DOI:10.32604/cmc.2021.013852

| Computers, Materials & Continua DOI:10.32604/cmc.2021.013852 |  |
| Article |
Robust Attack Detection Approach for IIoT Using Ensemble Classifier
1School of Information Technology and Engineering, Vellore Institute of Technology, Vellore, 632014, India
2Advanced Manufacturing Institute, King Saud University, Riyadh, 11421, Saudi Arabia
3Industrial Engineering Department, College of Engineering, King Saud University, Riyadh, 11421, Saudi Arabia
*Corresponding Author: Mohamed K. Aboudaif. Email: maboudaif@ksu.edu.sa
Received: 23 August 2020; Accepted: 6 October 2020
Abstract: Generally, the risks associated with malicious threats are increasing for the Internet of Things (IoT) and its related applications due to dependency on the Internet and the minimal resource availability of IoT devices. Thus, anomaly-based intrusion detection models for IoT networks are vital. Distinct detection methodologies need to be developed for the Industrial Internet of Things (IIoT) network as threat detection is a significant expectation of stakeholders. Machine learning approaches are considered to be evolving techniques that learn with experience, and such approaches have resulted in superior performance in various applications, such as pattern recognition, outlier analysis, and speech recognition. Traditional techniques and tools are not adequate to secure IIoT networks due to the use of various protocols in industrial systems and restricted possibilities of upgradation. In this paper, the objective is to develop a two-phase anomaly detection model to enhance the reliability of an IIoT network. In the first phase, SVM and Naïve Bayes, are integrated using an ensemble blending technique. K-fold cross-validation is performed while training the data with different training and testing ratios to obtain optimized training and test sets. Ensemble blending uses a random forest technique to predict class labels. An Artificial Neural Network (ANN) classifier that uses the Adam optimizer to achieve better accuracy is also used for prediction. In the second phase, both the ANN and random forest results are fed to the model’s classification unit, and the highest accuracy value is considered the final result. The proposed model is tested on standard IoT attack datasets, such as WUSTL_IIOT-2018, N_BaIoT, and Bot_IoT. The highest accuracy obtained is 99%. A comparative analysis of the proposed model using state-of-the-art ensemble techniques is performed to demonstrate the superiority of the results. The results also demonstrate that the proposed model outperforms traditional techniques and thus improves the reliability of an IIoT network.
Keywords: Blending; ensemble; intrusion detection; Industrial Internet of Things (IIoT)
Abbreviations
| ACO | Ant Colony Optimization |
| ANN | Artificial Neural Network |
| BPN | Back Propagation Network |
| CNN | Convolutional Neural Network |
| GRU | Gated Recurrent Unit |
| LSTM | Long Short Term Memory Networks |
| RNN | Recurrent Neural Network |
| CPS | Cyber Physical Systems |
| DT | Decision Tree |
| FNT | Flexible Neural Tree |
| GA | Genetic Algorithm |
| IoT | Internet of Things |
| IIoT | Industrial Internet of Things |
| KNN | K-Nearest Neighbor |
| KPCA | Kernel Principal Component Analysis |
| NB | Naïve Bayes |
| PCA | Principal Component Analysis |
| RF | Random Forest |
| SA | Simulated Annealing |
| SVM | Support Vector Machine |
Currently, the number of IoT devices and connected devices is estimated to be more than 15 billion, and up to 50 billion connected IoT devices are expected by 2022. Development of huge numbers of IoT devices combined with the pressure to deliver IoT devices to market in a timely and competitive manner has increased attention on privacy and security issues. Advances in the IoT and Cyber Physical System (CPS) domains has stimulated creation of Cyber-Physical Manufacturing Systems (CPMS). With the continuous development of CPMSs, significant security concerns have been raised in relation to the Industrial IoT (IIoT), which is characterized by real-time monitoring, automated systems, smart connections, and collaborative machines [1]. Identifying IIoT threats and developing defense strategies is required because the complete internet could be paralyzed if a single component and/or communication channel in an IIoT-based system is compromised.
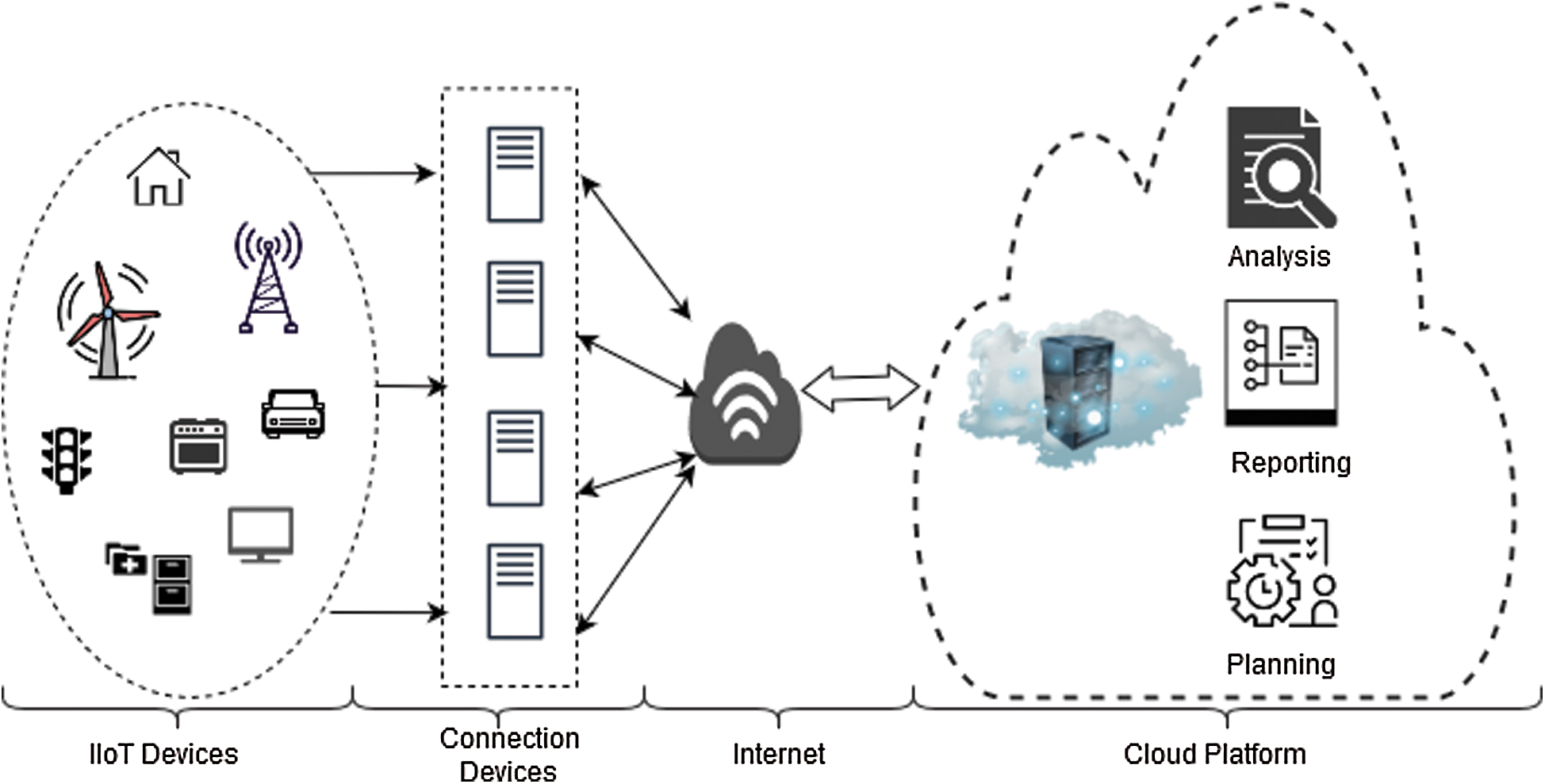
Figure 1: IIoT Architecture
The four-layered architecture of the IIoT is shown in Fig. 1. The first layer is the edge layer, which contains the IIoT devices, and the second layer, the aggregation layer, consists of connected devices. The third layer is the network layer. The fourth layer is the cloud layer, which performs analytics, reporting, and planning based on data captured from the IIoT devices. As shown in Fig. 1 (edge layer), IIoT devices will be distributed in various environments, including remote locations where routine maintenance is not feasible. Furthermore, the control logic on IIoT devices cannot be determined in the destination environment. IIoT devices are vulnerable to various types of attacks, such as DDoS, DoS, tampering, spoofing, privilege escalation, and IoT botnet attacks [2].
Cisco analyzed a survey [3] that identified Trojan as the most common type of malware deployed to access users and an organization’s computers. Security is a significant challenge that has to be addressed sensibly. As shown in Fig. 2, the global cybersecurity market has increased due to increasing threats and attacks, and, by 2023, it is expected that the market will increase exponentially. Despite measures implemented to maintain a secure environment, attacks can occur [4]. Building a network that is immune to all types of attack is not possible. Therefore, to realize a trust-based IoT network, developing ways to preventing or mitigate attacks is very important.
Security solutions use antivirus software and intermediate boxes, such as Intrusion Detection Systems (IDS) and firewalls. A firewall controls inbound and outbound traffic at the network endpoints based on the source and destination addresses. However, firewalls require knowledge of the host and are limited by the amount of state available. IDSs are security monitoring tools. They analyze network traffic and scan the system for malicious activities. In addition, IDSs notify the system administrator when a malicious incident is detected. Misuse, anomaly, and hybrid detection mechanisms are widely used in IDSs. With misuse identification, unknown attacks are detected by knowledge rules. In anomaly detection, attacker behavior is compared to normal behavior based on a hypothesis. Hybrid techniques integrate misuse and anomaly detection mechanisms.
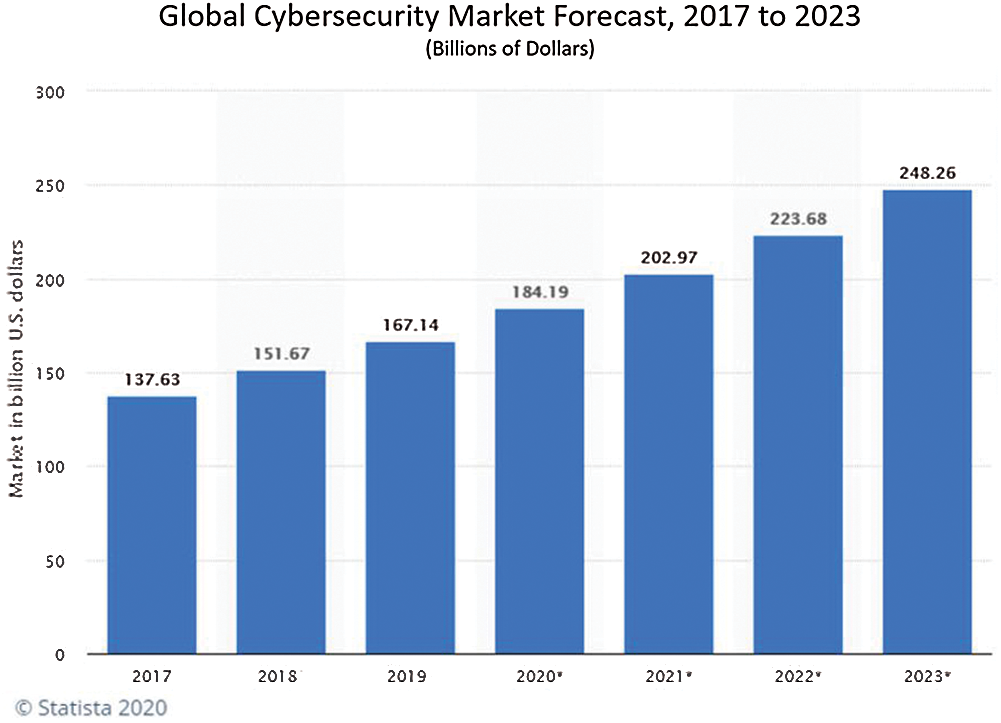
Figure 2: Global cybersecurity market projected to 2023
Various machine learning approaches have been developed for anomaly detection in the IoT. Methods based on machine learning have proven to be effective for identifying anomalous events in the network traffic flow. Machine learning strategies can be classified as supervised and unsupervised. Unsupervised learning does not require labelled data. However, with supervised learning, the algorithm is train on labelled samples; i.e., the process includes a function whereby samples are mapped to class labels. In the testing phase, the class for the unpredicted samples is determined according to the function. Widely used machine learning techniques include Naïve Bayes, SVM, KNN, and decision trees [5]. Convolutional Neural Networks (CNN) [6,7] are also employed in machine learning. There are many ensemble techniques, such as random forest [8], Bending, AdaBoost, and stacking. However, there is no universal approach that can work equally well on all datasets [9].
In this paper, a unified two-phase intrusion detection model is developed using an ensemble machine learning approach called blending that integrates SVM, NB, and DT in the first phase and a random forest classifier is used for prediction. In addition, the results of an Artificial Neural Network (ANN) classifier are integrated with those of the random forest to obtain the best prediction. A contingent analysis is performed by evaluating the integrated model against the WUSTL_IIOT-2018, N_BaIoT and Bot_IoT datasets. In this analysis, accuracy, precision, F-Score, and recall are measured.
The primary contributions of this study are as follows.
• Several existing studies on intrusion detection in the IoT are examined. The investigation focuses on the performance of the algorithms used to develop an attack identification approach.
• Base and ensemble machine learning techniques are integrated to construct a robust approach for anomaly detection.
• Accuracy and other performance metrics on various benchmark IoT datasets are analyzed.
The remainder of this paper is organized as follows. A brief review of related work is presented in Section 2. Section 3 addresses the proposed IIoT attack identification model. The results and performance analysis of the proposed model on various datasets are discussed in Section 4. Conclusions and suggestions for future work are provided in Section 5.
Machine learning approaches are known to provide optimal intrusion detection solutions. Compared to other methods, machine learning approaches provide better results because they can be applied to various types of datasets and can analyze real-time data. In a previous study, a trust model was constructed for machine-to-machine communication using various machine learning approaches, such as logistic regression, NB, DT, KNN and RF [4]. A comparative study has been performed to identify the best approach [5]. That study investigated various techniques, i.e., Naïve Bayes, an SVM, and decision trees. This approach provides accurate information regarding anomalous behaviors and can also analyze the source of the intrusion or the main issue. Typically, these problems are detected based on data patterns, which is time-consuming for human analysts. In this study, large data sets were evaluated, which is labor-intensive and time-consuming with conventional approaches.
Deep learning approaches, such as CNN, CNN-LSTM, CNN-RNN and CNN-GRU, have also been used to identify intrusions [6]. These approaches have proven to be more accurate; however, due to the complex architecture, a high computational cost is incurred during training. To increase accuracy, an ANN model that used a wrapper method for feature selection was constructed [8]. The proposed ANN model was compared to an SVM, and the comparison shows that the proposed model yielded more accurate results. Simulated annealing with an SVM is a hybrid approach that has been applied to network intrusion [10]. This approach proved to be significantly more accurate than an SVM alone.
The limitation of this approach that more false positives are generated compared to other methods, such as BPN. The deployment of machine learning approaches in cybersecurity has been analyzed [11]. In addition, multiple classifier techniques have been studied [12]. In that study, the misuse detection model is combined with anomaly detection. A decision tree was used in the anomaly detection module. This approach proved to be effective as it minimized the number of false positives, and the rate of detection was improved.
Bhattacharya et al. [13] constructed a network intrusion detection model that used an integrated PCA-Firefly-based XGBoost approach. In that study, PCA is applied to reduce dimensionality, and XGBoost, which is an advanced ensemble method, was used to predict the classification. Another study, proposed an intrusion identification model using hybrid PCA-GWO for IoMT [14]. The proposed model resulted in better accuracy and decreased the time complexity by 32% for faster alert generation. Rupa et al. [15] analyzed various classifiers, such as LinearSVC, logistic regression, MultinomialNB, and random forest, and developed a computational system that could classify cyber-crime offences. The results demonstrated that logistic regression outperformed superior all other analyzed classifiers.
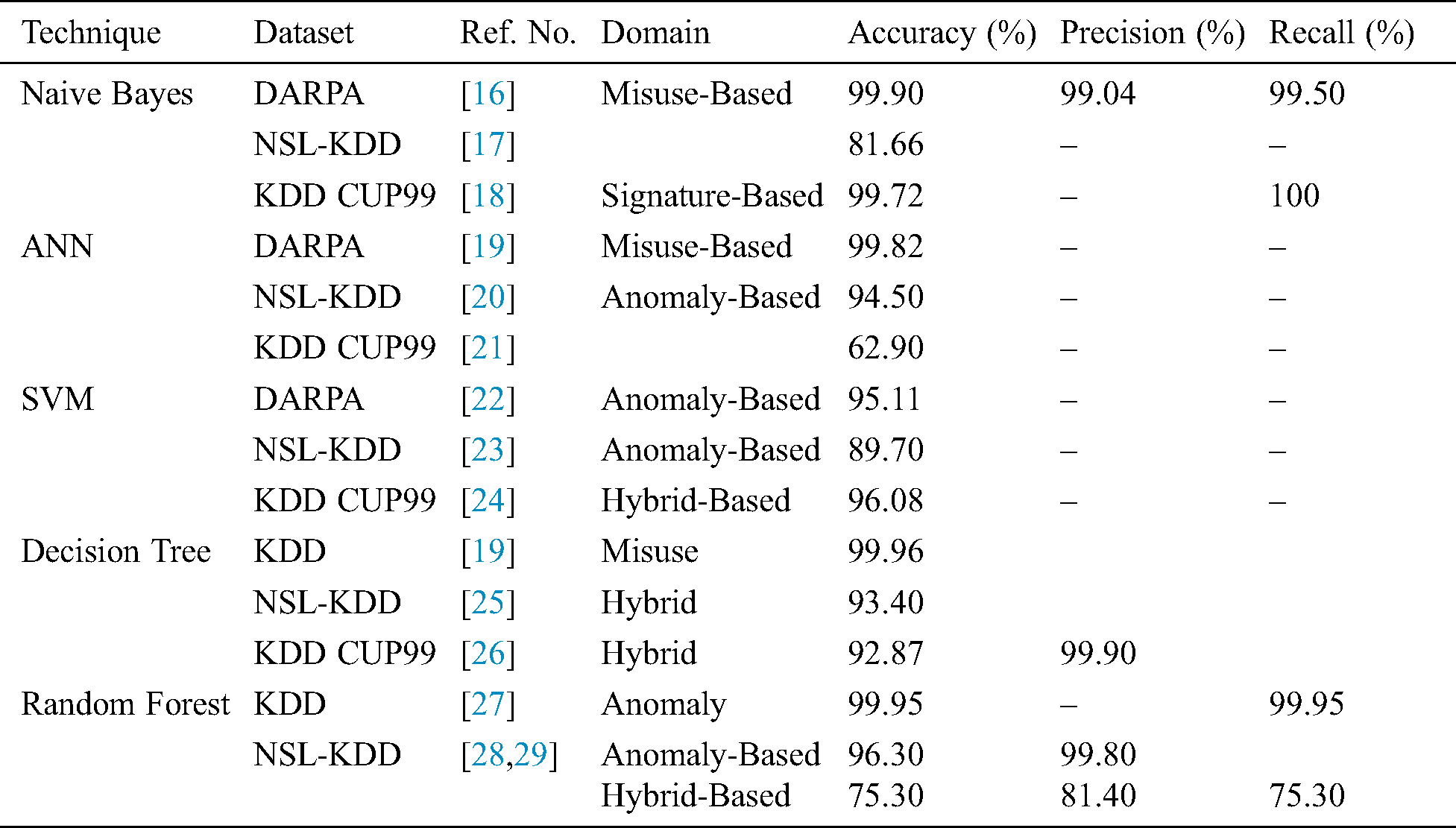
Significant machine learning algorithms deployed on various benchmark datasets are listed in Tab. 1. The DT, NB, ANN, and RF classifiers obtained maximum accuracy of 99% on at least one benchmark dataset. However, maximum accuracy for the SVM was 96% due to its known generalization issue. These results led to the selection of these classifiers for the proposed integrated anomaly detection model for IoT because a blend of these classifiers could result in increased accuracy and reduced error rates.
Table 1: Evaluation of significant machine learning techniques in cybersecurity
The proposed methodology (Fig. 3) is an efficient method that provides a trust-based attack identification model for a network. Initially, the datasets, i.e., WUSTL_IIOT-2018, N_BaIoT and Bot_IoT, are normalized. In the initial stage, the values are fitted between 0 and 1 using label encoding to avoid overfitting. Another level data preprocessing is performed using the Standard Scaler to eliminate null and redundant data. The Standard Scaler arranges the data in a standard normal distribution. In the next step, the data are divided with different cross-validation ratios, e.g., 60:40, 70:30, and 80:20. It was observed that an 80:20 ratio results in better accuracy at the first level of deployment. This model ensures that all observations from the dataset have a fair chance of appearing in the training and test data. A two-level of classification is deployed in the proposed model. In the first level, SVM, Naïve Bayes, and a decision tree are integrated as a blended ensemble, and the output is a new training set that is sent to a random forest classifier. In addition, an ANN classifier is deployed on the data using softmax as the activation function. Here, the Adam optimizer is used to improve accuracy. In the second level, both the ANN and random forest results are sent to the classification unit, and the most accurate result is considered the final predicted test result. The pseudocode of the proposed model is shown in Fig. 4.
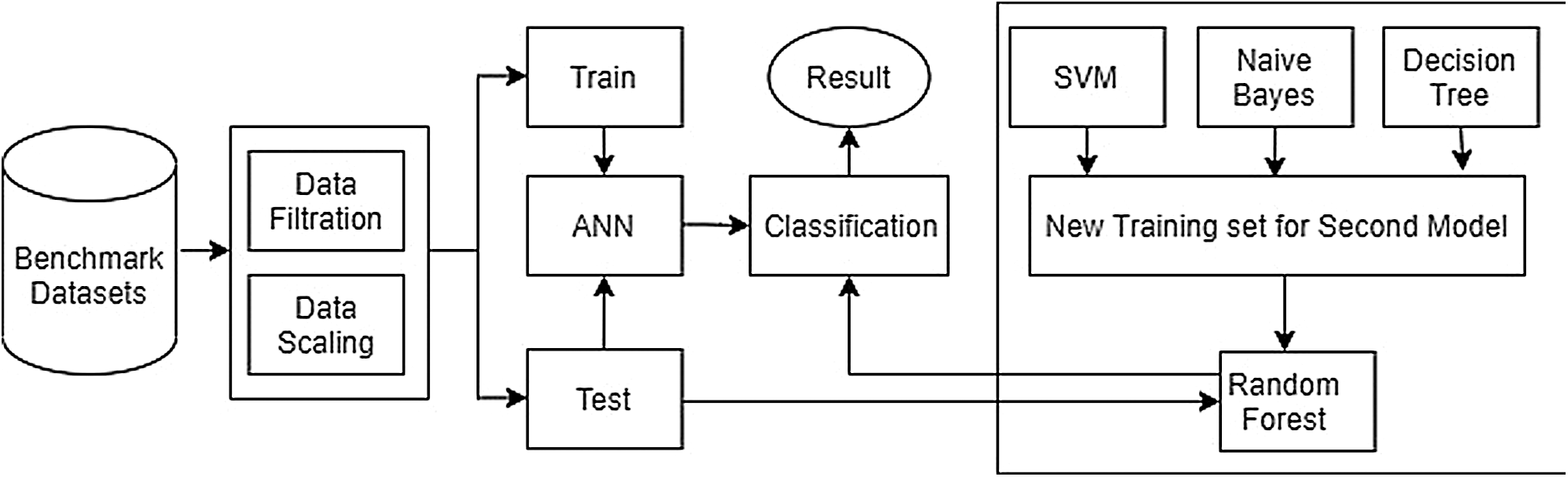
Figure 3: Proposed IIoT attack identification model
The first dataset used is the WUSTL_IIOT_2018 dataset for ICS (SCADA) Cybersecurity [30]. Real-world industrial systems are closely emulated, and cyber attacks are generated and captured. The different attacks generated in the testbed are listed in Tab. 2. The dataset contains 93.93% normal traffic and 6.07% abnormal traffic. Initially, the dataset has 25 features. However, based on an analysis, six features are selected, as shown in Tab. 3. After the data are cleaned to eliminate null and redundant data, a new column is introduced as “Target” wherein normal traffic is represented as “0” and attack traffic is represented as “1”.
The second dataset used for our analysis is the N_BaIoT dataset [31] that comprises data from nine commercial IoT devices infected by the Bashlite and Mirai botnets. The data is classified as malicicious (10 categories) and benign (1 category). Initially, the datasets had more than 100 features. However, after stream aggregation and deploying statistics, 12 features are used for analysis.
The final dataset is the BoT_IoT [32] generated by the Australian Centre for Cyber Security. This dataset contains both anomalous and normal events. There are six attack categories, i.e., Data exfiltration, Service Scan, DDoS, Keylogging, DoS, and OS attacks.
Table 2: Attacks generated in WUSTL_IIOT_2018 dataset
4.2 Pseudocode of the Proposed Model
Table 3: Features selected in WUSTL_IIOT_2018 dataset
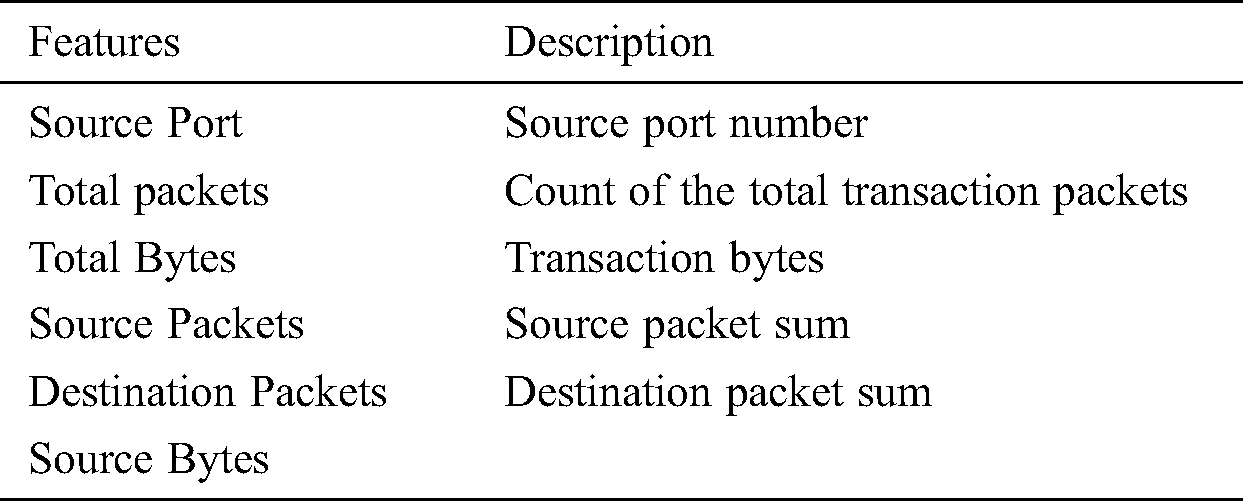
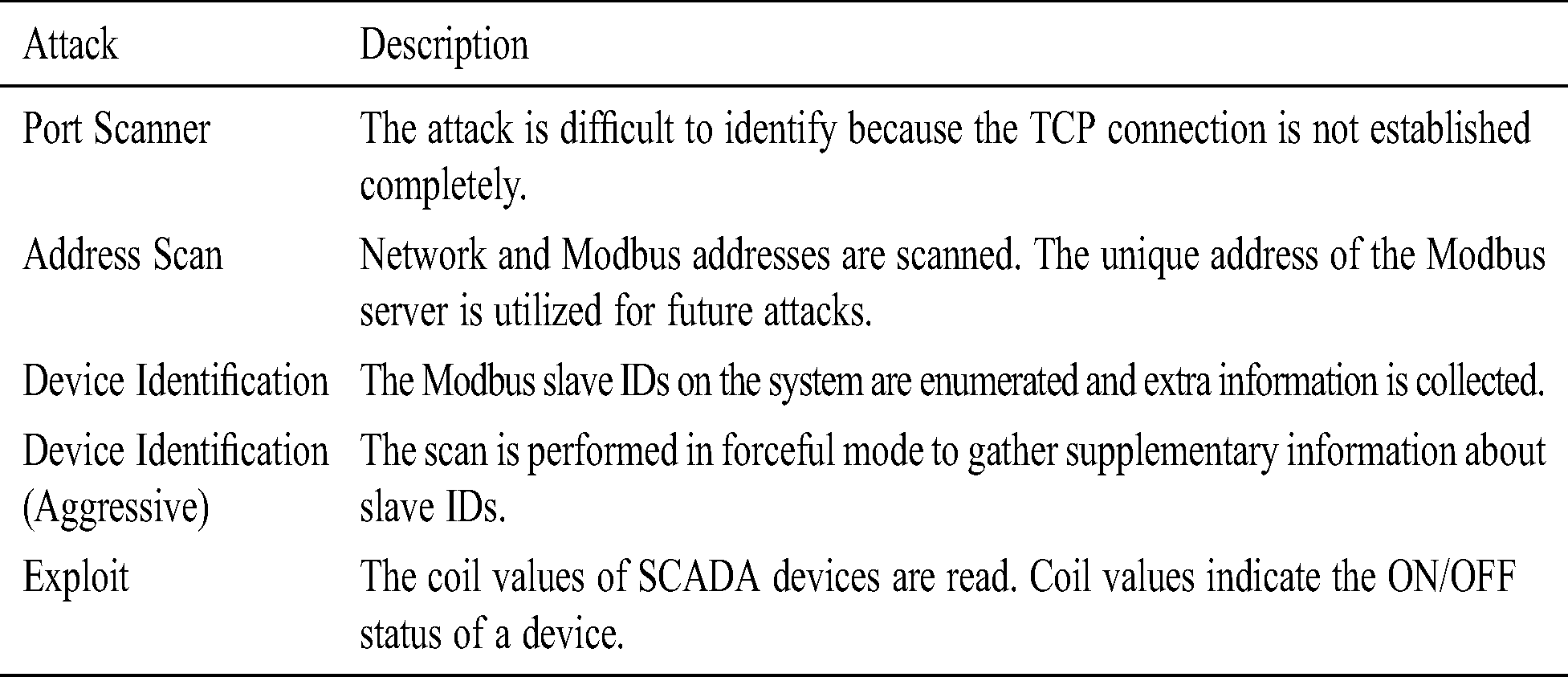
• Accuracy: Accuracy measures the correctness of a result. In this case, the correctness of the model’s predictions are measured. Accuracy can be expressed as follows.
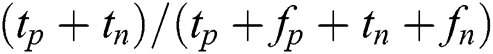
• Precision (P): Precision represents the exactness of a classifier and can be expressed as follows.
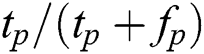
• Recall(R): Recall defines the completeness of a classification model Recall can be expressed as follows.
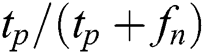
• F1 score: The F1 score measures acccuracy based on precision and recall values. F1 values are calculated as follows.
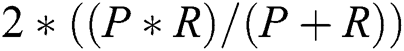
Here, true negatives, true positives, false positives, and false negatives are represented as tn, tp, fp, and fn, respectively.
Performance indicators, such as accuracy, precision, F1 score, and recall are measured to evaluated the proposed model. The various performance metrics obtained using the SVM, NB, and DT classifiers [33,34] on the WUSTL_IIOT_2018 dataset are shown in Fig. 5. Naive Bayes performs poorly with accuracy, precision, recall, and f-score values of 83, 86, 84, and 83, respectively. The SVM and DT classifiers results were similarly; the DT classifier demonstrated maximum accuracy of 96%.

Figure 4: Pseudocode of the Proposed Model
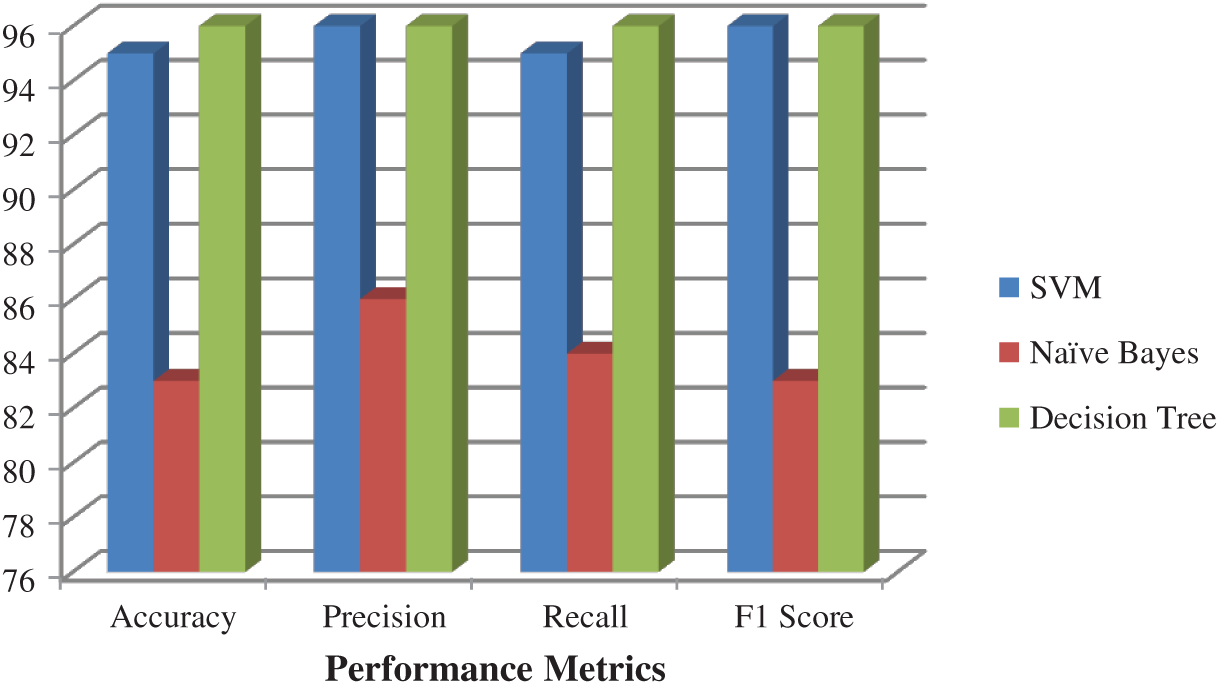
Figure 5: Performance metrics obtained on first level classification on WUSTL_IIOT_2018 dataset
The performance metrics of the proposed model on the WUSTL_IIOT_2018 dataset after the second level of classification are shown in Fig. 6. The classification result is obtained by predicting the better of the random forest and ANN classifier results. Here, maximum accuracy of 99% is obtained. Note that the Adam optimizer is deployed for the ANN as it can rapidly converge and has a high variance. Thus, a two-level classification results in the best prediction.
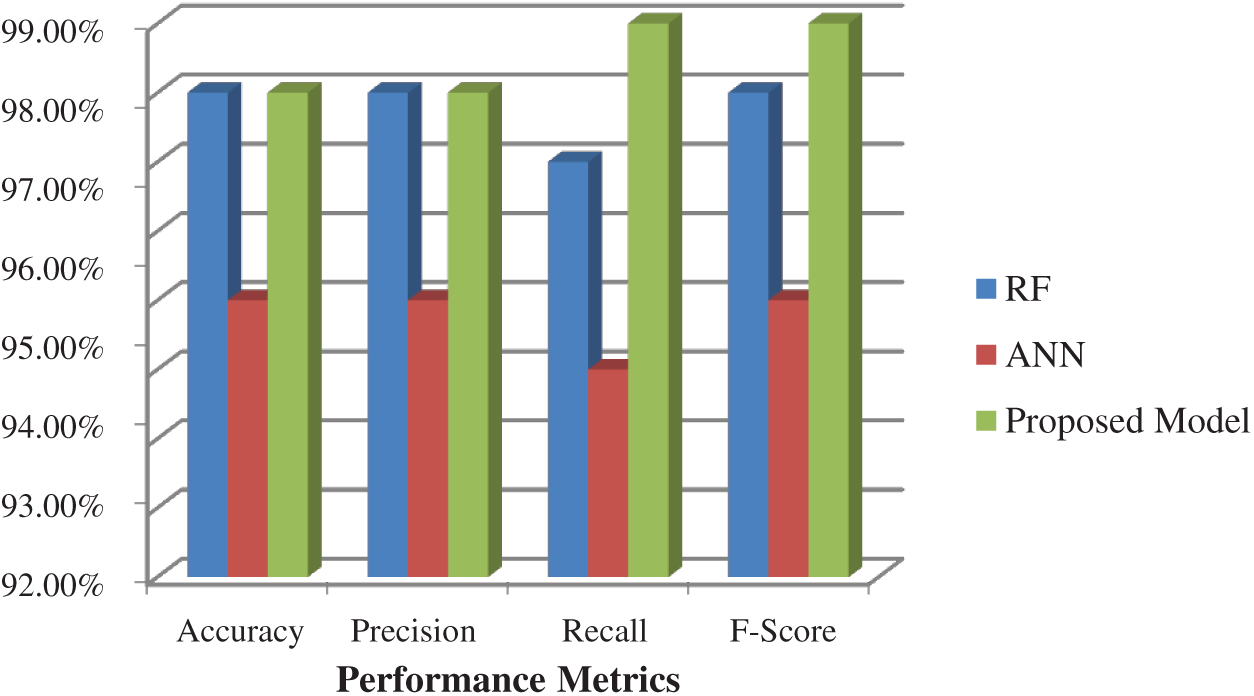
Figure 6: Performance metrics of the integrated model using WUSTL_IIOT_2018 dataset
The various performance metrics obtained using the SVM, NB, and DT classifiers on the N_BaIoT dataset are shown in Fig. 7. NB performs poorly with accuracy, precision, recall. and F-scores of 87, 88, 88, and 87, respectively. The SVM returns 95% accuracy, which is better than the NB classifier. The DT classifier outperforms both the SVM and the NB classifiers with maximum accuracy of 98%. The results of the proposed model after the second level of classification are shown in Fig. 8. The result of the blending is used to train new data and send it to the RF classifier. The ANN and RF predictions are merged to derive a new result with an accuracy of 99%.
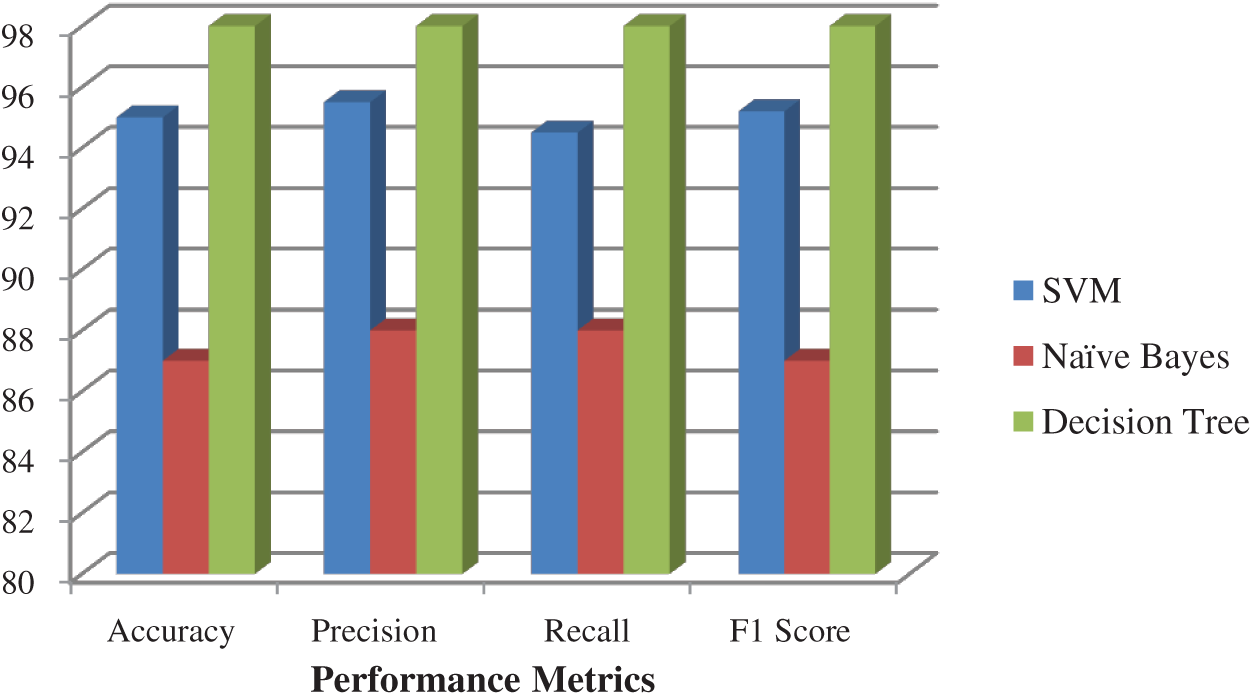
Figure 7: Performance metrics obtained on first level classification on N_BaIoT dataset
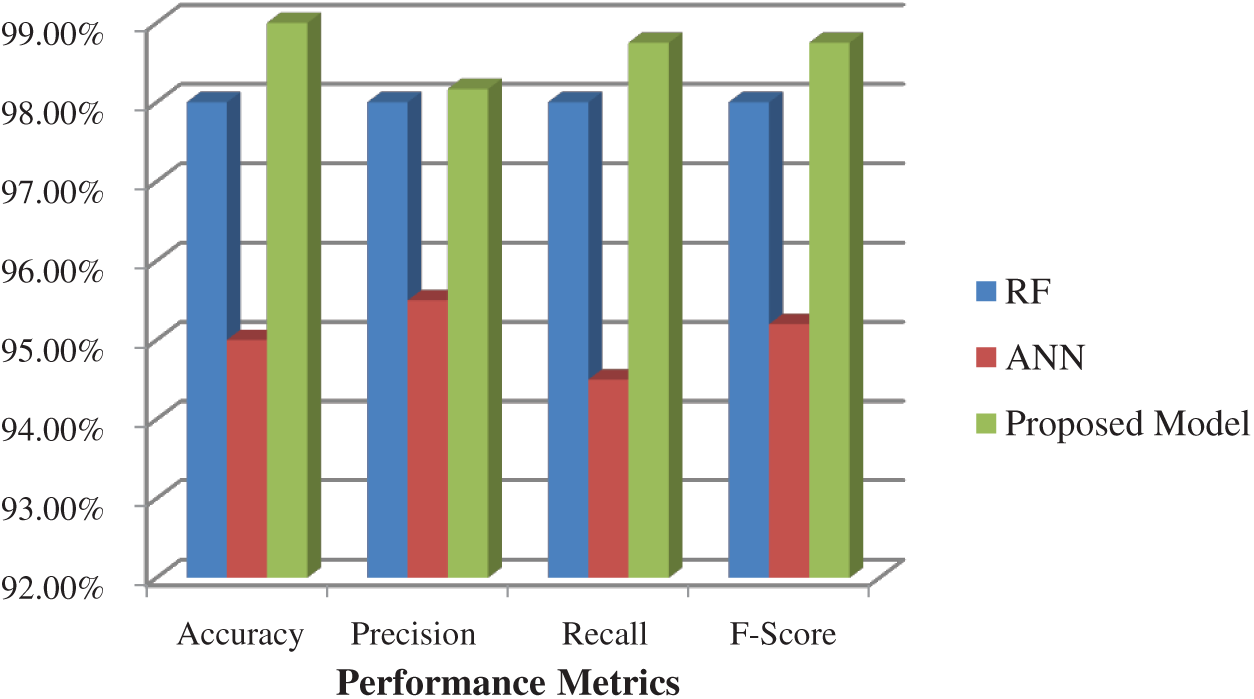
Figure 8: Performance metrics of the integrated model using N_BaIoT dataset
Fig. 9 shows the various performance metrics obtained using the SVM, NB, and DT classifiers on the BoT_IoT dataset. NB performs poorly with accuracy, precision, recall and f-scores of 87, 88, 88, and 87, respectively. The SVM performs better and results in an accuracy of 95%. The DT classifiers returned the best results with maximum accuracy of 98%. The performance of the proposed model after deploying the second level of classification using ANN and RF is shown in Fig. 10. The results of the merged prediction show an increase of 99% accuracy.
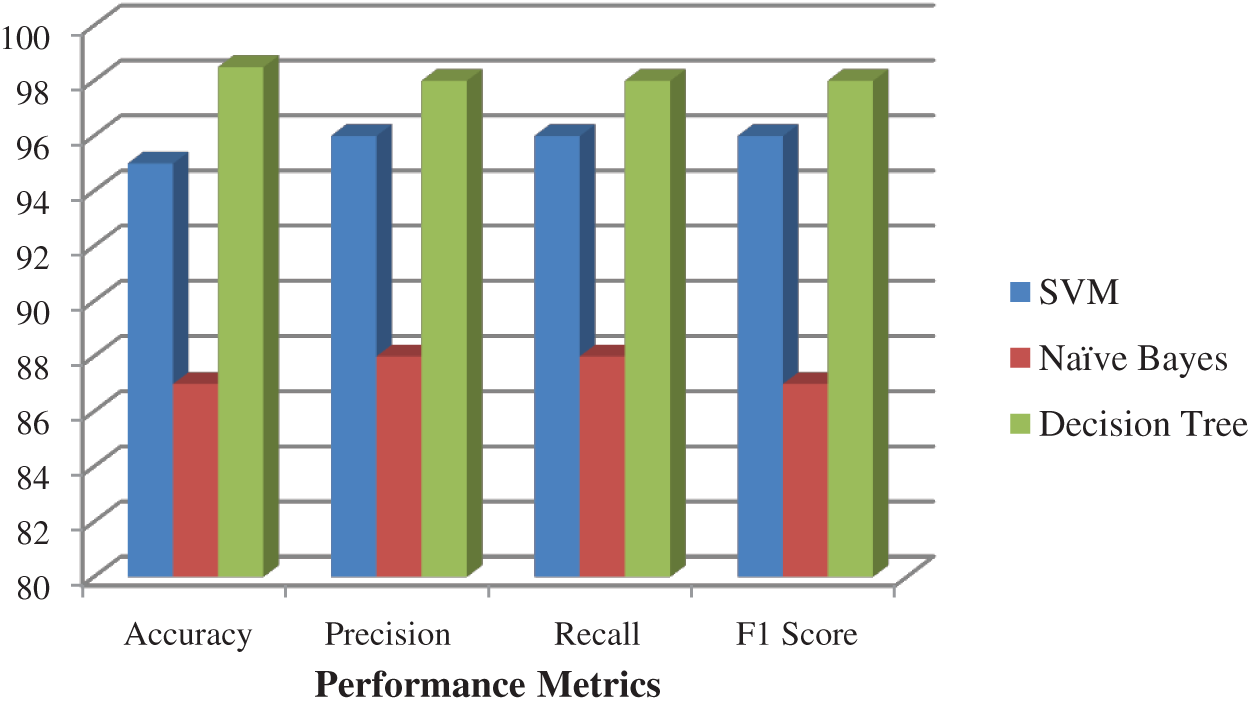
Figure 9: Performance metrics obtained on first level classification on BoT_IoT dataset
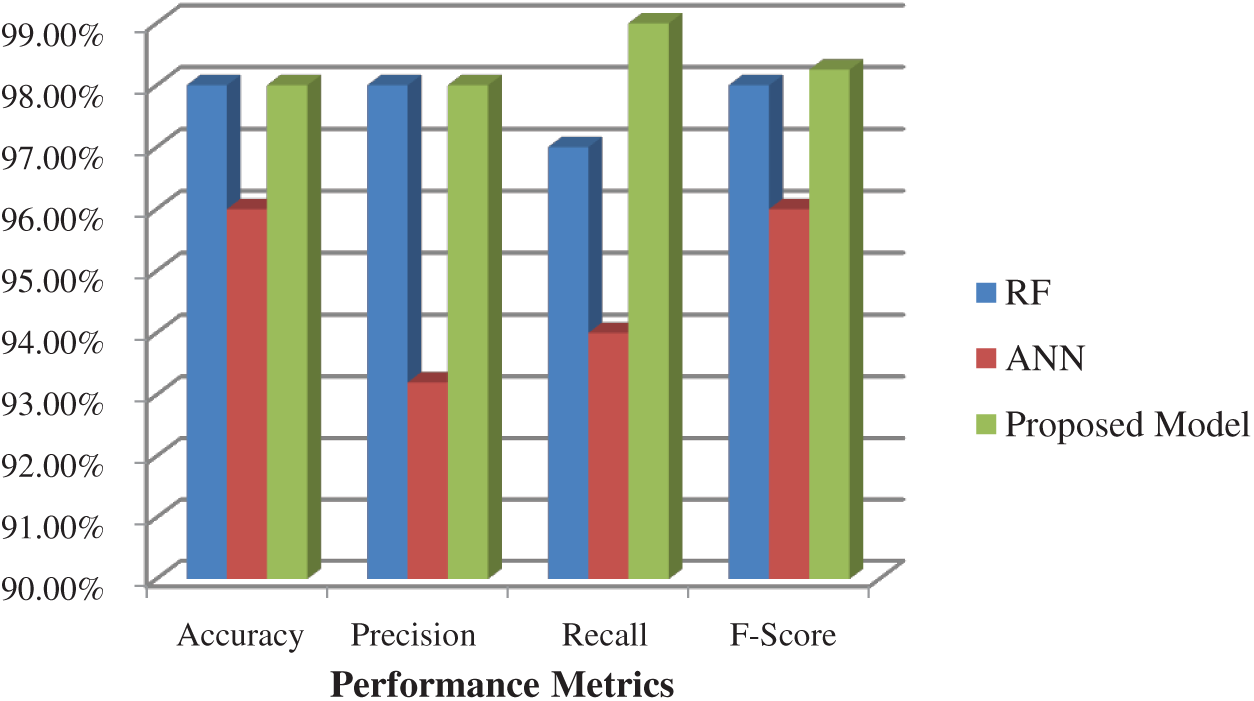
Figure 10: Performance metrics of the integrated model on BoT_IoT dataset
The major findings of the proposed work are as follows.
• Maximum accuracy of 99% is obtained for all three benchmark IoT intrusion detection datasets.
• The Adam optimizer increases the accuracy of the ANN and results in the overall best performance.
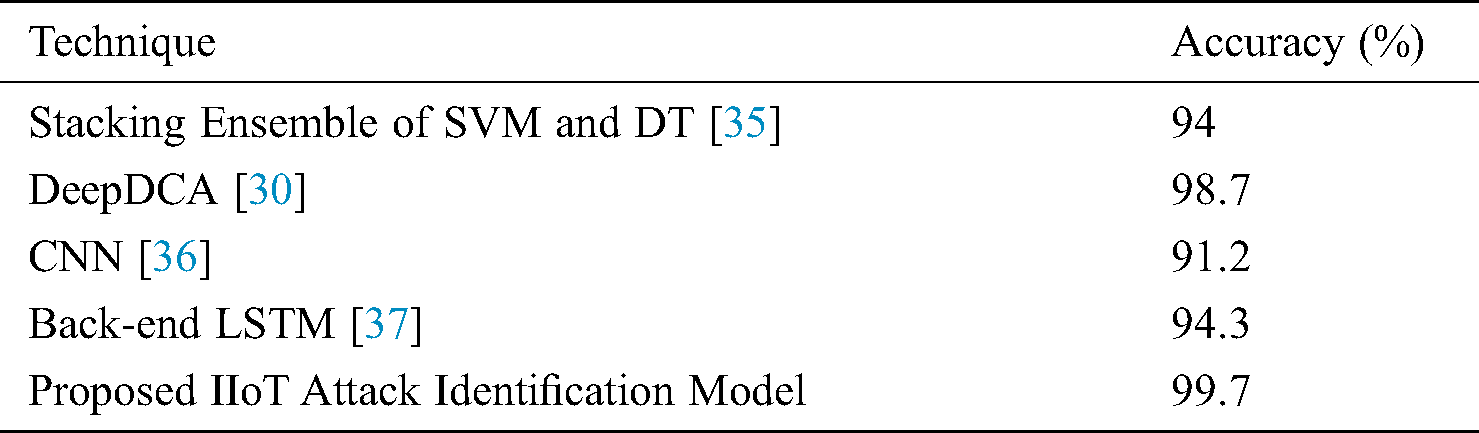
Tab. 4 lists the accuracy of the developed IIoT attack identification model compared to state-of-the-art intrusion detection models using multiple classifiers on the BoT_IoT dataset.
Table 4: Proposed model accuracy comparison with contemporary approaches
Intrusion detection models are powerful mechanisms to secure IIoT systems. We conducted a literature survey of studies that investigated machine learning techniques on standard datasets to identify cyber threats and deployed identified learning approaches in our proposed model. The proposed model integrates three base classifiers, NB, SVM, and KNN by blending, i.e., a stacked ensemble technique. The second level classifier used in the proposed model is RF, and it is one of the best approaches to achieve higher prediction. The ANN and RF classification results are compared, and the best accuracy is considered the final result. The proposed model is evaluated on the WUSTL_IIOT-2018, N_BaIoT, and Bot_IoT datasets. Maximum accuracy of 99% with a marginal change in decimal values is obtained for all three datasets. Precision, recall, and F-Score values were also greater than 98%.
Acknowledgement: The authors extend their appreciation to King Saud University for funding this work through Researchers supporting project number (RSP-2020/164), King Saud University, Riyadh, Saudi Arabia.
Funding Statement: The authors extend their appreciation to King Saud University for funding this work through Researchers Supporting Project number (RSP-2020/164), King Saud University, Riyadh, Saudi Arabia.
Conflict of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. J. Cheng, W. Chen, F. Tao and C. L. Lin. (2018). “Industrial IoT in 5G environment towards smart manufacturing,” Journal of Industrial Information Integration, vol. 10, pp. 10–19. [Google Scholar]
2. Y. Xin, L. Kong, Z. Liu, Y. Chen, Y. Li et al.,. (2018). “Machine learning and deep learning methods for cybersecurity,” IEEE Access, vol. 6, pp. 35365–35381. [Google Scholar]
3. C. Yin, Y. Zhu, J. Fei and X. He. (2017). “A deep learning approach for intrusion detection using recurrent neural networks,” IEEE Access, vol. 5, pp. 21954–21961. [Google Scholar]
4. E. Eziama, L. M. Jaimes, A. James, K. S. Nwizege, A. Balador et al. (2018). , “Machine learning-based recommendation trust model for machine-to-machine communication,” in 2018 IEEE Int. Sym. on Signal Processing and Information Technology, Louisville, Kentucky, USA, pp. 1–6. [Google Scholar]
5. B. Dong and X. Wang. (2018). “Comparison deep learning method to traditional methods using for network intrusion detection,” in 2016 8th IEEE Int. Conf. on Communication Software and Networks, Beijing, China, pp. 581–585. [Google Scholar]
6. R. Vinayakumar, K. P. Soman and P. Poornachandran. (2017). “Applying convolutional neural network for network intrusion detection,” in 2017 Int. Conf. on Advances in Computing, Communications and Informatics, Udupi, India, pp. 1222–1228. [Google Scholar]
7. Y. Meidan, M. Bohadana, Y. Mathov, Y. Mirsky, A. Shabtai et al. (2018). , “N-baiot—network-based detection of IoT botnet attacks using deep autoencoders,” IEEE Pervasive Computing, vol. 17, no. 3, pp. 12–22. [Google Scholar]
8. K. A. Taher, B. M. Y. Jisan and M. M. Rahman. (2019). “Network intrusion detection using supervised machine learning technique with feature selection,” in 2019 Int. Conf. on Robotics, Electrical and Signal Processing Techniques (ICRESTBangladesh, pp. 643–646. [Google Scholar]
9. Y. Hamid, M. Sugumaran and L. Journaux. (2016). “Machine learning techniques for intrusion detection: A comparative analysis,” in Proc. of the Int. Conf. on Informatics and Analytics, India, pp. 1–6. [Google Scholar]
10. M. N. Chowdhury, K. Ferens and M. Ferens. (2016). “Network intrusion detection using machine learning,” in Proc. of the Int. Conf. on Security and Management, Las Vegas, USA, pp. 30. [Google Scholar]
11. J. M. Torres, C. I. Comesana and P. J. García-Nieto. (2019). “Review: Machine learning techniques applied to cybersecurity,” International Journal of Machine Learning and Cybernetics, vol. 10, no. 10, pp. 2823–2836. [Google Scholar]
12. G. Kim, S. Lee and S. Kim. (2014). “A novel hybrid intrusion detection method integrating anomaly detection with misuse detection,” Expert Systems with Applications, vol. 41, no. 4, pp. 1690–1700. [Google Scholar]
13. S. Bhattacharya, R. Kaluri, S. Singh, M. Alazab and U. Tariq. (2020). “A novel PCA-firefly based XGBoost classification model for intrusion detection in networks using GPU,” Electronics, vol. 9, no. 2, pp. 219. [Google Scholar]
14. R. M. S. Priya, P. K. R. Maddikunta, M. Parimala, S. Koppu, T. Reddy et al. (2020). , “An effective feature engineering for DNN using hybrid PCA-GWO for intrusion detection in IoMT architecture,” Computer Communications, (In Press). [Google Scholar]
15. T. R. G. Ch. Rupa, M. H. Abidi and A. Al-Ahmari. (2020). “Computational system to classify cyber-crime offenses using machine learning,” Sustainability, vol. 12, no. 10, 4087. [Google Scholar]
16. M. Panda and M. R. Patra. (2007). “Network intrusion detection using naive bayes,” International Journal of Computer Science and Network Security, vol. 7, no. 12, pp. 258–263. [Google Scholar]
17. N. G. Relan and D. R. Patil. (2015). “Implementation of network intrusion detection system using variant of decision tree algorithm,” in 2015 Int. Conf. on Nascent Technologies in the Engineering Field, Mavi Mumbai, India, pp. 1–5. [Google Scholar]
18. H. Boyes, B. Hallaq, J. Cunningham and T. Watson. (2018). “The Industrial Internet of Things (IIoTAn analysis framework,” Computers in Industry, vol. 101, pp. 1–12. [Google Scholar]
19. P. Mishra, V. Varadharajan, U. Tupakula and E. S. Pilli. (2019). “A detailed investigation and analysis of using machine learning techniques for intrusion detection,” IEEE Communications Surveys & Tutorials, vol. 21, no. 1, pp. 686–728. [Google Scholar]
20. A. U. H. Qureshi, H. Larijani, N. Mtetwa, A. Javed and J. Ahmad. (2019). “RNN-ABC: A new swarm optimization based technique for anomaly detection,” Computers, vol. 8, no. 3, pp. 59. [Google Scholar]
21. M. Sheikhan, Z. Jadidi and A. Farrokhi. (2012). “Intrusion detection using reduced-size RNN based on feature grouping,” Neural Computing and Applications, vol. 21, no. 6, pp. 1185–1190. [Google Scholar]
22. R. T. Kokila, S. T. Selvi and K. Govindarajan. (2014). “DDoS detection and analysis in SDN-based environment using support vector machine classifier,” in 2014 6th Int. Conf. on Advanced Computing, Chennai, India, pp. 205–210. [Google Scholar]
23. J. Lee, J. Kim, I. Kim and K. Han. (2019). “Cyber threat detection based on Artificial Neural Networks using event profiles,” IEEE Access, vol. 7, pp. 165607–165626. [Google Scholar]
24. B. W. Masduki, K. Ramli, F. A. Saputra and D. Sugiarto. (2015). “Study on implementation of machine learning methods combination for improving attacks detection accuracy on Intrusion Detection System (IDS),” in 2015 Int. Conf. on Quality in Research, USA, pp. 56–64. [Google Scholar]
25. A. Ahmim, L. Maglaras, M. A. Ferrag, M. Derdour and H. Janicke. (2019). “A novel hierarchical intrusion detection system based on decision tree and rules-based models,” in 2019 15th Int. Conf. on Distributed Computing in Sensor Systems, Greece, pp. 228–233. [Google Scholar]
26. A. J. Malik and F. A. Khan. (2018). “A hybrid technique using binary particle swarm optimization and decision tree pruning for network intrusion detection,” Cluster Computing, vol. 21, no. 1, pp. 667–680. [Google Scholar]
27. Y. Gao, H. Wu, B. Song, Y. Jin, X. Luo et al. (2019). , “A distributed network intrusion detection system for distributed denial of service attacks in vehicular ad hoc network,” IEEE Access, vol. 7, pp. 154560–154571. [Google Scholar]
28. Y. Zhou, G. Cheng, S. Jiang and M. Dai. (2019). “An efficient intrusion detection system based on feature selection and ensemble classifier,” Journal of Latex Class Files, vol. 14, no. 8, pp. 1–8. [Google Scholar]
29. R. Vinayakumar, M. Alazab, K. P. Soman, P. Poornachandran, A. Al-Nemrat et al. (2019). , “Deep learning approach for intelligent intrusion detection system,” IEEE Access, vol. 7, pp. 41525–41550. [Google Scholar]
30. S. Aldhaheri, D. Alghazzawi, L. Cheng, B. Alzahrani and A. Al-Barakati. (2020). “DeepDCA: Novel network-based detection of IoT attacks using artificial immune system,” Applied Sciences, vol. 10, no. 6, 1909. [Google Scholar]
31. A. M. Chandrasekhar and K. Raghuveer. (2013). “Intrusion detection technique by using k-means, fuzzy neural network and SVM classifiers,” in 2013 Int. Conf. on Computer Communication and Informatics, India, pp. 1–7. [Google Scholar]
32. N. Koroniotis, N. Moustafa, E. Sitnikova and B. Turnbull. (2019). “Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-IoT dataset,” Future Generation Computer Systems, vol. 100, pp. 779–796. [Google Scholar]
33. A. Azab, M. Alazab and M. Aiash. (2016). “Machine learning based botnet identification traffic,” in 2016 IEEE Trustcom/BigDataSE/ISPA. Tianjin, China, 1788–1794. [Google Scholar]
34. A. Azab, R. Layton, M. Alazab and J. Oliver. (2014). “Mining malware to detect variants,” in 2014 5th Cybercrime and Trustworthy Computing Conf., Auckland, New Zealand, pp. 44–53. [Google Scholar]
35. A. Khraisat, I. Gondal, P. Vamplew, J. Kamruzzaman and A. Alazab. (2019). “A novel ensemble of hybrid intrusion detection system for detecting Internet of Things attacks,” Electronics, vol. 8, no. 11, 1210. [Google Scholar]
36. B. Susilo and R. F. Sari. (2020). “Intrusion detection in IoT networks using deep learning algorithm,” Information, vol. 11, no. 5, pp. 279. [Google Scholar]
37. G. D. L. T. Parra, P. Rad, K. K. R. Choo and N. Beebe. (2020). “Detecting internet of things attacks using distributed deep learning,” Journal of Network and Computer Applications, vol. 10, no. 4, pp. 1346–1352. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |