DOI:10.32604/cmc.2022.021077

| Computers, Materials & Continua DOI:10.32604/cmc.2022.021077 |  |
| Article |
Atmospheric Convection Model Based Digital Confidentiality Scheme
1Department of Applied Mathematics and Statistics, Institute of Space Technology, Islamabad, Pakistan
2Department of Mathematics, College of Science, King Khalid University, Abha, 61413, Saudi Arabia
3College of Computing and Information Technology, University of Tabuk, Tabuk, 71491, Saudi Arabia
4Department of Mathematics, Statistics and Physics, Qatar University, Doha, 2713, Qatar
*Corresponding Author: Majid Khan. Email: mk.cfd1@gmail.com
Received: 22 June 2021; Accepted: 04 August 2021
Abstract: Nonlinear dynamics is a fascinating area that is intensely affecting a wide range of different disciplines of science and technology globally. The combination of different innovative topics of information security and high-speed computing has added new visions into the behavior of complex nonlinear dynamical systems which uncovered amazing results even in the least difficult nonlinear models. The generation of complex actions from a very simple dynamical method has a strong relation with information security. The protection of digital content is one of the inescapable concerns of the digitally advanced world. Today, information plays an important role in everyday life and affects the surroundings rapidly. These digital contents consist of text, images, audio, and videos, respectively. Due to the vast usage of digital images in the number of social and web applications, its security is one of the biggest issues. In this work, we have offered an innovative image encryption technique based on present criteria of confusion and diffusion. The designed scheme comprises two major nonlinear dynamical systems. We have employed discrete fractional chaotic iterative maps to add confusion capability in our suggested algorithm and continuous chaotic Lorenz system. We have verified our offered scheme by using statistical analysis. The investigations under the statistical tests suggested that our proposed technique is quite reasonable for the security of digital data.
Keywords: Lorenz atmospheric convection model; fractional logistic map; image encryption; S-box
Nowadays, society is full of the sphere of information in a different form of the digital medium. The advancement in different private and public sectors demands new and innovative results towards handling big data with low-cost technologies. Digital information that travels through an insecure line of communication plays an important role because of emerging technology usage at a high scale on social media and web applications etc. This insecurity while utilizing these applications on small and large computational machines lost the confidence of the net user. The issue of information security not just stops here it extended towards the regime of corporate organizations which includes business, banking sectors, and commercial firms. The information breaches are now increasing widely due to the vast number of facilities available online for instance transactions and online banking. The online services increased by a daily boom of commercial organizations due to competition among different officialdoms in an advanced era. Different companies created their research and development teams that mainly deal with cybersecurity. The security of information and online data streams gradually increase to fifth-generation technologies and the same happened in the area of information security where one cannot remain away from cybersecurity attacks. There have been several mechanisms used for the security of information which includes cryptography, watermarking, and steganography. The privacy of the given information can be assured by using cryptography. The watermarking and information hiding techniques are utilized for both information integrity and authentication. The most fruitful area of information preserving, and confidentiality is chaotic cryptography. With the advancement in the area of nonlinear dynamics, several discrete and continuous chaotic systems were developed and tested against different chaotic tests. The relations between chaos and cryptography have been a mode of discussion for two decades [1]. Similarities among different concepts of chaos and cryptography make it a reasonable candidate for the encryption of digital data. The notion of diffusion and confusion in 1949 proposed by Claude Shannon added new directions in information security. Then different new block ciphers were designed which used confusion and diffusion. The addition of diffusion and confusion in a block cipher added a robust security layer against different cryptographic attacks. In modern cryptosystems, the notion of Claude Shannon is term as substitution-permutation network (SP-network) [2]. The idea of confusion is to make the relations between encrypted data and secret key as difficult as possible which can be achieved through substitution, whereas diffusion is used to scatter the statistical construction of original information over the greater part of encrypted information [3]. The diffusion is achieved through permutation which simply means to reorder certain bits. By utilizing SP-network collectively, it is quite hard to detect any non-uniform change in cipher-text. The same idea of SP-network is now followed by different chaos-based encryption algorithms [4–11].
Several image encryption schemes utilized chaotic dynamical systems for the confidentiality of digital contents [12–16]. Chaotic schemes were also helpful for the formulation of nonlinear components of block cipher known as Substitution boxes (S-boxes) [17–21]. The principal idea of constructing nonlinear components through chaotic dynamical systems is to add strong confusion capability which is surely one of the vital components in modern block ciphers. There exist many encryption structures in literature with weak security and vulnerability in implementation design due to skipping the notion of confusion and diffusion [22–25]. A small change in chaotic parameters produces a dynamically different trajectory similarly small variations in chaotic parameters produce a completely new substitution box. The main contribution of this work is as follows:
1. The idea of this research is to produce a nonlinear component by using a fractional chaotic logistic map.
2. Implementation of constructed S-box in the suggested chaos-based image encryption method.
3. The scheme also entails a continuous chaotic Lorenz system for diffusion that ultimately produces permutation [6].
4. Some security assessments are performed to examine the efficiency and robustness of offered system along with some statistical analysis.
This manuscript consists of seven sections. The basic concepts are reviewed in Section 2. The mathematical model of the Lorenz chaotic system is offered in Section 3. The offered substitution box and image encryption technique are presented in segments 4 and 5 correspondingly. The statistical analyses are presented in Section 6. As a final point, the conclusion is shown in the last section.
In this section, we have presented some basic keys, which are essential for the interpretation of innovative image encryption techniques though suggested S-box based on discrete fractional chaotic iterative maps.
The logistic map is one of the prominent and extensively utilized one dimensional (1-D) discrete logistic chaotic map proposed by R. M May, whose state evolves corresponding to the following mathematical equation [4]:
where
2.2 Riemann-Liouville Fractional Derivative
If
where
is known as Riemann-Liouville fractional derivative with order
2.3 Fractional Logistic Equation
For all
which is called fractional logistic equation (FLE) of order
3 Mathematical Formulation of Atmospheric Convection Model
In 1963, Edward Lorenz proposed a simple mathematical model for atmospheric convection. The mathematical derivation of Lorenz equations is given in [6,7]. There are three different models of chaotic Lorenz systems which are given as follows:
Viscosity + diffusion:
Buoyancy + diffusion:
Viscosity + buoyancy
4 Proposed S-Box Using Fractional Chaotic Map
The one-dimensional logistic map which was designed in 1967 by May [4] is one of the modest discrete nonlinear chaotic schemes which shows chaotic performance; its mathematical equation is described by the following iterative formula.
By using the concept of the fractional logistic map, taking
where x is variable of the map and

5 Suggested Image Encryption Algorithm
In this segment, a fractional chaotic S-box-based image encryption technique is suggested. The intended scheme offers less computational time and cost of image encryption parallel to other methods which are available in the literature. The working steps of offered encryption scheme are as follows:
Step 1: Choose a standard color image as input having size
Step 2: Divide the digital color image into three channels that are Red, Green, and Blue.
Step 3: Utilize different proposed substitution boxes on each image layer individually.
Step 4: Run Lorenz fractional chaotic equations and store all the generated output in one matrix.
Step 5: Arrange matrix in ascending order by using the command of the sort in MATLAB and
store the sorting position of each element in one matrix.
Step 6: Now shuffle the pixels of each image layer corresponding to the sorting position matrix
obtained in step 5.
Step 7: Apply bitwise XOR with random array generated from Lorenz chaotic equation on each
layer of the image obtained in step 6.
Step 8: Concatenate all the layers produced from step 7 in one image.
Step 9: The image attained from step 8 is the required encrypted image.
The structure diagram of the offered image encryption algorithm is depicted in Fig. 1.
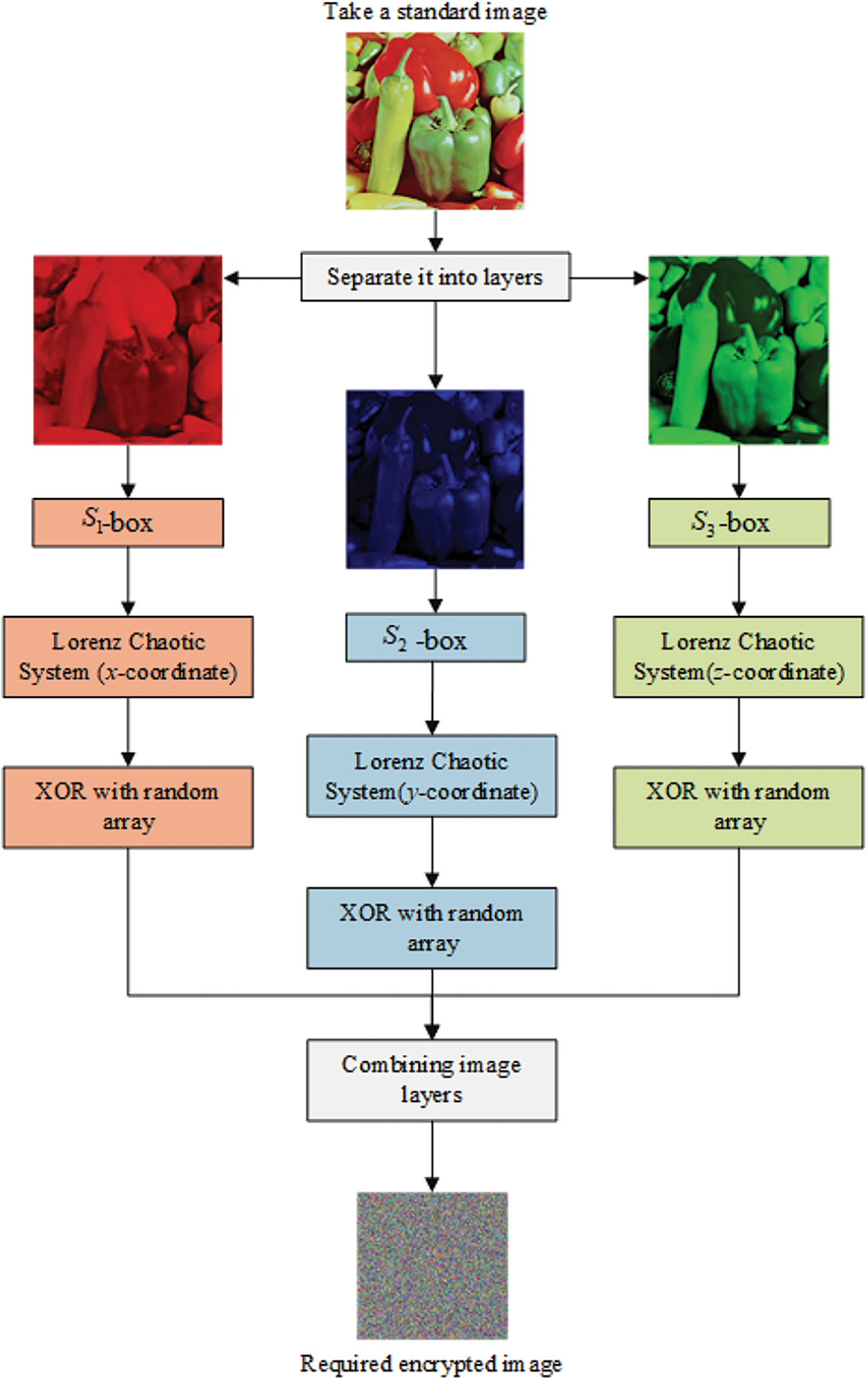
Figure 1: Design of proposed encryption scheme
Decryption of Image
The procedure of decryption is the same as the encryption procedure in reverse order. The original image can be retrieved easily by utilizing the decryption procedure. Figs. 2 and 3 show some standard layer-wise encrypted images through the proposed scheme.
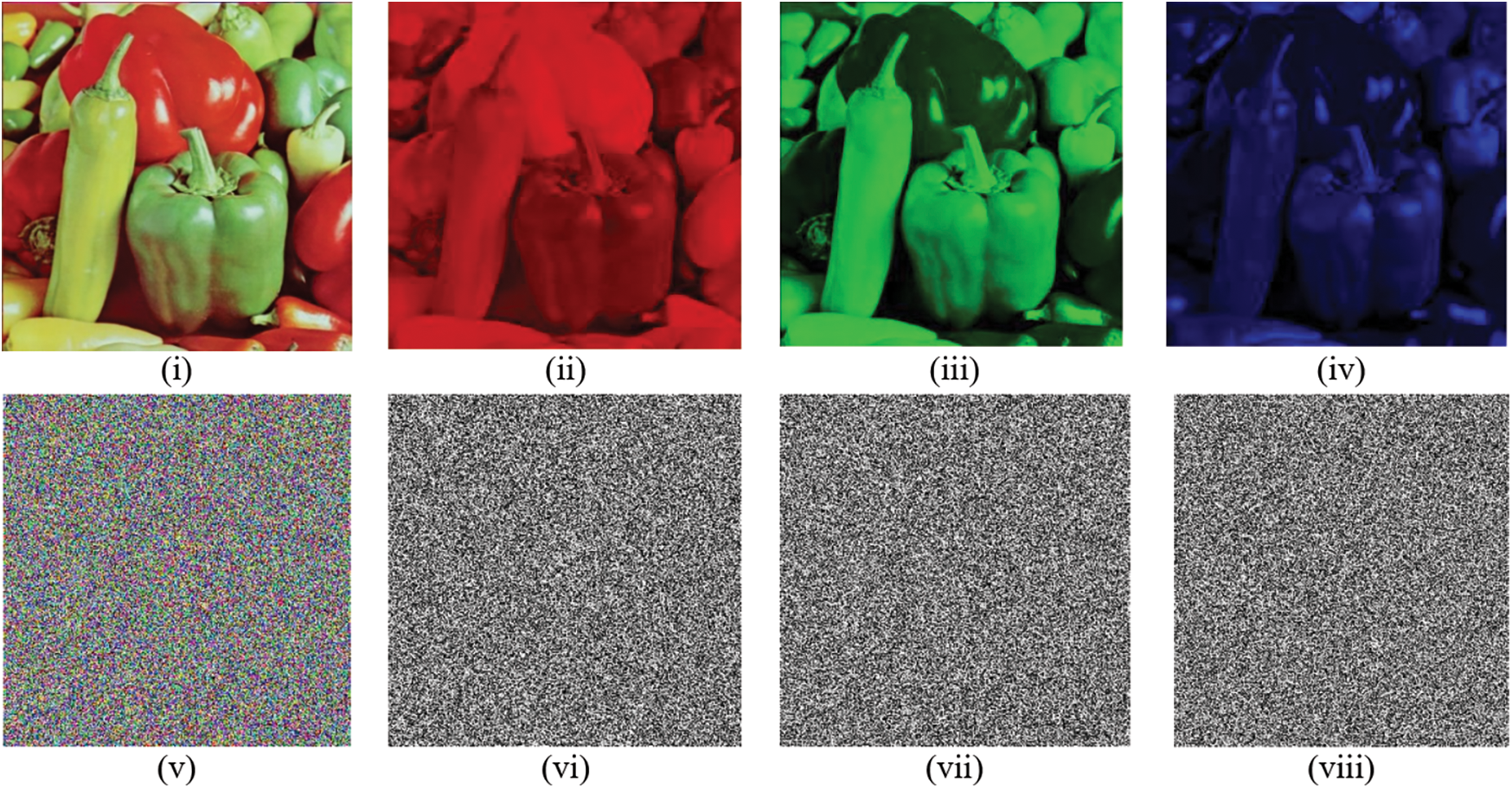
Figure 2: (i–iv) Original layers of peppers image (v–viii) Encrypted layers of Peppers image
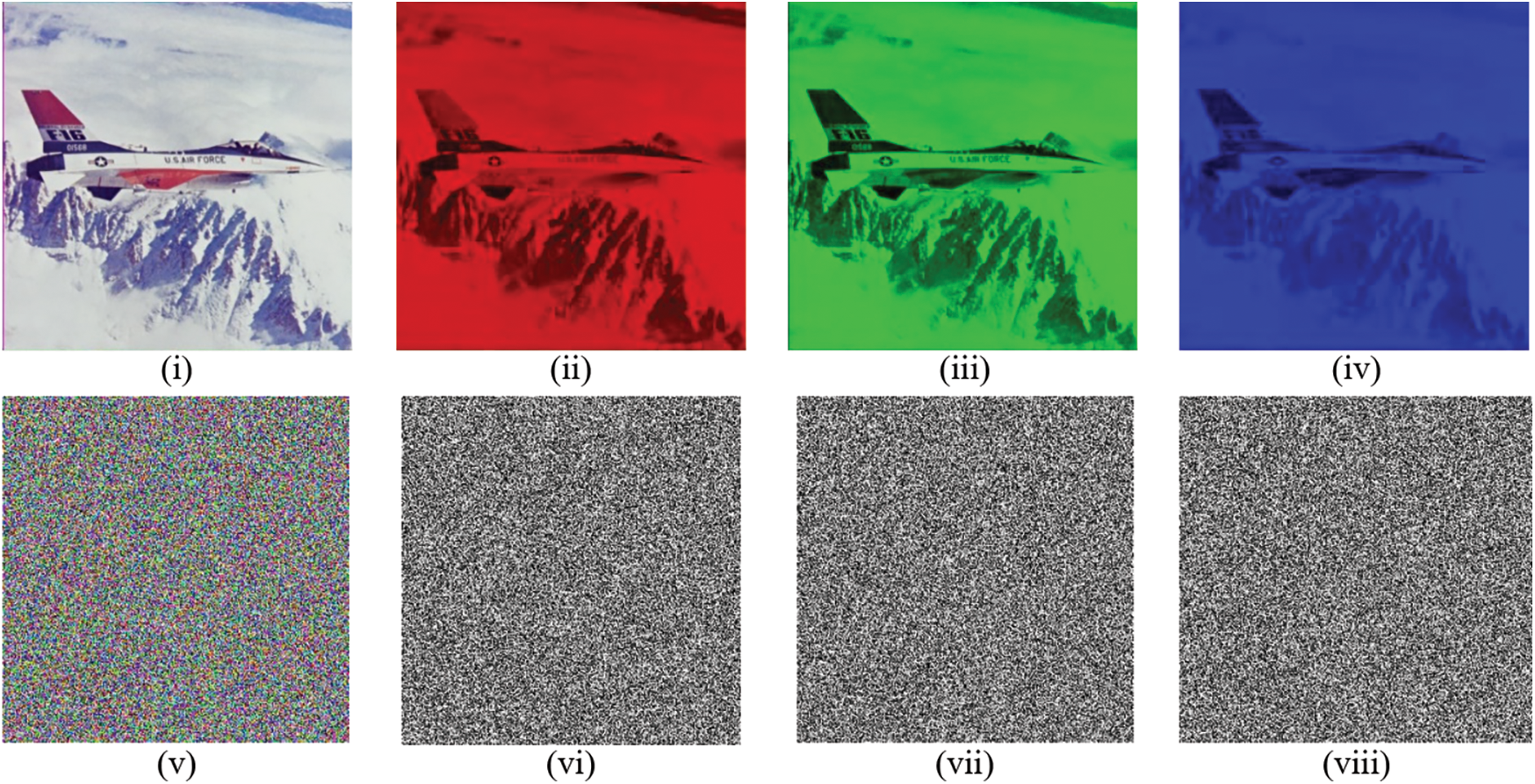
Figure 3: (i–iv) Original layers of airplane image (v–viii) Encrypted layers of Airplane image
6 Security Assessment of Suggested Technique
This part of the manuscript describes various safety constraints to explain the robustness of the suggested technique. Some statistical analyses are accumulated by utilizing plain and their respective cipher images. These statistical analyses comprise correlation, entropy, uniformity, similarity measures, pixel modification, and sensitivity of plaintext. Each of the analyses is examined in an aspect to validate the efficiency of the encryption technique [15,16].
The randomness of a cipher can also be determined by NIST-800-22 test suite offered by the National Institute of Standard and Technology in 2001. NIST suite comprises several tests to analyze the arbitrariness in output data with probability values (p values). The p-values of each assessment must be greater than 0.001 for a robust encryption scheme. The results of NIST for Peppers encrypted image of size 256 × 256 are depicted in Tab. 2. The obtained results reflect that the encrypted image layers are highly randomized therefore, the offered encryption scheme is robust against all statistical attacks.

The histogram is the plot of the number of pixels for each tonal value. The histogram of original images contains sharp peaks in its distribution. An ideal encryption scheme yields a cipher image with uniform histogram distribution. 3D histograms of the plain and enciphered Peppers image of size 256 × 256 image layers are displayed in Fig. 4. From experiments, we can analyze that the scattering of pixels of the encrypted images is uniform, which can extensively decrease the values of correlation among the pixels. Consequently, histogram analysis indicates that our encryption algorithm is protected besides attacks.
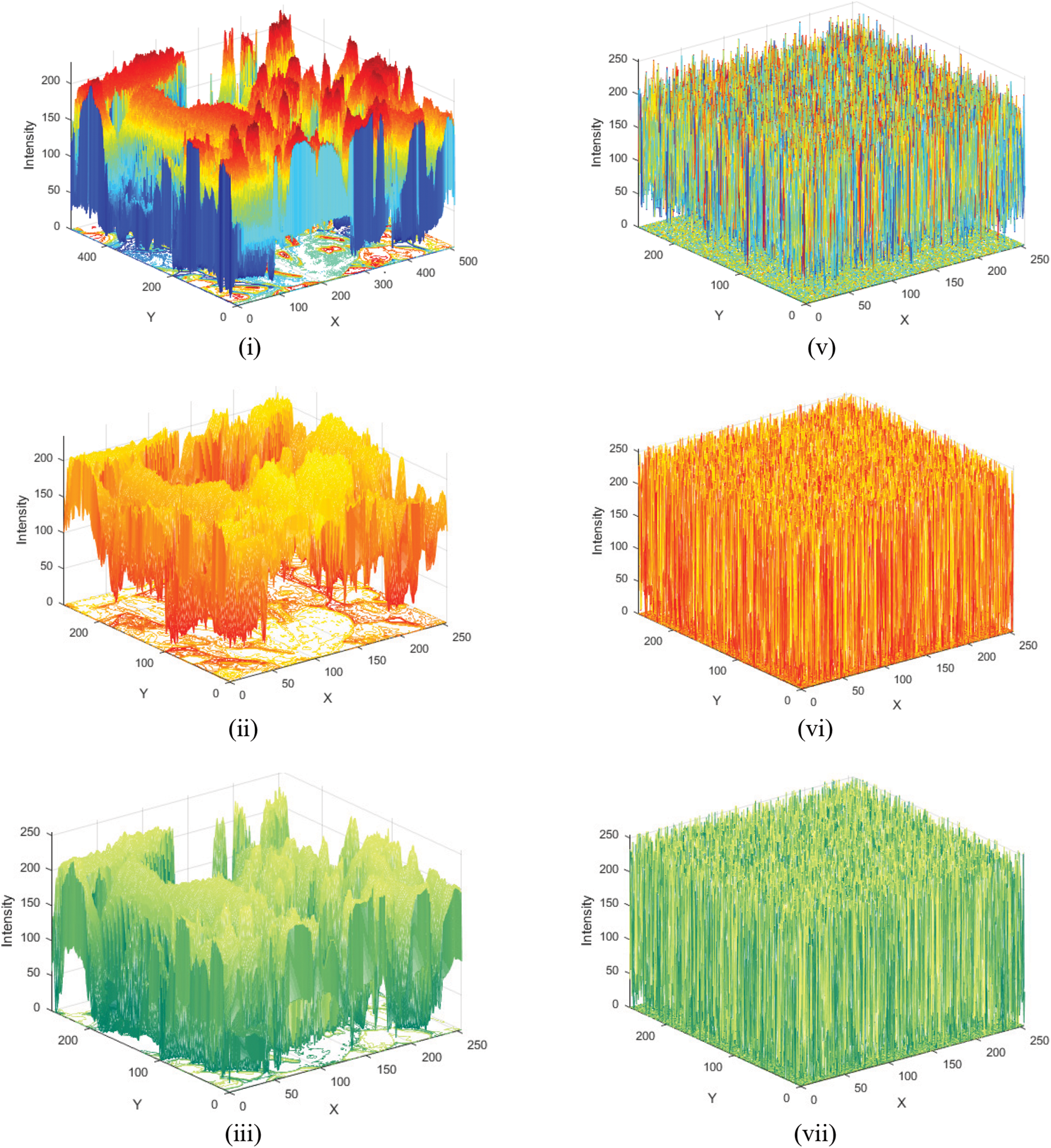
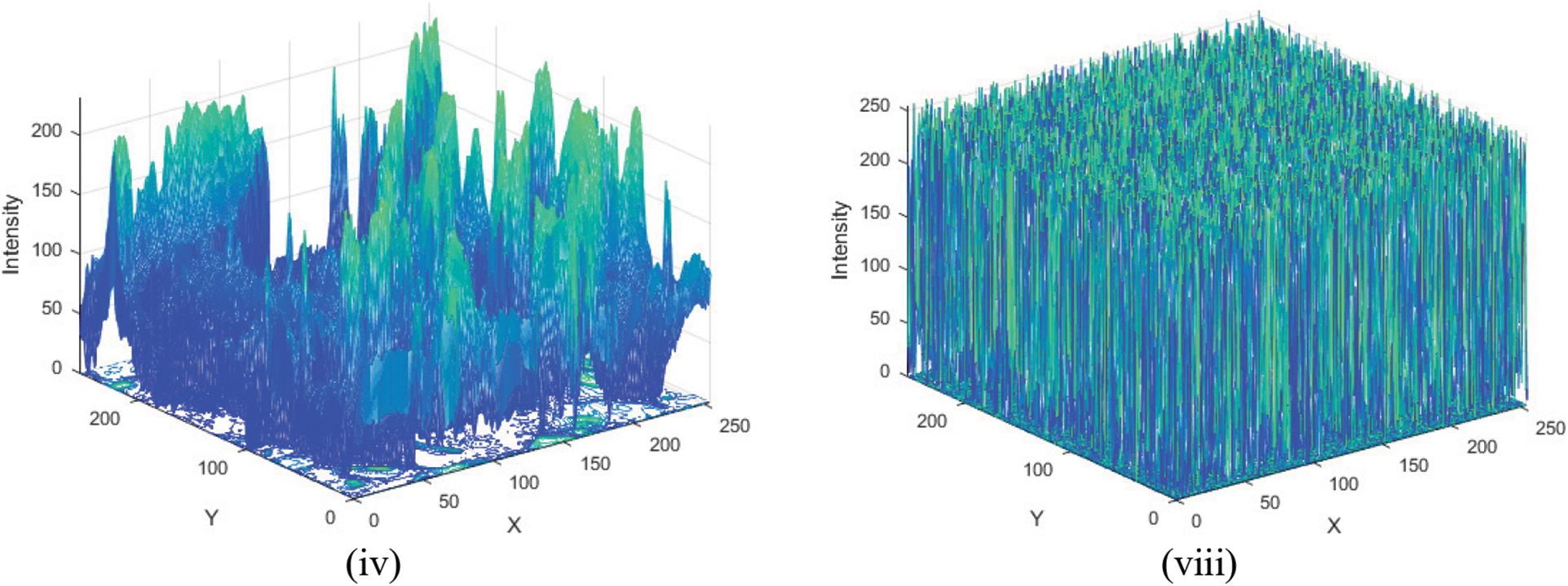
Figure 4: (i–iv) Histograms of peppers image of size 256 × 256 original layers (v–viii) Histograms of peppers image encrypted layers
The neighboring pixels of an image are highly correlated in horizontal, diagonal, and vertical directions. The original image exhibits the high correlation value, and alternatively, for an ideal encryption scheme, the correlation value must be less and approximately near to 0. A smaller value of the correlation of encrypted images leads to a secure encryption algorithm which reduces the possibility of attacks. The correlation coefficient of image pixels can be calculated by:
where
where M and N are the estimations between two nearby pixels at grayscale in the digital image. The correlation coefficients for the plain and enciphered image along horizontal, vertical, and diagonal axes are presented in Tab. 3.
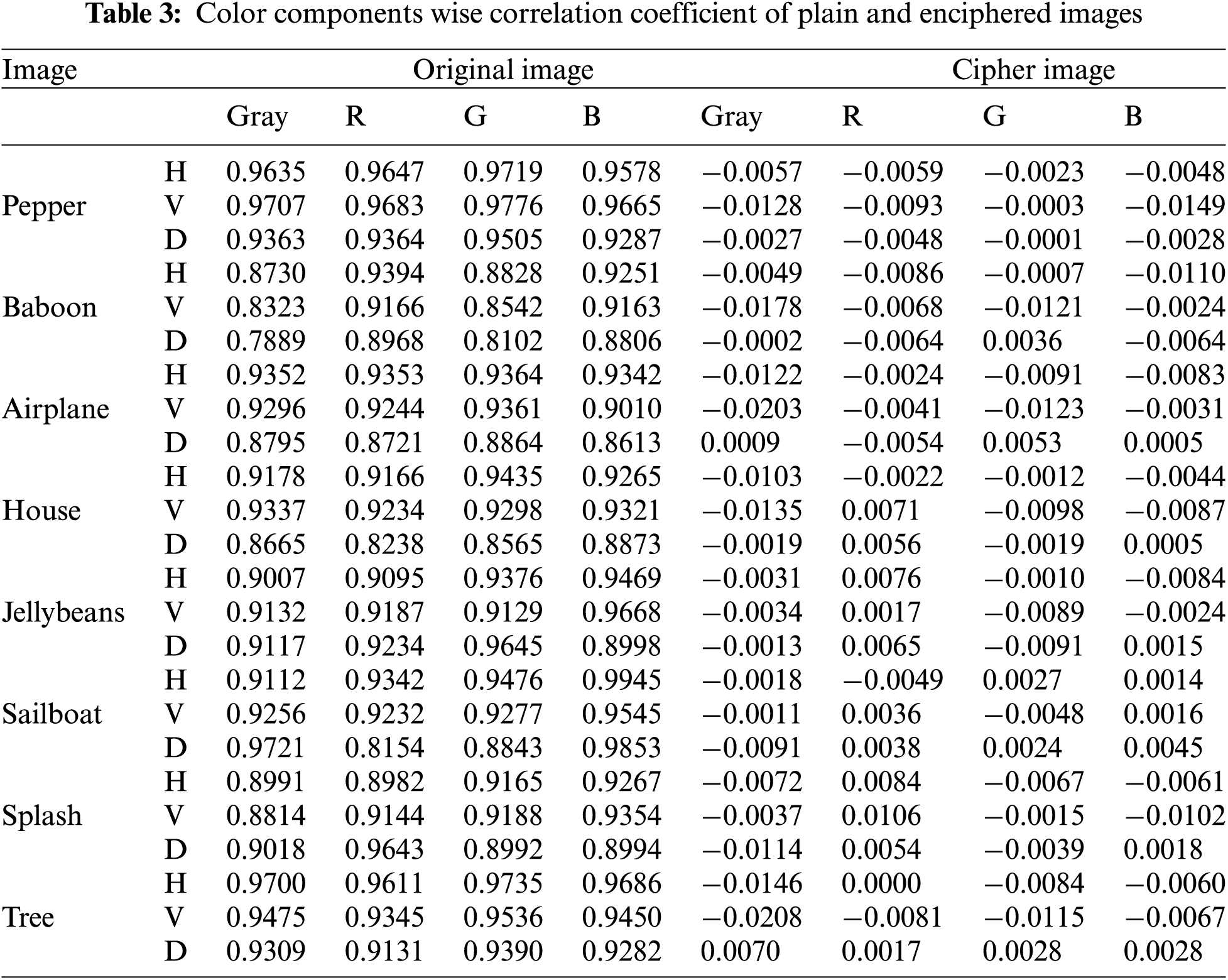
where H, V, and D shows the horizontal, vertical, and diagonal direction of the image, respectively. To quantify the correlation coefficient, we randomly choose 2500 sets of two adjoining pixels in three ways (horizontal, diagonal, and vertical) from encrypted and original image data. Tab. 3 presents the corresponding experimental results. From Tab. 3 we can examine that the values of correlation of original images are near to one, whereas the values of correlation of the enciphered images are near to 0. From the depicted results we can see that the suggested encryption technique reduces the correlation among image pixels accurately. Fig. 5, presents the adjacent pixel distributions in the horizontal, diagonal, and vertical axes for Peppers images. Figs. 5i–5iv presents the correlation of plain images, although Figs. 5v–5viii represents the correlation of encrypted images. As from these Fig. 5, we can see that the plain images exhibit high values of correlation, on the other hand, the enciphered images have a random distribution of correlation. The test results indicate that our encryption scheme has a very good influence on decreasing correlation. Therefore, the offered encryption algorithm is robust against all the attacks related to the correlation of pixels.
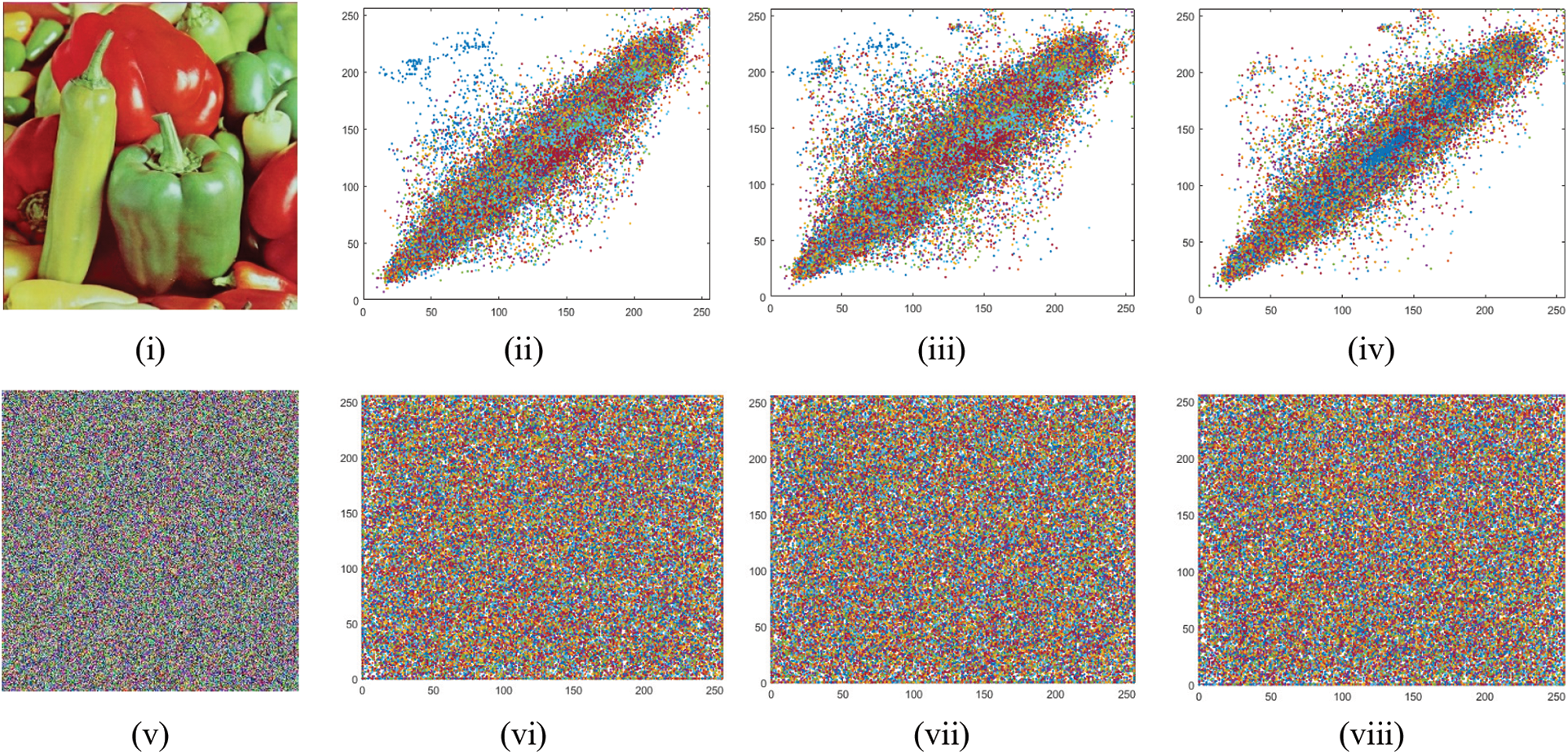
Figure 5: (i–iv) Correlation coefficient among pixel pairs for plain peppers image; (v–viii) Correlation coefficient among pixel pairs for enciphered peppers image
The distribution of gray values of the image is evaluated as the information entropy. Entropy increases with an increase in the uniformity of distribution of gray values. The encryption scheme is said to be highly secure if less information is leaked from the gray distribution value of images. Information entropy can be measured by the mathematical equation:
where
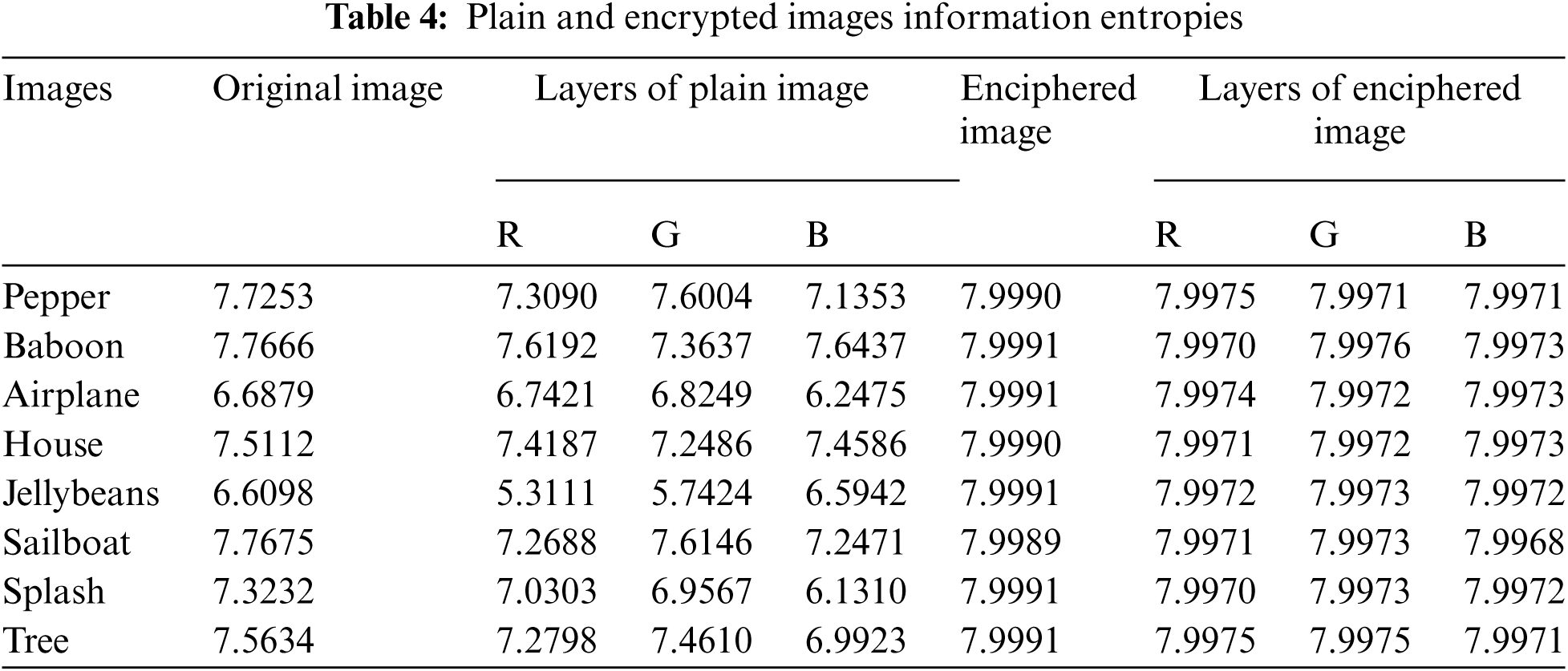
6.5 Distance Based Measurements
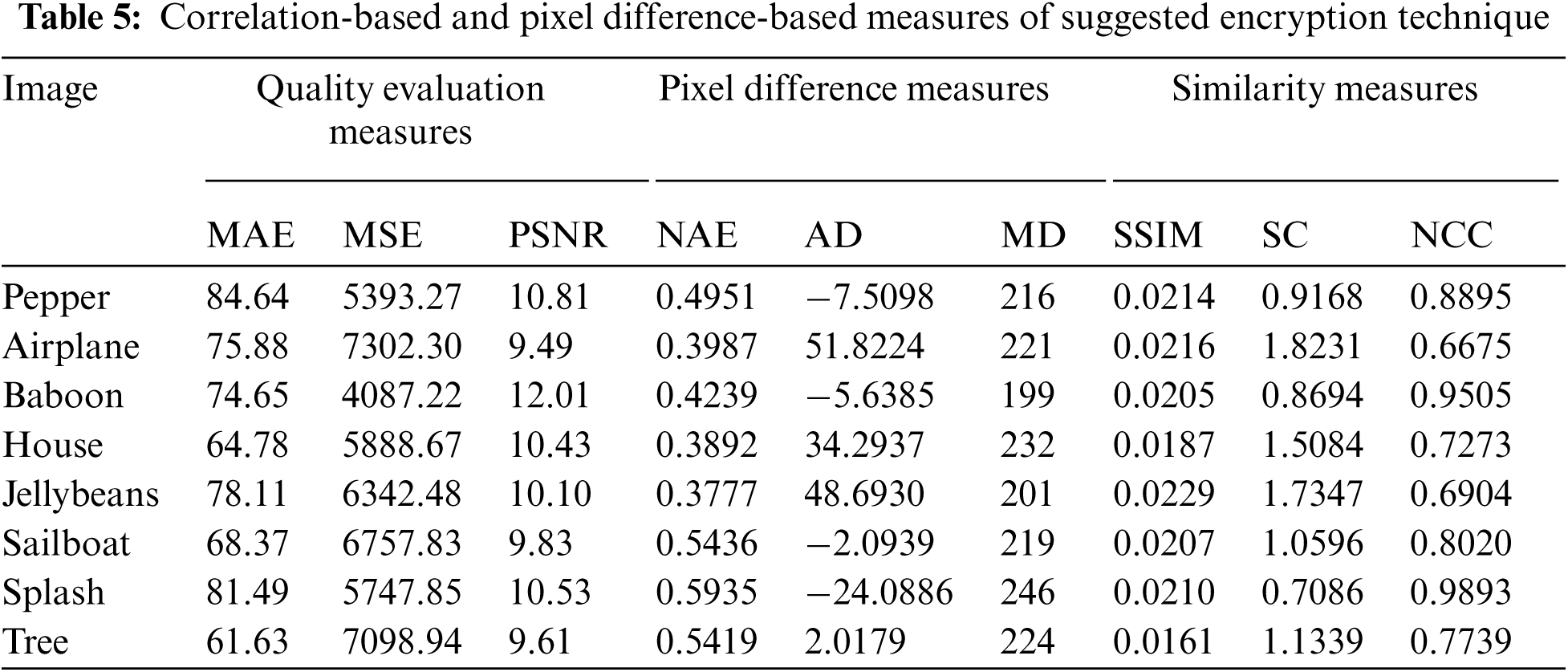
The image quality assessment based on pixel modification measures are done by calculating maximum difference (MD), mean square error (MSE), the average difference (AD), peak signal to noise ratio (PSNR), normalized correlation (NCC), normalized absolute error (NAE) and structure content value (SC). These are the error metrics that are utilized to compare different images.
Maximum Difference is also known as MD shows the maximum difference among the plain and enciphered images. The maximum difference can be represented in the mathematical form as follows:
Our analyzed results are presented in Tab. 5 which reflects that with the boost in the value of MD, the robustness of the encryption structure is increased.
The normalized absolute error also named NAE is represented in mathematical form as follows:
NAE defines the proportion of how far the enciphered digital data is from the plain image with the estimation of zero being impeccable similar images. From Tab. 5, we can see that the increase in the approximation of normalized absolute error demonstrates a good description of scrambled images with encryption procedure.
The average difference can be mathematically defined as:
The value of the average difference is preferably zero for two similar digital images. The calculated results of the average difference are presented in Tab. 5, which indicates that the suggested technique is robust against all possible differential assaults.
6.6 Mean Squared Error and Peak Signal to Noise Ratio Analysis
The encryption technique utilized to the original data adds noise to the actual digital contents therefore an encrypted digital image is not equivalent to the plain digital image. We process the MSE among the plain and encrypted images to evaluate the level of encryption. MSE can be formulated in mathematical form as:
where
where
Normalized cross-correlation, structure content, and structure similarity are utilized to estimate the resemblances between two signals. These are some standard analyses for measuring that original and encrypted images are analogous or different.
Normalized cross-correlation also known as NCC has been generally utilized as a metric. To check the level of difference (or resemblance) between two images. The NCC ranges from –1 and 1. Mathematically, the normalized correlation of the image is computed by the given formula [16–21]:
where X × Y denotes the size of plain image O and cipher image E both. Our analyzed results presented in Tab. 5 reveals that the calculation of NCC for encryption is near to unity which distinctly means that the suggested technique contains strong divergences among the pixels of original and enciphered images.
Structural content is also known as SC, measures the collective weight of a plain image to the respective encrypted image. It is, hence, a global metric. If the value of SC exhibits as one, at that point the encrypted image represents the better quality, and an increase in the assessment of SC denotes that the image is very low in quality. The mathematical form of structural content is as:
From Tab. 5 we can observe that our encryption technique gives the evaluation of SC which is not very near to unity due to the diffusion and confusion like noise disorder in the plain image.
6.8 Plaintext Sensitivity Analysis
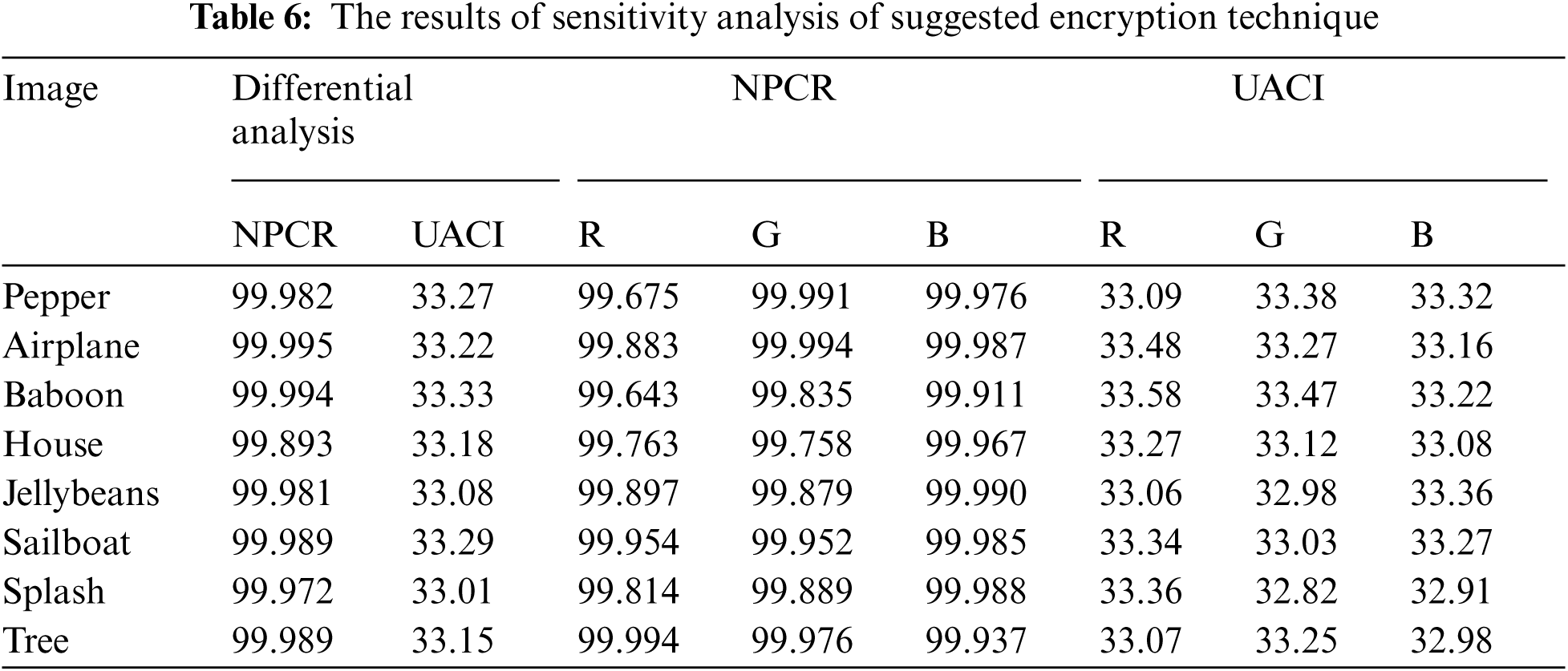
To check the randomness of the encryption technique, diffusion is an important constraint that must be assessed. Two basic methods are implemented recognized as the number of changing pixel rate (NPCR), and the unified averaged changed intensity (UACI) to examine the impact of one-bit alteration in the plain content and the enciphered content. NPCR focuses on the number of pixels that change the assessment in differential assaults although the UACI concentrates on the AD (averaged difference) among two paired enciphered images. Assume encrypted image previously and afterward, one-pixel change in original content image is
where
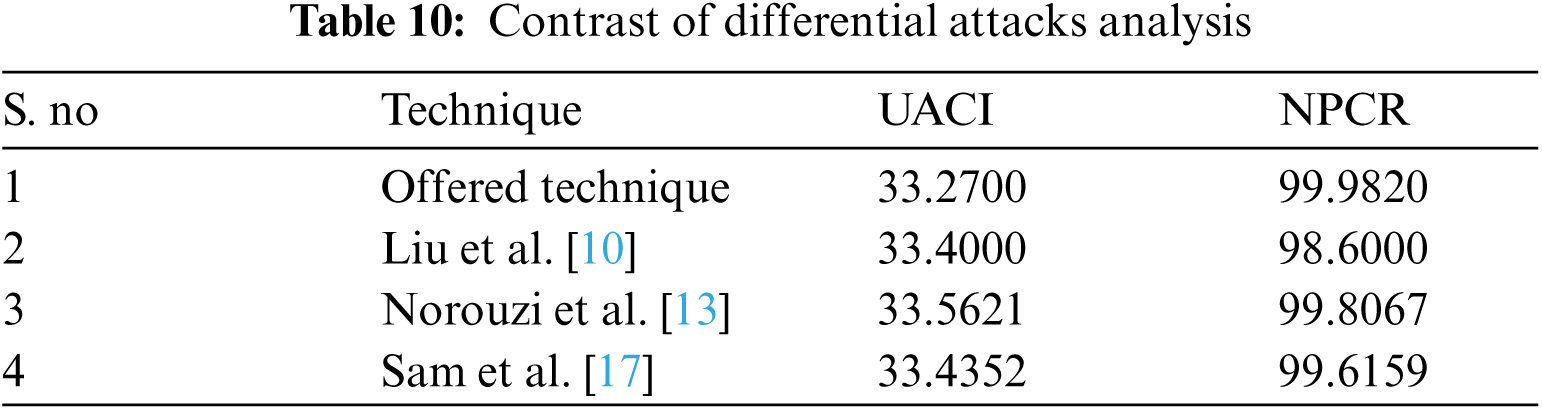
Tab. 6 presents the values of, UACI (≈33%) and NPCR (>99%) for every layer of image for nine different standard images. Investigational consequences demonstrate the estimated variance of UACI and NPCR are actual near to the theoretical measures, which explain the validity of theoretical standards. Hence our proposed encryption method is resilient against differential attacks.
6.9 Z1 Test for Randomness (0–1 Test)
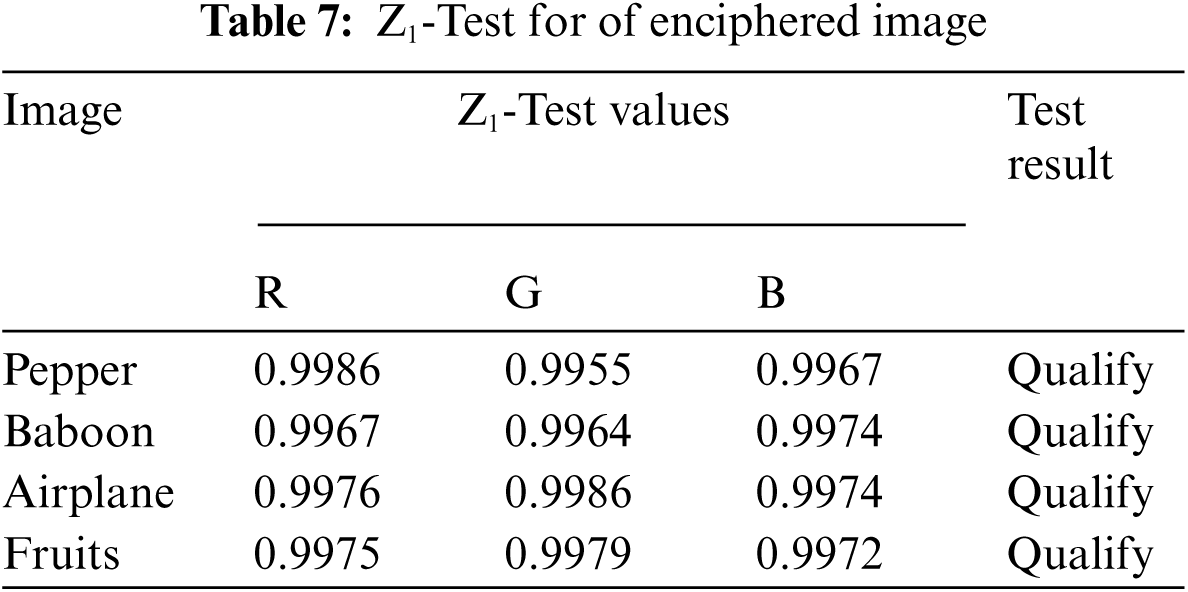
In this section, we have applied the 0–1 test for the chaos which checks the randomness of enciphered images. When the value of the Z1 test is near to one it means that the proposed scheme defines good randomness which shows that it is secure against differential attacks. On the other side, if the value of this test is near zero, this means the test is failed and there is no chaos in the encrypted image. Here we have presented analyzed results in Tab. 7 which defines the Z1 test value for the layer-wise encrypted image.
6.10 Comparative Analysis with Standard Results
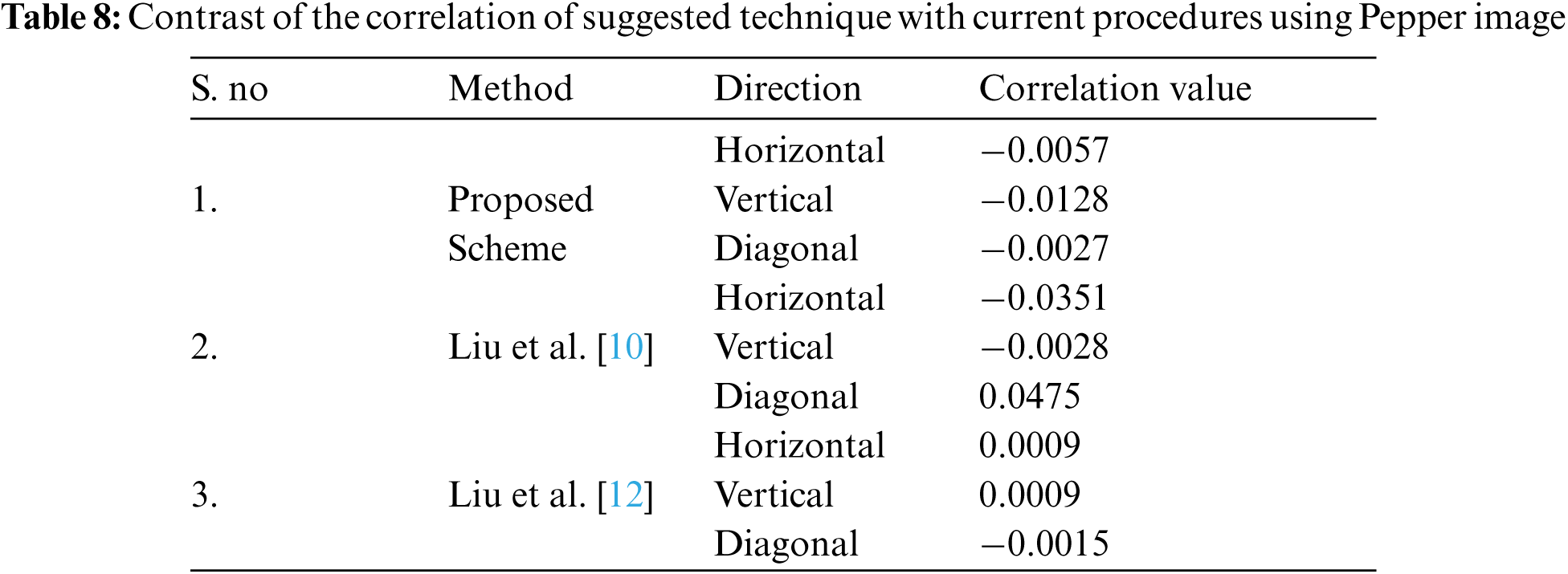
In this section, we compare the suggested encryption method with numerous states of the arts, which have high security. The comparison contains the following aspects: information entropy, correlation among different pixels of encrypted images, robustness to plaintext sensitivity analysis. Furthermore, from our experimental results, we can see that correlation values are high between three R, G, and B layers for plain color digital images, which makes data revelation conceivable. Moreover, we have presented a contrast of correlation coefficient of Pepper
Here we have offered a contrast of values of entropy of Pepper
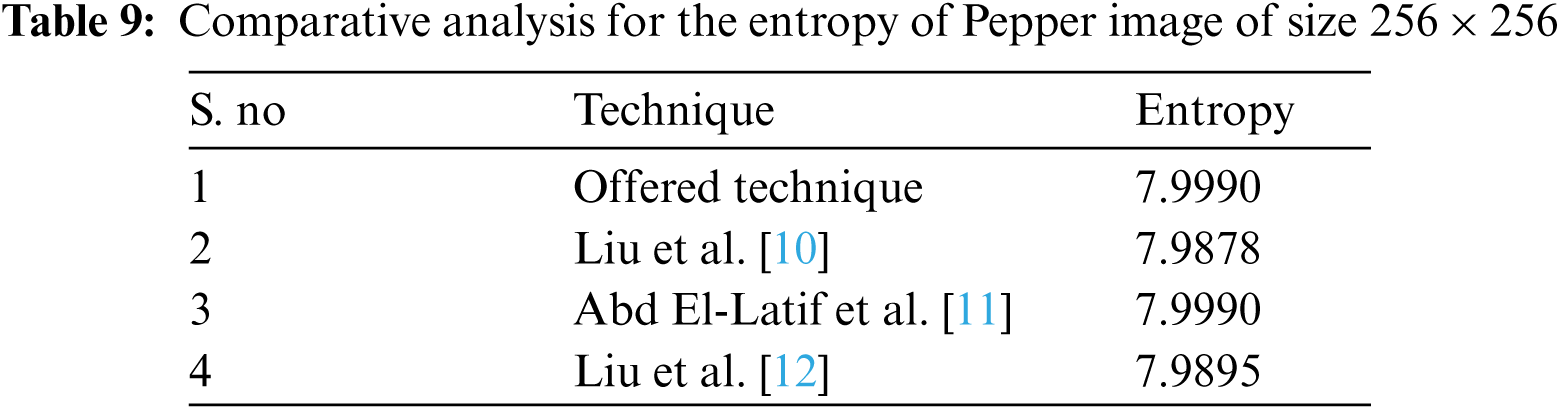
Thus, we have presented a UACI and NPCR of Pepper
The total time in seconds carried by the suggested technique to be run depending on the input length is described as time complexity. The algorithm was executed on a personal computer with an Intel(R) for the simulations. Core (TM) i7-7500U 2.90 GHz CPU and 8 GB memory capacity. MATLAB R2019b was utilized for the simulations. The execution time (in seconds) of different sizes of Peppers image is depicted in Tab. 11.

7 Conclusion and Future Recommendations
In this work, we have designed an innovative image encryption technique by employing a discrete one-dimensional logistic map and a continuous convective atmospheric model (Lorenz chaotic system). The first phase of offered image encryption scheme involves the construction of a nonlinear confusion component of the block cipher. This S-box is fundamentally accountable for the confusion in the anticipated encryption mechanism. In the second phase, we have employed a Lorenz chaotic system as a diffusion agent in the offered technique. The obtained outcomes are then contrasted with previously existing benchmarks in image encryption methods. Our anticipated image encryption scheme has quite satisfactory statistical results.
The suggested encryption structure can also be turned into a lightweight mechanism by offering small
Data Availability Statement: The data utilized in this manuscript are available in the open SIPI Image Database at http://sipi.usc.edu/database/.
Funding Statement: The author Mohammad Mazyad Hazzazi extend his appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through research groups program under Grant no. R.G.P. 2/150/42.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. L. Kocarev, “Chaos-based cryptography: A brief overview,” IEEE Circuits and Systems Magazine, vol. 1, no. 3, pp. 6–21, 2001. https://doi.org/10.1109/7384.963463. [Google Scholar]
2. T. T. K. Hue, C. V. Lam, T. M. Hoang and S. A. Assad, “Implementation of secure SPN chaos-based cryptosystem on FPGA,” in IEEE Int. Symp. on Signal Processing and Information Technology (ISSPIT), Ho Chi Minh City, Vietnam, pp. 129–134, 2012. https://doi.org/10.1109/ISSPIT.2012.6621274. [Google Scholar]
3. A. F. Webster and S. E. Tavares, “On the design of S-boxes,” Proceedings of Advances in Cryptology CRYPTO 85, Springer, Berlin, Heidelber, vol. 218, pp. 523–534, 1986, [Online]. Available: https://doi.org/10.1007/3-540-39799-X_41. [Google Scholar]
4. M. Lawnik, “Generalized logistic map and its application in chaos based cryptography,” in IOP Conf. Series: Journal of Physics, Conf. Series 936, Pafos, Cyprus, pp. 1–4, 2017. https://doi.org/10.1088/1742-6596/936/1/012017. [Google Scholar]
5. J. Munkhammar, “Chaos in fractional order logistic equation,” Fractional Calculus and Applied Analysis, vol. 16, no. 3, pp. 511–519, 2013, [Online]. Available: https://doi.org/10.2478/s13540-013-0033-8. [Google Scholar]
6. E. N. Lorenz, “Maximum simplification of the dynamic equations,” Tellus, vol. 12, pp. 243–254, 1960, [Online]. Available: https://doi.org/10.1111/j.2153-3490.1960.tb01307.x. [Google Scholar]
7. E. N. Lorenz, “Deterministic nonperiodic flow,” Journal of the Atmospheric Sciences, vol. 20, pp. 130–141, 1963, [Online]. Available: 2.0.CO;2}?>. [Google Scholar]
8. B. Saltzman, “Finite amplitude free convection as an initial value problem—I,” Journal of the Atmospheric Sciences, vol. 19, pp. 329–341, 1962, [Online]. Available: 2.0.CO;2}?>. [Google Scholar]
9. X. Liao, S. Lai and Q. Zhou, “A novel image encryption algorithm based on self-adaptive wave transmission,” Sig Process, vol. 90, no. 9, pp. 2714–2722, 2010, [Online]. Available: https://doi.org/10.1016/j.sigpro.2010.03.022. [Google Scholar]
10. H. Liu and X. Wang, “Color image encryption using spatial bit-level permutation and high-dimension chaotic system,” Optics Communications, vol. 284, pp. 3895–3903, 2011. [Google Scholar]
11. A. A. Abd El-Latif, L. Li, T. Zhang, N. Wang, X. Song et al., “Digital image encryption scheme based on multiple chaotic systems,” Niu Sens Imaging, vol. 13, pp. 67–88, 2012. [Google Scholar]
12. H. Liu and A. Kadir, “Asymmetric color image encryption scheme using 2D discrete-time map,” Signal Processing, vol. 113, pp. 104–112, 2015. [Google Scholar]
13. B. Norouzi and S. Mirzakuchaki, “A fast color image encryption algorithm based on hyper-chaotic systems,” Nonlinear Dyn, vol. 78, pp. 995–1015, 2014. [Google Scholar]
14. F. Masood, W. Boulila, J. Ahmad, S. Sankar, S. Rubaiee et al., “A novel privacy approach of digital aerial images based on mersenne twister method with DNA genetic encoding and chaos,” Remote Sensing, vol. 12, no. 11, pp. 1893, 2020. [Google Scholar]
15. F. Masood, J. Ahmad, S. A. Shah, S. S. Jamal and I. Hussain, “A novel hybrid secure image encryption based on julia set of fractals and 3D lorenz chaotic map,” Entropy, vol. 22, no. 3, pp. 274, 2020. [Google Scholar]
16. S. Arshad, M. Khan, I. Hussain “Pauli Half Spinning and Elliptic Curve Based Information Confidentiality Mechanism,” Journal of Theoretical Physics, vol. 60, pp. 3631–3650, 2021. [Google Scholar]
17. I. S. Sam, P. Devaraj and R. S. Bhuvaneswaran, “An intertwining chaotic maps based image encryption scheme,” Nonlinear Dyn, vol. 69, pp. 1995–2007, 2012. [Google Scholar]
18. S. I. Batool, M. Amin and H. M. Waseem, “Public key digital contents confidentiality scheme based on quantum spin and finite state automation,” Physica A: Statistical Mechanics and its Applications, vol. 537, pp. 1–17, 2020. [Google Scholar]
19. A. Alghafis, N. Munir, M. Khan and I. Hussain, “An encryption scheme based on discrete quantum map and continuous chaotic system,” Journal of Theoretical Physics, vol. 59, pp. 1227–1240, 2020, [Online]. Available: https://doi.org/10.1007/s10773-020-04402-7. [Google Scholar]
20. M. Khan and F. Masood, “A novel chaotic image encryption technique based on multiple discrete dynamical maps,” Multimedia Tools and Applications, vol. 78, no. 18, pp. 26203–26222, 2019. [Google Scholar]
21. M. Khan, F. Masood and A. Alghafis, “Secure image encryption scheme based on fractals key with fibonacci series and discrete dynamical system,” Neural Computing and Applications, vol. 32, pp. 11837–11857, 2020. [Google Scholar]
22. N. Munir, M. Khan, T. Shah, A. S. Alanazi and I. Hussain, “Cryptanalysis of nonlinear confusion component based encryption algorithm,” Integration, vol. 79, pp. 41–47, 2021. [Google Scholar]
23. I. E. I. Hanouti, H. El Fadili, and K. Zenkouar, “Breaking an image encryption scheme based on arnold map and lucas series,” Multimed Tools Appl, vol. 80, pp. 4975–4997, 2021, [Online]. Available: https://doi.org/10.1007/s11042-020-09815-4. [Google Scholar]
24. N. Munir, M. Khan, S. S. Jamal, M. M. Hazzazi and I. Hussain, “Cryptanalysis of hybrid secure image encryption based on julia set fractals and three-dimensional lorenz chaotic map,” Mathematics and Computers in Simulation, vol. 190, pp. 826–836, 2021. [Google Scholar]
25. C. X. Zhu and K. H. Sun, “Cryptanalysis and improvement of a class of hyperchaos based image encryption algorithms,” Acta Physica Sinica, vol. 61, no. 12, pp. 120503, 2012. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |