DOI:10.32604/cmc.2022.023732

| Computers, Materials & Continua DOI:10.32604/cmc.2022.023732 |  |
| Article |
5G Smart Mobility Management Based Fuzzy Logic Controller Unit
1Taif University-Khurma Univ. College-Department of Computer Sciences, Khurma, 2935, Kingdom of Saudi Arabia
2College of Computer and Information Sciences, Dep. of Computer Engineering and Networks, Jouf University, Skaka, K.S.A
*Corresponding Author: Chafaa Hamrouni. Email: cmhamrouni@tu.edu.sa
Received: 19 September 2021; Accepted: 05 November 2021
Abstract: In the paper, we propose a fuzzy logic controller system to be implemented for smart mobility management in the 5G wireless communication network. Mobility management is considered as a main issue for all-IP mobile networks future generation. As a network-based mobility management protocol, Internet Engineering Task Force developed the Proxy Mobile IPv6 (PMIPv6) in order to support the mobility of IP devices, and many other results were presented to reduce latency handover and the amount of PMIPv6 signaling, but it is not enough for the application needs in real-time. The present paper describes an approach based on the IEEE 802.21 Media Independent Handover (MIH) standard and PMIPv6, so we present a new vertical handover algorithm for anticipating handover process efficiently. Our object is to propose a smart mobility management that contribute in 5G wireless communication system network operating functions. Two proposed dynamic thresholds were successfully made to guaranty process triggering, and a new primitive MIH is proposed for signaling a needed handover to be done. Simulation results demonstrate a significant reduction of the handover delay, packet loss, handover blocking probability and signaling overhead. Simulation results and tests are accomplished.
Keywords: 5G; proxy mobile IPv6; media independent handover; wireless system; QoS; LTE; HDM
In a vertical handover situation, users are able to pass through several nodes based on different implemented algorithms and technologies [1–3] that affect communication quality of service (QoS). When a mobile node belongs to two different technologies [4,5] is obliged to pass through one cell to another, the mentioned phenomena emerges, and that's maintain a continuous and seamless communication. Several solutions were proposed for handover process [6,7]. However, we observe experimentally, packet loss and handover latency [8,9] are still very important and reduce the quality of service (QoS). In this context, we propose a solution for the 5G WiFi/LTE-A heterogeneous network mobility issues. This proposed new idea takes place during final step of the registration process in the handover procedure. It is based on the network mobility protocol, that means the proxy mobile (IPv6). We process the mobility protocol optimization [10,11], and since its operating time delay is less than the host-based mobility protocols delay (MIPv4 or MIPv6), that we call PMIPv6 [12,13], it presents several advantages able for minimizing the signaling overhead, reducing several requirements of MN's configuration, decreasing the movement detection time and improving the location privacy. In term of HL minimizing and compared to Mobile IPv6 [14]. Experimentally, the PMIPv6 is not able to minimize better the HL, it needs much more from PL, signaling overhead, powerless and authentication procedure is not yet accomplished. For an overall efficiency maximization, the IEEE 802.21 Media Independent Handover standard [15,16] is introduced. In this context, we constate that the mobility management is considered an important issue for the IP mobile networks, by the mobility management protocol for networks, several research works presented as presented, contribute in the Proxy Mobile IPv6 (PMIPv6) development to support IP devices mobility and or to reduce latency handover and the amount of PMIPv6 signaling. Our object is to mask dissimilarities basic technology for the upper layer, that validates united services operations. In order to ensure a good selection of suitable network to hand off depending on MIH use. In that case, the MN must query all surrounding networks, thus presenting a critical phase. IEEE 802.21 standard [17] is introduced to collect the maximum of information available in wireless networks, as well as to ensure the corresponding MIH layer integrated in PHY/MAC level.
The proposed new solution consists of handover mechanisms use, this phenomena is depending on MIH/PMIPv6. Our objective is vertical handover optimization mechanism [18] process. We contribute to add a pre-handover process, including a specific phases such time consuming for execution after actual handover decision explained by pre resources checking, pre_IP assignment, pre_Gauthentication and pre reservation. These mentioned steps are executed before handover decision is done. To predict the link quality degradation in advance, two thresholds are defined, as well as anticipating the phase preparation. In order to validate that an imminent handover decision is validate, an MIH primitive message is defined.
For HL minimization, with the 5 G WiFI and LTE-A, we introduce a tightly coupled architecture. E-UTRAN component trough LTE–Uu interface, a connection of UE is made to eNode B, and this whitout any interface. The main role of EUTRAN is to validate connection of UE and the core network. Serving gateway through S1–U interface is made by evolved packet. Interworking with untrusted non-3GPP IP access systems are provided by data gateway. For interworking compatibility within the 3GPP networks, the LTE-A rests on framework engineering development.
The LTE-A networks offload solution is guaranteed by widely deployed WiFi access point. WLAN interworking support is provided by LTE-A specifications [19], it includes seamless and non-seamless mobility, at core network level [20]. The Fig. 1 presents an arrangement in heterogeneous access networks, to ameliorete network-based localised mobility management: a new entity module named Handover Decision Maker is proposed in the protocol stack third layer [21]. Both the eNodeB and the UE is presented by HDM. By empowering the connection layer with a knowledge, the IEEE 802.21 MIH standard offers a consistent handover which is moved to a higher layers. It controls occasions and messages traded between the HDM and the diverse access technologies. All of media independent command services, media independent event services and media independent information services [22], are supported by media independent command services. Introducing MIH services enables effective events triggering and reduces in second layer the scanning delay, and accelerates the handover process. In the eNB, the HDM is responsible handover decision making according depending in criterion such the RSSI and the signal-to interference-plus-noise ratio. It collects in handover measurement collector to store them in measurement database. In order to collect different information, the HDM situated on the UE gives orders to both the HMC and the MIHF. For any information collection step, the HDM placed on UE orders the MIHF and the HMC. All network information such security policies, RSS, traffic load, the bandwidth, are gathered by MIHF. User preferences information and terminal-related are gathered by HMC, such as the consumption of power, velocity, quality of services as costs of services. As for information, both HMC and the MIHF are emitted to upper layers by MIH-service APs.
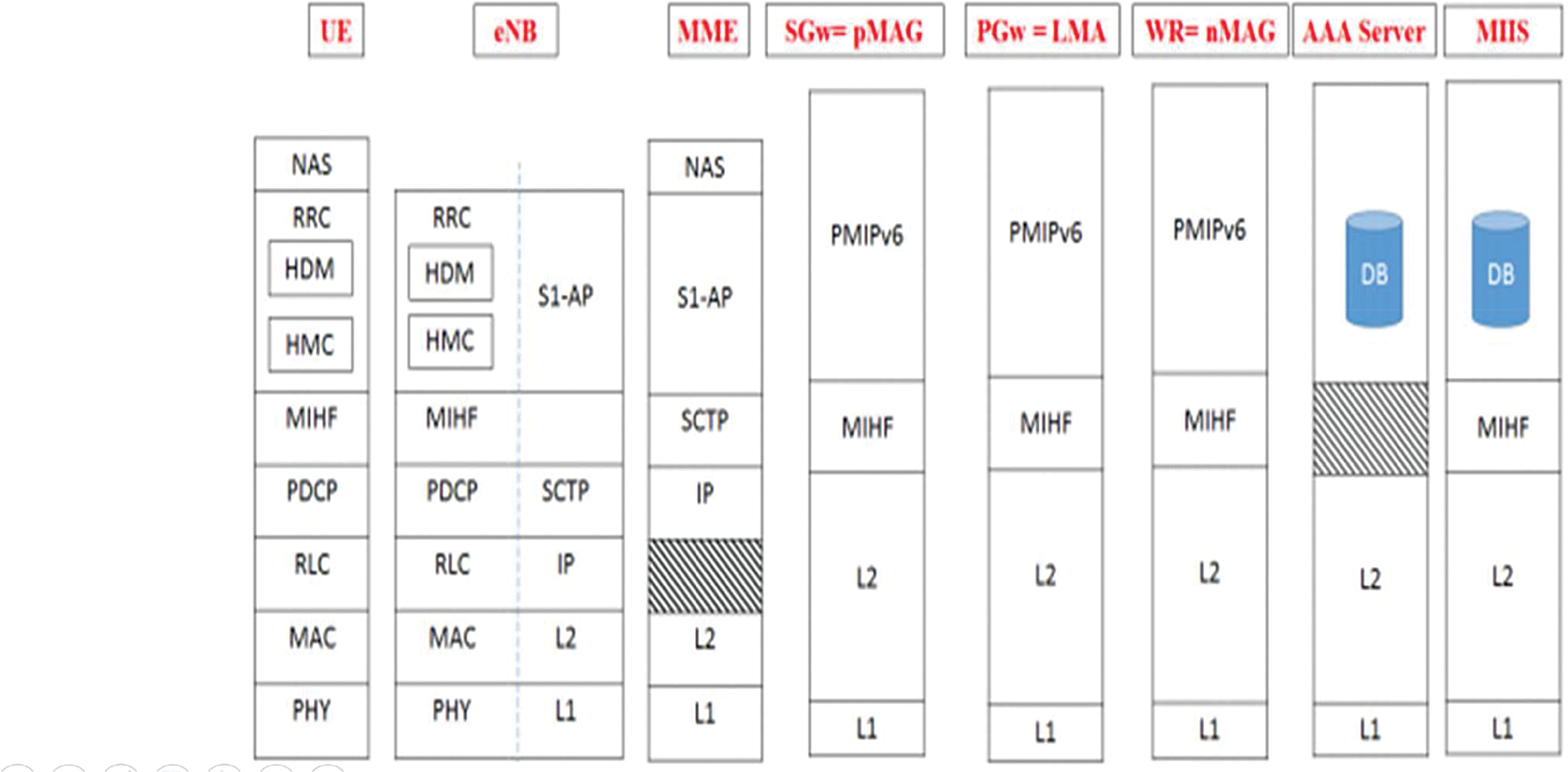
Figure 1: Proposed protocol stack
The Pre-associate going down the limit P-LGD_Thr shows that the connection quality is going down, it isn't calamitous yet, it is before long going to be break. This criticism (message) request starting the handover cycle forecast. We proposed to trigger a foreseen message demonstrating a handover earlier need to genuine connection corruption, and consequently to keep an enhanced quality of services QoS. Just the connection down message is emitted once the MN is appended to another PoA, to give enough quality of services QoS called delicate handover or make-before-break handover. The Link down limit is set to demonstrate an awful sign quality. That implies that the MN is disconnected from serving access organization. The trigger P-LGD_Thr is used to indicate that link is going to be broken, for the trigger LD_Thr is utilized to validate that connection is instantly broken with:
We propose two dynamic thresholds: firstly, LD_Thr which is calculated dropped call rate use, with the condition dropped call rate increases results the LD_Thr increases. Secondly P-LGD_Thr is a current cell RSS composite function, the candidate cells RSS and interferences levels. Mobile Node calculates the value of P-LGD_Thr that relying upon the neighbor cells signal quality. Since the Mobile Node is encircled by low quality cells, that outcomes P-LGD_Thr esteem decline and the handover chosen decision is postponed. In such circumstance, when a few decent quality cells is encompassing a versatile, the handover chosen decision will be sooner than the typical handover decision cycle. This handover type is utilized specifically cases, to diminish the one cell charge over in the over-burden organization, and this can be worked to change to another phone having a higher transfer speed or a superior QoS. The Hen signal strength is introduced under the characterized P-LGD_Thr edge, Mobile Node have a Pre_HO warning to start the cycle of handover forecast. Since a notice is gotten, the Mobile Node has sufficient opportunity to set up the handover cycle.
We compute the P-LGD_Thr threshold as a composite function. These composition elements are presented in Fig. 2, green curves for neighbouring cells RSS; red curve is for current cell RSS; and interferences levels as depicted. We determine P-LGD. Thr threshold as a link down prediction message. We take all measurements perio-dically. Using measurements values reports, we conclude that Mobile Node is able to detect signal quality which decrease over time. Other neighbor cells’ quality signal increasing continuously on real timr. We observe current cell RSS is presented below the P-LGD_Thr threshold periodically. That results MIH_Link_Going_ Down to transfert in order to indicate an unavoidable connection lost will take place. At this time the Mobile Node will look for a candidate cell matching three criteria:
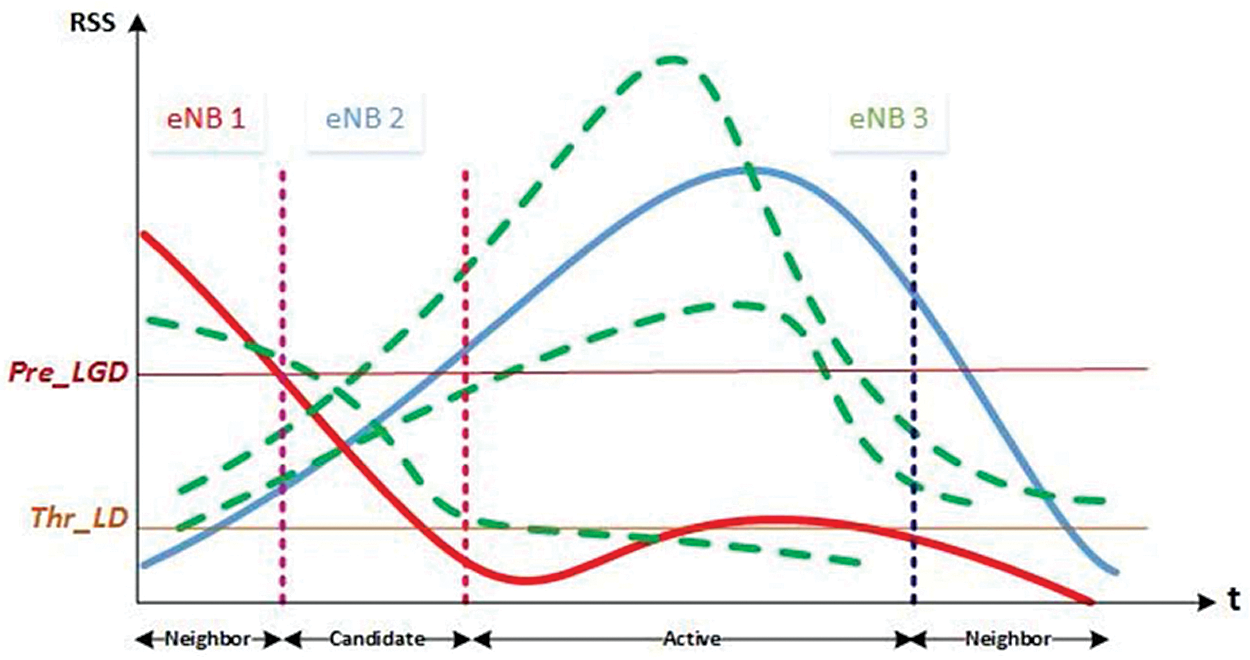
Figure 2: Defined thresholds
İf network exists on adjoining networks list, in case of Mobile Node checks, MIIS worker just sent. Mobile Node sends the Pre_HO_Initiation message to nMAG to trigger the pre-assets accessibility checking, the pre-assets reservation measures, the pre-verification and the pre-IP task stages. The Mobile Node gets the P-LGD_Thr edge and the MIH_Link_Going_Down sign, as of now it quires from the MIIS worker, all encompassing organizations data by utilizing MIH_Get Information. On the off chance that current cell RSS is underneath LD_Thr edge, current connection will be broken. The handover decision is immediately validated when we select candidate cell, resulting new connection establishment. So candidate cell will be active and the registration and resources release steps, following the handover decision step, are executed. Three different states are presented: neighbor cell existing with a same mobility domain, many cells are surrounding cells to the close vicinity cell. Second candidate cell is a cell to which the Mobile Node handoff. For our proposed approach, we predicted disconnection from the serving network: the handover, PLGD_Thr trigger is invoked prior to an actual link down event (LD_Thr) by at least the time required. We conclude that a handover process is performed in terms of PL, HD and communication cost. Normally, a Mobile Node don't begin constructing new new connection with any surrounding networks until until its connection link is lost, so once L2 is broken, right now Mobile Node start searching for the best network to handoff and inquiry information.
For more efficiency, we propose a Pre_HO Initiation message that represents a new MIH primitive. To indicate the handover procedure need, a message is transmitted from Mobile Node to nMAG. If under a predefined threshold value, we observe the RSS and SINR values are decreasing instantly, a handover procedure must be triggered. We proposed a technique depending (Fig. 3) on unique edges which shift due to introducing encompassing organizations. Since it is required, a handover setting off system encourages the Mobile Node to begin handover measure. Absolute handover disappointments number lessen and limit bogus handover number, which are guaranteed by the setting off system edge.
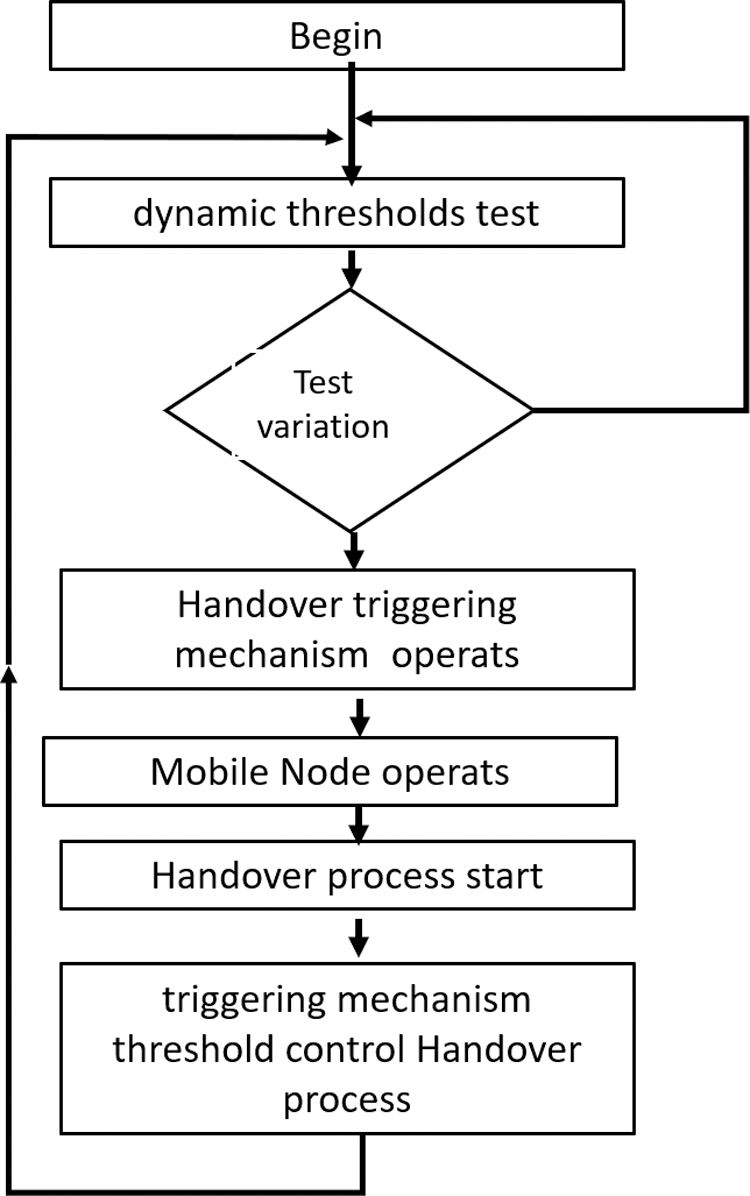
Figure 3: Dynamic thresholds method
Mobile Node checks if current network exists on nearby network list sent by MIIS worker a Pre_HO_Initiation message is moved to nMAG by the Mobile Node, the objectif is to trigger the pre_resources accessibility checking the pre_resources and pre_authentication reservation processes. MIH_Link Going_ Down gets sign, so MN quires for encompassing organizations data from MIIS worker, and this by the assistance of the MIH.
In the Fig. 4 is described the Pre_HO Initiation message which is composed of MIH header, and for the latter is presented the operation code, service identifier, as well as the action identifier. The service identifier determines each MIH services gathered with its corresponding values: command service (1), service management (2), information service (3) and event service (4). In our approach, the service identifier is a service management or an information service. OpCode characterize the service identifier that executes an operation cc.
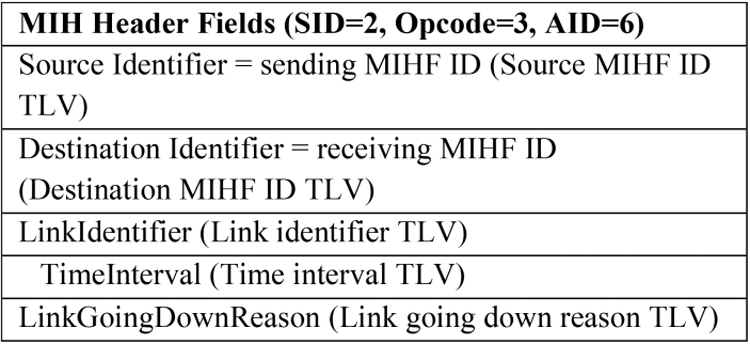
Figure 4: Pre_HO_initiation message structure
3 Key Performance Indicators (KPI)
The accompanying two measurements are utilized to evaluate the impact progressions of the key boundary blends have what's more, qualify the HO execution:
-Handover failure rate: The handover failure rate (RateHOF) is the ratio of the failed handover number (Numfail) to the number of handover attempts.
-Handover ping-pong rate: A handover is viewed as a ping-pong handover if a get back to is given and forward between two base stations in not exactly a crucial time (Tcrit = 1 s). The ping-pong handover rate (RateHPP) is determined by:
-The improvement targets: The goals of handover improvement are three folds:
• To accomplish a HO disappointment rate that is under an objective esteem (Ratefail_limit = 2%).
• To accomplish a HO ping-pong rate that is under a target esteem (Ratepp_limit = 2%).
• To limit the quantity of handovers (NumHO) while accomplishing target 1 and 2
-The Fitting Function of HO Failure Rate: From the early studies of relation between KPI RateHOF and KPP, we conjectured that RateHOF can be roughlyconstructed as quadratic function of offset with an impact factor of TTT. The polynomial of RateHOF can be described as:
where x, y denote offset and TTT value respectively, and pk is the undetermined coefficient. C. Fitting Function of HO Ping-pong Rate As RateHPP is highly sensitive to KPP in a certain range, and a slight change of KPP will cause a dramatic fluctuation of RateHPP with an exponential trend, we constructed the function of RateHPP by:
where x, y denotes offset and TTT value respectively.
3.1 Selected Key Performance Indicators (KPI)
It practices, type-2 fuzzy logic was initially introduced by Zadeh [23]. The presented technique has been proved to be very interesting especially in complex problems which are treating real world noisy applications [24]. We know that in during system development steps, Type-2 Fuzzy Logic (T2FL) defines the same lexicon of the classical type-1 FL as membership functions, rules, tnorms operations, fuzzification, inference and defuzzification, but those terms have unlike definitions to picture them. The big differentiations between Type-1 and Type-2 FL consists essentially in kind of fuzzy sets and in the output processor step which precede the defuzzification bloc; the type-1 MFs are certain and crisp, whereas these type-2 are themselves fuzzy; they are represented by a bounded region limited by two MFs, where corresponding to each primary MF (which is in [0, 1]), a secondary MF is used to the primary one.
Regarding the output processor, in type 1 FLSs it is represented just by the known defuzzification process (center of sets…), however, the in type-2 FLSs it consists of two components: Type reduction and defuzzification; type reduction makes a reduction from a type-2 fuzzy output sets to type-1 sets and then these reduced sets will be defuzzified to obtain the final crisp outputs. Fig. 5 illustrates the global architecture of a type-2 fuzzy logic system. Mendel and John proposed the Interval Type-2, (IT2) FLS. In fact, IT2 fuzzy sets have membership grades that are crisp interval sets bounded in [0, 1]. The uncertainty in the primary MF consists of the reunion of all MFs. This uncertainty represents a bounded region that it is called the Footprint of Uncertainty (FOU).
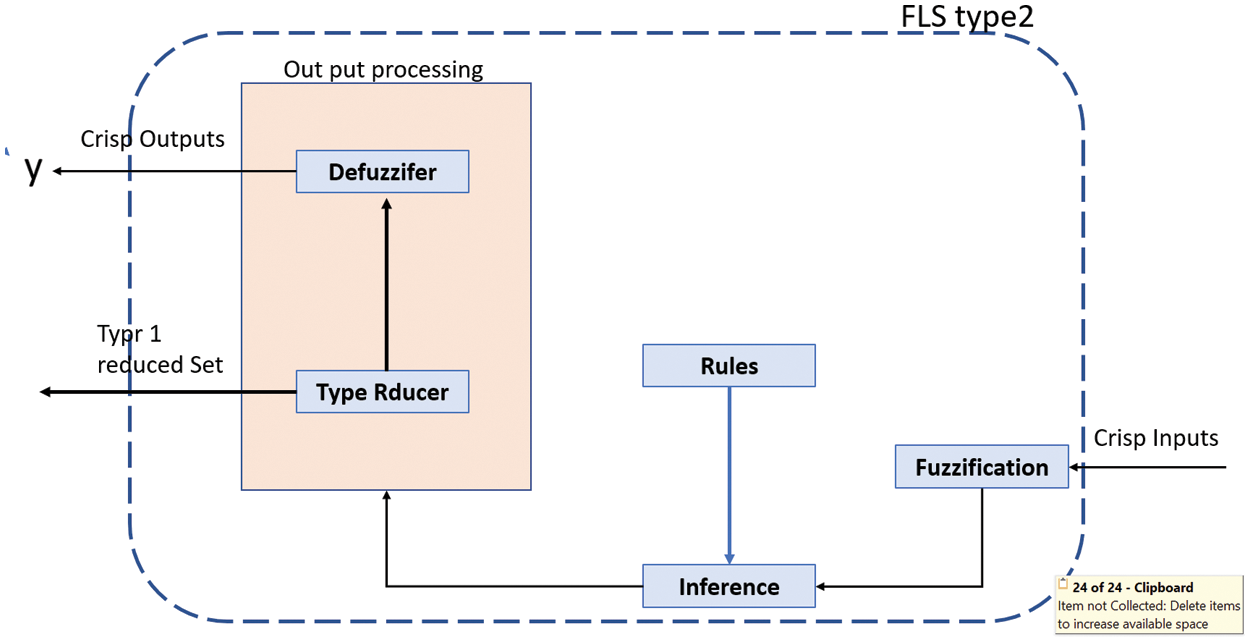
Figure 5: Architecture of fuzzy logic system type 2
4 Simulations Results and Discussions
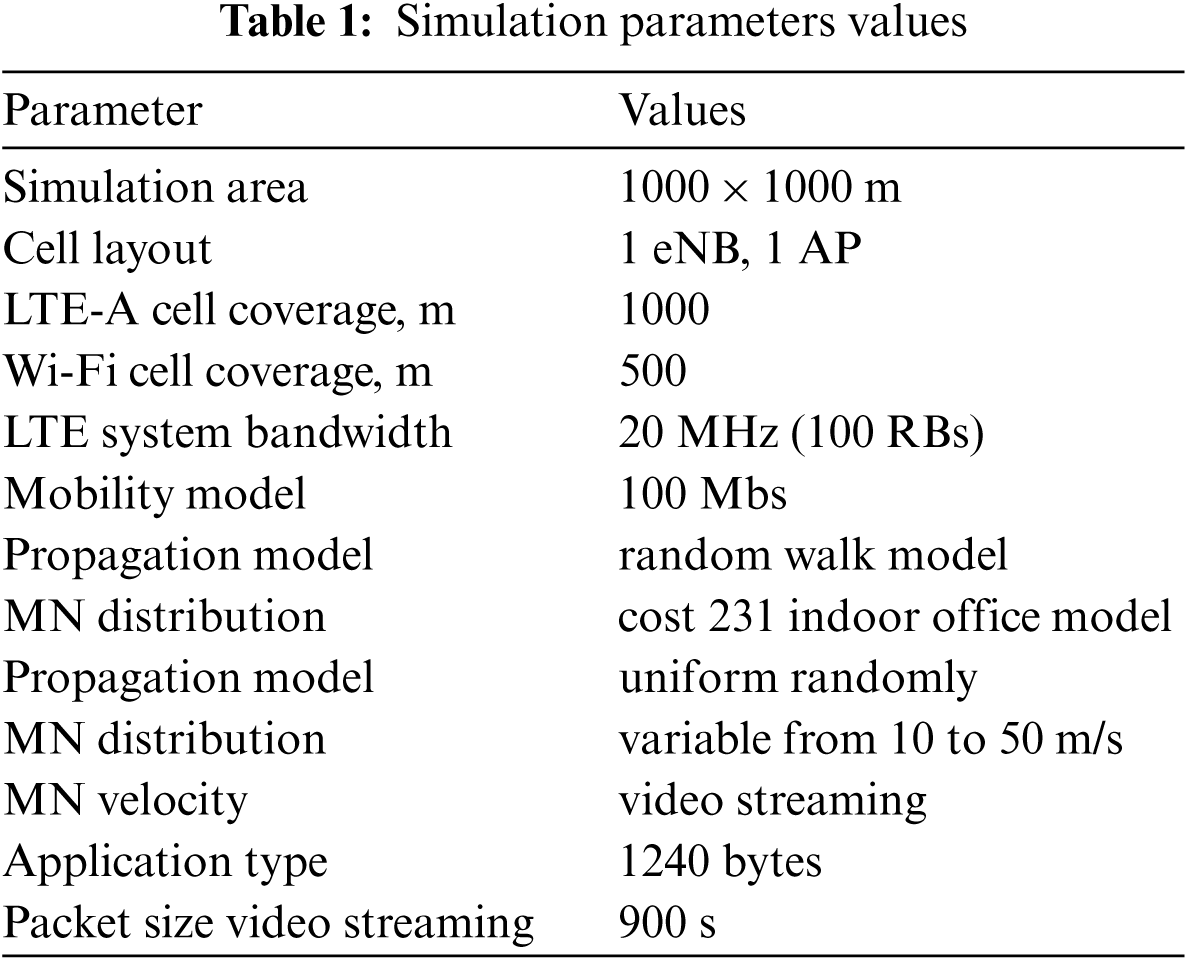
Our simulation tool is based on MATLAB R2015a environment, we evaluate the proposed vertical handover approach. Topology network consists of IEEE 802.11n wireless local area network, 3GPP LTE-Advanced and MIH protocol network information server entity. In case of LTE-A network, our simulation node for the presenting Mobile Node is 1000 × 1000 m, the motion is in accordance with the mobility model random walk point. Mobile Node propagation model assumes simulation model cost is 231 indoor office model. Its velocity varies from 10 to 50 m/s. The main system parameters are described in Tab. 1.
The proposed approach performance evaluation is based on MIH compared to existing approach, a study and analysis of PMIPv6 standard procedure with PL and HLHL.
HL represents the period of time beginning from Mobile Node disconnected from old AP when the new AP transmit the first packet to the Mobile Node. We consider the PL as the average of drops packet number, and beginning from old AP to the new one, the handover procedure takes place and its value can be determined. The total handovers numbers performed in the corresponding networks; in addition the probability of blocking Handover (VHO) determines the blocked handovers rate. In the Fig. 6 is presented HD comparison between the two approaches, that means existing approach and the proposed one. We can find out a variation of the MN's velocity in interval of 10 to 50 m/s, in case of PMIPv6 standard. VHO performance is improved in terms of PMIPv6 standard as well as delays, and these element using our proposed approach, justified by some omitted delays. Surrounding networks information can be collect from mobile node before scanning operation, and the delay from channel scanning is eliminated as well as the re-association delay. MIH services minimizes scanning time, when candidate networks physical information from the MIIS server. Prior network target authenticates step to handover decision resulting omitting authentication delay. Proposed HL solution reduces the RA delay, the registration delay as well as the re-association delay complexity.
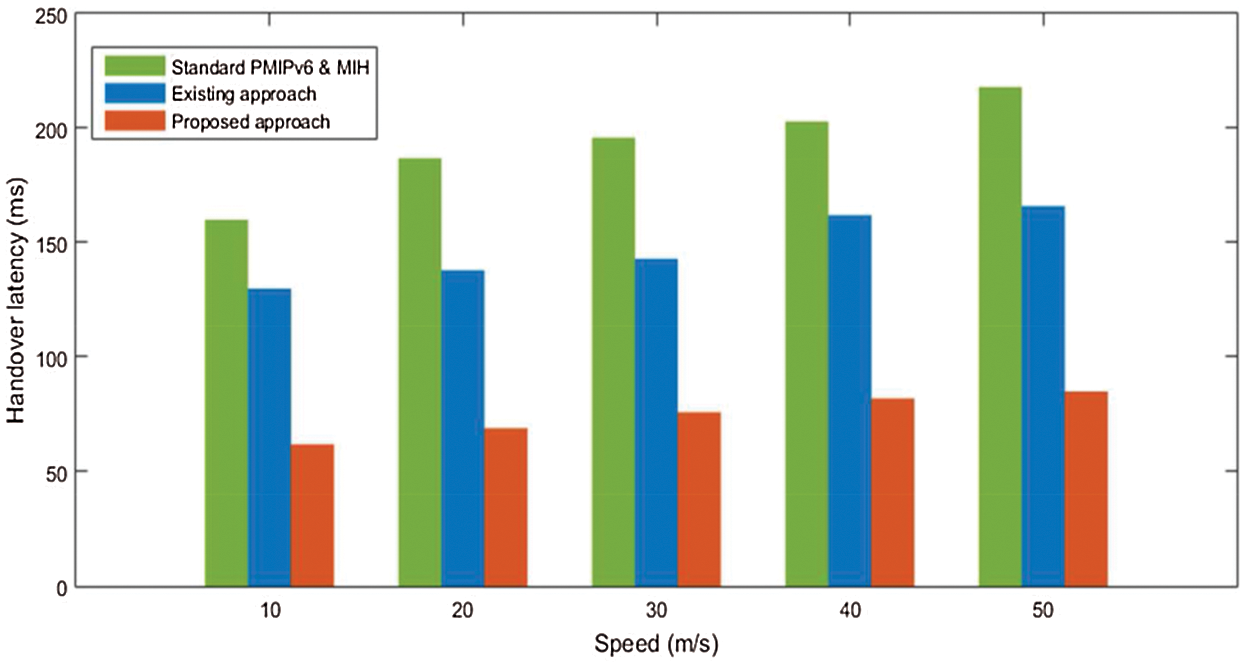
Figure 6: Handover latency verion MN
The Fig. 7 presents the PL rate as the speed of an operating mobile node. The lost packets rate of increases with the mobiles nodes speed. Under our developed approach. If we compare standard and existing approach, our approach presents the lowest rate.
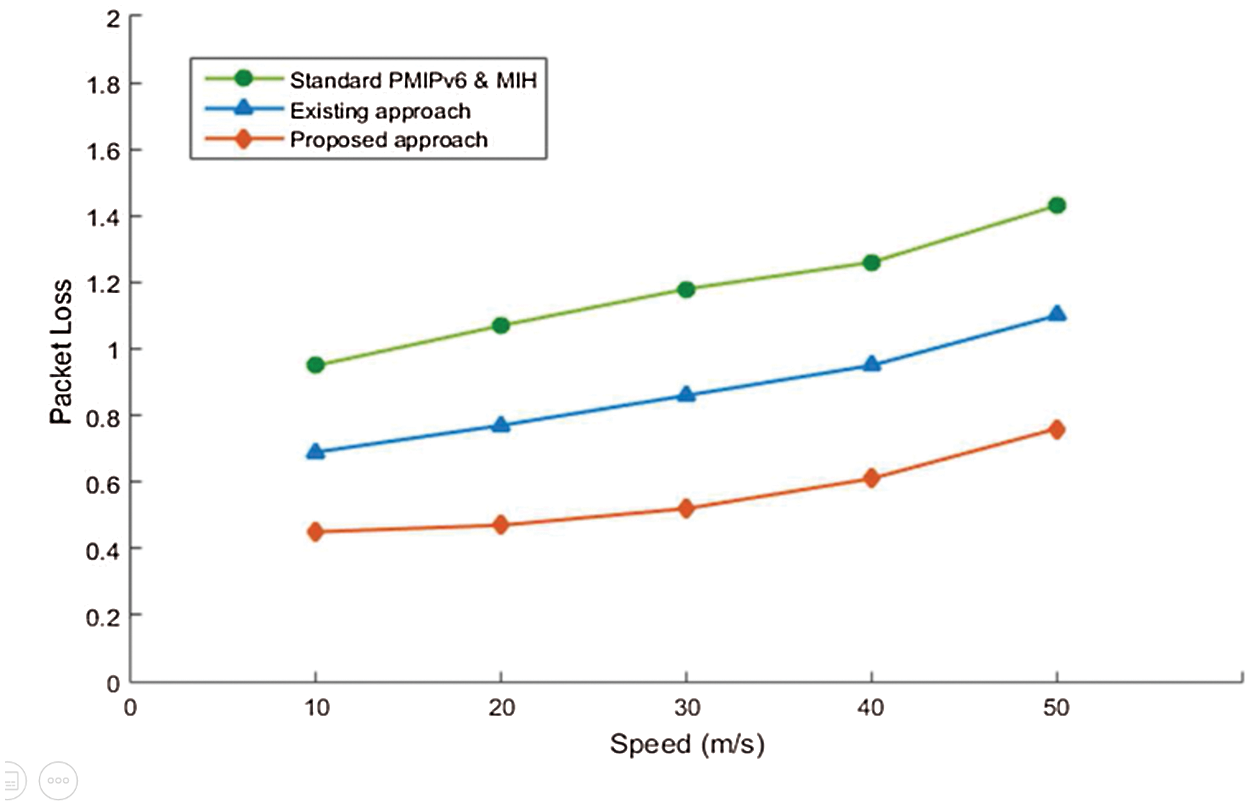
Figure 7: Packet loss version MN speed
We demonstrate in Fig. 8 that streaming video service blocking probability of the handover, in the case of PMIPv6 procedure with MIH, as well as our proposed solution, are clearly determined. Since the arrival call rate VHO increase, we conclude that probability blocking VHO for streaming service video increase also, we confirm experimentally that our approach is approved.
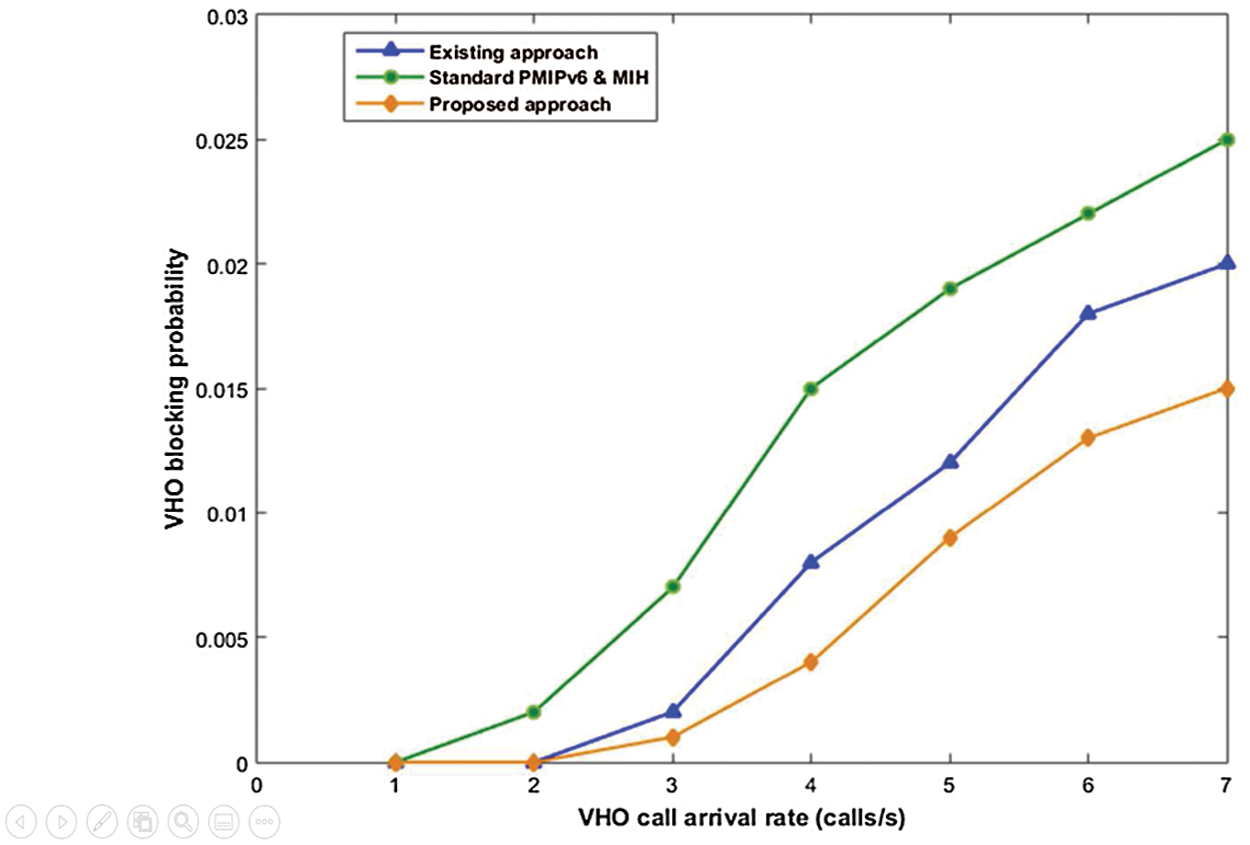
Figure 8: Probability blocking VHO vs. arrival rate call VHO
In this research work, the use of Fuzzy Logic Controller is validated. By a control of Etching Printed Antenna based on FLT2, the system operates with more precision which affect the quality of service of the wireless transmission system. The proposed system is mainly optimized for robots, in addition it ensures telecommunication constraints and facilitates data exchange. We obtained (as Figs. 9 and 10) outputs representing the surface with respect to inputs. These figures map the outputs decisions system.
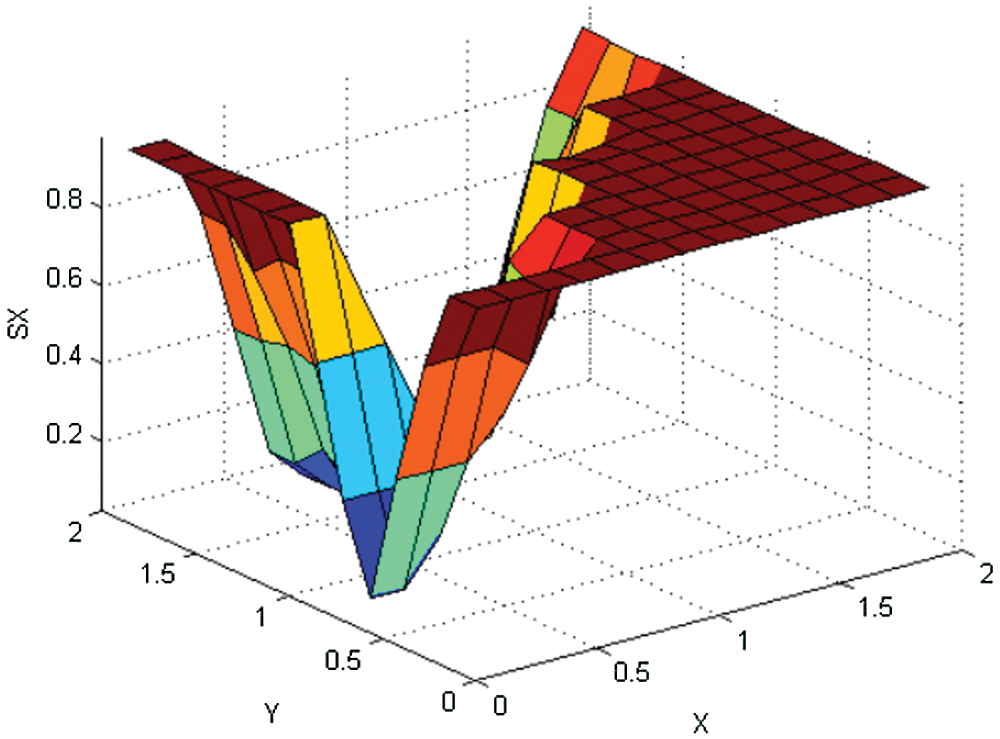
Figure 9: The surface viewers of each decision output variable SX
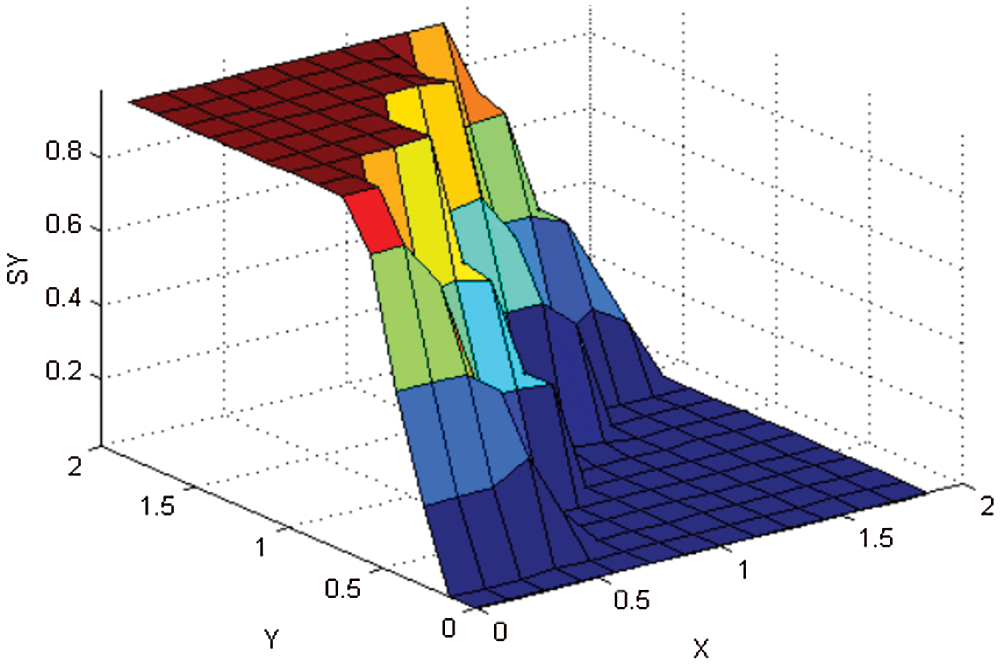
Figure 10: The surface viewers of each decision output variable SY
Most of traditioned research works have three main objectives firstly to propose a portability plot appropriate for all versatile hubs in CCN, the two distributers and supporters; secondly to depict the progressive versatility the executives technique during intra-area and between space handoff; and finally to set up a diagnostic model and detail the area update flagging expense. content-centric networking has arisen as a promising worldview in current internet due to the interest-driven, we concern more about the substance itself instead of the spot it found, and thusly, content-centric networking underpins endorser portability locally, notwithstanding, it stays a significant test in distributer versatility. But in our research work demonstrates how to solve mobility issues for 5G WiFi and LTE-A access technologies. It is known that these networks are considered as a high mobility domain, and we are face to several criteria, such handover failure probability, latency and network scale. All these elements should be taken with a higher attention. The propose method is based on IEEE 802.21 MIH standard and PMIPv6. In case where handover is mentioned to established immediately needed to be done very soon, we proposed a MIH primitive to be added. The two dynamic thresholds are considered as basic process trigger. Where for the 5G heterogeneous networks, we will also combine and test DMM approaches and MIH framework, in this research work, we validate experimentally based on simulation results and analytic evaluation that the handover blocking probability and PL are minimized, as well as the signaling overhead and the HD.
Acknowledgement: The Author would like to acknowledge the Dean of the Khurma University College and the Taif University Department of Scientific Research in the Kingdom of Saudi Arabiya, for motivation to accomplish the research work.
Funding Statement: The authors declare no specific funding received for this work.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present research work.
1. L. Liu, S. Yin, L. Zhang, X. Yin and H. Yan, “Improved results on asymptotic stabilization for stochastic nonlinear time-delay systems with application to a chemical reactor system,” Institute of Electrical and Electronics Engineers Transactions on Systems, Man, and Cybernetics: Systems, vol. 47, no. 1, pp. 195–204, 2016. [Google Scholar]
2. K. W. Hipel, L. Fang, K. Yang, Y. Chen, “An interactive portfolio decision analysis approach for system-of-systems architecting using the graph model for conflict resolution,” Institute of Electrical and Electronics Engineers Transactions on Systems, Man, and Cybernetics: Systems, vol. 44, no. 10, pp. 1328–1346, 2014. [Google Scholar]
3. M. A. Cardin, J. Yixin, H. Yue and F. Haidong, “Training design and management of flexible engineering systems: An empirical study using simulation games,” Institute of Electrical and Electronics Engineers Transactions on Systems, Man, and Cybernetics: Systems, vol. 45, no. 9, pp. 1268–1280, 2015. [Google Scholar]
4. Y. Wei, H. R. Karimi and W. Ji, “A novel memory filtering design for semi-markovian jump time-delay systems,” Institute of Electrical and Electronics Engineers Transactions on Systems, Man, and Cybernetics: Systems, vol. 48, no. 12, pp. 2229–2241, 2017. [Google Scholar]
5. K. Xing, M. C. Zhou, F. Wang, H. Liu and F. Tian, “Resource-transition circuits and siphons for deadlock control of automated manufacturing systems,” Institute of Electrical and Electronics Engineers Transactions on Systems, Man, and Cybernetics-Part A: Systems and Humans, vol. 41, no. 1, pp. 74–84, 2010. [Google Scholar]
6. C. Hamrouni, “Complex ESP systems proposal based on pump syringe and electronically injector modules for medical application,” Journal of Multimedia Information System (JMIS), vol. 7, no. 2, pp. 175–188, 2020. [Google Scholar]
7. J. Wu, Z. Guang, J. Li, G. Wang, H. Zhao et al., “Practical adaptive fuzzy control of nonlinear pure-feedback systems with quantized nonlinearity input,” Institute of Electrical and Electronics Engineers Transactions on Systems, Man, and Cybernetics: Systems, vol. 49, no. 3, pp. 638–648, 2018. [Google Scholar]
8. S. Pequito, F. Khorrami, P. Krishnamurth and G. J. Pappas, “Analysis and design of actuation–Sensing –Communication interconnection structures toward secured/Resilient LTI closed-loop systems,” Institute of Electrical and Electronics Engineers Transactions on Control of Net-Work Systems, vol. 6, no. 2, pp. 667–678, 2018. [Google Scholar]
9. Y. Xia, M. Fu, P. Shi, Z. Wu and J. Zhang, “Adaptive backstepping controller design for stochastic jump systems,” Institute of Electrical and Electronics Engineers Transactions on Automatic Control, vol. 54, no. 12, pp. 2853–2859, 2009. [Google Scholar]
10. S. Wang, X. Meng and T. Chen, “Orbital mechanics wide-area control of power systems through delayed network communication,” Institute of Electrical and Electronics Engineers Transactions Control Systems Technology, vol. 20, no. 2, pp. 495–503, 2011. [Google Scholar]
11. M. Eisen, M. M. Rashid, K. Gatsis, D. Cavalcanti, N. Himayat et al., “Control aware radio resource allocation in Low wireless control systems,” Institute of Electrical and Electronics Engineers Internet of Things, vol. 6, pp. 7878–7890, 2019. [Google Scholar]
12. C. Lu, A. Saifullah, B. Li, M. Sha, H. Gonzalez et al., “Real-time wireless sensor-actuator networks for industrial cyber-physical systems,” Proceedings of the Institute of Electrical and Electronics Engineers, vol. 104, no. 5, pp. 1013–1024, 2015. [Google Scholar]
13. Y. S. Sinem and C. Ergen, “Joint optimization of wireless network energy consumption and control system performance in wireless networked control systems,” Institute of Electrical and Electronics Engineers Transactions on Wireless Communications, vol. 16, no. 4, pp. 2235–2248, 2017. [Google Scholar]
14. Y. Wang, S. X. Ding, D. Xu and B. Shen, “An fault estimation scheme of wireless networked control systems for industrial real-time applications,” Institute of Electrical and Electronics Engineers Transactions on Control Systems Technology, vol. 22, no. 6, pp. 2073–2086, 2014. [Google Scholar]
15. M. G. Kibria, K. Nguyen, G. P. Villardi, O. Zhao, K. Ishizu et al., “Big data analytics, machine learning, and artificial intelligence in next-generation wireless networks,” Institute of Electrical and Electronics Engineers Access, vol. 6, pp. 32328–32338, 2018. [Google Scholar]
16. H. Jiang, Y. Guo, Z. Wu, C. Zhang, W. Jia et al., “Implantable wireless intracranial pressure monitoring based on Air pressure sensing,” Institute of Electrical and Electronics Engineers Transactions on Biomedical Circuits and Systems, vol. 12, no. 5, pp. 1076–1087, 2018. [Google Scholar]
17. W. Zhou, S. Sandeep, P. Wu, P. Yang, W. Yu et al., “A wideband strongly coupled magnetic reso-nance wireless power transfer system and Its circuit analysis,” Institute of Electrical and Electronics Engineers Microwave and Wireless Components Letters, vol. 28, no. 12, pp. 1152–1154, 2018. [Google Scholar]
18. F. Tian, X. Chen, S. Liu, X. Yuan, D. Li et al., “Secrecy rate optimization in wireless multi-hop full duplex networks,” Institute of Electrical and Electronics Engineers Access, vol. 6, no. 3, pp. 5695–5704, 2018. [Google Scholar]
19. C. T. Chen, Y. Wang, C. Wang, M. Ko, W. Fang et al., “Wireless monitoring system for oral-feeding evaluation of preterm Inf. ants,” Institute of Electrical and Electronics Engineers Transactions on Biomedical Circuits and Systems, vol. 9, no. 5, pp. 678–685, 2015. [Google Scholar]
20. X. Yuan, T. Shimizu, U. Mahalingam, J. S. Brown, K. Z. Habib et al., “Transistor mismatch properties in deep-submicrometer CMOS technologies,” Institute of Electrical and Electronics Engineers Transactions on Electron Devices, vol. 58, no. 2, pp. 335–342, 2010. [Google Scholar]
21. B. C. Rao, “Advances in science and technology through frugality,” Institute of Electrical and Electronics Engineers Engineering Management Review, vol. 45, no. 1, pp. 32–38, 2017. [Google Scholar]
22. H. Zhang, W. Huang and Y. Liu, “Handover probability analysis of anchor-based multi-connectivity in 5G user-centric network,” Institute of Electrical and Electronics Engineers Wireless Communications Letters, vol. 8, no. 2, pp. 396–399, 2019. [Google Scholar]
23. Y. Song, P. Kong and Y. Han, “Power-optimized vertical handover scheme for heterogeneous wireless networks,” Institute of Electrical and Electronics Engineers Communications Letters, vol. 18, no. 2, pp. 277–280, 2013. [Google Scholar]
24. F. Wang, Z. Wang, C. Qian, L. Dai and Z. Yang, “Efficient vertical handover scheme for heterogeneous VLC-rF systems,” Institute of Electrical and Electronics Engineers/OSA Journal of Optical Communications and Networking, vol. 7, no. 12, pp. 1172–1180, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |