DOI:10.32604/cmc.2022.022224

| Computers, Materials & Continua DOI:10.32604/cmc.2022.022224 |  |
| Article |
Design of Nonlinear Components Over a Mordell Elliptic Curve on Galois Fields
1Department of Mathematics, Quaid-i-Azam University, Islamabad, Pakistan
2College of Computing and Information Technology, University of Tabuk, Tabuk, 71491, Saudi Arabia
3Department of Mathematics, College of Science, King Khalid University, Abha, Saudi Arabia
*Corresponding Author: Hafeez ur Rehman. Email: hrehman@math.qau.edu.pk
Received: 31 July 2021; Accepted: 02 September 2021
Abstract: Elliptic curve cryptography ensures more safety and reliability than other public key cryptosystems of the same key size. In recent years, the use of elliptic curves in public-key cryptography has increased due to their complexity and reliability. Different kinds of substitution boxes are proposed to address the substitution process in the cryptosystems, including dynamical, static, and elliptic curve-based methods. Conventionally, elliptic curve-based S-boxes are based on prime field
Keywords: Galois field; elliptic curve; S-box; nonlinearity
The rapid growth of digital technology and network communications has improved electronic data transmission across many networks over the last few decades. Since most communication networks are open, the privacy of sensitive data transmission across that network is controversial, raising numerous concerns. The study of cryptography is the study of how to address the challenge of secure transformation. Therefore, Cryptographers have paid close attention to the security of sensitive data in recent decades. The researchers have suggested different types of informative security techniques to combat modern information security attacks. Shift cipher, hill cipher, transposition cipher, and various versions were the most prominent classical cryptosystems. In many well-known cryptosystems, including AES, S-box is used as a nonlinear component [1]. The safety of such cryptosystems is therefore dependent on the cryptographic properties of respective S-boxes. The Rijndael block cipher [2] has been adopted by the National Institute of Standards and Technology (NIST) as an Advanced Encryption Standard (AES). Because of the significance of AES, many researchers investigated the cryptographic characteristics of its S-box. Since S-box plays an essential role in AES, numerous cryptographers have proposed different S-box transformations based on various mathematical structures. An S-boxes passed specific tests, such as nonlinearity, approximation, strict avalanche, and bit independence. In that case, it is cryptographically enough to obtain the desired confusion. Several schemes based on different structures were designed to develop this nonlinear component of the block ciphers [3–7]. So, there is a lack of a parallel and less intricate scheme to design a nonlinear component of the block cipher.
Elliptic curves are also used in the development of powerful cryptosystems. Elliptic curve-based techniques are the most widely deployed to increase the security of information. Specifically, We will concentrate on elliptic curve cryptography (ECC) and the various methods put forward by various researchers throughout this area. Miller [8] proposed the first scheme to use the elliptic curve as a public key cryptosystem in 1985. In addition, a cryptosystem is supplied that is 20% efficient than the Diffie-Hellman algorithm. Reference [9] presents a relationship between the nonlinearity of rational functions over
The following are the primary motivations for this study to improve the strength of S-boxes over elliptic curves and their application in different cryptosystems.
1. Usually, the elliptic curves are considered over prime fields to construct S-boxes, and the generation of S-box is not possible for each input EC.
2. Moreover, the prime field dependent S-boxes do not address the maximum number of S-box possibilities.
3. In [15], they considered elliptic curve over the 16 order Galois field
The drawbacks of existing schemes prompt us to present this new scheme. The following steps will explain how to sum up the entire manuscript.
1. We used a simple method instead of arduous S-boxes designing algorithms with outstanding results to construct 8 × 8 S-boxes in the proposed work.
2. In this work, to generate elliptic curve points, we considered Mordell elliptic curve interpreted over the Galois fields
3. Inverse function under prescribed Galois field and primitive irreducible polynomial as for the generation of elliptic curve points applied to the pairs of elliptic curve points.
4. To get the different number of S-boxes, one can vary the parameter b of the Mordell elliptic curve or alter the primitive irreducible polynomial of a degree corresponding to the Galois field over the binary field.
The remaining paperwork is as follows: In Section 2, we offered some preliminary information. Section 3 discusses the proposed algorithm. In Section 4, we evaluated the designed S-boxes performance indices and compared them to other preexisting S-boxes. The application of designed S-boxes in image encryption algorithm and majority logic criterion is also carried out in Section 4. In the end, Section 5 presents some convincing remarks.
Some basic and essential concepts about the elliptic curves, Galois fields, Euler's totient function, irreducible polynomials, and primitive polynomials are reviewed in this section.
Galois fields, often known as Finite fields, are the foundations of any cryptographic theory, denoted by
Reference [17] presents Euler's phi function, also called Euler's totient function
2.3 Primitive Polynomials and Galois Fields
In [18], Some basic definitions are stated in this section of reducible, irreducible, and primitive polynomials over the Galois field. In this section,
There is precisely one finite field for every prime number p and positive integer n having order
If
If
For any prime p greater than
The Galois field
2.5.1 Addition and Subtraction in
As we work on the field of characteristic
Let
And if
Then
Note that whenever we multiply two polynomials or to find the multiplicative inverse of polynomial, both require coefficient modulo
In this section, we discussed two different S-box algorithm approaches. In the first technique, the nonlinear component of a block cipher is developed using Mordell elliptic curve interpreted over 256 order Galois field. In the second technique, instead of deploying 256 order Galois field dependent S-boxes, we construct a different number of
3.1 Construction of S-Box Using Mordell Elliptic Curve Over Galois Field GF(28)
Choose primitive polynomial
One can choose independently any other primitive polynomial of degree
where b is any element of Galois field except zero. The specialty of this curve is that when we choose Mordell elliptic curve over
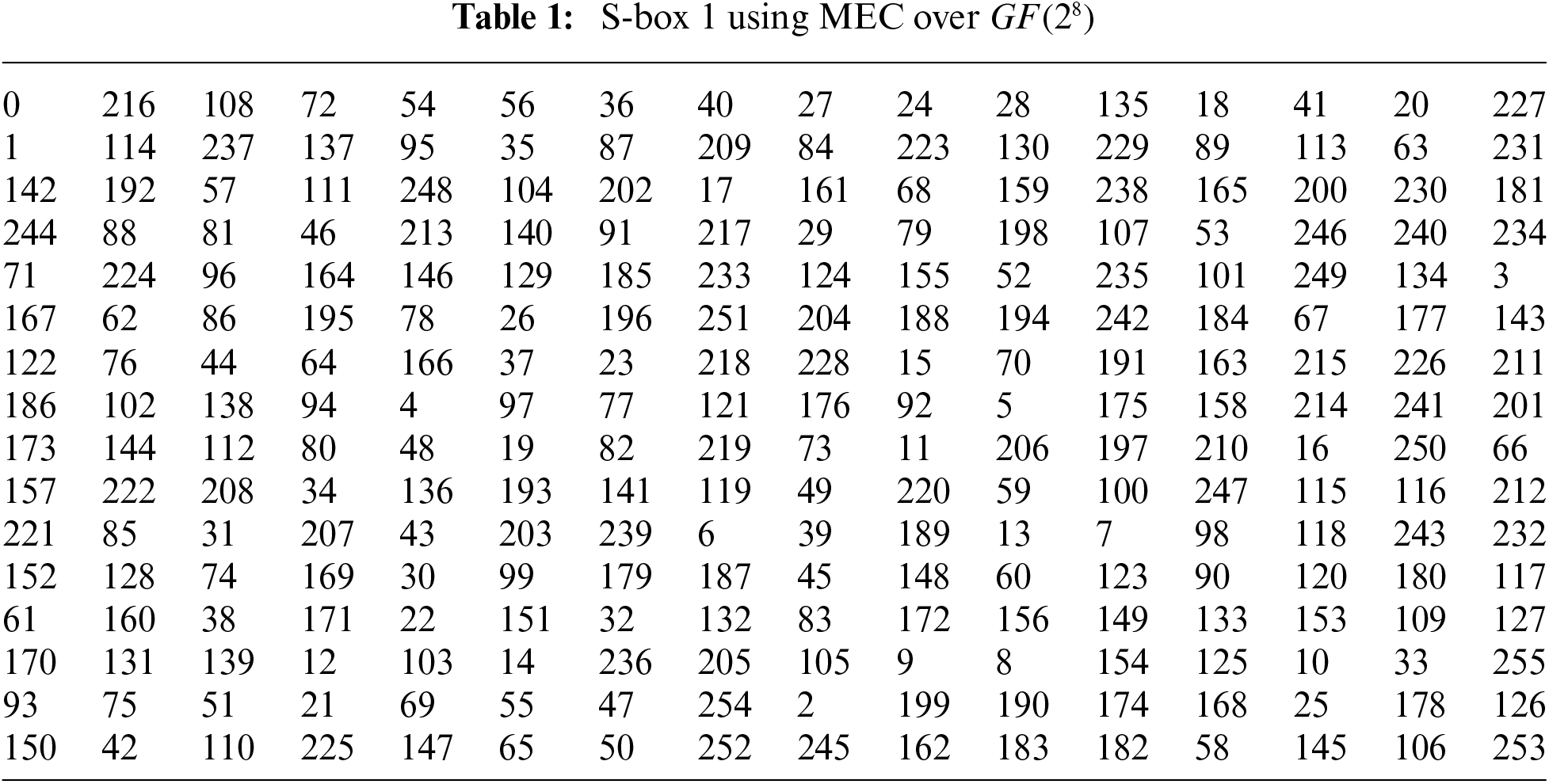
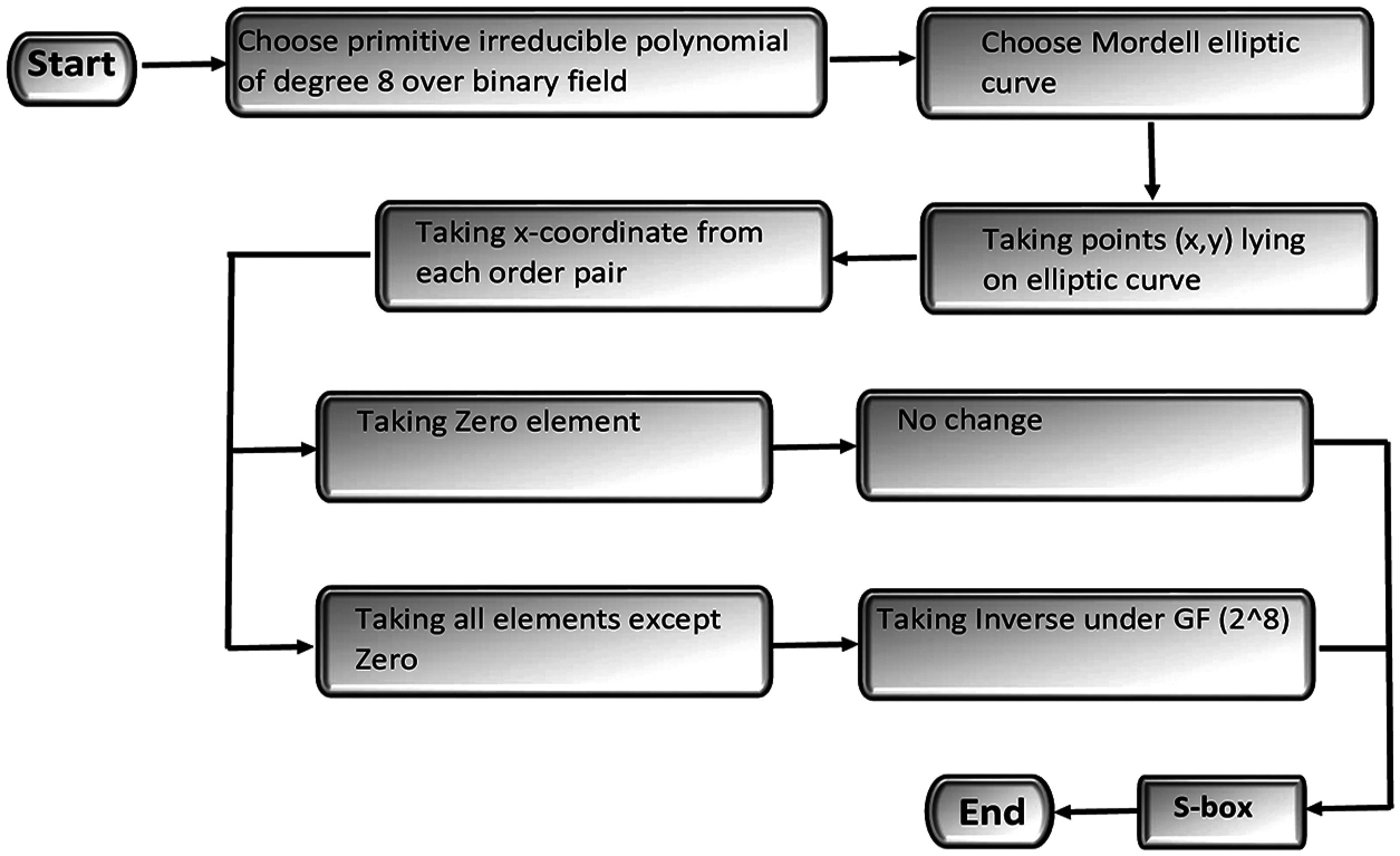
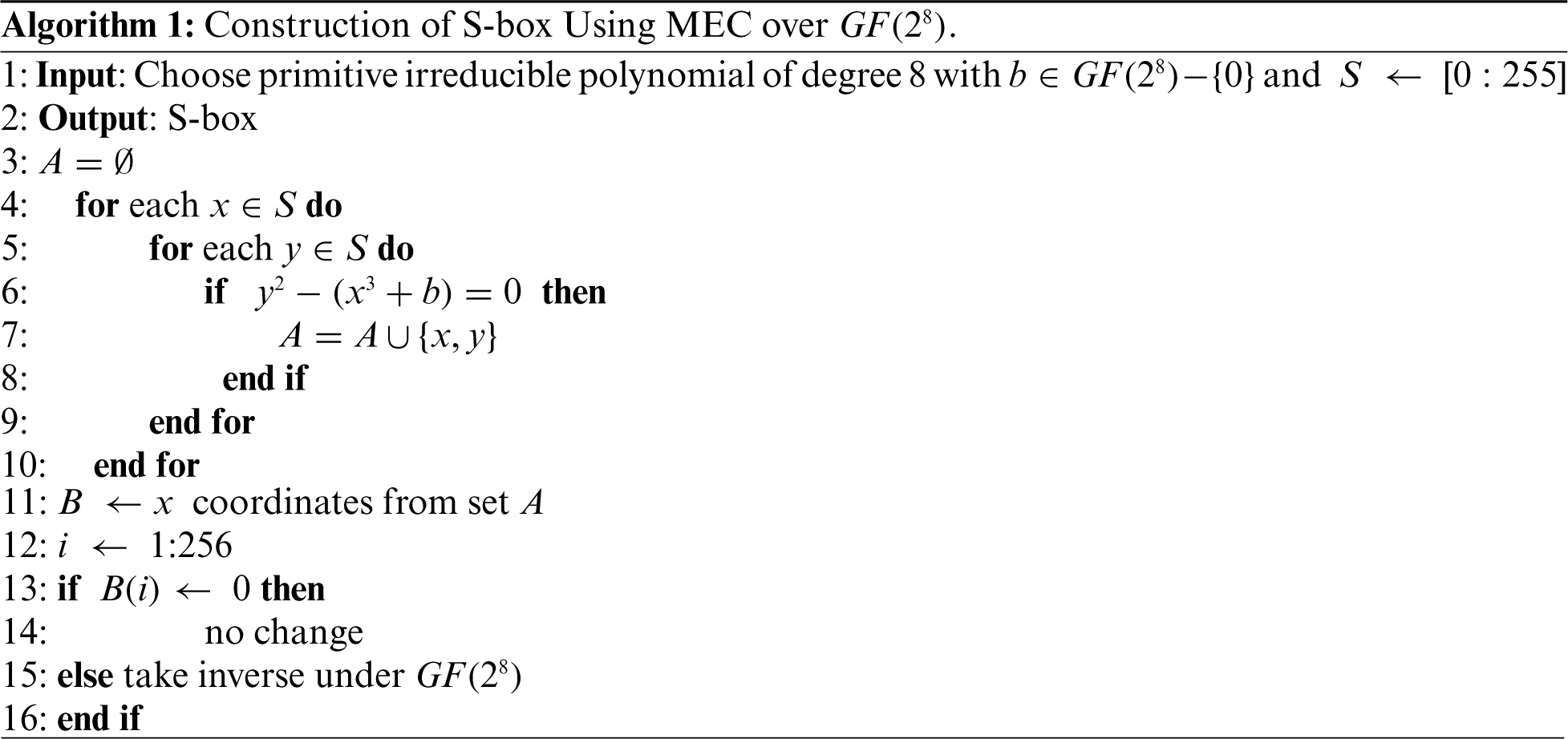
Figure 1: Proposed S-box scheme based on MEC over
3.2 Construction of S-Box Using Mordell Elliptic Curve Over Galois Field
The Galois fields
3.2.1 Construction of S-Box Using Mordell Elliptic Curve over Galois field
Firstly, choose primitive polynomial.
Over the binary field, any arbitrary primitive polynomial of degree
where
When we choose Mordell elliptic curve over
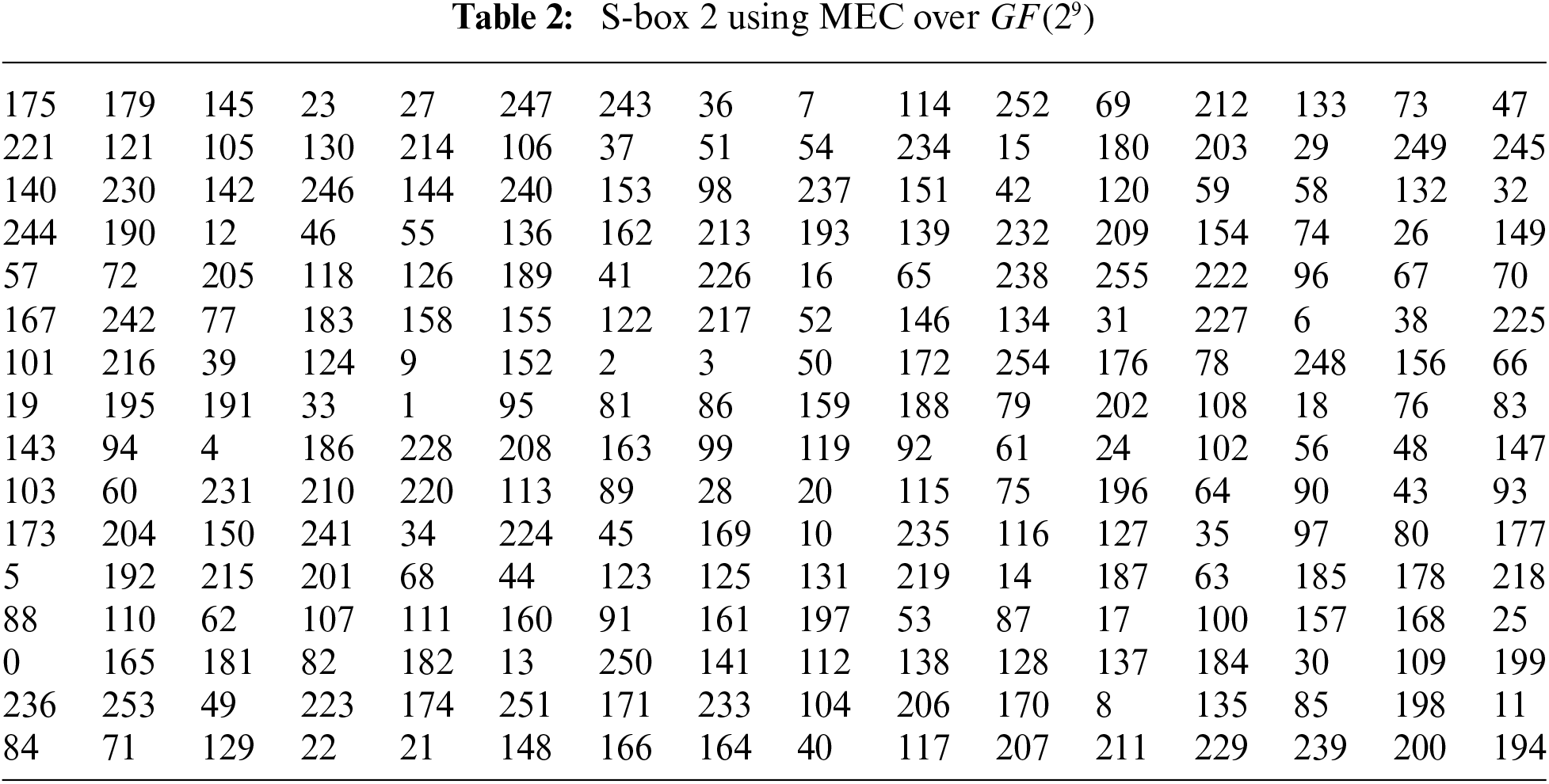
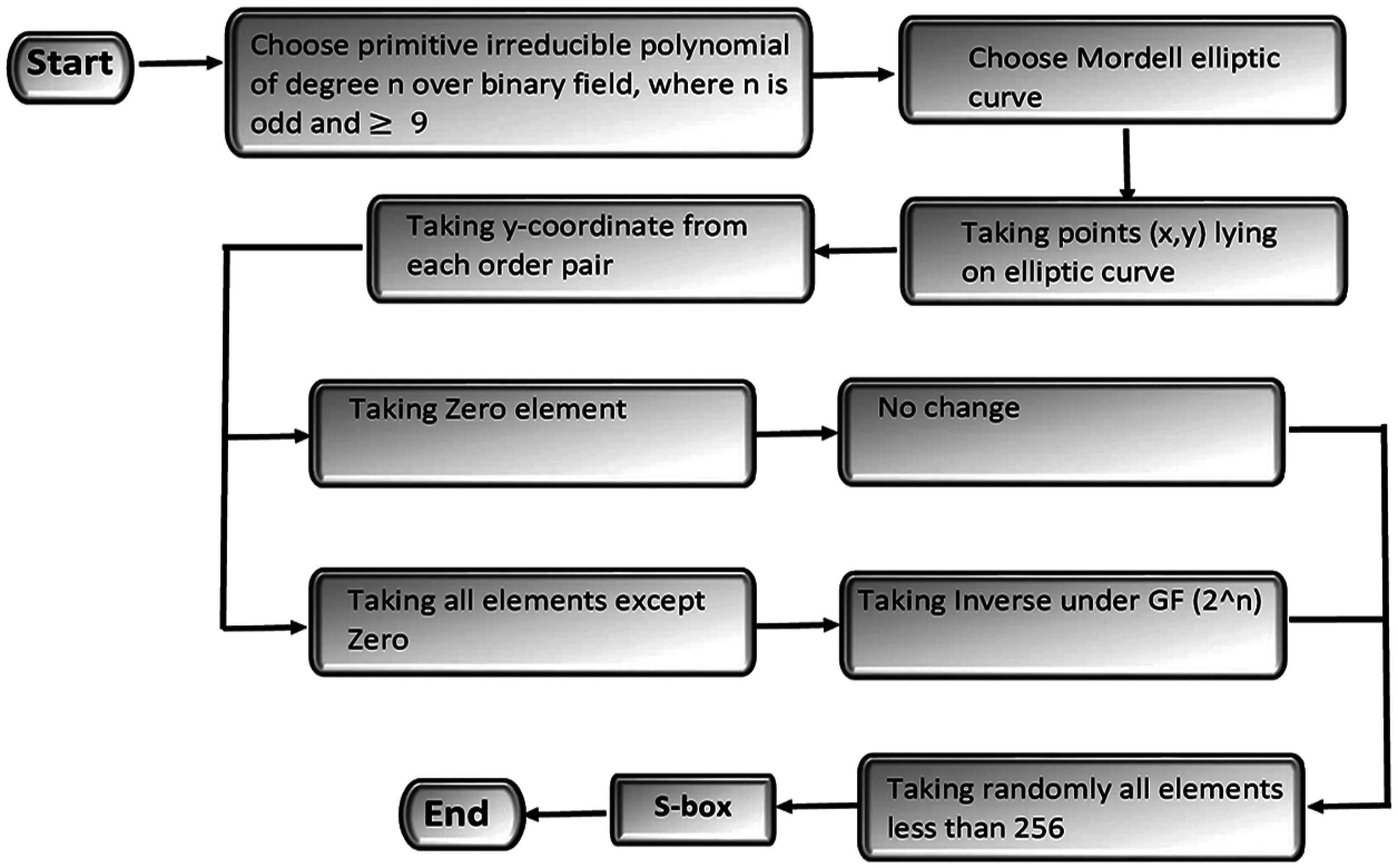
Figure 2: Proposed S-box scheme based on MEC over

3.2.2 Construction of S-Box Using Mordell Elliptic Curve Over Galois Field
Choose primitive polynomial.
In the binary field, any arbitrary primitive irreducible of degree
where b
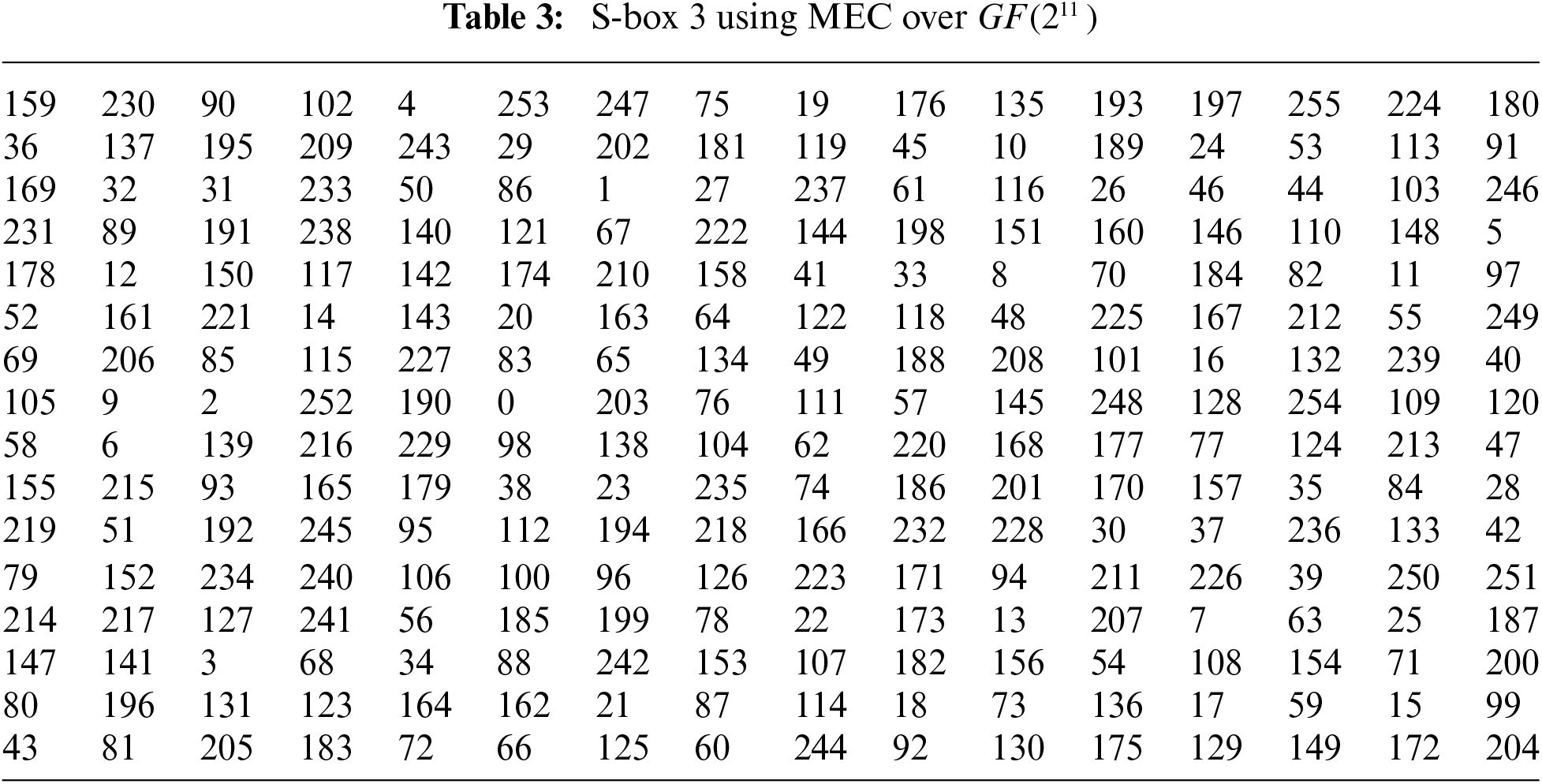
In this section, we mainly discussed the algebraic properties of newly designed S-boxes. We analyzed the cryptographic features of our proposed nonlinear component and compared the results to current benchmarks. Our proposed technique has clear advantages as compared to other algorithms as mentioned in the below tables.
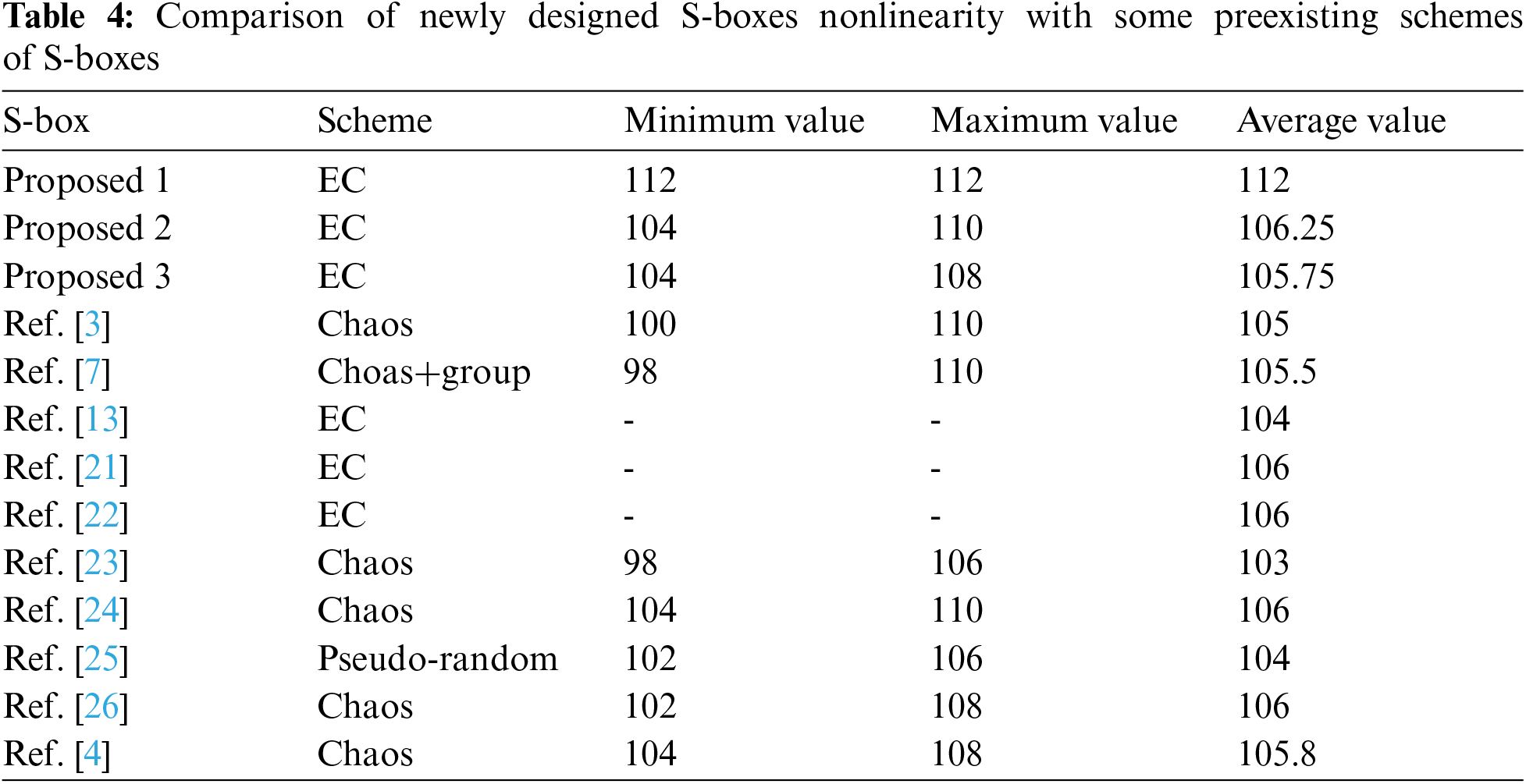
To calculate the nonlinearity of a given S-box, one can calculate the smallest distance of Boolean function h from a set of affine functions. An unknown individual might identify the information and actions of concerned Boolean functions if the proposed nonlinearity is insufficient. The nonlinearity of the S-box measures the confusion ability of the S-box over
4.2 Strict Avalanche Criterion
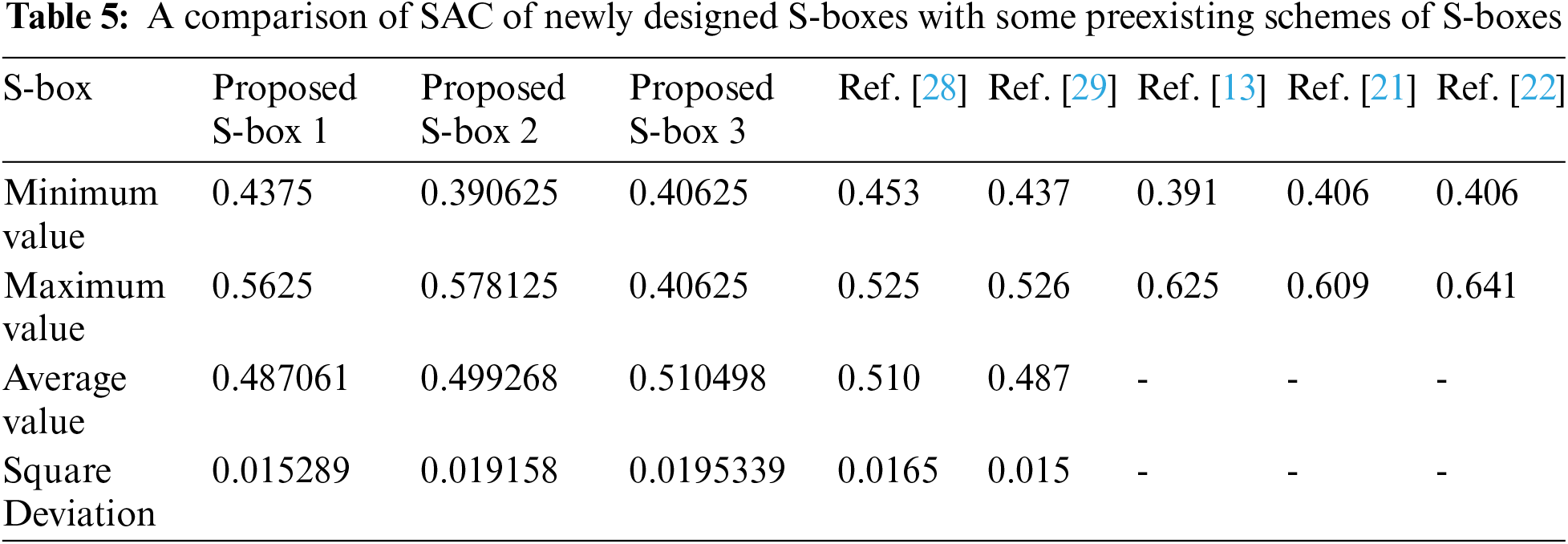
In [27], Webster and Tavares invented the theory of SAC in 1985. The criteria of SAC are fulfilled when the output bits deviation probability is 1/2, in the case when a single input bit is complemented. A 0.5 value of SAC assures that the correlation between input and output bits is minimal and makes the encryption procedure secure against various leakages. The SAC values of our S-boxes are close to 0.5, and the square deviation is also comparable to other existing S-boxes mentioned in Tab. 5. It clearly illustrates that the proposed S-boxes meet the requisite criteria better than different preexisting S-boxes SAC values.
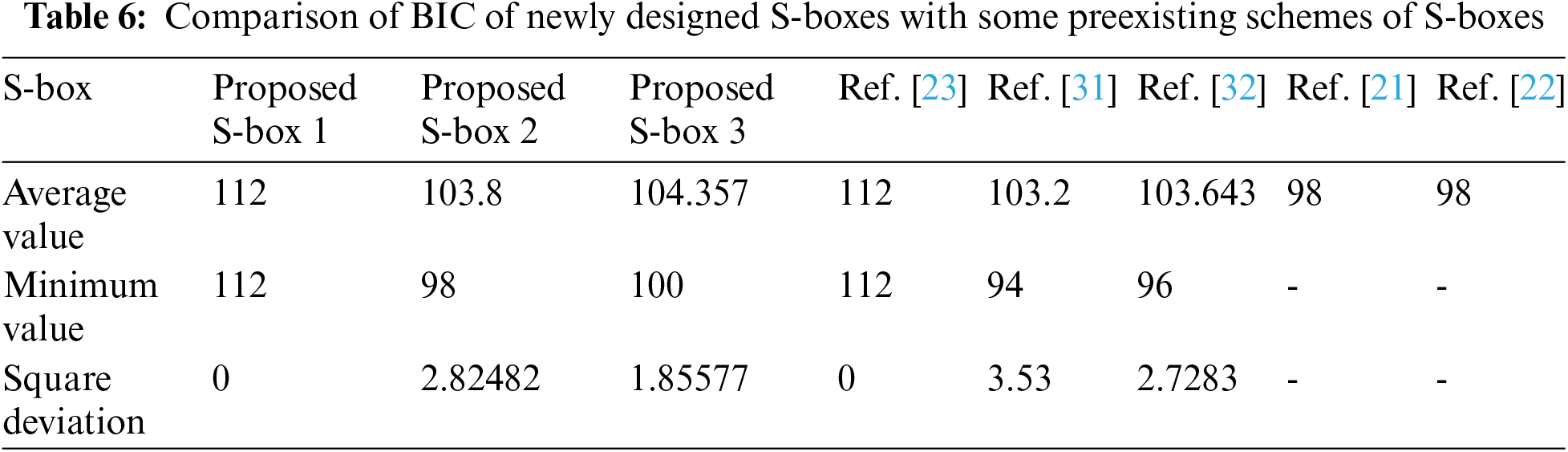
The BIC is an important test to evaluate the diffusion creation capability of the S-box. In [30], BIC is started off to check the dependence of two output bits when a single input bit is placed.
The BIC parameters are as follows:
Let
The function
SAC criteria satisfied.
The BIC of the newly designed S-boxes is calculated using this technique by assessing the nonlinearity and SAC of
4.4 Differential Approximation Probability
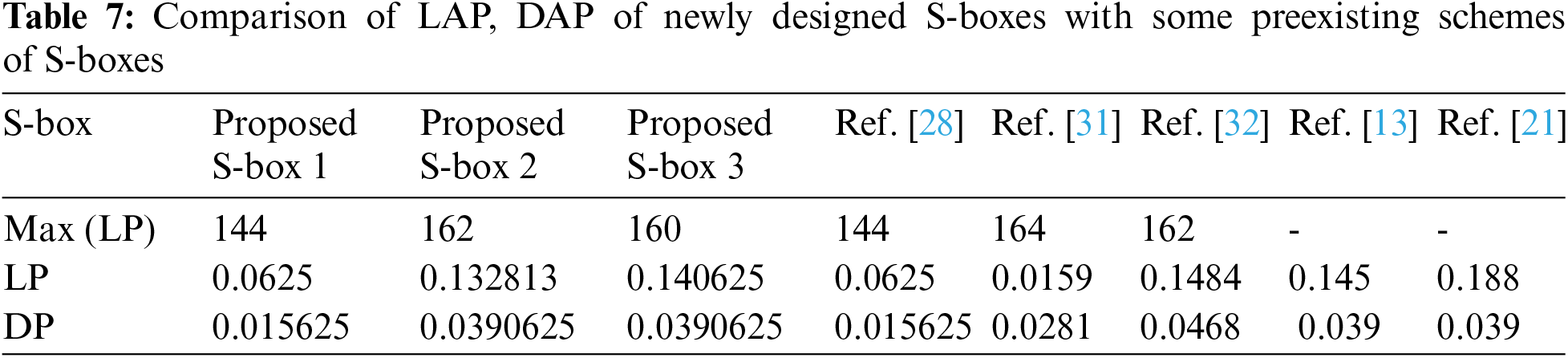
The DAP of an S-box is used to assess its resistance against differential approximation attacks. Reference [33] Introduces the probability of differential approximation to describe the probability effect of a reasonable difference in the input bit on the resulting output bit difference. The lower the value of DAP, the more secure S-box is against differential approximation attacks. The DAP of the proposed S-boxes is better than the various S-boxes mentioned in Tab. 7.
4.5 Linear Approximation Probability
The linear approximation probability is discussed in [34]. This determines the probability of getting a linear approximation of a given S-box. The LAP of the S-box is calculated by the correlation of input and output bits. If an S-box has a low LAP, it is highly resistant to linear attacks. The LAP value of the proposed S-boxes is very low as compared to other S-boxes mentioned in Tab. 7.
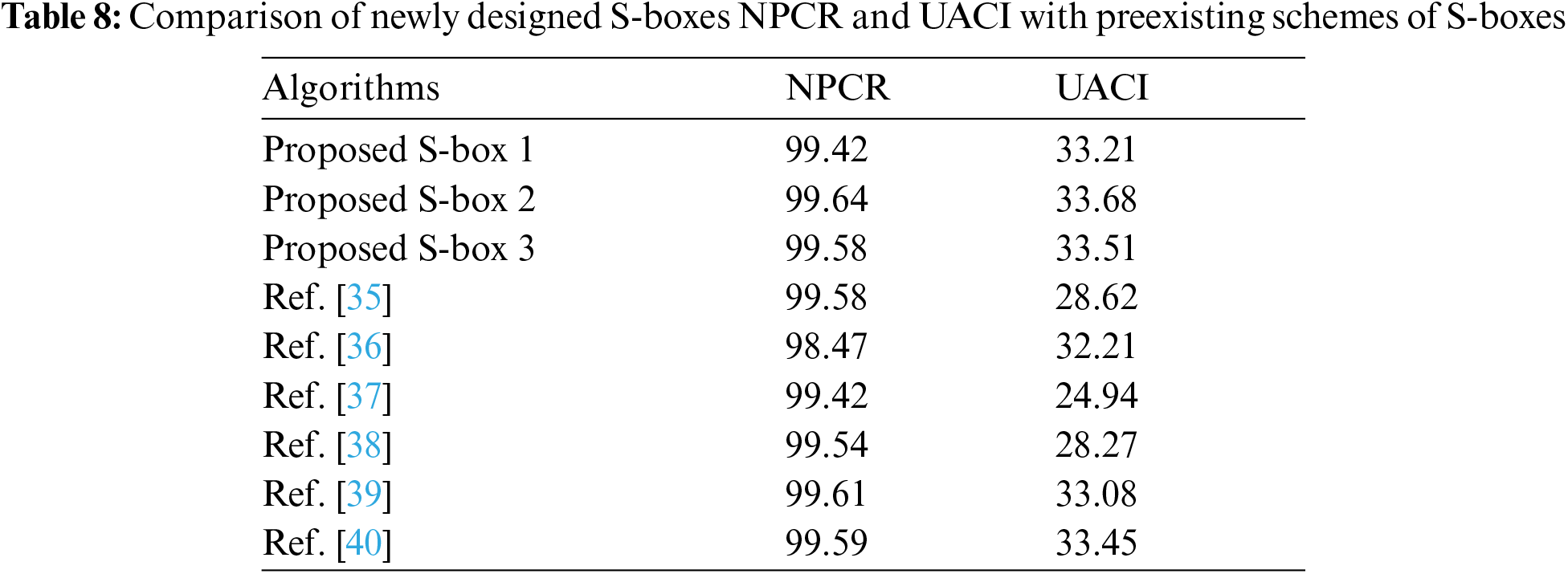
Hackers typically attempt to make minor changes to the original image before encrypting it with the proposed technique. Examine the original image with the image with changes after substitution. They discover the relationship between the original and encrypted images using this technique. Two significant studies are used to compute the influence of a one-pixel change in the original image on the image after substitution. The findings of the two most well-known tests, Unified averaged changed intensity (UACI) and several pixels changing rate (NPCR), are described in this part to measure the system's resistance to differential attacks. Mathematically NPCR is defined as
And UACI is defined as
where
4.7 Majority Logic Criterion Test
Reference [41] provides a detailed description of the majority logic criteria (MLC). These evaluations compare plaintext and encrypted images and so provide an accurate assessment of encryption technology. MLC performs statistical studies on both plain and encrypted data. MLC is essential in statistical feature analysis, such as in the enciphering process manipulation of data, which results in modifications in the plain data. MLC specifies a criterion for evaluating the outcomes of several statistical investigations, such as homogeneity, energy, correlation, contrast, and entropy. Its evaluation determined whether the S-box is appropriate for the use of an image encryption application or not. The
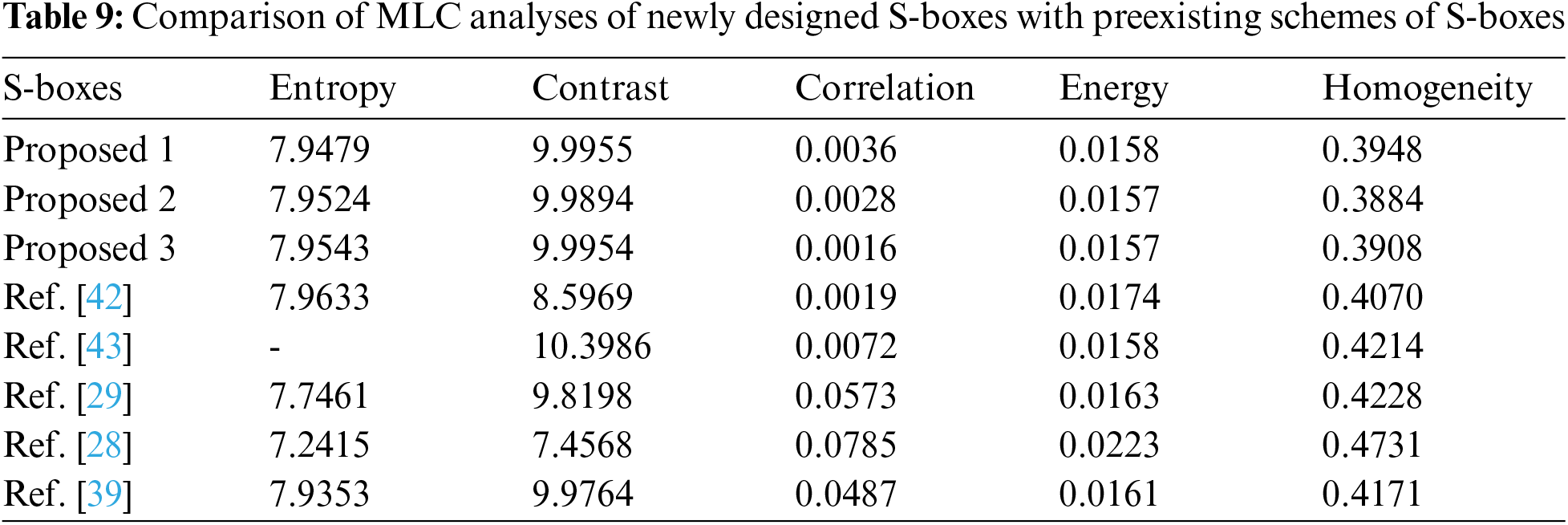
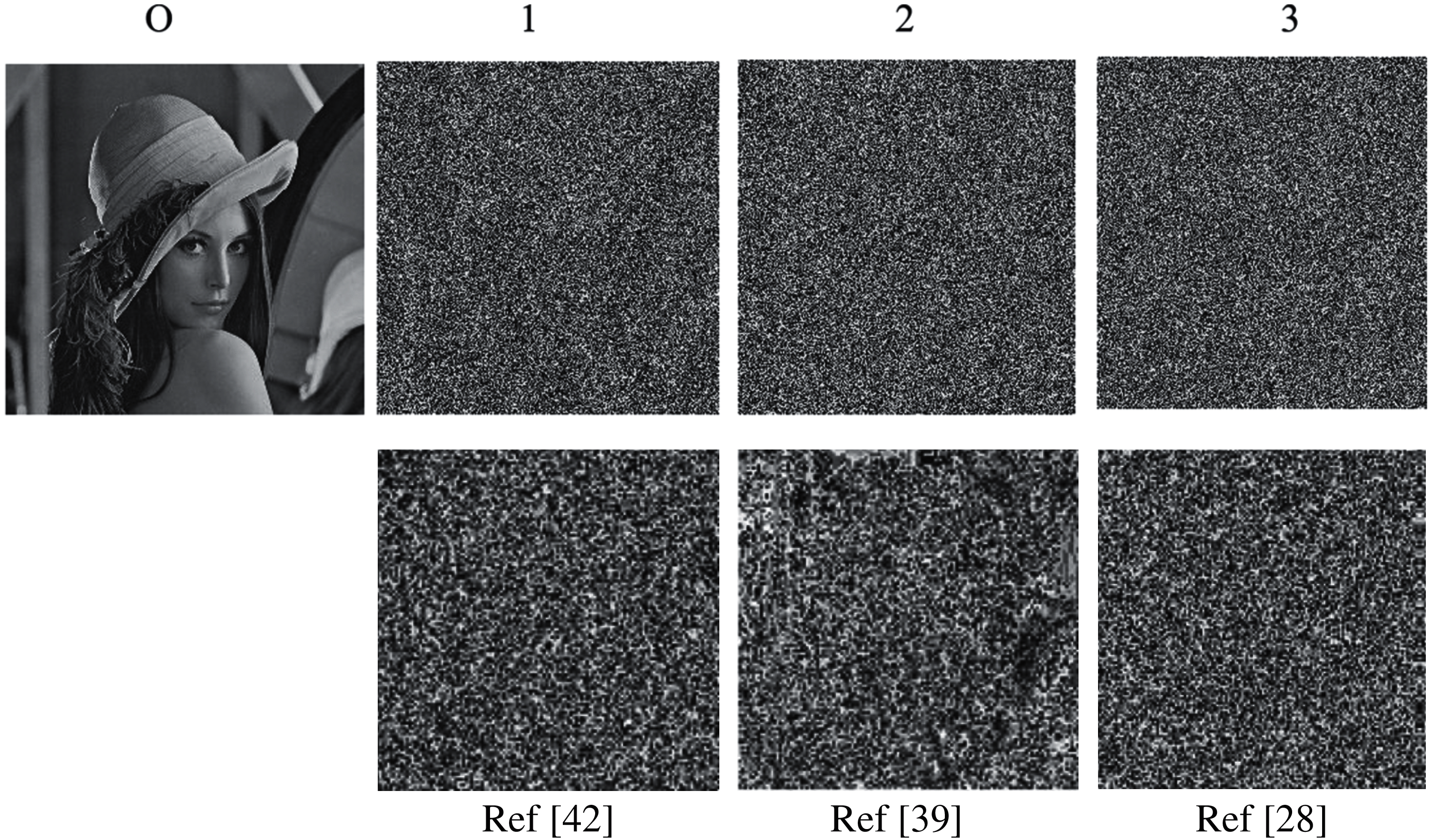
Figure 3: (O) Original lena image (1, 2, 3) Encrypted lena image using S-box 1, S-box 2, and S-box 3
The proposed algorithms of S-boxes construction are compared with other S-box designing schemes to assess their efficiency and resilience against various cryptographic attacks. The following point by point comparison is presented.
1. Tab. 4 shows some S-boxes based on chaos and elliptic curves with low nonlinearity compared to the proposed algorithm. The features of elliptic curves are used to construct nonlinear components of a block cipher in [13,21,22], but all work is done over the prime field. Instead of designing prime field dependent S-boxes, we used an innovative technique to consider elliptic curves over binary extension fields, and our results outperformed these algorithms.
2. The proposed S-boxes BIC and SAC results are much better than the existing algorithms [21–22,28] shown in Tabs. 5 and 6. In addition, our S-box BIC value is the optimal value. Consequently, the proposed S-boxes have a far more impressive diffusion creation power than other S-boxes.
3. The proposed S-boxes have lower LP values than the other schemes [13,21,28,32] S-boxes values shown in Tab. 7. As a result, the proposed algorithm is highly resistant to linear attacks and generates significant data confusion. Furthermore, the proposed S-boxes have lower DP values than the S-boxes in Tab. 7, making our scheme more resistant to various attacks.
4. In terms of NPCR and UACI, the proposed S-boxes outperform the schemes presented in Tab. 8. Compared to techniques [28–29,39,42], the MLC analysis of the proposed algorithm provided in Tab. 9 is considerably more refined, making our algorithm excellent for image encryption.
From comparative analysis, we may realize that the proposed S-boxes design method has an upright resistance against cryptanalysis compared to the prevailing S-box algorithms. According to the MLC test, the proposed S-boxes have outstanding image encryption features.
In this paper, the complex structure of elliptic curves defined over the binary Galois field extension
Funding Statement: The author extends their gratitude to the Deanship of Scientific Research at King Khalid University for funding this work through the research groups program under Grant Number R. G. P. 2/150/42.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. C. E. Shannon, “Communication theory of secrecy systems,” The Bell System Technical Journal, vol. 28, no. 4, pp. 656–715, 1949. [Google Scholar]
2. J. Daemen and V. Rijmen, “The Rinjdael block cipher: AES proposal,” in First Candidate Conference (AES1), pp. 343–348, 1999. [Google Scholar]
3. A. Belazi, A. Ahmad and A. E. Latif, “A simple yet efficient S-box method based on chaotic sine map,” Optic, vol. 130, pp. 1438–1444, 2017. [Google Scholar]
4. G. Liu, W. Yang, W. Liu and Y. Dai, “Designing S-boxes based on 3-D four-wing autonomous chaotic system,” Nonlinear Dynamics, vol. 82, no. 4, pp. 1867–1877, 2015. [Google Scholar]
5. U. Çavuşoğlu, A. Zengin, I. Pehlivan and S. Kaçar, “A novel approach for strong S-box generation algorithm design based on chaotic scaled zhongtang system,” Nonlinear Dynamics, vol. 87, no. 2, pp. 1081–1094, 2017. [Google Scholar]
6. H. Isa, N. Jamil and M. R. Zaba, “Construction of cryptographically strong S-boxes inspired by bee waggle dance,” New Generation Computing, vol. 34, no. 3, pp. 221–238, 2016. [Google Scholar]
7. M. Khan and T. Shah, “An efficient construction of substitution box with fractional chaotic system,” Signal, Image and Video Processing, vol. 9, no. 6, pp. 1335–1338, 2015. [Google Scholar]
8. V. S. Miller, “Use of elliptic curves in cryptography,” in Conf. on the Theory and Application of Cryptographic Techniques, Springer, Berlin, Heidelberg, pp. 417–426, 2000. [Google Scholar]
9. H. C. Jung, C. Seongtaek and P. Choonsik, “S-boxes with controllable nonlinearity,” in Int. Conf. on the Theory and Application of Cryptographic Techniques, Berlin, Heidelberg, Springer, pp. 286–294, 1999. [Google Scholar]
10. N. Koblitz, A. Menezes and S. Vanstone, “The state of elliptic curve cryptography,” Designs, Codes and Cryptography, vol. 19, no. 2, pp. 173–193, 2000. [Google Scholar]
11. R. K. Kodali, K. H. Patel and N. Sarma, “Energy efficient elliptic curve point multiplication for WSN applications,” in National Conf. on Communications (NCCIEEE, IIT Delhi, pp. 1–5, 2013. [Google Scholar]
12. I. Khalid, S. S. Jamal, T. Shah, D. Shah and M. M. Hazzazi, “A novel scheme of image encryption based on elliptic curves isomorphism and substitution boxes,” IEEE Access, vol. 9, pp. 77798–77810, 2021. [Google Scholar]
13. U. Hayat, N. A. Azam and M. Asif, “A method of generating 8 × 8 substitution boxes based on elliptic curves,” Wireless Personal Communications, vol. 101, no. 1, pp. 439–451, 2018. [Google Scholar]
14. U. Hayat and N. A. Azam, “A novel image encryption scheme based on an elliptic curve,” Signal Processing, vol. 155, pp. 391–402, 2019. [Google Scholar]
15. S. Farwa, A. Sohail and N. Muhammad, “A novel application of elliptic curves in the dynamical components of block ciphers,” Wireless Personal Communications, vol. 115, no. 2, pp. 1309–1316, 2020. [Google Scholar]
16. C. J. Benvenuto, “Galois field in cryptography,” University of Washington, vol. 1, no. 1, pp. 1–11, 2012. [Google Scholar]
17. E. W. Weisstein, “Totient function,” https://Mathworld.Wolfram.Com/, 2003. [Google Scholar]
18. S. Maitra, K. C. Gupta and A. Venkateswarlu, “Results on multiples of primitive polynomials and their products over GF (2),” Theoretical Computer Science, vol. 341, no. 1–3, pp. 311–343, 2005. [Google Scholar]
19. L. C. Washington, “Elliptic curves,” Number Theory and Cryptography, CRC press: Chapman and Hall, CRC, 2008. [Google Scholar]
20. W. Meier and O. Staffelbach, “Nonlinearity criteria for cryptographic functions,” in Workshop on the Theory and Application of Cryptographic Techniques, Springer, Berlin, Heidelberg, pp. 549–562, 1989. [Google Scholar]
21. N. A. Azam, U. Hayat and I. Ullah, “An injective S-box design scheme over an ordered isomorphic elliptic curve and its characterization,” Security and Communication Networks, vol. 18, pp. 9, 2018. [Google Scholar]
22. N. A. Azam, U. Hayat and I. Ullah, “Efficient construction of a substitution box based on a mordell elliptic curve over a finite field,” Frontiers of Information Technology, Electronic Engineering, vol. 20, no. 10, pp. 1378–1389, 2019. [Google Scholar]
23. M. A. Gondal, A. Raheem and I. Hussain, “A scheme for obtaining secure S-boxes based on chaotic baker's map,” 3D Research, vol. 5, no. 3, pp. 17, 2014. [Google Scholar]
24. U. Cavusoglu, A. Zengin, I. Pehlivan and S. Kacar, “A novel approach for strong S-box generation algorithm design based on chaotic scaled Zhongtang system,” Nonlinear Dynamics, vol. 87, no. 2, pp. 1081–1094, 2017. [Google Scholar]
25. K. Kazlauskas, G. Vaicekauskas and R. Smaliukas, “An algorithm for key-dependent S-box generation in block cipher system,” Informatica, vol. 26, no. 1, pp. 5165, 2015. [Google Scholar]
26. F. U. Islam and G. Liu, “Designing S-box based on 4D-4wing hyperchaotic system,” 3D Research, vol. 8, no. 1, pp. 9, 2017. [Google Scholar]
27. A. F. Webster and S. E. Tavares, “On the Design of S-boxes,” in Conf. on the Theory and Application of Cryptographic Techniques, Springer, Berlin, Heidelberg, pp. 523–534, 1985. [Google Scholar]
28. S. Farwa, T. Shah and L. Idrees, “A highly nonlinear S-box based on a fractional linear transformation,” Springer Plus, vol. 5, no. 1, pp. 1–12, 2016. [Google Scholar]
29. Y. Naseer, T. Shah, D. Shah and S. Hussain, “A novel algorithm of constructing highly nonlinear sp-boxes,” Cryptography, vol. 3, no. 1, pp. 6, 2019. [Google Scholar]
30. A. F. Webster and S. E. Tavares, “On the design of S-boxes. advances in cryptology,” Crypt 085 Lncs, vol. 218, pp. 523534, 1986. [Google Scholar]
31. K. F. Zkayna, “Construction of robust substitution boxes based on chaotic systems,” Neural Computing and Applications, vol. 31, no. 8, pp. 33173326, 2019. [Google Scholar]
32. A. Razaq, A. Yousaf, U. Shuaib, N. Siddiqui, A. Ullah et al., “A novel construction of substitution box involving coset diagram and a bijective map,” Security and Communication Networks, vol. 2017, pp. 1–16, 2017. [Google Scholar]
33. E. Biham and A. Shamir, “Differential cryptanalysis of DES-like cryptosystems,” Journal of Cryptology, vol. 4, no. 1, pp. 3–72, 1991. [Google Scholar]
34. T. Helleseth, “Advances in cryptology,” in Workshop on the Theory and Application of Cryptographic Techniques, Lothfus, Norway, Springer, vol. 765, 2003. [Google Scholar]
35. K. Loukhaoukha, J. Y. Chouinard and A. Berdai, “A secure image encryption algorithm based on Rubik's cube principle,” Journal of Electrical and Computer Engineering, vol. 12, no. 7, pp. 7–14, 2012. [Google Scholar]
36. G. A. Sathishkumar and D. N. Sriraam, “Image encryption based on diffusion and multiple chaotic maps,” arXiv preprint arXiv, vol. 10, pp. 1103.3792, 2011. [Google Scholar]
37. C. K. Huang and H. H. Nien, “Multi chaotic system S-Based pixel shuffle for image encryption,” Optics Communications, vol. 282, no. 11, pp. 2123–2127, 2009. [Google Scholar]
38. C. K. Huang, C. W. Liao, S. L. Hsu and Y. C. Jeng, “Implementation of gray image encryption with pixel shuffling and gray-level encryption by single chaotic system,” Telecommunication Systems, vol. 52, no. 2, pp. 563–571, 2013. [Google Scholar]
39. S. Hussain, S. S. Jamal, T. Shah and I. Hussain, “A power associative loop structure for the construction of non-linear components of block cipher,” IEEE Access, vol. 8, pp. 123492–123506, 2020. [Google Scholar]
40. X. Wang, X. Zhu and Y. Zhang, “An image encryption algorithm based on Josephus traversing and mixed chaotic map,” IEEE Access, vol. 6, no. 17, pp. 23733–23746, 2018. [Google Scholar]
41. A. K. Farhan, N. M. Al-Saidi, A. T. Maolood, F. Nazarimehr and I. Hussain, “Entropy analysis and image encryption application based on a new chaotic system crossing a cylinder,” Entropy, vol. 21, no. 10, pp. 958, 2019. [Google Scholar]
42. Y. Naseer, T. Shah, S. Hussain and A. Ali, “Steps towards redesigning cryptosystems by a non-associative algebra of IP-loops,” Wireless Personal Communications, vol. 108, no. 3, pp. 1379–1392, 2019. [Google Scholar]
43. F. A. Khan, J. Ahmad, J. S. Khan, J. Ahmed, M. A. Khan et al., “A new technique for designing 8 × 8 substitution box for image encryption applications,” in 2017 9th Computer Science and Electronic Engineering (CEECIEEE, Colchester, UK, pp. 7–12, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |