DOI:10.32604/cmc.2022.021490

| Computers, Materials & Continua DOI:10.32604/cmc.2022.021490 |  |
| Article |
Energy Aware Data Collection with Route Planning for 6G Enabled UAV Communication
1Department of Natural and Applied Sciences, College of Community-Aflaj, Prince Sattam bin Abdulaziz University, Saudi Arabia
2Department of Biomedical Engineering, College of Engineering, Princess Nourah bint Abdulrahman University, Saudi Arabia
3Department of Computer Science, King Khalid University, Muhayel Aseer, Saudi Arabia
4Faculty of Computer and IT, Sana’a University, Sana’a, Yemen
5Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
6Department of Information Systems, King Khalid University, Muhayel Aseer, Saudi Arabia
*Corresponding Author: Anwer Mustafa Hilal. Email: a.hilal@psau.edu.sa
Received: 04 July 2021; Accepted: 27 August 2021
Abstract: With technological advancements in 6G and Internet of Things (IoT), the incorporation of Unmanned Aerial Vehicles (UAVs) and cellular networks has become a hot research topic. At present, the proficient evolution of 6G networks allows the UAVs to offer cost-effective and timely solutions for real-time applications such as medicine, tracking, surveillance, etc. Energy efficiency, data collection, and route planning are crucial processes to improve the network communication. These processes are highly difficult owing to high mobility, presence of non-stationary links, dynamic topology, and energy-restricted UAVs. With this motivation, the current research paper presents a novel Energy Aware Data Collection with Routing Planning for 6G-enabled UAV communication (EADCRP-6G) technique. The goal of the proposed EADCRP-6G technique is to conduct energy-efficient cluster-based data collection and optimal route planning for 6G-enabled UAV networks. EADCRP-6G technique deploys Improved Red Deer Algorithm-based Clustering (IRDAC) technique to elect an optimal set of Cluster Heads (CH) and organize these clusters. Besides, Artificial Fish Swarm-based Route Planning (AFSRP) technique is applied to choose an optimum set of routes for UAV communication in 6G networks. In order to validated whether the proposed EADCRP-6G technique enhances the performance, a series of simulations was performed and the outcomes were investigated under different dimensions. The experimental results showcase that the proposed model outperformed all other existing models under different evaluation parameters.
Keywords: Unmanned aerial vehicle; 6G networks; artificial intelligence; energy efficiency; clustering; route planning; data collection; metaheuristics
In recent times, with the evolution of Internet of Things (IoT) and 6G technologies [1], the incorporation of cellular systems and UAVs has to shift towards novel network advance trends. At present, UAVs experience a rapid growth in different business applications. It is anticipated that these UAVs bring major advantages to its users in several areas like emergency communications, smart city construction, agriculture, mineral exploration, disaster assessment forestry, plant protection, power and oil pipeline inspections and other such broad application prospects [2]. Altogether, 6G UAV network can optimally fulfil a number of IoT applications and pave way to provide advanced services. In UAVs, the cellular converged network can perform as an aerial Access Node (AP)/Base Station (BS) to collect data from a huge amount of IoT nodes allocated to a specific extent and realize the connections with 6G networks. UAVs has the potential to interact with ground cellular BS. However, it creates a self-organizing cluster network via remote intelligence control framework [3]. Many UAVs are armed with distinct IoT devices to collect IoT data from distinct places simultaneously and send the collected data directly to the adjacent ground BSs or interact with ground BS via leader UAV with the help of AP ability. Though UAV flight and IoT device heavily rely upon power supply, all these devices have limited energy that severely influences the popularization and promotion of UAV-based IoT applications [4]. Thus, the collaborative process of multiple UAVs is a major problem to be used in radio spectrum resources. Further, it is essential to perform an advanced study on energy saving technology and spectrum usage under the basis of inexpensive hardware.
Transmission is a key aspect in a number of UAV schemes [5]. However, such UAV schemes have certain aspects of FANET such as high mobility of UAV nodes, sparse placement, and constraints in the available battery resource which altogether can hinder the stability and efficient transmission among the UAVs [6]. The high mobility nature of the UAV causes periodic changes in the topology. This requires a recurrent communication of new location among UAV nodes which results in energy utilization on the basis of overheads [7]. Comparatively, the sparse location of UAVs requires high energy for communication, owing to a considerably-longer distance among the UAVs. Smart clustering technique can enact the main role to enhance the energy efficiency of a network. Clustering is a process that splits the UAV nodes under many groups, when these nodes are located in a geographical place with certain similarities in achieving a particular purpose. In a cluster, every node is chosen as Cluster Head (CH). A CH node is permitted through coordination tasks and is relied upon the data of its cluster member to its end [8,9].
The current research work presents a novel Energy Aware Data Collection with Route Planning for 6G-enabled UAV communication (EADCRP-6G) technique. The goal of the proposed EADCRP-6G technique is to perform energy-efficient cluster-based data collection and optimal route planning for 6G-enabled UAV networks. The proposed EADCRP-6G technique includes an Improved Red Deer Algorithm-based Clustering (IRDAC) technique to elect a set of optimal Cluster Heads (CH) and organize the selected clusters. Besides, Artificial Fish Swarm-based Route Planning (AFSRP) technique is deployed in the selection of optimum set of routes for UAV communication in 6G networks. In order to examine the enhanced performance of EADCRP-6G technique, a series of simulations was conducted and the outcomes were investigated under different dimensions.
Liu et al. [10] proposed a novel non-stationary multi-mobility UAV-to-ship channel method. This method consists of SB and LoS modules as a result of sea water fluctuations. The MB component is presented based on the waveguide effects on sea surface. In the presented method, UAV is denoted by transmitter (Tx), ship is denoted by receiver (Rx), and the clusters between Rx and Tx can be viewed as moving in random directions and velocities. Later, a few common statistical properties of the projected UAV-to-ship channel module was investigated and the results were derived. Spyridis et al. [11] aimed at tracking a mobile IoT device of unknown position with the help of a set of UAVs, armed with RSSI sensors. The DL method executed the clustering process in UAV network at standard interval on the basis of GCN framework. In this execution, the data regarding UAV and RSSI locations was used. A heuristic technique was employed to define the number of clusters in a dynamic manner at all the instances. While the partitions were defined by optimizing RSSI loss function.
Bushnaq et al. [12] presented a relative analyses of U-UAV and T-UAV-aided cellular traffic offloading from a geographical location that endures heavy traffic situations. With the help of stochastic geometry tools, the researchers derived a joint distance distribution among UAV, hotspot users, and TBS. Na et al. [13] proposed a synergetic system for sub-slot allocation and UAV trajectory planning. Since the developed problems suffered from complications and non-convexity, an effective and iterative method was proposed to overcome the issues. Later, for fixed sub-slot duration and clustering state, the researchers optimized the UAV trajectory. In Faraji–Biregani et al. [14], a method was proposed to efficiently maintain the clusters that approached RF source while at the same time, the remaining UAVs were eliminated and returned to the base. Qi et al. [15] proposed an improved hierarchical 6G IoT network using UAVs in sky and armed IRS. The scheme utilized BackCom to transmit the data in free ride method. Through beamforming process, IRS improves the energy of reflectable signals, thus enhancing the performance and distance of BackCom. Tang et al. [16] studied about battery-constrained FEEL. In this study, the UAVs had the potential to alter the frequencies of functioning CPU, extend the lifetime of batteries and evade early dropping from FL training. The researchers optimized the scheme by jointly assigning both wireless bandwidth and computation resources upon time-differing platforms based on DDPG-based approach. In this approach, a linear integration of latency and energy utilization was executed to estimate the system cost.
Li et al. [17] investigated a joint downlink transmission power control and trajectory strategy challenge in multi type UABSs transmission networks. In order to satisfy the signal to noise power ratio of the user including interference, every UABS should alter its transmission power and location. Based on the communications among different transmission connections, a non-cooperative MFTG was presented earlier to model the joint optimization problem. Later, a Nash equilibrium solution was resolved using two phases: firstly, a user in the provided area is clustered to attain the early placement of UABSs; next, MFQ learning method is projected to resolve the distinct MFTG problems. Kurdi et al. [18] proposed a bacteria-inspired heuristic algorithm for effective distribution of tasks between the placed UAVs. The utilization of multi-UAVs is a significant model to combat the distribution of RPW in palm plantations. In order to improve the energy consumption and cost-aware transmission, a novel method named MRDSASL was presented in 6G network [19]. Then, multi-variate regression function was utilized as a threshold to analyze the evaluated node condition. Lastly, soft step activation function identified the effective nodes via regression analyses. Based on the results from deep analyses, 6G framework was implemented through effective nodes.
3 The Proposed EADCRP-6G Model
The proposed EADCRP-6G technique is designed to establish effective data collection and communication process in 6G-enabled UAV networks. The proposed EADCRP-6G technique encompasses two major processes namely, IRDAC technique for cluster construction and AFSRP technique for route planning. The detailed working stages of these two processes are offered in subsequent sections.
The upcoming 6G IoT demands the expansion of communication coverage while this ultra-high coverage is set to turn inevitable trends in the growth of smart cities. At present, drones are the most effectual solutions to improve transmission coverage due to time consumption and heavy cost incurred upon installing new BS. There are two major variances exist i.e., UAV communications and conventional ground wireless transmission. Here, UAV is loaded with fully-controllable maneuverability upon three dimensions. The horizontal position and height of the UAV can be adjusted at any point of time for the optimization of transmission efficiency with ground node. As displayed in Fig. 1, cylindrical antenna array is utilized improve the strength of transmission connection in an efficient manner. In order to ensure transmission performance between the UAV and BS, BS should execute precise beam-forming and take a certain location of UAV. In current research work, it is assumed that GPS and inertial measurement units are given to motion sensing and position of the UAVs. Each UAV is aware of its own location, location of the ground station, and location of other neighboring UAVs. Also, UAVs are armed with long- and short-range transmission with the help of 6G technologies. While the former one is utilized for data transmission within the cluster in the name of intra-cluster transmission, the latter one is utilized for data transmission between ground station and the CHs. Moreover, UAV-based mobile transmission aims at explicit data rate
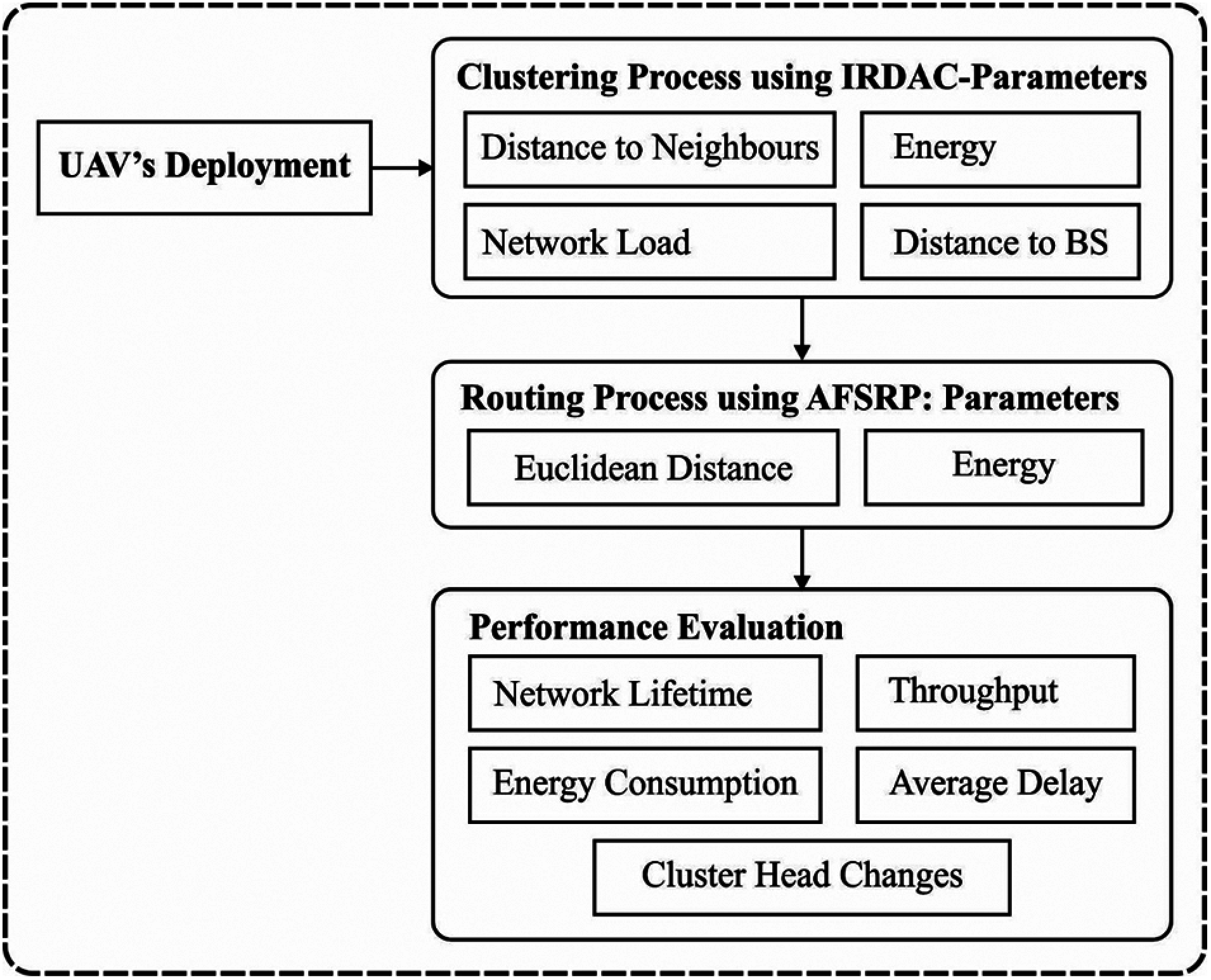
Figure 1: Overall working process of EADCRP-6G model
RDA technique is initiated by an initial arbitrary population that is equivalent to that of the Red Deers (RDs). The number of optimum RDs in a population is determined and are named after ‘male RD’ while rest are named as ‘hinds’. At first, male RD must roar. Depending upon the roaring capability, it is categorized under two groups such as Stags and Commanders. Alternatively, the commander builds the harem. Thus, the number of hinds in a harem is directly related with the capacity of commander in terms of fighting and roaring activities. At last, the commander mates with the hind in harem.
It is obvious that other males are named after stags for mating with adjacent hinds and no deliberation of constrained harems. Generally, the earlier steps of RDA evolve on the basis of exploration and exploitation phases efficiently. It can be stated that an RD provides a likely solution X in solution spaces. The dimension of solution X is Nvar. Succeeded by, Nvar dimension optimization problem, RD, is an
Indeed, Eq. (1) shows the element of X. As well, the function value is evaluated for each RD in Eq. (2):
To invoke this approach, the early population of size Npop is generated. Later, a group of optimum RD to Nmale is selected and the remaining one is Nhind (Nhind
Now, a male RD attempts to improve the efficacy using roaring. Therefore, during roaring procedure, it may be ineffective/effective. It can be stated that a male RD is deliberated as an optimum solution. In the event of solution area, male
In spite of generating a likely neighborhood solution of males, UB and LB limit the search space. They are deliberated as UB and LB of the search space, consistently.
It is noted that
In fact, the dramatic variation exists between males i.e.,
Here,
whereas
Consider that every commander fights with stags arbitrarily. Thus, two new solutions are obtained and exchanged by the commanders. These solutions are optimized whereas an optimal solution is superior to four solutions such as stag, commander, and two new solutions. In the event of fighting procedure, two mathematical formulas are used in Eqs. (6),(7):
Here, New1 & New2 represent the new solutions created with the help of fighting. Stag and Com indicate stags and commanders, respectively. In the event of new solutions, UB and LB diminish the search spaces. Since the fighting procedure is randomized,
whereas
Then, the number of hinds in a harem is calculated by Eq. (10):
Here,
Here,
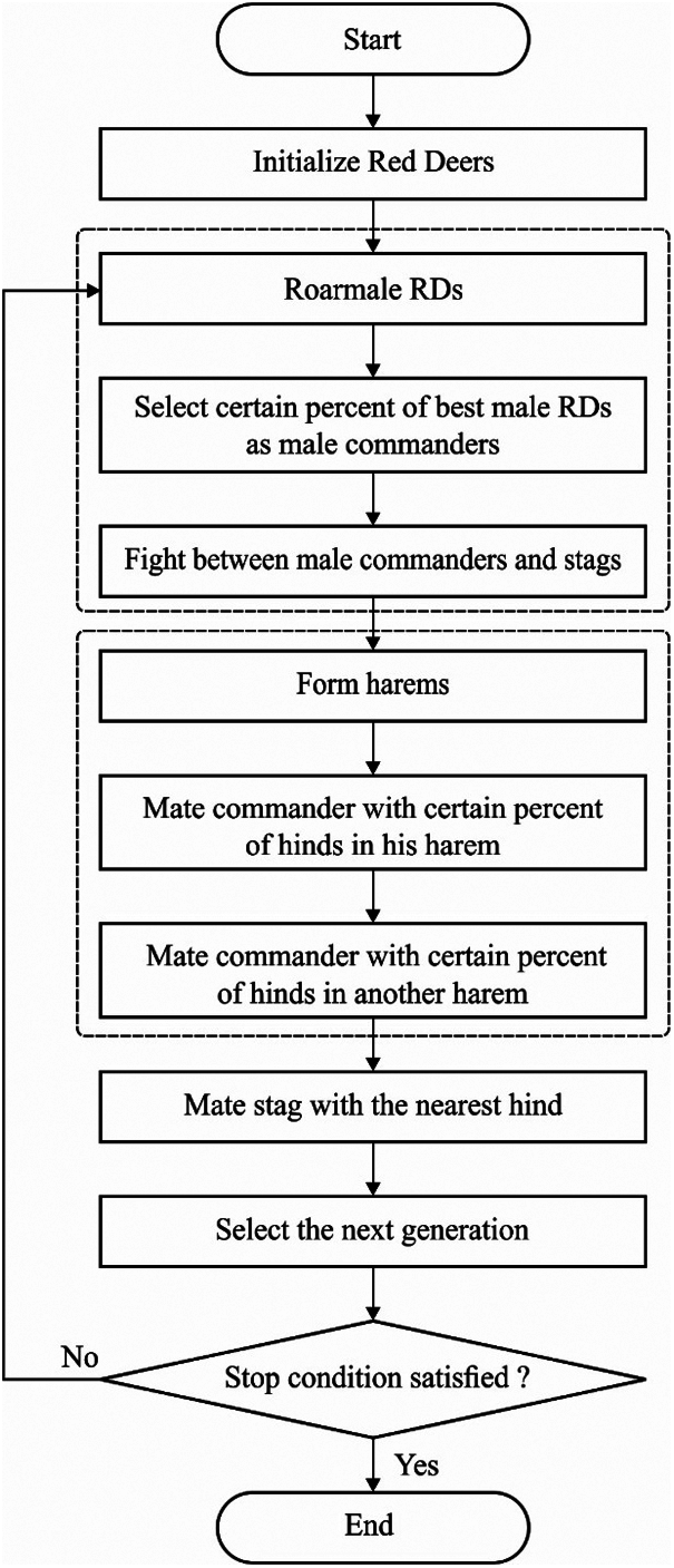
Figure 2: Flowchart of red deer algorithm
Succeeded by,
Here, Com & Hind denote hinds and commanders. Additionally,
The harem is chosen in an arbitrary way and male commanders mate with
whereas
Now, the stags mate with nearby hind. During mating, a male RD needs to employ a useful hind. It is the desired hind among other hinds without supposing the harem region.
whereas
In order to eliminate the RDA from local optimal problem, Levy Distribution (LD) concept is incorporated in it. LD is an arithmetic method of initiating a sudden drift. Fig. 3 is a diagram of RDA module. Levy flight is an arbitrary walk procedure where the step length of searching tasks gets improved with a sudden drift and is denoted by.
whereas
whereas
whereas α is equivalent to 1.5,
whereas
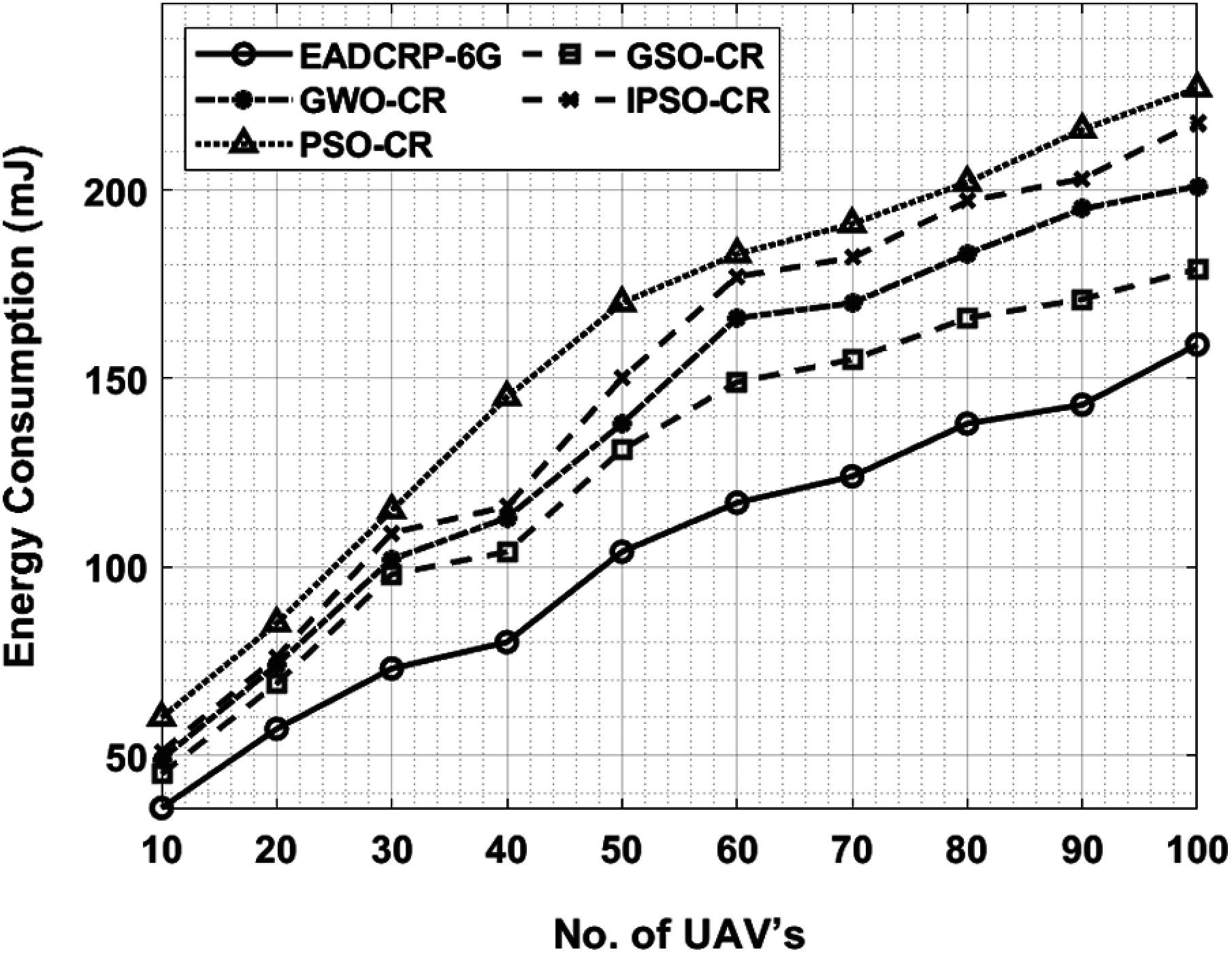
Figure 3: Energy consumption analysis of EADCRP-6G model
Generally, there exists four objective functions while every function encloses a substantial factor which is required for many purposes such as energy efficient clustering, energy maintenance by limiting the number of CHs, recognizing the current energy ratio, reducing the distance between BS and CH, mitigation of intracluster distances, enhanced intercluster distance between CHs, and load balancing amongst CHs. The recently-proposed hybrid WGWO method provides an optimum solution by deriving a FF with the help of distance to neighbours, energy, network load, and distance to BS. Thus, FF is defined in the recently used method as follows.
Here,
The following function defines the distance to neighbours, defined as Euclidean distance between the SNs.
The 3rd function decreases the distance between CH & BS. This method is deliberated as
The last function is used for load management from CH. Eq. (23) tells the high load constraints amongst CHs.
AFSA is a popular SI optimization module developed on the basis of fish swarming behaviour. This method is highly useful in the development of intelligent models to identify the global optimum solutions and does not attain gradient details of the objective function. Now, an artificial fish explores for food based on the foraging hierarchy of swarming nature and arbitrary behavior. Furthermore, artificial fish permits mutual data transmissions until a global optimal solution is attained. Assume
(1) Foraging behavior
Assume
whereas
(2) Swarming behavior
In a fish swarm, artificial fish
whereas
(3) Following behavior
When
(4) Random behavior
The artificial fish determines a state arbitrarily from Visual range and travels to the corresponding location. It is called default behavior.
(5) Behavior selection
In the event of AF, the predetermined behavior is compared and performed [21]. Thus, an optimum nature is determined to upgrade the current position of AF. Bulleting can be employed to record the best position i.e.,
Thus, AFSA employs the social nature of fish swarm to resolve the optimization problem. It is highly helpful for fish environment data and self-information to change the search direction so as to gain an optimal convergence and diversity. Thus, AF attains a location, where the food resource is maximal. Although AFSA is a superior member of global optimization methods among other optimization problems, it is still at risk in converging to sub optimum methods like metaheuristics. It is called early convergence of complex optimization problems which results in low performance. In order to detect an optimum set of routes, the dimension of every fish is made equivalent to CHs and further positions are located in BS. Assume,
The aim is to define an optimal set of routes from CH to BS with the help of FF including two variables such as distance and energy. Initially, the RE of subsequent hop node is defined and the node with maximal energy is processed as a relay node. In order to transmit the data, the source node transmits it to relay node that additionally moves towards the BS through inter CHs. Thus, the node with high RE is processed as a subsequent hop node. The initial sub objective
Also, Euclidean distance is employed in the calculation of distance from CHs to BS. The minimization of energy dissipation mostly depends upon the transmission distance. In the event of low distance, the energy gets considerably stored. When the distance is raised, a huge volume of energy is consumed. Hence, a node using minimal distance is preferred for a relay node. Thus, the following sub-objective i.e.,
The aforementioned sub-objectives are summarized as a FF herewith, in which
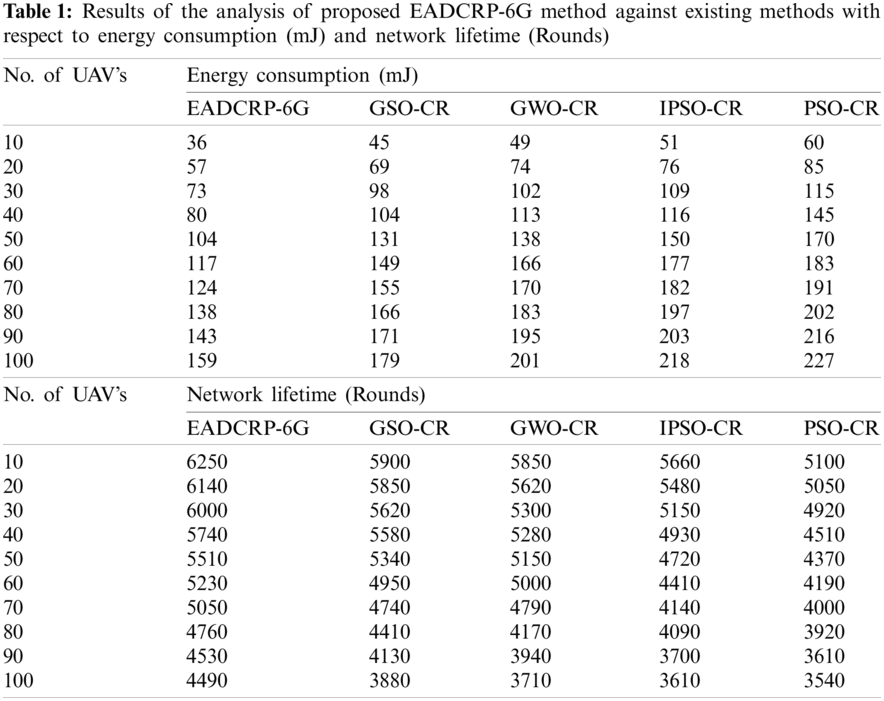
The current section examines the performance of the proposed EADCRP-6G technique under different performance measures. Tab. 1 shows the results achieved from Energy Consumption Analysis (ECA) and Network Lifetime Analysis (NLTA) of EADCRP-6G technique under varying number of UAVs. Fig. 3 shows ECA results of the proposed EADCRP-6G technique against existing techniques under distinct UAVs. From the figure, it can be inferred that the proposed EADCRP-6G technique accomplished an optimum performance over other methods with low ECA. For instance, with 10 UAVs, EADCRP-6G technique obtained a minimal ECA of 36 mJ, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques attained the maximum ECA values such as 45, 49, 51, and 60 mJ respectively. Meanwhile, with 30 UAVs, EADCRP-6G approach attained a lesser ECA value of 73 mJ, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methods gained high ECA values of 98, 102, 109, and 115 mJ correspondingly. Eventually, with 50 UAVs, the proposed EADCRP-6G technique achieved a minimum ECA of 104 mJ, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques achieved high ECA values such as 131, 138, 150, and 170 mJ correspondingly. In line with these, at 70 UAVs, EADCRP-6G method obtained a minimal ECA of 124 mJ, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methods gained maximum ECA values such as 155, 170, 182, and 191 mJ correspondingly. Lastly, with 100 UAVs, EADCRP-6G technique obtained the least ECA of 159 mJ, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methodologies attained high ECA values such as 179, 201, 218, and 227 mJ correspondingly.
Fig. 4 shows the detailed results of NLTA achieved by EADCRP-6G technique under varying UAVs. The experimental results demonstrate that the proposed EADCRP-6G technique attained effective outcomes with an improved NLTA. For instance, with 10 UAVs, EADCRP-6G technique demonstrated a high NLTA of 6250 rounds, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques produced low NLTA values such as 5900, 5850, 5660, and 5100 rounds respectively. Followed by, with 30 UAVs, the proposed EADCRP-6G approach outperformed other methods with a superior NLTA of 6000 rounds, while GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methods yielded less NLTA values such as 5620, 5300, 5150, and 4920 rounds correspondingly. Concurrently, with 50 UAVs, EADCRP-6G technique exhibited a high NLTA of 5510 rounds, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques achieved low NLTA values as given herewith; 5340, 5150, 4720, and 4370 rounds correspondingly. In the meantime, under 70 UAVs, EADCRP-6G method demonstrated a high NLTA of 5050 rounds, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methods achieved low NLTA values such as 4740, 4790, 4140, and 4000 rounds correspondingly. Finally, under 100UAVs, the presented EADCRP-6G algorithm portrayed a maximum NLTA of 4490 rounds, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methods achieved less NLTA values such as 3880, 3710, 3610, and 3540 rounds correspondingly.
Tab. 2 examines the results of throughput and average delay accomplished by the proposed EADCRP-6G method under varying numbers of UAVs. A brief throughput of EADCRP-6G method is shown in Fig. 5 under varying UAVs. The experimental outcomes showcase that the proposed EADCRP-6G method achieved effective outcomes with increased throughput. For sample, under 10 UAVs, the proposed EADCRP-6G technique displayed a superior throughput of 0.88 Mbps, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR algorithms offered low throughput values such as 0.82, 0.81, 0.79, and 0.75 Mbps correspondingly. Likewise, under 30 UAVs, the proposed EADCRP-6G technique demonstrated an increased throughput of 0.79 Mbps, whereas other methods such as GSO-CR, GWO-CR, IPSO-CR, and PSO-CR achieved low throughput values such as 0.69, 0.61, 0.56, and 0.53 Mbps respectively. Similarly, under 50 UAVs, EADCRP-6G method achieved a maximum throughput of 0.74 Mbps, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques accomplished minimum throughput values such as 0.57, 0.50, 0.45, and 0.37 Mbps respectively.
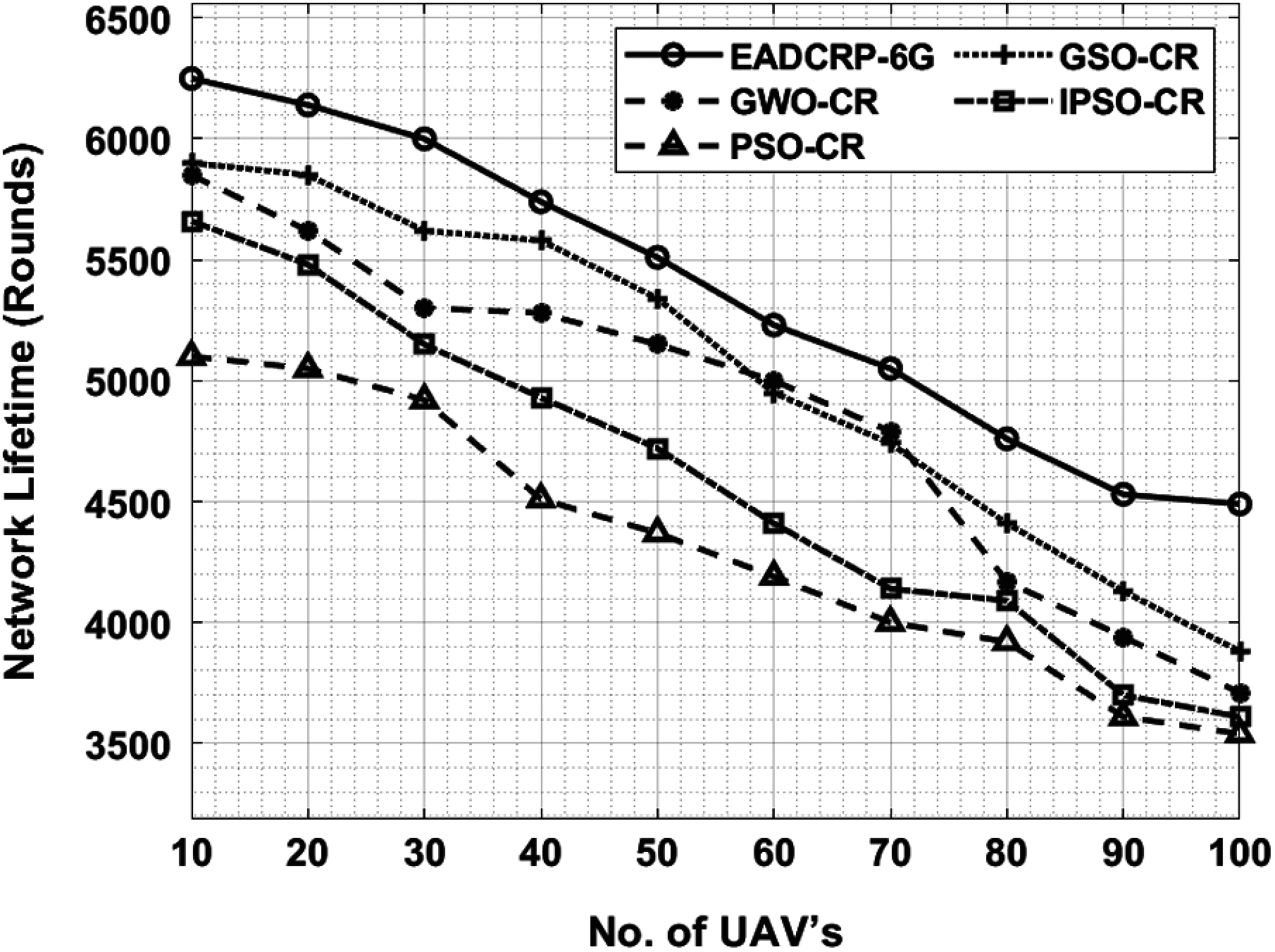
Figure 4: Network lifetime analysis of EADCRP-6G model
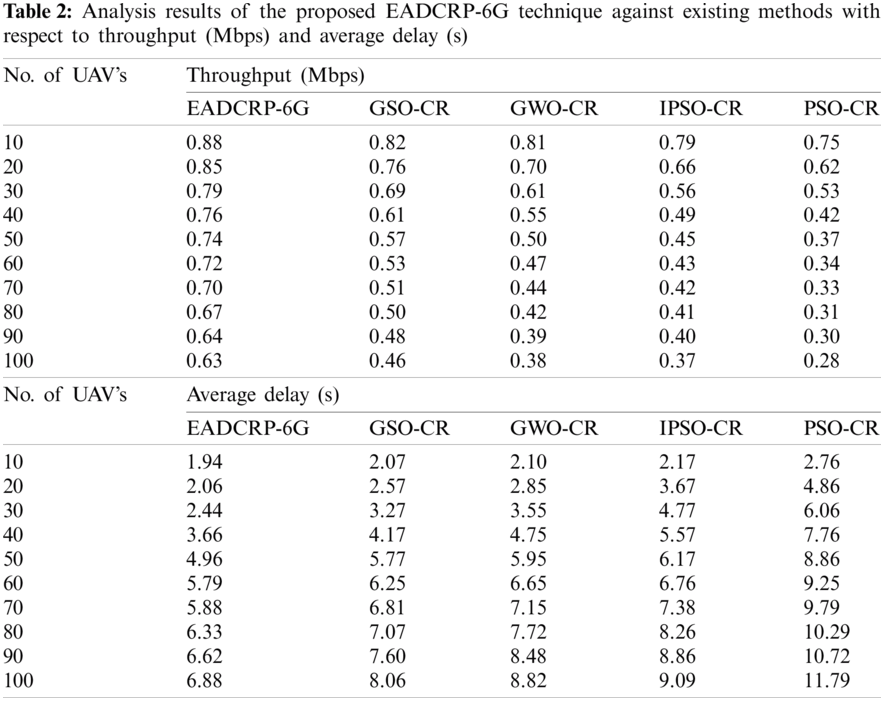
Also, under 70 UAVs, the proposed EADCRP-6G technique depicted an increase in the throughput of 0.70 Mbps, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques achieved low throughput values such as 0.51, 0.44, 0.42, and 0.33 Mbps respectively. Lastly, under 100 UAVs, EADCRP-6G methodology outperformed all other methods with a superior throughput of 0.63 Mbps, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methods achieved minimal throughput values such as 0.46, 0.38, 0.37, and 0.28 Mbps correspondingly.
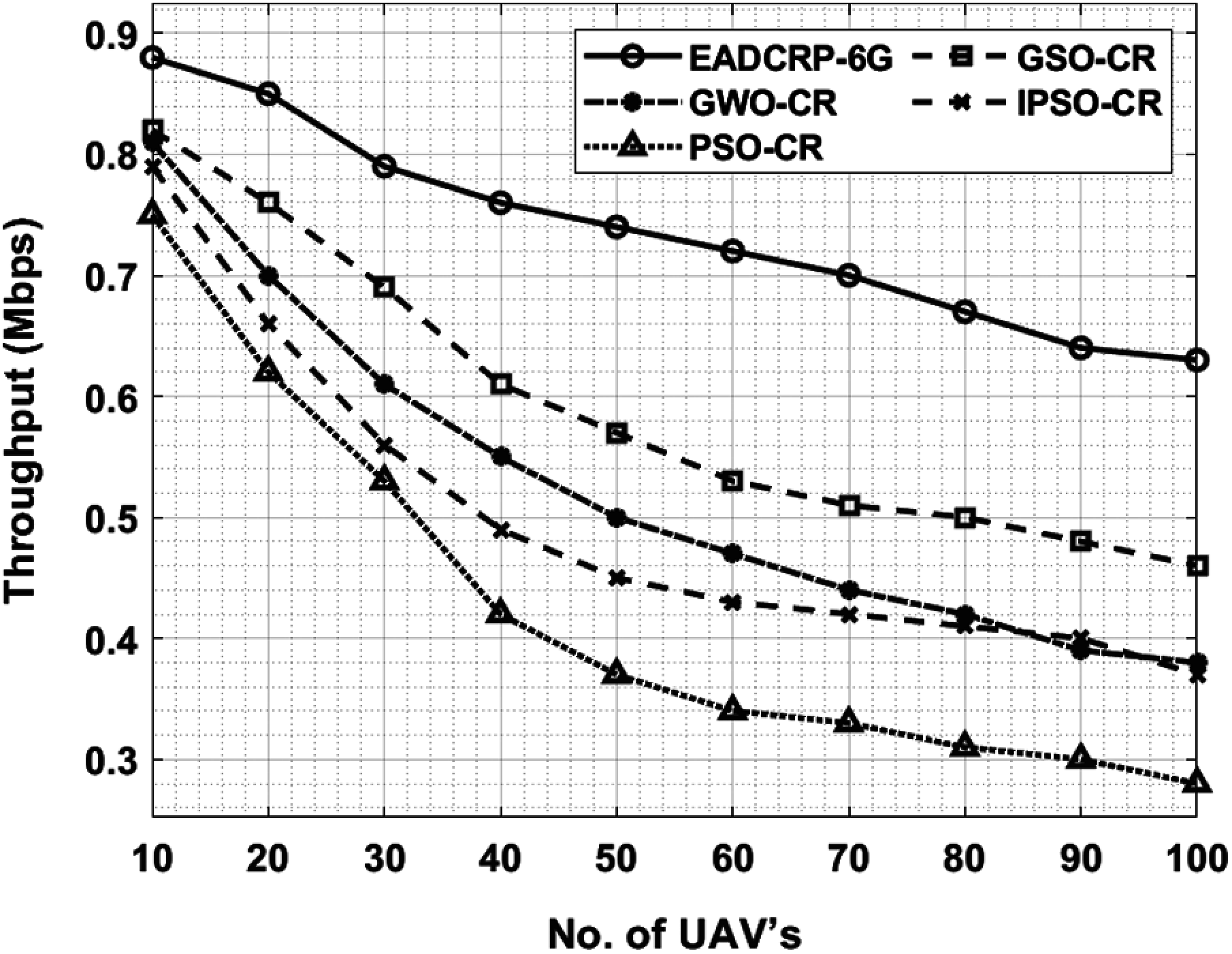
Figure 5: Throughput analysis of EADCRP-6G model
Fig. 6 shows the average delay results of EADCRP-6G method against existing algorithms under different UAVs. From the figure, it can be understood that the proposed EADCRP-6G technique accomplished a better performance over other methods with the least average delay. For instance, under 10 UAVs, the proposed EADCRP-6G method attained a low average delay of 1.94 s, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methodologies reached maximal average delays of 2.07, 2.10, 2.17, and 2.76 s correspondingly. In line with this, at 30 UAVs, EADCRP-6G approach attained the minimum average delay of 2.44 s, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques attained maximum average delay values such as 3.27, 3.55, 4.77, and 6.06 s correspondingly. Likewise, with 50 UAVs, EADCRP-6G technique obtained a minimum average delay of 4.96 s, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR techniques accomplished the maximum average delay time such as 5.77, 5.95, 6.17, and 8.86 s correspondingly. At the same time, with 70 UAVs, EADCRP-6G technique attained a less average delay of 5.88 s, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR methods gained the maximum average delays such as 6.81, 7.15, 7.38, and 9.79 s correspondingly. Finally, with 100 UAVs, the proposed EADCRP-6G manner attained the least average delay of 6.88 s, whereas GSO-CR, GWO-CR, IPSO-CR, and PSO-CR algorithms attained the maximal average delay values such as 8.06, 8.82, 9.09, and 11.79 s correspondingly.
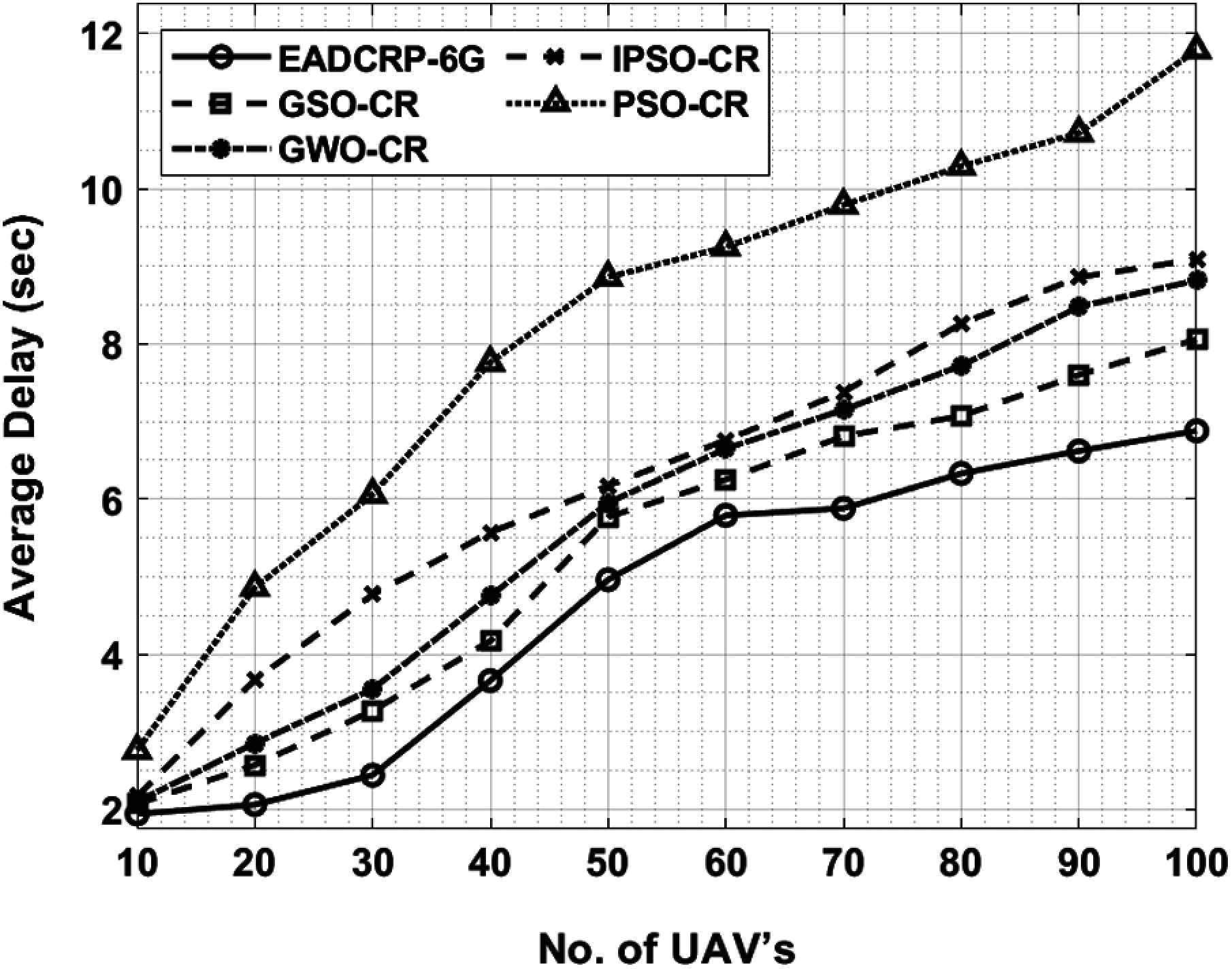
Figure 6: Average delay analysis of EADCRP-6G model
The current research paper presented a novel EADCRP-6G technique to execute effective data collection and communication process in 6G-enabled UAV networks. The proposed EADCRP-6G technique encompasses two major processes namely, IRDAC technique for cluster construction and AFSRP technique for route planning. EADCRP-6G technique includes IRDAC technique in order to elect an optimal set of CHs and organize the selected clusters. Besides, AFSRP technique is deployed to elect an optimum set of routes for UAV communication in 6G networks. In order to validate the enhanced performance of EADCRP-6G technique, a series of simulations was conducted and the outcomes were investigated under different dimensions. The experimental results showcase that the performance of the proposed model got enhanced under different evaluation parameters. In future, effective MAC scheduling techniques can be designed to accomplish effective resource-balanced 6G-enabled UAV networking.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work under Grant Number (RGP 2/209/42), Received by Fahd N. Al–Wesabi. https://www.kku.edu.sa. This research was funded by the Deanship of Scientific Research at Princess Nourah bint Abdulrahman University through the Fast-Track Path of Research Funding Program.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. F. Qi, W. Li, P. Yu, L. Feng and F. Zhou, “Deep learning-based BackCom multiple beamforming for 6G UAV IoT networks,” EURASIP Journal on Wireless Communications and Networking, vol. 2021, no. 1, pp. 50, 2021. [Google Scholar]
2. I. V. Pustokhina, D. A. Pustokhin, E. L. Lydia, M. Elhoseny and K. Shankar, “Energy efficient neuro-fuzzy cluster based topology construction with metaheuristic route planning algorithm for unmanned aerial vehicles,” Computer Networks, vol. 196, pp. 108214, 2021. [Google Scholar]
3. S. Sun, M. Kadoch, L. Gong and B. Rong, “Integrating network function virtualization with SDR and SDN for 4G/5G networks,” IEEE Network, vol. 29, no. 3, pp. 54–59, 2015. [Google Scholar]
4. I. V. Pustokhina, D. A. Pustokhin, P. K. Pareek, D. Gupta, A. Khanna et al., “Energy-efficient cluster-based unmanned aerial vehicle networks with deep learning-based scene classification model,” International Journal of Communication Systems, vol. 34, no. 8, pp. 1–16, 2021. [Google Scholar]
5. M. A. Khan, A. Safi, I. M. Qureshi and I. U. Khan, “Flying ad-hoc networks (FANETsA review of communication architectures, and routing protocols,” in 2017 First Int. Conf. on Latest trends in Electrical Engineering and Computing Technologies (INTELLECTKarachi, pp. 1–9, 2017. [Google Scholar]
6. A. Rajagopal, G. P. Joshi, A. Ramachandran, R. T. Subhalakshmi, M. Khari et al., “A deep learning model based on multi-objective particle swarm optimization for scene classification in unmanned aerial vehicles,” IEEE Access, vol. 8, pp. 135383–135393, 2020. [Google Scholar]
7. A. Khan, F. Aftab and Z. Zhang, “BICSF: Bio-inspired clustering scheme for FANETs,” IEEE Access, vol. 7, pp. 31446–31456, 2019. [Google Scholar]
8. A. Rajagopal, A. Ramachandran, K. Shankar, M. Khari, S. Jha et al., “Fine-tuned residual network-based features with latent variable support vector machine-based optimal scene classification model for unmanned aerial vehicles,” IEEE Access, vol. 8, pp. 118396–118404, 2020. [Google Scholar]
9. B. L. Nguyen, E. L. Lydia, M. Elhoseny, I. V. Pustokhina, D. A. Pustokhin et al., “Privacy preserving blockchain technique to achieve secure and reliable sharing of IoT data,” Computers, Materials & Continua, vol. 65, no. 1, pp. 87–107, 2020. [Google Scholar]
10. Y. Liu, C.-X. Wang, H. Chang, Y. He and J. Bian, “A novel non-stationary 6G UAV channel model for maritime communications,” IEEE Journal on Selected Areas in Communications, vol. 37, pp. 1, 2021. [Google Scholar]
11. Y. Spyridis, T. Lagkas, P. Sarigiannidis, V. Argyriou, A. Sarigiannidis et al., “Towards 6G IoT: Tracing mobile sensor nodes with deep learning clustering in UAV networks,” Sensors, vol. 21, no. 11, pp. 3936, 2021. [Google Scholar]
12. O. M. Bushnaq, M. A. Kishk, A. Celik, M.-S. Alouini and T. Y. Al-Naffouri, “Optimal deployment of tethered drones for maximum cellular coverage in user clusters,” IEEE Transactions on Wireless Communications, vol. 20, no. 3, pp. 2092–2108, 2021. [Google Scholar]
13. Z. Na, Y. Liu, J. Shi, C. Liu and Z. Gao, “UAV-supported clustered NOMA for 6G-enabled internet of things: Trajectory planning and resource allocation,” IEEE Internet Things Journal, vol. 39, pp. 1, 2020. [Google Scholar]
14. M. Faraji-Biregani and R. Fotohi, “Secure communication between UAVs using a method based on smart agents in unmanned aerial vehicles,” The Journal of Supercomputing, vol. 77, no. 5, pp. 5076–5103, 2021. [Google Scholar]
15. F. Qi, W. Li, P. Yu, L. Feng and F. Zhou, “Deep learning-based BackCom multiple beamforming for 6G UAV IoT networks,” EURASIP Journal on Wireless Communications and Networking, vol. 2021, no. 1, pp. 50, 2021. [Google Scholar]
16. S. Tang, W. Zhou, L. Chen, L. Lai, J. Xia et al., “Battery-constrained federated edge learning in UAV-enabled IoT for B5G/6G networks,” Physical Communication, vol. 47, pp. 101381, 2021. [Google Scholar]
17. L. Li, Y. Sun, Q. Cheng, D. Wang, W. Lin et al., “Optimal trajectory and downlink power control for multi-type UAV aerial base stations,” Chinese Journal of Aeronautics, vol. 34, pp. 11–23, 2021. [Google Scholar]
18. H. Kurdi, M. F. AlDaood, S. Al-Megren, E. Aloboud, A. S. Aldawood et al., “Adaptive task allocation for multi-UAV systems based on bacteria foraging behaviour,” Applied Soft Computing, vol. 83, no. 1, pp. 105643, 2019. [Google Scholar]
19. R. Sekaran, M. Ramachandran, R. Patan and F. Al-Turjman, “Multivariate regressive deep stochastic artificial learning for energy and cost efficient 6G communication,” Sustainable Computing: Informatics and Systems, vol. 30, pp. 100522, 2021. [Google Scholar]
20. G. N. Nguyen, N. H. L. Viet, A. F. S. Devaraj, R. Gobi and K. Shankar, “Blockchain enabled energy efficient red deer algorithm based clustering protocol for pervasive wireless sensor networks,” Sustainable Computing: Informatics and Systems, vol. 28, pp. 100464, 2020. [Google Scholar]
21. Q. He, X. Hu, H. Ren and H. Zhang, “A novel artificial fish swarm algorithm for solving large-scale reliability-redundancy application problem,” ISA Transactions, vol. 59, no. 2, pp. 105–113, 2015. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |