DOI:10.32604/cmc.2022.022475

| Computers, Materials & Continua DOI:10.32604/cmc.2022.022475 |  |
| Article |
Windows 10's Browser Forensic Analysis for Tracing P2P Networks’ Anonymous Attacks
1Air University, Department of Computer Science, Multan, 60000, Pakistan
2Centre for Research in Data Science, Department of Computer and Information Sciences, Universiti Teknologi PETRONAS, Seri Iskandar, Perak, 32610, Malaysia
3IAR Systems, Märsta, Stockholm, Station Gatan 23, 19542, Sweden
*Corresponding Author: Tauqeer Safdar Malik. Email: tauqeer.safdar@aumc.edu.pk
Received: 09 August 2021; Accepted: 29 September 2021
Abstract: A web browser is the most basic tool for accessing the internet from any of the machines/equipment. Recently, data breaches have been reported frequently from users who are concerned about their personal information, as well as threats from criminal actors. Giving loss of data and information to an innocent user comes under the jurisdiction of cyber-attack. These kinds of cyber-attacks are far more dangerous when it comes to the many types of devices employed in an internet of things (IoT) environment. Continuous surveillance of IoT devices and forensic tools are required to overcome the issues pertaining to secure data and assets. Peer to peer (P2P) applications have been utilized for criminal operations on the web. Therefore, it is a challenge for a forensic investigator to perform forensic analysis of the evolving hardware and software platforms for IoT. For identity concealment and privacy protection, the Onion Router (Tor) and Chrome with the Invisible Internet Project (I2P) as the foundation browser are often used. Confirmation is required to determine whether Tor is truly anonymous and private as they claim. Some people, on the other hand, utilize the Tor browser for evil reasons. Tools and techniques are available for the collection of artifacts, identifying problem areas, further processing and analysis of data on the computer and IoT. Present research tried to explore a few tools for the tracing of I2P activities over computer on windows 10 that reflects IoT devices. According to the results of this research, it leaves an excessive amount of important digital evidence on the operating system that can be exploited to attack the information of users. This research is based on windows operating system and does not support other operating systems.
Keywords: Cyber-security; peer-to-peer; invisible internet project (I2P); forensic analysis; the onion router (Tor)
The Internet has become the inevitable part of our life today. According to datareportal.com, almost 4.66 billion people were active internet users as of Jan 2021, having 59.5% of the global population [1]. This tremendous increase in internet users has provided consumers with a variety of useful services, such as entertainment, social networking, e-commerce, live gaming, blogging, online tickets, banking, and so on. Furthermore, it is worth mentioning that approximately 8 million internet users use Tor to access the internet [2]. However, there are cyber-attacks escalation as well. In the field of computers, every activity is stored in digital form and can be retrieved by the process of forensic analysis. Today, many tools are available to obtain anonymity for the purpose of trackless browsing. In some countries, there is the possibility of having legal cover for anonymity, and in some areas, it could be a lethal weapon for cyber criminals [3]. There have been some major cyber-attacks that have prompted investigators to consider cybercrime, which is a growing problem in today's world. Cybercrime is defined as any fraudulent activities using a computer, digital device, or a network node.
The Tor project was started in 1995 by the US Naval Research Laboratories with the goal of separating the identity of a user as of routing and providing a military-friendly anonymous communication network [4]. No doubt, Tor was especially built for the military, but now, as per Tor metrics, about 3 million active users are available, having more than 7000 nodes for their traffic and 26 Gbps of bandwidth for the network. Tor is an advanced version of Mozilla Firefox that connects to the Tor overlay network to route users’ communications anonymously, providing enhanced privacy and hidden identity capabilities.
Peer-to-Peer networks (P2P) are self-controlled overlay networks that are spread over Internet Protocol (IP) networks. P2P file-sharing networks are modelled after the Internet of Things (IoT), which features self-governing connected devices in dispersed and de-centralized systems [5]. The Scalability is facilitated by P2P overlays in a dynamic and de-centralized system. On the contrary toward the client-server architecture, the nodes in a P2P system are handled separately. These overlay networks can sometimes provide services those are not available through traditional client-server systems.
The most widely used open-source unidentified communication tool is the Invisible Internet Project (I2P) featuring identity hiding and maintaining privacy. The I2P is an unidentified peer to peer network layer over which enormous unidentified applications can work. I2P is mainly used for nameless browsing, file sharing, email, chat, blogs, online shopping and much more. To participate in an I2P network, an application software known as a router is required. The software does not know the endpoints or destinations linked to different applications. Thus, an end user would have several local destinations on their router. A separate tunnel is created for explicitly sending and receiving messages through a predefined list of routers. In I2P communication, inbound and outbound tunnels are used. I2P also uses garlic routing, a modified version of an onion router. It can encrypt multiple messages together and, hence, traffic analysis will be more complex and the data transfer speed would increase as shown in Fig. 1.
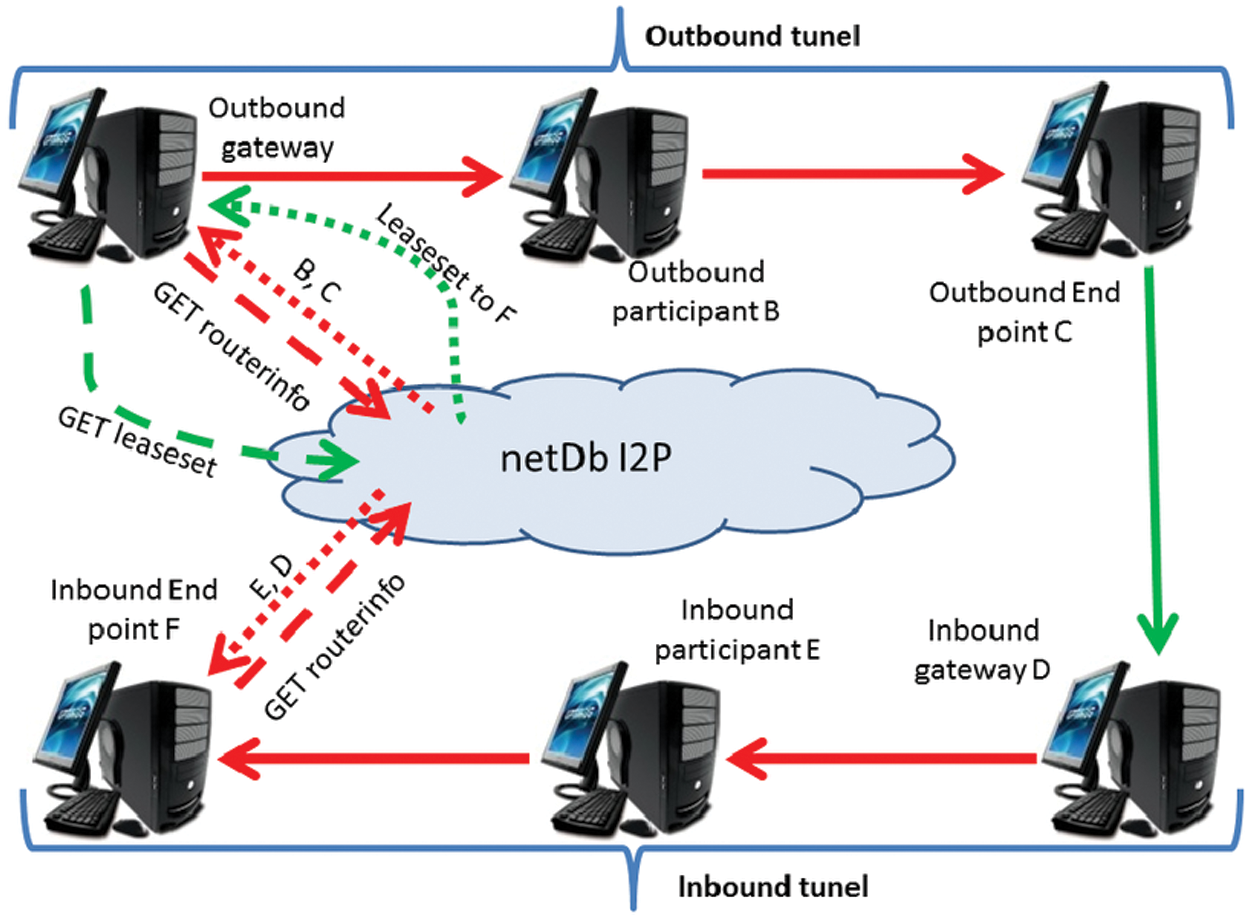
Figure 1: I2P connectivity in P2P networks for inbound and outbound users
In Fig. 1 virtual circuits B, C, E and D are created for sharing routing information of inbound and outbound participants E, F, D and B, C respectively. Tor client can get relay information from directory server netDb of I2P network. A “tunnel” is another crucial phrase to comprehend I2P. A tunnel is a path that is steered through a set of routers that has been carefully chosen. Each tunnel has a beginning and an end point (the first router, often known as the “gate”). There are two types of tunnels: “Outbound,” which sends a message from the tunnel's maker, and “Inbound,” which delivers a message to the tunnel's originator. We can convey messages from the sender to the recipient using the combination of these two tunnels. The I2P network database (netDb) is required to connect the two tunnels. This database contains the information needed to contact a certain router (public keys, transport addresses, and so on) as well as the information needed to reach the target recipient (the gateway, which enables a destination, the lifetime of the tunnel, a public key pair to encrypt messages).
The most difficult problem is addressing the misappropriations caused by the P2P network's capabilities in I2P. Many Law Enforcement Organizations (LEO) are struggling to cope with the new technologies and techniques that are being mistreated by P2P users who help facilitate and contribute to fraudulent activities online. There is a need to investigate the P2P networks for forensic analysis of I2P browsers on Windows 10 to recover some important artifacts in memory, registry and browsing activities on the hard disk. Moreover, it is pertinent to mention here that as far, no research is available for Law Enforcement Agencies (LEA) and with the help of proposed research forensic analysis of Windows 10 can be done speedily and easily. Therefore, our main focus is on cybercrime to benefit law enforcement agencies by providing a mechanism for forensic analysis. Furthermore, most of the time the network artefacts or Windows-based artefacts are under observations, hence, we are discovering the traces of dark web activity in criminal investigations on Windows 10. This is helping in P2P document sharing for organizations which are using the mirror for the Internet of Things (IoT) worldview with self-ruling arranged gadgets inside conveyed and decentralized framework [6].
The rest of the paper is organized as Section 2 presents the related work and shows the need of the presented work. Section 3 describes the methodology with its detailed tools and phases. Section 4 analyzes the results and compares with the previous research work. Finally, the conclusion section summarizes the current research with future work.
Studies of Tor and I2P forensics have previously motivated on memory forensics to recognize the source of dark web sites or to de-anonymize users. In [6], researchers presented a database containing domain link to present the reconstructed relations as graph and analyzed for interconnection with darknet. The results shows that main darknet service play important role in the communication paths of the darknet. As limitations, it is hard to find weaknesses if dataset contains services of TOR that are deployed securely. Several browsing tools are analyzed and presented a feature based comparison for analysis of browser running in normal, private and portable mode. Best forensic approaches are applied for the creation of digital artifacts [7]. A Case Study for Privacy and Anonymity on the Web has collected TOR artifacts from host machine and carried out a detail analysis of artifacts from registry, memory and hard disks [8]. The obtained results are supportive for LEA in cases where a Tor browser user is under investigation. It is performed on windows 8.1 with no support for latest operating systems. It is found that when the user used Incognito mode all the data of each event made by the user is traced like Login details, Email details, browsing details, etc. even after the browser closed or even open. The Universal Control (UC) Browser dealer said that by using Incognito mode of it, user history of events and other details will not be observable but using this forensics investigation it can be discoverable and the private browsing mode is still challenging according to user privacy [9]. The limitations for the research is that the research has been done on the incognito mode of the UC browser and finds some artifacts. But no forensic analysis on the onion browser.
A similar research on the forensic analysis of web browser is done in which the way to analyze the browser forensically is to take the image of the hard drive, select some user's search words from the history file, and use the Forensic Toolkit (FTK) Live Search option to search those keywords in the image drive. She revealed that no user can browse safely on the internet [10]. The researcher uses investigation based on the steps from live forensics method for acquisition of data on live media. The research is compatible to perform data acquisition process and background to the problem behind live forensic methods. For testing, Firefox browser is used in the research with privacy feature on and off. The result of the investigation shows that sufficient and valuable information is obtained after live memory forensic about suspicious activities [11]. These activities included traces of email and Facebook id even after the browser is closed, website visited, clear history and keywords on the internet. These artifacts are sufficient for the accusing of culprit.
The study of correlating message from multiple Instant Messaging (IM) networks to identify digital forensic artifacts, the suspect is communicating with correspondent relatedly through Digsby Instant Messaging (DIM) client. For the experimenting and conducting research, they have taken four IM protocols which include AIM, Windows Live Messenger protocols, Google Talk and Yahoo Messenger. The chat contents of each IM protocol either in complete or fractional form found at various locations found in Random Access Memory (RAM). Forensic Analyst can collect complete conversation contents from RAM as stored in Digsby logs. Additionally, the status updates (live, idle, away, etc.) can also gather from RAM using login ID of particular IM protocol and login ID of Digsby. Moreover, an automated tool should be developed to resolve the issue of using multiple IM protocols for a single conversation session [12]. In computer forensics, extraction of memory forensic artifacts are very important and provide basis for data acquisition. Thomas et al. have done memory forensic in different phases such as identification of Kernal Process Control Register (KPCR), extraction of running process list, identifying Process Environment Block (PEB) and its related structures and extracting process memory. They observed that the process of memory analysis is highly dependent on the operating system. In the given paper method for acquiring important information are KPCR, CR3 register value, process details, loaded Dynamic Link Libraries (DLLs) and process memory from windows 7 memory dump. However, as far as limitations are concerned this whole technique can be done on the latest window like windows 8.1 and windows 10 [13].
The researcher in [14] have proposed a system which extracts the physical memory dumps and local files of the system as input and processes it and then generates a report having I2P artifacts as output. The traces of I2P were successfully pointed out using in depth analysis of the memory dump and local system files. Furthermore, registry also contain I2P traces and HDD is also a place where traces of I2P can be find. No support for registry and HDD analysis is provided. Overall objectives in this research have been obtained but complex and updated application needs further improvements in research.
The implementation of classification of I2P network data traffic is performed on the basis of algorithms such as Baysnet, naivebays, Support Vector Machine (SVM) and random forest traffic [15]. The obtained results shows that for segmentation of data set, RandomForest is greatest having accuracy of 100%. As far as limitations are concerned no in-depth detailed analysis of the encryption principle and anonymous implementation of the I2P protocol. Whereas in [16], authors presented I2P characteristics to point out the security flaws and problems finding artifacts of the I2P. The results shows that the I2P artifacts collected and analyzed on the basis of vulnerabilities of I2P networks and specific security issues. The platform comprises on data acquisition module, forum information inquiry module and visualization module are analyzed in [17]. The obtained results help law enforcement agencies to analyze illegal and criminal activities over dark web. Research on Tor or onion routers is missing. In [18], a theoretical comparison of TOR and I2P is made from a variety of aspects, including community visibility, scalability, memory utilization, latency, bandwidth, documentation, vulnerability to DoS attacks, and the number of exit nodes. The authors attempted to characterize the file sharing environment within I2P, analyzing how it affects the network's anonymity. The majority of I2P's activities are focused on file sharing and anonymous site hosting, according to the findings. Furthermore, the nodes are found to be spatially scattered.
As per analysis of various literatures, comprehensive research on the latest windows 10 is missing as well as browser artifacts are mandatory in analysis. Various researches are also available on the topic but Tor left various browsing artifacts on memory and hard disk which is missing in previous research. The comparative analysis of some important research papers on the basis of above literature review is given as under see Tab. 1. Many structures for digital forensics already exist, demonstrating their relevance to the area. These current frameworks serve as a foundation for the suggested framework for this study. Tor memory forensics encompass huge research gap [19]. The present paper throws light on this issue and proposed a forensic platform for I2P and Tor browser memory, registry and hard disk analysis.
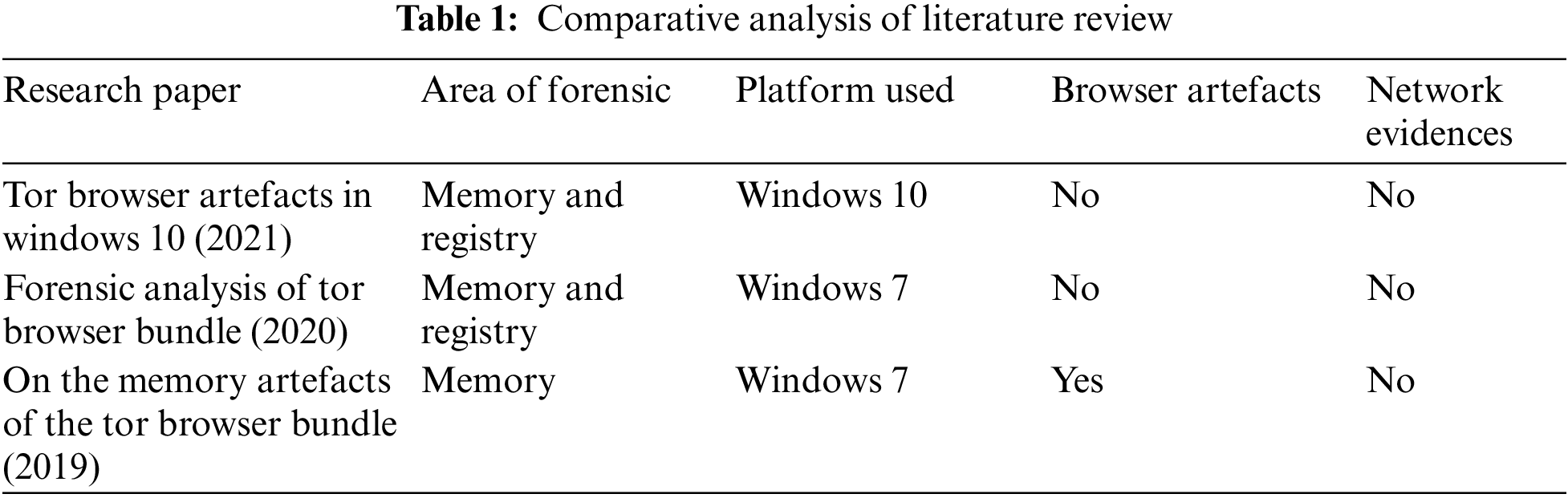
With the invention of new hardware and software, as well as the rapid growth in internet users, many Peer-to-Peer (P2P) users are contributing to and facilitating illegal activities online, which should be addressed based on solid evidence. For the collection of these evidences, law enforcement agencies must be updated with new tools and techniques. The methodology that will be adopted in this work is shown in Fig. 2. In the first phase of methodology, a computer system having virtual machine with windows 10 operating system was setup for experimental purposes. The second phase comprises of acquisition of data for forensic analysis. In this phase artefacts were collected from registry, RAM and hard disk were taken. After acquisition, collected data was forensically analyzed in third phase for presentation of evidences. For the experimental purpose, the required platform and tools will be prepared on the host system. After installation of the required tools, data acquisition will be carried out. In the first phase, registry data artifacts will be collected and in second phase, memory data artifacts will be collected. Finally, browsing data artifacts will be collected as shown in Fig. 2. The mandatory investigational tools are tabulated in Tab. 2 to produce a fast and accurate result, a fresh Windows 10 installation was prepared in a virtual box. The tools used for the current investigations are totally free and easy to use.
Before the start of forensic analysis, some input is required to be given to the system. So that system could produce artifacts. In order to fulfill the requirement, experimental input was prepared in the form of performing activities over I2P and Tor browsers. One Instagram account, one Yahoo mail account, two Gmail accounts, two Skype accounts, two Twitter accounts, and three Facebook accounts are created for this purpose. The sample data is also shared between these accounts. Tab. 3 contains information on these activities. After these activities, all the downloaded images and files are removed from the system before the data acquisition.
Figure 2: Proposed system design for forensic analysis


The data acquisition is completed in three phases. In the first phase, registry data is collected and in the second phase, I2P based Tor only memory data is collected. Finally in the third phase, artifacts of memory and storage are collected. After the data is collected from the three phases, the system is returned to a spotless state to confirm that no pieces from the preceding phase remained. The first phase entails gathering pre-installation data. The acquisition of post-installation data is part of the second phase. The third step is to collect post-uninstallation data. The Regshot tool is used for data acquisition of the registry [19]. Memory data acquisition is carried out in two portions. These parts are I2P based Tor only and I2P based Tor browsing. Whereas two scenarios are considered for I2P based Tor browsing open and closed.
Browsers are necessary for a productive work environment but they also serve as an ideal vector for cyber-attacks. Cyber-attacks and crimes are multi-faceted in today's world and they are on the rise [20]. With sophisticated tools, digital forensics is a great discipline for limiting and investigating such risks. The web browser is the most extensively used application for accessing content on the internet and serves as the user's interface to the rest of the world. Visit web pages, access email accounts, use social media, and upload and download various files are all common browsing activities. There are three stages to forensic analysis such as registry snapshots followed by memory and storage images in the second and third stages respectively.
The Regshot tool is used to take registry snapshots and to analyze them. During installation, this browser adds three registry keys, according to the research. After uninstallation, all of these keys remain in the registry, showing that it does not erase its registry artefacts. It is also revealed that in different instances that these keys are added in a different order as shown in Tab. 4. The browser is installed in this case with the option to “Open browser automatically after installation.” The browser is automatically launched after installation. The first two keys were inserted into the registry. When the browser was reopened after being closed, the third key was added.

The browser is installed in this case without the option to “Open browser automatically after installation.” After the installation is complete, the first key is added. When the browser is opened, the second and third keys are added. These scenarios will be highly useful in circumstances when investigators want to determine if the individual only set up the Tor browser and if they used it after that. In respect to MS Word documents, various digital evidences can be recovered from memory. Al-Sharif et al. [21] developed a memory forensic technique based on the XML form utilized by MS Office internally. Different parts of MS Word can be recovered from memory to establish that the document was seen or modified by the user, according to their findings. Al-Saleh et al. [22] have investigated the effects of memory forensic methods on network reconnaissance detection. They made use of the data that can be retrieved from memory. Furthermore, they discovered that packets sent or received across the network can be stored in memory for a long time. Their findings revealed that memory analysis was useful in detecting assault artefacts. Primary artifacts recovered from Autopsy as shown in Fig. 3.
After installation, software leaves a large number of artifacts on the host machine. This section of the research focuses on recovering all of the artifact left on the host machine by Tor browser after installation and operation. For forensics analysis of obtained memory images, the Autopsy framework is employed. According to memory analysis, the Tor browser has two processes in memory: Firefox.exe and tor.exe. Other artifacts associated to these two processes are also recovered using their process ids. The key terms “Firefox” and “tor.exe” are used in obtaining information about Tor version artifacts for the two programs.
The third VMware snapshot was obtained for the “Open Browser” scenario, while the fourth was engaged for the “Closed Browser” scenario, as detailed in Data Acquisition. These two VMware snapshots’ memory images (.mem files) are examined for surfing evidence. For analysis, the tool bulk extractor and a Hex workshop are utilized [23]. The bulk extractor is used for the majority of the analysis. Bulk extractor uses string search to locate links to user's social media account profiles, the profiles visited, videos watched and another artifact. The current strings are derived from the address of the site visited and user names that are used during the user's activity of browsing phase. Without utilizing strings searches, all of these artefacts can be found by analyzing all of the sites collected by Bulk Extractor, though this method is slower than string searches. Hex work-shops are used to search for email text in memory. To find these emails, the memory image was unwrapped using tool Hex workshop and various string explorations are conducted. During the user activities section, some strings from email text that are sent and received are also searched. The emails can also be recovered in memory without using string explorations by using hex workshop to display all strings present in memory completely. However, in the case of big memory images, this method is quite time consuming. All Gmail and Yahoo inbox emails, including unopened emails, are stored in memory when using Tor browser. Fig. 4 illustrates some of the emails found using string searches in the memory image of the third snapshot. Public keys and other relevant information of Tor relays used during communication by Tor browser for transmitting its traffic can be found using the strings “PUBLIC KEY” and “Relay=.” IP address, Bandwidth, Ports, Name and Fingerprint, Tor version used, date and time of connection, and present status are among the other details (entry or exit) [24]. Figs. 5 and 6 show screenshots of public keys and some useful other information taken in the third VMware snapshot's memory picture.
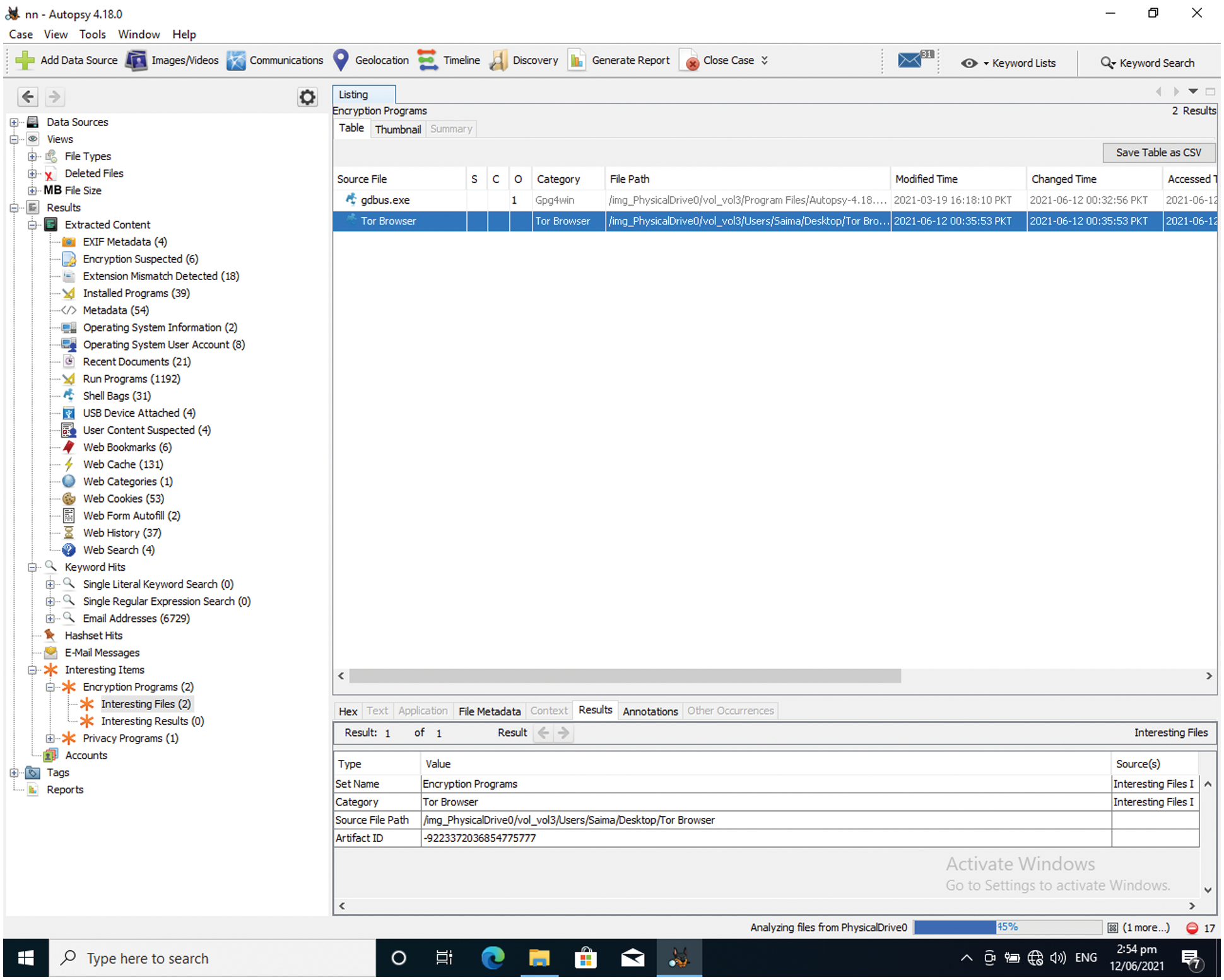
Figure 3: Tor artifacts recovered from autopsy
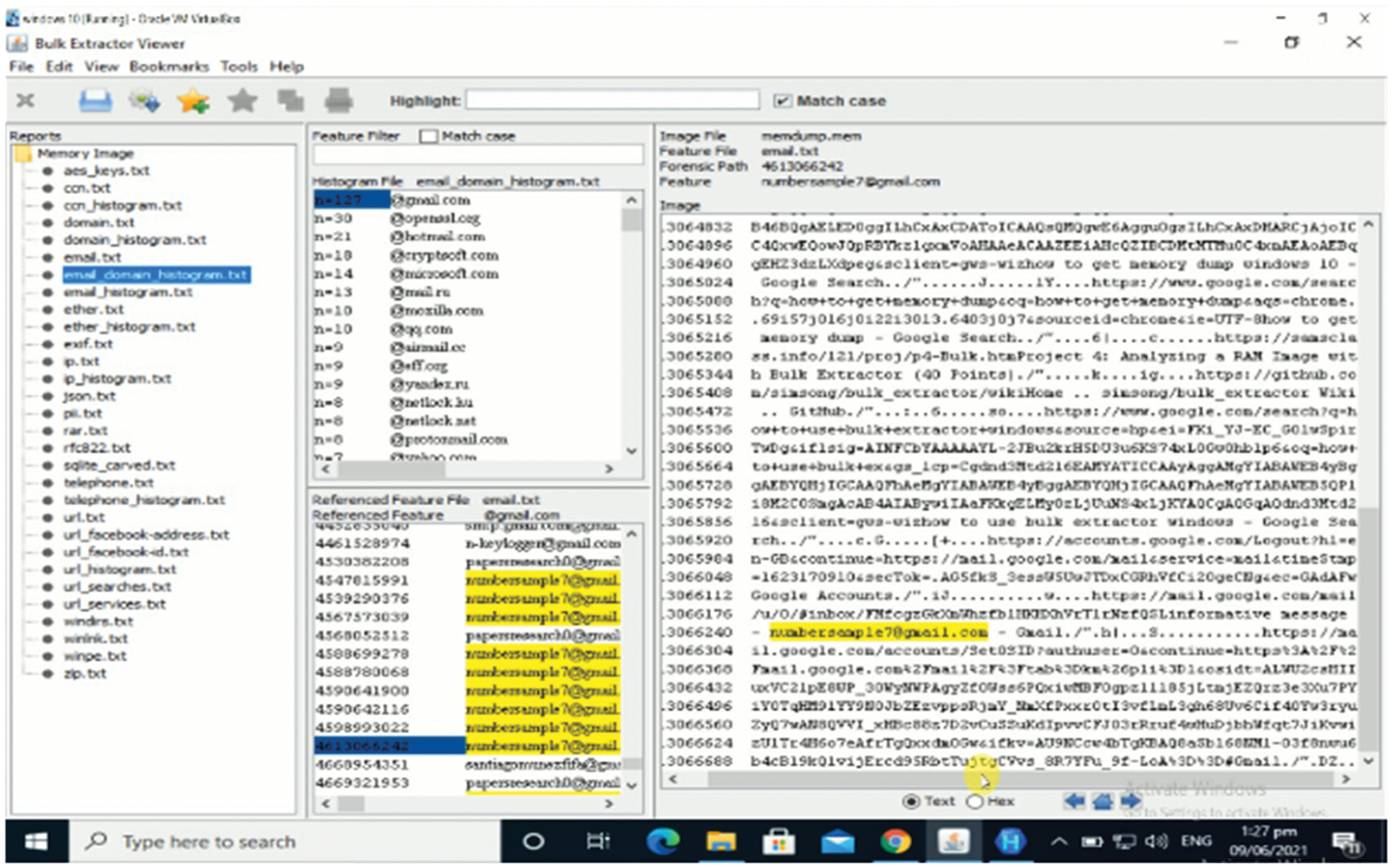
Figure 4: Recovered email artifacts using bulk extractor
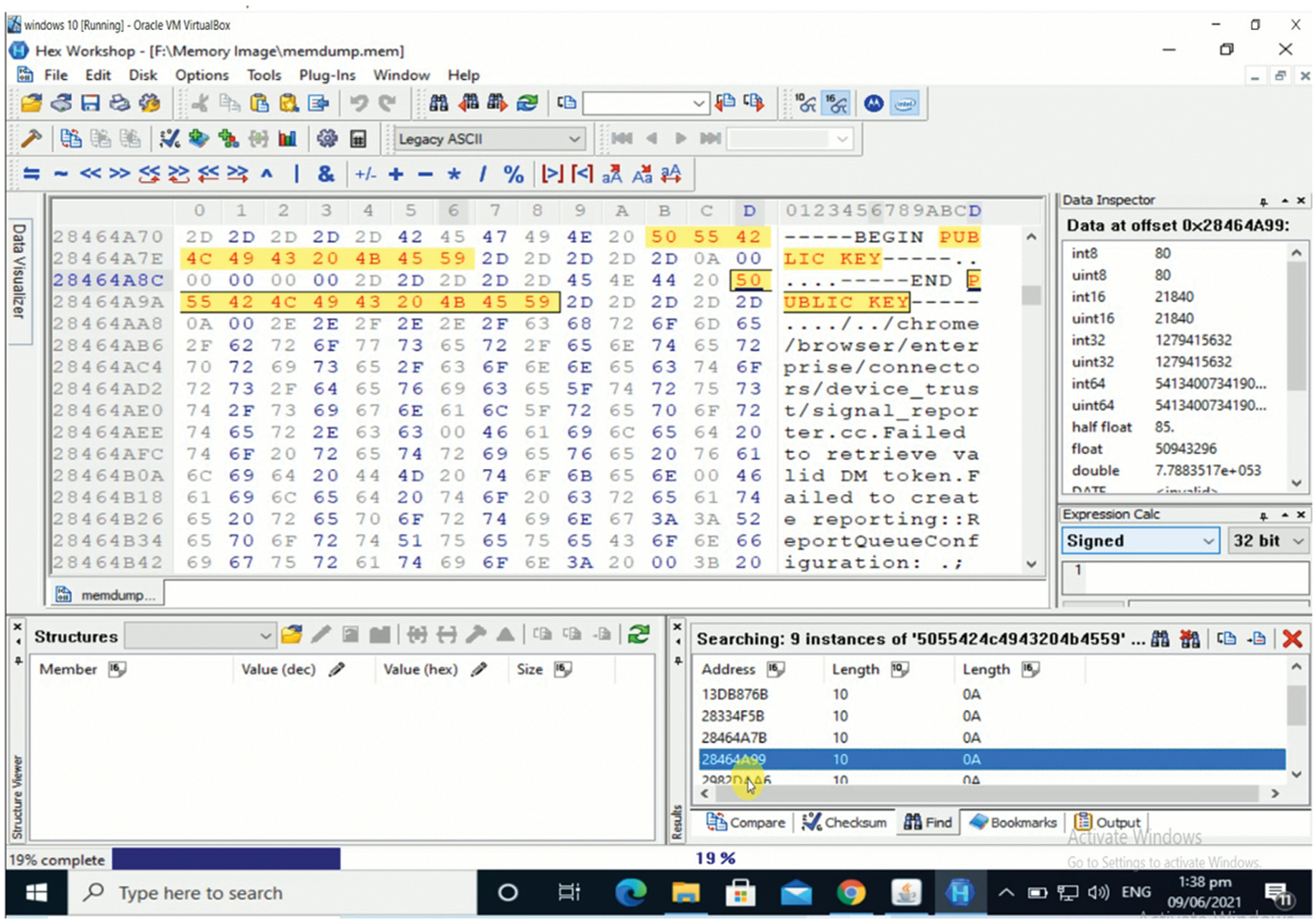
Figure 5: Memory showing public key of tor relay
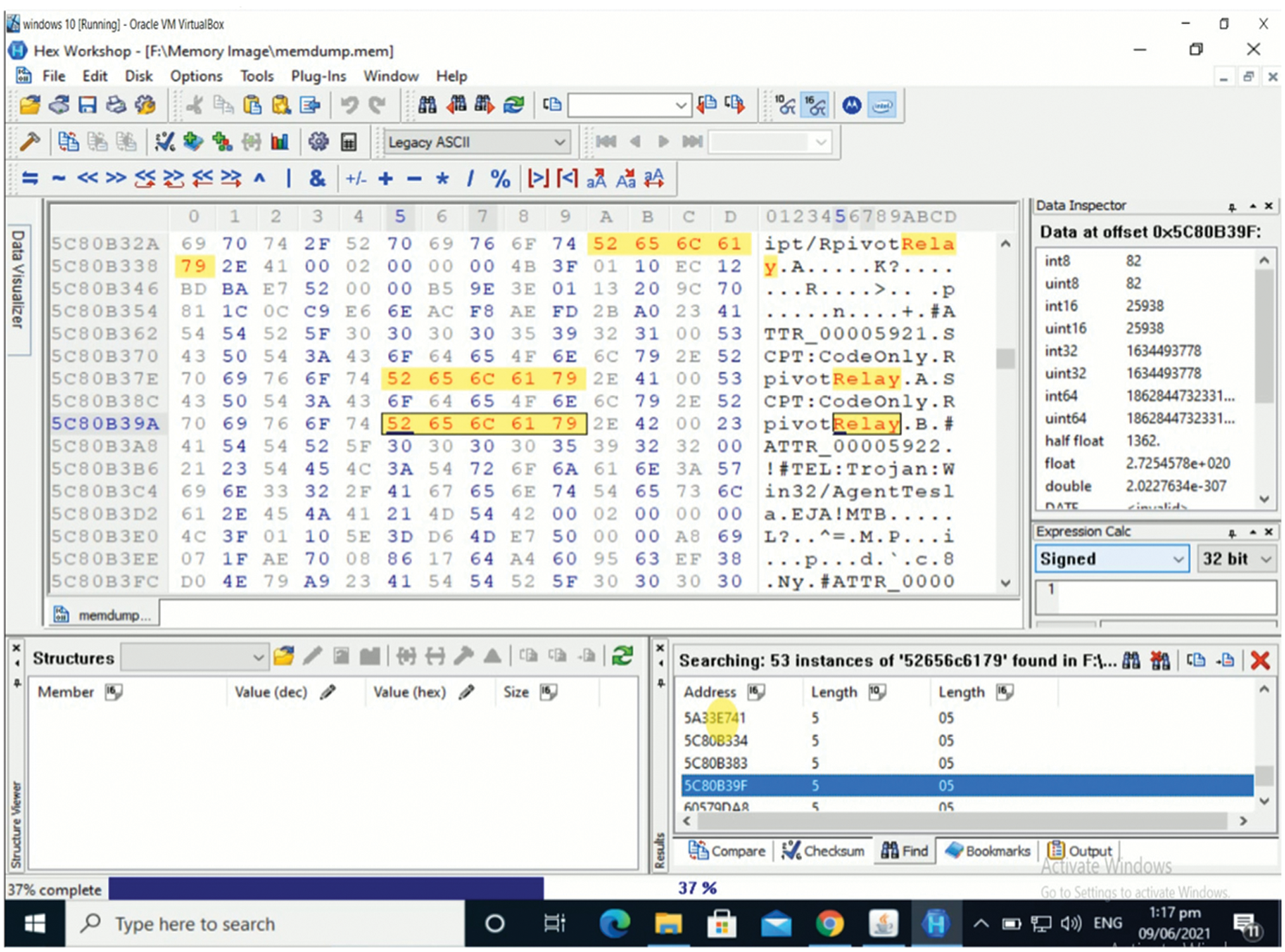
Figure 6: Memory showing relay information of Tor
The “cached-certs”, “cached-microdesc-consensus”, “cached-microdescs” and “cached-micro- descs. new” folders in TorBrowser/Browser/TorBrowser/Data/Tor also contain the same artifact. As demonstrated in A, B, and C these files are evaluated in Hex Workshop. Various artifact can assist LEA in tracking down a person using Tor for any criminal behavior through gathering evidence about the user's browsing activities from these relays. Both memory pictures contained identical traces, indicating that Tor did not remove browsing history of user from memory when the Tor is closed. Tab. 5 presents a detail of all the artifacts discovered in memory about user browsing behaviors. Fig. 7 show screenshots of several of these artefacts. All of these artifacts were discovered using bulk extractor, with the exception of Yahoo and Gmail inbox messages, those are discovered using Hex workshop.

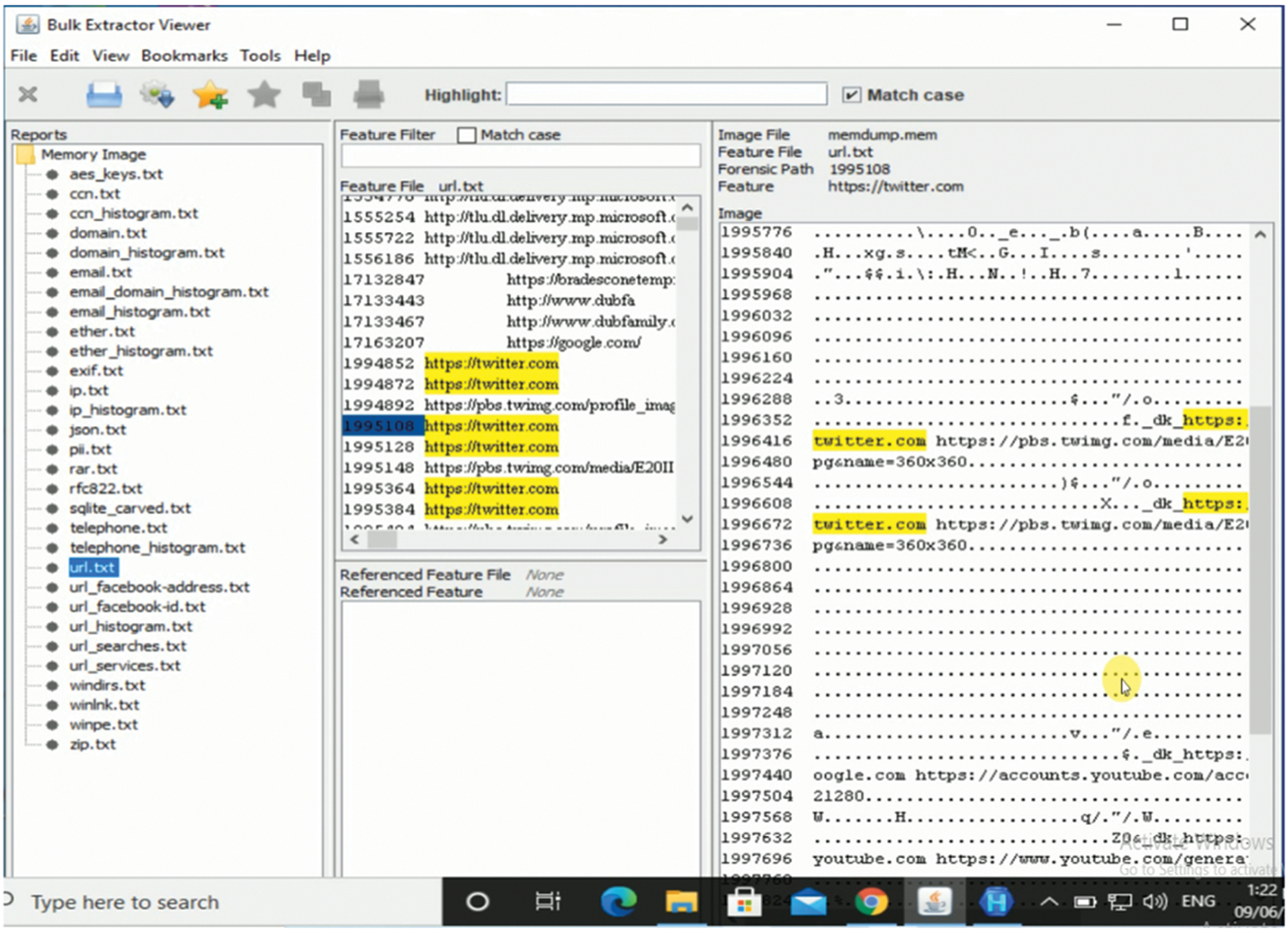
Figure 7: Twitter artifacts in memory
The artifacts on the hard disk are analyzed when the browser is open using the Magnet Axiom to examine both the VMDK file of OS and the snapshot VMDK file of the third snapshot. The registry artifact found in these VMDK files are searched using Hex Workshop. The OS VMDK file is supported by Magnet Axiom, however the snapshot VMDK file is not. Using the image conversion method, we convert this VMDK file into EnCase Image File Format, which is supported by Axiom, using FTK imager. To confirm the integrity of converted snapshot VMDK files, hashes were calculated and matched before and after conversion using the FTK imager. FTK imager was also used to construct MD5 and SHA1 hashes for the OS virtual hard drive file. On the OS VMDK file, no Tor artifacts were discovered. This VMDK file was inspected in Hex Workshop for registry artifacts, and various string searches were conducted. In these searches, the strings “firefox.exe % b” and “SIGN.MEDIA = 31C3D37” were used. In the OS VMDK file, there were no registry artifacts. However, as shown in Tab. 6, various artifacts are discovered during the examination of the converted snapshot VMDK file.
Magnet Axiom discovered artifacts that contained all of the download data. Torrent files are displayed as peer-to-peer artefacts, whereas downloaded photos were displayed as media artefacts. Apart from downloaded images, Axiom found a plethora of other photographs from the OS's internal application. The Tor browser icon could also be seen in the photos, showing that Tor had been installed on the device. There was no other instance under the OS artefacts except for firefox.exe. During the collection of artifacts various artifacts of Tor browser regarding relays information has been recovered. This information is very useful in scenarios where back tracking is essentially required. This is done by obtaining the address of next node. Several artifacts recovered from Tor Browser are presented below as additional artifacts.
This artifact is collected when the Tor Browser is open. “cached-cert” file located in Tor browser folder at Desktop was loaded in Hex workshop. The file contains public key of Tor Browser. This artifact is collected when the Tor Browser is open. “cached-microdesc.new” file located in Tor browser folder at Desktop was loaded in Hex workshop. The file contains public key of Tor Relay as shown in Figs. 8–10. This artifact was collected when the Tor Browser is open. “cached-microdesc-consensus” file located in Tor browser folder at Desktop was loaded in Hex workshop. The file contains Relays information of Tor Browser.
Various researches have been performed for the analysis of security and privacy of Tor browser [25]. A few researches are found on the topic and detailed comparison of research is shown in Tab. 7. In a research where windows 7 platform is used for analysis of Tor browser [26]. Only memory was considered for obtaining artefacts for finding traces of Tor. Moreover, platform used was outdated. Whereas in our research many important artefacts were recovered from registry and hard disk as well as analysis performed on windows 10. Another research comprises on the analysis of user browsing artefacts from memory was presented [27]. Authors also confirmed that Tor remove all of its artefacts from memory when it is closed. Where our results shows that Tor leaves artefact while it is closed. Analysis of registry and hard disk is also missing. A research performed on windows 10 presented analysis over windows 10 [28]. But major drawback was no browser artefacts were collected and analysis performed [29]. Another major findings of our research is tracing relays information from hard disk and memory. The relays information will be useful in backtracking process. No previous research on recover relay information of Tor forensic. Browsing artefacts are also recovered in previous research from our dated windows. Our research is capable of collecting browsing artefacts from memory and hard disk running OS windows 10.
Figure 8: Cached-microdesc-consensus file contains relay information
Figure 9: Cached-cert file finds public keys of tor relay
Figure 10: Cached-microdesc.new file searches public key of tor relay

The forensic study of the Tor browser on Windows 10 is presented in this study. We observed the registry of the system, RAM and HDD for any traces that the Tor left on the user's system when it's open and when it's closed. We were looking for evidence of installation of Tor, use, and browsing behaviors. The findings of the research reveal that the Tor leaves several artifacts on the user's computer, particularly in the system memory. By using different open source tools, all the necessary and sufficient available artifacts of the Tor browser were collected and analyzed. Network forensics is an essential component of any digital inquiry. The Tor browser's network forensics is an area of interest for future research. This will aid in understanding the browser's forensic behavior. We're especially curious about the forensics of Orfox, the browser used for Android devices. Another app runs on Android that acts as a Tor proxy is Orbot. Our future research aims also involve forensic investigation of this application.
Acknowledgement: This research is ongoing research supported by Yayasan Universiti Teknologi PETRONAS Grant Scheme; 015LC0029 and 015LC0277.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. A. Mani, T. Wilson-Brown, R. Jansen and A. Jhonson, “Understanding tor usage with privacy-preserving measurement,” The Internet Measurement Conference (IMC’18), Boston MA USA, pp. 175–187, 2018. [Google Scholar]
2. The Tor Project, 2021. [Online]. Available: https://metrics.torproject.org/userstats-relay-table.html. [Google Scholar]
3. M. Wilson and B. Bazli, “Forensic analysis of I2P activities,” in 22nd International Conference on Automation and Computing (ICAC), Colchester, UK, pp. 529–534, 2016. [Google Scholar]
4. Digital Forensics: What Is It in 2021—2022?, 2021. [Online], Avialable: https://recfaces.com/articles/digital-forensics. [Google Scholar]
5. C. Cilleruelo, L. de-Marcos, J. Junquera-Sanchez and J. Martinez-Herraiz, “Interconnection between darknets,” IEEE Internet Computing, vol. 25, no. 3, pp. 61–70, 2021. [Google Scholar]
6. S. Jo, J. Lee, J. Han and S. Ghose, “P2p computing for intelligence of things,” Peer-to-Peer Networking and Applications, vol. 13, pp. 575–578, 2020. [Google Scholar]
7. A. Rasool and Z. Jalil, “Review of web browser forensic analysis,” Researchpedia Journal of Computing, vol. 1, no. 1, pp. 15–21, 2020. [Google Scholar]
8. A. K. Jadoon, W. Iqbal, M. F. Amjad, H. Afzal and Y. A. Bangash, “Forensic analysis of tor browser: A case study for privacy and anonymity on the web,” Forensic Science International, vol. 299, pp. 59–73, 2019. [Google Scholar]
9. G. Horsman, B. Findlay, J. Edwick, A. Asquith, K. Swannell et al., “A forensic examination of web browser privacy-modes,” in Forensic Science International: Reports, vol. 1, pp. 100036, Elsevier, Netherlands, 2019. [Google Scholar]
10. N. Shafqat, “Forensic investigation of user's web activity on Google chrome using various forensic tools,” International Journal of Computer Science and Network Security, vol. 16, no. 9, pp. 123–132, 2016. [Google Scholar]
11. R. Umar, A. Yudhana and M. N. Faiz, “Experimental analysis of web browser sessions using live forensics method,” International Journal of Electrical and Computer Engineering, vol. 8, no. 5, pp. 2951–2958, 2018. [Google Scholar]
12. S. Soney, C. Balan, P. P. Sajan and E. R. Lalson, “I2p forensic analysis,” International Journal of Recent Technology and Engineering, vol. 8, no. 6, pp. 1678–1682, 2020. [Google Scholar]
13. E. Qawasmeh, M. I. AlSaleh and Z. A. AlSharif, “Towards a generic approach for memory forensic,” in IEEE 6th HCT Information Technology Trends (ITT), United Arab Emirates, 2019. [Google Scholar]
14. H. Yin and Y. He, “I2p anonymous traffic detection and identification,” in 5th Int. Conf. on Advanced Computing & Communication Systems (ICACCS), India, 2019. [Google Scholar]
15. B. Bazli, M. Wilson and W. Hurst, “The dark side of I2P: A forensic analysis case study,” Systems Science & Control Engineering, vol. 5, no. 1, pp. 278–286, 2017. [Google Scholar]
16. Y. Yang, L. Yang, M. Yang, H. Yu, G. Zhu et al., “Dark-web forum correlation analysis research,” in IEEE 8th Joint Int. Information Technology and Artificial Intelligence Conf. (ITAIC), China, 2019. [Google Scholar]
17. B. D. Carrier and J. Grand, “A hardware–based memory acquisition procedure for digital investigations,” Digital Ivestigation, vol. 1, no. 1, pp. 50–60, 2004. [Google Scholar]
18. R. Magan-Carri, A. A. Galera, G. M. Fernandez and P. G. Teodoro, “Unveiling the I2P web structure: A connectivity analysis,” Computer Networks, vol. 194, pp. 108158, 2021. [Google Scholar]
19. D. Dayalamurthy, “Forensic memory dump analysis and recovery of the artefacts of using tor bundle browser–the need,” in 11th Australian Conf. on Digital Forensic, Australia, 2013. [Google Scholar]
20. E. Erdin, C. Zachor and M. H. Gunes, “How to find hidden users: A survey of attacks on anonymity networks,” IEEE Communications Surveys & Tutorials, vol. 17, no. 4, pp. 2296–2316, 2015. [Google Scholar]
21. Z. A. Al Sharif, H. Bagci and A. Asad, “Towards the memory forensics of MS-Word documents,” in Advances in Intelligent Systems and Computing, Springer, Singapore, pp. 179–185, 2018. [Google Scholar]
22. M. I. Al Saleh, Z. A. Al Sharif and L. Alawneh, “Network reconnaissance investigation: A memory forensics approach,” in IEEE 10th Int. Conf. on Information and Communication Systems (ICICS), Jordan, pp. 36–40, 2019. [Google Scholar]
23. A. Ali, M. Khan, M. Saddique, U. Pirzada, M. Zohaib et al., “Tor vs I2P: A comparative study,” in IEEE Int. Conf. on Industrial Technology (ICIT), Taiwan, pp. 1748–1751, 2016. [Google Scholar]
24. J. P. I. Chrisment and O. Festor, “A bird's eye view on the I2P anonymous file-sharing environment,” in Int. Conf. on Network and System Security, Tianjin, China, Springer, pp. 135–148, 2012. [Google Scholar]
25. W. Darcie, R. Boggs, J. Sammons and T. Fenger, “Online anonymity: Forensic analysis of the tor browser bundle,” Forensic Science International, USA, 2014. [Google Scholar]
26. S. Soltani and S. A. H. Seno, “A survey on digital evidence collection and analysis,” in 7th Internation Conf. on Computer and Knowledge Engineering (ICCKE), Iran, 2017. [Google Scholar]
27. T. Bakhshi, “Forensic of things: Revisiting digital forensic investigation in internet of things,” in IEEE Int. Conf. on Emerging Trends in Engineering, Sciences and Technology (ICEEST), Pakistan, 2019. [Google Scholar]
28. M. Stoyanova, Y. Nikoloudakis, S. Panagiotakis, E. Pallis and K. Markakis, “A survey on the internet of things (IoT) forensics: Challenges, approaches and open issues,” IEEE Communicaation Surveys & Tutorials, vol. 22, no. 2, pp. 1191–1221, 2020. [Google Scholar]
29. G. Surange, Z. A. Al Sharif and P. Khatri, “IoT forensics: A review on current trends, approaches and foreseen challenges,” in 8th Int. Conf. on Computing for Sustainable Global Development, India, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |