DOI:10.32604/cmc.2021.014371

| Computers, Materials & Continua DOI:10.32604/cmc.2021.014371 |  |
| Article |
Research on Electronic Document Management System Based on Cloud Computing
1Nanjing University of Information Science & Technology, Nanjing, 210044, China
2Research Institute of State Grid Hunan Electric Power Company Limited, Changsha, 410007, China
3Nanjing University, Nanjing, 210093, China
4Waterford Institute of Technology, Waterford City, X91 K0EK, Ireland
*Corresponding Author: Jin Shi. Email: shijin@nju.edu.cn
Received: 16 September 2020; Accepted: 08 October 2020
Abstract: With the development of information technology, cloud computing technology has brought many conveniences to all aspects of work and life. With the continuous promotion, popularization and vigorous development of e-government and e-commerce, the number of documents in electronic form is getting larger and larger. Electronic document is an indispensable main tool and real record of e-government and business activities. How to scientifically and effectively manage electronic documents? This is an important issue faced by governments and enterprises in improving management efficiency, protecting state secrets or business secrets, and reducing management costs. This paper discusses the application of cloud computing technology in the construction of electronic file management system, proposes an architecture of electronic file management system based on cloud computing, and makes a more detailed discussion on key technologies and implementation. The electronic file management system is built on the cloud architecture to enable users to upload, download, share, set security roles, audit, and retrieve files based on multiple modes. An electronic file management system based on cloud computing can make full use of cloud storage, cloud security, and cloud computing technologies to achieve unified, reliable, and secure management of electronic files.
Keywords: Cloud computing technology; electronic file management system; cloud security
With the continuous promotion, popularization and vigorous development of e-government and e-commerce in China, the number of documents in electronic form is increasing. Electronic documents are the indispensable main tools and real records of e-government and business activities. To realize the scientific management of electronic documents and avoid the huge losses caused by improper management, strengthening the theoretical research and practice of electronic document management is particularly urgent and important.
The electronic document management system is built on the cloud architecture, making full use of cloud storage, cloud security, and cloud computing technologies to achieve unified, reliable, and secure management of electronic files. Through the development of an electronic file management system based on cloud computing, users can perform file uploading, downloading, sharing, security role setting, auditing, and file retrieval based on multiple modes. Based on this, this paper proposes an electronic document management system architecture based on cloud computing, discusses the corresponding key technologies, and analyzes the advantages of cloud-based electronic file systems.
2 Cloud Computing Technology and Electronic File Management System Overview
At present, the academic circles have different opinions on the definition of cloud computing, and each has its own merits. According to the definition of NIST of the National Institute of Standards and Technology: Cloud computing is a kind of rapid provision and release, ubiquitous, convenient, on-demand distribution with minimal management capabilities or interaction with service providers. Access patterns to configurable computing resource shared pools such as networks, servers, storage, applications, and services [1]. At the moment, cloud computing has been widely used [2,3].
In his doctoral thesis, Feng Huiling pointed out that electronic records (Electronic Records/Documents) are the product of the development of computer technology, and have three characteristics: computer generated and read, digital information recorded, and “file requirements” [4]. With the continuous development of electronic documents, the number of documents is increasing, and the content of documents is more and more extensive. In order to realize the scientific and effective management of electronic documents, electronic document management systems have emerged. Establishing an inclusive management system, receiving and storing electronic documents, and ensuring the authenticity, reliability, integrity and availability of electronic documents is an important part of management [5,6]. Cloud computing is a new direction in the development of information and communication technology, which is bound to have an unprecedented impact on the development of electronic document management [7]. Liu explained all the typical styles of document security management products [8]. Juris proposed NoSQL Document-oriented database technology and its implementation in Enterprise Content Management area [9]. Hsu implemented a Ubiquitous Location-based Service System (ULSS) who solved the problem that cloud computing to inefficient development and a low potential reuse [10]. All of these make it possible to manage electronic documents in cloud computing architecture.
The advantages of cloud computing for electronic file management are: unified management of electronic files, cloud storage of electronic files, resolution of electronic file transfer and exchange, and implementation of electronic file integration services [11]. Brent Gatewood pointed out that the research focus of electronic files in the era of cloud computing should focus on how to apply file management rules to cloud computing information storage solutions [12]. According to Tshepho, Lungile and Olefhile, search engines are the guarantee of storage space, and unlimited space and semantic web search bring great opportunities for future digital file and file management [13–16].
3 Cloud-Based Electronic File Management System Architecture
3.1 Technical Architecture Design in Cloud Computing Platform
Cloud computing includes three service models, namely software as a service, platform as a service and infrastructure as a service. Platform as a Service and Software as a Service can provide services to platform users directly through SOA, or indirectly to end users as a support platform for software as a service model.
The cloud-based services for electronic file management are defined at the infrastructure-as-a-service layer, and the physical environment includes the data center physical environment and the network environment. Switches, routers, and load-balanced network infrastructure devices are set up in the network cloud. In the storage pool, you can choose three mainstream storage solutions: SAN, NAS, and distributed storage. In the computing pool, you can choose three main virtual server devices: PC server, blade server and minicomputer. In the infrastructure-as-a-service platform, it includes interactive functions such as user interfaces, automated services, resource scheduling, virtual computing, operations management, virtual storage, process management, and virtual networks for virtualized applications.
Dedicated platforms and tools for supporting business applications are defined at the platform as a service layer. It includes relational database, middleware, digital signature, layout curing, data encapsulation, data management, directory services, etc., but also includes a variety of platform-based application support engines, such as business collaboration processes, data capture, specification document generation, information sharing, Search, etc. The various application databases supported by the electronic file data management are also set up at the platform as a service layer, including electronic file databases, metadata databases, long-term preservation databases, thematic databases, and search databases.
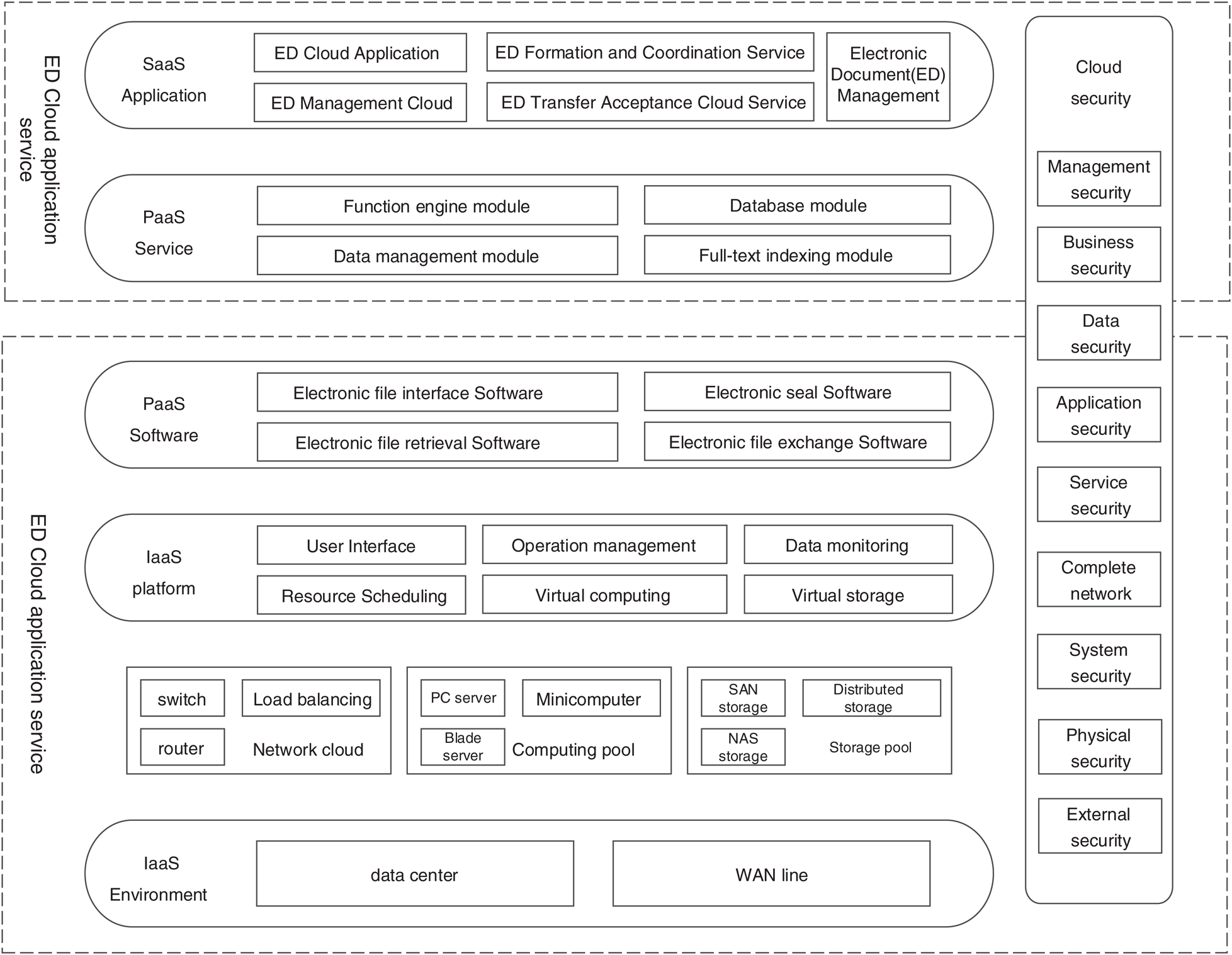
Figure 1: Cloud platform electronic file management technology architecture
In the software-as-a-service layer, various applications for electronic document management are provided, including an electronic document formation processing system, an electronic document management system, an electronic document handover reception, and a long-term storage system. A key issue in cloud computing systems is security, so in a cloud-based electronic file management system, a secure cloud is built. The security cloud should conduct comprehensive security services from different levels, including management, services, data, applications, services, networks, systems, physics and external security management, as shown in Fig. 1.
3.2 Electronic Document Management Application Architecture Design
Use the SOA architecture method to build an electronic file management related system, divide the application function into fine-grained, stateless components, package the components into services, and spread different instances of the same service to multiple instances to run, thereby improving the overall service. Availability.
The electronic file management application architecture design includes a presentation layer, a business application layer, a service plug-in support layer, an infrastructure layer, and a standard support layer. The presentation layer is the business system involved in the application, including the document receiving and dispatching system, the document circulation system, the document retrieval system, the unified authentication, the single sign-on and other business systems; the business application layer is the platform supporting various business applications of the project. Software, including file capture, classification scheme, authentication processing, file retrieval, data storage, data management, rights management, log management, system users, statistical reports, interface management, system management, etc.; service plug-in layer is a variety of tools Software products are mainly software support tools for securing system security for application systems. Including electronic official seal, identity authentication, layout curing, digital signature, data encapsulation, spreadsheet, copyright protection, privilege role, tool support; infrastructure layer includes cloud computing IAAS equipment and IAAS services; standard bearer layer lists the needed Industry standard specification, see Fig. 2 below.
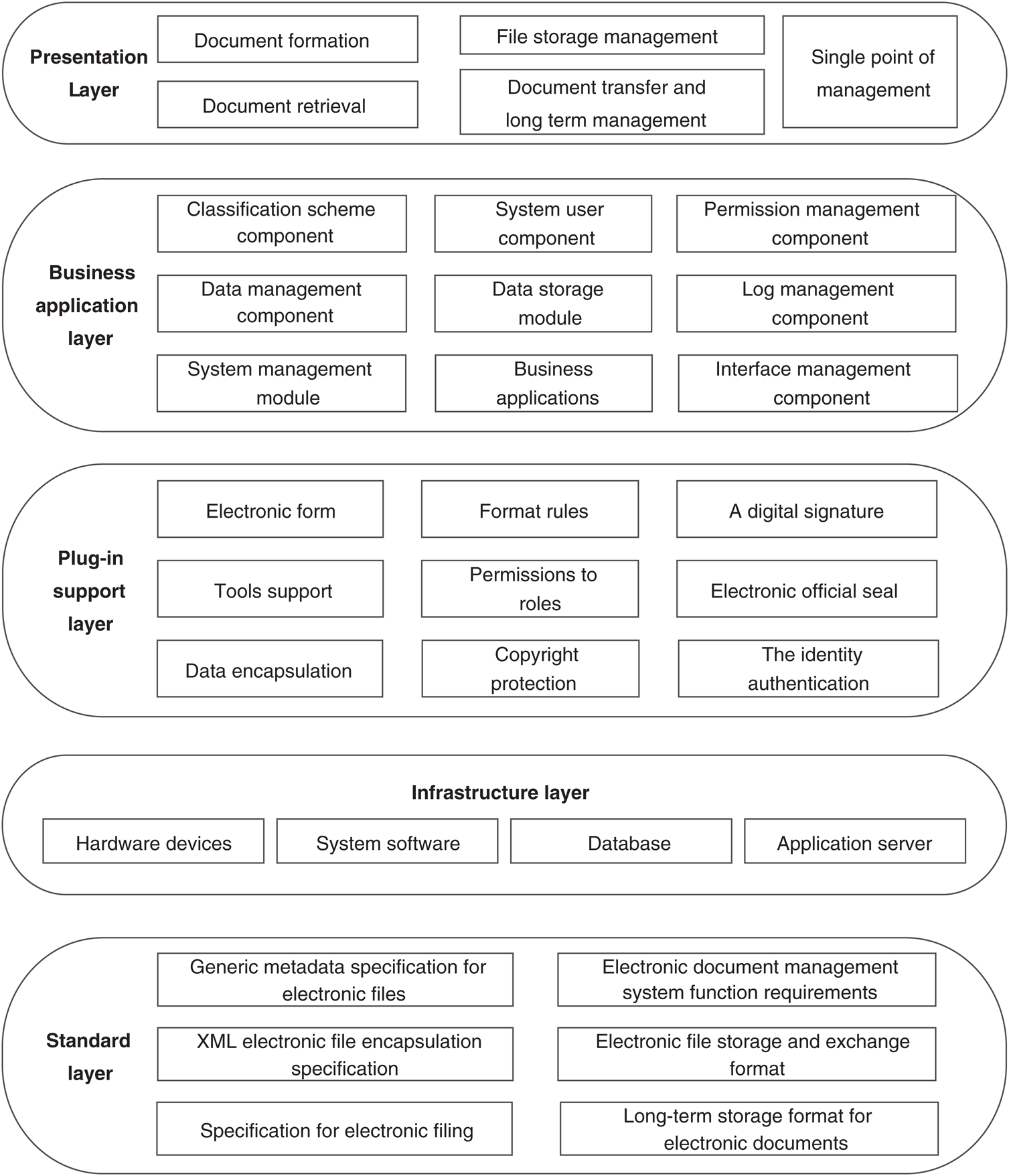
Figure 2: Electronic document management application architecture
3.3 Cloud-Based Electronic File Management System Deployment
Fig. 3 shows the overall deployment of the system. The system is composed of multiple electronic file management subsystems. Each subsystem realizes the shared connection by means of the cloud platform network. The upper system and the lower system can communicate in real time through the network, realizing the logical concentration and physical distribution of electronic file management, and improving the electronic Document management efficiency, see Fig. 3 below.
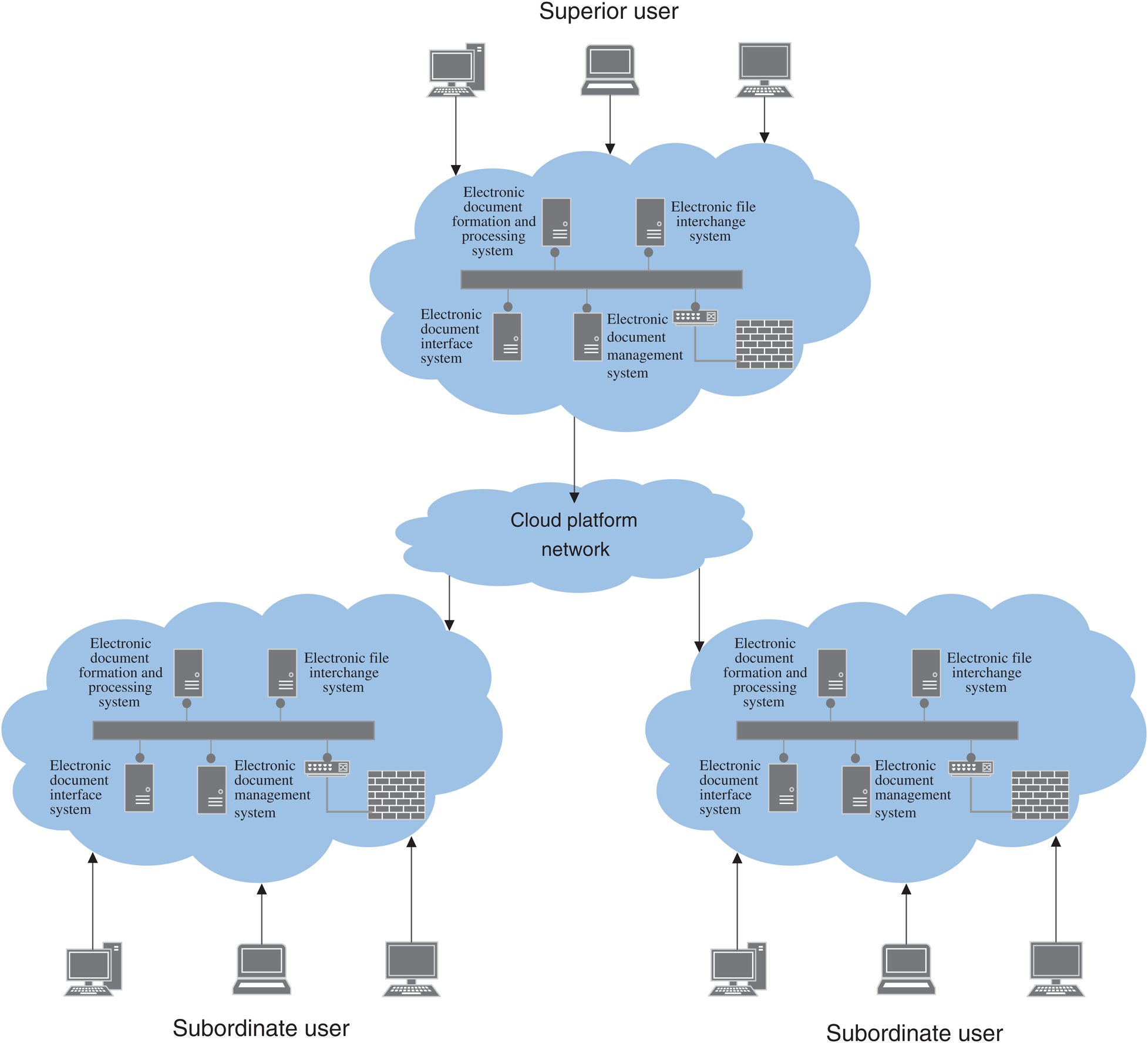
Figure 3: Cloud-based electronic file management system deployment
3.4 Key Technologies of Electronic Document Management System
3.4.1 Data Processing and Storage Services
The most important module in electronic management is the data processing and storage of electronic files. The electronic files have the characteristics of large amount of data and small files (less than 64M). Electronic file data consists of entity data and metadata. Therefore, it is necessary to focus on solving the electronic document entity data as the planning goal, and describe the relational data represented by metadata as the starting point in the database construction scheme.
In the data storage construction, the whole cloud storage is mainly used, and an electronic file library and an electronic file temporary library are separately established, and the stable electronic files and the electronic files to be processed are respectively stored. Providing a secure and reliable data storage center in the cloud computing mode, the data management platform performs unified resource allocation on all data storage resources, load balancing, deploying software, and security management of the data therein. At the same time, in terms of data sharing, policy management is performed according to different security rights, and data security is guaranteed from the network level. When the data is stored in the terminal, it is marked with the corresponding application system category and security level. When passing through the cloud network, the security level of the data is checked by the network layer, and if the high security level data is sent to the low security level. In the area, the discard operation is performed according to the security policy and alarm processing is performed to ensure data security at the circulation level.
Based on the importance and criticality of electronic documents, backup management of electronic files is very important. The cloud computing system itself has a strong backup mechanism. For electronic file service code and electronic file metadata, a full backup is performed each time a service is updated or a new service is installed. For electronic document libraries, daily data updates are large, and full backups are scheduled every other month or week. On this basis, incremental backups are made every other short interval. It is also an essential part of managing the media that has already been backed up.
3.4.3 Operation and Maintenance of the System
In the implementation process of the system, it is necessary to prevent data loss, damage, tampering and leakage to the greatest extent, improve the safety, reliability and stability of the system operation, and ensure the safe operation of the system. It is necessary to monitor and manage the system, timely grasp the current status and configuration information of the network information system resources, reflect the availability and health status of the information system resources, and create a controllable IT environment to ensure various business application systems of the user information system. It can operate reliably, efficiently, continuously and safely.
3.5 Cloud Computing Security Service System
The cloud computing security service system consists of a series of cloud security services and is an important technical means to achieve system security goals. According to their different levels, cloud security services can be further divided into three levels: Secure cloud infrastructure services, cloud security infrastructure services, and cloud security application services.
3.5.1 Secure Cloud Infrastructure Services
Secure cloud infrastructure services provide secure data storage, computing and other services for upper-layer cloud applications, and are the cornerstone of the entire cloud computing system security. The security here includes two aspects: On the one hand, the cloud platform should analyze the security problems faced by traditional computing platforms and adopt comprehensive and strict security measures. For example, consider plant security at the physical layer, consider integrity and file/log management, data encryption, backup, disaster recovery, etc. at the storage layer. Denial of service attacks, DNS security, network reachability, and data transmission secrets should be considered at the network layer. The system layer should cover security issues such as virtual machine security, patch management, system user identity management, etc. The data layer includes database security, data privacy and access control, data backup and cleaning, etc., and the application layer should consider the program integrity. Sex testing and vulnerability management. On the other hand, the cloud platform should prove to users that they have some level of data privacy protection. For example, the storage service proves that user data is stored in a compact state, and the computing service proves that the user code is running in protected memory. Due to differences in user security requirements, cloud platforms should have the ability to provide secure cloud infrastructure services at different levels of security.
3.5.2 Cloud Security Basic Services
The cloud security basic service belongs to the cloud basic software service layer and provides common information security services for various cloud applications. It is an important means to support cloud applications to meet user security goals. The typical cloud security services include cloud user identity management service. In the cloud environment, identity aggregation and single sign-on can support more convenient sharing of user identity information and authentication services between partners in the cloud, and reduce duplicate authentication zones. Operational overhead; cloud access control services, the implementation of cloud access control services depends on how to properly implement traditional access control models (such as role-based access control, attribute-based access control models, and mandatory/autonomous access control models) and various authorization policy language standards (such as XACML, SAML, etc.) are extended and ported into the cloud environment; cloud audit service, cloud audit service must provide all the evidence to meet the list of audit events and the credibility of the evidence. In addition, the cloud audit service is also an important way to ensure that cloud service providers meet various compliance requirements; cloud password service, due to the widespread data encryption and decryption computing requirements among cloud users, the emergence of cloud password service is also very natural. In addition to the most typical encryption and decryption algorithm services, key management and distribution, certificate management and distribution in cryptographic operations can be regarded as the form of basic cloud-based security services. The cloud password service not only simplifies the design and implementation of the cryptographic module for the user, but also makes the use of the cryptographic technology more centralized, standardized, and easier to manage.
3.5.3 Cloud Security Application Service
Cloud security application services are closely integrated with the needs of users. Typical examples are DDOS attack protection cloud services, Botnet detection and monitoring cloud services, cloud web filtering and antivirus applications, content security cloud services, security event monitoring and alert cloud services, cloud spam filtering and prevention.
4 Implementation of Electronic File Management System Based on Cloud Computing
The electronic file management system based on cloud computing is a comprehensive, wide-ranging and high-tech system. In the implementation process of the system, establishing a sound organization and doing a good job of personnel distribution management is the basis for the normal operation of the system. Before implementing the system, it is necessary to improve the implementation environment of the system and formulate an appropriate implementation plan.
The implementation environment of the system mainly includes the system specification. In addition to the traditional specifications that need to be directly configured in the system, it is also necessary to formulate a cloud-based electronic document management process and a system of division of responsibilities, system operation and maintenance, etc.; personnel distribution, including systems User manuals for different roles, professionally trained personnel settings, etc.; Cloud-based systems require third-party software support, which requires ensuring that the software can be installed and configured with the system software. The implementation plan of the system should clearly define all the information from the birth of the system in advance to ensure the completeness of the system in practical applications.
The implementation method of cloud-based electronic document management system has direct replacement of traditional systems, simultaneous operation of new and old systems, replacement of traditional systems in stages, pilot implementation, etc. The specific implementation methods depend on the business needs of the organization, technical environment, project budget, and project. Cycle and the impact of management culture. Generally speaking, under the premise of allowing, the gradual implementation method of piloting and post-promotion should be considered as much as possible, so as to give users time to accept and master new technologies and methods.
In the actual system implementation, it is preferred to configure the software to ensure that the system can be used normally. Perform functional and integrity tests on the system, test the user interface, input and output, and response and recovery time of the system to verify whether the system can be installed and operated under normal or emergency conditions. Test to verify that the system can run the design specification in normal or emergency situations. When applying cloud-based electronic document management systems, organizations need to consider a comprehensive migration strategy, and output legacy files from traditional systems to new systems at the right time to ensure the authenticity, integrity, reliability and reliability of the files. The migration process and results should be fully documented.
5 Features and Advantages of Cloud-Based Electronic File System
5.1 Reduce Costs, Hardware and Software Become Resources
Cloud-based electronic file management abstracts both software and hardware resources and provides them in the form of services over the network. In the traditional IT operation mode, each unit of the same level needs to build its own hardware infrastructure, and also includes some related management personnel to meet the needs of electronic file management. In the cloud computing mode, the application unit only needs to use the hardware and software resources in the cloud computing to meet the electronic file management requirements, without having to construct a data center separately, and reducing the input cost of each application unit. The management of the same level of electronic files only needs to build a cloud computing center and be uniformly maintained by the cloud computing center, which greatly reduces the operation and maintenance burden and reduces the cost.
5.2 Realize Unified Management of Resources and Facilitate Business Integration
The electronic file management system based on cloud computing integrates electronic file resources on the cloud platform to facilitate unified management of resources. The management unit configures the corresponding access rights according to the electronic file management requirements of each application unit, reduces unnecessary links, and improves work efficiency. In this way, when the business system and the electronic file management system are docked and integrated, the unified implementation of the cloud computing architecture standard can be implemented.
5.3 Electronic Files are Logically Concentrated and Physically Distributed
Cloud-based electronic file management, due to the uniformity and standardization of cloud computing, can achieve physical distribution among users at different levels, but logically centralized and unified. In this way, the requirements for unified management can be truly achieved, and the standardization of electronic document management is greatly improved.
This paper analyzes the electronic file management system from the perspective of cloud computing, and proposes an electronic file management system architecture based on cloud computing. This architecture has both software and hardware as resources to reduce costs; unified management of resources to facilitate business integration. To achieve the characteristics and advantages of electronic file logical concentration, physical distribution, etc. At the same time, this paper discusses the key technologies and implementation of electronic file management system based on cloud computing. The next step of this paper will be an in-depth study of the key technologies and implementations of the system presented in this paper.
Funding Statement: This research is financially supported by research Grants from the National Social Science Foundation of China (Grant No. 18FTQ005). The author of the grant is Shi Jin. The URL of the sponsor site is http://www.npopss-cn.gov.cn/.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. Peter and G. Tim. (2011). “The NIST definition of cloud computing (draft),” NIST Special Publication, vol. 53, no. 2, pp. 129–156. [Google Scholar]
2. P. J. Sun. (2020). “Security and privacy protection in cloud computing: Discussions and challenges,” Journal of Network and Computer Applications, vol. 160. [Google Scholar]
3. H. N. Talal, Z. Sherali, A. Abdullah and Z. S. Quan. (2018). “Mobile cloud computing: Challenges and future research directions,” Journal of Network and Computer Applications, vol. 115, pp. 70–85. [Google Scholar]
4. H. L. Feng. (1998). “Understanding electronic documents: One of the abstracts of having new memory-research on electronic document management,” Journal of Archives, vol. 1, pp. 44–48. [Google Scholar]
5. L. Y. Yu. (2015). “Analysis of the application of big data in electronic document management,” Library Work and Study, vol. S1, pp. 139–140. [Google Scholar]
6. Y. S. Chen, X. X. Yang, H. Heng and H. Su. (2015). “Archives management in e-government system: Problems and reflections,” Archival Research, vol. 1, pp. 28–37. [Google Scholar]
7. S. S. Xue. (2011). “Review of electronic document management in cloud computing environment,” Beijing Archives, vol. 9, pp. 25–27. [Google Scholar]
8. N. Liu. (2011). “Cloud technology in the security management of enterprise document,” in Second Int. Conf. on Innovations in Bio-inspired Computing and Applications, Shengzheng, China, pp. 267–269. [Google Scholar]
9. R. Juris and E. Gints. (2013). “Using of cloud computing, clustering and document-oriented database for enterprise content management,” in Second Int. Conf. on Informatics and Applications (ICIALodz, Poland, pp. 72–76. [Google Scholar]
10. I. Hsu. (2019). “XML-Based information fusion architecture based on cloud computing ecosystem,” Computers, Materials & Continua, vol. 61, no. 3, pp. 929–950. [Google Scholar]
11. Y. Zhao. (2013). “Opportunity and risk: Electronic document management in cloud computing environment,” Archives and Construction, vol. 10, pp. 4–6. [Google Scholar]
12. B. Gatewood. (2009). “Clouds on the information horizon: How to avoid the storm: Cloud-based solutions, such as web-based e-mail, have many advantages. but organizations must be aware of the compliance issues related to storing their information outside of their own control,” Information Management Journal, vol. 43, no. 4, pp. 1068–1089. [Google Scholar]
13. B. W. Wang, W. W. Kong, H. Guan and N. X. Neal. (2019). “Air quality forcasting based on gated recurrent long short term memory model in Internet of things,” IEEE Access, vol. 7, no. 1, pp. 69524–69534. [Google Scholar]
14. T. Mosweu, L. Lungile and O. Mosweu. (2019). “Implications of cloud-computing services in records management in Africa: Achilles heels of the digital era?,” South African Journal of Information Management, vol. 21, no. 1, pp. e1–e12.
15. V. L. Orlov and E. A. Kurako. (2017). “Electronic document management systems and distributed large-scale systems,” in 2017 Tenth Int. Conf. Management of Large-Scale System Development (MLSDMosow, Russia, pp. 1–5.
16. H. H. Song. (2020). “Testing and evaluation system for cloud computing information security products,” Procedia Computer Science, vol. 166, pp. 84–97. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |