DOI:10.32604/cmc.2022.021859

| Computers, Materials & Continua DOI:10.32604/cmc.2022.021859 |  |
| Article |
Evolutionary Algorithm Based Task Scheduling in IoT Enabled Cloud Environment
1Department of Information Science & Engineering, CMR Institute of Technology, Bengaluru, 560037, India
2Department of Computer Science & Engineering, Cambridge Institute of Technology, Bengaluru, 560036, India
3Department of Computer Applications, CMR Institute of Technology, Bengaluru, 560037, India
4Department of Computer Science & Engineering, Swarnandhra College of Engineering and Technology, Narasapur, 534280, India
5Department of Applied Data Science, Noroff University College, Kristiansand, 4612, Norway
6Department of Computer Techniques Engineering, Al-Mustaqbal University College, Hillah, 51001, Iraq
7Department of Computer Science and Engineering, Soonchunhyang University, 31538, Korea
*Corresponding Author: Yunyoung Nam. Email: ynam@sch.ac.kr
Received: 16 July 2021; Accepted: 17 August 2021
Abstract: Internet of Things (IoT) is transforming the technical setting of conventional systems and finds applicability in smart cities, smart healthcare, smart industry, etc. In addition, the application areas relating to the IoT enabled models are resource-limited and necessitate crisp responses, low latencies, and high bandwidth, which are beyond their abilities. Cloud computing (CC) is treated as a resource-rich solution to the above mentioned challenges. But the intrinsic high latency of CC makes it nonviable. The longer latency degrades the outcome of IoT based smart systems. CC is an emergent dispersed, inexpensive computing pattern with massive assembly of heterogeneous autonomous systems. The effective use of task scheduling minimizes the energy utilization of the cloud infrastructure and rises the income of service providers by the minimization of the processing time of the user job. With this motivation, this paper presents an intelligent Chaotic Artificial Immune Optimization Algorithm for Task Scheduling (CAIOA-RS) in IoT enabled cloud environment. The proposed CAIOA-RS algorithm solves the issue of resource allocation in the IoT enabled cloud environment. It also satisfies the makespan by carrying out the optimum task scheduling process with the distinct strategies of incoming tasks. The design of CAIOA-RS technique incorporates the concept of chaotic maps into the conventional AIOA to enhance its performance. A series of experiments were carried out on the CloudSim platform. The simulation results demonstrate that the CAIOA-RS technique indicates that the proposed model outperforms the original version, as well as other heuristics and metaheuristics.
Keywords: Internet of things; cloud computing; task scheduling; metaheuristics; resource allocation
Internet of Things (IoT) [1] permits to achievement of useful and actionable information, multiple tasks, and glean. It also experienced rapid development of objects driven by a gadget of consumers for accessing multimedia files to achieve various tasks that work independently/individually [2]. The fundamental framework of IoT allows objects to connect and collaborate with Internet in a smart manner without human interventions (viz., smart objects). Smart objects can interact, create, and sense ubiquitous environments. Within this environment, data can be used and collected for supporting further decision makings like manufacturing, emergency handling applications, industrial automation, healthcare, logistics, and scheduling in transportation. Moreover, IoT could be viewed as a kind of largescale distributed system like in Cloud Computing (CC) wherein such objects have a higher amount of heterogeneity regarding software and hardware.
In spite of the present connectivity solution, wide-ranging efforts are required in the scheme of a novel framework IoT reference method. As a result, novel method provision is required for resource allocation (RA) and communication to effectively assist huge IoT placement based on devices and services [3]. The novel IoT reference framework needs to scale economically and operationally with the extension of IoT components and provides smart functionality for autonomous reasoning amongst objects. Order to Implement IoT system in the market would provide greater opportunity and allow various services and devices to interact, stream, and connect in small business/single homes. The IoT could be seen as largescale distributed systems in which the modules have a higher amount of heterogeneity regarding hardware and software based on devices and services. The Quality of Services (QoS) for the user accessing IoT supporting with CC is exponentially increasing.
The most significant challenge in the CC domain is resource scheduling (RS). While carrying out RS, at least fulfilling levels of QoS must be preserved with the help of appropriate hardware algorithms and infrastructure [4]. The components of cloud framework, generally denoted as the broker in recent survey, is accountable to map requested end users task to the accessible virtualized hardware i.e., generally executed by means of virtual machine (VM). The broker carries out mapping by implementing the scheduling process. With the development of several available resources and submitted tasks, it has become highly complex for mapping tasks to the proper VMs for implementation [5]. When an improper scheduling process is utilized, few VMs might be under-utilized/over-utilized, and the inference of this scenario leads to degrading the overall performances of the cloud system. The RS problems belonging to the set of NP (non-deterministic polynomial time) hard optimization problems. It must be pointed out that in the modern computer science literature, the terms cloudlet, and task scheduling are also adapted for the procedure of mapping submitted end-user tasks to accessible VMs.
Several IoT application involves various devices attempt to exploit the underutilized assets. The ability of heterogeneous devices and multi-servers for providing different services to the income requests are distributed in a different way. Therefore, the exploitation of heterogeneous server devices and systems should assist in scheduling multiple tasks and share resources for meeting the user QoS needs. Such exploitations are based on the kind of priority of task scheduling, allocation policy selection, and flexibility. There are various kinds of policy selection which have severe limitations to be fulfilled with the potential usage of system resources and applications [6]. Also, almost all the scheduling methods in real world system could not offer an optimum scheduling solution on pre-emptive scheduling when fulfilling their RA needs like tardiness, minimize Makespan, maximum throughput, and utilization ratio in CC when getting huge requests. Ineffective scheduling could lead to lower throughput, excessive utilization, and undesired long delay of IoT resources. The major issue is how to allocate tasks in an effective manner based on minimizing Makespan when fulfilling deadlines and another limitation [7]. Thus, it is vital to suggest a proper scheduling process for facilitating optimum task scheduling to minimize the Makespan of potential use of IoT RA between different heterogeneous systems of devices and servers.
Several techniques and algorithms for RA in CC platform are now accessible. As, in few schemes, traditional (deterministic) algorithm is utilized. But, traditional optimization methods aren't effective because deterministic algorithms cannot generate fulfilling, or optimum, or best solutions within a moderate computation time for NP-hard problems. Because of the exponential number of potential solutions and search space complexity, traditional methods cannot estimate all possible solutions from the search domain in polynomial time [8]. While addressing NP-hard processes like CC-RS, rather than utilizing traditional optimization methods, approaches which estimate only possible portions of the search space (not the entire search domain) with the help of a smart system while selecting that solution to estimate the following, must be used. The effective way for tackling the RS challenge is the execution of metaheuristics and heuristics based methods which don't assurance detecting optimum solutions, but practically, they have proven, that it is capable of generating fulfilling solutions within a polynomial time.
This paper presents an intelligent Chaotic Artificial Immune Optimization Algorithm for Task Scheduling (CAIOA-RS) in IoT enabled cloud environment. The proposed CAIOA-RS algorithm resolves the problem of resource allocation in the IoT enabled cloud environment. It also fulfills the makespan by carrying out the optimal task scheduling process with the different policies of incoming tasks. The design of CAIOA-RS technique integrates the concept of chaotic maps into the traditional AIOA to improve its performance. An extensive set of simulations take place on the CloudSim platform and examined the outcomes interms of different performance measures.
This section performs an extensive survey of different task scheduling algorithms for the IoT enabled CC environment. In Praveenchandar et al. [9], an enhanced task scheduling and an optimum power minimization method are projected for an effective dynamic RA procedure. With the prediction and dynamic resource table upgrading mechanism, efficacy of RA based on response time and task completion is realized. This architecture carries effective results based on power reduction as it decreases the power utilization in data centres. The presented method provides precise values for upgrading resource table. An effective RA is attained using an enhanced task scheduling method and decreased power utilization method.
In Rjoub et al. [10], a trust aware scheduling solution named BigTrustScheduling is projected which contains 3 phases: trust-aware scheduling, VMs trust level computation, and tasks priority level determination. An experiment was carried out on real Hadoop cluster environments with real time dataset gathered and Bit brains task. Hasan et al. [11] proposed a task scheduling approach in terms of CPSO method for solving the problems of resource management and RA in heterogeneous and homogeneous IoT CC. The aim is to fulfill the Makespan by carrying out optimum task scheduling when taking into account various policies of incoming tasks. Abd Elaziz et al. [12] proposed another task scheduling technique for IoT requests in a cloud fog platform. Abdelmoneem et al. [13] developed an effective IoT framework, mobility aware allocation, and scheduling techniques for health care sector. The presented method assists the movement of the patient using an adoptive RSS based handoff system. The presented framework enables dynamic sharing of healthcare tasks between computation nodes either fog devices/cloud devices using execution of a MobMBAR approach.
Ma et al. [14] proposed a deadline and cost aware scheduling approach which decreases the implementation cost of a task under the deadline constraint in the IaaS method. Taking into account the VM acquisition delay and performance variation, firstly they split tasks into various types based on the topological framework thus no dependencies are present among tasks on a similar level. The 3 strings are utilized for coding the genes in the presented method to reflect the resilient and heterogeneous features of cloud environment. Later, HEFT is utilized for generating individuals with minimal cost and completion time. In Basu et al. [15], a cognitive or intelligent method of bioinspired method is utilized for finding an optimum task scheduling for IoT application.
Al-Turjman et al. [16] proposed a cooperative RS in energy constrain application for fault-tolerant and reliable performances. They presented a task scheduling approach in terms of strong CPSO and FIPS approaches for solving the problems of RA in heterogeneous and homogeneous cloud based IoT applications. Xu et al. [17] formulated related task scheduling problems to constrained optimization problems in cloud fog platforms. An LBP-ACS approach is presented for tackling these problems. In this method, an approach of task scheduling is considered the finished deadline and the priority of a task. For handling the sensitivity of task delay, the laxity based priority method is adapted for constructing task scheduling sequences with a moderate priority. While, for minimizing the overall energy utilization, the constrained optimization approach depends on ACO method is utilized for obtaining the accurate optimum scheduling system around the world.
3 The Proposed Task Scheduling Technique
Fig. 1 demonstrates the overall working process of proposed method. For solving the issue of resource optimization within the cloud structure, a standard CC technique. This technique utilized in this investigation is same as the approach. The cloud scheme has several geographically distributed data centers (DC) related to internet. Initially, the DC has several compute and store servers and other needed resources. The server in all DCs are linked utilizing consistent and high bandwidth communication networks. So, in this presented technique, communication delay was regarded as negligible. During the presented technique, user accesses the cloud resource with user interfaces. In cloud manager accomplishes every resource utilizing distinct cloud components, for instance, the network modules, image modules, pricing modules, and certification modules, and so on. The user task is allocated amongst distinct DCs obtainable in cloud framework. All DCs separates the user tasks as to various subtasks and allocates them amongst the accessible Processing Elements (PE's) in respective DCs. The presented task scheduling scheme in the structure was responsible for effectively shared of user tasks as to distinct existing servers with objective of optimizing energy utilization and profit of service providers.
In this technique, the cloud applications are regarded as gathered of user jobs which perform difficult computing tasks with utilizing cloud resources. Assume that
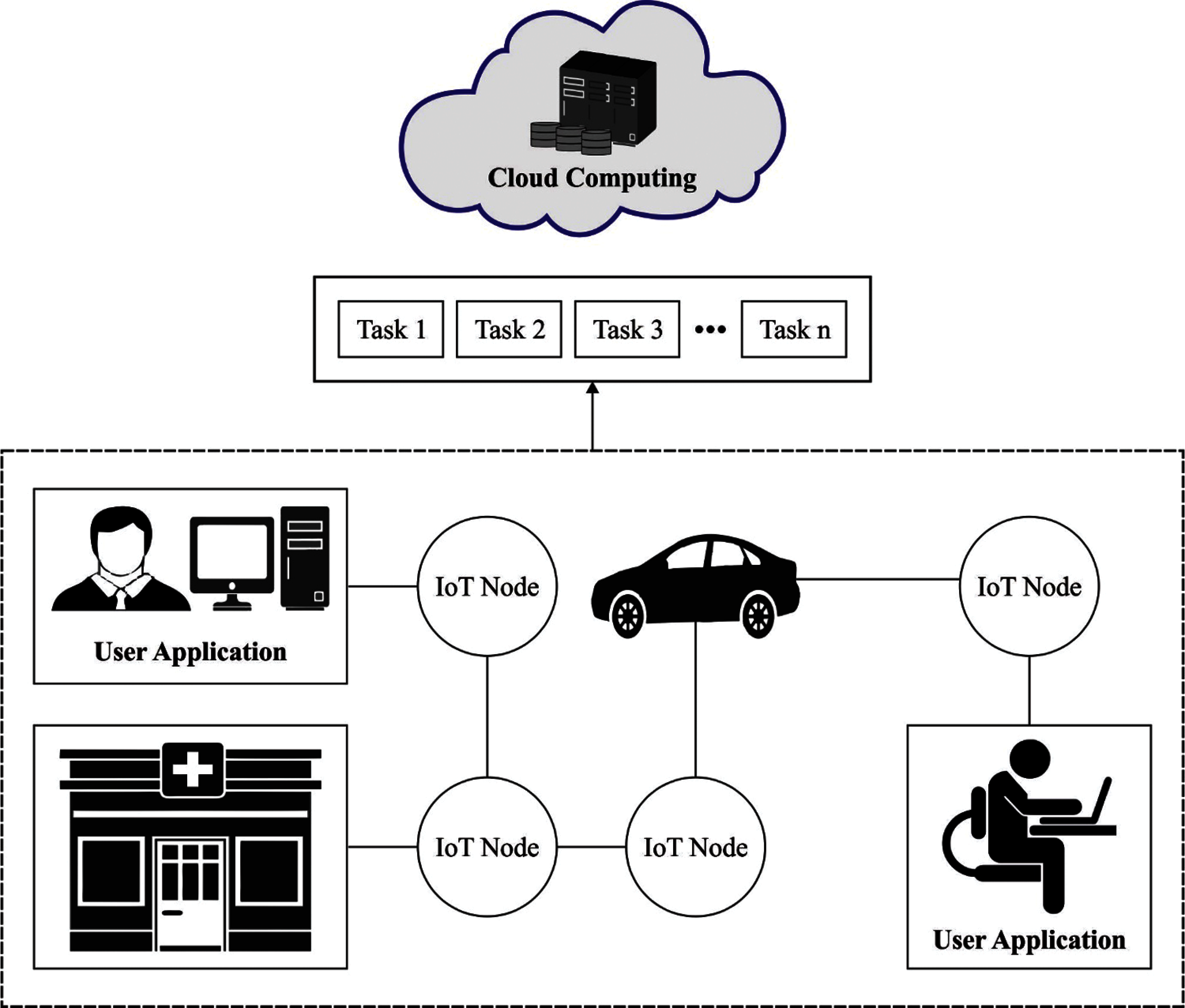
Figure 1: Overall process of proposed method
Supposing user jobs
Thus, the entire time essential for completing the user job as
where
The Energy utilization for computing the user jobs
where
The cost for processing the user job as DC
where
The consumption
The main functions of this presented technique are written as:
Subjected to:
• The user job necessity end before deadline
• All user jobs are assigned to only one DC.
• The amount of user jobs are lesser than the amount of existing DC at a specific time.
3.3 Design of CAIOA for Task Scheduling
In order to flexible task scheduling issues in cloud model, it examined the permutation based encoded technique, i.e., the assignment of integer number to every job and the order of all the jobs signifies the processing order. For instance, there are 5 jobs that exist processing with 3 stages, and in every stage, there are many parallel devices. The processing time to all tasks on every device is 3, 2, and 2 parallel devices in 3 stages correspondingly. To provide one solution {1, 2, 3, 4, 5}, it implies that in the initial stage in cloud modal, the processing order of jobs is
Once the scheduling order was defined as subsequent work is for assigning the candidate devices to process it [19]. During this case, it can employ the easy but effectual manner for assigning the device to process the task, and it can be provided as:
1. At the beginning stage, all tasks are allocated to device with minimal completion time, i.e., the device existing as initial as feasible.
2. Once the task is finished their work is in the present stage, allocate it to subsequent stage directly and elect the devices with simplest idle time.
AIOA operator includes: operator calculation of individual level, affinity evaluation operator, immune selection operator, incentives meter calculate son, operator, population suppression cloning, mutation operator, and Refresh operator clone (individual multiplication) operator. Using GA and related intelligent optimization methods, artificial immune method to depend on evolution optimization procedure operator to attain. As the encoding method might be a discrete, different, real number coding techniques in the operator would be distinct.
Antibody Density Operator
Whereas Ai denotes the initial
The antibody is generally the evaluation of excitation levels that could be utilized antibodies density and affinity in calculating the outcomes of numerical operation. Antibodies incentive amounts (sim (x):
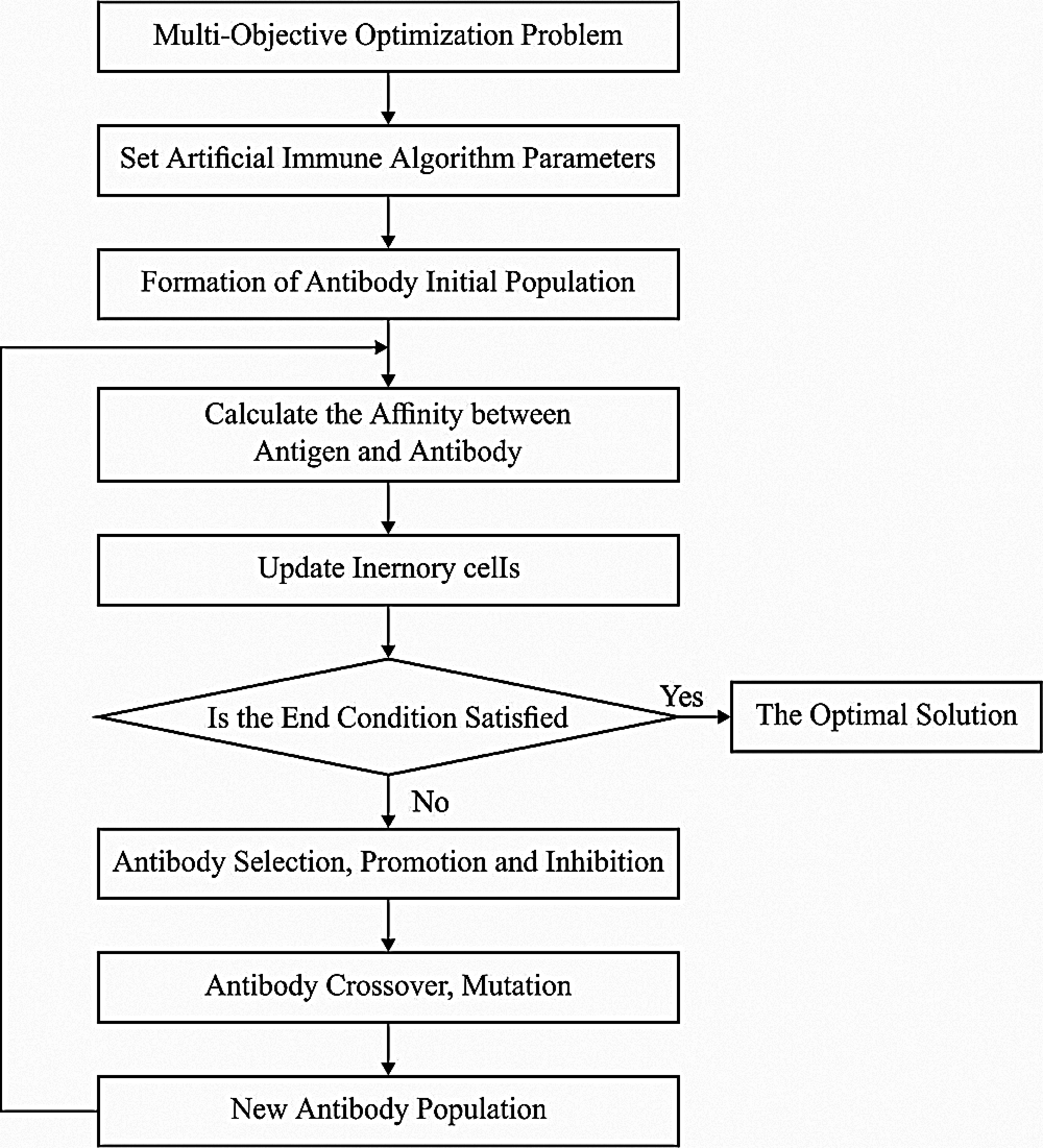
Figure 2: Flowchart of AIOA
In stocks to refresh operator
Incentives in the higher antibody set of antibodies using improved quality individual are highly possible to be chosen for selecting clone operator, highly useful in the search space, the search region for staring local search.
Inhibit in the cloning procedure, the clone part of mutation operator and operator operation antibody using temporary antibodies population attained afterward the creation of a general set of Xi (antibodies cloning Ai mutation result using the structure, prevent the actions would save this clone set the maximum affinity antibodies, inhibit of other antibodies.
One of the meta-heuristic techniques is arbitrariness parameters. This parameter is utilizing probability distributions, generally Gaussian or uniform distribution. In recent times, the chaos model has been utilized for enhancing these parameters. It is similar features as arbitrariness, with optimum dynamical as well as statistical features. The chaos is named a phenomenon. Some changes of primary state of chaos can lead to nonlinear modify to the future performance. 3 important properties are explaining the chaos; (i) quasi-stochastic, (ii) ergodicity, and (iii) sensitivity to primary criteria. Mixing of these features guarantees the diversity of created solution. Therefore, this diversity is sufficient for reaching all modes of multi-modal issues. In quasi-stochastic has determined as capability for replacing arbitrary variable with value of chaotic map. In ergodic properties refer to capability of chaotic variables for searching non-repeatedly every state within a particular range. Eventually, the sensitivity to primary state property is determined as some tiny modification, at the beginning initial points, can leads to distinct performance. Relating to every property is considerably boosted the efficiency of meta-heuristic optimization techniques. During this case, ten distinguished non-invertible maps with various features are utilized. During this work, a primary point to every adopted chaotic map has primarily been set to 0.7. This value is similar value utilized to similar ten chaotic maps.
At the CAIOA technique, the arbitrary established is substituted by chaotic initialization, i.e., the initialization of
where Xid implies the dth dimensional of place of ith antibody, n represents the amount of decision variables, Xmax,d and Xmin,d signifies the upper and lower bounds of dth decision variables, and chaos(.) refers the standard chaotic map functions.
This section examines the performance of the proposed CAIOA-RS technique with existing techniques. The proposed CAIOA-RS technique is validated on the synthetic datasets and the results are investigated under different numbers/sizes of tasks. There are different types of tasks such as extra-large (800–1000 tasks), large (600–700 tasks), medium (400–500 tasks), and small (100–200 tasks). A comprehensive comparison analysis of the CAIOA-RS technique with existing techniques interms of average turnaround time (ATAT) and average response time (ART) is in Tab. 1.
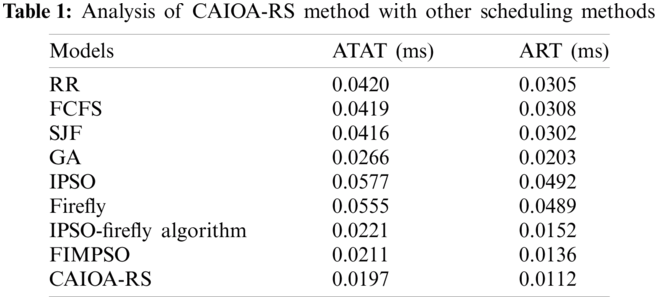
Fig. 3 investigates the ATAT analysis of the CAIOA-RS technique with existing techniques. The results demonstrated that the IPSO and Firefly algorithms have demonstrated ineffective outcomes with the ATAT of 0.0577 and 0.055 ms, respectively. In line with, the RR, FCFS, and SJF techniques have obtained moderate outcomes with the ATAT of 0.042, 0.0419, and 0.0416 ms, respectively. Likewise, the GA, IPSO-Firefly algorithm, and FIMPSO techniques have showcased competitive performance with the ATAT of 0.0266, 0.0221, and 0.0211 ms, respectively. However, the proposed CAIOA-RS technique has showcased effectual outcomes with the ATAT of 0.0197 ms.
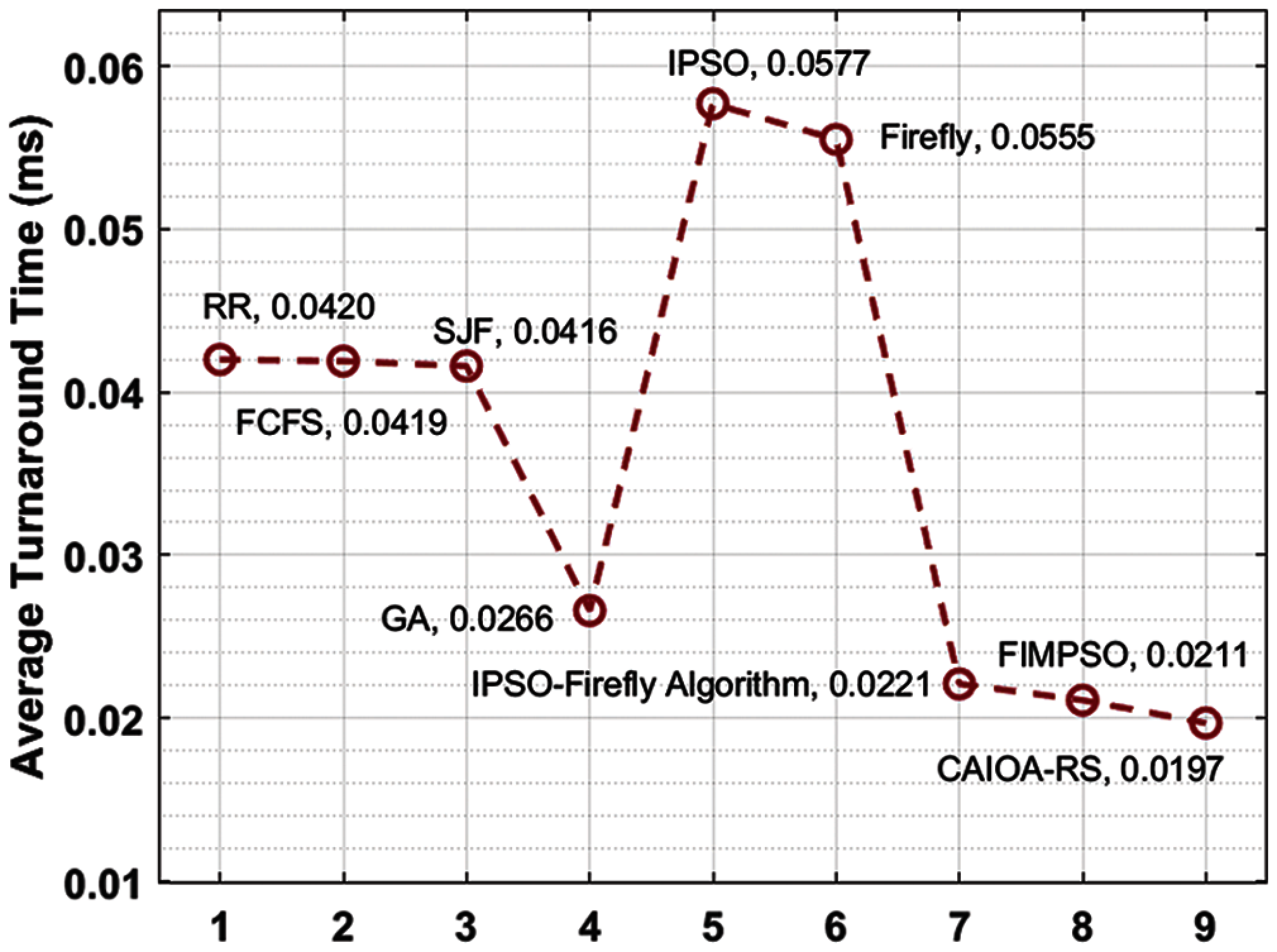
Figure 3: Result analysis of CAIOA-RS method interms of ATAT
Fig. 4 examines the ART analysis of the CAIOA-RS approach with recent methods. The outcomes exhibited that the IPSO and Firefly manners have portrayed ineffective results with the ART of 0.0492 and 0.0489 ms, correspondingly. Also, the FCFS, RR, and SJF algorithms have reached moderate outcomes with the ART of 0.0308, 0.0305, and 0.0302 ms, correspondingly. In line with, the GA, IPSO-Firefly algorithm, and FIMPSO manners have depicted competitive performance with the ART of 0.0203, 0.0152, and 0.0136 ms, correspondingly. Finally, the projected CAIOA-RS methodology has outperformed effectual results with the ART of 0.0112 ms.
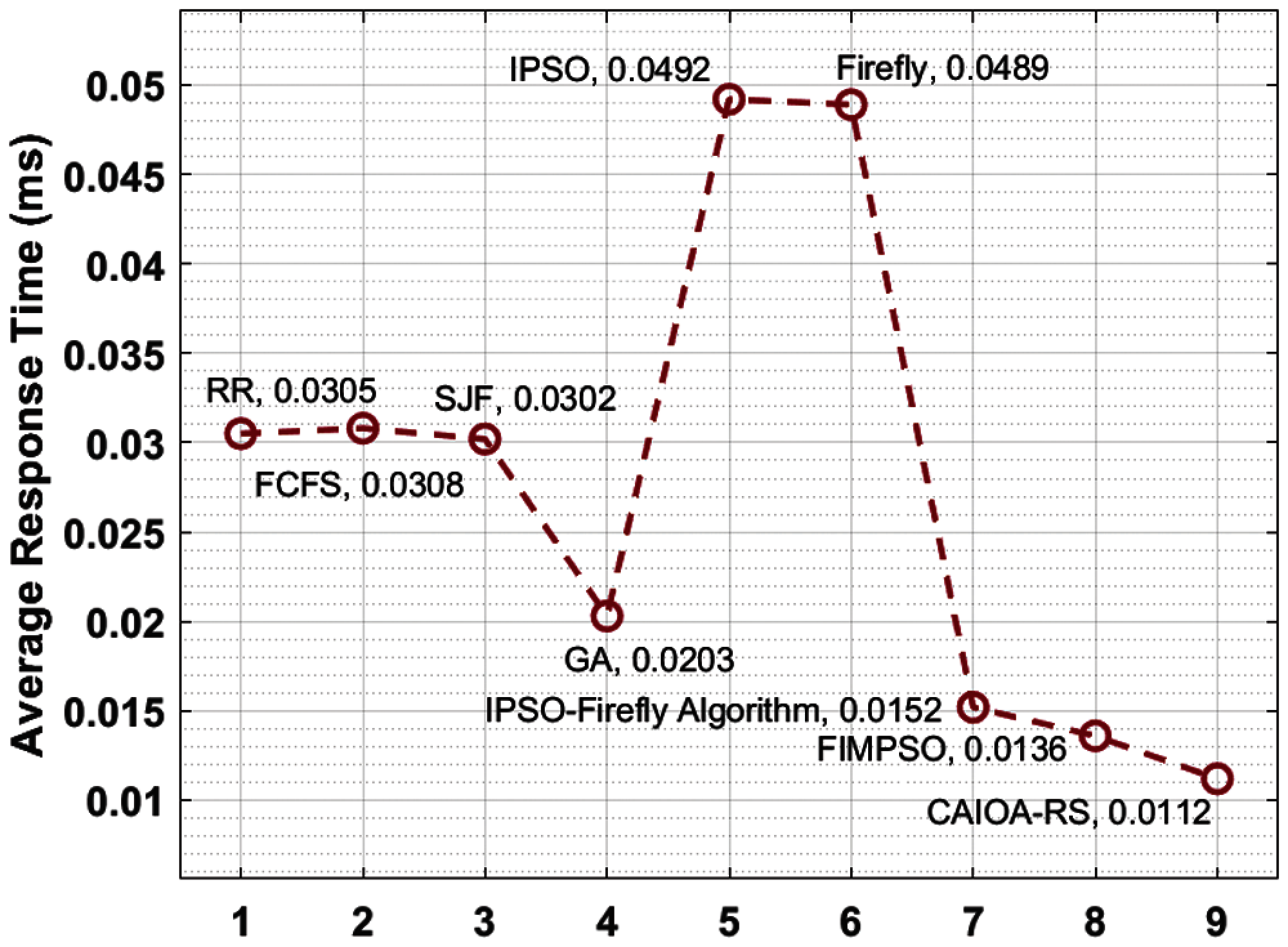
Figure 4: Result analysis of CAIOA-RS method interms of ART
Tab. 2 demonstrates the comparative analysis of CAIOA-RS method with existing techniques interms of CPU utilization, memory utilization, makespan, and average throughput. A CPU utilization of the CAIOA-RS technique with existing techniques in Fig. 5. The figure demonstrated that the CAIOA-RS technique has accomplished improved performance over the other techniques. Meanwhile, the RD and WRR methods have obtained poor CPU utilization over the other techniques. Likewise, the DLB and LB-BC techniques have demonstrated effectual outcome slightly improved CPU utilization over the earlier methods. In the same way, the LB-RC and IPSOF techniques have portrayed moderate CPU utilization performance. Meanwhile, the IPSOF and FIMPSO algorithms have accomplished competitive CPU utilization performance. Finally, the CAIOA-RS technique has resulted in a higher CPU utilization over the other techniques.
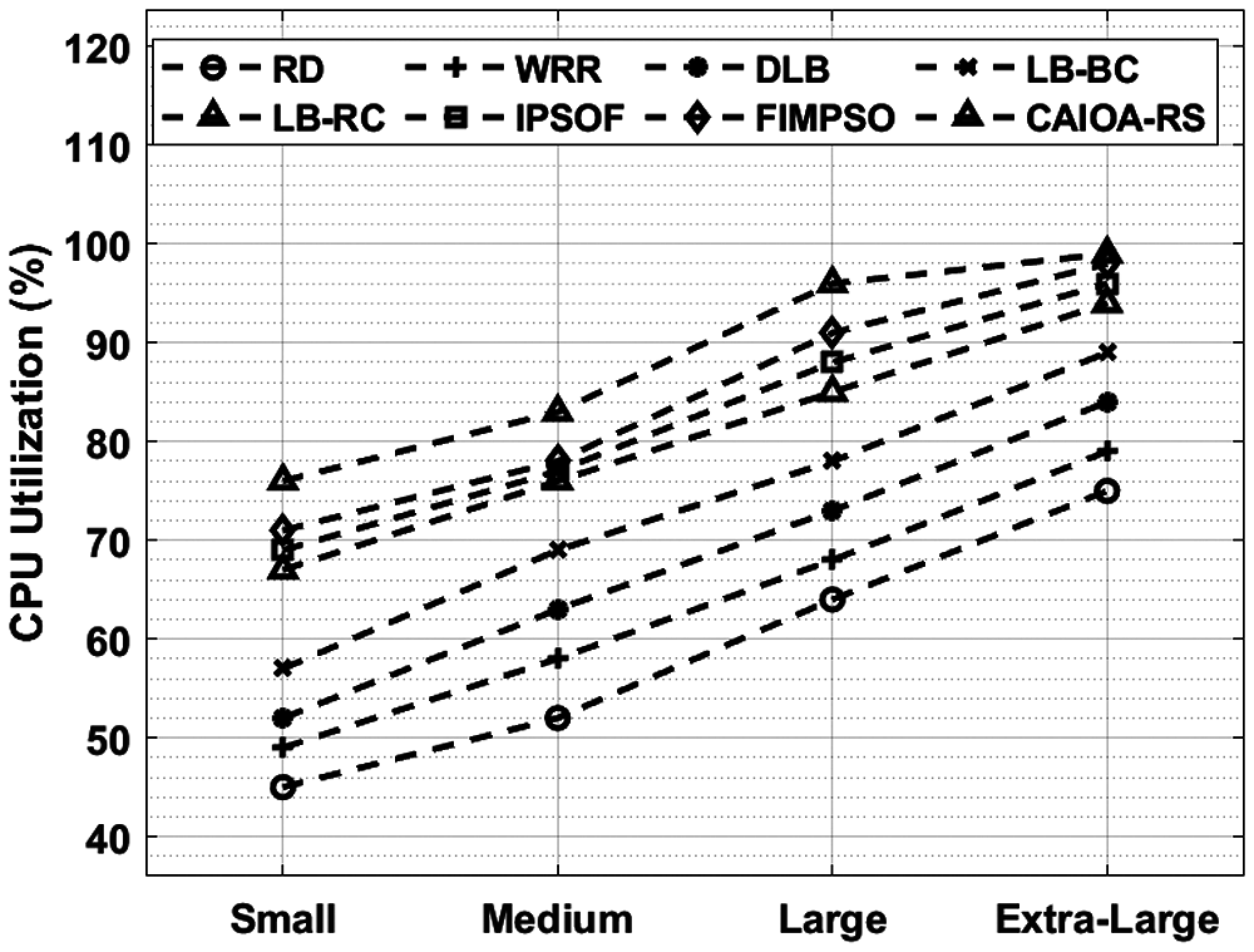
Figure 5: Comparative CPU utilization analysis of CAIOA-RS techniques
Memory utilization of the CAIOA-RS approach with recent methods in Fig. 6. The figure outperformed that the CAIOA-RS manner has accomplished enhanced performance over the other approaches. Also, the RD and WRR approaches have gained worse memory utilization over the other methods. Similarly, the DLB and LB-BC techniques have outperformed effectual outcome somewhat increased memory utilization over the earlier techniques. In addition, the LB-RC and IPSOF approaches have showcased moderate memory utilization performance. In the meantime, the IPSOF and FIMPSO methodology have accomplished competitive memory utilization performance. Eventually, the CAIOA-RS approach has resulted in superior memory utilization over the other algorithms.
Fig. 7 examines the performance of the proposed CAIOA-RS technique with existing techniques that take place interms of makespan. The figure showcased that the RD and WRR models have accomplished ineffective performance with the higher makespan. In addition, the DLB and LB-BC techniques have obtained somewhat performance with the moderate makespan. Followed by, the IPSOF and FIMPSO techniques have accomplished near optimal performance with the competitive makespan. At last, the CAIOA-RS technique has resulted in a lower makespan under different types of tasks.
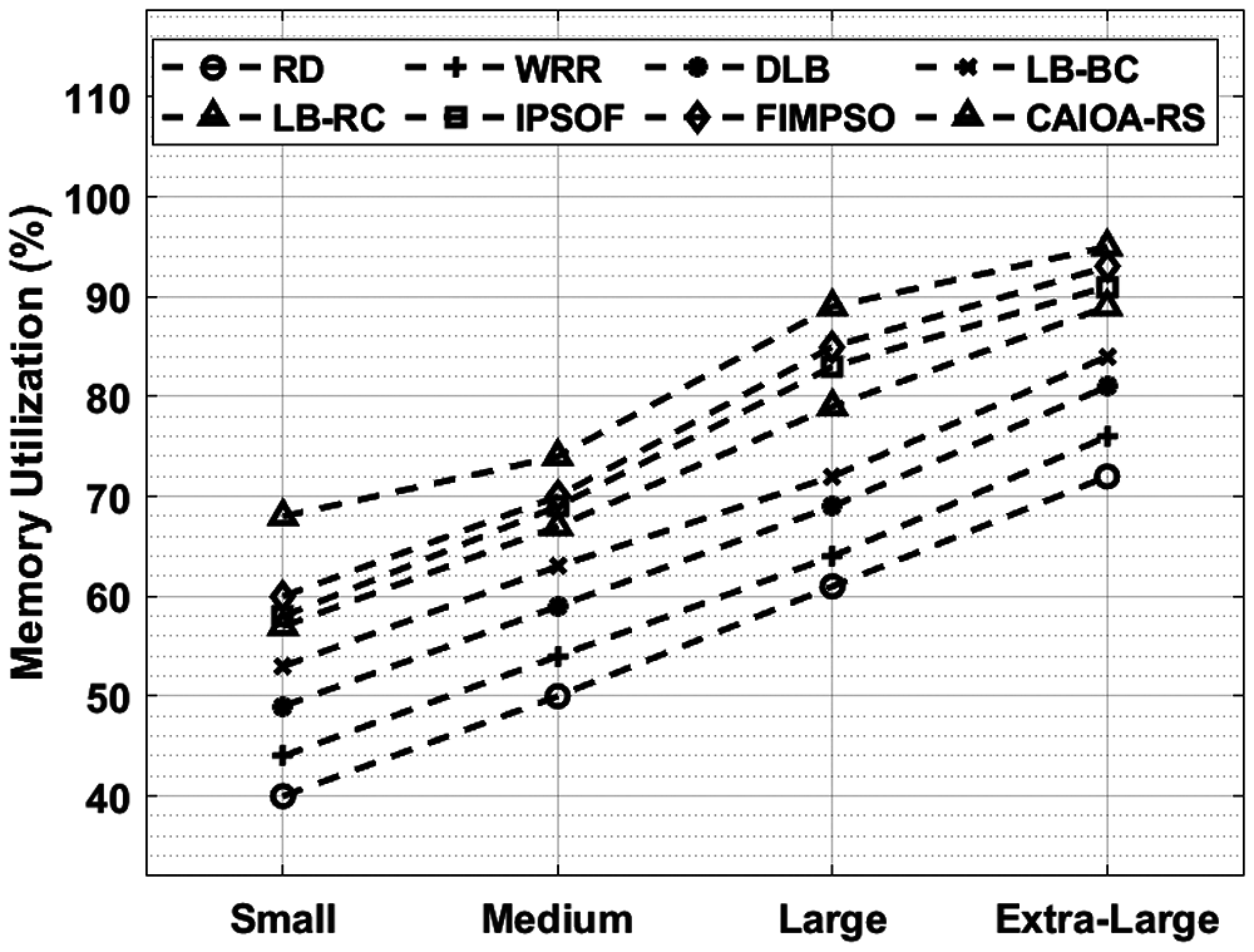
Figure 6: Memory utilization analysis of CAIOA-RS with existing techniques
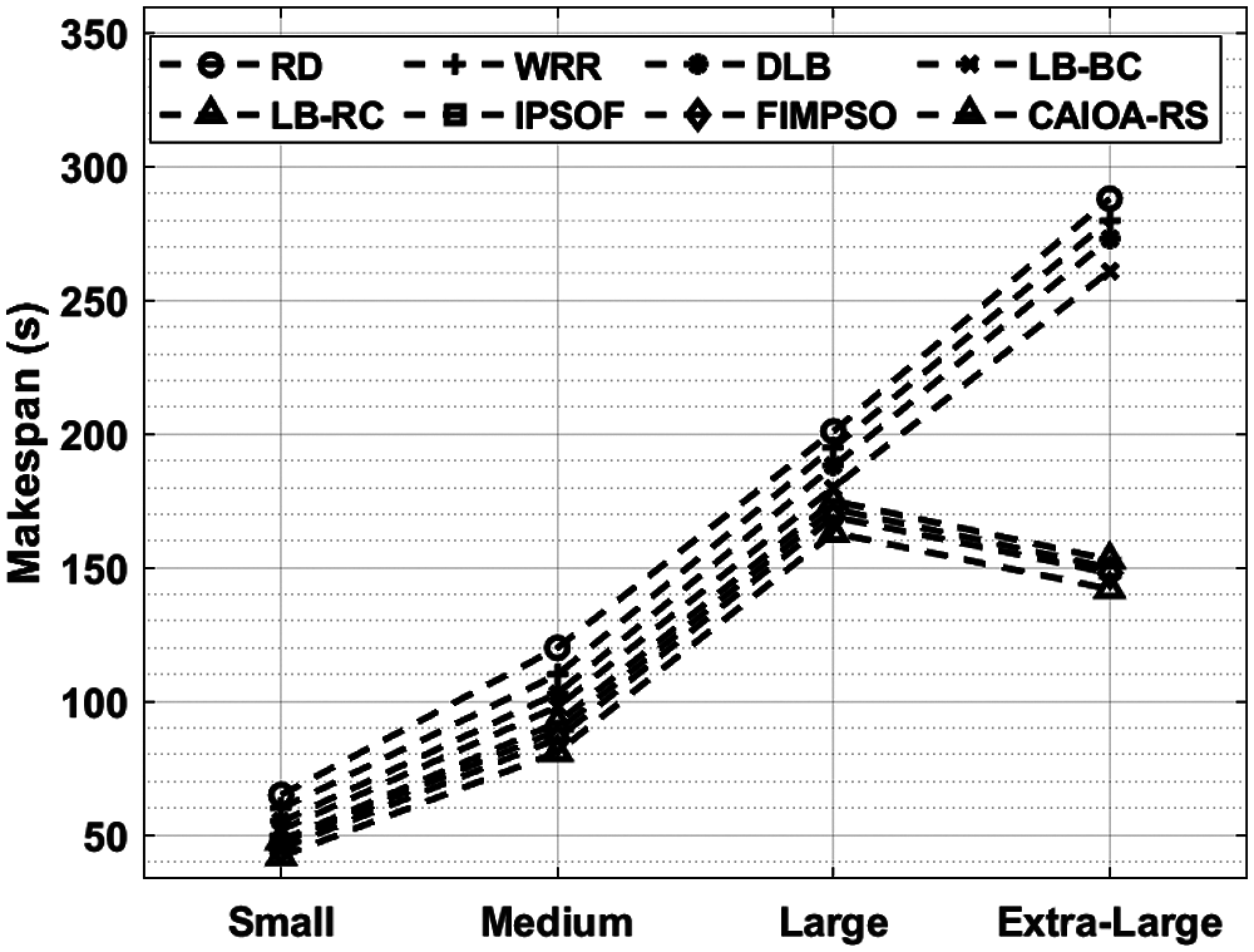
Figure 7: Makespan analysis of CAIOA-RS model with other approaches
Finally, an average throughput of the CAIOA-RS approach with existing algorithms in Fig. 8. The figure outperformed that the CAIOA-RS technique has accomplished higher efficiency over the other manners. Afterward, the RD and WRR algorithms have achieved least average throughput over the other methods. Concurrently, the DLB and LB-BC techniques have displayed effectual results slightly maximum average throughput over the earlier approaches. Besides, the LB-RC and IPSOF algorithms have demonstrated moderate average throughput performance. Meanwhile, the IPSOF and FIMPSO technique have accomplished nearly optimum average throughput performance. Lastly, the CAIOA-RS methodology has resulted in a superior average throughput over the other algorithms.
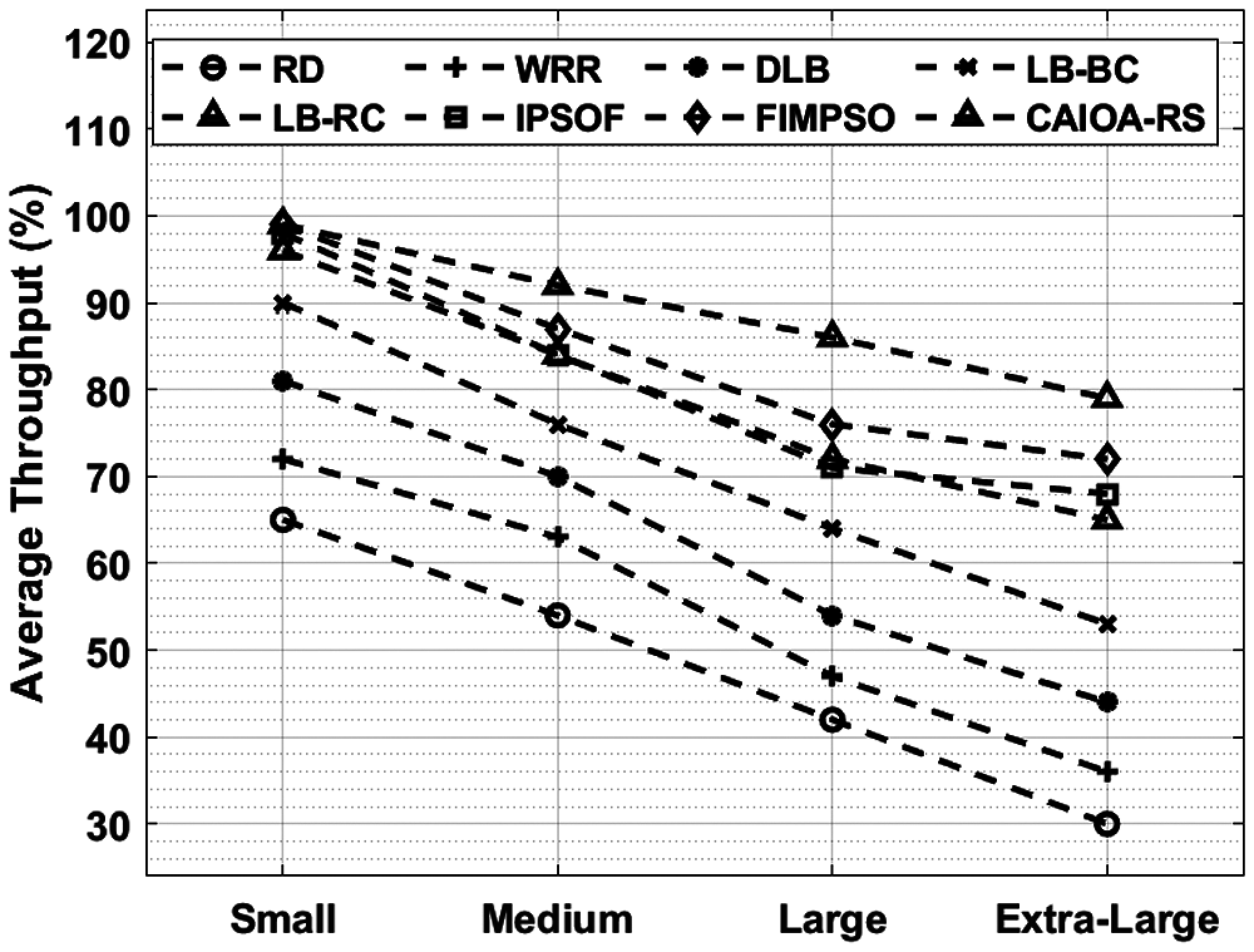
Figure 8: Average throughput analysis of CAIOA-RS model with existing techniques
This paper has developed an effective CAIOA-RS technique in the IoT enabled cloud environment. The proposed CAIOA-RS algorithm resolved the problem of resource allocation in the IoT enabled cloud environment. It also satisfies the makespan by carrying out the optimum task scheduling process with the distinct strategies of incoming tasks. The design of CAIOA-RS technique incorporates the concept of chaotic maps into the conventional AIOA to enhance its performance. An extensive simulation analysis is performed on the CloudSim platform and assessed the outcomes interms of different performance measures. The simulation results demonstrate that the CAIOA-RS technique indicates that the proposed model is superior to other techniques. As a part of future scope, data offloading mechanism can be designed to accomplish optimum resource allocation in the IoT enabled cloud environment.
Funding Statement: This research was supported by Korea Institute for Advancement of Technology(KIAT) grant funded by the Korea Government(MOTIE) (P0012724, The Competency Development Program for Industry Specialist) and the Soonchunhyang University Research Fund.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. K. Shankar, E. Perumal, M. Elhoseny and P. Thanh Nguyen, “An iot-cloud based intelligent computer-aided diagnosis of diabetic retinopathy stage classification using deep learning approach,” Computers, Materials & Continua, vol. 66, no. 2, pp. 1665–1680, 2021. [Google Scholar]
2. M. Z. Hasan and F. Al-Turjman, “Optimizing multipath routing with guaranteed fault tolerance in internet of things,” IEEE Sensors Journal, vol. 17, no. 19, pp. 6463–6473, 2017. [Google Scholar]
3. N. A. B. Namboothiri and R. J. S. Raj, “A comparative study on job scheduling algorithm augmenting load balancing in cloud,” in 2016 Second Int. Conf. on Science Technology Engineering and Management (ICONSTEMChennai, India, pp. 582–588, 2016. [Google Scholar]
4. R. J. S. Raj and S. V. M. Prasad, “Survey on variants of heuristic algorithms for scheduling workflow of tasks,” in 2016 Int. Conf. on Circuit, Power and Computing Technologies (ICCPCTNagercoil, India, pp. 1–4, 2016. [Google Scholar]
5. A. F. S. Devaraj, M. Elhoseny, S. Dhanasekaran, E. L. Lydia and K. Shankar, “Hybridization of firefly and improved multi-objective particle swarm optimization algorithm for energy efficient load balancing in cloud computing environments,” Journal of Parallel and Distributed Computing, vol. 142, pp. 36–45, 2020. [Google Scholar]
6. Y. Zhang and J. Sun, “Novel efficient particle swarm optimization algorithms for solving QoS-demanded bag-of-tasks scheduling problems with profit maximization on hybrid cloud,” Concurrency and Computation: Practice and Experience, vol. 29, no. 21, pp. e4249, 2017. [Google Scholar]
7. K. Shankar, “Iot with cloud based end to end secured disease diagnosis model using light weight cryptography and gradient boosting tree,” Recent Advances in Computer Science and Communications, vol. 14, no. 8, pp. 1–8, 2021. [Google Scholar]
8. T. Vaiyapuri, V. S. Parvathy, V. Manikandan, N. Krishnaraj, D. Gupta et al., “A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for IoT based mobile edge computing,” Wireless Pers. Commun., Ahead of Print, 2021. https://doi.org/10.1007/s11277-021-08088-w. [Google Scholar]
9. J. Praveenchandar and A. Tamilarasi, “Dynamic resource allocation with optimized task scheduling and improved power management in cloud computing,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, no. 3, pp. 4147–4159, 2021. [Google Scholar]
10. G. Rjoub, J. Bentahar and O. A. Wahab, “Bigtrustscheduling: Trust-aware big data task scheduling approach in cloud computing environments,” Future Generation Computer Systems, vol. 110, pp. 1079–1097, 2020. [Google Scholar]
11. M. Z. Hasan and H. Al-Rizzo, “Task scheduling in internet of things cloud environment using a robust particle swarm optimization,” Concurrency and Computation: Practice and Experience, vol. 32, no. 2, pp. e5442, 2020. [Google Scholar]
12. M. Abd Elaziz, L. Abualigah and I. Attiya, “Advanced optimization technique for scheduling IoT tasks in cloud-fog computing environments,” Future Generation Computer Systems, vol. 124, pp. 142–154, 2021. [Google Scholar]
13. R. M. Abdelmoneem, A. Benslimane and E. Shaaban, “Mobility-aware task scheduling in cloud-Fog IoT-based healthcare architectures,” Computer Networks, vol. 179, pp. 107348, 2020. [Google Scholar]
14. X. Ma, H. Gao, H. Xu and M. Bian, “An IoT-based task scheduling optimization scheme considering the deadline and cost-aware scientific workflow for cloud computing,” EURASIP Journal on Wireless Communications and Networking, vol. 2019, no. 1, pp. 249, 2019. [Google Scholar]
15. S. Basu, M. Karuppiah, K. Selvakumar, K. C. Li, S. K. HafizulIslam et al., “An intelligent/cognitive model of task scheduling for IoT applications in cloud computing environment,” Future Generation Computer Systems, vol. 88, pp. 254–261, 2018. [Google Scholar]
16. F. Al-Turjman, M. Z. Hasan and H. Al-Rizzo, “Task scheduling in cloud-based survivability applications using swarm optimization in IoT,” Transactions on Emerging Telecommunications Technologies, vol. 30, no. 8, pp. 1–20, 2019. [Google Scholar]
17. J. Xu, Z. Hao, R. Zhang and X. Sun, “A method based on the combination of laxity and ant colony system for cloud-fog task scheduling,” IEEE Access, vol. 7, pp. 116218–116226, 2019. [Google Scholar]
18. R. K. Jena, “Task scheduling in cloud environment: A multi-objective ABC framework,” Journal of Information and Optimization Sciences, vol. 38, no. 1, pp. 1–19, 2017. [Google Scholar]
19. J. Li and Y. Han, “A hybrid multi-objective artificial bee colony algorithm for flexible task scheduling problems in cloud computing system,” Cluster Computing, vol. 23, no. 4, pp. 2483–2499, 2020. [Google Scholar]
20. M. Mobini, Z. Mobini and M. Rabbani, “An artificial immune algorithm for the project scheduling problem under resource constraints,” Applied Soft Computing, vol. 11, no. 2, pp. 1975–1982, 2011. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |