN, there is a need to develop big data processing technique in smart sensor environment like M-WMSN.
M-WMSN is generated using ‘N’ number of mobile sensor nodes, which are arbitrarily placed in the target area (i.e., healthcare environment) with subsequent considerations:
• Nodes are mobile, whereas the BS and SCH are stationary.
• Nodes are heterogeneous.
• Nodes are unaware of their position coordinates.
• Death of nodes occurs due to exhaustion of energy.
• Nodes could adjust the communication power.
A simplified first order radio energy model is utilized here [27]. The total quantity of energy consumption to transmit l-bit packet over a distance, ‘d’ can be equated by

The energy spent for free space propagation 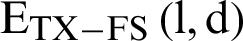 is computed as
is computed as

The energy spent for multipath propagation 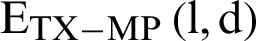 is computed as
is computed as

where 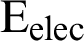 denotes the energy dissipation per bit in source or destination side,
denotes the energy dissipation per bit in source or destination side, 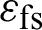 and
and 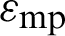 indicate the energy dissipated per bit in RF amplifier and d0is the threshold distance which is computed by:
indicate the energy dissipated per bit in RF amplifier and d0is the threshold distance which is computed by:

The total sum of energy consumption to receive l-bit can be equated as follows:

This model is used to estimate the total amount of energy required for transmitting and receiving data between two mobile nodes.
For distance (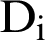 ) computation, the nearby nodes can be identified for each node and is equated as:
) computation, the nearby nodes can be identified for each node and is equated as:

where 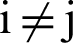 ,
, 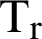 denotes the transmission range of node, and
denotes the transmission range of node, and 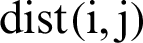 is the distance between nodes i and j. The distance
is the distance between nodes i and j. The distance 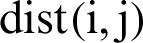 is Euclidian distance and is determined as follows.
is Euclidian distance and is determined as follows.
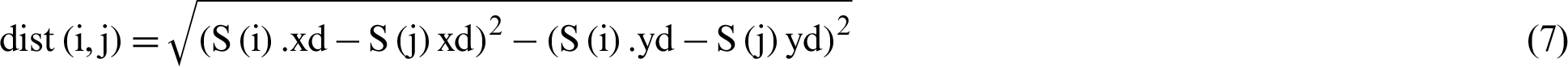
The basic idea of DBC method is to group the sensor nodes on the basis of similar properties, i.e., dense regions, for instance, the nodes with similar amount of residual energy are grouped together to form a cluster. In the proposed DBC algorithm, the aim is to cluster the sensor nodes which possess high energy, less distance and high centrality. DBC algorithm operates in two phases such as setup and steady states as portrayed in Fig. 2. In the setup state, the DBC algorithm forms the clusters and CHs are selected for each cluster. In steady state, the DBC algorithm enables the cluster members to forward the data to CH. Then the CHs transmit the data to the BS or data collector (SCH), whichever is closer. SCH receives, aggregates, and transmits data to the BS. The detailed workflow of the proposed DBC method is given in the Algorithms 1 to 4.

Figure 2: The overall operation of the DBC algorithm
In the beginning, the deployed region is divided into two equaled space regions called grid in a horizontal way. For instance, in a network area of  m2, the region is divided into two grids, each measuring
m2, the region is divided into two grids, each measuring  m2. After nodes are deployed, the grids are formed. Then, every node shares its information to its nearby nodes. In M-WMSN, data fusion is recommended in which every round of the gathering task results in a predefined number
m2. After nodes are deployed, the grids are formed. Then, every node shares its information to its nearby nodes. In M-WMSN, data fusion is recommended in which every round of the gathering task results in a predefined number  of sensor nodes as the CHs. At the initial rounds, each sensor node creates a random number between 0 and 1 and a comparison is made with arbitrary value and a probability value
of sensor nodes as the CHs. At the initial rounds, each sensor node creates a random number between 0 and 1 and a comparison is made with arbitrary value and a probability value 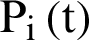 . When the arbitrary value is less than
. When the arbitrary value is less than 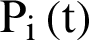 , the node occasionally transmits an advertisement message to its nearby nodes in order to intimate that it would be the CH. In such scenario, the
, the node occasionally transmits an advertisement message to its nearby nodes in order to intimate that it would be the CH. In such scenario, the 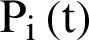 can be equated by:
can be equated by:

where, 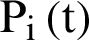 is the possibility that node acts as the CH at time
is the possibility that node acts as the CH at time 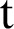 . Here
. Here 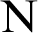 and
and 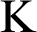 indicate the nodes and CHs at every CHs and during every round whereas
indicate the nodes and CHs at every CHs and during every round whereas 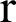 indicates the present working round. Since DCH is a distributed clustering technique, the nodes exchange its own information directly.
indicates the present working round. Since DCH is a distributed clustering technique, the nodes exchange its own information directly.
By leveraging the information communication process, each node updates its neighbor details in the form of a triplet {Ei, Di, Ci}, where Ei, Di and Ci denote the energy level, distance and centrality. Energy Ei is computed using the Eqs. (3) and (5). Next, the distance Di is determined using the Eqs. (6) and (7). Node centrality value indicates how far the node is present centrally among its neighbors. This value is determined by taking a total of the squared distance of sensor nodes from a fixed sensor node.
The nodes, with almost identical values in the triplet, are grouped together to form a cluster. At the beginning, every node considers itself as a candidate for CH selection. When a node finds a neighboring node with higher energy, it becomes a cluster member automatically. This process continues until a CH is selected. In each cluster, a CH is selected and the status is broadcasted to every cluster member. The cluster member may get two CH status messages, in case of overlapping communication range of two nodes. In such cases, the node joins with the nearest CH. As exceptional cases, the nodes sometimes fail to join any other CH by choosing itself as a CH. These nodes are called ‘isolated nodes’ which transmit the data to the nearby CH. When a CH or cluster member moves out of the cluster, the CH selection process is repeated and relative mobility needs to be computed. Relative mobility 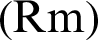 of nodes indicates relative mobility among sensor nodes and CH, not the total vector of velocities, as it indicates stable clusters. Further, the nodes with less mobility should be chosen as CHs. The relative mobility is computed by:
of nodes indicates relative mobility among sensor nodes and CH, not the total vector of velocities, as it indicates stable clusters. Further, the nodes with less mobility should be chosen as CHs. The relative mobility is computed by:
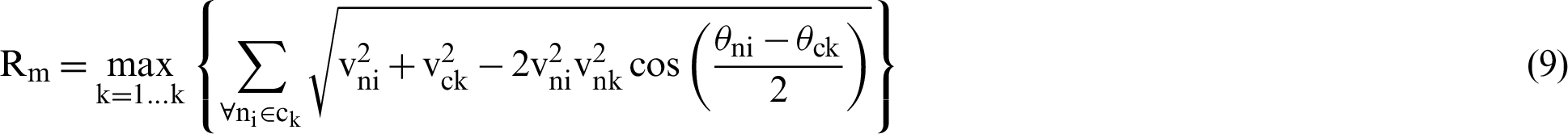
where 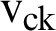 is the velocity of CH,
is the velocity of CH, 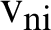 is the moving velocity of CMs,
is the moving velocity of CMs, 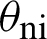 is the movement angle of nodes, and
is the movement angle of nodes, and 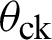 is the movement angle of CH.
is the movement angle of CH.
For illustration, three sample scenarios are taken and shown in the Figs. 3–5. In a network of 30 mobile sensor nodes, four clusters are formed with 4 CHs and 2 static SCHs. In scenario 1, the mobile sensor nodes are formed into four clusters and CH is selected from every cluster. From each cluster, the selected CHs are N8, N21, N13 and N30 for clusters 1–4 respectively. For instance, in cluster 1, the selected CH is N8 and the cluster members are N2, N3, N4 and N5 respectively. Similarly, in cluster 2, the selected CH is N32 and the corresponding cluster members are N15, N16, N17, N18 and N19. In cluster 3, the chosen CH is N13 which has three cluster members i.e., N9, N10 and N14. In cluster 4, the selected CH is N30 whereas the cluster members are N22, N23, N24 and N25. It is also shown that two SCHs are placed in this region to receive data from CHs and forward it to BS.

Figure 3: Scenario 1: Cluster construction by DBC algorithm

Figure 4: Scenario 2: Cluster construction by DBC algorithm
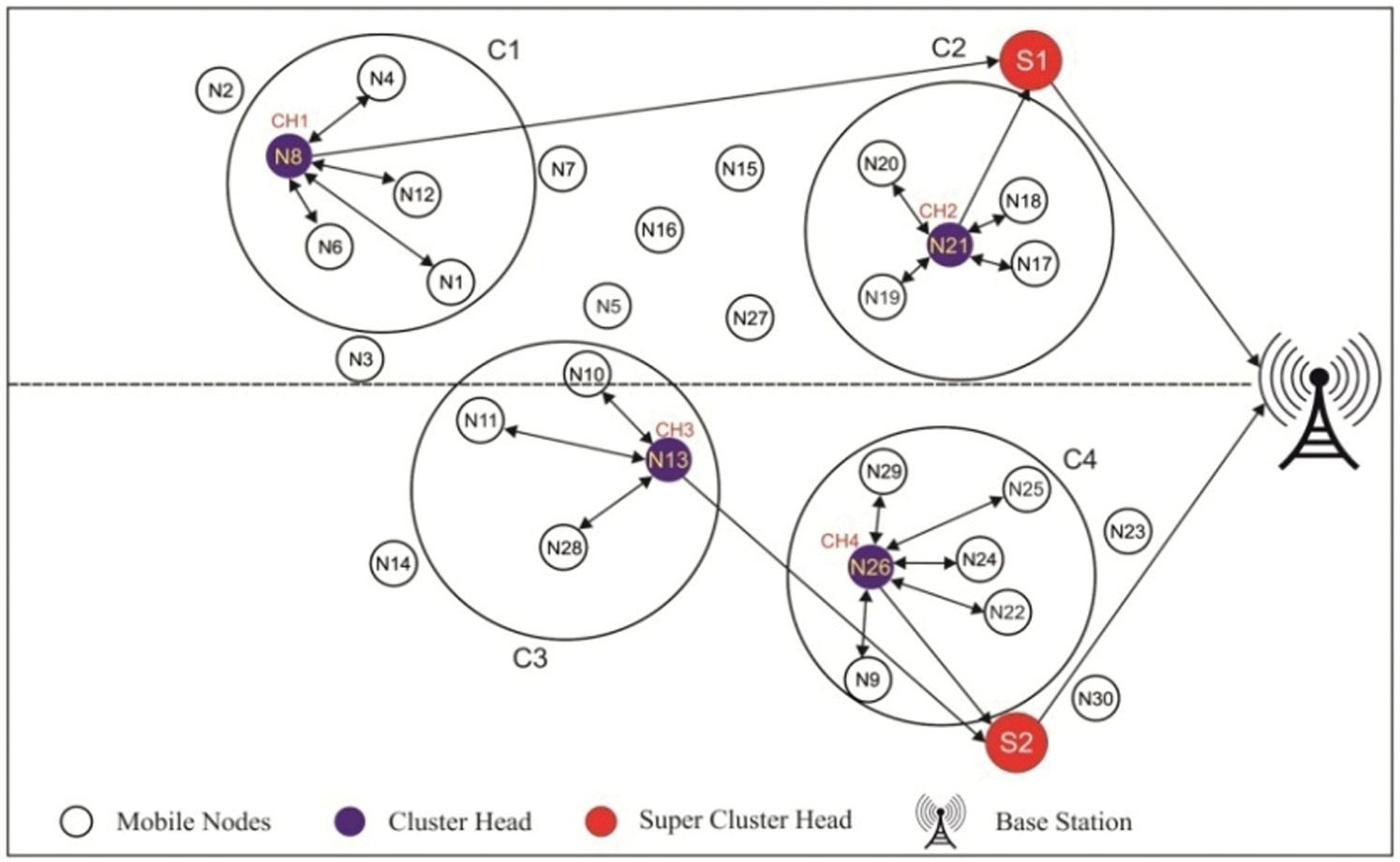
Figure 5: Scenario 3: Cluster construction by DBC algorithm
After some rounds of operation, the sensor nodes move into another cluster and a new network scenario is formed as shown in the Fig. 3. Similar to scenario 1, the nodes in scenario 2 are also clustered into four groups and a CH is selected from every cluster. It can be seen that some of the cluster members move out of the cluster and become normal mobile node. For instance, in cluster 1, the node N4 moves out of the cluster and node 2 joins cluster 1, due to mobility. As shown in the Fig. 5, in scenario 3, it is noted that the CH also gets changed from N30 to N26, where N30 moves out of the cluster. In all the above three scenarios, the present CHs transfer the data to SCH which in turn transfer the data to BS. The process of updating CHs in mobility, by the proposed method, significantly enhances the energy efficiency and network lifetime.
DBC technique divides the network into two grids, whereas two SCHs are placed near the BS. After cluster formation and CH selection, each CH generates a TDMA slot and is transmitted to the cluster members. To avoid data collision and interference, the cluster members transmit the data to CH in their respective slot. The CHs receive the data and aggregate it. The data aggregation process involves the deletion of redundant and unwanted data. The proposed work introduces SCH concept which acts as a data collector point. SCH is a static sensor node with superior power compared to other nodes in terms of computation power and energy level and is located near BS. SCH receives the data from CHs and it only forwards the data to BS. The usage of SCH significantly reduces the energy expenditure of CHs and it minimizes the distance of communication between CHs and BS. In other words, it can be stated that SCH relays the data from CHs to BS via multi-hop communication. The CH accumulates the data from its CMs and then transmits it to BS. The DBC algorithm follows multi-hop transmission for inter-cluster communication. The CHs transmit the accumulated data to BS via intermediate CHs which then reaches the SCH. Similar to CH, the SCH receives, accumulates and transfers data to the BS directly. Since SCH consumes high power compared to normal CHs, it helps in the reduction of communication distance of CHs to BS. In this way, the energy utilization is reduced significantly.




The simulation of the proposed method was performed using MATLAB R2014a in Intel Core i3 CPU@1.70 GHz with 6 GB RAM. For validation, the energy model explained in the previous section was used. For comparison purposes, the authors used few methods such as LEACH [27], TEEN [30], ABC [36] and M-LEACH protocols.
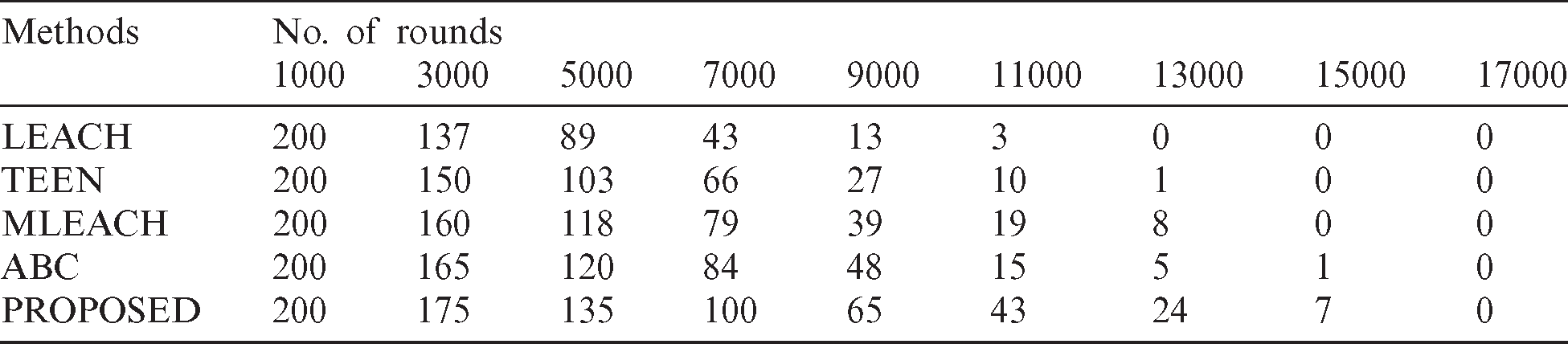
A detailed experimental analysis was made to understand and showcase the benefits of the proposed DBC method. Fig. 6 and Tab. 1 compare the results attained from different clustering approaches in terms of network lifetime and number of alive nodes. From this figure, it is clear that LEACH showed poor performance, where the number of alive nodes got drastically reduced over several rounds. At earlier rounds of 1100, the nodes started to exhaust its energy completely. At round number 4634, 50% of the nodes were dead in the network, i.e., only 100 nodes were alive whereas the other 100 nodes were dead. In round number 6459, only 25% of nodes were alive indicating that 175 nodes were already dead. In line with this, the last node in the network died at the round number, 11241. Next, TEEN attained an increase in the network lifetime compared to LEACH, but not greater than M-LEACH and the proposed DBC technique. Similarly, the M-LEACH managed to produce good results compared to LEACH and TEEN. But, it was unable to outperform the DBC technique and ABC algorithm. Though ABC algorithm seemed to have managed well, the proposed DBC technique outperformed all the compared methods.

Figure 6: Network lifetime analysis
Table 1: Network lifetime analysis
The efficiency of clustering technique can also be investigated using the number of packets successfully delivered at the BS over several rounds. The results are based on the number of packets delivered rather than packets sent in the M-WMSN. Fig. 7 demonstrates the comparative analysis of diverse clustering techniques interms of number of packets received at the BS. The figure clearly indicates the number of packets delivered at the BS in a time interval of 1000 rounds. At round number 1000, least number of packets were delivered using LEACH, whereas the value slightly increased by TEEN. At the same time, M-LEACH performed well and yielded better performance than LEACH and TEEN. However, the proposed DBC algorithm outperformed the other methods used for comparison significantly.

Figure 7: Packets delivered at the BS
From the figure, it is inferred that no packets were received by LEACH, TEEN and M-LEACH after the round numbers, 11000, 13000, and 14000 respectively. This phenomenon could be attributed to the fact that none of the nodes were alive and the network went inoperative at specific rounds. Interestingly, the DBC method allowed data transmission till 16000 rounds. This increased communication led to enhanced lifetime of the M-WMSN. The worst result of the LEACH might be due to uncontrolled CH selection which resulted in reduced communication between the nodes and BS. Additionally, the reactive nature of TEEN resulted in reduced data transmission. Further, it also remained inefficient to observe the overall picture of M-WMSN. M-LEACH selected the CHs arbitrarily and it failed to achieve better data transmission successfully to the BS.
To validate the consistent results of the presented DBC method, energy consumption was analyzed for 1000, 2000 and 3000 rounds. Figs. 8–10 show the results of the analyses. The results portray that the proposed DBC required less amount of energy compared to other methods. The randomized CH selection and single-hop communication of the LEACH protocol had a strong impact on energy consumption. Since TEEN transmitted data on the occurrence of event, the energy consumption automatically reduced resulting in high energy efficiency, compared to LEACH. However, probability-based CH-selected TEEN made it inefficient over M-LEACH and DBC techniques. Though M-LEACH yielded some benefits over LEACH and TEEN methods, it is still inefficient when compared to DBC.

Figure 8: Energy consumption analysis for 1000 rounds

Figure 9: Energy consumption analysis over 2000 rounds

Figure 10: Energy consumption analysis over 3000 rounds
The proposed DBC method was found to be superior to other methods. The reduced energy utilization might be due to the characteristics of DBC algorithm. The DBC algorithm utilized SCH to forward the data from CHs. This, in turn, significantly reduced the energy needs for data transmission among clusters to BS. The productive process of CH selection also paved the way for reduction in energy utilization. Besides, the process of multi-hop communication also reduced energy utilization.
The authors developed a novel clustering technique called DBC algorithm to select CHs using three input variables which include energy level, distance, and node centrality. DBC can be mainly employed for data collection in healthcare environment. Besides, two static data collector points called SCH were placed to gather the data from CHs which then forward the data to the BS directly. The use of SCH supported multi-hop communication to balance the available energy effectively. The proposed method was validated experimentally and the results were verified in terms of network lifetime, energy efficiency and throughput. The proposed DBC technique was found to be energy efficient with maximum lifetime over LEACH, TEEN, and M-LEACH. The DBC method allowed data transmission until 16000 rounds, whereas no packets were received by LEACH, TEEN and M-LEACH after 11000, 13000, and 14000 rounds respectively. These values indicate the superiority of the proposed method in terms of network lifetime. The authors recommend that in future, new researchers can use the proposed DBC algorithm in real-world application scenarios. In addition, the performance of the DBC technique can be further enhanced by hybridizing with bio-inspired algorithms to resolve hot spot problems and maximize network lifetime.
Funding Statement: The author(s) received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1 H. Karl and A. Willig. (2007). Protocols and Architectures for Wireless Sensor Networks. England: John Wiley & Sons. [Google Scholar]
2 I. M. Akyildiz, W. Su, Y. Sankarasubramaniam and E. Cayirci. (2002). “A survey on sensor networks,” IEEE Communications Magazine, vol. 40, no. 8, pp. 102–114. [Google Scholar]
3 V. Ramasamy. (2017). “Mobile wireless sensor networks: An overview,” in Wireless Sensor Networks: Insights and Innovations. London: IntechOpen Limited, pp. 3–19. [Google Scholar]
4 R. Silva, Z. Zinonos, J. S. Silva and V. Vassiliou. (2011). “Mobility in WSNs for critical applications,” in 2011 IEEE Symp. on Computers and Communications, Greece: IEEE, pp. 451–456. [Google Scholar]
5 Q. Mamun. (2012). “A qualitative comparison of different logical topologies for wireless sensor networks,” Sensors, vol. 12, no. 11, pp. 14887–14913. [Google Scholar]
6 M. Elhoseny, X. Yuan, Z. Yu, C. Mao, H. K. El-Minir et al. (2014). “Balancing energy consumption in heterogeneous wireless sensor networks using genetic algorithm,” IEEE Communications Letters, vol. 19, no. 12, pp. 2194–2197. [Google Scholar]
7 M. Elhoseny, K. Elleithy, H. Elminir, X. Yuan and A. Riad. (2015). “Dynamic clustering of heterogeneous wireless sensor networks using a genetic algorithm, towards balancing energy exhaustion,” International Journal of Scientific & Engineering Research, vol. 6, no. 8, pp. 1243–1252.
8 M. Elhoseny, X. Yuan, H. K. El-Minir and A. M. Riad. (2014). “Extending self-organizing network availability using genetic algorithm,” in Fifth Int. Conf. on Computing, Communications and Networking Technologies, Hefei, China, pp. 1–6. [Google Scholar]
9 C. H. Wu and Y. C. Chung. (2007). “Heterogeneous wireless sensor network deployment and topology control based on irregular sensor model,” in Int. Conf. on Grid and Pervasive Computing, Berlin, Heidelberg: Springer-Verlag, pp. 78–88. [Google Scholar]
10 S. Sankar, H. Ranganathan and S. Venkatasubramanian. (2009). “A study on next generations heterogeneous sensor networks,” in 2009 5th IEEE GCC Conf. & Exhibition, Kuwait City, Kuwait, pp. 1–4. [Google Scholar]
11 K. Romer and F. Mattern. (2004). “The design space of wireless sensor networks,” IEEE Wireless Communications, vol. 11, no. 6, pp. 54–61. [Google Scholar]
12 J. Wang, X. Yang, Z. Zhang, B. Li and J. U. Kim. (2014). “A survey about routing protocols with mobile sink for wireless sensor network,” International Journal of Future Generation Communication and Networking, vol. 7, no. 5, pp. 221–228. [Google Scholar]
13 V. C. Gungor, G. P. Hancke and P. G. (2009). “Industrial wireless sensor networks: Challenges, design principles, and technical approaches,” IEEE Transactions on Industrial Electronics, vol. 56, no. 10, pp. 4258–4265. [Google Scholar]
14 N. Srivastava. (2 010). “Challenges of next-generation wireless sensor networks and its impact on society,” Journal of Telecommunications, vol. 1, no. 1, pp. 128–133.
15 A. Rathee, R. Singh and A. Nandini. (2016). “Wireless sensor network-challenges and possibilities,” International Journal of Computer Applications, vol. 140, no. 2, pp. 1–15. [Google Scholar]
16 D. Gupta, A. Khanna, SK. L., K. Shankar, V. Furtado et al. (2019). “Efficient artificial fish swarm based clustering approach on mobility aware energy-efficient for MANET,” Transactions on Emerging Telecommunications Technologies, vol. 30, no. 9, e3524. [Google Scholar]
17 C. Kumar, A. K. Singh, P. Kumar, R. Singh and S. Singh. (2020). “SPIHT-based multiple image watermarking in NSCT domain,” Concurrency and Computation: Practice and Experience, vol. 32, no. 1, e4912.
18 K. Shankar and P. Eswaran. (2016). “An efficient image encryption technique based on optimized key generation in ECC using genetic algorithm,” in Artificial Intelligence and Evolutionary Computations in Engineering Systems, New Delhi: Springer, pp. 705–714.
19 M. Elhoseny, K. Shankar, S. K. Lakshmanaprabu, A. Maseleno and N. Arunkumar. (2018). “Hybrid optimization with cryptography encryption for medical image security in internet of things,” Neural Computing and Applications, vol. 32, no. 15, pp. 1–15.
20 K. Shankar, M. Elhoseny, E. D. Chelvi, S. K. Lakshmanaprabu and W. Wu. (2018). “An efficient optimal key based chaos function for medical image security,” IEEE Access, vol. 6, pp. 77145–77154.
21 R. Irviani and M. Muslihudin. (2018). “Nur algorithm on data encryption and decryption,” International Journal of Engineering & Technology, vol. 7, no. 2.26, pp. 109–118.
22 K. Shankar and S. K. Lakshmanaprabu. (2018). “Optimal key based homomorphic encryption for color image security aid of ant lion optimization algorithm,” International Journal of Engineering & Technology, vol. 7, no. 9, pp. 22–27. [Google Scholar]
23 H. P. Singh and S. Sharma. (2011). “Guard against cooperative black hole attack in mobile ad-hoc network,” International Journal of Engineering Science and Technology (IJEST), vol. 3, no. 7, pp. 5629–5634. [Google Scholar]
24 Y. Gu, L. Zhao, D. Jing and J. Guo. (2012). “A novel routing protocol for mobile nodes in WSN,” in 2012 Int. Conf. on Control Engineering and Communication Technology, Liaoning, China, pp. 624–627. [Google Scholar]
25 S. Bandyopadhyay and E. J. Coyle. (2003). “An energy efficient hierarchical clustering algorithm for wireless sensor networks,” Twenty-Second Annual Joint Conf. of the IEEE Computer and Communications Societies IEEE INFOCOM, Casablanca, Morocco, vol. 3, pp. 1713–1723. [Google Scholar]
26 R. N. Enam, R. Qureshi and S. Misbahuddin. (2014). “A uniform clustering mechanism for wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 10, no. 3, 924012. [Google Scholar]
27 W. B. Heinzelman. (2000). “Application-specific protocol architectures for wireless networks.” Doctoral dissertation, Massachusetts Institute of Technology. [Google Scholar]
28 G. S. Kumar, M. V. Paul, G. Athithan and K. P. Jacob. (2008). “Routing protocol enhancement for handling node mobility in wireless sensor networks,” in TENCON 2008-2008 IEEE Region 10 Conf., Hyderabad, India, pp. 1–6. [Google Scholar]
29 D. S. Kim and Y. J. Chung. (2006). “Self-organization routing protocol supporting mobile nodes for wireless sensor network,” in First Int. Multi-Symp. on Computer and Computational Sciences, Hanzhou, Zhejiang, China, vol. 2, pp. 622–626. [Google Scholar]
30 S. A. Awwad, C. K. Ng, N. K. Noordin and M. F. A. Rasid. (2011). “Cluster based routing protocol for mobile nodes in wireless sensor network,” Wireless Personal Communications, vol. 61, no. 2, pp. 251–281. [Google Scholar]
31 G. S. Sara. (2010). “Energy efficient clustering and routing in mobile wireless sensor network.” arXiv preprint arXiv: 1011. 5326. [Google Scholar]
32 H. Luo, F. Ye, J. Cheng, S. Lu and L. Zhang. (2005). “TTDD: Two-tier data dissemination in large-scale wireless sensor networks,” Wireless Networks, vol. 11, no. 1–2, pp. 161–175. [Google Scholar]
33 J. Luo, J. Panchard, M. Piórkowski, M. Grossglauser and J. P. Hubaux. (2006). “Mobiroute: routing towards a mobile sink for improving lifetime in sensor networks,” in Int. Conf. on Distributed Computing in Sensor Systems, Berlin, Heidelberg: Springer, pp. 480–497. [Google Scholar]
34 O. Mezghani and M. Abdellaoui. (2014). “Improving network lifetime with mobile LEACH protocol for wireless sensors network,” in 2014 15th Int. Conf. on Sciences and Techniques of Automatic Control and Computer Engineering (STApp. 613–619. [Google Scholar]
35 B. Nazir and H. Hasbullah. (2010). “Mobile sink based routing protocol (MSRP) for prolonging network lifetime in clustered wireless sensor network,” in 2010 Int. Conf. on Computer Applications and Industrial Electronics, pp. 624–629. [Google Scholar]
36 Y. Yue, J. Li, H. Fan and Q. Qin. (2016). “Optimization-based artificial bee colony algorithm for data collection in large-scale mobile wireless sensor networks,” Journal of Sensors, vol. 2016, pp. 1–12. [Google Scholar]
37 S. Deng, J. Li and L. Shen. (2011). “Mobility-based clustering protocol for wireless sensor networks with mobile nodes,” IET Wireless Sensor Systems, vol. 1, no. 1, pp. 39–47. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |