DOI:10.32604/cmc.2021.014687

| Computers, Materials & Continua DOI:10.32604/cmc.2021.014687 |  |
| Article |
Adaptive Expanding Ring Search Based Per Hop Behavior Rendition of Routing in MANETs
1Faculty of Electrical and Computer Engineering, University of Engineering and Technology, Peshawar, 25120, Pakistan
2Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
*Corresponding Author: Durr-e-Nayab. Email: nayab.khan@uetpeshawar.edu.pk
Received: 09 October 2020; Accepted: 08 November 2020
Abstract: Routing protocols in Mobile Ad Hoc Networks (MANETs) operate with Expanding Ring Search (ERS) mechanism to avoid flooding in the network while tracing step. ERS mechanism searches the network with discerning Time to Live (TTL) values described by respective routing protocol that save both energy and time. This work exploits the relation between the TTL value of a packet, traffic on a node and ERS mechanism for routing in MANETs and achieves an Adaptive ERS based Per Hop Behavior (AERSPHB) rendition of requests handling. Each search request is classified based on ERS attributes and then processed for routing while monitoring the node traffic. Two algorithms are designed and examined for performance under exhaustive parametric setup and employed on adaptive premises to enhance the performance of the network. The network is tested under congestion scenario that is based on buffer utilization at node level and link utilization via back-off stage of Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA). Both the link and node level congestion is handled through retransmission and rerouting the packets based on ERS parameters. The aim is to drop the packets that are exhausting the network energy whereas forward the packets nearer to the destination with priority. Extensive simulations are carried out for network scalability, node speed and network terrain size. Our results show that the proposed models attain evident performance enhancement.
Keywords: Expanding ring search; mobile ad hoc networks; multi hop wireless networks; on-demand ad hoc networks; per hop behavior; quality of service
The Ad Hoc Routing research has high demand in the exploration of network response with respect to animatedly adjustment of routing protocol parameters. The Mobile Ad Hoc Networks (MANETs) has no pre-installed infrastructure for connectivity as the communication is carried out via several intermediate nodes between the source and destination node. Hence due to limited transmission range of wireless interfaces, the traffic is relayed between several hops without any base station in order to manage the connectivity. It is for this reason MANETs are also known as mobile multi hop ad hoc networks [1]. When a link between two nodes is up, it means they are in the transmission range of each other and can communicate directly. But when the direct linkage is not possible i.e., two nodes are not in each other’s transmission range, the nodes may use a number of intermediate nodes for communication. These intermediate nodes are also known as hops between source and destination and the total number of these hops measures the length of path between source and destination. Routing being the process of selecting routes through which the data is sent from source to destination is the most crucial challenge in MANETs. The nodes and routes in MANETs experience frequent changes in network topology resulting in unstable routes which affect the network quality of service (QoS) [2,3].
The dynamicity of MANETs makes efficient routing a very tricky job and since the nodes do not perform periodic tasks or keep records to cover the whole network; sending route requests from source to destination may cause congestion due to flooding. To tackle this scenario, routing protocols in MANETs exhibit Expanding Ring Search (ERS) for searching the routes and diminishing congestion [4,5]. In order to avoid flooding, the ERS in routing manage the route search in such a way that source node searches for the target node in a multiple rings search based on TTL instead of one to all scheme. Fig. 1 gives an illustration of a typical ERS based route discovery where the source (Node A) aims to send data to destination (Node B). The route discovery is achieved by increasing the TTL value from an initial state to a predefined threshold value and the radius of the search expands stepwise. The source node broadcasts a RREQ with initial TTL number and if no RREP is received after a certain amount of time, the TTL for RREQ is incremented with defined step respective of the routing scheme. This procedure for route discovery is repeated until the destination node is reached or the whole network is traversed.
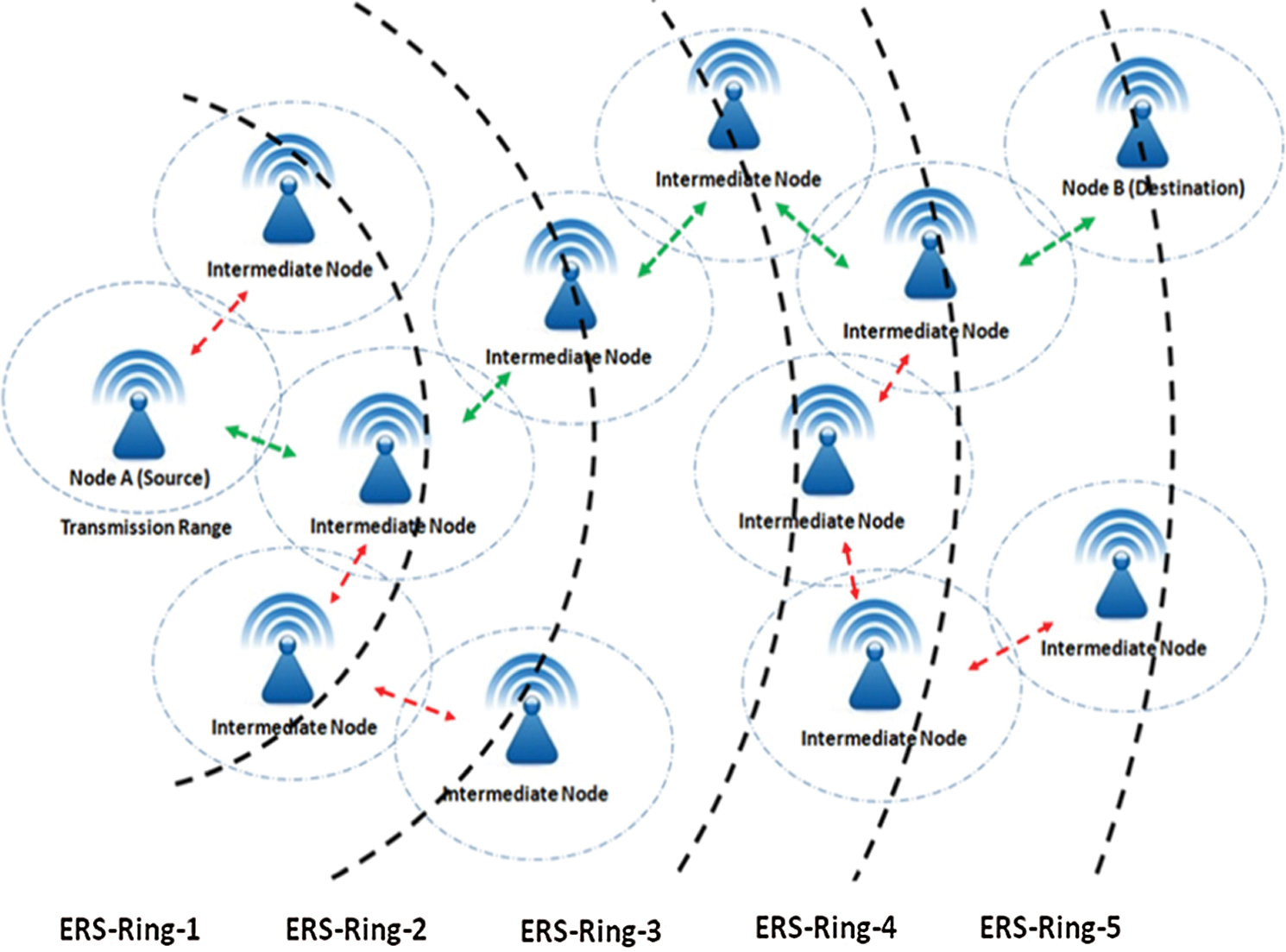
Figure 1: Node A (source) communicates with Node B (destination) through intermediate nodes in a MANET using ERS
ERS being an efficient search mechanism does avoid congestion due to flooding but it may cause overheads and more energy consumption as the route discovery process begins at the source node each time especially in widely spread networks [6]. Hence more enhanced versions of ERS are proposed for routing and research in this area still has space for exploration. After exploring different research works in this domain [4,7–13], we found there was no significant work on how the packets are presented for routing based on ERS parameters. We have explored the response of network to packets rendition using the combination of metrics such as buffer size, waiting time, hop count and ERS TTL values to achieve an adaptive routing mechanism to enhance the performance of MANETs routing.
The rest of the paper is organized in Section 2 that provides details of related work, Section 3 demonstrates the methodology and stepwise implementation of the proposed algorithm, Section 4 illustrates the simulation environment, Section 5 discusses the results and observations and Section 6 concludes the paper and provides an insight on future enhancements.
During the process of routing in MANETs the nodes make route requests and gets route reply from the nodes which are managed by the routing protocols via ERS mechanism. ERS use the TTL field in the IP header to reach out the nodes for route requests or route replies without causing flooding. A max weight packet scheduling scheme is proposed in [9] for reducing the packet drop due to retransmission. The scheme takes the knowledge on ERS in ad hoc on-demand distance vector (AODV) and improves the throughput of the network by achieving fair scheduling. Prioritizing different kinds of packets on the basis of network coding scheme aids to improve transmission efficiency. The proposed scheme attains a class based priorities to the ERS rings and combines the advantage of using proportional fair scheduling. Similar mechanism as in [14] works on unequal packet priority based on ERS that is utilized for wireless video broadcasting. Retransmissions are managed through buffer aided decodable network coding and priority aid. A route discovery mechanism for location based prediction model is proposed in [15]. The model is named as Hop-Prediction-ERS-AODV (HP-ERS-AODV), designed to discover the destination node based on previous hop counts. The performance of the proposed algorithm is compared with both Flood-ADOV and ERS-AODV and it is shown that HP-ERS-AODV outperforms both. An adaptive version of AODV is proposed in [16] based on max hop count as parameter to take routing decisions named as Dynamic-adjusting AODV (DA-AODV) routing protocol. DA-AODV utilizes the value of max hop count of the nodes in the network and adjusting the network parameters such node power accordingly to improve the network performance. The performance is enhanced in terms of energy consumption and end to end delay.
A congestion control model for MANETs is provided in [10], where hybrid approaches for clustering and queuing known RED (Random Early Detection) is attained via working on the arrangement of packets before routing process begins. The packets are classified and prioritized based on differentiated services for ensuring QoS. The results are improved as compared to another version Neighborhood Random Early Detection (NRED). The authors in [17] proposed another version of RED based on PHB (Per Hop Behavior) to ensure the QoS for new users when added to the network. The policy for QoS is set by the end users and the intermediate routers adapt and accept it automatically. Different variations of ERS are proposed and compared in [7,13] such as Blocking ERS (BERS), Improved Blocking ERS (I-BERS), TTL-Sequence ERS (TTLS-ERS), ERS+ and Improved Time-Efficiency in Blocking ERS (tBERS+). The results of these research works show that the BERS models has improved performance due to early flood cancellation in high node density environment of MANETs. The algorithms explore the ERS response to different waiting time. Adaptive values of waiting time are used to enhance the performance. An Energy Efficient ERS (E2-ERS) is proposed in [18] for optimizing the routing protocol. E2-ERS controls the number of RREQ retransmissions during route discovery process. The performance of original ERS is tallied with E2-ERS for multicast AODV with varying TTL_INCREMENT values in terms of end to end delay, packets delivery ratio and throughput.
Routing in MANETs is an interesting research domain due to extremely dynamic nature of MANETs and its applications in copious domains. The motivation for this work is to explore ERS mechanism of the routing protocols for enhancing the performance of MANETs in terms of routing. This is attained by changing the way in which the packets are handled for routing. Three mechanisms are designed for this purpose in which the TTL value of each route request is associated with per hop behavior before processing the packet. The details of the algorithm are provided in Section 3.
3 Per Hop Behavior for Packets Execution
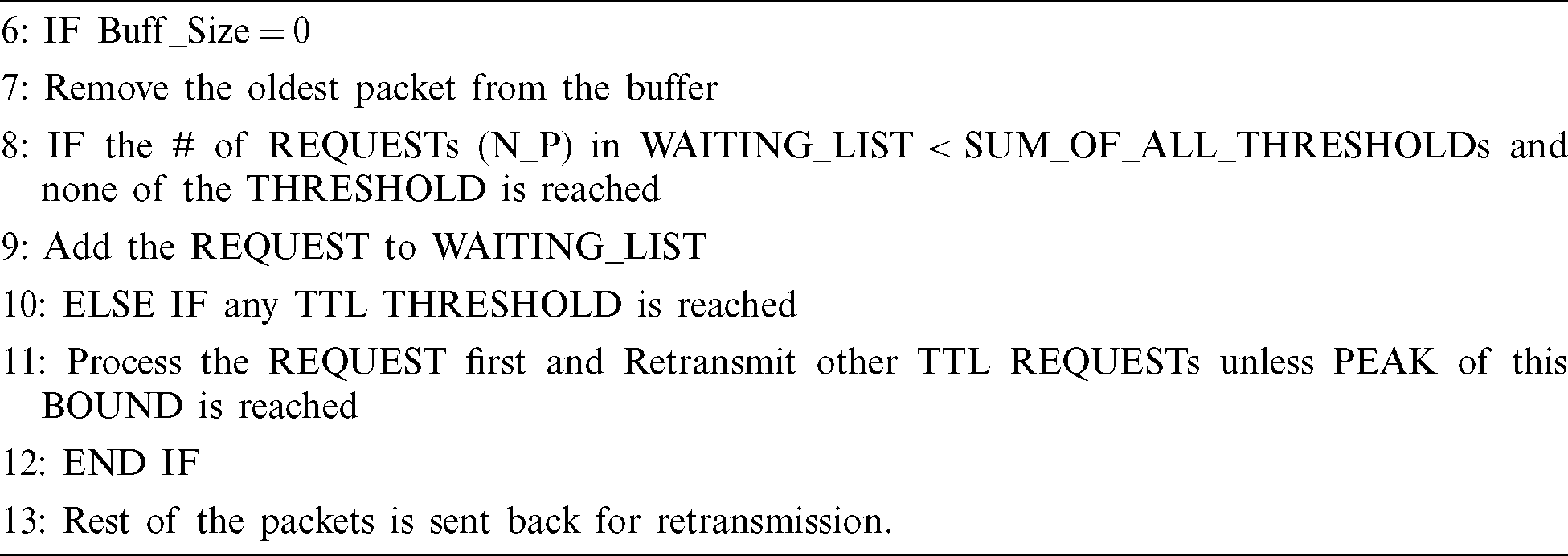
Routing protocols in MANETs (i.e., AODV, DYMO, DSR) deploy ERS for searching the route towards the target node [4,11,13,15]. Each protocol has its own respective values for TTL_ START, TTL_INCREMENT, TTL_THRESHOLD and NETWORK_DIAMETER values with different WAITING_TIMEs for implying ERS mechanism. All of these parameters are set up for devising the way in which the routing protocol carry route searches [19]. We explored the network routing response to these parameters based on per hop behavior and designed algorithms for adaptive routing of the packets. A route request (RREQ) or route reply (RREP) is evaluated for TTL value and node density in terms of number of RREQs and RREPs that are waiting to be processed for routing. To evaluate the frequency of TTL on a node, histograms are created in the node header and utilized for taking decision. The TTL has direct impact on the message delivery as it decides how long the packet stays in the network and when to leave the network. Conventional buffer management method waits for all the packets until the TTL expires. There is no mechanism for buffer management that is based on parameters such as buffer size, waiting time, hop count and ERS TTL values. Our proposed algorithm uses these metrics to decide which packet is to be processed for routing and which packet to be dropped.
Figs. 2a–2d depict the process of route request handling by proposed algorithm through adaptive ERS based PHB rendition. Three packets with TTL values TTL_1, TTL_2 and TTL_3 are waiting to be heard by the node. Initially the algorithm checks the number of requests (n) in waiting list of the node as shown in Fig. 2a and straight away adds the request if 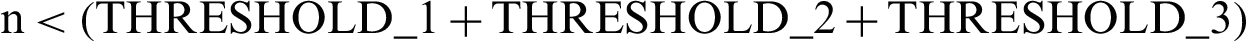 , i.e., none of the thresholds is reached. This is to ensure that as long as no constraint is reached the requests are handled without any loss. Once any THRESHOLD is reached the request is handled accordingly as shown in Figs. 2b–2d for THRESHOLD_2, THRESHOLD_2 and THRESHOLD_1 respectively. The retransmission is handled at transport level and the buffer management occurs at network level. The aim is to prioritize the TTL values that occur more frequently and have spent less time in the network whereas those taking longer time and less frequently occurring are dropped for retransmission. The frequency of the hops are intricately observed using histograms. The purpose of observing these histograms is to observe the behavior of packets in the network with respect to ERS values. Fig. 3 illustrates the histograms for network scalability of 10–50 nodes and provides a depiction of frequent TTL values. It can be observed in Fig. 3 that the hops count is dense in some TTL values and is scarce on other because of ERS setup.
, i.e., none of the thresholds is reached. This is to ensure that as long as no constraint is reached the requests are handled without any loss. Once any THRESHOLD is reached the request is handled accordingly as shown in Figs. 2b–2d for THRESHOLD_2, THRESHOLD_2 and THRESHOLD_1 respectively. The retransmission is handled at transport level and the buffer management occurs at network level. The aim is to prioritize the TTL values that occur more frequently and have spent less time in the network whereas those taking longer time and less frequently occurring are dropped for retransmission. The frequency of the hops are intricately observed using histograms. The purpose of observing these histograms is to observe the behavior of packets in the network with respect to ERS values. Fig. 3 illustrates the histograms for network scalability of 10–50 nodes and provides a depiction of frequent TTL values. It can be observed in Fig. 3 that the hops count is dense in some TTL values and is scarce on other because of ERS setup.
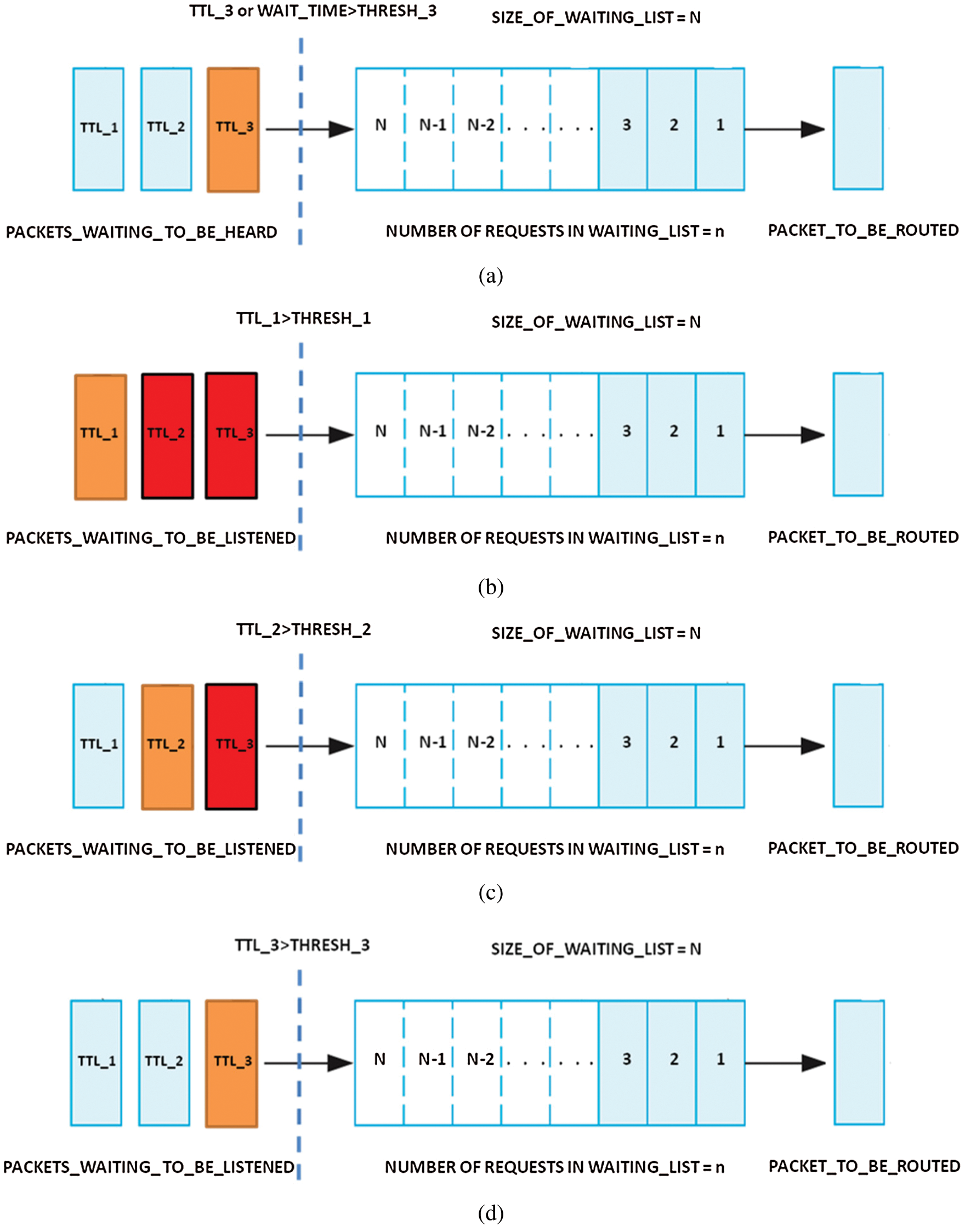
Figure 2: Route requests processing mechanism of the proposed algorithm. (a) Packet with ttl value TTL_3 is straight away added to the buffer as none of the thresholds is reached. (b) Packet with ttl value TTL_1 is added to the buffer as THRESH_1 is reached; whereas packets with ttl values TTL_2 and TTL_3 are dropped for retransmission. (c) Packet with ttl value TTL_2 is added to the buffer as THRESH_2 is reached; whereas packet with ttl values TTL_3 is dropped for retransmission and TTL_1 is waiting to be heard. (d) Packet with ttl value TTL_3 is added to the buffer as THRESH_3 is reached; whereas packets with ttl values TTL_1 and TTL_2 are waiting to be heard
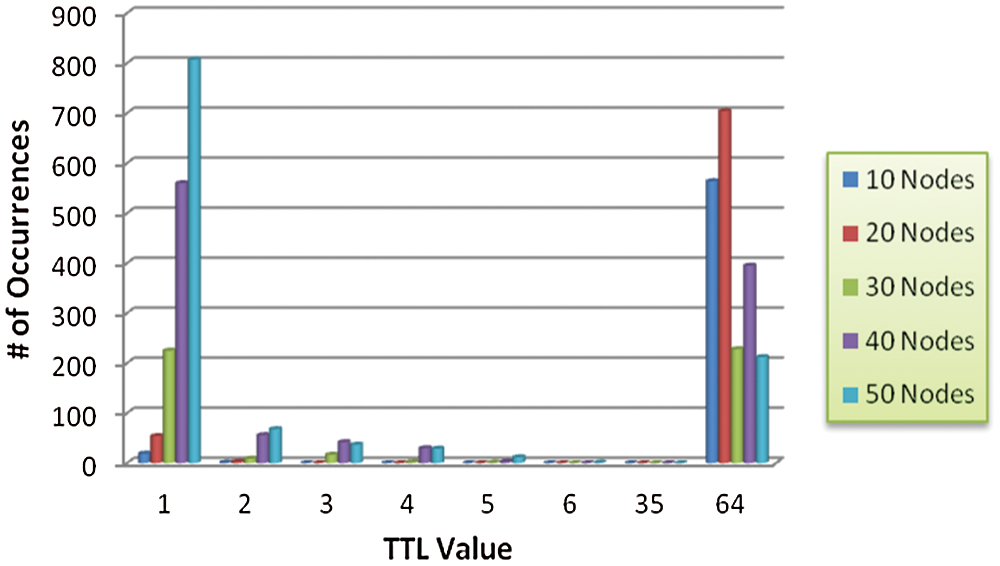
Figure 3: Histograms of TTL values for network scalability of 10–50
It can also be observed that according to network scalability the hop values also vary for instance lower TTL values are dense at higher node density and higher TTL values are scarce at lower node density and vice versa. This behavior plays a vital role in devising the proposed algorithm. Also the histograms are monitored both on network level as well as node level. Two modules are designed for this purpose to monitor the probabilities and respond accordingly. Correspondingly once the packets are added to the buffer; they are monitored for expiry time. If a packet is taking longer than expiry time it is dropped for retransmission.
The parameters explored for our algorithm are given as follows.
Hop count measures the number of hops a packet takes since it has been sent from the sender. When a packet is transmitted from the sender, it takes node by node journey towards it destination. Each time the packet goes through a node its hop count is incremented. The higher the value of hop count the higher the bandwidth is being consumed and higher the time taken by the packet in the network. Mathematically, as shown in Eq. (1), when a packet moves from node i towards node j next hop to it, its hop count (H_C) is incremented.

3.1.2 Waiting Time/Outstanding Buffer Time
Waiting time is the time a packet would spend in a node buffer to be handled by the routing protocol for routing. Waiting time is the measure of how much time the packet has spent in queue and is different from TTL of a message as shown in Eq. (2) mathematically.

where W_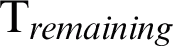 is the remaining waiting time of a message in buffer, W_
is the remaining waiting time of a message in buffer, W_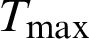 is the total waiting time for a packet to wait in queue as defined by the protocol in use (e.g., 30 s for AODV, DSR and DSDV), C_T is the current time and A_T is the arrival time of the packet in buffer.
is the total waiting time for a packet to wait in queue as defined by the protocol in use (e.g., 30 s for AODV, DSR and DSDV), C_T is the current time and A_T is the arrival time of the packet in buffer.
Route Re-Tries is the number of message/packets retransmitted by a node. When a node sends a packet out for its destination; the packet traverses the allowed number of first round of hops under ERS. The node sends out another copy of this packet for second round of hops and the local RRT is incremented as shown in Eq. (3).

Time To Expire (TTE) is the time after which the message leaves the network. When TTE is reached the message is removed from its destination and the network using Eq. (4).

where F_T is the packet formation time, C_T is the current time and TTL is the time to live of a message.
Buffer Size refers to the number of packets occupying the buffer of a node. When more and more packets are released by the source and the processing speed is not efficient enough; the buffer overflow occur that leads to packets drop. When the buffer has maximum capacity of MAX_Q_L and the number of packets in buffer is N_P then the buffer size can be given by Eq. (5).

Detailed demonstration of the algorithm is given in this section. The algorithm is divided into three Modules. Step wise demonstration is provided for Module 1 while Module 2 operates in the similar manner as Module 1 with different values for TTL priorities, THRESHOLDs and UPPER_BOUNDs as mentioned in the detailed demonstration. Module 3 is an adaptive routing module that takes decision based on network scenario.
Considerations:
THRESHOLD_1 monitors ERS_TTL_THRESHOLD
THRESHOLD_2 monitors NETWORK_DIAMETER
THRESHOLD_3 monitors 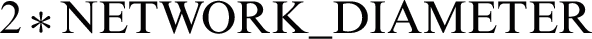
Different UPPER_BOUNDs are set for all three THRESHOLDs, selected on the basis of simulation results._
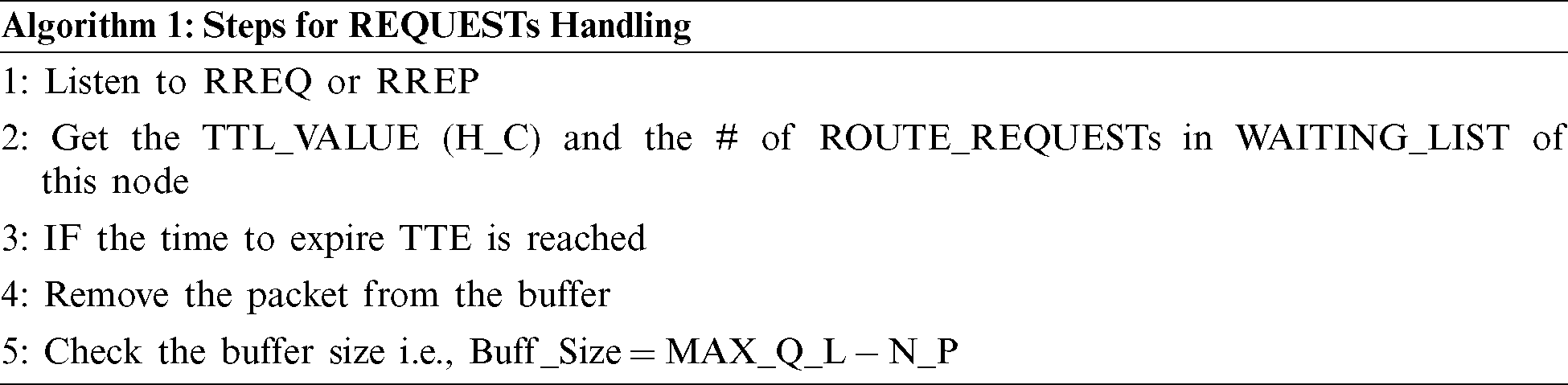
:
Packet to Route Generalization:
Packet to 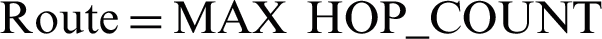 {(
{(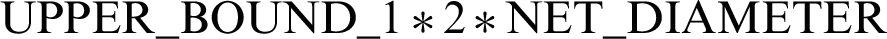 ), (
), (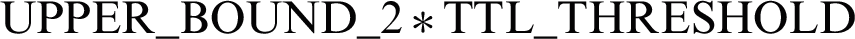 ), (
), (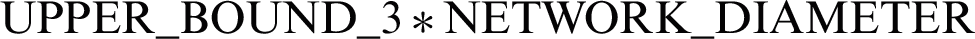 )}
)}
Considerations:
Here the packets are handled with common THRESHOLDs and priorities are given based on ERS Parameters, Waiting time and TTL values with no retransmissions. The priorities in both Modules 1 and 2 are given in the following manner:
Packets with 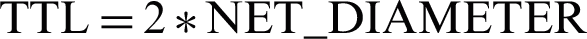 are processed first. That is, the highest TTL value in ERS is processed first for finding the route.
are processed first. That is, the highest TTL value in ERS is processed first for finding the route.
Packets with 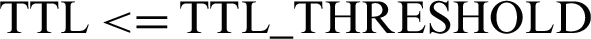 are processed first. That is, the lowest TTL values in ERS are processed first for finding the route.
are processed first. That is, the lowest TTL values in ERS are processed first for finding the route.
Packets with 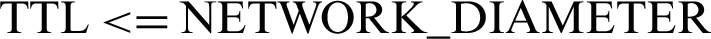 are processed first.
are processed first.
3.2.3 Module 3 (Adaptive Routing Model)
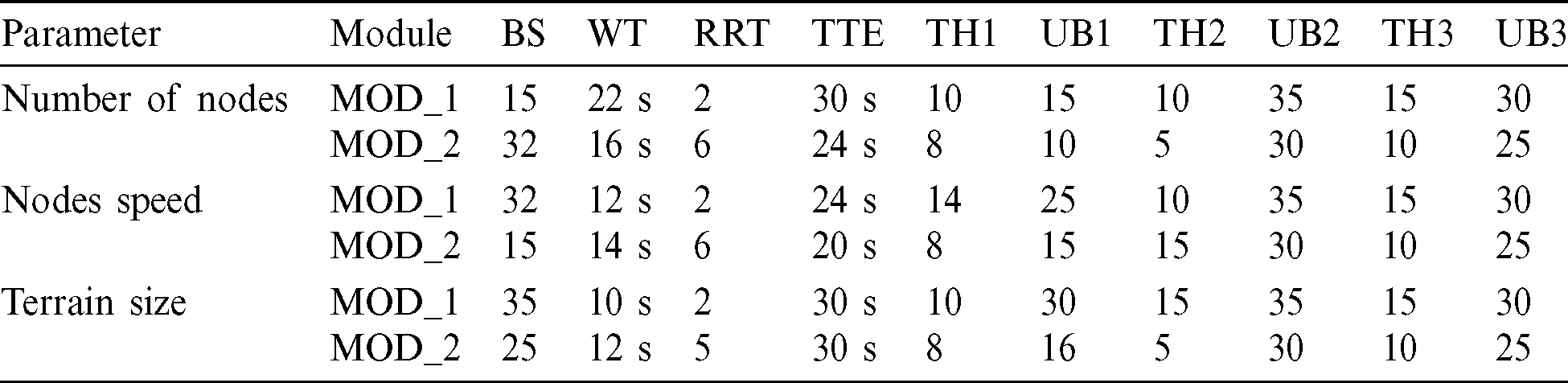
The adaptive model takes decision based on the network topology and selects the best suited method based on TTL accordingly. This mechanism is designed for future work where various routing protocols will be simulated for various network topologies and learning techniques will be trained on them [20–22]. The machine learning techniques will then be exploited for taking decision for selection of best routing protocol in given network scenario. This is preliminary stage work hence we have evaluated the results manually. Here the algorithm selects the best suited routing algorithm among the newly designed algorithms and a mechanism that prioritizes packets on the basis of TTL value. Step wise demonstration of the proposed algorithm is provided in Fig. 4 in the form of flow chart. The values of parametric setup for the proposed algorithm are tabularized in Tab. 1. The values of Buffer Size (BS), Wait Time (WT), Route Retries (RRT), Time to Expire (TTE), Thresholds (THs) and Upper Bounds (UBs) are provided for varying network scalability, node speed and terrain size. The parameters are tabulated for module 1 and module 2 of proposed algorithm.
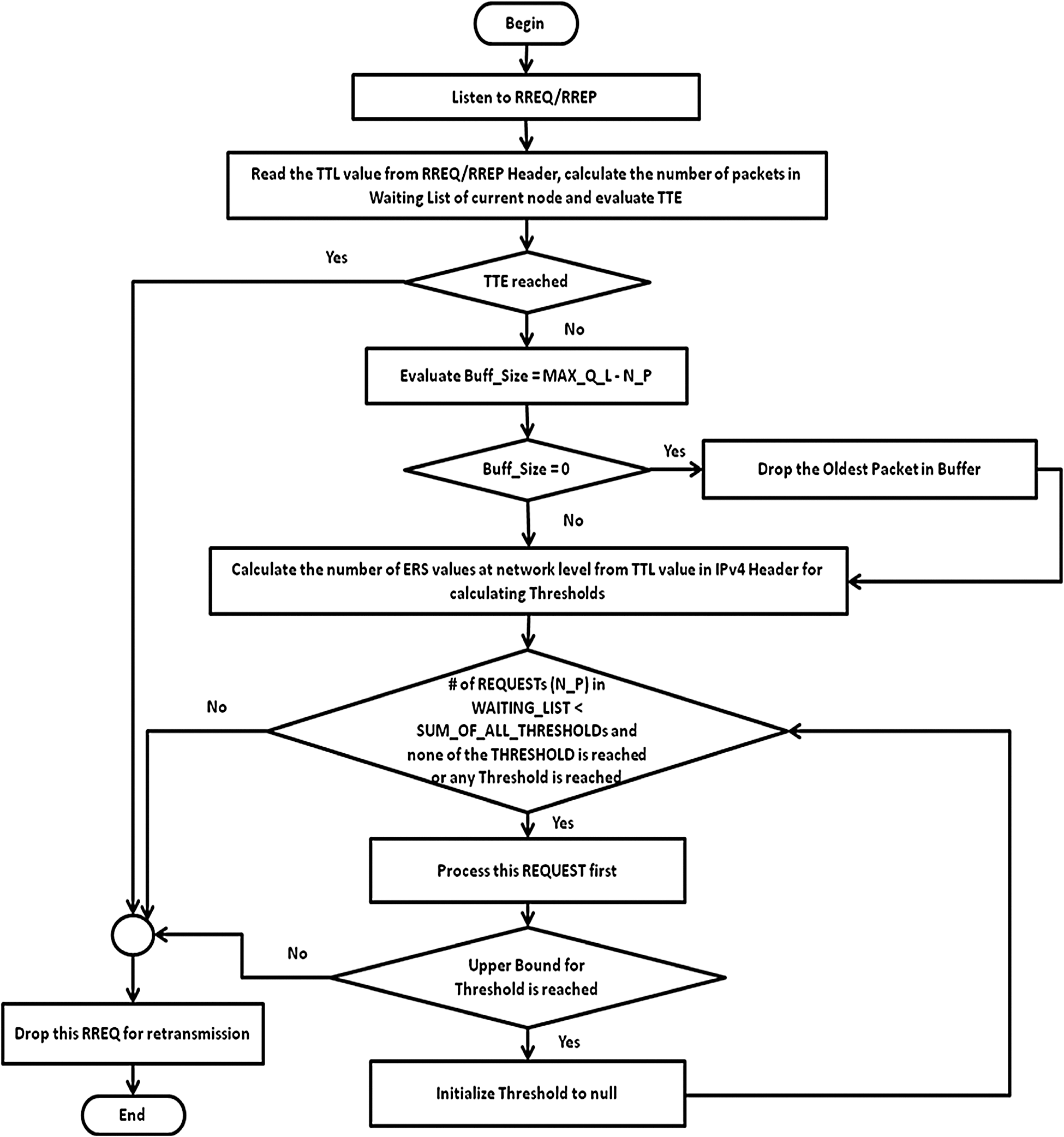
Figure 4: Flow chart of proposed algorithm
Table 1: Parametric settings for proposed algorithm
4 Experimental Setup and Simulation Environment
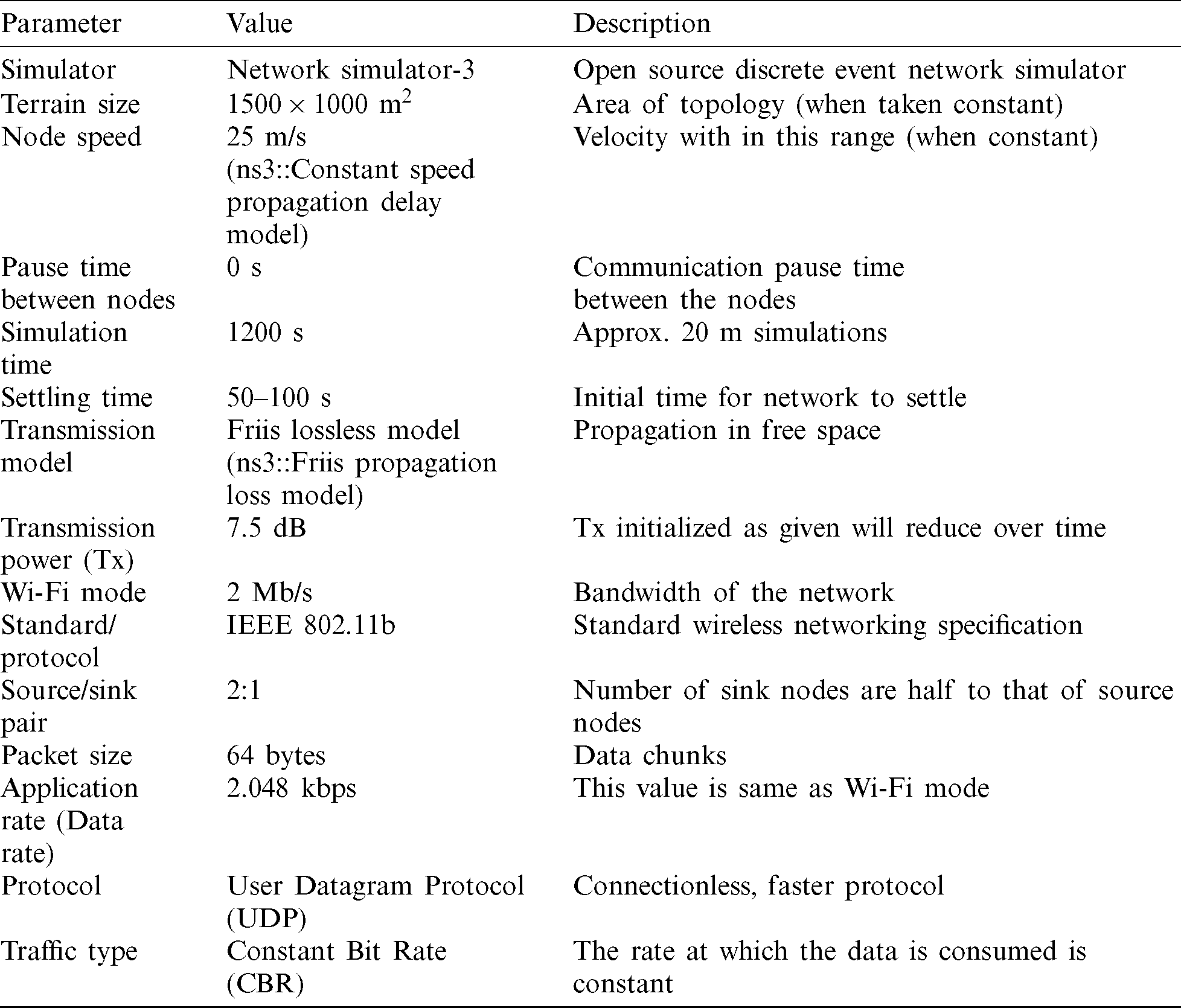
In order to evaluate the performance of the network, we have used Network Simulator-3 (NS-3) [23] which is an open source tool and widely used for research in the field of wireless Ad-hoc networking. The parametric settings for Ad Hoc network environment settings in NS-3 are provided in Tab. 2. Note that the settling time varies for difference algorithms. The simulation uses Frii’s lossless model i.e., the loss directly depends upon the distance a node travels from its neighbor while sending packets. The Wi-Fi is in ad-hoc mode with 2 Mb/s rate i.e., the hardware consideration is made by employing constant bit rate traffic type. Such node comes under the category of Wi-Fi Ad-hoc nodes, following 802.11b IEEE protocol with MAC layer distributed coordination function.
Table 2: Parametric settings for topology in network simulator-3
4.1 Metrics for Performance Evaluation
4.1.1 Average End to End Delay
Average End to End (E2E) delay refers to the time taken by a packet to traverse across a network between source and destination. This includes all possible delays caused by buffering during routing discovery latency, queuing at the interface queue, processing delays, retransmission delays at the MAC, propagation and transfer times. Thus this parameter readily explicates the usage of a specific protocol for communication between nodes as well as the architecture used on each node besides media access mode and noise profile. The delay is measured in nano-seconds which is then converted in seconds by multiplying with 109.
4.1.2 Average Receive Rate/Throughput
Average receive rate is the average rate at which the network is transmitting data from source to sink per second, i.e., the rate at which the data packets are received at nodes in each adopted protocol. This represents the bandwidth of the channel. This is also synonymous to throughput of the network. The throughput is measured in kbps and mathematically measure as in Eq. (6).

4.1.3 Packets Delivery Ratio (PDR)
Packets Delivery Ration (PDR) is the ratio between the number of packets transmitted and the received packets by the sinks. This metric specifies the success rate of packets, i.e., how efficiently the packets in the network are transmitted from sender end to receiver end. The higher the PDR value the higher is the probability of successful packets delivery and lesser packets loss. Percentage PDR is measured for each iteration by mathematical expression given in Eq. (7).

This metric measures the number of packets that do not reach their respective destination successfully. High number of lost or dropped packets affect the efficiency of the network. When the packets are frequently dropped, the network attempts to retransmit the packet unless they reach their destination. Such retransmissions overload the network. Also loss of too many packets may cause incomplete data transmission.
Network density or the network size is the total number of nodes in the network. When the network is denser the average hop length or TTL value increases which may cause more retransmissions and increase the load on the network. Numerous topologies are devised for network density ranging from 10 to 50 nodes while other simulation parameters as shown in Tab. 2 are kept constant.
Node speed specifies the maximum velocity a node in the network can attain. The node speed varies from 10 to 100 m/s in the network density of 25 nodes with max sinks up to 5. These values of speed are chosen for general speed of human, ground vehicles and unmanned air vehicles (UAV). The rest of the parametric settings are kept constant.
The size of the network topology in terms of area in meter square region is taken by x and y coordinates. Almost eight topologies are explored for terrain ranging from  m2–
m2– m2. The network density is 20 nodes with max sinks up to 5 while other simulation parameters are kept constant.
m2. The network density is 20 nodes with max sinks up to 5 while other simulation parameters are kept constant.
5 Simulation Results and Discussions
This section summarizes the results of the proposed algorithms and compares them with standard protocols for performance evaluation. Figs. 5a–5d illustrate the throughput, packet loss, E2E delay and packet delivery ratio of the proposed algorithm for varying network node densities. The comparison of proposed algorithm is not only given with standard AODV-ERS over which it is applied but three other standard reactive and proactive routing protocols are also compared such as DSR, DSDV and OLSR. The results are evaluated for 90% confidence interval of 10 different runs of same seed simulations. The proposed algorithm AERSPHB outperforms all protocols in most parametric set up. High throughput in most cases, as shown in Fig. 5a, is achieved also the number of lost packets as shown in Fig. 5b is less as compared to others; this change in behavior confirms the response of routing protocol. The E2E delay as shown in Fig. 5c does not improve in some scenarios i.e., in lower number of nodes but in higher network scalability better performance w-r-t delay is achieved. This initial decline can be improved by changing the attributes as mentioned in Tab. 1 which is part of our future work where we will use artificial neural networks (ANNs) to automate the parametric setup of Tab. 1. Higher PDR is achieved by AERSPHB, as shown in Fig. 5d, compared to AODVERS and other protocols.
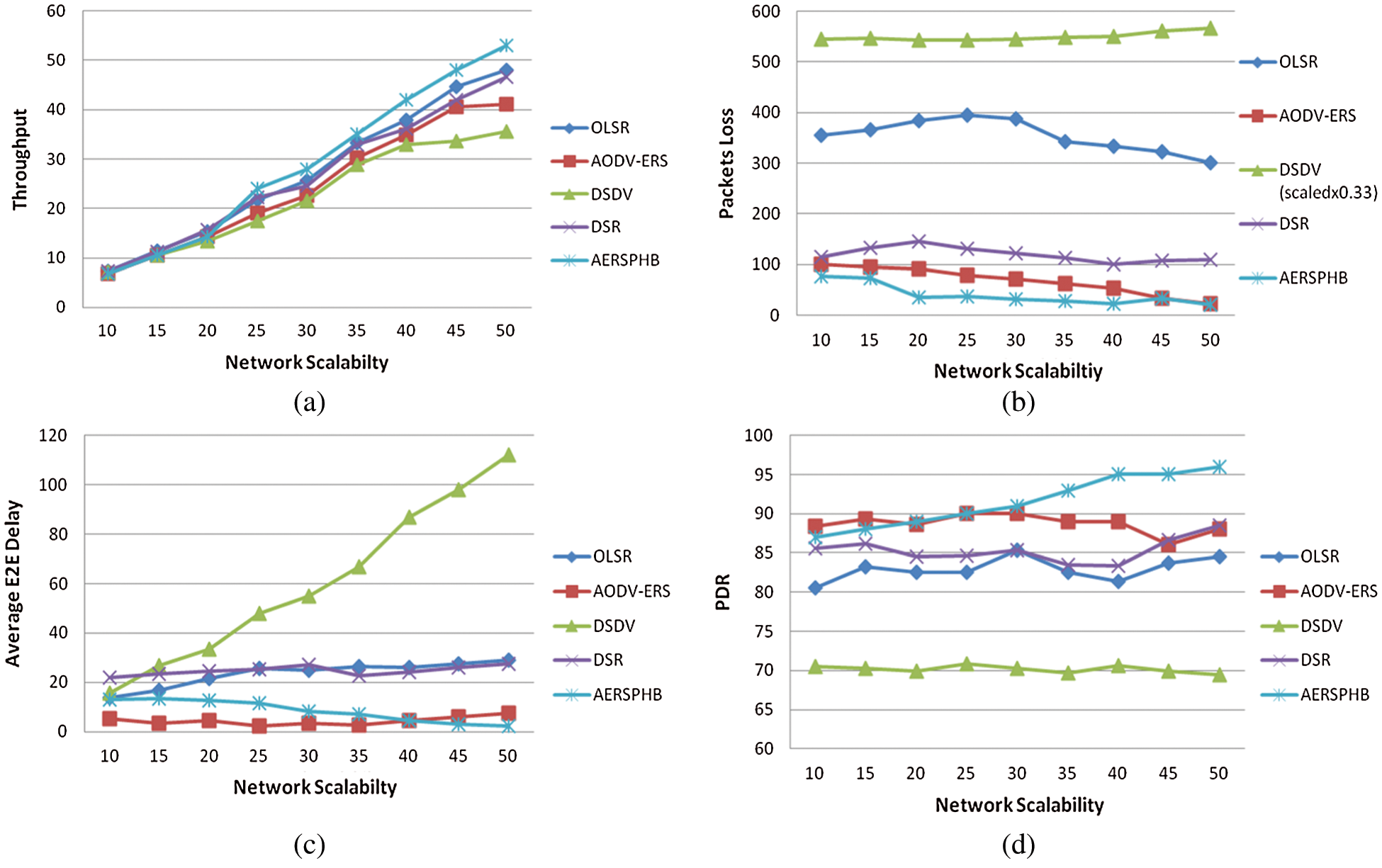
Figure 5: (a) Throughput, (b) packet loss, (c) average end to end delay and (d) PDR of the proposed algorithm (AERSPHB) vs. standard protocols for varying network scalability
Figs. 6a–6d illustrate the simulation results in terms of network size in meter square region. The performance comparison is given for proposed algorithm and standard routing protocols in terms of throughput, average E2E delay, number of lost packets and PDR. Significant improvement is achieved as shown in Figs. 6a–6d however the delay in some cases has increased slightly. This delay was improved with different parametric setup of Tab. 1 but that disproved the performance of the other cases. Hence there is a tradeoff which will be targeted in our future work as mentioned earlier.
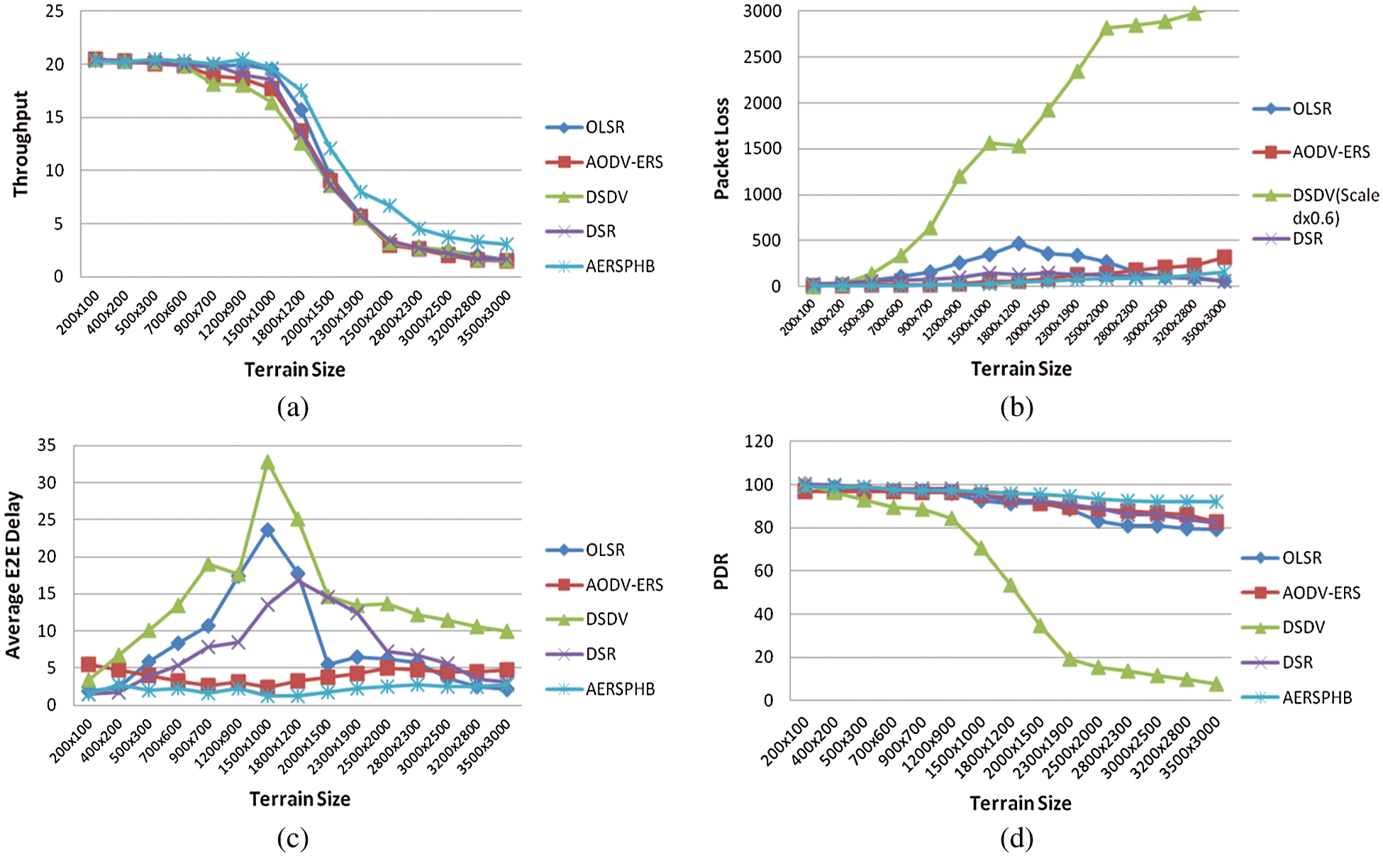
Figure 6: (a) Throughput, (b) packet loss, (c) average end to end delay and (d) PDR of the proposed algorithm (AERSPHB) vs. standard protocols for varying network size
The results for varying network nodes speed are shown in Figs. 7a–7d. Some standard speed values are employed such as normal speed of human, vehicles and unmanned air vehicle (UAV). The performance is evaluated and is compared for the mentioned network setup. The throughput, lost packets, E2E delay and PDR values as shown Figs. 7a–7d verify that AERSPHB has significantly achieved better performance, i.e., adaptive ERS based PHB mechanism improves the performance of standard protocol and can be further improved if the parametric setup is tested for further values and automated using ANN.
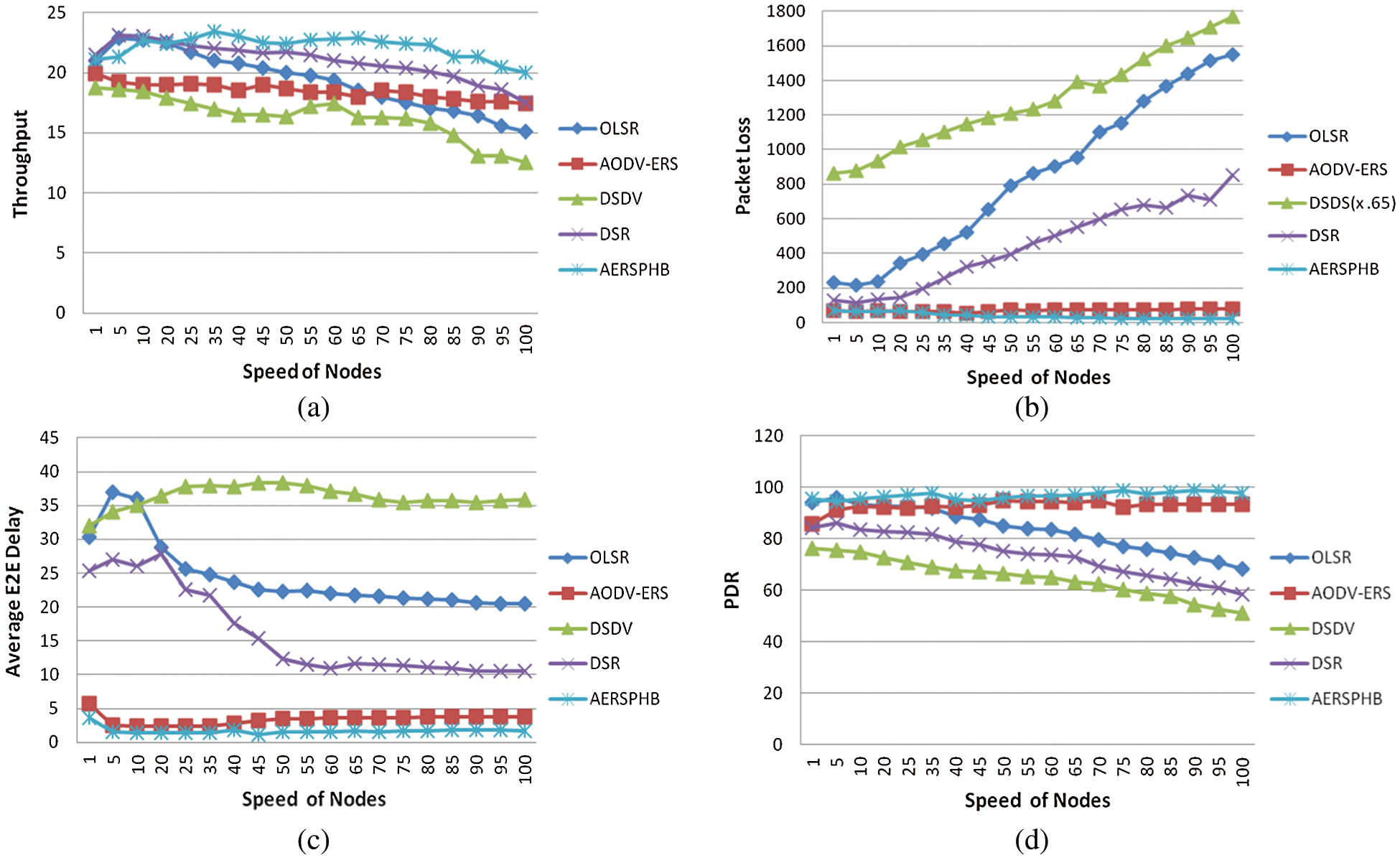
Figure 7: (a) Throughput, (b) packet loss, (c) average end to end delay and (d) PDR of the proposed algorithm (AERSPHB) vs. standard protocols for varying speed of nodes
6 Conclusion and Future Enhancements
Mobile ad-hoc networks are core of the modern wireless networking and mobile computing technologies. Researchers these days are more interested in improving and upgrading the routing protocols for MANETs to enhance the performance and utilize them for more applied technologies such as Internet of Things (IoT). This research exploits the relation between the time route request of a packet spends in the network in order to reach its destination, the node and link level congestion and the ERS parametric setup employed for routing. Three methods are designed in which the requests are handled based on ERS, hops count, buffer utilization and timings arrangement of the network. Packets are arranged and prioritized before being processed for various network scenarios. The results illustrate that the performance of the routing has significantly improved which declares the relation between ERS setup, buffer size, hops count and timings net. This put forth further research pull towards exploring and automating more parametric arrangements for ERS and the thresholds used in proposed algorithm using machine learning techniques. We are exploiting ANNs as future enhancement of this work based on collected simulation results. Another contribution from this work will be to apply the proposed algorithm for more protocols that exhibit ERS such as DSR and DYMO and automate the parametric setup for them. The results generated in this work can provide enough data to be fed to the algorithms and achieve decision making techniques for other networks and attain maximum network throughput, context aware routing for packet sensed routing and many more research in which the IETF, IoT, WSN and other network enhancement and application communities may indulge.
Funding Statement: The author(s) received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. E. Ghadimi, A. Khonsari, A. Diyanat, M. Farmani and N. Yazdani. (2011). “An analytical model of delay in multi-hop wireless ad hoc networks,” Wireless Networks, vol. 17, no. 7, pp. 1679–1697.
2. N. A. M. Saudi, M. A. Arshad, A. G. Buja, A. F. A. Fadzil and R. M. Saidi. (2019). “Mobile ad-hoc network (MANET) routing protocols: A performance assessment,” in Proc. Third Int. Conf. on Computing, Mathematics and Statistics, Singapore: Springer, pp. 53–59.
3. Z. Guo, S. Sheikh, C. Al-Najjar, H. Kim and B. Malakooti. (2010). “Mobile ad hoc network proactive routing with delay prediction using neural network,” Wireless Networks, vol. 16, no. 6, pp. 1601–1620.
4. N. Javaid, Z. A. Khan, U. Qasim, M. Jamil, M. Ishfaq et al. (2015). , “Modeling routing overhead of reactive protocols at link layer and network layer in wireless multihop networks,” Mathematical Problems in Engineering, vol. 2015, no. 1, pp. 1–14.
5. Y. Mai, F. M. Rodriguez and N. Wang. (2018). “CC-ADOV: An effective multiple paths congestion control AODV,” in Proc. IEEE 8th Annual Computing and Communication Workshop and Conf., Las Vegas, NV, USA, pp. 1000–1004.
6. D. Krishnamoorthy, P. Vaiyapuri, A. Ayyanar, Y. R. Harold, R. Kumar et al. (2020). , “An effective congestion control scheme for MANET with relative traffic link matrix routing,” Arabian Journal for Science and Engineering, vol. 45, no. 8, pp. 6171–6181.
7. K. Y. Gwak, S. Park and J. Song. (2019). “Performance evaluation: Two flood-cancellation methods of the blocking expanding ring searches on the AODV/WiFi MANET environment,” in Proc. 21st Int. Conf. on Advanced Communication Technology, PyeongChang, South Korea, pp. 239–248.
8. N. Akhtar, M. A. K. Khattak, A. Ullah and M. Y. Javed. (2019). “Congestion aware and adaptive routing protocols for MANETs: A survey, ” in Recent Trends and Advances in Wireless and IoT-enabled Networks, 1st ed., vol. 1. Cham, Switzerland: Springer, pp. 159–169.
9. J. Zhou, X. Chen, Y. Deng, L. Cui, K. Wei et al. (2017). , “Maximum weight packet scheduling scheme with retransmission in multi-hop wireless networks,” in Proc. IEEE Tenth Int. Conf. on Mobile Computing and Ubiquitous Network, Toyama, Japan, pp. 1–4.
10. S. Sharma, D. Jindal and R. Agarwal. (2018). “Analysing mobile random early detection for congestion control in mobile ad-hoc network,” International Journal of Electrical and Computer Engineering, vol. 8, no. 3, pp. 1305–1314. [Google Scholar]
11. N. Javaid, A. Bibi, S. N. Mohammad, Z. A. Khan and N. Alrajeh. (2015). “Towards optimizing routing overhead in wireless multi-hop networks,” International Journal of Ad Hoc and Ubiquitous Computing, vol. 19, no. 1/2, pp. 4–18. [Google Scholar]
12. S. Li and W. Jia. (2010). “AODV route protocol research based on improved ERS algorithm,” in Proc. IEEE Int. Conf. on Wireless Communications, Networking and Information Security, Beijing, China, pp. 102–106. [Google Scholar]
13. A. H. Shintre and S. Sondur. (2014). “Improved blocking expanding ring search (I-BERS) protocol for energy efficient routing in MANET,” in Proc. IEEE Int. Conf. on Recent Advances and Innovations in Engineering, Jaipur, India, pp. 1–6. [Google Scholar]
14. T. Niu, D. Zhang, K. Xu, L. Wu and Y. Jiang. (2016). “Buffer-aided instantly decodable network coding for wireless video broadcasting with unequal packet–priority retransmission,” in Proc. IEEE 16th Int. Sym. on Communications and Information Technologies, Qingdao, China, pp. 117–122. [Google Scholar]
15. K. Adhvaryu. (2020). “Performance comparison of multicast routing protocols based on route discovery process for MANET,” in Inventive Communication and Computational Technologies, 1st ed., vol. 89. Singapore: Springer, pp. 79–85. [Google Scholar]
16. T. Xing, Y. Liu, B. Tang and F. Wu. (2010). “Dynamic-adjusting AODV routing protocol based on max hop count,” in Proc. IEEE Int. Conf. on Wireless Communications, Networking and Information Security, Beijing, China, pp. 535–539. [Google Scholar]
17. I. Topalova and P. Radoyska. (2018). “Control of traffic congestion with weighted random early detection and neural network implementation,” in Proc. 14th Int. Conf. on Automatic and Autonomous Systems, Nice, France, pp. 8–12. [Google Scholar]
18. K. U. Adhvaryu. (2019). “Energy efficient ERS for multicast routing in MANET,” in Proc. IEEE Int. Conf. on Recent Advances in Energy–Efficient Computing and Communication, Nagercoil, India, pp. 1–4. [Google Scholar]
19. N. E. Majd, N. Ho, T. Nguyen and J. Stolmeier. (2019). “Evaluation of parameters affecting the performance of routing protocols in mobile ad hoc networks (MANETs) with a focus on energy efficiency,” in Future of Inf. and Communication Conf., Cham, Switzerland: Springer, 70, pp. 1210–1219. [Google Scholar]
20. A. Ghaffari. (2017). “Real-time routing algorithm for mobile ad hoc networks using reinforcement learning and heuristic algorithms,” Wireless Networks, vol. 23, no. 3, pp. 703–714. [Google Scholar]
21. M. Duraipandian. (2019). “Performance evaluation of routing algorithm for MANET based on the machine learning techniques,” Journal of Trends in Computer Science and Smart Technology, vol. 1, no. 1, pp. 25–38. [Google Scholar]
22. H. Yang, Z. Li and Z. Liu. (2019). “A method of routing optimization using CHNN in MANET,” Journal of Ambient Intelligence and Humanized Computing, vol. 10, no. 5, pp. 1759–1768. [Google Scholar]
23. L. Maygua–Marcillo, L. Urquiza–Aguiar and M. Paredes–Paredes. (2019). “Creating a new model in NS3 network simulator,” in Preprints, Basel, Switzerland, pp. 1–5. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |