DOI:10.32604/cmc.2021.015056

| Computers, Materials & Continua DOI:10.32604/cmc.2021.015056 |  |
| Article |
Service-Aware Access Control Procedure for Blockchain Assisted Real-Time Applications
1Department of Information Systems, Faculty of Computing and Information Technology (FCIT), King Abdul Aziz University (KAU), Jeddah, Kingdom of Saudi Arabia
2School of Information and Communication Engineering, University of Electronic Science and Technology of China (UESTC), Chengdu, China
*Corresponding Author: Alaa Omran Almagrabi. Email: aalmagrabi3@kau.edu.sa
Received: 04 November 2020; Accepted: 17 December 2020
Abstract: The design of distributed ledger, Asymmetric Key Algorithm (AKA) blockchain systems, is prominent in administering security and access control in various real-time services and applications. The assimilation of blockchain systems leverages the reliable access and secure service provisioning of the services. However, the distributed ledger technology’s access control and chained decisions are defaced by pervasive and service unawareness. It results in degrading security through unattended access control for limited-service users. In this article, a service-aware access control procedure (SACP) is introduced to address the afore-mentioned issue. The proposed SACP defines attended access control for all the service session by identifying the users and service provider availability. The distributed nature of the ledger systems and classification tree learning are combined to determine unattended access. The sole access is determined by summarizing the closed and open access requests and the service provider’s availability and integrity checks. In this process, the learning process classifies the secured access request and completed the integrity checks of the current and previous service dissemination. This classification-based access administration reduces the service disconnections and false access rate of the applications.
Keywords: Access control; blockchain classification trees; service dissemination; unattended access
A Blockchain is a technique that stores and protects the network’s data and shares the overview information to the other end applications. It is a digital block that is continuously connected and stores its transaction history for security; it uses the cryptography method [1,2]. By processing this, it avoids the risk of malicious access to the system. The blockchain is associated with transaction history, identity and stores the timely incoming data. It the distributed ledger of user records and provides authorized access [3]. In this manner, data loss and hacking are reduced, and it shows the timely manner of data retrieval. The process of retrieval is allowed from the server [4]. Based on this valid access, the services are allocated to the user. If the user wants to access the particular service, it requests the server, the server, and the server to check whether it is a valid user or not [5]. The verification is acquired from the blockchain, where it stores the history of the user process and provides the required information. The trust-based service and access control are developed for security and are implemented on real-time applications [6–8].
Blockchain-based access control is determined to manage the smart digital information and respond to the user [9]. The response is used to evaluate the user’s resultant data from the server based on reasonable access control [10]. They are three types of access controls that are determined, such as access control methods include discretionary access control (DAC), identity-based access control (IBAC), and mandatory access control (MAC) [11]. Based on the application, the required access controls are used in the blockchain to process adequate data acquiring [12,13]. In this manner, access control is provided to the valid user, determined by evaluating the security-based access control. It includes the user’s identity and previous activity and provides timely data retrieval for the requested user [14]. For every transaction, the data and access is determined by associating the information based on the time that includes the data storing time and retrieval data. Thus, Blockchain access control is used to store the data and retrieves the user based on the access control method [15,16]. The master–slave relation with the original copies can be used to duplicate the database provides a timely manner in which data retrieval for the requested user is determined by associating the information based on the time. The master tracks updates, the slave, which notifies the update that has been obtained successfully to relay subsequent updates. Secure service access control is used to reduce the organization’s risk, which allows the authorized user to access the service [17]. Three types of access control are used to secure the service in real-time applications. The access control includes role-based access control (RBAC), discretionary access control (DAC), and mandatory access control (MAC) [18]. All these are used to secure the data from the malicious user and provide reliable access. If the user requests the service, the server provides access based on these three methods [19]. The security includes the identity of the user based on the request using the identity match is evaluated. Thus, both authentication and authorization are performed to address security applications [20–22]. By processing this, it decreases service disconnection and false access rates in real-time applications.
Attribute-based access control is designed by Ding et al. [23] that is developed for IoT in Blockchain. The objective of this work is to improve high efficiency and lightweight calculation for IoT devices. Xu et al. [24] presented a blockchain-based secure data-sharing platform with fine-grained access control (BSDS-FA) to acquire the authenticated user. The blockchain is used to evaluate the decryption algorithm based on tracking the information.
In this paper, the author developed two techniques to improve the system’s performance and data consistency [25]. Here, the Hyperledger Fabric blockchain framework and attributed based access control (ABAC) are used to address three types of services. It includes Device Contract (DC), Policy Contract (PC), and Access Contract (AC) is used to enhance the throughput of the system. Blockchain monitoring and upgrading systems for request-response reduce the consequences of incorrect resource access in this process that have been surveyed. In the blockchain, the request’s state is changed for more entry along with the services available. Further, the Classification lessons are used to define the various state of the recommendations to simplify updating. Increasing drivers in improving users Access Security are data collection and integrity verification validations between service providers and end-user apps.
2 Service-Aware Access Control Procedure
Blockchain is a distributed ledger that holds internet transactions and handles data in the cloud. This role is based on a classification tree leaning, in which a service-aware access control mechanism (SACP) is built. SACP is formally described in blockchain-based application services in Fig. 1. Between the apps and the network layer and the service provider’s layers, blockchain services are given. During the access interval between programmers and applications, the SACP mechanism is administered. The connectivity layer provides infrastructure-based support for request and response exchange.

Figure 1: SACP in blockchain-based applications services
SACP is built based on the proposed classification tree and addresses the unattended entry. It eliminates service disconnection and false access rates in the real-time application by processing. To fix this problem, SACP is added, which specifies the customer and service provider availability based on the access control for the whole service session. The distributed design of ledger structures and tree learning classification is combined to defined unattended access. The unattended data access is processed through a communication layer in which blockchain processing is validated between consumers and service providers.
To defined unattended access, the distributed design of ledger structures and tree learning classification is combined. Closed, free access requests, and integrity checks conducted by the service provider are integrated as unattended access. Both facilities’ meetings at the proposed SACP are subject to access control by determining its customers’ supply. The distributed architecture of the ledger structures and classification tree learning are combined to detect unattended entry. Unattended access will be known as closed and open access requests in which service providers perform the integrity checks. By blockchain processing, the un-attended data access is obtained between users and service provider availability. In this paper, four types of blockchain processing are accepted, and the following Eq. (1) is used to evaluate the status of the request as processing or not.

The analysis is calculated in (1), where an authorized user is provided with the blockchain upgrade permission by processing the above Equation. Data processing is based on the allotted time, which is seen as T when referred to ask, is observed. The analysis is called A and is determined for the individual facility. The service is termed as 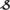 , and the processing server is represented as
, and the processing server is represented as  . The service to the requested user is denoted as
. The service to the requested user is denoted as 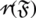 .
.
It is obtained by deriving  in this; the data is denoted as
in this; the data is denoted as  are acquired in blockchain
are acquired in blockchain  . Here the blockchain is evaluated to observe the service at the appropriate time and finds the data are processed or not, which is represented as
. Here the blockchain is evaluated to observe the service at the appropriate time and finds the data are processed or not, which is represented as  . In this, the access is provided if the user completes the processing, access is termed as
. In this, the access is provided if the user completes the processing, access is termed as 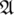 , if the process is not processed means the response is not derived, which is defined as
, if the process is not processed means the response is not derived, which is defined as  . If the process is not available, the malicious user accesses the service that is denoted as
. If the process is not available, the malicious user accesses the service that is denoted as  . Based on this, the blockchain assessment for the request-response is obtained by evaluating the below Eq. (2).
. Based on this, the blockchain assessment for the request-response is obtained by evaluating the below Eq. (2).

The blockchain is processed by evaluating the above Eq. (2) that is determined as  in this; the data are monitored that is represented as
in this; the data are monitored that is represented as 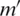 . Here the user’s identity and transaction are stored for every transaction, referred to as
. Here the user’s identity and transaction are stored for every transaction, referred to as  and
and  where it processes in the allocated time. Thus, by computing
where it processes in the allocated time. Thus, by computing  in this, the services are requested to the user where the transaction is observed in the given time interval. By estimating the Blockchain process, the user’s request and response are calculated below Eq. (3).
in this, the services are requested to the user where the transaction is observed in the given time interval. By estimating the Blockchain process, the user’s request and response are calculated below Eq. (3).

The evaluation of request and response is determined in the above Eq. (3), in this  The time-based services are provided to the requested user. The data transfers can be reviewed blockchain if the user finishes the server process. Blockchain tracks the integrity of the data by processing it. It is accessed on the customer’s side and provides the user with the service if the operation is complete. The following Eq. (4) is formulated to obtain the verification phase of blockchain to the user and process the services between server and user.
The time-based services are provided to the requested user. The data transfers can be reviewed blockchain if the user finishes the server process. Blockchain tracks the integrity of the data by processing it. It is accessed on the customer’s side and provides the user with the service if the operation is complete. The following Eq. (4) is formulated to obtain the verification phase of blockchain to the user and process the services between server and user.

The authentication is used from the customer side to track the current service once it is processed by supplying access from the server to potential requests. This search is evaluated as X to allow legitimate user access to the unprocessed service’s processing service. This allows the blockchain to verify and upgrade data between users and servers. The checking and updating phase of the request is seen in Figs. 2a and 2b in this paragraph.

Figure 2: (a) Request state verification, (b) update process
In this, classification is used to determine the request’s status, service provider validity, and integrity check. The observation is determined by rewriting Eqs. (3) and (4) to obtain a verified evaluation in the below Eq. (5). The requested customer provides time-based services based on the connectivity structure. If the user finishes the server process, data transactions can be checked in the blockchain. By processing it, blockchain monitors the quality of the data. After the process has been finished, the client reaches it and provides the user with the service. The blockchain testing stage is configured for the user, and the services between the application and the user are handled.

By rewriting the above Eq. (5) is extracted in this, the verification phase is evaluated for the Blockchain update, denoted as  . In this Eq. (5), three types of derivation are determined for the classification of services on the server-side. It is determined as
. In this Eq. (5), three types of derivation are determined for the classification of services on the server-side. It is determined as  in this non-processed data are monitored and protects the services from a malicious user that is represented
in this non-processed data are monitored and protects the services from a malicious user that is represented  , and the number of users is denoted as
, and the number of users is denoted as  . Thus,
. Thus,  In this processing are evaluated where it is computed in the allocated time interval. In Tab. 1, the service dissemination ratio for different requests, as observed, is presented. The authentication is used to monitor the existing service from the customer’s side, in which the service offers access to potential applications from the server. This search is evaluated as X, allowing legitimate users to enter the unprocessed service. The blockchain enables data between users and servers to be reviewed and updated. This figure indicates the check-up and upgrade process of the order. In that subsection, Figs. 2a and 2b.
In this processing are evaluated where it is computed in the allocated time interval. In Tab. 1, the service dissemination ratio for different requests, as observed, is presented. The authentication is used to monitor the existing service from the customer’s side, in which the service offers access to potential applications from the server. This search is evaluated as X, allowing legitimate users to enter the unprocessed service. The blockchain enables data between users and servers to be reviewed and updated. This figure indicates the check-up and upgrade process of the order. In that subsection, Figs. 2a and 2b.
Table 1: Service dissemination ratio for different requests

Here, by evaluating  . This integrity is used to obtain the processes based on blockchain, and it determines the data that indicates the processing and non-processing data. The classification is based on three derivations. They are associated with the request’s progress or not, which is evaluated based on four service determinations between the user and the server. Thus, classification is considered to obtain the resultant data on the server-side.
. This integrity is used to obtain the processes based on blockchain, and it determines the data that indicates the processing and non-processing data. The classification is based on three derivations. They are associated with the request’s progress or not, which is evaluated based on four service determinations between the user and the server. Thus, classification is considered to obtain the resultant data on the server-side.
3 Classification Process in SACP
The classification is obtained to process unattended access associated with the service is open or close that represents the request received from the server. By processing, this open and close state of demand is determined, and it finds the malicious user and avoids the signs of progress in the cloud application service. The classification is obtained to provide access to the user or not, which is based on the blockchain update, and the following Eq. (6) is used to represents the classification based on requests.

The classification is evaluated as  , based on a request from the server and processes the service for the end-user in the cloud environment, represented in the above Eq. (6). The designation is obtained to process the unattended access associated with the server request’s opening or closing. This state of demand is calculated by processing, and the malicious user is detected, and signs of improvement in the cloud application service are stopped. This is collected to grant the user permission or not, depending on the blockchain update and the accompanying Eq. (6), the grouping is used based on queries.
, based on a request from the server and processes the service for the end-user in the cloud environment, represented in the above Eq. (6). The designation is obtained to process the unattended access associated with the server request’s opening or closing. This state of demand is calculated by processing, and the malicious user is detected, and signs of improvement in the cloud application service are stopped. This is collected to grant the user permission or not, depending on the blockchain update and the accompanying Eq. (6), the grouping is used based on queries.
By computing  the response is obtained from the user. If the request is closed (non-processed), the request from the user is accessed. If not, the access is denied, and evaluation is obtained from the blockchain. This evaluation consists of the transaction and identity of the user. The update is computed based on the service that is already processed, and it makes an easy evaluation at the time of providing access to the particular service. Thus, the following Eq. (7) is used to obtain the ‘if and else’ condition to receive the open (processed) and closed (non-processed) data.
the response is obtained from the user. If the request is closed (non-processed), the request from the user is accessed. If not, the access is denied, and evaluation is obtained from the blockchain. This evaluation consists of the transaction and identity of the user. The update is computed based on the service that is already processed, and it makes an easy evaluation at the time of providing access to the particular service. Thus, the following Eq. (7) is used to obtain the ‘if and else’ condition to receive the open (processed) and closed (non-processed) data.

The request is determined to obtain the service is an open or close state based on this the above Eq. (7) is derived, in this the ‘if condition’ are associated by computing  here, the progressed data are obtained. The second else condition satisfies the closed data service on the server-side. If it is an open service and the server’s requests to access the other task, the server obtains the blockchain’s information. The additional constraint is based on the service is closed on the user side, and its request for the service on the server-side verifies whether service is processed, which is done by processing integrity check. The following Eq. (8) is used to obtain the processed data.
here, the progressed data are obtained. The second else condition satisfies the closed data service on the server-side. If it is an open service and the server’s requests to access the other task, the server obtains the blockchain’s information. The additional constraint is based on the service is closed on the user side, and its request for the service on the server-side verifies whether service is processed, which is done by processing integrity check. The following Eq. (8) is used to obtain the processed data.

In the above Eq. (8), the processed and non-processed service is obtained; here, the processed are used to deploy the server’s service and determine access to process the upcoming task. It is derived to achieve the data progressing when the verification is acquired from the blockchain. In non-progressing, the integrity check is necessary to provide access to the user based on updating the above Eq. (7). Here the evaluating is termed to obtain the integrity check to avoid access from the malicious user, and it is computed by representing  . In this scenario, the unattended access is computed to obtain permission from the server. This is provided according to the open and close status of the request. Figs. 3a and 3b presents the classification and processing of requests/response.
. In this scenario, the unattended access is computed to obtain permission from the server. This is provided according to the open and close status of the request. Figs. 3a and 3b presents the classification and processing of requests/response.

Figure 3: (a) Classification of requests, (b) processing of requests
Here the permission is allowed if the update in the blockchain is processed correctly. The precise processing includes the time and what type of access is used to process the services. If a user requests access to the server and back, the server checks the last transaction in the blockchain and provides the necessary access.
The classification is assessed under C, based on a server request, and processes the end-user service in the cloud context, as seen in the above Eq. (6). The answer is obtained from the consumer, which is closed (not processed), based on the user’s request. Further, the blockchain will reject entry and test it. The transaction and identity of the customer is the test based on the validation factor. Post to this request process, the four different categories are obtained to evaluate the service-based access control. The status of the closed or no-update of the service determines the first stage of processing. It is due to the inactive server and is computed as

The evaluation is based on determining the above Eq. (9) if the service is closed and its user request. At that time, the server is not active that is denoted as i0 the access is not provided to the user here; the synchronization of time is evaluated. In this case, the blockchain update is not progressed. The second processing represents if the service is closed and the blockchain is updated. According to this, the integrity check is estimated by computing the below Eq. (10). Further, the processed and unprocessed data is obtained, in which the processed service is used to deploy the server to create access for the next task. Data advancing is accessed from the blockchain, which is extracted. In the case of non-progress, a completeness check is required to provide the user with access.

The integrity check is evaluated using the above Eq. (10). If the service is progressed, a blockchain update is carried out, and an integrity check proceeds. In this service-based access is obtained to the requested user in an allocated time interval. Thus, the third process includes whether the service is not progressed and the blockchain is analyzed based on the data’s malicious user access. It is evaluated in the below Eq. (11).

If the service is not processed and at the same time the blockchain and server are closed, then the update is not deployed. In this manner, by determining  the malicious user accesses the service is analyzed based on active state of blockchain, and the server is observed. They are determined by computing the process in the mentioned time interval for non-processed requests from the user to provide access from the server. The fourth evaluation represents if the user is malicious and requests the server’s service, which is derived by calculating the below Eq. (12).
the malicious user accesses the service is analyzed based on active state of blockchain, and the server is observed. They are determined by computing the process in the mentioned time interval for non-processed requests from the user to provide access from the server. The fourth evaluation represents if the user is malicious and requests the server’s service, which is derived by calculating the below Eq. (12).

The above Eq. (12) is determined by  here if the blockchain and server are open to provide the service to the user. If the user is progressed, the response is obtained from the server else; it is denied denoted as
here if the blockchain and server are open to provide the service to the user. If the user is progressed, the response is obtained from the server else; it is denied denoted as  . It is determined if the malicious user sent the request for a new service that is termed as ns and the server checks the previous process is not completed. The service is not provided to the user, and thus the classification is observed based on time. Based on the objective, the service disconnection is decreased by formulating the below Eq. (13).
. It is determined if the malicious user sent the request for a new service that is termed as ns and the server checks the previous process is not completed. The service is not provided to the user, and thus the classification is observed based on time. Based on the objective, the service disconnection is decreased by formulating the below Eq. (13).

The service is obtained by calculating the above Eq. (13) where the service disconnection is addressed and decreased by deriving  . If the server obtains the user’s request, it is verified to classify processed or non-processed data. In this manner, by computing
. If the server obtains the user’s request, it is verified to classify processed or non-processed data. In this manner, by computing  . The new service is provided to the user based on the Blockchain verification. The other constrain is to reduce the false access rate that avoids the malicious user in the cloud environment, and it is represented in the following Eq. (14).
. The new service is provided to the user based on the Blockchain verification. The other constrain is to reduce the false access rate that avoids the malicious user in the cloud environment, and it is represented in the following Eq. (14).

In the above Eq. (14), the false access rate is reduced that is derived as  where two types of conditions are evaluated. The first derivative is computed as
where two types of conditions are evaluated. The first derivative is computed as  in this, the Blockchain update is processed and monitors the identity of the user. In Tabs. 2 and 3, the disconnection ratio observed for different requests, and data processed is summarized.
in this, the Blockchain update is processed and monitors the identity of the user. In Tabs. 2 and 3, the disconnection ratio observed for different requests, and data processed is summarized.
Table 2: Disconnection ratio for requests
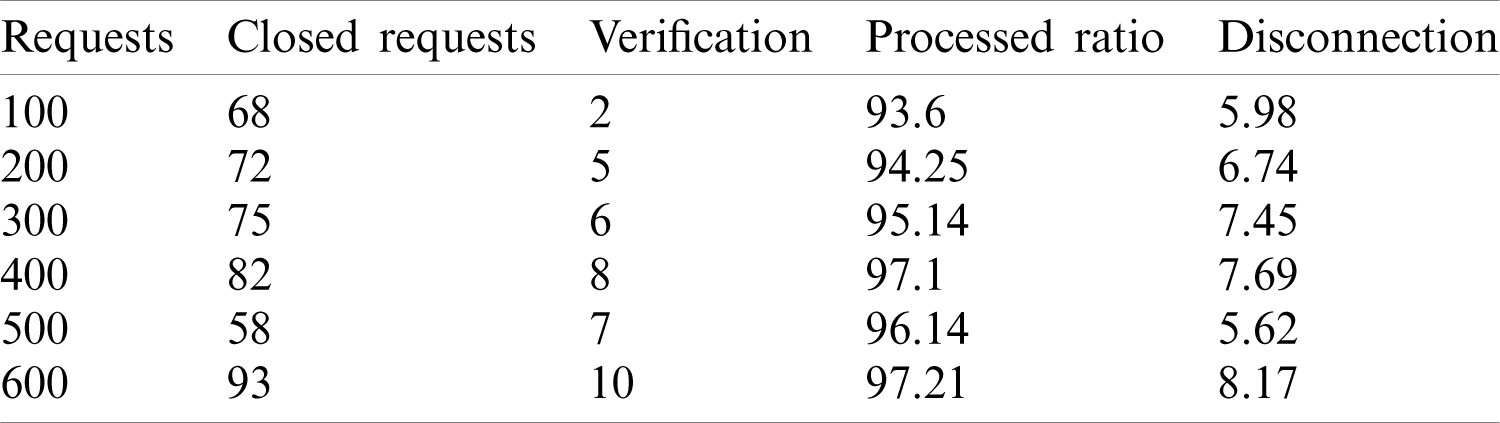
Table 3: Disconnection ratio for data processed

Here, the processing is evaluated in the allocated time, and it satisfies the objective. In contrast, the second derivations are analyzed, and it does not help because the timely processes are not computed. Fig. 4 shows the overall operation of the SACP after classification.
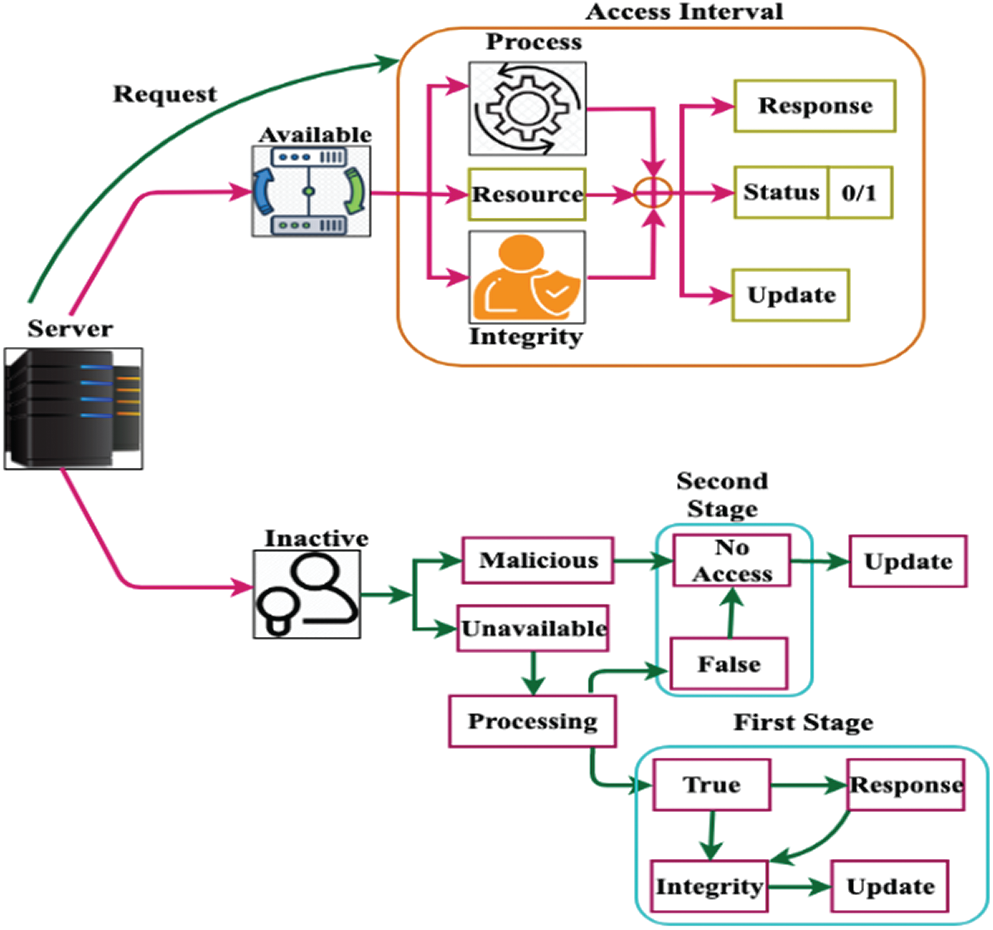
Figure 4: Post classification process
The proposed work’s objective is evaluated by computing the above two Eqs. (13) and (14) in this, the service disconnection and false access rates are decreased. By assessing this, it improves the service access control between the user request and server response. Here, the blockchain is updated for every processing and verifies the request is processed or non-processed service. In this method, the legitimate user receives access control, determined by the determination of the security-based service access control. It requires the customer’s identity and past operation that provides the requesting user with prompt data recovery. The details and access vary with each transaction; the time associated with the data collection and retrieval data shall be calculated according to the time.
This section briefs the assessment of the proposed SACP using a precise experimental setup. In the experimental design, 60 end-user devices are deployed for sharing resources from a cloud server. The maximum request is 600 for retrieving information from the storage of size 1 TB. The classification and verification instances are set as 50 and 10, respectively. In this process, two blockchain security servers are deployed to track the requests and perform periodic updates regarding resource and service response availability. For verifying the reliability of the proposed method, the performance is verified using the metrics false access rate, disconnection ratio, computation overhead, and access delay. In this verification process, the methods SBAC, BaCS, and BDSS are considered for comparative analysis.
In Figs. 5a and 5b, a false access rate is determined concerning several user requests and the service provided. It is observed by calculating the processing based on a timely manner, and it is defined as  . The request is sent to the server based on the processing and non-processing service. The response is provided. The service provider verifies the user service, and based on this; the Blockchain processing is evaluated by obtaining
. The request is sent to the server based on the processing and non-processing service. The response is provided. The service provider verifies the user service, and based on this; the Blockchain processing is evaluated by obtaining  . The access is provided for the user if the previous services are completed in another case; if the service is not met, still processing the blockchain update is not performed. The Blockchain stores the user identity and transaction of the user, which is denoted as
. The access is provided for the user if the previous services are completed in another case; if the service is not met, still processing the blockchain update is not performed. The Blockchain stores the user identity and transaction of the user, which is denoted as  . Here the access control varies by processing the request and provides the response to it and manages the services, so the false access is lesser.
. Here the access control varies by processing the request and provides the response to it and manages the services, so the false access is lesser.
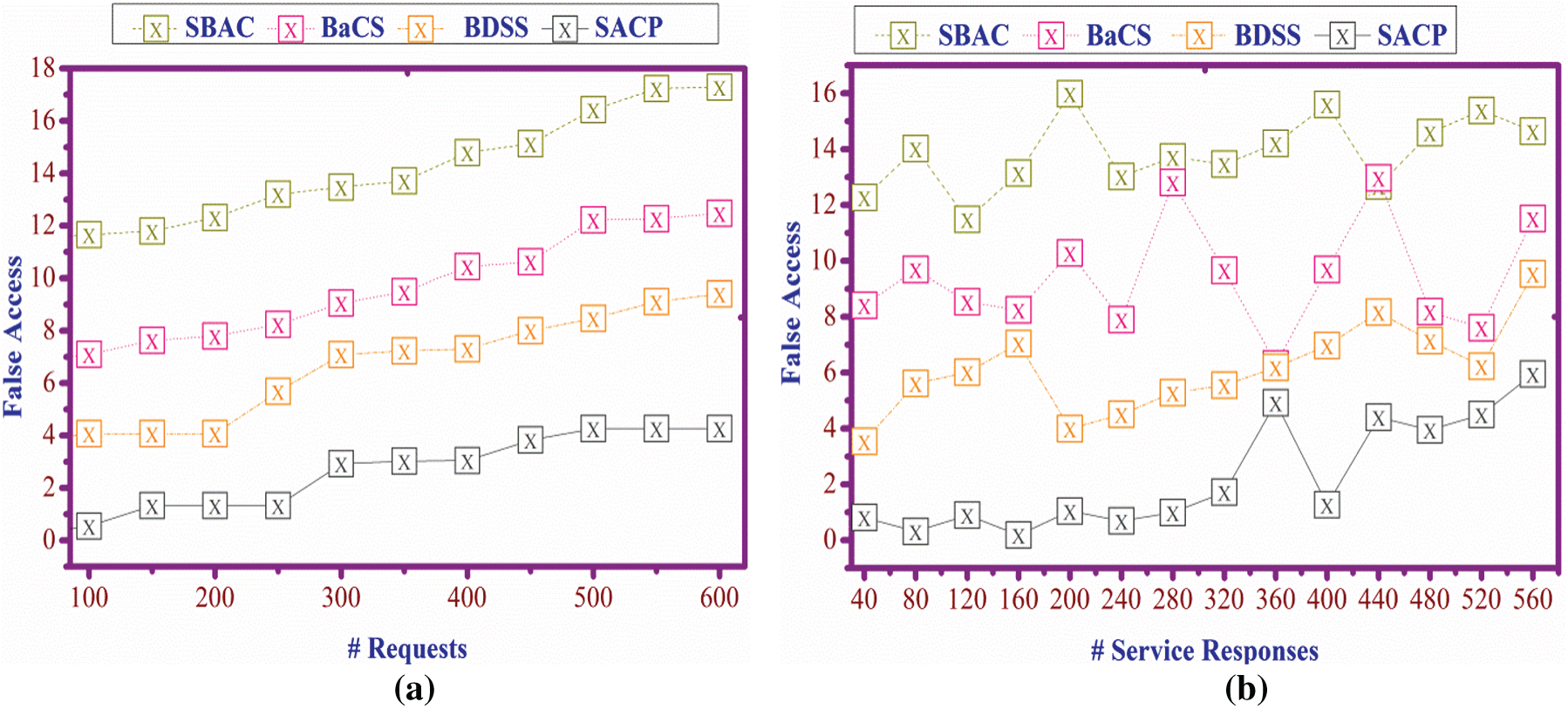
Figure 5: (a) False access rate for requests, (b) service responses
Service disconnection is decreased in the proposed method, and it is compared with the current work. Here it is determined by computing  in this, the analysis is evaluated by providing the processing and non-processing data. It is based on the update of blockchain, and it determines the service from the user. The verification phase is evaluated for the blockchain update that includes the service from the user. Based on this, the processing is observed by deriving the time. The time is followed by formulating
in this, the analysis is evaluated by providing the processing and non-processing data. It is based on the update of blockchain, and it determines the service from the user. The verification phase is evaluated for the blockchain update that includes the service from the user. Based on this, the processing is observed by deriving the time. The time is followed by formulating  in this service request and responses are acquired at the appropriate time. By processing this, it verifies whether the data are processing is not, which is associated with evaluating the service is open or closed. The representation of use and its access is computed by
in this service request and responses are acquired at the appropriate time. By processing this, it verifies whether the data are processing is not, which is associated with evaluating the service is open or closed. The representation of use and its access is computed by 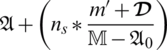 . The new service is requested from the user and checks whether the service is open; it is not allocated if it is open. If the service is closed, the service is provided to the user, and it protects from malicious user access [Refer to Figs. 6a and 6b].
. The new service is requested from the user and checks whether the service is open; it is not allocated if it is open. If the service is closed, the service is provided to the user, and it protects from malicious user access [Refer to Figs. 6a and 6b].
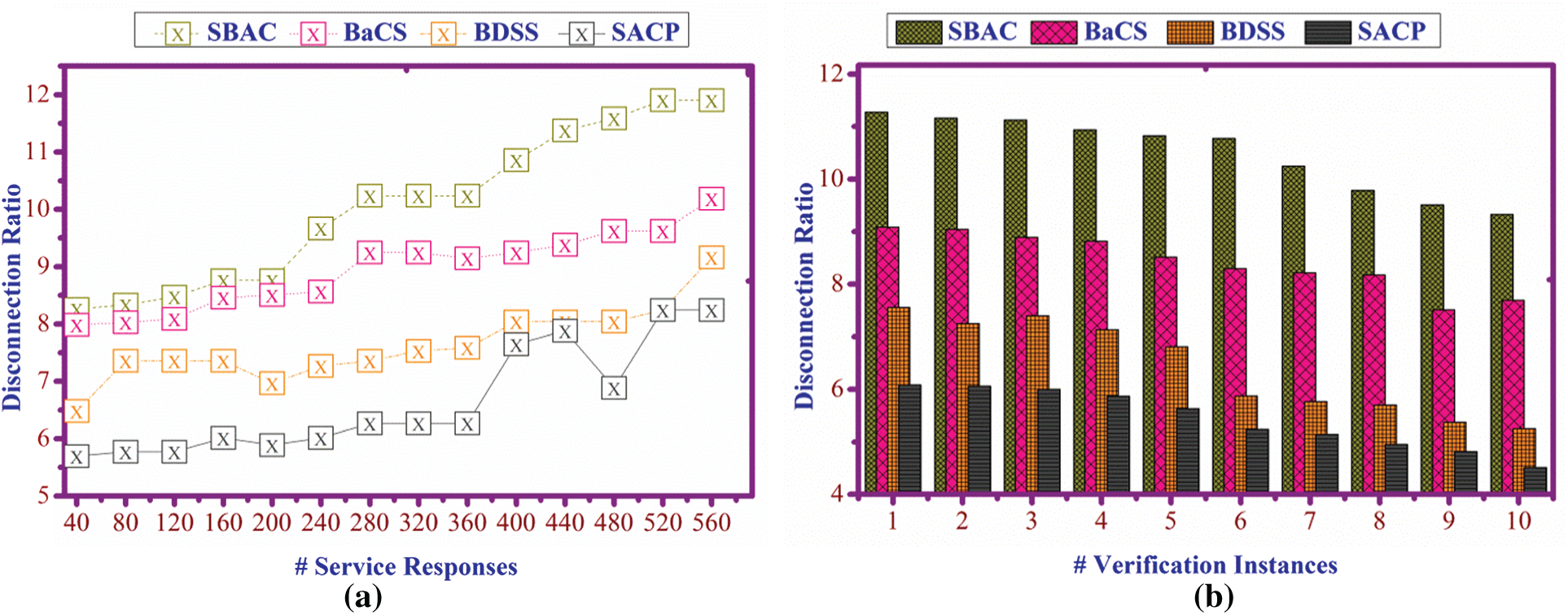
Figure 6: (a) Disconnection ratio for service responses, (b) verification instances
The computation overhead shows the lesser value, and it is represented in Figs. 7a and 7b, where it is obtained by evaluating 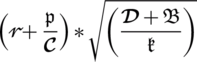 . The processing is determined based on the classification processing, where the data are processed in the blockchain. The processing of data is observed in the appropriate time interval, and thus it computes the request from the user and provides the service. The computations are obtained by deriving the data based on time, and it evaluates the request from the user. It is processed for the number of claims and verification instances in specific applications. They are obtained by determining
. The processing is determined based on the classification processing, where the data are processed in the blockchain. The processing of data is observed in the appropriate time interval, and thus it computes the request from the user and provides the service. The computations are obtained by deriving the data based on time, and it evaluates the request from the user. It is processed for the number of claims and verification instances in specific applications. They are obtained by determining  In this, the request and response are computed if they are inactive servers. If the server is idle, the processing is evaluated based on the new service to the requested user. The verification instances are acquired by processing the request and assess the overheads, and it is represented as
In this, the request and response are computed if they are inactive servers. If the server is idle, the processing is evaluated based on the new service to the requested user. The verification instances are acquired by processing the request and assess the overheads, and it is represented as  . Thus, the analysis is provided for the update of blockchain.
. Thus, the analysis is provided for the update of blockchain.
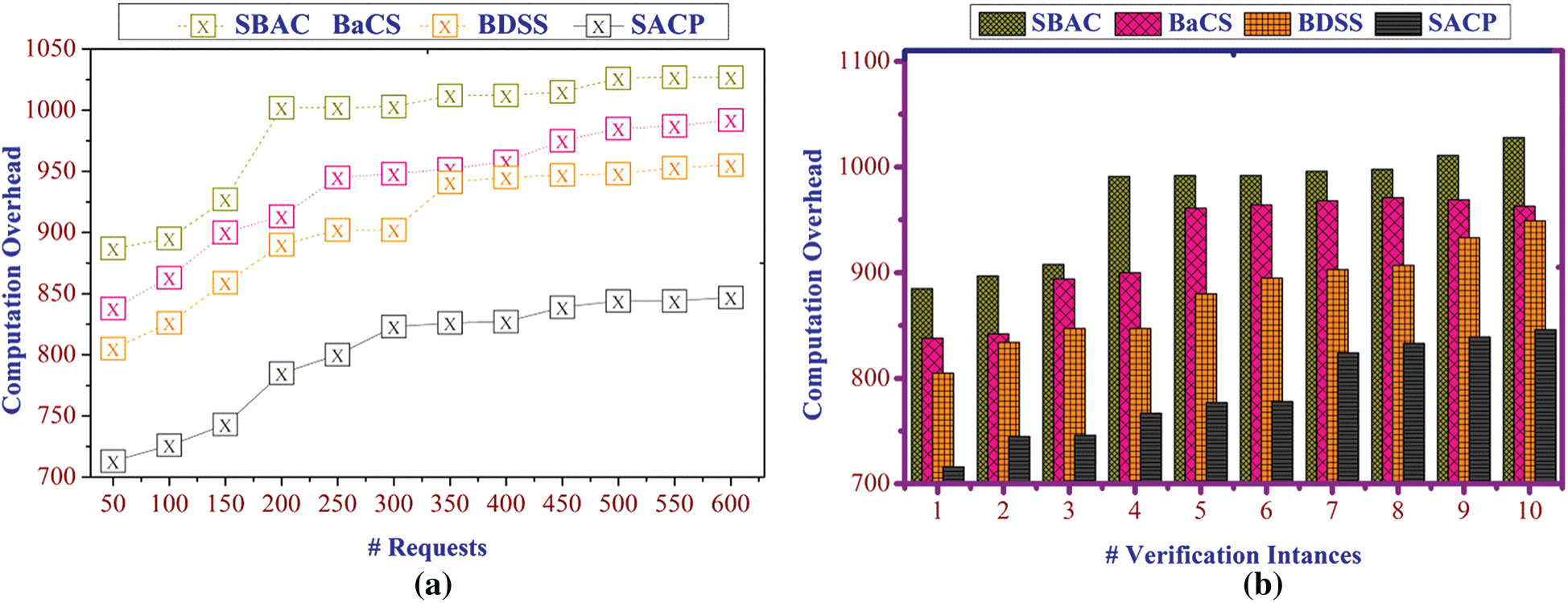
Figure 7: (a) Computation overhead for requests, (b) verification instances
In Fig. 8, the access delay is found to be less on comparing it with the other three methods, and it is formulated by  . Here, the evaluation is processed for the number of users and the data requested. It is evaluated if the request from the user decreases, the access delay also decreases, and it is represented as
. Here, the evaluation is processed for the number of users and the data requested. It is evaluated if the request from the user decreases, the access delay also decreases, and it is represented as  . The identification and transaction of the user are acquired in the blockchain are obtains the resultant data. So, the verification is evaluated in the blockchain, which acts as the updated medium between server and user. Thus, the user requests special access, and the response is provided to the server’s user. By formulating
. The identification and transaction of the user are acquired in the blockchain are obtains the resultant data. So, the verification is evaluated in the blockchain, which acts as the updated medium between server and user. Thus, the user requests special access, and the response is provided to the server’s user. By formulating  the integrity checks are defined, and they are associated with the request, and responses are obtained sequentially. In Tabs. 4a–4c, the comparative study results are summarized.
the integrity checks are defined, and they are associated with the request, and responses are obtained sequentially. In Tabs. 4a–4c, the comparative study results are summarized.
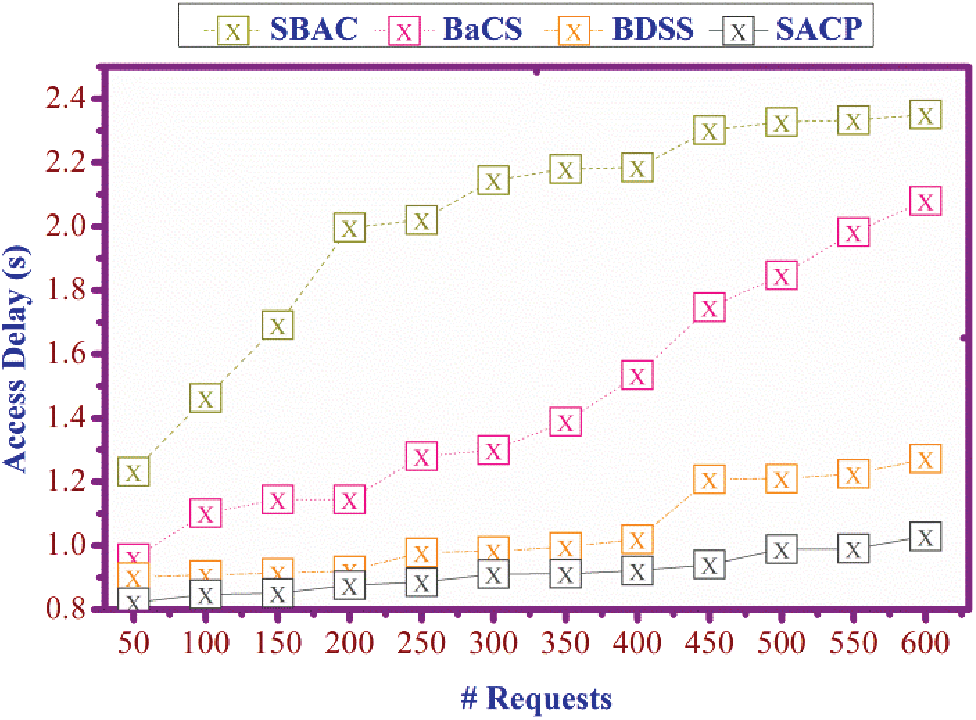
Figure 8: Access delay
Table 4: (a) Comparative study for requests, (b) comparative study for service responses, (c) comparative study for verification instances

In Fig. 9, request and response rates are determined, and it provides the service for the requested user based on Blockchain update. It is processed by  The processing and non-processing are obtained. Thus, the request-response rate increases for ten verifications rates by comparing it with a single verification confirmation based on the access control method. Based on the observation from Figs. 8 and 9, the user’s identity and transaction are retrieved with the resulting data in the blockchain. The authentication is analyzed as a modified medium between server and user in the blockchain. Therefore, users seek specific access, and the user from the server receives the response.
The processing and non-processing are obtained. Thus, the request-response rate increases for ten verifications rates by comparing it with a single verification confirmation based on the access control method. Based on the observation from Figs. 8 and 9, the user’s identity and transaction are retrieved with the resulting data in the blockchain. The authentication is analyzed as a modified medium between server and user in the blockchain. Therefore, users seek specific access, and the user from the server receives the response.
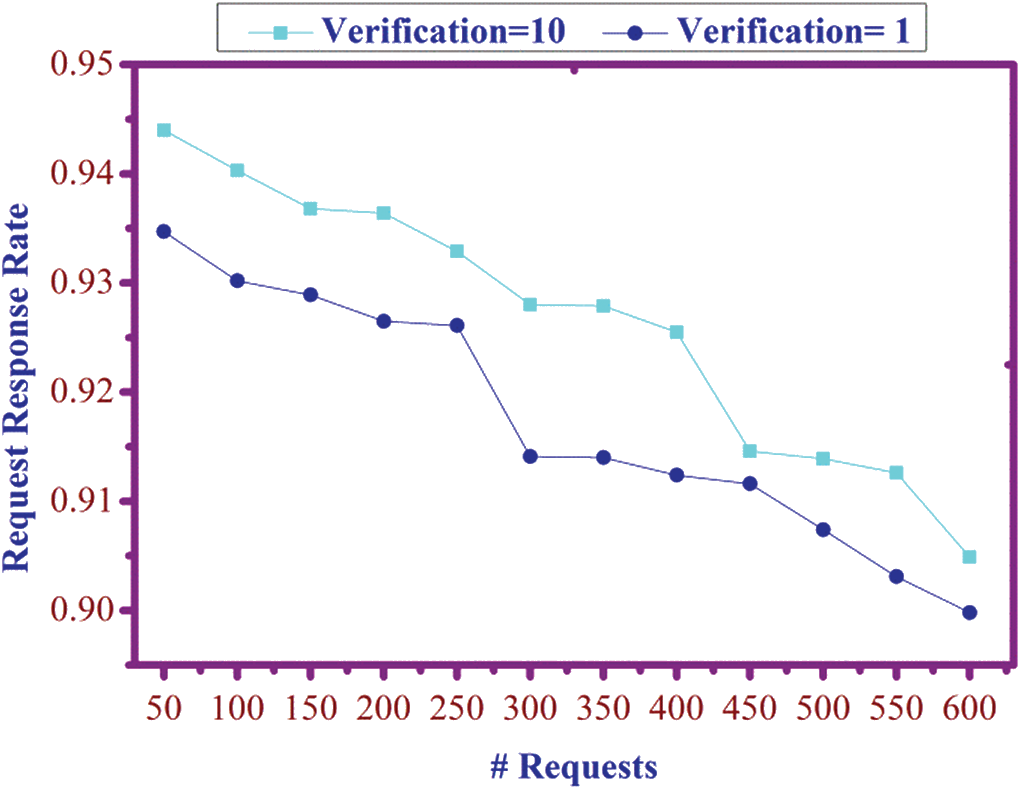
Figure 9: Response rate for  and 10
and 10
The classifications of the proposed work are determined for processing ratio, and it is formulated by  . It determines the access for the analyzed user, the evaluation and no evaluation states are derived here. Thus, the processing ratio for the assessment is higher than the no evaluations (Fig. 10a). The user access rate is determined for the service disconnection ratio and classification process. The access rate increases by processing the service disconnection, and it shows better improvement by evaluating the classification and processing ratio of data. Comparing with the above two evaluations determines more improvement by evaluating classification, processing, and integrity (Fig. 10b).
. It determines the access for the analyzed user, the evaluation and no evaluation states are derived here. Thus, the processing ratio for the assessment is higher than the no evaluations (Fig. 10a). The user access rate is determined for the service disconnection ratio and classification process. The access rate increases by processing the service disconnection, and it shows better improvement by evaluating the classification and processing ratio of data. Comparing with the above two evaluations determines more improvement by evaluating classification, processing, and integrity (Fig. 10b).
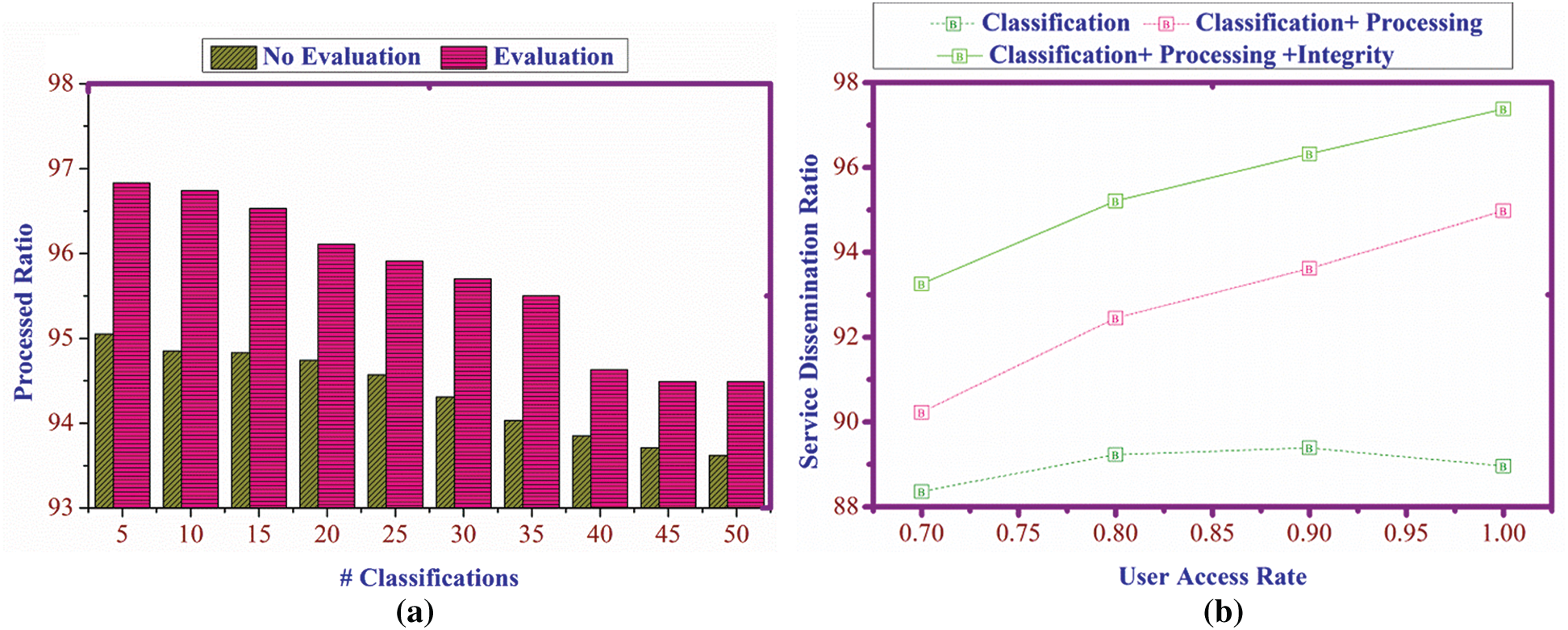
Figure 10: (a) Processed ratio for classifications, (b) service dissemination ratio for access
This article discusses a service-aware access control procedure for reducing cloud services’ false access rate by administering the blockchain paradigm. In this procedure, blockchain performs request-response tracking and update processes to minimize the impact of incorrect resource access. The status of the request and the server availability are updated in the blockchain for further access. For easing the update, classification learning is used to identify the different status of the requests. Data processing and integrity check validations between the service provider and end-user application are the augmenting factors for improving users’ access control. This process reduces unattended access, and the service dissemination ratio of 97.5% is improved. The experimental assessment shows that the proposed SACP enhances service access reliability by reducing false access, service disconnection, computation overhead, and access delay. In the future, learning-based algorithms are processed, which helps to improve the reliability of the network.
Funding Statement: This work was supported by the Deanship of Scientific Research (DSR), King Abdulaziz University, Jeddah, under Grant No. (DF-444-611-1441). The author, therefore, gratefully acknowledge DSR technical and financial support.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. L. Tan, N. Shi, S. Yang and K. Yu. (2020). “A blockchain-based access control framework for cyber-physical-social system big data,” IEEE Access, vol. 8, pp. 77215–77226. [Google Scholar]
2. C. Lin, D. He, X. Huang, K. K. R. Choo and A. V. Vasilakos. (2018). “BSeIn: A blockchain-based secure mutual authentication with fine-grained access control system for industry 4.0,” Journal of Network and Computer Applications, vol. 116, pp. 42–52. [Google Scholar]
3. G. Zhang, T. Li, Y. Li, P. Hui and D. Jin. (2018). “Blockchain-based data sharing system for AI-powered network operations,” Journal of Communications and Information Networks, vol. 3, no. 3, pp. 1–8. [Google Scholar]
4. A. Prathik, K. Uma and J. Anuradha. (2016). “Particulate matter on human health and their feasibility study using machine learning algorithms,” Journal of Chemical and Pharmaceutical Research, vol. 8, no. 9, pp. 260–264. [Google Scholar]
5. J. Guo, C. Li, G. Zhang, Y. Sun and R. Bie. (2019). “Blockchain-enabled digital rights management for multimedia resources of online education,” Multimedia Tools and Applications, vol. 79, no. 15–16, pp. 9735–9755. [Google Scholar]
6. H. Zhao, P. Bai, Y. Peng and R. Xu. (2018). “Efficient key management scheme for health blockchain,” CAAI Transactions on Intelligence Technology, vol. 3, no. 2, pp. 114–118. [Google Scholar]
7. Y. Wang, A. Zhang, P. Zhang and H. Wang. (2019). “Cloud-assisted EHR sharing with security and privacy preservation via consortium blockchain,” IEEE Access, vol. 7, pp. 136704–136719. [Google Scholar]
8. P. F. Sheron, K. P. Sridhar, S. Baskar and P. M. Shakeel. (2019). “A decentralized scalable security framework for end-to-end authentication of future IoT communication,” Transactions on Emerging Telecommunications Technologies, vol. 31, no. 12, pp. e3815. [Google Scholar]
9. R. M. Alguliyev, R. M. Aliguliyev and L. V. Sukhostat. (2020). “Efficient algorithm for big data clustering on single machine,” CAAI Transactions on Intelligence Technology, vol. 5, no. 1, pp. 9–14. [Google Scholar]
10. J. Sun, K. Yao, S. Wang and Y. Wu. (2020). “Blockchain-based secure storage and access scheme for electronic medical records in IPFS,” IEEE Access, vol. 8, pp. 59389–59401. [Google Scholar]
11. S. S. L. Preeth, R. Dhanalakshmi and P. M. Shakeel. (2019). “An intelligent approach for energy efficient trajectory design for mobile sink based IoT supported wireless sensor networks,” Peer-to-Peer Networking and Applications, vol. 13, no. 6, pp. 2011–2022. [Google Scholar]
12. Y. Chen, S. Chen, J. Liang, L. W. Feagan, W. Han et al. (2020). , “Decentralized data access control over consortium blockchains,” Information Systems, vol. 94, pp. 101590. [Google Scholar]
13. D. D. F. Maesa, P. Mori and L. Ricci. (2019). “A blockchain based approach for the definition of auditable access control systems,” Computers & Security, vol. 84, pp. 93–119. [Google Scholar]
14. Y. Cao, F. Jia and G. Manogaran. (2019). “Efficient traceability systems of steel products using blockchain-based industrial internet of things,” IEEE Transactions on Industrial Informatics, vol. 16, no. 9, pp. 6004–6012. [Google Scholar]
15. M. Y. Khan, M. F. Zuhairi, T. Ali, T. Alghamdi and J. A. Marmolejo-Saucedo. (2019). “An extended access control model for permissioned blockchain frameworks,” Wireless Networks, pp. 1–12. [Google Scholar]
16. Y. Maleh, M. Shojafar, M. Alazab and I. Romdhani (Eds.). (2019). Blockchain for cybersecurity and privacy: Architectures, challenges, and applications. CRC Press. [Google Scholar]
17. T. Cai, Z. Yang, W. Chen, Z. Zheng and Y. Yu. (2020). “A blockchain-assisted trust access authentication system for solid,” IEEE Access, vol. 8, pp. 71605–71616. [Google Scholar]
18. M. Ma, G. Shi and F. Li. (2019). “Privacy-oriented blockchain-based distributed key management architecture for hierarchical access control in the IoT scenario,” IEEE Access, vol. 7, pp. 34045–34059. [Google Scholar]
19. G. Ali, N. Ahmad, Y. Cao, Q. E. Ali, F. Azim et al. (2019). , “BCON: Blockchain based access control across multiple conflict of interest domains,” Journal of Network and Computer Applications, vol. 147, pp. 102440. [Google Scholar]
20. G. Gürsoy, R. Bjornson, M. E. Green and M. Gerstein. (2020). “Using blockchain to log genome dataset access: Efficient storage and query,” BMC Medical Genomics, vol. 13, no. 7. [Google Scholar]
21. G. G. Dagher, J. Mohler, M. Milojkovic and P. B. Marella. (2018). “Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology,” Sustainable Cities and Society, vol. 39, pp. 283–297. [Google Scholar]
22. B. Liu, L. Xiao, J. Long, M. Tang and O. Hosam. (2020). “Secure digital certificate-based data access control scheme in blockchain,” IEEE Access, vol. 8, pp. 91751–91760. [Google Scholar]
23. S. Ding, J. Cao, C. Li, K. Fan and H. Li. (2019). “A novel attribute-based access control scheme using blockchain for IoT,” IEEE Access, vol. 7, pp. 38431–38441. [Google Scholar]
24. H. Xu, Q. He, X. Li, B. Jiang and K. Qin. (2020). “BDSS-FA: A blockchain-based data security sharing platform with fine-grained access control,” IEEE Access, vol. 8, pp. 87552–87561. [Google Scholar]
25. H. Liu, D. Han and D. Li. (2020). “Fabric-IoT: A blockchain-based access control system in IoT,” IEEE Access, vol. 8, pp. 18207–18218. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |