DOI:10.32604/cmc.2022.020774

| Computers, Materials & Continua DOI:10.32604/cmc.2022.020774 |  |
| Article |
A Secure Key Agreement Scheme for Unmanned Aerial Vehicles-Based Crowd Monitoring System
1Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, Saudi Arabia
2Department of Computer Science and Software Engineering, International Islamic University Islamabad, Pakistan
3Department of Information and Communication Engineering, Yeungnam University, Gyeongsan, 38541, Korea
*Corresponding Author: Muhammad Shafiq. Email: shafiq@ynu.ac.kr
Received: 07 June 2021; Accepted: 16 August 2021
Abstract: Unmanned aerial vehicles (UAVs) have recently attracted widespread attention in civil and commercial applications. For example, UAVs (or drone) technology is increasingly used in crowd monitoring solutions due to its wider air footprint and the ability to capture data in real time. However, due to the open atmosphere, drones can easily be lost or captured by attackers when reporting information to the crowd management center. In addition, the attackers may initiate malicious detection to disrupt the crowd-sensing communication network. Therefore, security and privacy are one of the most significant challenges faced by drones or the Internet of Drones (IoD) that supports the Internet of Things (IoT). In the literature, we can find some authenticated key agreement (AKA) schemes to protect access control between entities involved in the IoD environment. However, the AKA scheme involves many vulnerabilities in terms of security and privacy. In this paper, we propose an enhanced AKA solution for crowd monitoring applications that require secure communication between drones and controlling entities. Our scheme supports key security features, including anti-forgery attacks, and confirms user privacy. The security characteristics of our scheme are analyzed by NS2 simulation and verified by a random oracle model. Our simulation results and proofs show that the proposed scheme sufficiently guarantees the security of crowd-aware communication.
Keywords: IoT; unmanned aerial vehicles; authentication; crowd monitoring
Crowding usually occurs in major occasions, such as international games and sports competitions, cultural festivals, concerts, religious gatherings, etc. We cannot ignore the possibility of accidents in large gatherings, such as the Hajj 2006 or Love Parade 2010 in Germany, and the Kumbh Mela stampede reported in 2013 in the past few years [1,2]. The demand for crowd management solutions in urban metropolises is also becoming more and more common. Such gatherings always have risks, so precautions need to be taken in advance to ensure public safety. In addition, it is also important to use technology to identify anti-social and atypical behaviors in the population, and to distinguish these factors in order to take preventive measures to enhance public safety and security. Recently, the pandemic riot phenomenon needs to perceive crowd behavior without involving human factors, and further requires technological innovation to deal with it. In order to ensure public safety, the administrator or event manager must foresee and check the indicators of real-time data captured from the crowded terrain, and finally make timely decisions to curb unforeseen situations.
In the follow-up of major catastrophic situations such as floods, earthquakes, fire outbreaks, and rescue operations, Unmanned Aerial Vehicles (UAVs) are the first responders. According to observations, surveillance is one of the emerging fields, which has expanded the application range of UAVs (or drones). The sensors in drones help these devices effortlessly expand the scope of mission execution, so they are very suitable for surveillance-based rescue and monitoring operations [3,4]. The drone can focus on their target location and can easily provide the control team with key information about what is happening at that location. The economy of its use and the technological improvement of drones make these devices a strong competitor to improve the safety of surveillance and crowd monitoring operations.
UAVs can help police officers ensure the security and safety of large cities, because these devices can be introduced in real time to collect real-time updates on various actions on the spot. For example, police officers in the United Kingdom use drones to catch suspected robbers [5]. However, it becomes very challenging to manage the efficiency and effectiveness of such monitoring systems in cities. Other agencies such as the US Congress and the US Department of Justice have allowed the use of drones to manage large-scale events in large cities [6]. The combination of drones with multimedia streaming, safe wireless interaction, forensic applications, video detection technology for abnormal motion [7], and video recognition of human abnormal behavior [8] may help to achieve a peaceful living place.
Nevertheless, this development of drone network technology exposes new ways of cyber threats, such as eavesdropping, privacy, forgery, and data reconciliation issues, which makes crowd management very challenging. If any malicious adversary accesses surveillance-related data, it may disrupt the entire surveillance activity. If any legal mobile user wants to access the data collected by a specific drone introduced in the flight area, this must be possible in the follow-up process of the mutual authentication process, leading to an agreed session key. The gateway is a trusted entity that cannot be hacked by opponents, and the mobile user's equipment and drones may be physically compromised. Therefore, designing a secure and lightweight authentication key agreement is essential for the Internet of Drones (IoD) architecture to overcome the above shortcomings.
The salient features of the contribution are as follows:
• We propose a secure key agreement scheme for UAVs-based crowd sensing system. In the proposed scheme, police or intelligence personnel can safely obtain the real-time status of crowd dynamics with mobile devices by using crowd-sensing drones. These drones are used to report the perceived crowd information to the mobile user/police officer (CMDi) through the reliable registration agency GRSj after adopting an appropriate authentication process and using a mutually shared session key. However, this communication must be carried out between legitimate members after using a successful authentication procedure and establishing a mutually agreed session key
• We have verified the session key security of the proposed scheme using the ROR (Real-Or-Random) trusted model [9]. In addition, an informal security analysis was conducted to prove the security function of the proposed schemes against a capable adversary.
• We developed a simulation in NS2 to verify the efficiency of the proposed model in terms of throughput and latency benchmarks. The performance evaluation results show that the proposed scheme is sufficiently safe and efficient in computation and communication.
The rest of this article is organized as follows. Section 2 describes the related work. Section 3 explains the system model and adversary model. Section 4 demonstrates the proposed model. Section 5 analyzes the methods proposed on the formal and informal routes. Section 6 introduces the performance evaluation and comparative study of the proposed models. The conclusion is drawn in the last section.
We can find some research articles on protecting drone-based surveillance [10]. In [11], for example, the authors proposed a UAV communication scheme for rescue operations. In [12], the authors demonstrated the advantages and disadvantages of using drones to monitor the US border. In [13], the authors proposed a security method based on multi-UAV architecture to manage catastrophic scenarios. In [14], the authors discussed equipment for monitoring crowds. In [15], the hierarchical intrusion detection is designed as a lightweight detection and response method to protect drone-based networks from known attacks. Since then, the Time Credential-based Anonymous Lightweight Authentication Scheme (TCALAS) has tried to solve the problems in key protocols related to drone networks. In [16], a certificate-less group key authentication protocol for untrusted drone architecture is proposed. In [17], the authors proposed another lightweight authentication protocol for drone Internet. However, this scheme does not support mutual authentication and so lacks a secure key agreement. In [18], the authors proposed a mobile user authentication protocol for wireless sensor networks related to the Internet-of-Things (IoTs) framework, which establishes an agreed session key with sensor nodes. However, this protocol is particularly suitable for sensor nodes with insufficient resources only and so it uses minimal hash-based operations and XOR operations to support mutual authentication among sensor nodes, mobile users, and gateway server nodes. In [19], authors proved that the scheme in [18] is vulnerable because it does not support anonymity and untraceability. In addition, this solution is susceptible to forgery attacks, stolen card attacks, and man-in-the-middle attacks. In [20], authors proposed a novel and efficient signature-based authentication protocol for IoT-based architecture, in which data is accessed from IoT sensors in real time after a mutual authentication process. However, no solution can meet the goals of real-world online application scenarios to make full use of a secure drone-based crowd sensing system.
There is always a communication security threat between entities in the IoD environment. This requires the development of effective and efficient authentication protocols. The network model of the proposed framework is shown in Fig. 1, including three participating roles, such as control room (CR), ground registration station (GRSj), mobile user (MUi), and crowd monitoring drone (CMDi). The IoD network consists of multiple flight zones with specific identifiers (FZi), and a specific UAV is deployed to any specific FZi, and at the same time it can fly and communicate with other GRSj and drones of the same FZi. GRSj acts as a trusted entity and is connected to the CR endpoint. GRSj registers all mobile users and remote drones by providing long-term keys based on their identity. Mobile user MUi or police officer with smart device obtain is/her own long-term key through GRSj. The drone CMDi introduced in a specific FZi can report to GRSj in real time after scanning and monitoring crowd-based information.
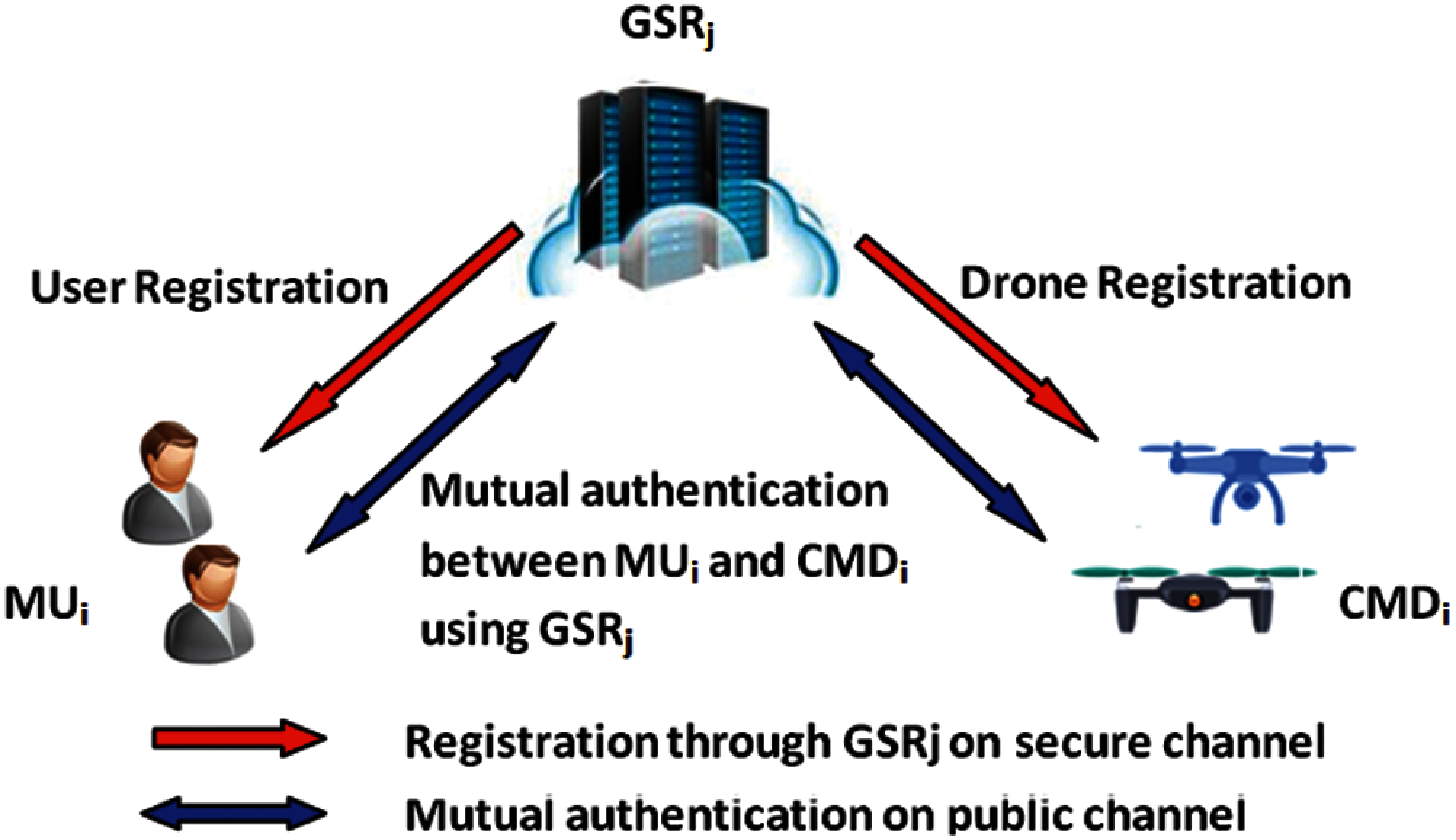
Figure 1: System model
We use the Dolev-Yao (DY) threat model to assume the capabilities of malicious adversaries. Under the DY threat model, adversary
Our proposed scheme consists of three sub-phases, namely the network establishment phase, the MUi registration phase, the CMDi registration phase and the mutual authentication procedure. Before we proceed, we have listed a summary of the symbols used in Tab. 1.
In the network setting, entities in the IoD network are initialized with key secret parameters before deployment on site. First, GRSjconstructs its master secret key and auxiliary parameters required in the protocol, as shown in the following.
• The GRSj selects its 160-bit master secret key KG as well as bit-mask key mk along with a high entropy parameter n.
• The GRSj selects its identity IDGR and calculates PIDG = h(IDGR || mk).
• Next, GRSj stores the parameters (KG, mk) secretly and publicizes the vector (h, n, PIDG).

In the MUi registration phase, the user MUi becomes part of the IoD system through the registration process. GRSj uses confidential channels to perform MUi registration by issuing secret parameters. This stage includes the following steps:
• The MUi chooses its identity IDu and password PWu, and submits the identity IDu as request message for registration towards GRSj.
• Upon the receipt of registration message request from MUi, the GRSj calculates PIDu = h(IDu || k), Bi = h(IDu || KG). Then, it stores the factors {IDu, Bi, PIDu} in its repository, and forwards the message {Bi, PIDu, PIDd} to MUi as shown in Fig. 2.
• The MUi after receiving the message calculates Bi' = h(IDu || PWu) ⊕ Bi, PIDu' = h(IDu || PWu) ⊕ PIDu , and finally stores (Bi’, PIDu’, PIDd) in its memory.
The crowd monitoring drone CMDi registers itself with GRSj and becomes part of the IoD environment. In order to complete the registration, CMDi performs the following steps:
• The CMDi chooses its identity IDd on random basis, and submits the same towards GRSj to initiate the registration process.
• The GRSj, then computes PIDd = h(IDd || k) , Bj = h(IDd || KG) and stores the parameters {IDd, Bj, PIDd} in its repository, and forwards the message {Bj, PIDd} to CMDi.
• The CMDi, ultimately stores the same factors in its memory.
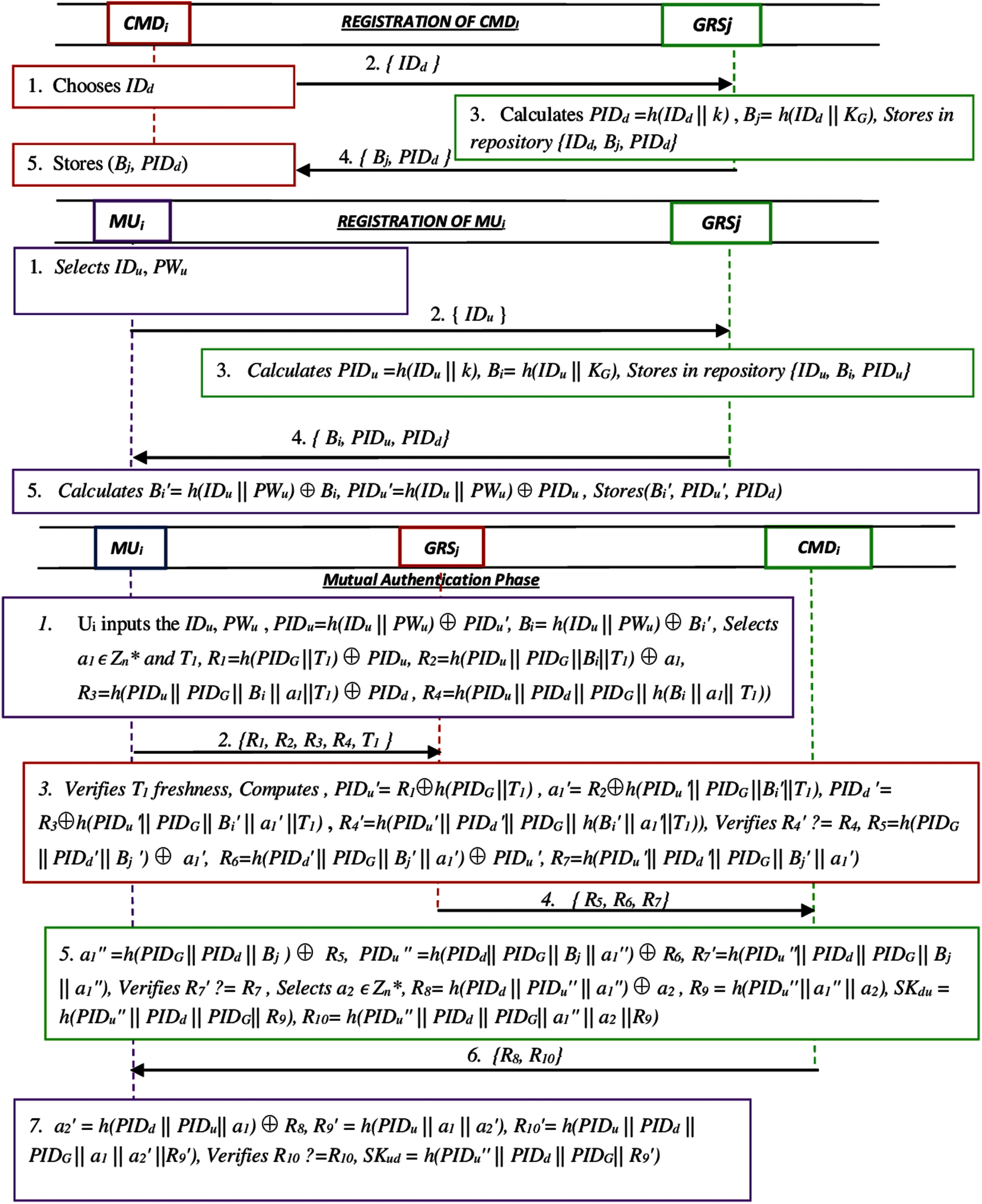
Figure 2: Proposed authentication model
4.4 Login and Authentication Phase
The MUi and CMDi participate in this stage to establish a mutual authentication session key at the end of the authentication session so that these entities can safely forward their data. The main steps at this stage can be described as follows:
• The MUi inputs the identity IDu and password PWu into the mobile phone device. Then, the device calculates PIDu = h(IDu || PWu) ⊕ PIDu’, Bi = h(IDu || PWu) ⊕ Bi’. Next, it selects a random integer a1
• Upon the receipt of message from MUi, the GRSj verifies the freshness for T1. If it is fresh, it calculates PIDu’ = R1⊕h(PIDG ||T1) and retrieves Bi’ from repository LR, otherwise, rejects the session. Next, it calculates a1' = R2⊕h(PIDu'||PIDG||Bi'||T1), PIDd' = R3⊕h(PIDu'||PIDG||Bi'||a1'||T1), R4' = h(PIDu’ || PIDd'|| PIDG || Bi’ || a1'||T1). Next, GRSj verifies R4’ ? = R4, if it is false, it aborts the session. On the other hand, it calculates R5 = h(PIDG || PIDd’ || Bj’)⊕ a1’, R6 = h(PIDd’ || PIDG || Bj’ || a1’) ⊕ PIDu’, R7 = h(PIDu'|| PIDd'|| PIDG || Bj’ || a1’). In the last, it submits the message R5, R6, R7 towards CMDi.
• The CMDi, after getting the message (R5, R6, R7), calculates a1″ = h(PIDG || PIDd || Bj ) ⊕ R5, PIDu ″ = h(PIDd|| PIDG || Bj || a1″) ⊕ R6 and R7″ = h(PIDu ″|| PIDd || PIDG || Bj || a1″). Next, the CMDi verifies the equality R7″ ? = R7 , it aborts the session if it is not true. On the other hand, it randomly selects a 160-bit integer a2
• The MUi after getting the message (R8, R10) calculates a2′ = h(PIDd || PIDu|| a1) ⊕ R8, R9′ = h(PIDu || a1 || a2′) and R10′ = h(PIDu || PIDd || PIDG || a1 || a2′ ||R9′). Next, it verifies the equation R10 ? = R10. If it does not hold valid, it terminates the session. On the other hand, it authenticates the CMDi and calculates a mutual session key as SKud = h(PIDu′ || PIDd || PIDG|| R9′).
5 Security Evaluations and Analysis
We here formally prove that our scheme can resist the known attacks under the random oracle model. In addition, we informally stated that our plan is protected from contemporary threats. The following subsections consider both formal and informal security analysis.
We describe a model related to formal security analysis, which is described with the help of a game played between malicious
The “Reveal” query models the erroneous use of the session key in the session. Upon the execution of Reveal query, in case the instance is effectively created, the challenger would return the session key SK for the instance
After the use of Test query (Test (
The adversary may employ the above mentioned queries, i.e., Send, Reveal, Extract after initiating the Test query [23]. Here, one disadvantage to
Definition 1 (AKE-secure): When there is a negligible polynomial probability, the adversary may auspiciously win that game with a non-negligible benefit
The adversary may positively compromise the mutual authenticity of the contributed protocol
Definition 2 (ME-secure): In case there exists no probability for any polynomial time attacker such that one may auspiciously win the game with considerable benefit
We acknowledge that there lies no adversary
Lemma1: We assume that a polynomial time attacker
Proof: The challenger chooses a 160-bit randomly generated integer q, and submits the factors {h, n} towards the adversary. The challenger produces a new hash-list LHs, which is blank on initial basis, and is meant for recording the query inputs as well as outputs for hash-based oracles. Then, it chooses two random drone identities, such as IDU and IDD to proceed. We assume that the rest of the oracles may be queried once the hash-based oracles perform their function. The queries’ responses are illustrated as under:
h(yi): The challenger initially verifies the occurrence of yi in the LHs list. If it exists in the list, the challenger would return Yi to attacker. Otherwise, it selects a random integer Yi, inserts (yi, Yi) in the LHs list and returns the same Yi to attacker.
Extract (IDU): In case u
Send (
Send (
Send (
Reveal (
We assume qsd, qLR and qLHs represent the number of Send, LR and LHs queries executed by the adversary.
where a represents the valid record index in Send (
Nonetheless, this shows the contradiction regarding the hardness for guessing 160-bit random integer as shown in Eq. (3). Alternatively, the attacker may not construct a legitimate login request or response message, so the drones in the protocol may verify the authenticity of one another.
Theorem 1. The proposed protocol is ME-Secure for rigid guessing of 160-bit random integer.
According to Lemma1, no adversary may construct a legitimate login request or response message for guessing the high entropy 160-bit random integer. Thus, the contributed protocol is ME-Secure.
Theorem 2. The proposed protocol is AKE-Secure for rigid guessing of 160-bit random integer.
Proof. We assume that the probabilistic polynomial-time attacker produces the valid b'=b with non-negligible chance
• ESKi: The adversary may get the legitimate session key upon the execution of Test query.
• EMU: The adversary runs the Test query for the instance
• ECMD: The adversary runs the Test query with success for the instance
EMUi-GRSj-CMDi: The adversary may disrupt the authentication session between MUi and GRSj, as well as between MUi and CMDi. It is known that the attacker may guess the valid b with the missing information of b as
Hence
In relation to Pr[ECMDiEMUi-GRSj-CMDi] = Pr[ECMDi]
We have Pr[ESKi
The events ESKi
5.3 Informal Security Analysis
The proposed scheme provides mutual authenticity to both participants by devising a unique and mutual agreed session key between them. We know that the benefit that adversary may take by launching the login as well as an authentication request and response message is quite negligible due to illustrated lemma1 in above section [24]. Hence, the MUi and CMDi could mutually authenticate one another with the assistance of GRSj. Hence, the proposed approach supports mutual authentication.
In the contributed protocol the MUi does not send its identity plainly on pubic channel, rather it is masked in the form of PIDu = h(IDu || k). Furthermore, PIDu is integrated in the message R1=h(PIDG ||T1) ⊕PIDu during mutual authentication process. It is hard problem in polynomial terms to recover the 160-bit random integer on account of guessing the values [25], so it is not feasible to calculate the legitimate identity of mobile drone CMDi without compromising the high entropy factor k. Thus our scheme affirms anonymity to the participants in protocol.
We employ random integers a1 and a2 along with fresh timestamps in different sessions which enable the constructed messages (R1, R2, R3, R4) in a session to be unique each time these are generated [26,27]. The attacker may not be able to distinguish the exchanged messages among for MUi and CMDi across various sessions. Furthermore, the legal identifies such as IDu or PIDu are used in collision-resistant one hash function which enables the protocol in affording the untraceability feature.
In the proposed scheme, the MUi confirms the authenticity of CMDi through validating R10, which ensures that both of these entities are having the legitimate randomly generated factors, a1 and a2. In this manner both entities construct a secure session key SK = SKud = SKdu = h(PIDu || PIDd || PIDG|| R9) to interact in the future. Hence our scheme supports secure key agreement between the members.
In case the adversary is able to capture the legal drone physically, it may access all of the stored information in its memory including pseudonym identities for CMDi [28,29]. Then if the adversary attempts to forge the legal MUi, it would construct the legal messages (R1, R4) and submit towards GRSj. Now the adversary may compute the correct R1 = h(PIDG ||T1) ⊕PIDu and R4 = h(PIDu || PIDd || PIDG || h(Bi || a1|| T1)), while a1 and Bi depict the random integers as chosen by the adversary for random number and the protected key, respectively. After the receipt of (R1, R4), the GRSj initially would parse from R1 and recover the related secret as Bi in the list LHs. Thereafter, the GRSj calculates the parameter R4’ along with another factor Bi and verifies the equation validity as R1’ = R1. Therefore, the attacker does not expose the valid parameter Bi, and make the GRSj distinguish the MUu from legal user.
5.3.6 Server Masquerading Attack
The attacker may impersonate himself as GRSj and submits the message R7 towards the CMDi. Then the attacker calculates R7 = h(PIDu′|| PIDd′|| PIDG || Bj′ || a1′), where Bj acts as a random integer chosen as CMDi's private key by the adversary. After the receipt of R7, the CMDi constructs R4’ along with Bj and also checks the equality for R7’ ? = R7. Nonetheless, the adversary may not access the Bj parameter or the CMDi accesses the malicious server. Thus, our scheme is resistant to the spoofing attack.
The drones are vulnerable in the hands of adversaries, and could be physically compromised at any time. We assume that the adversary captures e number of drones and access the stored contents including Bj = h(IDd || KG), PIDd = h(IDd || k), and SKud = h(PIDu|| PIDd || PIDG|| R9′) where j = (1
5.3.8 Stolen MUi's Smart Device Threat
In case the adversary is able to approach the MUi's smart device and recover its contents (Bi′, PIDu′, PIDd) using differential analysis, where Bi′ = h(IDu || PWu) ⊕ Bi and PIDu′ = h(IDu || PWu) ⊕PIDu. The attacker may guess the password from Bi′ only if it can test its accuracy, however without the MUi's identity it cannot verify it. Thus, our scheme is resistant to the stolen device threat.
The participants MUi and GRSj select random numbers and compute the login request message and response message as R4 and R10, respectively. Since the random nonces are fresh, the participants GRSj, CMDi and MUi might discern the legitimate requests from the replayed messages through verification checks. Hence, our scheme is immune to this replay attack threat.
5.3.10 Known Session Key Attack
If an attacker becomes familiar about the current session key of any session in our scheme, it may not compute the previous session keys employing the current session key [31]. This is because the attacker needs to approach crucial pseudonym parameters besides the random nonces to construct the legal session key, however these parameters are protected under collision resistant one way hash function and cannot be compromised in polynomial amount of time.
This section evaluates the performance of contributed protocol against the comparative studies including Wazid et al., Singh et al., Challa et al., and Turkanovic et al. on the basis of computational and communicational costs. The execution latency for the crypto-primitives employed by the comparative schemes [17,18,20,22] is depicted as Tfe to execute fuzzy extractor operation, Th to execute one-way hash operation, Tex to execute modular exponentiation operation, Tm to execute modular multiplication operation, Tecm to execute (Elliptic Curve Cryptography) ECC-based point multiplication [31]. These crypto-primitive operations have been implemented for mobile user device as client and desktop computer as server. The mobile drones or user devices are equipped with biochemical detectors, infrared, microphone and camera-based sensors. We calculate the cost of computations with the help of MIRACL library [23] and Android-enabled MUi/CMDi client (Lenovo Zuk Z1 having 2.5Ghz Quad-core microprocessor, Android V5.1.2 OS, and 4GB RAM). To simulate the GRSj environment we used desktop computer (HP E8300 Core i5 2.96Ghz, Ubuntu 16.12 OS and 8GB RAM). The experiments were conducted on the discussed client and server hardware platform that provides varying execution costs for various primitives. We select a multiplicative cyclic group G with order n having 160-bit prime integer.
This group G helps to achieve the 1024-bit RSA level of security. Using the above simulation, the execution timing of various crypto-primitives such as Tfe ≈ Tecm, Th, Tex, Tm and Tecm is computed as 16.403, 0.078, 3.943, 0.012 and 0.012 ms for MUi/CMDi, and 6.276, 0.013, 0.438, 0.003 and 0.003 ms, respectively. In [17], the mobile user takes 1Tfe + 16Th computational cost with 17.6 ms of execution latency. The CMDi takes seven Th operations and GRSj incurs eight Th operations with computational cost 0.54 ms and 0.104 ms respectively. In [22], the GRSj does not participate in the mutual authentication process. Therefore, in this phase the MUi and CMDi require 2Tex + 5Tm and 2Tex + 7Tm, i.e., 7.946 ms and 7.97 ms of computational cost, respectively. In [20], the MUi and CMDi entities bear 98.8 ms and 65.8 ms computational cost with given primitives 1Tfe + 5Tecm + 5Th and 3Th + 4Tecm respectively. On the server's end, it bears 31.43 ms of computational latency with 4Th + 5Tecm computations [18] bears 0.54 ms latency for both MUi and CMDi with 7 hash operations (7Th) each, while on the GRSj's end it incurs 19 hash operations with 1.482 ms computational latency. The proposed scheme employs 10Th, 7Th, 7Th operations with 0.78 ms, 0.54 ms, and 0.54 ms of computational costs for MUi, CMDi and GRSj, respectively. Tab. 2 describes the computational costs of [17,18,20,22] that are compared with the proposed schemes. For being lightweight symmetric crypto-operation, the hash function h(.) with Th is suitable for crowd sensing drone-based ecosystem to save the energy of mobile devices and ultimately improve their uptime.
In order to compare communication costs, we assume that |G| characterize 1024-bit element size, while |Zn| represents the 160-bit of each element in Zn. Similarly, the |ID| depict the 32-bit size of timestamp as well as MUi's identity. We make the functionality comparison of our scheme against Wazid, Singh, Challa and Turkanovic et al. schemes in Tab. 4. The incurred communication cost of protocols [17,18,20,22] is compared against the proposed scheme as shown in Tab. 3. The Wazid et al. [17] bears the communication cost of 1696-bits which is calculated as 10|Zn| + 3|ID| having 10 Zn operations and 3 ID operations. Similarly, the [22,20,18] bear 4256-bits, 2528-bits, 2720-bits against 4|G| + 4|ID|, 10|Zn| + 3|ID| and 10|Zn| + 3|ID| crypto-operations, respectively. In comparison with other schemes, the proposed scheme has remarkably less communication cost of 1472-bits against 9|Zn| + |ID| operations.



We now discuss the simulation details of the proposed model based on NS2 and the simulation details of the comparison schemes in [17,18,20,22]. We performed the simulation by using Ubuntu 14.04 long-term support (LTS platform) on the NS2 2.35 simulator [27]. We discussed the simulation parameters in Tab. 5. The total time taken by simulation is set as 2400 s (40 min). The entities CMDi, MUi, and Sj symbolize for ith drone, ith mobile user device, and jth IoT sensor in the compared schemes. We consider the various mobility parameters as 20, 30 and 40 mps for CMDi, MUi and Sj. We also assume a fixed server gateway across all of these schemes. The communication messages as exchanged among these participants are shown in Tab. 3. In the simulated experiment, three network performance-based benchmarks are evaluated, i.e., packet loss rate (number of packets), EED (sec) and throughput (bps). We now discuss the impact on these factors in the experiment in the following.

We calculate the throughput based on the number of bits transmitted per unit of time i.e., (rp
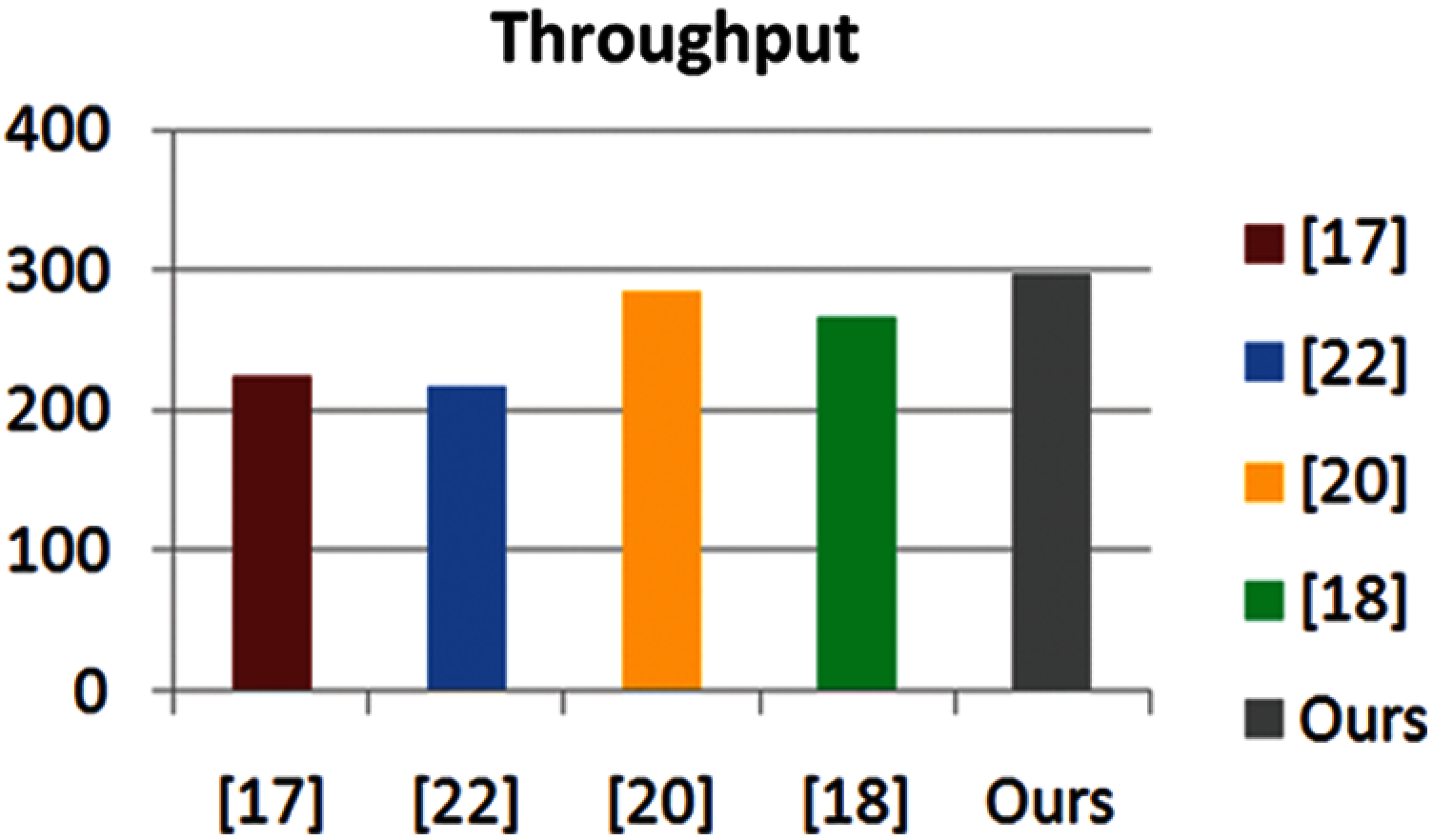
Figure 3: Throughput
The EED shows the average time of packets to get to the sink or destination. This factor may be represented in numeric terms as
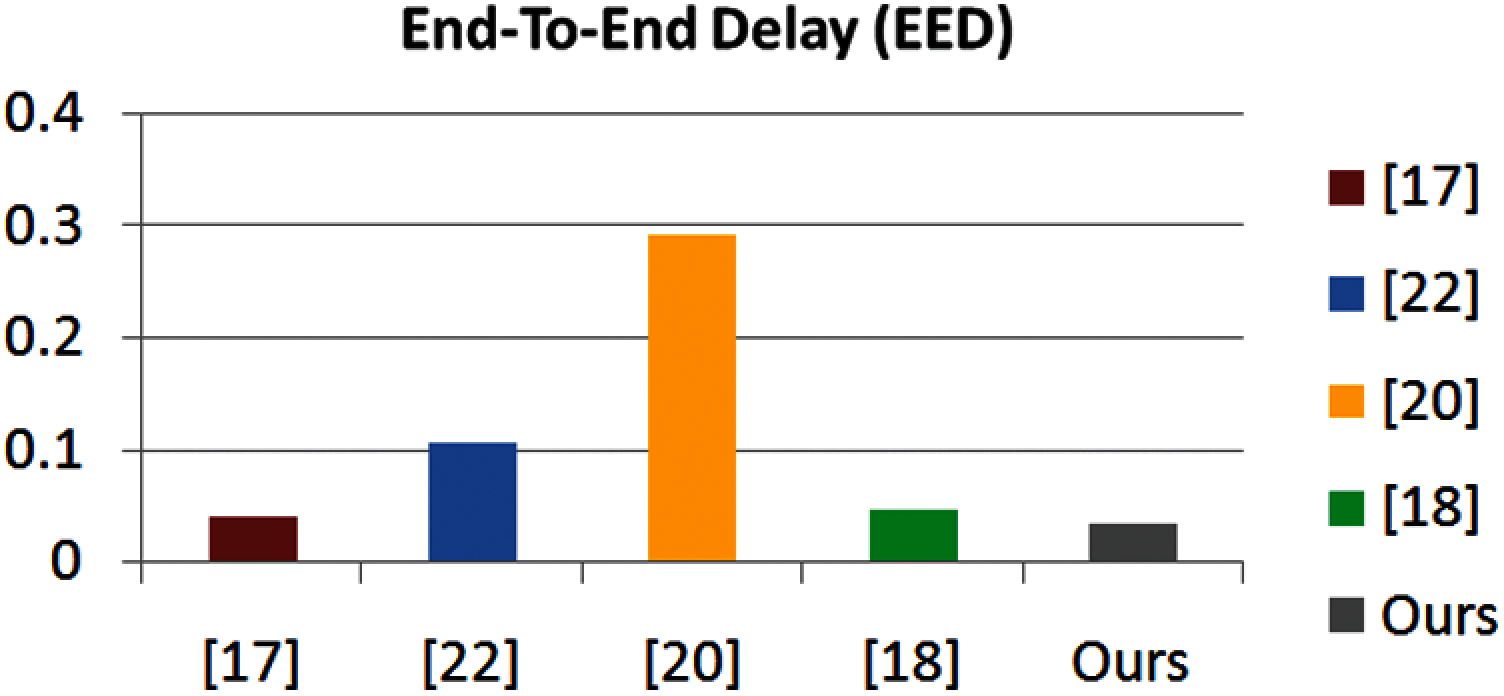
Figure 4: End-to-end delay
The PLR factor describes the number of lost data packets per unit time and can be expressed as (nip/Td), where Td represents the total time in seconds, and nip represents the number of lost data packets. This factor must be as small as possible to make network-based communication more reliable. Fig. 5 shows the packet loss rate of different scenarios considering the comparison scheme and the contribution model. Obviously, the contribution model has a lower PLR compared with other schemes.
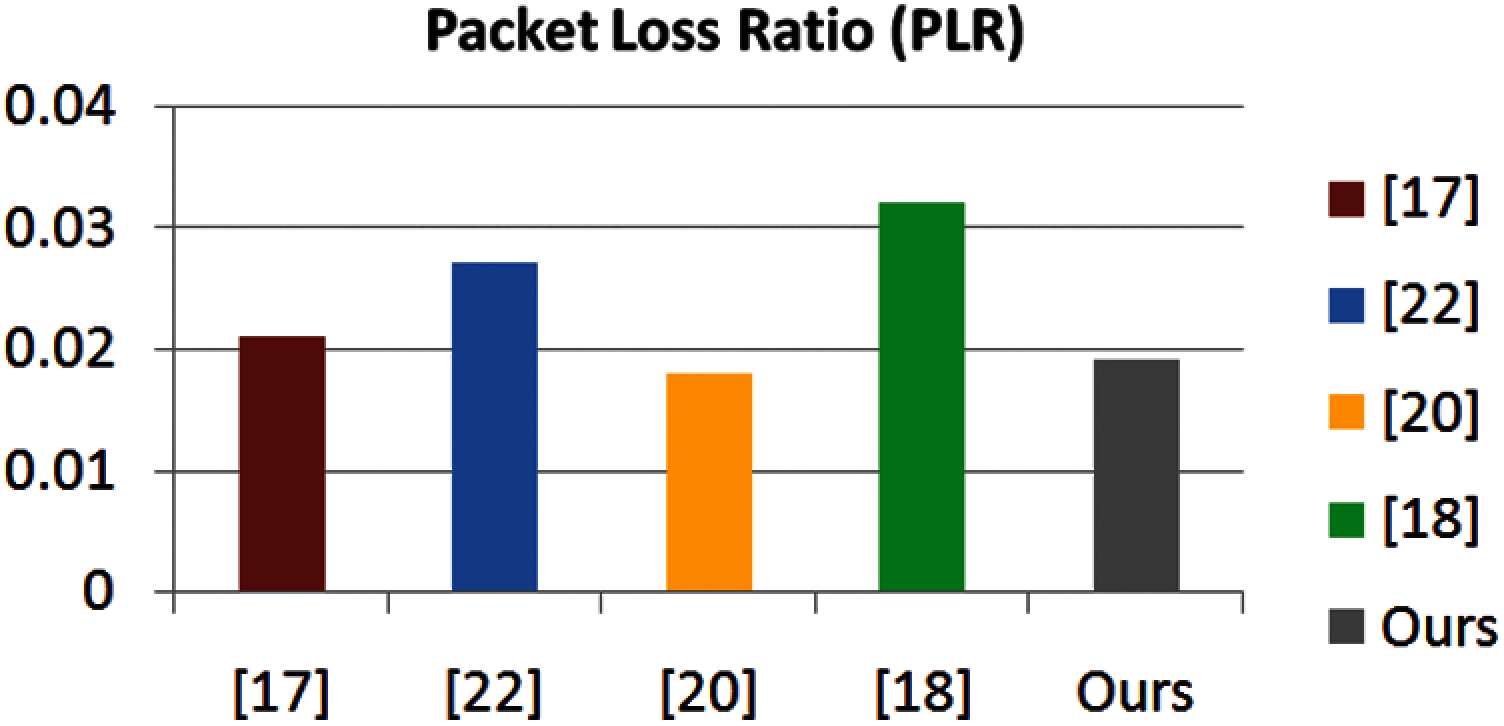
Figure 5: Packet loss ratio
The security and privacy requirements for reliable distribution of aerial monitoring and surveillance-based services have received increasing attention due to the vulnerability of the drone terrain. If the underlying authentication key agreement between the participating entities is not secure, the attacker may launch various attacks to disrupt the communication. In order to solve the security and privacy issues in such networks, we demonstrated a new identity verification protocol based on crowd monitoring drones, which enables participants to establish an agreed session key between them, and secure communication afterwards. Formal analysis under the Random Oracle Model (ROM) proved the proposed scheme. In addition, we used NS2 simulation to compare the proposed scheme with the existing scheme. Our analysis proves that the proposed scheme outperforms other schemes in terms of throughput, end-to-end delay and packet loss rate. Performance evaluation and benchmark factors show that the proposed scheme is secure compared with other contemporary studies in the same field. In the future, we can explore the prospect of using distributed systems based on blockchain to protect air surveillance.
Acknowledgement: The authors express their gratitude to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the Project Number (227).
Funding Statement: This work was supported by the Deputyship for Research & Innovation, Ministry of Education (in Saudi Arabia) through the Project Number (227).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. W. Xiao, M. Li, B. Alzahrani, R. Alotaibi, A. Barnawi et al., “A blockchain-based secure crowd monitoring system using UAV swarm,” IEEE Network, vol. 35, no. 1, pp. 108–115, 2021. [Google Scholar]
2. A. Trotta, U. Muncuk, M. F. Di and K. R. Chowdhury, “Persistent crowd tracking using unmanned aerial vehicle swarms: A novel framework for energy and mobility management,” IEEE Vehicular Technology Magazine, vol. 15, no. 2, pp. 96–103, 2020. [Google Scholar]
3. T. Alladi, V. Chamola and N. Kumar, “PARTH: A two-stage lightweight mutual authentication protocol for UAV surveillance networks,” Computer Communications, vol. 160, pp. 81–90, 2020. [Google Scholar]
4. L. Nkenyereye, S. R. Islam, M. Bilal, M. Abdullah-Al-Wadud, A. Alamri et al., “Secure crowd-sensing protocol for fog-based vehicular cloud,” Future Generation Computer Systems, vol. 120, pp. 61–75, 2021. [Google Scholar]
5. G. Cardone, A. Cirri, A. Corradi, L. Foschini, R. Ianniello et al., “Crowdsensing in urban areas for city-scale mass gathering management: Geofencing and activity recognition,” IEEE Sensors Journal, vol. 14, no. 12, pp. 4185–4195, 2014. [Google Scholar]
6. B. Alzahrani, O. S. Oubbati, A. Barnawi, M. Atiquzzaman and D. Alghazzawi, “UAV assistance paradigm: State-of-the-art in applications and challenges,” Journal of Networks and Computer Applications, vol. 166, pp. 102706, 2020. [Google Scholar]
7. Y. Jiang, Y. Miao, B. Alzahrani, A. Barnawi, R. Alotaibi et al., “Ultra large-scale crowd monitoring system architecture and design issues,” IEEE Internet of Things Journal, vol. 8, no. 13, pp. 10356–10366, 2021. [Google Scholar]
8. O. P. Popoola and K. Wang, “Video-based abnormal human behavior recognition—a review,” IEEE Transactions on Systems, Man and Cybernetics, vol. 42, no. 6, pp. 865–878, 2012. [Google Scholar]
9. M. Abdalla, P. Fouque and D. Pointcheval, “Password-based authenticated key exchange in the three-party setting,” in Proc. IWPKC, Les Diablerets, Switzerland, vol. 3386, pp. 65–84, 2005. [Google Scholar]
10. C. Lin, D. He, N. Kumar, K. K. R. Choo, A. Vinel et al., “Security and privacy for the internet of drones: Challenges and solutions,” IEEE Magazine, vol. 56, no. 1, pp. 64–69, 2018. [Google Scholar]
11. M. Silvagni, A. Tonoli, E. Zenerino and M. Chiaberge, “Multipurpose UAV for search and rescue operations in mountain avalanche events,” Geomatics, Natural Hazards and Risk, vol. 8, no. 1, pp. 18–33, 2017. [Google Scholar]
12. J. Blazakis, “Border security and unmanned aerial vehicles,” Connections, vol. 5, no. 2, pp. 154–159, 2006. [Google Scholar]
13. I. Maza, F. Caballero, J. Capitán, J. R. Martínez-de Dios and A. Ollero, “Experimental results in multi-uAV coordination for disaster management and civil security applications,” Journal of Intelligent & Robotic Systems, vol. 61, no. 1, pp. 563–585, 2011. [Google Scholar]
14. N. H. Motlagh, M. Bagaa and T. Taleb, “UAV-Based IoT platform: A crowd surveillance use case,” IEEE Communications Magazine, vol. 55, no. 2, pp. 128–134, 2017. [Google Scholar]
15. H. Sedjelmaci, S. M. Senouci and N. Ansari, “A hierarchical detection and response system to enhance security against lethal cyber-attacks in UAV networks,” IEEE Transactions on Systems, Man and Cybernetics, vol. 48, no. 9, pp. 1594–1606, 2017. [Google Scholar]
16. B. Semal, K. Markantonakis and R. N. Akram, “A certificateless group authenticated key agreement protocol for secure communication in untrusted UAV networks,” in Proc. DASC, London, UK, pp. 1–8, 2018. [Google Scholar]
17. M. Wazid, A. K. Das, N. Kumar, A. V. Vasilakos and J. J. Rodrigues, “Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment,” IEEE Internet of Things Journal, vol. 6, no. 2, pp. 3572–3584, 2018. [Google Scholar]
18. M. Turkanovic, B. Brumen and M. Hölbl, “A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the internet of things notion,” Ad Hoc Networks, vol. 20, pp. 96–112, 2014. [Google Scholar]
19. M. S. Farash, M. Turkanovic, S. Kumari and M. Hölbl, “An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the internet of things environment,” Ad Hoc Networks, vol. 36, pp. 152–176, 2016. [Google Scholar]
20. S. Challa, M. Wazid, A. K. Das, N. Kumar, A. G. Reddy et al., “Secure signature-based authenticated key establishment scheme for future IoT applications,” IEEE Access, vol. 5, pp. 3028–3043, 2017. [Google Scholar]
21. S. T. Messerges, E. A. Dabbish and R. H. Sloan, “Examining smart-card security under the threat of power analysis attacks,” IEEE Transactions on Computers, vol. 51, no. 5, pp. 541–552, 2002. [Google Scholar]
22. J. Singh, A. Gimekar and S. Venkatesan, “An efficient lightweight authentication scheme for human-centered industrial internet of things,” International Journal of Communication Systems, pp. e4189, 2019. [Google Scholar]
23. Y. Zhang, D. He, S. Zeadally, D. Wang and K. K. R. Choo, “Efficient and provably secure distributed signing protocol for mobile devices in wireless networks,” IEEE Internet of Things Journal, vol. 5, no. 6, pp. 5271–5280, 2018. [Google Scholar]
24. M. Tao, X. Li, H. Yuan and W. Wei, “UAV-Aided trustworthy data collection in federated-WSN-enabled IoT applications,” Information Sciences, vol. 532, pp. 155–169, 2020. [Google Scholar]
25. A. S. Abdalla, K. Powell, V. Marojevic and G. Geraci, “UAV-Assisted attack prevention, detection, and recovery of 5G networks,” IEEE Wireless Communications, vol. 27, no. 4, pp. 40–47, 2020. [Google Scholar]
26. K. Gai, Y. Wu, L. Zhu, K. K. R. Choo and B. Xiao, “Blockchain-enabled trustworthy group communications in UAV networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 7, pp. 4118–4130, 2020. [Google Scholar]
27. J. W. Jung, S. W. Chang and S. S. Lee, “Appropriate module configuration for vehicular networking using NS2 simulator,” in Proc. ICTC, Busan, Korea, pp. 611–612, 2014. [Google Scholar]
28. R. Canetti and H. Krawczyk, “Analysis of key-exchange protocols and their use for building secure channels,” in Proc. EUROCRYPT ‘21’, Innsbruck, Austria, Springer, pp. 453–74, 2001. [Google Scholar]
29. I. U. Khan, I. M. Qureshi, M. A. Aziz, T. A. Cheema and S. B. H. Shah, “Smart IoT control-based nature inspired energy efficient routing protocol for flying ad hoc network (FANET),” IEEE Access, vol. 8, pp. 56371–56378, 2020. [Google Scholar]
30. I. U. Khan, R. Alturki, H. J. Alyamani, M. A. Ikram and M. A. Aziz, “RSSI-Controlled long-range communication in secured IoT-enabled unmanned aerial vehicles,” Mobile Information Systems, vol. 2021, 2020. [Google Scholar]
31. I. U. Khan, S. Z. Zukhraf, A. Abdollahi, S. A. Imran, I. M. Qureshi et al. “Reinforce based optimization in wireless communication technologies and routing techniques using internet of flying vehicles,” in Proc. ICFNDS, New York, NY, USA, pp. 1–6, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |