DOI:10.32604/cmc.2022.019252

| Computers, Materials & Continua DOI:10.32604/cmc.2022.019252 |  |
| Article |
Location Prediction for Improved Human Safety at Complex Environments
1Department of Electrical and Electronics Engineering, Angel College of Engineering and Technology, Tirupur, Tamilnadu, India
2Department of Electronics and Communication Engineering, Sri Krishna College Technology, Coimbatore, Tamilnadu, India
3Department of Electronics and Communication Engineering, KGISL Institute of Technology, Coimbatore, Tamilnadu, India
*Corresponding Author: S. G. Siddharth. Email: siddharth.bannari@gmail.com
Received: 07 April 2021; Accepted: 09 October 2021
Abstract: In underground operation, primary consideration is safety. In recent decades, for minimizing accident and for preventing major economic losses and casualties, wireless sensors are used by various large mineral countries through early warning. The Improved DV-Hop Localization Algorithm (IDVHLA) is used in existing works for doing this. However, accurate anchor node detection is impossible in existing works with the malicious nodes presence, where there won't be any accurate sharing of anchor node's location information. In case of emergency situation, faster communication is a highly complex one. A technique called Modified Distance Vector Hop based Multipath Routing Protocol (MDVHMRP) is introduced in this proposed research work for resolving this. In this work, to detect anchor node position, a Modified Distance Vector Hop technique is introduced. This research work considers time taken and session time for computing neighbour node's presence in addition to hop count values. Malicious nodes presence can be avoided by considering session time in neighbour node presence detection. The alert message are send by people in emergency crisis to sever in initial condition. Then Dynamic Source Routing (DSR) routing protocol is used for doing immediate route path selection. In case of route path failure, for ensuring uninterrupted communication and faster communication, this work introduces a multi path routing. The modified distance vector hop technique is used for predicting anchor node location information and predicted information will be transmitted. In NS2 simulation environment, overall evaluation of this research work is carried out. When compared with available techniques, localization accuracy is enhanced by proposed technique as proven in experimental results.
Keywords: Distance vector hop; uninterrupted communication; multipath routing; anchor node; localization
Predicting an emergency position with a large number of sensors will function as a protection service in emergencies [1]. Huge amount of small sensors with minimal memory and various sensing capacities that autonomously coordinate as well as reorganise themselves as ad hoc networks in response to emergency tasks and signals from atmosphere may be made up of a real-time variable safety net [2].
The navigation device deployed in advance is activated for executing two guiding activities when an emergency occurs [3]. In the first example, it is important to lead a stuck person out of emergency area, avoiding dangerous areas [4]. Second, in order to aid stranded people in distress, rescuers need to be directed into emergency region [5].
Wireless Sensor Networks (WSNs) have received substantial reactions from academics and businesses in various fields with new technologies being developed [6]. Any of the possible uses include surveillance of the landscape and plants, search and rescue operations, object detection, such as tracking medical patients and doctors, patient monitoring, military and other industrial applications.
Sensor nodes that are small in scale, are cheaper and use less resources with capabilities such as sensing, data storage, computing and wireless communication have been developed as a result of technical progress [7]. Localization is an important and demanding aspect of many WSN applications, including design, implementation, synchronisation, calibration, quality of service and security [8], among others.
In order to make it important for localization, sensor data must be added to the measured data, as this is fundamentally relevant in the tracking and documenting of wide-ranging information such as acoustic, thermal, visual, seismic or any other kind of measured observation [9]. For example, the location or part of the farm from which the data is collected will require an individual monitoring a large vegetation farm with a wide range of vegetables, since various vegetables have different basic requirements.
Node localization is expected to disclose the origin of objects, so that community sensor requests, routing, and network coverage questions can be supported or addressed. Over the decade, study has offered a range of solutions to the issue of node localization [10]. In general due to their implementation criteria, there is often a trade-off between localization precision, computational complexity, and energy efficiency of techniques.
A WSN typically has large amount of sensor nodes spatially dispersed, making it impossible and inefficient to record sensor nodes positions when nodes are deployed [11]. There is also a risk that the sensor node will later be relocated to some other location from its original location. An algorithm is therefore needed that will autonomously decide the position of the nodes.
The key purpose of this research is to introduce a system for data transmission that can support people in emergency situations. This analysis work helps to forecast, to assist them on time, the position of the people in need. This is achieved by implementing the algorithm of position prediction that will assist individuals to predict the exact location, so it is possible to perform on-time recovery acts. This is done by using data submitted by individuals via a multi-path routing algorithm.
This research work's overall organization is given as follows: In this section, general introduction about wireless sensor network and emergency crisis handling is given. In Section 2, description about different related research methods that focus on predicting location of sensor nodes are given. In Section 3, detailed overview of proposed research technique along with suitable examples and diagrams are given. In Section 4, simulation analysis of research work is given in detailed. Finally in Section 5, overall conclusion of research work in terms of simulation outcome is given.
In order to reduce energy consumption incurred by multi-hop transmitting of event-related data, Vincze et al. [12] suggested an adaptive technique which shifts sink node adaptively within covered area based on current events evolution. For two optimization techniques, both analytical and simulation results are provided: minimising total energy usage and minimising maximum load on a given sensor, respectively.
The LEACH protocol was expanded by Yuan et al. [13] to allow multi-hop transmissions between clusters by inserting a cooperative MIMO technique into hop-by-hop transmissions. This technique will achieve successful performance enhancement with respect to energy consumption and reliability through cooperative node's adaptive collection and collaboration between multi-hop routing and cooperative MIMO transmissions.
The energy efficient clustering algorithm for multi-hop wireless sensor networks was implemented by Nayak et al. [14]. These algorithms concentrate on CH's performance, which can be adoptive, scalable, and intelligent enough for spreading load between sensor nodes that can increase network's lifespan. Unfortunately, however majority of algorithms use the FL (T1FL) model type-1. In this article, on basis of interval type-2 FL model, we suggest a clustering algorithm intended to manage unknown level decisions better than the T1FL model.
In order to assess node localization problem's accuracy in wireless sensor networks, Goyal et al. [15] identified Meta heuristic optimization algorithm termed as bat algorithm. Meanwhile, using bacterial foraging techniques of bacterial foraging optimization algorithm, original bat algorithm has also been updated.
Node localization assisted by unmanned aerial vehicle has been suggested by Yang et al. [16]. There are three phases of the localization process: node image selection, non-occluded node localization and occluded node localization. In first phase, deployment area for capturing node images is shot by an unmanned aerial vehicle carrying a Global Positioning System. Then convolutional neural network approach is used for classifying nodes in non-occluded node localization process.
Liu et al. [17] suggested a novel adaptation for global optimization of the multi-group quasi-affine transformation evolutionary algorithm. Enhanced demographic diversity is introduced by arbitrarily splitting the population into three groups for adaptation to multi-group quasi-affine evolutionary algorithm transformation. To increase the algorithm's performance, each party adopts a mutation strategy differently.
In wireless sensor networks, the elephant herding optimization algorithm (EHO) adopted by Strumberger et al. [18] is used to solve localization problems. EHO is a comparatively recent meta-heuristic swarm intelligence that when dealing with hard problems with NP, obtains positive outcomes. The issue of node localization in wireless sensor networks, which belongs to NP's hard optimization group, is one of the most important problems in this field. For each unspecified sensor node randomly deployed in the monitoring area, the object of node localization is to set geographical coordinates.
A new node localization algorithm according to secondary correction errors has been proposed by Ma et al. [19]. Firstly, for correcting distance error, orthogonal polynomial fitting process, a mathematical model, is used. In addition, first and then square subtraction, a technique, is introduced for resolving equations.
At the same time to build weighted matrix for overcoming unknown node coordinates, real distance and distance error are used as weighting variables. Finally, for refining positions of unknown nodes, redundant knowledge produced by solving equations is employed.
A node localization approach based on a recent bio-inspired algorithm termed as Salp Swarm Algorithm (SSA) was proposed by Kanoosh et al. [20]. The proposed algorithm is compared under various WSN deployments to well-known optimization algorithms like grey wolf optimizer (GWO), firefly algorithm (FA), Butterfly optimization algorithm (BOA) and particle swarm optimization (PSO).
A range-free localization process based on a fuzzy-logic approach was proposed by Bhowmik et al. [21]. Based on their proximity to the sensor nodes, the localization scheme uses the Received Signal Strength (RSS) from the anchor nodes and fuzzy logic is used to create the relationship between RSS and distance to determine precise localization. We have compared our proposed solution to other known algorithms through detailed simulations.
An efficient Cuckoo Search (CS) algorithm for node localization was proposed by Cheng et al. [22]. This method helps the population to approach the global optimal solution easily, depending on the change in phase size, and the fitness of each solution is used to construct the likelihood of mutation to prevent local convergence. In addition, the method limits the population within a certain range such that the energy usage generated by negligible searches can be avoided.
3 Location Prediction Concerned Data Transmission
The key aim of the research work suggested is to ensure quicker and safe contact with the servers regarding the location of the people employed in the underground tunnels. With this knowledge, it is possible to make quicker decisions in the event of an emergency situation. The methodologies introduced in the research work proposed are described below:
■ In this work, the modified Distance Vector Hop approach is used to detect the location of the anchor node. The existence of adjacent nodes will be taken into account in this research work, along with the hop count values, session time and even time taken. Provided the session time to detect the presence of nearby nodes, the presence of malicious nodes will be avoided.
■ In the event of an emergency situation, individuals must first transmit the warning request to the server, thereby choosing the immediate route direction using the DSR routing protocol.
■ In this work, multi path routing is applied to ensure quicker connectivity and continuous communication in the event of a breakdown of the route path.
■ The anchor node position information will be transmitted using the modified distance vector hop process.
Around 95% production is done via underground mining because of the coal resource's complex storage conditions. Coal mine geological structure is a highly complex one and serious effects may be produced due to natural disasters. There are many hidden risks also. So, research on early warning system's in coal mine plays a significant role. Using coal mine safety early warning and monitoring system, it if possible to form a management decision information channel for underground wells and coal mines as well as reliable safety early warning mechanism. For accident rescue, management decision making, production command and disaster warning, personal safety and environmental parameter's dynamic information are provided by this.
A crucial role is played by a WSN wireless positioning algorithm's positioning accuracy in underground operation positioning structure system and coal mine intelligent safety early warning system. Between nodes, minimum hop path is assumed as straight line by DV-Hop algorithm. But in practical applications, this is not always possible. In estimated distance using hop-size and hop count, error is generated by this assumption. Communication range plays another drawback in DV-Hop algorithm. Because of radio and noise irregularity, a perfect circle will not be formed by every node's communication range in real environment.
The ‘N’ number of sensor nodes in m × m network area is deployed at random. In the middle of the m × m region, the sink is located. ‘n’ sensor nodes with two dimensional space coordinates such as (x, y) are clustered according to the cross correlation factor. It is possible to measure the cross correlation factor by
where,
x, y represents two dimensional space coordinates
Corr represents Correlation
Pearson product moment co-efficient is used for obtaining correlation and it is also termed as correlation coefficient.
where,
x, y represents two dimensional coordinate points
μx, μy represents Mean Value of x, y
Cov represents Covariance
σx,σy represents Standard Deviation of x, y
If the correlation coefficient ranges from (0 to 1), the nodes deployed are strongly correlated and the distance between the nodes is less, nodes require less energy consumption to transmit the data. If the coefficient ranges from (0 to −1), the lower the association between the nodes deployed is implied.
3.3 Multipath Routing Using Modified Dynamic Source Routing Protocol
Multipath routing is the routing strategy used by a network to use several alternate routes, which can provide a range of advantages, such as fault tolerance, increased bandwidth or better protection. It is possible to cross, edge-disjoint or node-disjoint several paths computed with each other. CMR (Concurrent Multipath Routing) is also taken to mean that various available routes for the transfer of data streams originating from an application or multiple applications are concurrently handled and used.
Each stream is allocated a different path in this type, uniquely to the degree provided by the available number of routes. Any streams can share paths if there are more streams than open paths. By building multiple active transmission queues, this offers greater use of usable bandwidth.
It also offers a fault tolerance measure such that if a path fails, only the traffic assigned to that path is disrupted, the other paths continue to support their stream flows; preferably, there is also an immediately available alternate path on which the broken stream can continue or restart.
Ratings are collected by reputation systems and are processed and consolidated by this. Upon request, this information is made available. There are two effects of it.
■ It provides the information, which allows the users for predicting future behavior of someone.
■ Simultaneously, they influence future by giving incentive to behave well.
A reputation is characterized as an import of past actions of a person. It is used by companies in brick and mortar universe to figure out possibility of obtaining optimal amount of fulfilment from their transaction with other individual whose credibility is being assessed. Until spreading it further or labelling it as unknown, credibility mechanisms can motivate users to check details.
Many emerging approaches to the use of credibility structures for ad-hoc mobile networks rely on addressing routing challenges created by misbehaving nodes. They still ignore complexities of a highly mobile node situation where potential for meeting someone again is tiny. Privacy questions are totally overlooked in the majority of situations.
In specific, if a human user is assumed as device owner, reputation is a sensitive personal information. Often, it has entity's former transactions detailed information. For an entity, it is critical, reputation should not be lost by false accusation.
■ For making reputation as highly usable and objective one, they are assigned with numerical values.
■ Node behavior is continuously monitored using monitoring module in reputation based system and every node is assigned with a reputation value according to its packet forwarding activity.
■ Neighbors as well as nodes had transaction with its reputation values are maintained by every node. Range of reputation value lies in-between 0 to 1, where best behavior is indicated using the value 1 and worst behavior is indicated using the value 0.
■ Ratio between packets forwarded by a node and packets send to it defines the reputation values.
■ During the first meeting of a node, entity for other nodes are created and reputation value of 1 is assigned to them.
■ Relative mobility of a node defines the nature of packet forwarding and data flow between nodes. Packets forwarded by node Q is observed by node P and a reputation value r (P, Q) is assigned by it. Ratio between packets count forwarded by Q and packets sent to it defines reputation value. These reputation values are stored by every node as new and old values weighted average (μ) via following expression.
■ In conditions when a node P wants to form an opinion about a certain node Q, reputation values are requested by it. Expression suggested to compute composite reputation value from reputation values computed from a neighbor, says R, is expressed as,
■ Nodes may move in and out of other node's range frequently in ad-hoc setting, which disrupts/reroutes ongoing flows.
■ As a result, target node's behavior can be best described using a node having longest association.
In general, there must be a reliable data transfer and no data during transmission needs to be ensured. So, reliable data transfer from one node to another node is ensured using two basic techniques. They are, non-acknowledgment based techniques and acknowledge based technique. Due to the following reasons, for reliable data transmission, acknowledgment based technique is used in this research work. Three message types are used for both non-ack and ack based techniques.
a. Data packet pi's transmission.
b. Packet pi's acknowledgement for ack based technique and RMP that is request to missing packet in non-ack based technique.
c. Packet pi's re-transmission.
After sending packet to receiver, a node waits for an acknowledgment from receiver. For a time period (ta), it waits. The data packet is re-transmitted again, if there is no acknowledgement is received within this time period and until sender receiving acknowledgement for the transmitted data packet, this process is repeated.
3.4 Location Estimation Using Modified Distance Vector Hop Protocol
In every anchor node, for computing initial Average Hop Distance (AHD), traditional DV-Hop algorithm is used in this work and following additional steps are used in this proposed work for enhancing localization accuracy and it forms a Modified DV-Hop algorithm. The hops count among nodes is fixed in general under DV-hop idea premise. The AHD is adjusted in modified DV-Hop for computing minimum error between actual distance and estimated distance.
Based on introduced DV-hop in second phase of ‘‘DV-Hop localization algorithm”, there is a chance for high error where every anchor node selected all other anchors as reference nodes for estimating an AHD, as large error may be produced by some of them in random topology networks. So, an approach for removing reference anchors is provided by modified DV-hop which may produce a huge error in this way for enhancing AHD's computation accuracy.
At first, every node's pseudo-range error factor is defined to its reference nodes. For example, pseudo-range error factor is computed by anchor Ni to jth reference anchor as mentioned below,
where, between anchor Ni and anchor Nj, actual distance is represented as dij, estimated distance is represented as
where, bop-count between anchor Nj and anchor Ni is represented hopij and anchor Ni's average hop size is represented as HopSizei.
High closeness between real distance and pseudo-range is indicated using small value of diff_errij. Then, in ascending order, diff_errij are sorted and top k(k>= 3) reference anchors are selected for forming an optimum group of anchors (OGAsi, k) of Ni for recalculating AHD of Ni using expression (8). At last, for replacing HopSizei as AHD,
If anchor Ni is an unknown node, by computing its distances to every anchor among OGAsi, k, Ni locates itself. Expression (9) is used for computing the distance between jth (1 <= j <= k) anchor node and Ni within OGAsi, k as,
The Ni's position correction values can be computed using expression (10) as Ni's true location is known to us.
where, Ni's actual coordinate is represented as (xi, yi) and its estimated coordinate is represented as
a. After the DV-Hop's first step, according to the distances and hops between itself and its neighbours, its AHD (HopSize1) are computed and using expression (7), estimated the distance to anchors. In the next step, expression (6) is used for computing anchor 1's pseudorange error factors with respect to reference nodes.
b. In ascending order, pseudo-range error factors are sorted and from OGAsi, k of anchor 1, top k reference nodes are selected. Here, value of k is assigned as 5 and assumption is made that, anchors 2–6 are selected as OGAs1, 5.
c. For acquiring corrected AHD (HopSize51), expression (8) is adopted by Anchor 1 and for computing distances to every reference node among OGAs1, 5, HopSize51 is used and it computes position (E1). Then, for computing anchor 1's coordinate corrections, expression (10) is used by it. Likewise, coordinate correction values and corrected AHD are obtained for every anchor node. Then, message packages are broadcasted by anchor 1 to its neighbours and its format is {ID = 1, OGAs1, 5, HopSize51, (
Highly similar topological structure and physical environment like interference noise, multi-path effect and electromagnetic environment are shown by nodes in close proximity in WSNs. So, if same OGAs are used by every unknown node and its closest anchor node for estimating its own coordinates, then it produces same coordinate correction values. The unknown node's coordinates are corrected reasonably using the coordinate correction values of its nearest anchor.
However, under topology random networks, Gaussian distribution is obeyed by correction values. On unknown node's positioning accuracy, greater effect is shown by the closest anchor node. Thus, for ensuring closest anchor node which is having high effect on localization results, weights pi = 1/hopui are defined, where, hop-count between unknown node nu and anchor Ni is given by hopui and Ni within OGAsi, k. Then, expression (11) is used for modifying nu's coordinates. The nu's final estimates are given by (xu, yu).
For computing unknown node U's position, assumption is made that anchor node 1 is nearest anchor node to unknown node U.
a. From anchor node 1, message package are received by unknown node U. Then, for computing estimated coordinates U1, range between U and every anchor node among OGAs1, 5 is used by U.
b. At last for acquiring localization result U2, in expression (11), OGAs1, 5's coordinate correct values and U1 coordinates are used as an input.
The flow model of the proposed system is shown as in Fig. 1. Various routing protocol's performance is evaluated using the simulation results. In this section, simulation results of Modified Disnce Vector Hop based Multipath Routing Protocol (MDVHMRP), Improved DV-Hop Localization Algorithm (IDVHLA) and Multiple MQoS aware Route Path Establishment (MQoS-RPE) are presented and various parameter metrics like end-to-end delay, energy consumption, packet delivery are used for making performance comparison.
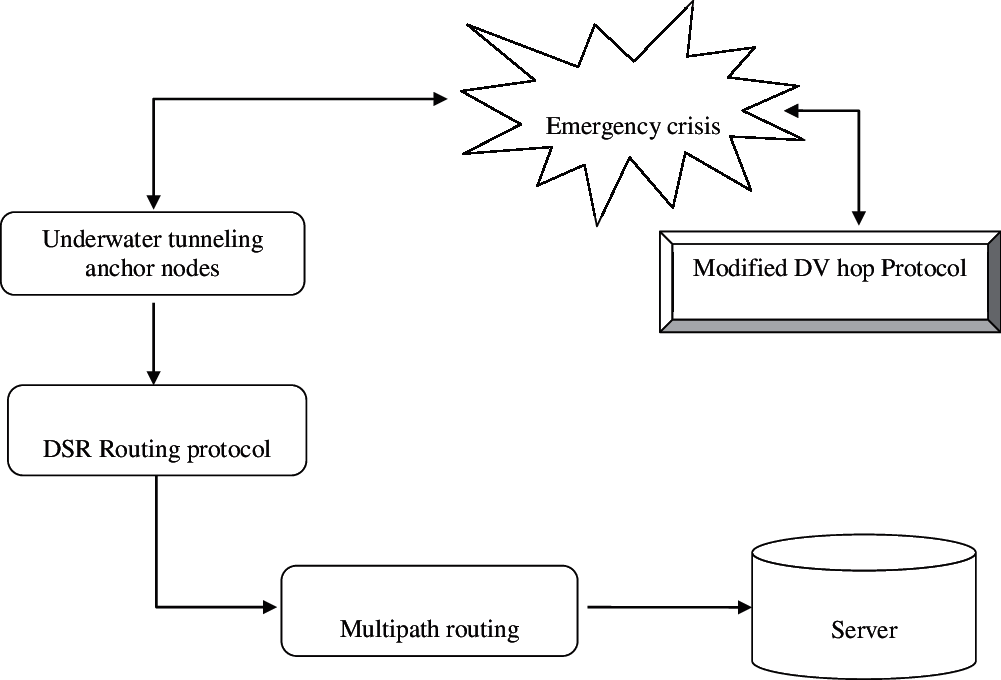
Figure 1: Flow of proposed research method
Rate at which waves are received by sink are given by throughput. Sensor network views throughput as a phenomenon of “monitoring rate”. In general, production's maximum rate or maximum processing rate is defined by throughput. In the network, cumulative sum of data rates that are delivered to all nodes defines throughput. It is defined by packets per second.
where,
Np(i) indicates total packets count transmitted by ith node
t(i) indicates time period of ith node transmission
Protocol's better performance is achieved with better through values as indicated in Fig. 2. Tab. 1 summarizes the simulation results of through metric.
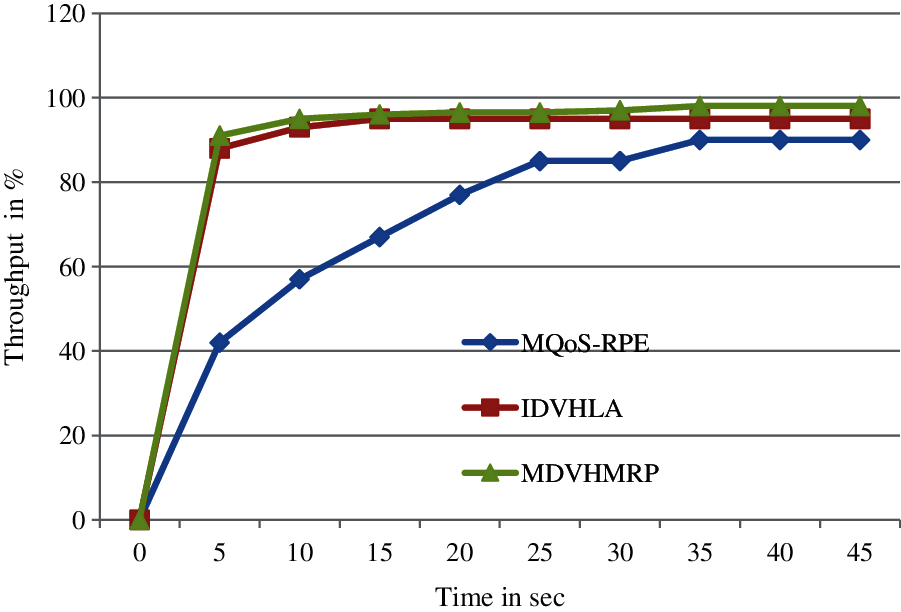
Figure 2: Throughput comparison
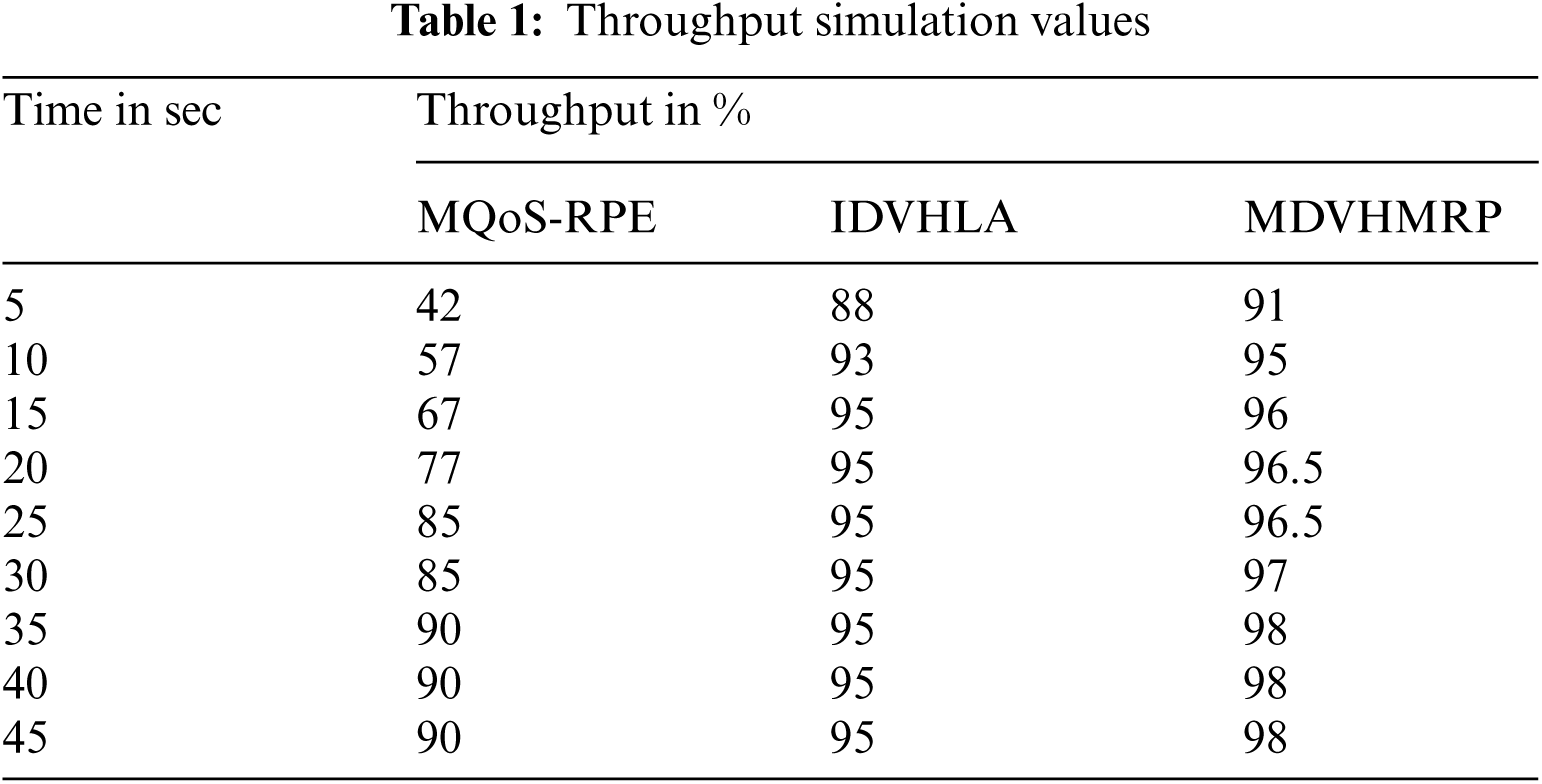
Throughput comparison between proposed research technique and existing technique are shown in Fig. 2. Better performance is produced by proposed research technique when compared with available technique with respect to throughput. With increased data packets count, better performance cannot be achieved using available techniques and 15 sec saturated level time needed by these techniques. Around 2.3% enhancement and around 26.79% enhancement can be achieved using this proposed MDVHMRP methodology when compared with IDVHLA and MQoS-RPE respectively.
From source to destination, time required by a packet to get transmitted over the network defines one-way delay (OWD) or end-to-end delay. From source node to sink node, amount of time required is defined by this. Protocol's better performance can be achieved using low value of this end to end delay as shown in Fig. 3. Tab. 2 summarizes the simulation results of End-To-End Delay metric.
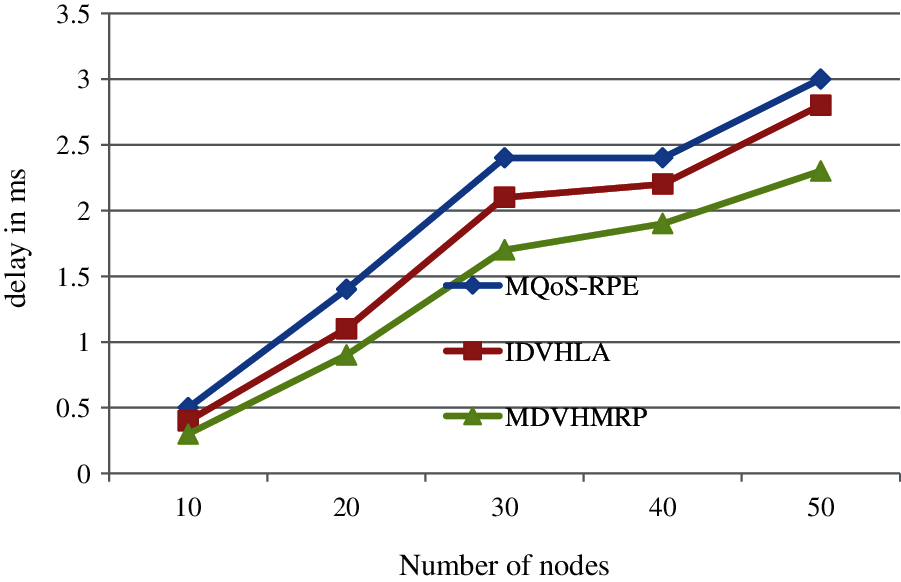
Figure 3: End to end delay comparison
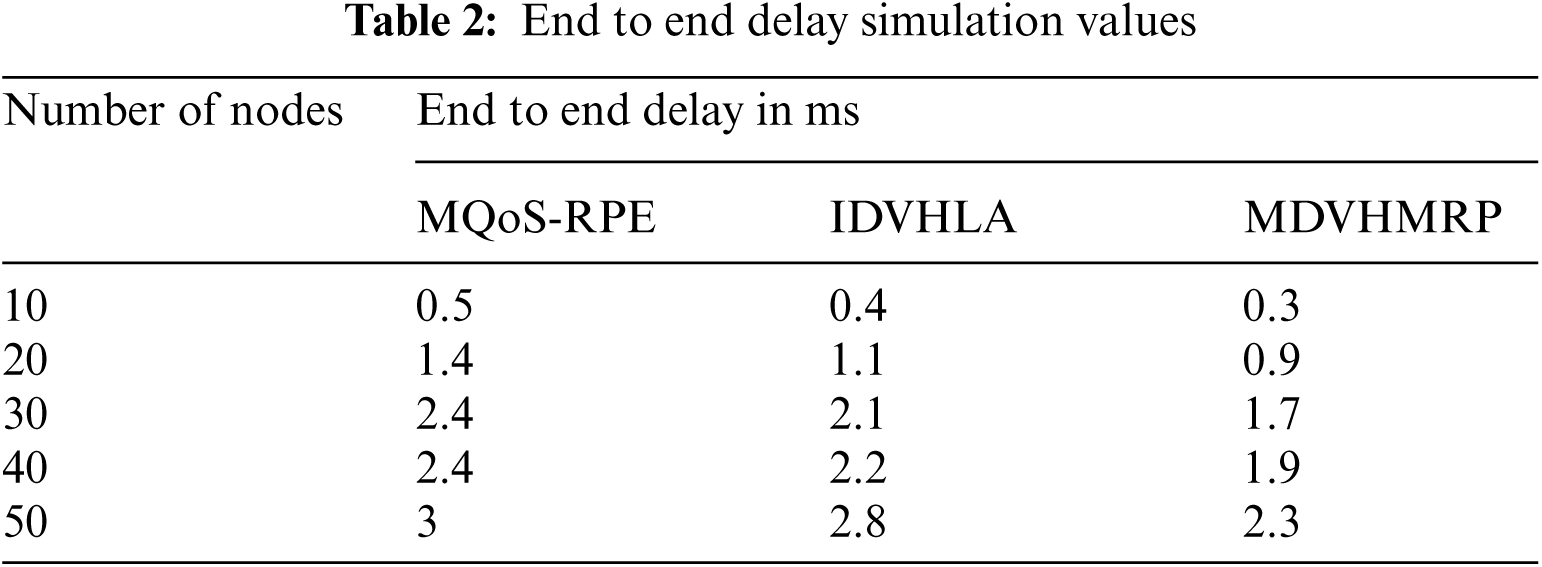
where,
Rt (i) indicates received time of ith data packet
Tt (i) indicates transmitted time of ith data packet
Tp indicates Total transmitted packets count
End to end metric comparison between proposed research technique and existing technique are shown in Fig. 3. Better performance is produced by proposed research technique when compared with available technique with respect to end to end delay. Around 50–70 packets can be send using a proposed methodology in a second. Around 17% enhancement and around 26% enhancement can be achieved using this proposed MDVHMRP methodology when compared with IDVHLA and MQoS-RPE respectively.
In a simulated duration, average amount of consumed energy is indicated using this. Better lifetime of a network is achieved with lower energy consumption. Cumulative energy consumed to transmit a data to base station from source nodes gives the total energy consumed (mJ). Difference between node's initial energy and consumed energy defines this and it is expressed as,
where,
ET indicates total energy consumption
EI (i) indicates initial energy of ith node
EC (i) indicates consumed energy of ith node
When compared with other research methodologies, considerably less energy is consumed by proposed research technique as indicated in Fig. 4. There will be a linear increase in energy consumption, when there is an increase in nodes count. Around 16% consumption of energy and 48% consumption of energy is minimized by proposed MDVHMRP technique, when compared with available IDVHLA and MQoS-RPE techniques. Tab. 3 summarizes the simulation results of Energy Consumption metric.
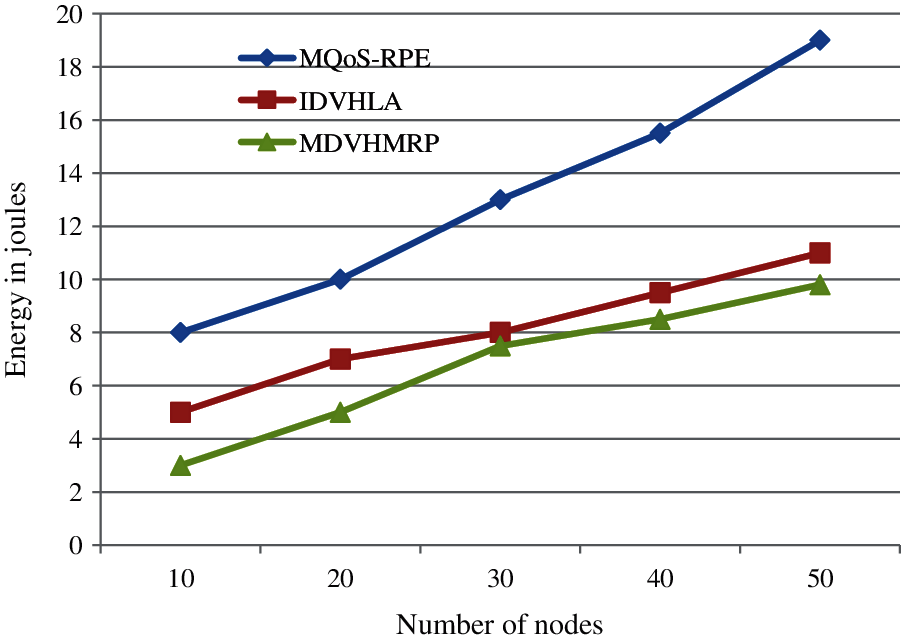
Figure 4: Energy comparison
Ratio between data packets count delivered to destination and total number of packets transmitted defines this packet delivery ratio. Delivered data level to the destination is illustrated using this. Better performance is indicated using high value of packet delivery ratio. Ration of packets count successfully transmitted to destination defines this Packet Delivery Ratio (%) and it is expressed by,
where,
PDR indicates Packet Delivery Ratio
Pr indicates number of packets received
Pt indicates number of packets transmitted
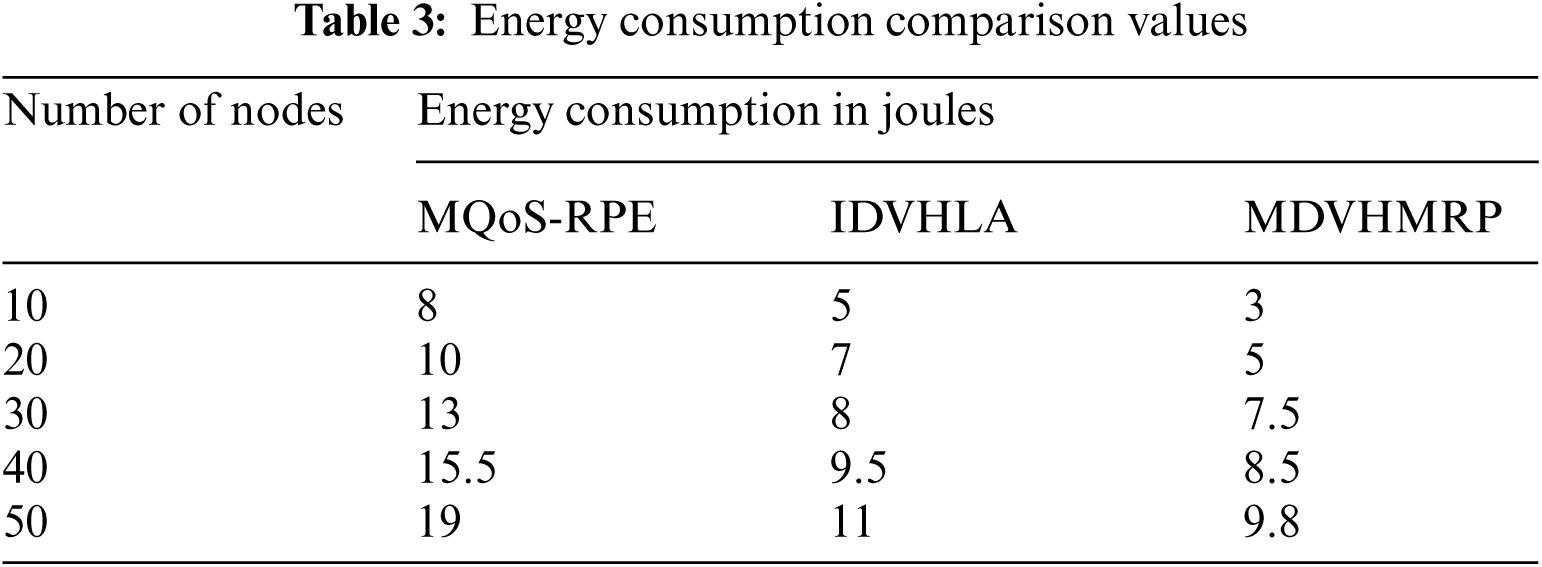
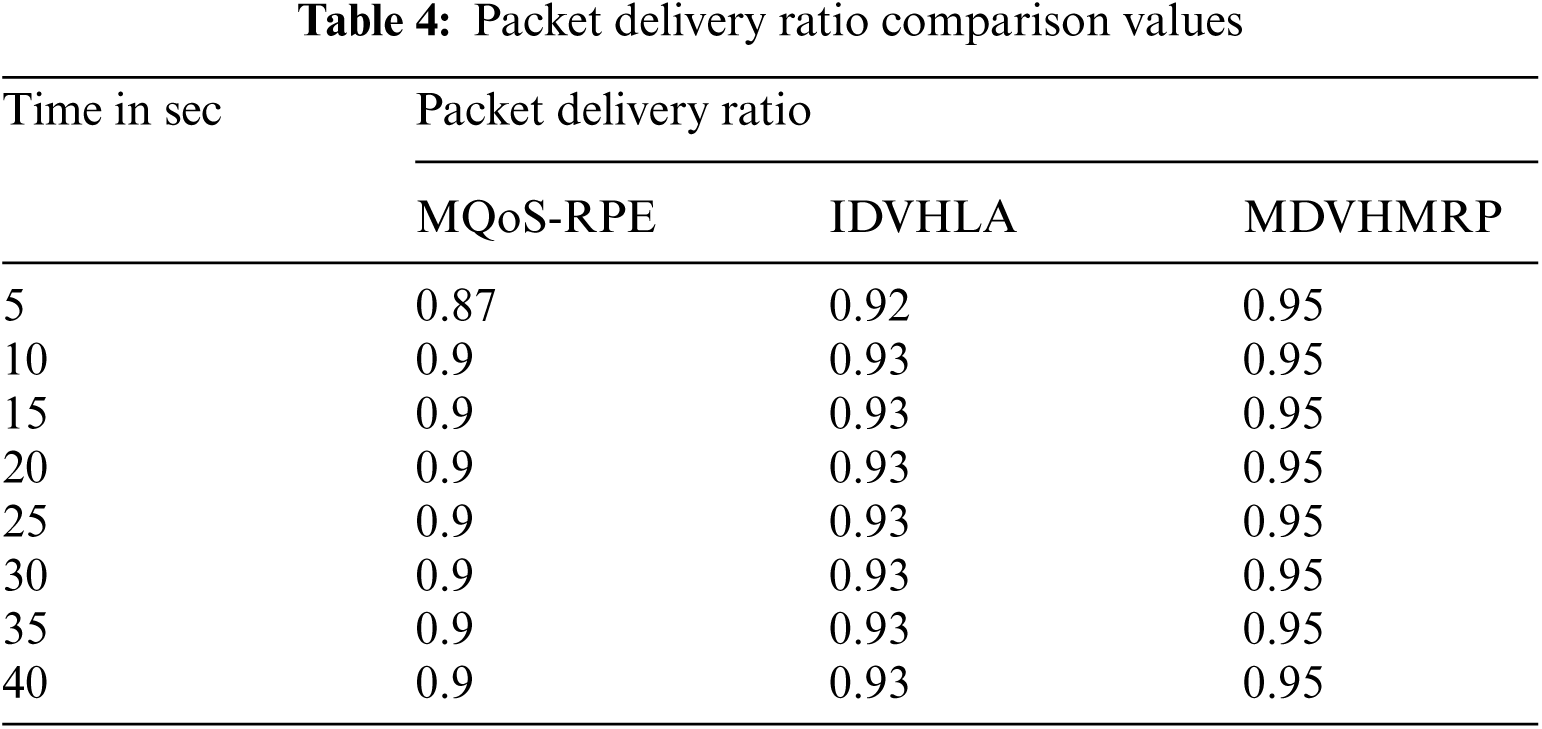
While making comparison with available techniques, high packet delivery ratio will be produced by proposed research technique as indicated in Fig. 5. High packet delivery ratio count can be produced using MDVHMRP at lower time. In addition to topology control, multipath routing and multihop communication is used with collaborative communication by nodes, which makes this increase in packet delivery ratio. Proposed research work provides better performance results when compared with available techniques as proven in experimental results. When compared with IDVHLA, 2% enhancement and compared with MQoS-RPE, 5% enhancement is produced by this proposed technique. Tab. 4 summarizes the simulation results of Packet Delivery Ratio metric.
Figure 5: Packet delivery ratio comparison
For anchor node position detection, a Modified Distance Vector Hop technique is proposed in this research work. For neighbour nodes presence detection, time taken and session time are also considered in this research work in addition to hop count values. Malicious nodes presence can be avoided by considering session time in neighbour node presence detection. The alert message are send by people in emergency crisis to sever in initial condition. Then DSR routing protocol is used for doing immediate route path selection. In case of route path failure, for ensuring uninterrupted communication and faster communication, this work introduces a multi path routing. The modified distance vector hop technique is used for predicting anchor node location information and predicted information will be transmitted. In NS2 simulation environment, overall evaluation of this research work is carried out. When compared with available techniques, localization accuracy is enhanced by proposed technique as proven in experimental results.
Acknowledgement: The authors would like to thank Dr. Hayat Dino Bedru and Shirley S.T. Yeung for their extensive support during the critical review of this article.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. N. E. Horelik, H. Katz, G. C. Mahoney IV, J. T. Hinton IV and M. J. Martin, “Emergency location analysis system,” U.S. Patent Application No. 16271634, Patent No. 10820181, 2019. [Google Scholar]
2. S. Han, Y. Noh, U. Lee and M. Gerla, “Optical-acoustic hybrid network toward real-time video streaming for mobile underwater sensors,” Ad Hoc Networks, vol. 83, pp. 1–7, 2019. [Google Scholar]
3. H. Bi, W. L. Shang and Y. Chen, “Cooperative and energy-efficient strategies in emergency navigation using edge computing,” IEEE Access, vol. 8, pp. 54441–54455, 2020. [Google Scholar]
4. C. Wang, H. Lin, R. Zhang and H. Jiang, “A situation-aware emergency navigation algorithm with sensor networks,” IEEE Transactions on Mobile Computing, vol. 16, no. 4, pp. 1149–1162, 2016. [Google Scholar]
5. A. Depari, A. Flammini, D. Fogli and P. Magrino, “Indoor localization for evacuation management in emergency scenarios,” IEEE Workshop on Metrology for Industry 4.0 and IoT, vol. 1, pp. 146–150, 2018. [Google Scholar]
6. H. Yetgin, K. T. K. Cheung, M. El-Hajjar and L. H. Hanzo, “A survey of network lifetime maximization techniques in wireless sensor networks,” IEEE Communications Surveys & Tutorials, vol. 19, no. 2, pp. 828–854, 2017. [Google Scholar]
7. B. Prabhu, M. Pradeep, and E. Gajendran, “Military applications of wireless sensor network system,” A Multidisciplinary Journal of Scientific Research & Education, vol. 2, no. 12, pp. 164–168, 2016. [Google Scholar]
8. A. K. Paul and T. Sato, “Localization in wireless sensor networks: A survey on algorithms, measurement techniques, applications and challenges,” Journal of Sensor and Actuator Networks, vol. 6, no. 4, pp. 1–24, 2017. [Google Scholar]
9. R. C. Shit, S. Sharma, D. Puthal and A. Y. Zomaya, “Location of things (LoTA review and taxonomy of sensors localization in IoT infrastructure,” IEEE Communications Surveys & Tutorials, vol. 20, no. 3, pp. 2028–2061, 2018. [Google Scholar]
10. G. Tuna and V. C. Gungor, “A survey on deployment techniques, localization algorithms, and research challenges for underwater acoustic sensor networks,” International Journal of Communication Systems, vol. 30, no. 17, pp. e3350, 2017. [Online]. Available: https://onlinelibrary.wiley.com/doi/abs/10.1002/dac.3350. [Google Scholar]
11. P. Shrivastava, “A hybrid sink repositioning technique for data gathering in wireless sensor networks,” Wireless Sensor Networks: Insights and Innovations, 2017. [Online]. Available: https://www.intechopen.com/books/wireless-sensor-networks-insights-and-innovations/a-hybrid-sink-repositioning-technique-for-data-gathering-in-wireless-sensor-networks. [Google Scholar]
12. Z. Vincze, D. Vass, R. Vida, A. Vidács and A. Telcs, “Adaptive sink mobility in event-driven multi-hop wireless sensor networks,” Proc. of the First Int. Conf. on Integrated Internet Ad Hoc and Sensor Networks, Nice, France, vol. 138, pp. 13–23, 2006. [Google Scholar]
13. Y. Yuan, M. Chen and T. Kwon, “A novel cluster-based cooperative MIMO scheme for multi-hop wireless sensor networks,” EURASIP Journal on Wireless Communications and Networking, vol. 2006, no. 1, pp. 1–9, 2006. [Google Scholar]
14. P. Nayak and B. Vathasavai, “Energy efficient clustering algorithm for multi-hop wireless sensor network using type-2 fuzzy logic,” IEEE Sensors Journal, vol. 17, no. 14, pp. 4492–4499, 2017. [Google Scholar]
15. S. Goyal and M. S. Patterh, “Modified bat algorithm for localization of wireless sensor network,” Wireless Personal Communications, vol. 86, no. 2, pp. 657–670, 2016. [Google Scholar]
16. X. Yang, Z. Gao and Q. Niu, “Unmanned aerial vehicle–assisted node localization for wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 13, no. 12, pp. 1–13, 2017. [Google Scholar]
17. N. Liu, J. S. Pan and J. Wang, “An adaptation multi-group quasi-affine transformation evolutionary algorithm for global optimization and its application in node localization in wireless sensor networks,” Sensors, vol. 19, no. 19, pp. 1–25, 2019. [Google Scholar]
18. I. Strumberger, M. Beko, M. Tuba, M. Minovic and N. Bacanin, “Elephant herding optimization algorithm for wireless sensor network localization problem,” Doctoral Conf. on Computing, Electrical and Industrial Systems, Costa de Caparica, Portugal, vol. 521, pp. 175–184, 2018. [Google Scholar]
19. X. Ma, W. Liu and Z. Wang, “Node localization of wireless sensor network based on secondary correction error,” International Symp. on Parallel Architecture, Algorithm and Programming, Haikou, China, vol. 729, pp. 142–151, 2017. [Google Scholar]
20. H. M. Kanoosh, E. H. Houssein and M. M. Selim, “Salp swarm algorithm for node localization in wireless sensor networks,” Journal of Computer Networks and Communications, vol. 2019, no. 4, pp. 1–12, 2019. [Google Scholar]
21. S. Bhowmik, R. Kar and C. Giri, “Fuzzy node localization in wireless sensor network,” in IEEE Int. Conf. on Wireless Communications, Signal Processing and Networking (WiSPNET), pp. 1112–1116, 2016. [Google Scholar]
22. J. Cheng and L. Xia, “An effective cuckoo search algorithm for node localization in wireless sensor network,” Sensors, vol. 16, no. 9, pp. 1–17, 2016. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |