DOI:10.32604/cmc.2022.023907

| Computers, Materials & Continua DOI:10.32604/cmc.2022.023907 |  |
| Article |
Multi-dimensional Security Range Query for Industrial IoT
1School of Engineering Technology, Al Hussein Technical University (HTU), Amman, 11831, Jordan
2Department of Mechanical Engineering, College of Engineering, Taif University, Taif, 21944, Saudi Arabia
3Department of Electrical Engineering, University of Engineering and Technology Peshawar, Pakistan
4Department of Computer Science and Engineering, Chungnam National University, Daejeon, 34134, Korea
*Corresponding Author: Ki-Il Kim. Email: kikim@cnu.ac.kr
Received: 26 September 2021; Accepted: 02 November 2021
Abstract: The Internet of Things (IoT) has allowed for significant advancements in applications not only in the home, business, and environment, but also in factory automation. Industrial Internet of Things (IIoT) brings all of the benefits of the IoT to industrial contexts, allowing for a wide range of applications ranging from remote sensing and actuation to decentralization and autonomy. The expansion of the IoT has been set by serious security threats and obstacles, and one of the most pressing security concerns is the secure exchange of IoT data and fine-grained access control. A privacy-preserving multi-dimensional secure query technique for fog-enhanced IIoT was proposed in light of the fact that most existing range query schemes for fog-enhanced IoT cannot provide both multi-dimensional query and privacy protection. The query matrix was then decomposed using auxiliary vectors, and the auxiliary vector was then processed using BGN homomorphic encryption to create a query trapdoor. Finally, the query trapdoor may be matched to its sensor data using the homomorphic computation used by an IoT device terminal. With the application of particular auxiliary vectors, the spatial complexity might be efficiently decreased. The homomorphic encryption property might ensure the security of sensor data and safeguard the privacy of the user's inquiry mode. The results of the experiments reveal that the computing and communication expenses are modest.
Keywords: Internet of things; data security; ciphertext; privacy encryption
The Internet of Things (IoT) is regarded as the third revolution in the development of the information technology industry after computers and the Internet. Relying on the rapid development of smart homes, Internet of Vehicles (IoV), smart medical care, and smart grids based on the IoT, the era of the Internet of Everything (IoE) has arrived [1–5]. The latest statistics from the Statista website show that it is expected to exceed 30 billion interconnected devices in 2020 [6–10].
Countless smart terminals in the IoT transmit the massive amounts of data they sense through complex information and communication channels to data centers with huge data storage and processing capabilities, which can be abstracted as a “terminal transmission pipeline cloud” architecture, which also corresponds to the IoT three logical levels: perception layer, transmission layer and application layer [11–14]. Because of its ubiquitous network, comprehensive perception, reliable transmission, and intelligent processing, the characteristic elements are becoming more prominent, causing the IoT to face very severe security challenges [15].
The IIoT is the integration of the IoT system and the industrial automation system. It has the characteristics of comprehensive perception, interconnected transmission, and intelligent processing. It is one of the main development directions of the IoT technology in the future [16]. One of the important tasks of the IIoT application system is to analyze and process the sensor data of the IoT devices. If all the sensor data of the IoT devices are collected in the control center for processing, not only may the system be delayed due to network congestion, but also it will expose the system to the risk of a single point of failure [17–20]. The edge computing model that has emerged in recent years can effectively alleviate the performance bottlenecks and security risks that exist in the traditional centralized computing model by making full use of the computing power of the network edge devices [21–25]. By deploying fog devices at the edge of the IIoT, the sensor data in the IoT can be preprocessed on the edge of the network to improve the quality of service (QoS) [26–30].
The protection of sensor data of IoT devices is one of the important issues that need to be considered in fog-enhanced IIoT systems [31]. For example, in a fog-enhanced industrial Internet system, operation and maintenance personnel need to monitor whether the IoT devices in the system are operating normally, that is, query whether the sensor data of the IoT devices is in a reasonable range to determine their operating status. For security considerations, sensor data and query results cannot be leaked to any other unauthorized parties during the query process, so a secure data query plan must be designed [32]. In terms of data security query, many scholars have considered outsourcing the query of encrypted data. For example, the authors in [33] used Bloom filters to build a query index, which realized the fuzzy multi-keyword sort range query of encrypted data. The authors in [34] proposed a range query method that integrates bucket partitioning, identity authentication and verification code technologies for the data query problem in a two-layer wireless sensor network (WSN). The authors in [35] studied the multi-dimensional confidential range query of outsourcing data, and proposed an individualized query scheme with flexible permissions. In recent years, the range query for non-outsourced encrypted data has attracted the attention of researchers. For example, Reference [36] proposed a range query matrix method, and designed a single-dimensional security range query scheme using homomorphic encryption technology. Existing research on range query that supports privacy protection features mainly focuses on the query range and the confidentiality of the query subset that meets the conditions. Multi-dimensional query is not supported, and the communication overhead is relatively high.
Because some large-scale IoT devices in the IIoT have many different types of sensors, the monitoring of their status requires multiple sensor data belonging to the device, that is, multi-dimensional data query, while the traditional data query can only use multiple queries will increase the system's computing and communication costs. Therefore, it is necessary to design a multi-dimensional data query solution for the IIoT. In addition, the confidentiality of sensor data and the protection of user query mode need to be considered when designing the scheme. Constructing multi-dimensional data-oriented query trapdoors and matching based on homomorphic encryption is a feasible idea to solve this problem, such as the Boneh-Goh-Nissim (BGM) encryption algorithm [37] and the algorithm proposed by Reference [38]. The user performs confidential processing of the query range to form a query trapdoor. After receiving the query trapdoor in the form of ciphertext, the IoT device matches its own sensor data, and uses the self-blindness of the homomorphic encryption algorithm to form a new sensor data and report the ciphertext to the fog device. The fog device collects the ciphertext of the sensor data that meets the conditions submitted by the IoT device to which it belongs, and returns the collected result to the inquiring user for calculation and decryption.
This paper proposes a multi-dimensional security range query solution with privacy protection features for the fog-enhanced IIoT. The solution uses query interval matrix generation, decomposition and reconstruction based on auxiliary vectors, and other methods to reduce the storage and communication costs. Then, uses the homomorphic encryption to achieve privacy protection. The proposed algorithm first maps the range of n-dimensional data involving multiple different dimensions and different starting points to a query matrix. The size of the matrix is determined by the total query interval size and is not affected by the required query dimension. Second, construct multiple auxiliary vectors to decompose and reconstruct the matrix. Third, we used the BGN homomorphic encryption to design the query trapdoor generation and matching. Finally, the feasibility and performance of the proposed and existing schemes are verified and analyzed through simulation experiments.
This section introduces the two basic mathematical methods used in the proposed algorithm, namely the large composite number
2.1 Large Composite Order Bilinear Mapping
Let
1) Bilinear. For any
2) Non-degenerate. There exists
3) Computability. There is an efficient algorithm, when
The large composite order bilinear parameter generator CGen(K) is a probabilistic algorithm, which takes the safety parameter K as an input value and outputs a five-tuple (N,
Let
2.2 BGN Homomorphic Encryption Algorithm
The BGN homomorphic encryption algorithm is a well-known fully homomorphic encryption algorithm, which consists of three phases, namely the key generation, encryption and decryption.
1) Key Generation Phase
Given the safety parameter K, the composite order bilinear mapping parameter group (N,
2) Encryption Phase
Suppose the message space which contains only integers and whose capacity is determined by the specific application
3) Decryption Stage
Given the ciphertext c = E(m, r) = gmhr
In addition, the BGN homomorphic encryption algorithm has self-blindness, that is, given the ciphertext E(m, r)
The BGN homomorphic encryption algorithm has the following homomorphic characteristics.
a) Additive homomorphism on group G. Given E(m1, r1)
For the sake of simplicity, the random number term can be ignored and rewritten as
b) Multiplicative homomorphism on group G. Given
c) Multiplicative homomorphism from group G to group
d) Additive homomorphism on the group
e) Multiplicative homomorphism on the group
3 Multi-Dimensional Query Scheme with Privacy Protection Features
The proposed algorithm is an aggregation query solution for various fog-enhanced IIoT. The multi-dimensionality in this article means that the sensor data of an IoT device is composed of data of multiple different dimensions. The data includes water temperature, voltage, volume, material allowance, etc. According to actual needs, it may be necessary to query the sensor data of different dimensions of the device at the same time. For example, in a factory, the average value of water temperature, voltage, volume, and material remaining can be counted, which cannot only understand and predict the operating status of the equipment in time, but also provide a basis for optimizing the production process.
It should be noted that in the actual IIoT environment, data have different dimensions and accuracy. For example, power consumption data, water consumption data, etc. may have decimals. Since each IoT device is unlikely to change its detection accuracy through software means such as over the air (OTA) upgrades after manufacturing, in order to simplify the calculations and adapt to the needs of multi-dimensional queries, the proposed algorithm is as follows. The sensing data with an accuracy of less than 1 needs to be converted when participating in the calculation. For example, the value of the power sensor data at a certain time node is 10.37 W. In the calculation, multiply it by 100, which becomes 1037 and then perform range query. In this way, the range query of multiple dimensions can be realized without loss of accuracy. In fact, the amplification factor of a certain dimension of data can be written into the device when it is deployed.
There are three types of entities in the proposed scheme, namely, fog equipment at the edge of the network, IIoT equipment D = {D1, D2, …, DN} located within the jurisdiction of fog equipment, and query users. The proposed model is shown in Fig. 1.
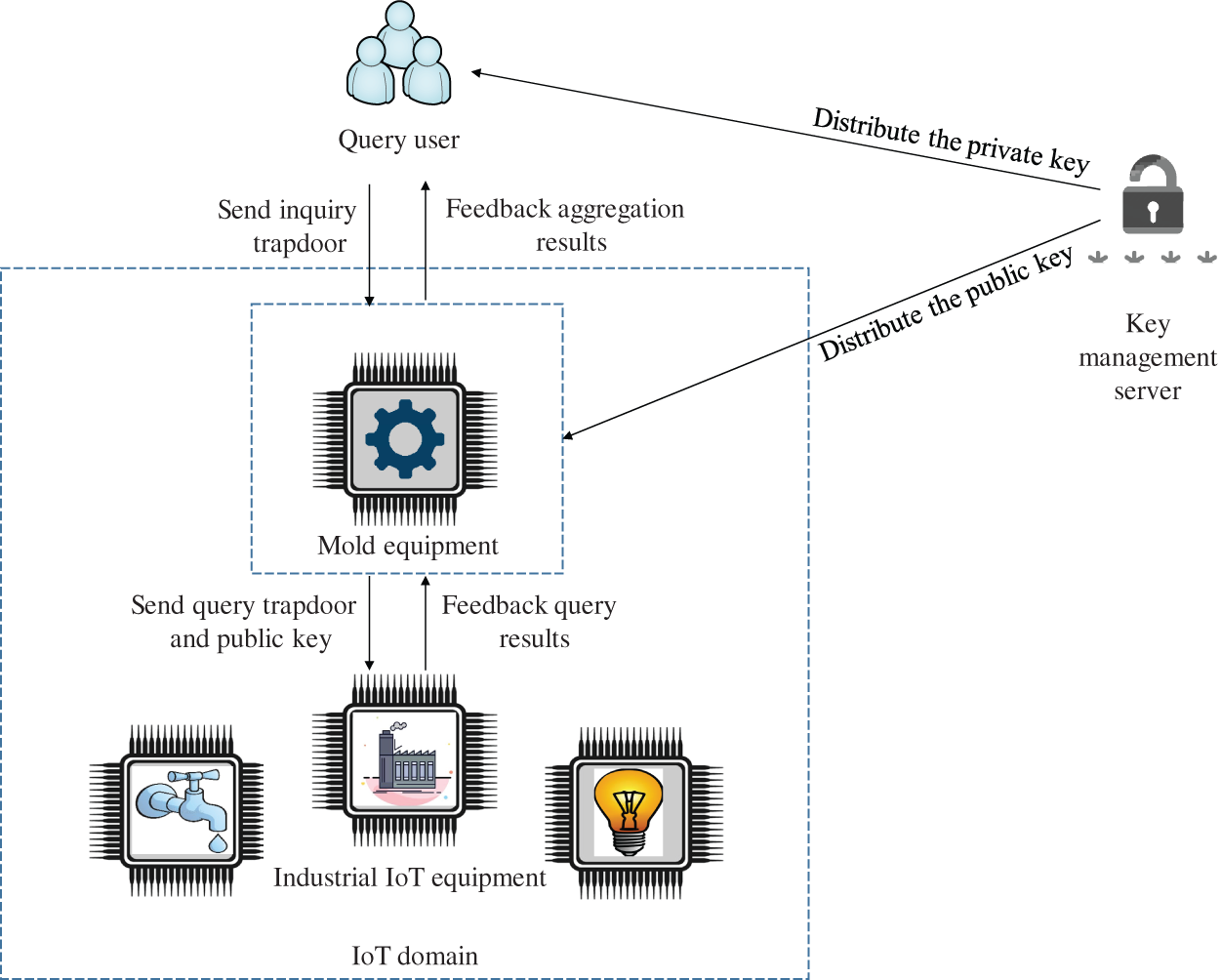
Figure 1: Proposed system model
1) Industrial Internet of Things equipment D = {D1, D2, …, DN} is a collection of a group of devices, which are distributed in each specific domain. Each IoT device not only has the ability to detect and collect specific data, but also has the ability to transmit data, so that each IoT device Dk can periodically report sensor data to fog devices in its domain.
2) The fog equipment in the model of this paper is located at the edge of the network, and each fog equipment has its own jurisdiction. This jurisdiction can be determined according to specific application scenarios, such as a production equipment, a workshop, or even a factory area. The fog device can collect and calculate the sensor data of the device within its jurisdiction, and complete the query request sent by the user. Compared with IoT devices, fog devices have stronger computing and storage performance, and can complete sensing data collection and response to IoT devices in real time.
3) In the model of the solution in this paper, the query user can directly generate multiple-dimensional range queries and send them to the fog device to obtain the required data from the fog device. For example, the user may want to know how many device sensor data within the range of fog devices can satisfy dimension 1, range [B1, T1], dimension 2, range [B2, T2], …, dimension m, range [Bm, Tm]. The sensor data of which devices meet the conditions. What is the average value of sensor data in each dimension of the device that meets the conditions? The fog device can collect the sensory data that meets the conditions fed back from all devices within the jurisdiction, and then generate the correlation degree based on the feedback data, and finally return the correlation degree and sensor data to the user.
3.2 Multi-Interval Query Matrix
The proposed algorithm is improved on the basis of the single query interval matrix algorithm, so that the multi-dimensional range query can be matrixed while maintaining low communication overhead. Through observation, it can be found that any given query interval can be decomposed into two types of rows, namely partial rows (PR) and continuous rows (CR). Fig. 2 shows the query matrix after the mapping of two query intervals, the dark gray part is PR, and the light gray part is CR. This matrix structure provides the possibility to further compress the matrix. In general, a typical query interval can be decomposed to get two PR and one CR.
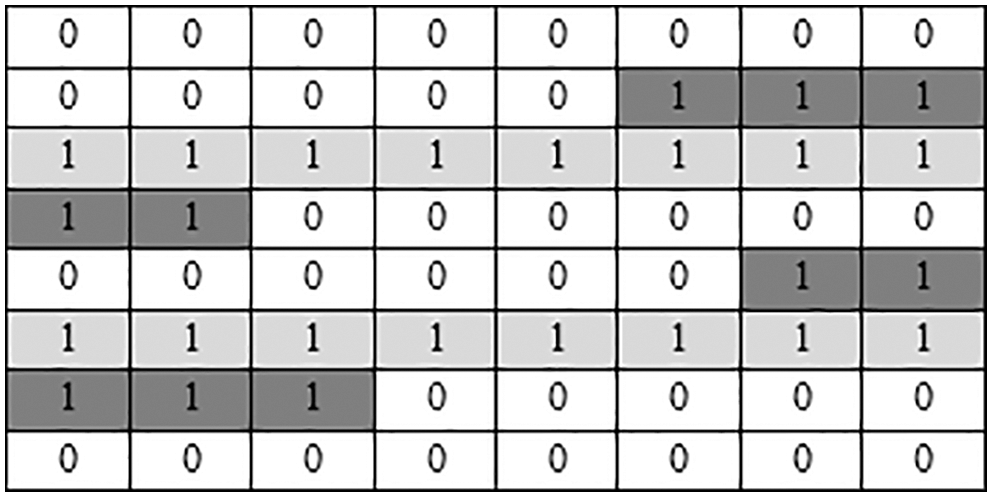
Figure 2: The query matrix after the mapping of two query intervals
Suppose the total number of query intervals is n. First, define four special auxiliary vectors.
1) Xk = (xk1, xk2,…, xkn). The generation rule is that when the i-th row elements in the k-th matrix are all 1, set xki = 0; otherwise, xki = 1.
2) Yk= (yk1, yk2,…, ykn). The generation rule is that when there is at least one 1 in the j-th column of the k-th matrix, set ykj = 0; otherwise, yki = 1.
3)
4)
This article deals with incomplete rows and continuous rows in the matrix respectively. First, split the incomplete rows corresponding to n query intervals into multiple matrices R1, R2,…, R2n independently, and split all consecutive rows into a matrix RC, as shown in Fig. 3. Obviously, the original query matrix R = R1
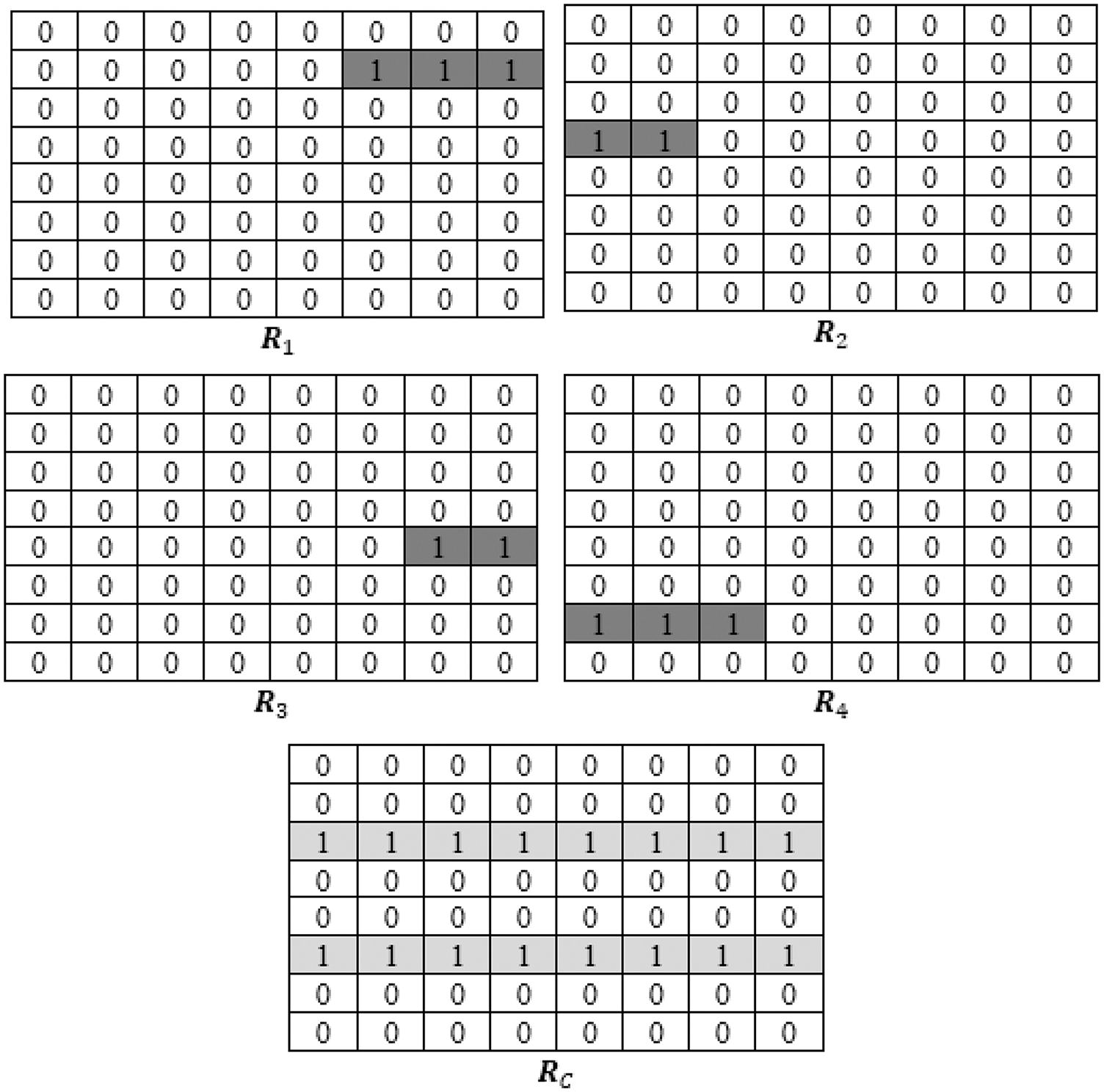
Figure 3: Query the split result of the matrix
Construct the vectors Xk, Yk,
At this time, all elements in the matrix can be obtained through vector operations. Use Rk to represent the matrix related to incomplete rows, and use RC to represent the matrix related to continuous rows. The AND operation of the matrix is expressed as a bitwise AND operation, and the matrix OR operation is expressed as a bitwise OR operation and sorted into a vector multiplication. The form of sum vector addition is shown in Eq. (3).
Among the 8n + 4 vectors involved in the operation, there are 4n + 1 vectors whose elements are all 1, and donot need to be calculated and stored, namely
After calculation, it can be seen that the vector
The program flow of the proposed method is mainly composed of three parts. First, the key management server generates the query key, distributes the private key to the user, and the public key to the fog device FDi. When the user performs a data range query, the private key is used to encrypt the query range and query dimension to generate a trapdoor, and send it to the fog device FDi. Then, after receiving the query trapdoor and query dimension ciphertext from the user, the fog device sends the query trapdoor to the IoT device under its jurisdiction for query. After the IoT device calculates the result ω of this query, it sends it to the fog device for aggregation. The fog device obtains ζ through aggregation and calculation and feeds it back to the user. Finally, the user calculates and decrypts the received ζ, and the query result can be obtained. The whole process is shown in Fig. 4. The following will specifically introduce the process of this article.
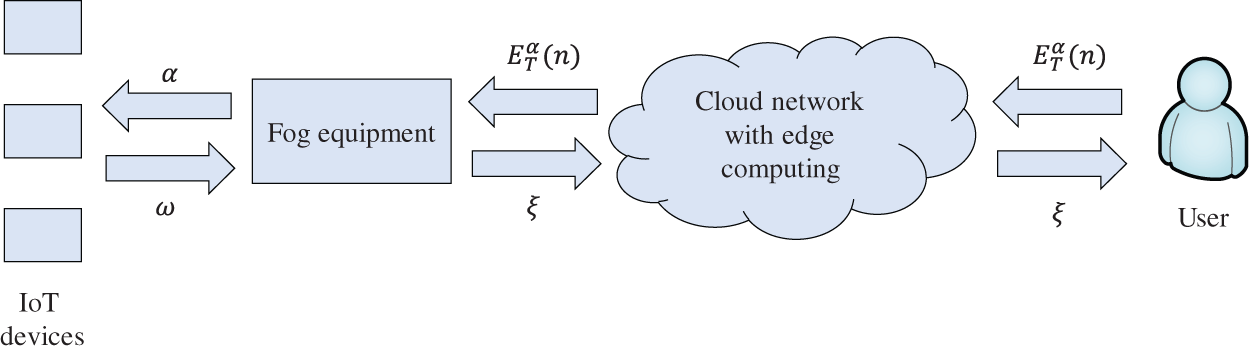
Figure 4: System flow
To facilitate the description of the data query process, the main parameters used in the process structure are listed in Tab. 1.
1) Key Generation
Given the security parameter K, the key management server generates a composite order bilinear mapping parameter set (N, g, G, GT, e) by the generator CGen(K). Where N = pq, p, q are two K bit random prime numbers, G, GT are two N-th order groups, g
2) Query Trapdoor Generation
For each certain use scenario, the number and type of dimensions involved in each query initiated by the user are determined. In the proposed scheme, the number of dimensions of the data to be queried is set to n, that is, the number of intervals that users query is n. It should be noted that the query intervals [Bquery, Tquery] referred to in the process are all multiplied sensing data intervals. The IoT has also performed the same multiplication processing on the data, so the data multiplication process will not be repeated. The trapdoor generation of a range query consists of the following steps.
a) Data Mapping and Conversion. Set any query dimension of this query as the first interval, and then determine the starting point of each interval in the query sequence according to the following rules. Among them, li is the interval length of the i-th interval.
That is, the starting point of any i-th interval is the position after the end point of the (i − 1)-th interval is increased by one interval length to prevent multiple intervals from being connected and forming too many CR blocks. After determining the starting point, the ending point of any i-th interval is
For a query interval
The data offset βi of the query interval can be determined by the starting point of the query interval. After the offset, the k-th element in the query interval is vik, then βi and vik satisfy the condition shown in Eq. (8).
Determine the matrix order m from the end point of the last query interval, and then construct the m-order query matrix R. In order to map the query interval to the query matrix R, map
The order m of the matrix is determined by the end point of the last query interval rather than the upper bound of a single query interval, so the storage space requirement of each vector has nothing to do with the upper bound of a single interval of multi-dimensional query, only the length of all query intervals and related, the storage overhead is O(m).
b) Vector Generation and Encryption. After generating the query matrix R, according to the method described in Section 3.2, the corresponding vectors X, Y, X′, Y′ are generated from the query matrix, and the required 4n + 1 vectors are selected for storage and encryption. which is
For the convenience of calculation, the vector
According to Eq. (4), all elements
The user selects 2n + 1 random numbers r1, r2,…, r2n+1 to encrypt all 4n + 1 vectors to obtain
where
In order to meet the needs of multi-dimensional query, two values need to be added to the original
Calculate the hash value
At this point, the query trapdoor
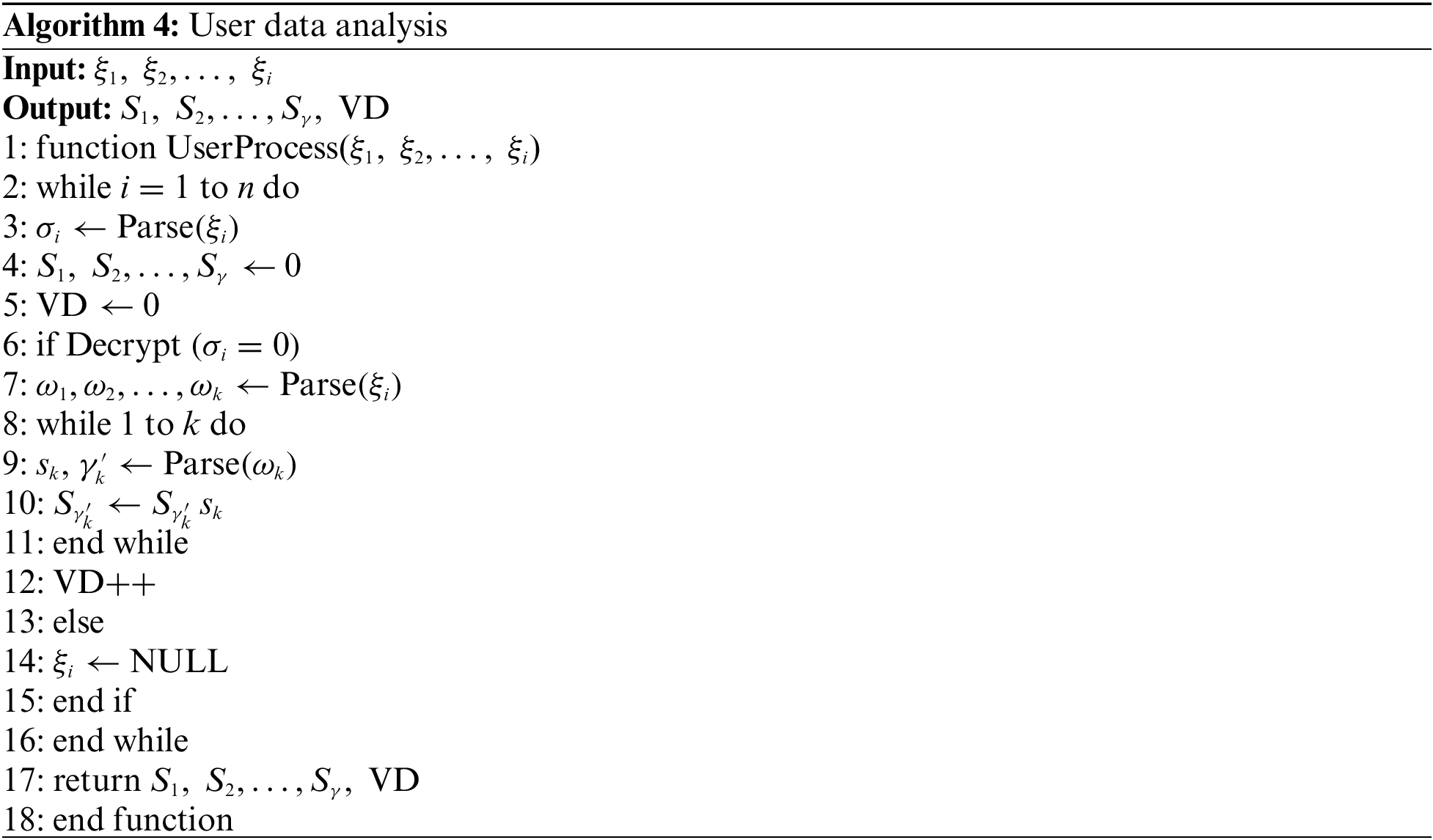
3) Processing on the Device Side of the IoT
Corresponding to the dimension identifier

After obtaining the queryVector, the IoT device first extracts the offset

For the ck and
By executing Algorithms 1 and 2, the sensor data
4) Treatment of Fog Equipment
After the fog device FDi receives the

5) User Analysis Data
After the user receives the data
At this time,
This section analyzes the security of the solution in this article, including forward security, backward security, privacy protection, unlinkability and other key security features, and introduces some attack modes designed for encryption range query solutions in recent years. The security of the proposed scheme is analyzed in the face of these attack modes.
4.1 Forward and Backward Safety
Assuming that the adversary A obtains the private key sk = p used in a certain query, it can only decrypt the ciphertext of the current query. Since each time a query is made, the user will use the newly generated public and private key to query, the adversary A can only know the security parameter K used by the user to generate the key using the private key sk = p, and cannot be calculated from this. Any information of the key previously generated by the user cannot decrypt any previously queried data except the current queried data. Therefore, the proposed scheme satisfies forward and backward security.
4.2 Privacy Protection in Query Mode
Suppose that adversary A intercepts the trapdoor used by user U in a certain query
In addition to the adversary A, the IoT device Dk and the fog device FDi also cannot know the specific information of the query trapdoor. Because the proposed scheme is different from the traditional query solution, as it uses homomorphic encryption calculation to replace the traditional comparison process. Dk determines its original sensor data
4.3 Sensing Data Confidentiality
Assume that adversary A intercepts the message
Suppose that the adversary A intercepts the message
In addition to the adversary A, the fog device FDi cannot learn the raw sensor data of the IoT device Dk
In the proposed method, due to the use of random numbers, all query trapdoors generated by user U are random. Even if two or more query trapdoors are sent by the same user, external attackers cannot determine whether these queries come from the same user, which means that the attacker cannot associate two different queries to a specific user. Therefore, the proposed solution provides unlinkability, and the attacker cannot associate the identity of the queryer by intercepting the query trapdoor.
In order to prevent data integrity damage that may occur during data transmission, in the proposed solution, when user U generates a query trapdoor, paired query vectors
In the proposed solution, the query process for the sensor data of IoT devices is essentially a BGN-based homomorphic encryption calculation process. The process does not involve decryption operations. The IoT devices and fog devices only need to know the system public key pk and the private key sk is only in the hands of the inquiring user. Therefore, there are fewer entities involved in key management and update, and the cost of key management is lower.
4.7 Protection Against Other Attack Methods
In addition to the above-mentioned common types of security attacks, in recent years, there have been a variety of attacks against encryption range queries. Among them, Reference [40] attacked encrypted data query by means of access mode disclosure. Reference [41] attacked the deterministic encryption (DTE) and order preserving encryption (OPE) methods in the attribute scheme, and used encrypted information and public auxiliary data to complete the plaintext recovery. Reference [42] defined two basic sources of leaks, such as access mode leaks and communication capacity leaks, and developed a universal one that is applicable to any system that supports range query and whose access mode or communication capacity is leaked. Reference [43] proposed an improved replay attack on encrypted data using the data leaked in the range query, including query mode and sorting information.
Different from the database query scenarios discussed in [40–43], the proposed scheme mainly considers the range query with privacy protection features in the fog-enhanced IIoT, which is an aggregate privacy protection query. The proposed scheme can protect the privacy of the upper and lower bounds in the range query and the subset of devices that meets the query conditions, and will not reveal the related information such as query mode and keyword frequency. In addition, for any range query, the data volume of the query results returned by the proposed scheme is the same, and no flow information will be leaked. Therefore, the proposed scheme can resist the above-mentioned several typical attacks on the security range query.
This section analyzes and compares the performance of the proposed scheme with the existing similar schemes, mainly including the comparison of the calculation and communication overheads of the query trapdoor generation phase and the server query phase. All simulation experiments were carried out on a notebook computer configured with Intel i7-9750H 2.60 GHz, 16 GB memory, and running Windows 10 system, using Java Math's large number calculation library and JPBC library [44] to implement the algorithm. In addition, the operations that consume less time for addition operations, hash operations, etc., are ignored in the comparison.
5.1.1 Computational Overhead at Each Stage
For convenience, define Tm, To, Tp, and Tem to represent the time cost of single integer multiplication, integer modular power, bilinear mapping, and point multiplication on elliptic curves, respectively. Let l be the length of the query interval in each dimension, k is the total number of dimensions, and q is the upper bound of a single query interval. For solutions that only support single-dimensional queries, such as the Reference [36] solution, a multi-dimensional query is treated as multiple single-dimensional queries. Tab. 2 shows the comparison of the computational cost of each stage.
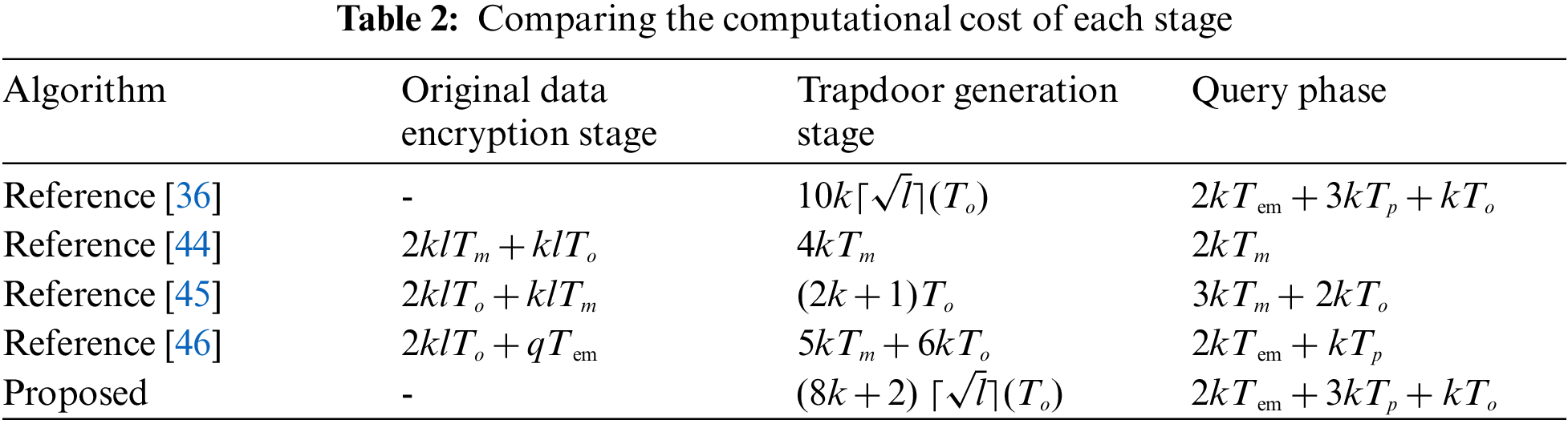
Both the proposed scheme and Reference [36] method involve the IoT devices directly at the edge of the network to participate in the query, so the sensor data does not need to be encrypted and stored on the server, and the encryption phase does not generate computational overhead.
5.1.2 Full-Dimension Query Calculation Cost
This section considers the computational cost of querying data of all dimensions for each query when the total number of dimensions is certain. Suppose the total number of dimensions k = 10, the length of the query interval l = 36, and the upper bound of the query interval q = 50. Then the References [36,44–46] algorithms and the proposed algorithm takes about 22.641, 15.864, 20.191, 21.638 and 20.360 ms to complete a full-dimensional query.
Fig. 5 shows the comparison result of the calculation cost of the full-dimension query of the specified dimensions for the scheme in this paper and the existing schemes. Among them, the proposed algorithm and Reference [36] schemes introduces the bilinear mapping operations in the query process, and the computational cost is higher than that in [44,45] that uses the integer encryption operations, but References [44–46] schemes need to encrypt and send the sensor data to a third-party data storage server in advance, this process will inevitably have time delay and generate encryption overhead. The scheme in [36] do not need to encrypt and send sensor data, and support users to query sensor data in real time. It only supports single-dimensional query, so the overall computational cost is higher than the propose scheme when multi-dimensional query is performed.
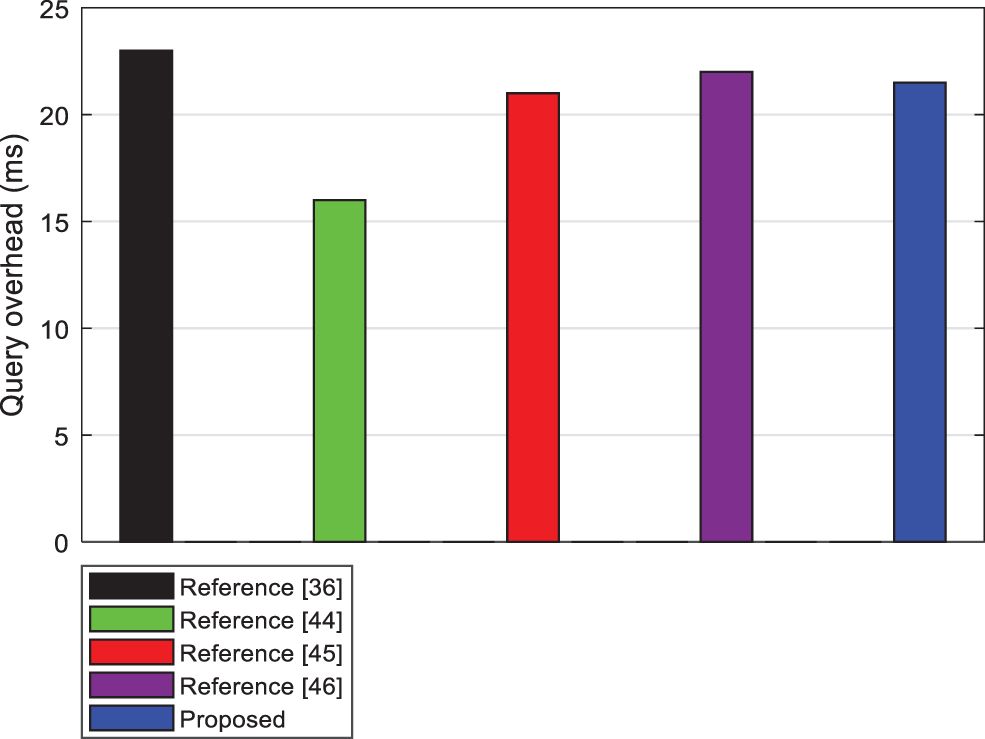
Figure 5: Comparing the calculation cost of full-dimensional query
5.1.3 Partial Dimensional Query Calculation Cost
Partial dimension quantity query means that when the total number of dimensions is certain, each query only queries the sensor data of part of the dimensions. Assuming that the total number of dimensions k = 10, the query interval length l = 36, and the upper bound of the query interval q = 50, part of the dimension queries with dimensions 5, 7, and 9 are performed respectively. Fig. 6 shows the comparison results of the calculation cost of the proposed scheme and the existing schemes when performing partial dimension query. It should be noted that, considering that even if part of the dimension query is performed, the amount of data stored by the data storage server should be the same as that of the full-dimensional query. Therefore, for a solution that needs to encrypt and store sensor data, the encryption overhead is still equivalent to full-dimensional query. Although the proposed algorithm and literature [36,46] all uses the bilinear mapping operation, the query stage overhead is high, but because the proposed and Reference [36] schemes are for real-time query of sensor data, they do not needs to be encrypted and stored in advance, so when fewer dimension queries are performed under the condition of a given total number of dimensions (5, 7 queries), the overall computing overhead is still lower than that of a solution that requires encrypted storage of sensor data. Since Reference [36] only supports single-dimensional query, it needs to repeatedly send query trapdoors when performing multi-dimensional query, and its overall computational cost is also higher than the proposed scheme.

Figure 6: Comparing the calculation cost of different dimensions
5.1.4 Computational Overhead for Querying with Different Interval Lengths
The query of different interval length means that when the total number of dimensions, the upper limit of the query interval length, and the upper limit of the query interval are certain, each query only queries the finite interval length. Suppose the total number of dimensions k = 10, the upper limit of the query interval length l = 100, and the upper limit of the query interval q = 100. When querying 25%, 50%, and 75% length intervals respectively, the proposed algorithm and the query of different interval lengths refer to the case of the total number of dimensions, the upper limit of the query interval length, and the upper limit of the query interval, each query only queries the finite interval length. Suppose the total number of dimensions’ k = 10, the upper limit of the query interval length l = 100, and the upper limit of the query interval q = 100. When querying 25%, 50%, and 75% length intervals respectively, compare the proposed scheme with existing schemes when completing a query calculation cost, and the result is shown in Fig. 7.
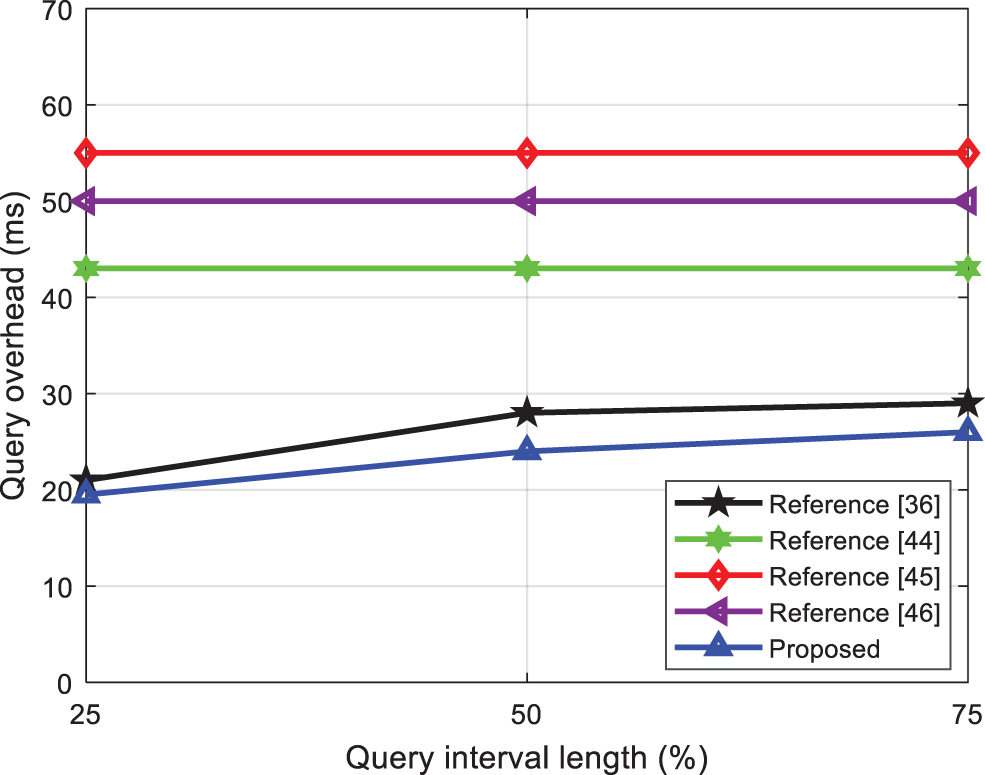
Figure 7: Comparing the computational cost of queries with different interval lengths
According to the analysis of the calculation cost of the query of the number of dimensions in this article, it can be seen that for the storage scheme that needs to encrypt the original sensor data, the encryption cost is the same as the calculation cost of the full-dimensional query. Except for the proposed and Reference [36] schemes, the computational cost of the other three schemes is not related to the length of the query interval, but is related to the total number of query dimensions. However, due to References [44–46] schemes, the original sensor data needs to be encrypted and stored in advance, so that when the query interval length is large and the total number of dimensions is high, the overall computational cost is relatively high. The Reference [36] scheme does not support multi-dimensional queries, and repeatedly sends single-dimensional query trapdoors when performing multi-dimensional queries. It uses more vectors than the proposed scheme, and the computational cost is higher.
This section compares the communication overhead of the proposed scheme and the existing schemes. Set the total number of dimensions k = 10, the length of the query interval l = 36, and the upper bound of the query interval q = 50 full-dimensional query, and compare the communication overhead of the whole process of different schemes. In order to compare the communication overhead of each scheme fairly, the following assumptions are made.
1) The security parameters (or key length) of each scheme are 128 bits.
2) The hash algorithm used in each scheme is SHA-1, therefore, the hash digest length of each scheme is 160 bits.
3) The random numbers used in each scheme are all 64 bits.
The communication process of the proposed scheme mainly lies in the sending stage of query trapdoor, the stage of fog device feedback from IoT devices and the stage of user feedback query from fog devices. Since the proposed scheme is to vectorize the query matrix, the communication overhead of the query trapdoor is relatively large, and the overhead of the other stages is relatively small. The communication cost of the query trapdoor generated of the proposed scheme during the sending phase of the query trapdoor is about 31016 B, the communication cost of the fog device phase of the IoT device feedback is about 1365 B, and the communication cost of the fog device feedback query user part is about 1370 B, a total of about 33751 B. Tab. 3 shows the communication overhead of the scheme in this article and the comparison scheme.
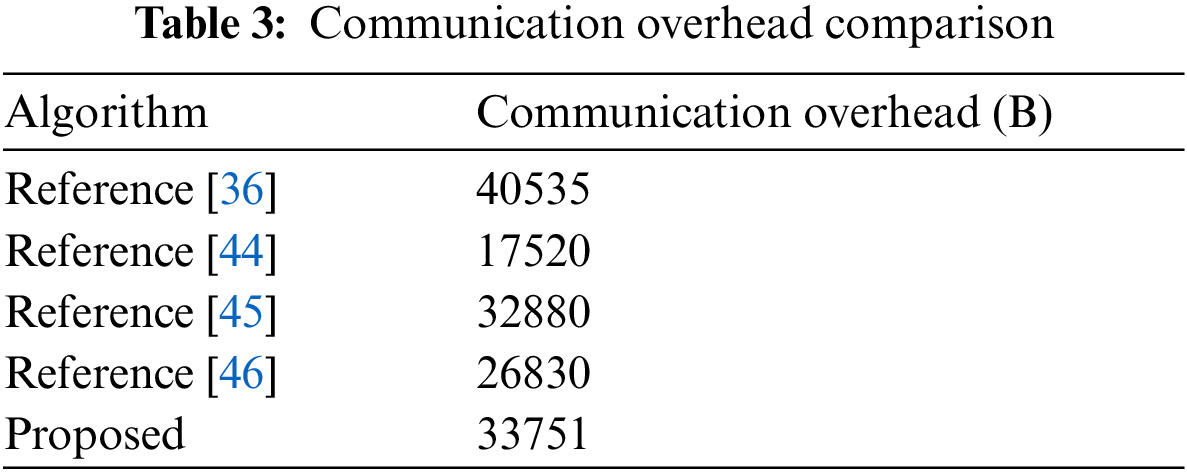
Reference [44] scheme uses a homomorphic encryption algorithm in the integer domain improved from the SHE encryption scheme. Under the same conditions, the ciphertext length is small, but its algorithm is susceptible to noise in the ciphertext. When the noise in the ciphertext is large, it affects the decryption process. Reference [45] scheme has a slightly lower communication overhead than the proposed scheme, however this and Reference [44] schemes encrypt sensor data and query the data transmitted to the server, and it requires two servers to participate in the calculation, and the transmission delay is too large to realize the real-time query of sensor data. Reference [46] scheme query trapdoor is smaller in size, which makes its communication cost lower than the proposed and Reference [36] schemes, but its computational cost is high, and it does not support real-time query of sensor data. Reference [36] scheme that provides real-time data query only supports single-dimensional query, and multiple queries need to be initiated when querying a multi-dimensional sensor data, and its communication overhead is higher than the solution in this paper.
In summary, the proposed algorithm achieves a good balance in computing overhead, communication overhead, and support for multi-dimensional query features.
In this paper, a multi-dimensional security query scheme with privacy protection features with high communication efficiency is designed for the fog-enhanced industrial Internet of Things. The proposed scheme uses the BGN homomorphic encryption algorithm to encrypt the query trapdoor, and integrates matrix decomposition and reconstruction technology to protect the privacy of the query mode, while ensuring that the sensor data will not be leaked to unauthorized parties. Security analysis and simulation experiments show that the scheme in this paper can maintain a low level of computing and communication costs while ensuring multiple security features and multi-dimensional query functions. The next step will further optimize the proposed scheme, such as further improving communication efficiency and reducing communication overhead.
Acknowledgement: Taif University Researchers Supporting Project Number (TURSP-2020/260), Taif University, Taif, Saudi Arabia
Funding Statement: This study was supported by the Institute for Information & Communications Technology Planning & Evaluation (IITP) grant funded by the Korean government (MSIT) (No. 2019-0-01343, Training Key Talents in Industrial Convergence Security).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. Y. Sun, J. Liu, J. Wang, Y. Cao and N. Kato, “When machine learning meets privacy in 6G: A survey,” IEEE Communications Surveys & Tutorials, vol. 22, no. 4, pp. 2694–2724, 2020. [Google Scholar]
2. T. Huang, W. Yang, J. Wu, J. Ma, X. Zhang et al., “A survey on green 6G network: Architecture and technologies,” IEEE Access, vol. 7, pp. 175758–175768, 2019. [Google Scholar]
3. A. A. Fuqaha, M. Guizani, M. Mohammadi, M. Aledhari and M. Ayyash, “Internet of things: A survey on enabling technologies, protocols, and applications,” IEEE Communications Surveys & Tutorials, vol. 17, no. 4, pp. 2347–2376, 2015. [Google Scholar]
4. M. A. Garadi, A. Mohammed, A. K. Ali, X. Du, I. Ali et al., “A survey of machine and deep learning methods for internet of things (IoT) security,” IEEE Communications Surveys & Tutorials, vol. 22, no. 3, pp. 1646–1685, 2020. [Google Scholar]
5. S. Li, L. Li, B. Xu, Y. Feng and H. Zhou, “Research of a reliable constraint algorithm on MIMO signal detection,” International Journal of Embedded Systems, vol. 12, no. 2, pp. 13–26, 2020. [Google Scholar]
6. J. Gojal, E. Monteiro and J. S. Silva, “Security for the internet of things: A survey of existing protocols and open research issues,” IEEE Communications Surveys & Tutorials, vol. 17, no. 3, pp. 1294–1312, 2015. [Google Scholar]
7. K. Tange, M. D. Donno, X. Fafoutis and N. Dragoni, “A systematic survey of industrial internet of things security: Requirements and foq computing opportunities,” IEEE Communications Surveys & Tutorials, vol. 22, no. 4, pp. 2489–2520, 2020. [Google Scholar]
8. S. Bashir, M. H. Alsharif, I. Khan, M. A. Albreem, A. Sali et al., “MIMO-terahertz in 6G nano-communications: Channel modeling and analysis,” Computers, Materials & Continua, vol. 66, no. 1, pp. 263–274, 2020. [Google Scholar]
9. F. Jameel, T. Ristaniemi, I. Khan and B. M. Lee, “Simultaneous harvest-and-transmit ambient backscatter communications under Rayleigh fading,” EURASIP Journal on Wireless Communications and Networking, vol. 19, no. 1, pp. 1–9, 2019. [Google Scholar]
10. Q. Alsafasfeh, O. A. Saraereh, A. Ali, L. A. Tarawneh, I. Khan et al., “Efficient power control framework for small-cell heterogeneous networks,” Sensors, vol. 20, no. 5, pp. 1–14, 2020. [Google Scholar]
11. K. M. Awan, M. Nadeem, A. S. Sadiq, A. Alghushami, I. Khan et al., “Smart handoff technique for internet of vehicles communication using dynamic edge-backup node,” Electronics, vol. 9, no. 3, pp. 1–17, 2020. [Google Scholar]
12. W. Shahjehan, S. Bashir, S. L. Mohammed, A. B. Fakhri, A. A. Isaiah et al., “Efficient modulation scheme for intermediate relay-aided IoT networks,” Applied Sciences, vol. 10, no. 6, pp. 1–12, 2020. [Google Scholar]
13. B. M. Lee, M. Patil, P. Hunt and I. Khan, “An easy network onboarding scheme for internet of things network,” IEEE Access, vol. 7, pp. 8763–8772, 2018. [Google Scholar]
14. O. A. Saraereh, A. Alsaraira, I. Khan and B. J. Choi, “A hybrid energy harvesting design for on-body internet-of-things (IoT) networks,” Sensors, vol. 20, no. 2, pp. 1–14, 2020. [Google Scholar]
15. T. Jabeen, Z. Ali, W. U. Khan, F. Jameel, I. Khan et al., “Joint power allocation and link selection for multi-carrier buffer aided relay network,” Electronics, vol. 8, no. 6, pp. 1–15, 2019. [Google Scholar]
16. M. Waqas, Y. Niu, Y. Li, M. Ahmed, D. Jin et al., “A comprehensive survey on mobility-aware D2D communications: Principles, practice and challenges,” IEEE Communications Surveys & Tutorials, vol. 22, no. 3, pp. 1863–1886, 2020. [Google Scholar]
17. M. Ahmed, Y. Li, M. Waqas, M. Sheraz, D. Jin et al., “A survey on socially aware device-to-device communications,” IEEE Communications Surveys & Tutorials, vol. 20, no. 3, pp. 2169–2197, 2018. [Google Scholar]
18. F. S. Shaikh and R. Wismuller, “Routing in multi-hop cellular device-to-device (D2D) networks: A survey,” IEEE Communications Surveys & Tutorials, vol. 22, no. 3, pp. 2622–2657, 2018. [Google Scholar]
19. M. Haus, M. Waqas, A. Y. Ding, Y. Li, S. Tarkoma et al., “Security and privacy in device-to-device (D2D) communication: A review,” IEEE Communications Surveys & Tutorials, vol. 19, no. 2, pp. 1054–1079, 2017. [Google Scholar]
20. O. Hayat, R. Ngah, S. Z. M. Hashim, M. H. Dahri, R. F. Malik et al., “Device discovery in D2D communication: A survey,” IEEE Access, vol. 7, pp. 131114–131134, 2019. [Google Scholar]
21. A. Asadi, Q. Wang and V. Mancuso, “A survey on device-to-device communication in cellular networks,” IEEE Communications Surveys & Tutorials, vol. 16, no. 4, pp. 1801–1819, 2014. [Google Scholar]
22. B. M. Elhalawany, R. Ruby and K. Wu, “D2D communication for enabling internet-of-things: Outage probability,” IEEE Transactions on Vehicular Technology, vol. 68, no. 3, pp. 2332–2345, 2019. [Google Scholar]
23. I. Loannou, V. Vassiliou, C. Christophorou and A. Pitsillides, “Distributed artificial intelligence solution for D2D communication in 5G networks,” IEEE Systems Journal, vol. 14, no. 3, pp. 4232–4241, 2020. [Google Scholar]
24. P. Pawar, A. Trivedi and M. K. Mishra, “Outage and ASE analysis for power controlled D2D communication,” IEEE Systems Journal, vol. 14, no. 2, pp. 2269–2280, 2020. [Google Scholar]
25. F. Qamar, M. U. A. Siddiqui, M. H. D. Hinidia, R. Hassan and Q. N. Nguyen, “Issues, challenges, and research trends in spectrum management: A comprehensive overview and new vision for designing 6G networks,” Electronics, vol. 9, no. 9, pp. 1–124, 2019. [Google Scholar]
26. Y. R. B. Al-Mayouf, N. F. Abdullah, O. A. Mahdi, S. Khan, M. Ismail et al., “Real-time intersection-based segment aware routing algorithm for urban vehicular networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 19, no. 7, pp. 2125–2141, 2018. [Google Scholar]
27. M. K. Hasan, M. M. Ahmad, A. H. A. Hashim, A. RAzzaque, S. Islam et al., “A novel artificial intelligence based timing synchronization scheme for smart grid applications,” Wireless Personal Communications, vol. 114, no. 2, pp. 1067–1087, 2019. [Google Scholar]
28. S. N. Makhadmeh, A. T. Khader, M. A. Al-Betar, S. Naim, A. K. Abasi et al., “A novel hybrid grey wolf optimizer with min-conflict algorithm for power scheduling problem in a smart home,” Swarm and Evolutionary Computation, vol. 60, no. 2, pp. 1–17, 2021. [Google Scholar]
29. N. Nurelmadina, M. K. Hasan, I. Memon, R. A. Saeed, K. A. Z. Ariffin et al., “A systematic review on cognitive radio in low power wide area network for industrial IoT applications,” Sustainability, vol. 13, no. 1, pp. 1–21, 2021. [Google Scholar]
30. K. R. Choo, R. X. Lu, L. Q. Chen and X. Yi, “A foggy research future: Advances and future opportunities in fog computing research,” Future Generation Computer Systems, vol. 78, no. 2, pp. 677–679, 2018. [Google Scholar]
31. R. X. Lu, K. Hueng, A. H. Lashkari and A. A. Ghorbani, “A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT,” IEEE Access, vol. 5, pp. 3302–3312, 2017. [Google Scholar]
32. R. Lu, X. H. Liang, X. Li and X. Shen, “EPPA: An efficient and privacy-preserving aggregation scheme for smart grid communications,” IEEE Transactions on Parallel and Distributed Systems, vol. 23, no. 9, pp. 1621–1631, 2012. [Google Scholar]
33. J. Wang, X. Yu and M. Zhao, “Privacy-preserving ranked multi-keyword fuzzy search on cloud encrypted data supporting range query,” Arabian Journal for Science and Engineering, vol. 40, no. 8, pp. 2375–2388, 2015. [Google Scholar]
34. H. Dai, Q. Ye, X. Yi, R. He, G. Yang et al., “VP2RQ: Efficient verifiable privacy-preserving range query processing in two-tiered wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 12, no. 11, pp. 1–15, 2016. [Google Scholar]
35. Y. Shen, L. S. Huang and W. Yang, “Achieving personalized and privacy-preserving range queries over outsourced cloud data,” in IEEE Int. Conf. on Communications, Paris, France, pp. 1–6, 2017. [Google Scholar]
36. R. Lu, “A new communication-efficient privacy-preserving range query scheme in fog-enhanced IoT,” IEEE Internet on Things Journal, vol. 6, no. 2, pp. 2497–2505, 2018. [Google Scholar]
37. D. Boneh, J. E. Goh and K. Nissim, “Evaluating 2-DNF formulas on ciphertexts,” in Theory of Cryptography Conf., Berling, Germany, pp. 325–341, 2005. [Google Scholar]
38. P. Paillier, “Public-key cryptosystems based on composite degree residuosity classes,” in Int. Conf. on the Theory and Applications of Cryptographic Techniques, Berlin, Germany, pp. 223–238, 1999. [Google Scholar]
39. M. S. Islam, M. Kuzu and M. Kantarcioglu, “Interface attack against encrypted range queries on outsourced databases,” in Proc. of the 4th ACM Conf. on Data and Application Security and Privacy, New York, USA, pp. 235–246, 2014. [Google Scholar]
40. M. Naveed, S. Kamara and C. V. Wright, “Interface attacks on property-preserving encrypted databases,” in Proc. of the 22nd ACM SIGSAC Conf. on Computer and Communications Security, New York, USA, pp. 644–655, 2015. [Google Scholar]
41. G. Kellaris, G. Kollios, K. Nissim and A. Neill, “Generic attacks on secure outsourced databases,” in Proc. of the ACM SIGSAC Conf. on Computer and Communications Security, New York, USA, pp. 1329–1340, 2016. [Google Scholar]
42. M. Lacharite, B. Minaud and K. Paterson, “Improved reconstruction attacks on encrypted data using range query leakage,” in IEEE Symp. on Security and Privacy, San Francisco, USA, pp. 297–314, 2018. [Google Scholar]
43. C. A. De and V. Iovino, “jPBC: Java pairing based cryprography,” in IEEE Symp. on Computers and Communication, Kerkyra, Greece, pp. 850–855, 2011. [Google Scholar]
44. B. Huang and S. Liang, “A range search scheme based on encrypted index hiding order and access patterns,” in Int. Conf. on Internet of Things (iThings), Atlanta, USA, pp. 340–347, 2019. [Google Scholar]
45. C. Guo, R. Zhuang, Y. Jie, K. Choo and X. Tang, “Secure range search over encrypted uncertain IoT outsourced data,” IEEE Internet of Things Journal, vol. 6, no. 2, pp. 1520–1529, 2018. [Google Scholar]
46. J. Liang, Z. Qin, S. Xiao, J. Zhang, H. Yin et al., “Privacy-preserving range query over multi-source electronic health records in public clouds,” Journal of Parallel and Distributed Computing, vol. 135, no. 4, pp. 127–139, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |