DOI:10.32604/cmc.2022.019827

| Computers, Materials & Continua DOI:10.32604/cmc.2022.019827 |  |
| Article |
Opto-Video Encryption Based on Logistic Adjusted Sine map in FrFT
1Department of Information Technology, College of Computers and Information Technology, Taif University, P.O. Box 11099, Taif 21944, Saudi Arabia
2Department of Electrical Engineering, Kafrelsheikh University, Kafrelsheikh 61519, Egypt
3Electrical Department, Faculty of Industrial Education, Suez University, Suez 43527, Egypt
4Department of Electronics and Electrical Communication Engineering, Al-Obour High Institute for Engineering and Technology 3036, Egypt
5Department of Computer Science and Engineering, Faculty of Electronic Engineering, Menoufia University, Menouf 32952, Egypt
6Department of Electrical Engineering, Faculty of Engineering, Menoufia University, Shebin El-Kom 32511, Egypt
*Corresponding Author: Osama S. Faragallah. Email: o.salah@tu.edu.sa
Received: 27 April 2021; Accepted: 23 June 2021
Abstract: In the last few years, videos became the most common form of information transmitted over the internet, and a lot of the traffic is confidential and must be protected and delivered safely to its intended users. This introduces the challenges of presenting encryption systems that can encode videos securely and efficiently at the same time. This paper presents an efficient opto-video encryption system using Logistic Adjusted Sine map (LASM) in the Fractional Fourier Transform (FrFT). In the presented opto-video LASM-based FrFT scheme, the encoded video is split into distinct frames and transformed into optical signals utilizing an optical supply. Each of the developed optical video frames is ciphered by utilizing the LASM in optical FrFT system using two-phase modulation forms on the video frame, the first in the time-domain and the second in the FrFT domain. In the end, the ciphervideo frame is spotted utilizing a CCD digital camera and transformed into a digital structure that can be managed using a computer. We test the proposed opto-video LASM-based FrFT scheme using various security tools. The outcomes demonstrate that the presented scheme can effectively encrypt and decrypt video signals. In addition, it encrypts videos with a high level of encryption quality without sacrificing its resistance to noise immunity. Finally, the test outcomes demonstrate that the presented scheme is immune to known attacks.
Keywords: Optical encryption; FrFT; logistic-adjusted sine map
Since the presentation of video cameras in the mid of 19th century, watching movies and videos have become a norm in our daily lives. For instance, we watch movies and films for entertainment and educational purposes. Videos have also been utilized for many other applications, including but not limited to video chatting and conferencing to communicate with people, advertising products and services and playing video games. Videos are considered nowadays the most common form of information transmitted over the internet. Online video traffic had increased from 67% of all internet traffic in 2014 to 80% of all internet traffic in 2019. This increase is due to advancements in internet speeds. A lot of video traffic is confidential and must be kept only for the intended users [1,2]. For instance, video chatting and conferencing can be hacked to obtain secret information. In addition, paid Video on Demand (VoD) services must be kept only for the rightful subscribers. Copyrighted films and videos must be kept safe from tampering or stealing. That is why in many applications encrypting videos while being transmitted over the internet is a must.
Since videos are large, traditional encryption systems are not practically used to encrypt videos. Therefore, we must consider the trade-off between performance and security. To address this issue, many works in encrypting videos had been introduced in the literature. Xu et al. [3] presented an efficient video encryption system. Their system is based on generating a keystream to encrypt videos selectively. This keystream is created using a chaotic pseudo-random number generator (RNG). The experimental outcomes demonstrate that their system is efficient, and it can withstand cryptanalysis attacks.
Fahmeeda et al. [4] presented a computational and time-efficient video encryption system suitable for real-time video applications such as VOD and pay-per-view without affecting security. Their system does not require any special hardware requirements, and the encryption/decryption keys are small and manageable. In their system, the video frames in the videos are twisted by an angle and encrypted using keys created by Faro in an out perfect scrambling algorithm.
Altaf et al. [5] presented a selective video encryption system that considersincreasing security with minimal computational resources. Their system also preserves the video compression and fulfillment to the video format. First, their system compresses the video data in a way the statistical and structural properties are maintained. Then, chaotic maps alter the substation boxes in the advanced encryption standard (AES) [6]. Then the video is encrypted utilizing the altered AES and H.264/AVC [7]. The test results show that their system has reasonably distorted the encrypted video without negatively affecting the video format and compression. Valli et al. [8] proposed two video encryption systems based on chaotic maps. The first is based on a high 12D chaotic map, and the second one is founded on the Ikeda delay differential equation (DDE). To encrypt the videos, the proposed system uses the chaotic maps to scramble the first frame, then the scrambled first frame is then XORed with the second frame, and the result is scrambled using the chaotic map and so on. This technique in encryption is called cipher block chaining (CBC). Their systems are secure against cryptanalysis attacks, but this comes with the cost of not supporting parallel processing. Salamudeen et al. [9] presented a video encryption system that uses spin and element anti-diagonal matrices to encrypt videos. The spin matrix is used to divide the video frame into blocks of pixels, and then the element anti-diagonal matrix is used to encrypt/decrypt these blocks. Their system is computationally efficient and fast, which makes it suitable for online video streaming. In addition, the proposed system effectively degrades the quality of the encrypted video, and it does not rely on the video format. Their system can withstand cryptanalysis attacks. In [10], Xu presented a hybrid encryption/steganographic system used to secure high efficiency video coding (HEVC). Their system is commutative, i.e., the embedded data has no negative effect on decrypting an encrypted video, and the inserted data can be properly recovered from the ciphered video. The HEVC parameters of motion vector difference (MVD) sign, the intra-prediction mode (IPM) and the quantized transform coefficient (QTC) signs are encoded. This results in a huge degradation inthe video quality. The proposed system embeds the data in the QTC, which minimizes the effect of the embedded data on the video. The proposed system allows extracting the embedded data from both the encrypted and decrypted versions of the video. Nalawade et al. [11] introduced a video encryption scheme that is built on the RSA algorithm, named after its inventors Rivest, Lihua et al. [12] and Pseudo Noise (PN). This system is suitable for videos that require a high-security level regardless of the encryption/decryption speeds. Their system is designed to encrypt Audio Video Interleaved (AVI) [13] video format, but it can be easily modified to encrypt Moving Picture Experts Group (MPEG) [14] video format. The frames and the audio of the foundation video file are encrypted twice using the RSA algorithm followed by PN to increase the security level. Khyioon et al. [15] introduced a video encryption method built on the NTRU [16] encryption (an open-source cryptosystem based on the lattice) and chaotic maps. Their system works with various video formats, including AVI, Windows Media Video (WMV), MOV, which is a format for QuickTime and MP4. Their system encrypts videos using the NTRU encryption while decrypts videos using chaotic maps. This allows a high level of security while maintaining a high decryption speed. They implemented their system using visual basic.
Long et al. [17] proposed a hybrid steganographic/encryption system that works for the HEVC video format. The signs of residual coefficients and the amplitudes of motion vector differences are encrypted using RC4 [18] using an encryption key. At the same time, data can be embedded in nonzero AC residual coefficients using a hiding key, which is independent of the encryption key. Their system is separable, i.e., a receiver can decrypt the video with an acceptable quality if he possesses the decryption key but cannot get the hidden data without the hiding key. On the other hand, the receiver can get the inserted data using the hiding key but cannot decrypt the video without the decryption key. Thus, he must have both keys to decrypt the video and extract the inserted data.
The remainder of the paper is sectioned as follows. Section 2 explores the fundamental transform frameworks, including the Logistic-adjusted-Sine map (LASM) and the Fractional Fourier Transform (FrFT). Section 3 presents the opto-video LASM-based FrFT scheme. Section 4 represents the simulation outcomes of the proposed opto-video LASM-based FrFT scheme. Finally, section 5 represents the conclusions of the paper.
2 Fundamental Transform Frameworks
This part presents the two essential components utilized to construct the proposed video encryption system; the Logistic-adjusted-Sine map and the Fractional Fourier Transform (FrFT).
2.1 Logistic Adjusted Sine Map (LASM)
The LASM represents a 2D chaotic mapping that can mix the pixels in a video frame. Its mathematical form is as follows [19,20]:
where μ ∈ [0,1]. The LASM is a mixture of Sine and Logistic maps. Firstly, the logistic equation
2.2 The Fractional Fourier Transform (FrFT)
The FrFT represents a linear alteration thought as a generality of the classical Fourier Transform (FT). Hence, the FrFT is named rotational FT. The FrFT kernel is expressed as follows [21–23]:
The FrFT works by revolving the entered signal in the continuous time-frequency plane anticlockwise from
where
where
3 The Proposed Encryption Mechanism
In the proposed opto-video LASM-based FrFT scheme, the plainvideo frames are split into distinct frames and then transformed to optical signals utilizing an optical source. Each of the developed optical video frames is ciphered by utilizing the LASM in optical FrFT system using two-phase modulation forms; the first in the time-domain and the second in the FrFT domain. Lastly, the video frame is collected and transferred into a digital structure that can be managed via a computer. Therefore, the encryption steps for the presented opto-video LASM-based FrFT scheme can be reviewed as follows:
a) Read the plainvideo bit-streams.
b) Divide the incoming condensed plainvideo bit-streams into separated plainvideo frames.
c) For each plainvideo frame, apply the LASM and the optical FrFT, apply LASM and the inverse of optical FrFT to get the ciphervideo frame.
d) Collect all ciphervideo frames to create the ciphervideo bit-streams.
e) Send the ciphervideo bit-streams via a communication network to the receiver.
In the decryption mechanism of the proposed opto-video LASM-based FrFT scheme, each ciphervideo frame is subjected to the optical FrFT and the inverse of LASM, and then apply the inverse of optical FrFT and again the inverse of LASM to get the plainvideo frame. Finally, the decrypted video frames are accumulated to acquire the plainvideo bit-streams. Therefore, the receiver begins collecting the ciphervideo bit-streams. Thus, the steps of the decoding process for the proposed opto-video LASM-based FrFT scheme can be reviewed as follows:
a) Receive the ciphervideo bit-streams.
b) Divide the incoming ciphervideo bit-streams into separated ciphervideo frames.
c) For each ciphervideo frame, apply the optical FrFT and the inverse of LASM, apply the inverse of optical FrFT and again the inverse of LASM to get the plainvideo frame.
d) Collect all plainvideo frames to produce the recovered plainvideo bit-streams.
We test the proposed opto-video LASM-based FrFT scheme using four samples of different video frames presented in Fig. 1.

Figure 1: Different samples of original video frames
We first visually inspect the encoded and decoded video frames of the proposed opto-video LASM-based FrFT scheme. Then, we test the quality of the encoded video frames utilizing the entropy [24], the correlation coefficient [25], the histogram deviation (
We visually inspect the encrypted and decrypted video frames quality. The visual results are depicted in Tab. 1. From these figures, we can see that the proposed opto-video LASM-based FrFT scheme can conceal the details of the video frames and successfully retrieve back the original frames without any noticeable quality distortion.

We first explain the measurements used to investigate the encryption quality of the presented opto-video LASM-based FrFT scheme, and then we show and discuss the results.
Information entropy is used to measure how much information is in a video frame [24]. It is built on the chances of the existence of every pixel’s value in the video frame. The more the entropy is, the more the chances of every pixel’s value in the video frame are close to each other. Consequently, the more improved is the characteristic of the encoded video frames [24]. The information entropy can be expressed as:
where
An accepted video encryption system must hide any statistical similarity among the video frame and its encoded form. This is essential to avoid any leak of the video frame data. The correlation coefficient is a measurement of the statistical hardiness of encryption systems. A recognized characteristic of video frames is that the neighboring pixels are vastly correlated. An accepted video encryption system should conceal this correlation. The correlation coefficient
where
4.2.3 The Histogram Deviation (
The histogram deviation
where d(i) is the absolute change between the amplitudes at pixel level
4.2.4 The Irregular Deviation (
The video encryption quality can be calculated by finding the
where h(i) is the video frame histogram at level
A vital characteristic of a video encryption system is the diffusion characteristic [28]. A minimal alteration in the video frame before encryption leads to a whole transformation in the encrypted video frame. This is essential for video encryption systems to endure cryptanalysis attacks. Two tools are utilized to measure the diffusion characteristic; the NPCR and the UACI [26]. The
where
The
It can be expressed as [28]:
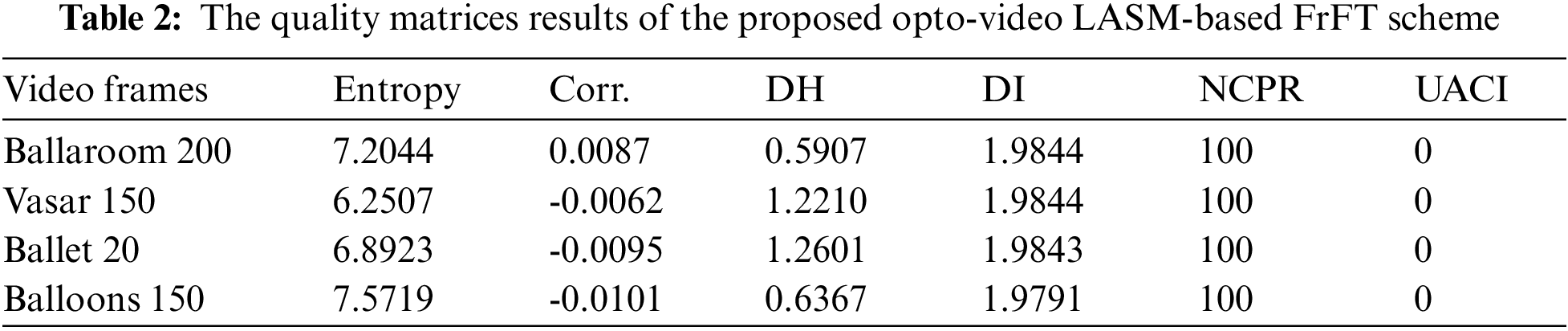
High NPCR and UACI values imply more enhanced encoded video frames quality. The outcomes of the entropy, the correlation coefficients, the histogram deviation (DH), the irregular deviation (DI), NPCR and UACI of the proposed opto-video LASM-based FrFT scheme are listed in Tab. 2.
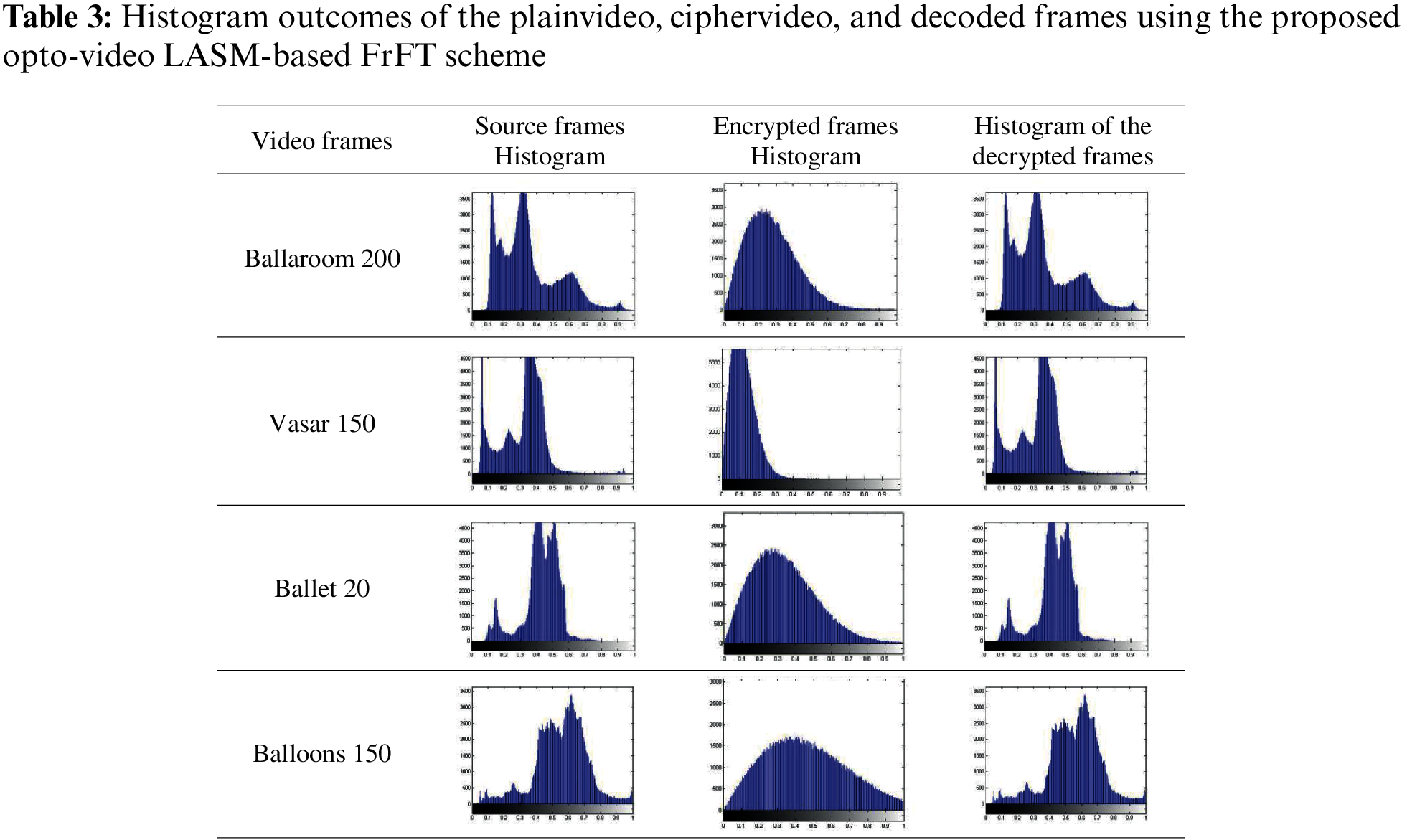
The histogram of a video frame is a plot that demonstrates the relationship among the pixel values and their occurrences in the video frame [29]. The more constant the plot is, the more enhanced is the encrypted video frames quality. Furthermore, the plainvideo and ciphervideo frames histogram must be dissimilar to ensure no statistical information leak about these frames. In addition, the histograms of the decrypted and the original frames must be identical for perfect decryption. The histograms of the plainvideo, ciphervideo, and decoded frames are shown in Tab. 3.
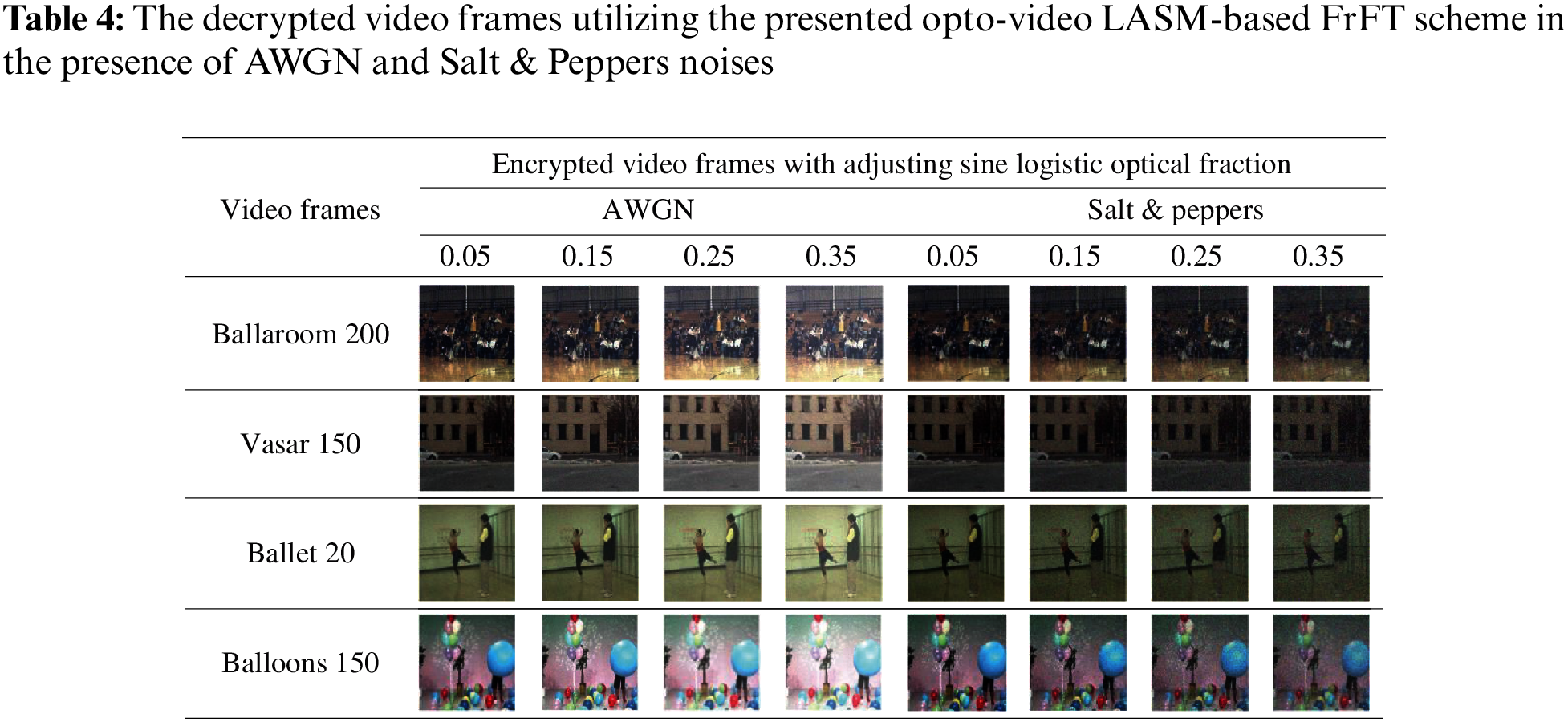
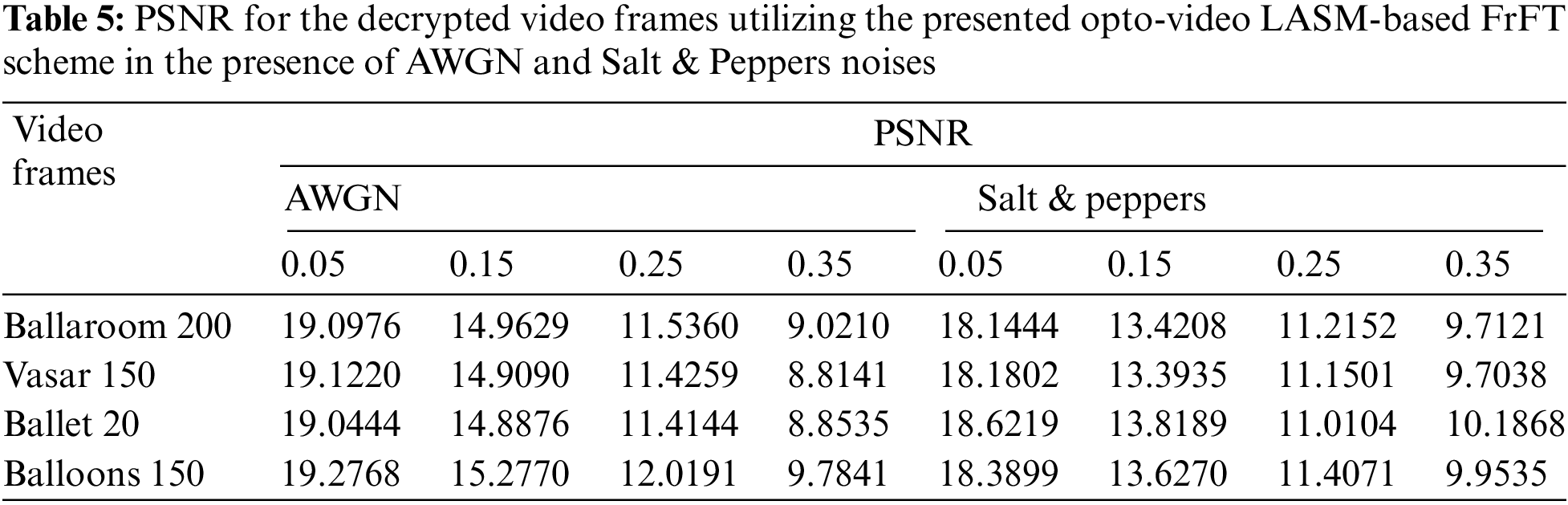
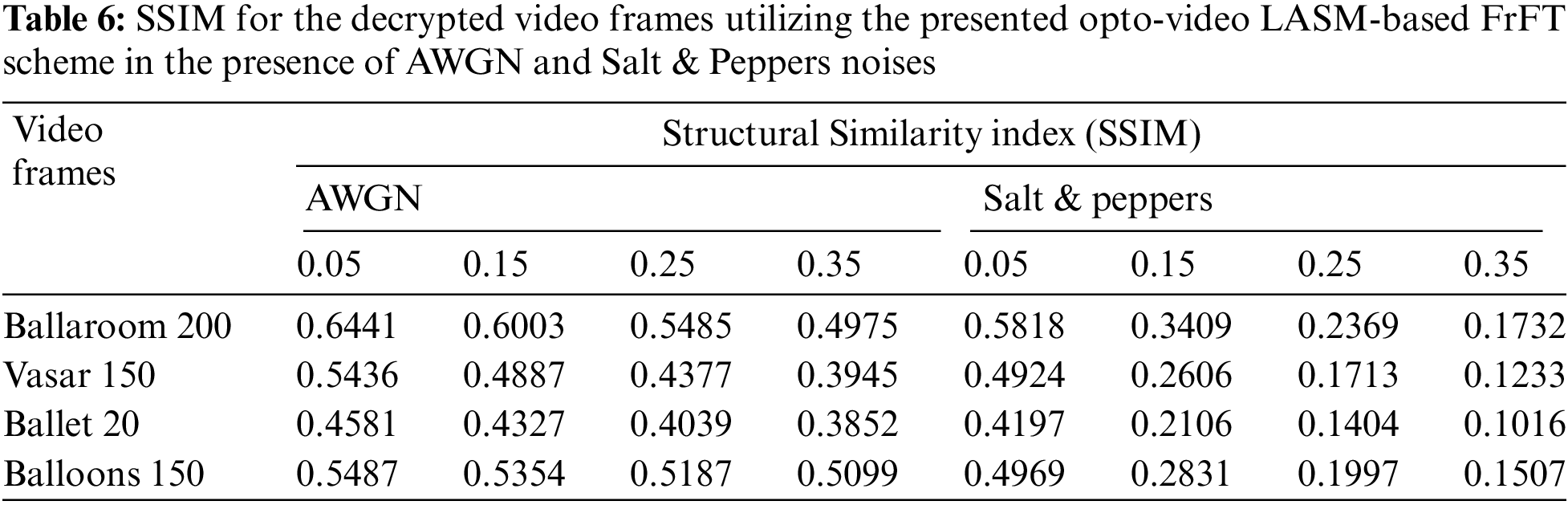
The noise immunity for the proposed opto-video LASM-based FrFT scheme is defined as the capability of the encryption system to successfully decrypt the video frame when it is vulnerable to noise throughout the communication. The noise immunity of the proposed opto-video LASM-based FrFT scheme is verified using the Additive White Gaussian Noise (AWGN) and salt and pepper noise of multiple intensities. After that, we compare the decrypted ciphervideo frame quality. The assessment of the noise immunity is done using visual inspection, the PSNR, the SSIM and the FSIM [30].
The PSNR is the fraction between the maximum pixel value (255 in the case of gray scale frames or
The PSNR can be expressed as [30]:
where
where
The SSIM measures the decrypted video frame quality compared with the original video frame for the structure information, the luminance masking and the contrast masking [30]. The SSIM ranges between 1 and −1 where 1 shows that both video frames are matching. It is expressed as follows [30]:
where
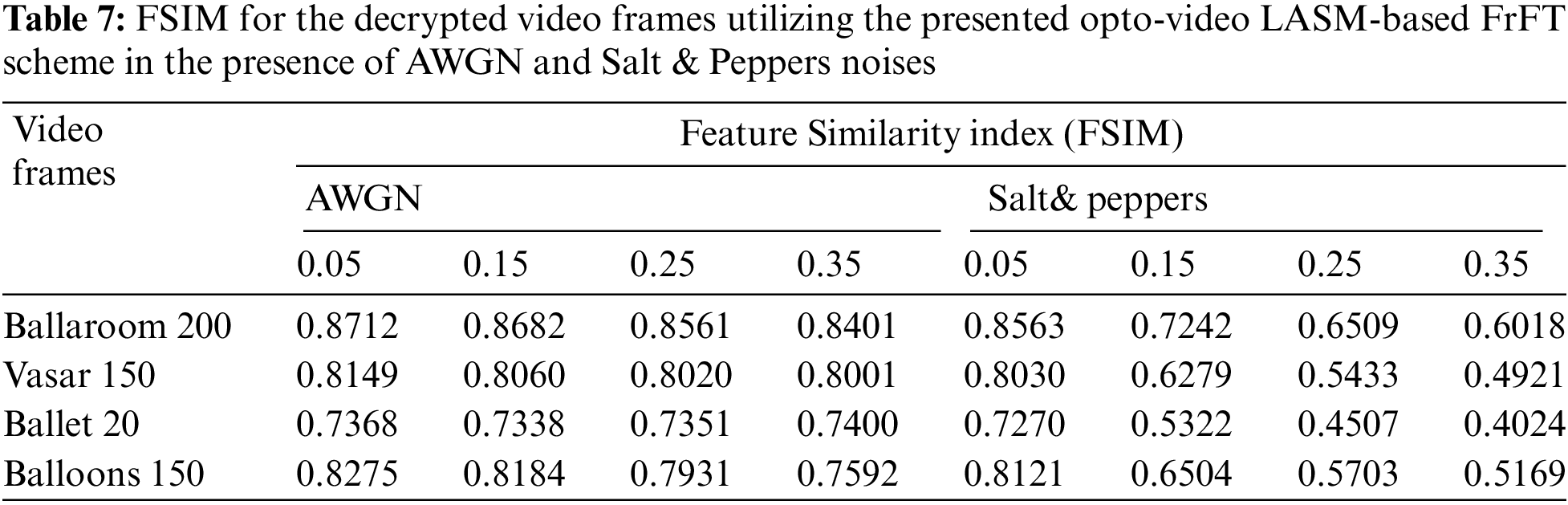
The Feature Similarity Index Method (FSIM) measures the features resemblance of two video frames using two factors; the Phase Congruency (PC) and Gradient Magnitude (GM) [26]. The PC detects the video frame structures in the frequency domain while the GM gets the video frame gradient [30].
Assume two video frames; O for the plainvideo and R for the decrypted ciphervideo frame. The congruency of the decrypted and the original video frames are PC1 and PC2. We also obtain the magnitude gradients G1 and G2 from the decrypted and original video frames correspondingly. The FSIM can be evaluated as follows [30]:
Next, we find the resemblance between both video frames based on G1 and G2 as follows:
where T1, T2 are positive constants.
FSIM of the two video frames can be formulated using
where a and b are the factors of comparative standing between the PC and the MG [30]. The decrypted video frames are shown in Tab. 4. The results of PSNR, SSIM and FSIM among the plainvideo and decrypted ciphervideo frames with AWGN and salt and pepper noises are depicted in Tabs. 5–7.
4.4 Immunity Against Occlusion Attacks
The occlusion attack is an attack that crops the encrypted video frames, and the proposed opto-video LASM-based FrFT scheme can withstand this attack if most of the features can be recovered in the decryption. We test the proposed opto-video LASM-based FrFT scheme by attacking the encrypted video frames with 25% and 50% occlusions and testing the similarity between the original and decrypted video frames. The occlusion attack results for Ballaroom 200 and Vasar video frames illustrated in Tab. 8 prove the immunity of the presented opto-video LASM-based FrFT scheme against the occlusion attack.

This paper presents an efficient and secure opto-video LASM-based FrFT scheme based on LASM and FrFT. In the proposed opto-video LASM-based FrFT scheme, the encoded video frames are split into distinct frames and then transformed from electrical signals to optical signals utilizing an optical supply. Each of the optical video frames is encrypted by utilizing the LASM in the optical FrFT system using two-phase modulation forms; the first in the time-domain and the second in the FrFT domain. In the end, the video frame is captured with a CCD digital camera and transformed into a digital format which can be handled with the computer. We tested the quality of the proposed opto-video LASM-based FrFT scheme using the visual inspection, the entropy, the correlation coefficient, the DH, the DI, the histogram analysis, the NPCR and the UACI. The results showed that the presented opto-video LASM-based FrFT scheme effectively encrypts and decrypts video signals without forfeiting its resistance to noise immunity. In addition, the presented opto-video LASM-based FrFT system was tested for its immunity vs. recognized attacks such as the occlusion attack and the edge detection, and the results showed that its immunity against these types of attacks. To conclude, the proposed opto-video LASM-based FrFT scheme can be used to secure videos transmitted over the internet without sacrificing its efficiency.
Acknowledgement: The authors would like to thank the Deanship of Scientific Research, Taif University Researchers Supporting Project Number (TURSP-2020/08), Taif University, Taif, Saudi Arabia for supporting this research work.
Funding Statement: This study was funded by the Deanship of Scientific Research, Taif University Researchers Supporting Project Number (TURSP-2020/08), Taif University, Taif, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. H. Kwon, H. Yoon and K. Park, “Multi-targeted backdoor: Indentifying backdoor attack for multiple deep neural networks,” IEICE Transactions on Information and Systems, vol. 103, no. 4, pp. 883–887, 2020. [Google Scholar]
2. H. Kwon, Y. Kim, H. Yoon and D. Choi, “Random untargeted adversarial example on deep neural network,” Symmetry, vol. 10, no. 12, pp. 738, 2018. [Google Scholar]
3. H. Xu, X. Tong and X. Meng, “An efficient chaos pseudo-random number generator applied to video encryption,” Optik, vol. 127, no. 20, pp. 9305–9319, 2016. [Google Scholar]
4. S. S. Fahmeeda and D. C. Shubhangi, “Video encryption algorithm and key management using perfect shuffle,” International Journal of Engineering Research and Applications, vol. 7, no. 2, pp. 1–5, 2017. [Google Scholar]
5. M. Altaf, A. Ahmad, F. A. Khan, Z. Uddin and X. Yang, “Computationally efficient selective video encryption with chaos-based block cipher,” Multimedia Tools and Applications, vol. 77, no. 21, pp. 27981–27995, 2018. [Google Scholar]
6. Ç. Unal, S. Kacar, Z. Ahmet and I. Pehlivan, “A novel hybrid encryption algorithm based on chaos and S-AES algorithm,” Nonlinear Dynamics, vol. 92, no. 4, pp. 1745–1759, 2018. [Google Scholar]
7. H. Yuan, C. Guo, J. Liu, X. Wang and S. Kwong, “Motion-homogeneous-based fast transcoding method from H.264/AVC to HEVC,” IEEE Transactions on Multimedia, vol. 19, no. 7, pp. 1416–1430, 2017. [Google Scholar]
8. D. Valli and K. Ganesan, “Chaos based video encryption using maps and Ikeda time delay system,” The European Physical Journal Plus, vol. 132, no. 12, pp. 542, 2017. [Google Scholar]
9. A. Salamudeen, M. M. Iddrisu and M. I. Daabo, “Perceptual video encryption via unit anti-diagonal matrix,” Applied Mathematics and Information Sciences, vol. 12, no. 5, pp. 923–929, 2018. [Google Scholar]
10. D. Xu, “Commutative encryption and data hiding in HEVC video compression,” IEEE Access, vol. 7, pp. 66028–66041, 2019. [Google Scholar]
11. C. V. Nalawade, S. N. Sayyad and P. S. Sutar, “Dual-layer video encryption and decryption using RSA algorithm,” International Journal of Innovative Research in Computer and Communication Engineering, vol. 116, no. 1, pp. 33–40, 2017. [Google Scholar]
12. G. Lihua, Q. Kaide, D. Chengzhi and Z. Nanrun, “An optical 3DV frame compression and encryption scheme based on compressive sensing and RSA algorithm,” Optics and Lasers in Engineering, vol. 121, pp. 169–180, 2019. [Google Scholar]
13. Y. Yang, Z. Xu, L. Liu and G. Sun, “A security carving approach for AVI video based on frame size and index,” Multimedia Tools and Applications, vol. 76, no. 3, pp. 3293–3312, 2017. [Google Scholar]
14. N. Barman and M. G. Martini, “H.264/MPEG-AVC, H.265/MPEG-HEVC and VP9 codec comparison for live gaming video streaming,” in IEEE Ninth Int. Conf. on Quality of Multimedia Experience (QoMEX), Erfurt, Germany, pp. 1–6, 2017. [Google Scholar]
15. Z. Khyioon, A. R. T. Shawe, S. A. Hussein, F. N. Abbas and A. K. Ridha, “Encryption video using NTRU and chaotic algorithms,” Journal of Southwest Jiaotong University, vol. 54, no. 6, pp. 1–7, 2019. [Google Scholar]
16. A. Martin, S. Bai and L. Ducas, “A subfield lattice attack on overstretched NTRU assumptions,” Annual International Cryptology Conference, vol. 9814, pp. 153–178, 2016. [Google Scholar]
17. M. Long, F. Peng and H. Li, “Separable reversible data hiding and encryption for HEVC video,” Journal of Real-Time Image Processing, vol. 14, no. 1, pp. 171–182, 2018. [Google Scholar]
18. M. H. Abood, “An efficient 3DV frame cryptography using hash-LSB steganography with RC4 and pixel shuffling encryption algorithms,” in Annual Conf. on New Trends in Information & Communications Technology Applications (NTICT), Baghdad, Iraq, pp. 86–90, 2017. [Google Scholar]
19. O. S. Faragallah and H. S. El-Sayed, “Secure opto-audio cryptosystem using XORing mask and hartley transform,” IEEE Access, vol. 9, pp. 25437–25449, 2021. [Google Scholar]
20. Z. Hua and Y. Zhou, “Image encryption using 2D logistic-adjusted-Sine map,” Information Sciences, vol. 339, no. 8, pp. 237–253, 2016. [Google Scholar]
21. O. S. Faragallah, A. Afifi, W. El-Shafai, H. S. El-sayed, E. A. Naeem et al., “Investigation of chaotic image encryption in spatial and FrFT domains for cybersecurity applications,” IEEE Access, vol. 8, pp. 42491–42503, 2020. [Google Scholar]
22. O. S. Faragallah, H. S. El-sayed, A. Afifi and W. El-Shafai, “Efficient and secure opto-cryptosystem for color images using 2D logistic-based fractional Fourier transform,” Optics and Lasers in Engineering, vol. 137, no. 6, pp. 106333, 2021. [Google Scholar]
23. O. S. Faragallah, M. A. AlZain, H. S. El-sayed, J. F. Al-Amri, W. El-Shafai et al., “Secure color image cryptosystem based on chaotic logistic in the FrFT domain,” Multimedia Tools and Applications, vol. 79, no. 3, pp. 2495–2519, 2020. [Google Scholar]
24. O. S. Faragallah, A. I. Sallam and H. S. El-Sayed, “Utilization of HEVC ChaCha20-based selective encryption for secure telehealth video conferencing,” Computers, Materials & Continua, vol. 7, pp. 831–845, 2021. [Google Scholar]
25. O. S. Faragallah, A. I. Sallam and H. S. El-Sayed, “Visual protection using RC5 selective encryption in telemedicine,” Intelligent Automation & Soft Computing, vol. 31, pp. 177–190, 2021. [Google Scholar]
26. A. Sallam, E. EL-Rabaie and O. S. Faragallah, “CABAC-based selective encryption for HEVC using RC6 in different operation modes,” Journal of Multimedia Tools and Applications, vol. 77, no. 21, pp. 28395–28416, 2018. [Google Scholar]
27. O. S. Faragallah, H. S. El-sayed, A. Afifi and S. F. El-Zoghdy, “Small details gray scale image encryption using RC6 block cipher,” Wireless Personal Communications, vol. 118, no. 2, pp. 1559–1589, 2021. [Google Scholar]
28. A. Sallam, E. EL-Rabaie and O. S. Faragallah, “HEVC selective encryption using RC6 block cipher technique,” IEEE Transactions on Multimedia, vol. 20, no. 7, pp. 1636–1644, 2018. [Google Scholar]
29. O. S. Faragallah, A. Afifi, W. El-Shafai, H. S. El-sayed, M. A. AlZain et al., “Efficiently encrypting color images with few details based on RC6 and different operation modes for cybersecurity applications,” IEEE Access, vol. 8, pp. 103200–103218, 2020. [Google Scholar]
30. O. S. Faragallah, A. Afifi, I. F. Elashry, E. A. Naeem, H. M. El-Hoseny et al., “Efficient optical double image cryptosystem using chaotic mapping-based Fresnel transform,” Optical and Quantum Electronics, vol. 53, no. 305, pp. 1–26, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |