DOI:10.32604/cmc.2022.023052

| Computers, Materials & Continua DOI:10.32604/cmc.2022.023052 |  |
| Article |
Hybrid Machine Learning Model for Face Recognition Using SVM
1IES College of Technology, Bhopal, 462044, India
2Maulana Azad National Institute of Technology, Bhopal, 462003, India
3Department of Information Technology, Manipal University Jaipur, Jaipur, 303007, India
4Department of Computer and Communication Engineering, Manipal University Jaipur, Jaipur, 303007, India
5Department of Software Engineering, College of Computer Science and Engineering, University of Jeddah, Jeddah, 23218, Saudi Arabia
*Corresponding Author: Punit Gupta. Email: punitg07@gmail.com
Received: 26 August 2021; Accepted: 28 December 2021
Abstract: Face recognition systems have enhanced human-computer interactions in the last ten years. However, the literature reveals that current techniques used for identifying or verifying faces are not immune to limitations. Principal Component Analysis-Support Vector Machine (PCA-SVM) and Principal Component Analysis-Artificial Neural Network (PCA-ANN) are among the relatively recent and powerful face analysis techniques. Compared to PCA-ANN, PCA-SVM has demonstrated generalization capabilities in many tasks, including the ability to recognize objects with small or large data samples. Apart from requiring a minimal number of parameters in face detection, PCA-SVM minimizes generalization errors and avoids overfitting problems better than PCA-ANN. PCA-SVM, however, is ineffective and inefficient in detecting human faces in cases in which there is poor lighting, long hair, or items covering the subject's face. This study proposes a novel PCA-SVM-based model to overcome the recognition problem of PCA-ANN and enhance face detection. The experimental results indicate that the proposed model provides a better face recognition outcome than PCA-SVM.
Keywords: Face recognition system (FRS); face identification; SVM; discrete cosine transform (DCT); artificial neural network (ANN); machine learning
The past decade has seen a rise in the use of computer and information technologies. This rapid development has spawned the growth of identity identification techniques. Whether in the fields of finance, manufacturing, e-commerce, education, transportation, or energy, accurate user identification is needed to ensure that users can access the Internet while protecting their data and preventing privacy intrusion. Face recognition technology has received the most significant research attention among the biometric technologies available today. From the US, UK, EU to China, face recognition systems (FRSs) have been used in various capacities to identify criminals, maintain social vigilance, and discourage terrorist activities in society. Organizations like Apple, Facebook, Amazon, Alphabet, and the Federal Bureau of Investigation use FRSs for authentications, identifications, and searching information from a database. The need for FRSs for reconnaissance in markets, railways, banks, and other public spaces has been strengthened by the development of smart cities, e-government, e-administration, and Internet-of-Things. By installing FRSs in cities and communities, security experts believe that law enforcement authorities can easily prevent crimes and arrest individuals aiding and abetting illegal activities. This belief stems from the fact that FRSs can identify human faces in a wide domain of circumstances with high precision [1–3].
Despite the advantages of FRSs for criminal identification, they have many setbacks. Individuals with similar facial features, for instance, could be profiled by FRSs to have the same face. This error is a huge concern because innocent individuals whose faces are similar to individuals who committed a crime could be erroneously labelled as criminals. It is not clear who should be held responsible for the mistakes made by facial recognition technology. The use of FRSs can also result in threats to privacy, data thefts, and violation of rights. Armed with facial recognition techniques, companies can influence consumers’ buying decisions based on their historical facial preferences [4–8]. The US, China, and India are at the forefront of face recognition technology [9,10]. Some government agencies in these nations are employing FRSs to profile citizens based on tribe, race, religion, or beliefs. In China, for instance, face recognition algorithms are trained to identify and distinguish faces of Uyghur people from those of other ethnic groups. For facial recognition technology to succeed, these drawbacks need to be addressed.
The success of facial recognition technology relies on its ability to detect and recognize faces accurately. Face detection is an essential component of FRSs, and it can be divided into four methods: appearance-based, template-matching, feature-invariant, and knowledge-based methods. These methods are employed by security experts in detecting faces. In contrast to face recognition, two stages are required in face recognition. They include the training process and evaluation process. In the training process, FRSs are fed with samples of images to be learned, and a unique pattern for each image is obtained. In the evaluation process, a newly created model of image datasets is developed and compared with all existing models in the database. This comparison of models is enhanced using facial recognition algorithms such as Principal Component Analysis (PCA), Independent Component Analysis (ICA), Elastic Matching, and Support Vector Machine (SVM). The task of facial recognition algorithms is to distinguish face highlights by extracting significant points from the subject's face. For instance, an algorithm may break down the relative position of the faces, including the eyes, nose, cheekbones, and jaw. The coordinates of these parts are then used to find completely different photos with coordinative elements. Today's algorithms can normalize face images and modify them on another plane to separate the elements. With feature extraction methods, researchers can even reduce the facial elements required to recognize a subject from a large pool of individuals [11–15].
FRS is extremely significant in our life because the pictures give better security to think about that content. The pictures are intense instruments for viable and secure data. Data is assisting us with making better choices [16–20]. Therefore, these strategies can be utilized as a security reason for some developing fields. With the headway in the learning of face acknowledgement, biometric has turned into a rising innovation for perceiving people. Biometric [2] is a mechanized acknowledgement arrangement of individuals, which depends on physiological or behavioural qualities. The biometric framework incorporates acknowledgement of unique fingerprint, face, iris, retina, hand geometry, voice, mark, and others. In this manner, it is clear that face recognition has been utilized to a more prominent degree lately, and much accentuation is being put on further research and imaginativeness.
Among one of the best settled biometric procedures that fall under the umbrella of biometrics is FRS. It will be acknowledged all the more broadly later on because it's less difficult to set up and utilize furthermore getting less expensive. In the early 1960s [21–23], in the United States (US), open feature reconnaissance was brought into the private division and used essentially by banks. In the following decade, it was broadly spread in spots, for example, doctor's facilities and comfort stores. Be that as it may, utilization of this innovation was restricted because the remote observing of the feature was generally occupied, and the nature of film and cameras frequently brought about foggy pictures. In the 1980s, another headway has been done included things, for example, zoom lenses and advanced innovation. This permitted camera to gather unmistakable, distinctive pictures without much lighting. With the capacities’ development of the camera, the FRS converges with biometric innovation. Once, the defence department of the United States [24] was attempting to discover an innovation that can check hoodlums at the outskirt crossing. Right now, specialists additionally need to take a shot at facial acknowledgement with the state of the budgetary backing from the defence department of the United States. Inevitably, organizations started commercializing the innovation in the mid of 1990s. This innovation stood out as truly newsworthy in February 2001 right away, it was initially utilized as a part of open at Super Bowl XXXV in Tampa by the powers to hunt down criminals and terrorists among a horde of 100,000 onlookers. Quickly, the frameworks are additionally introduced and utilized as a part of Tampa's Ybor City, a seaside town, and some different places, for example, in the city of Virginia shoreline to search for criminal suspects and missing kids and others.
In 2001, the FRS [25–30] was utilized for observation at Tampa, Florida and Newham, Great Britain. Trials of the frameworks yielded poor results. The Newham framework didn't bring about a solitary capture being made in three years. Logan Airport, in Boston, performed two trials of face recognition frameworks. The framework accomplished just 61.7% accuracy [31–33]. The Australian traditions revealed its Smart Gate framework to robotize checking countenances with identification photographs in 2004. Google is trying face recognition utilizing a shrouded element as a part of its picture-looking site. Google bought a personal computer (PC) vision organization Neven Vision in 2006 and there were arrangements to actualize its innovation into its Picasa photograph programming. At the present, the Aadhar Card has assembled at most 50% of the number of inhabitants in India till October 2015. The project was propelled in 2009. The focal target is to give general character to each Indian inhabitant. On the other hand, in the early phase of induction, subjects languished a bundle of confusion over occasion specialized obstacles, inaccurate information showed furthermore the noteworthiness of Aadhaar card was indistinct. These days, a significant number of the issues are resolved. Presently, people, in general, can get the card without hardly lifting a finger as its acknowledgement is a necessary record [34–36]. The administration needs to include it with Permanent Account Number (PAN), and Voter ID card to make a protected recognizable proof. It has officially connected on account of LPG-sponsored gas administrations, managing an account as Know Your Customer (KYC) for a secure character. In, Pradhan Mantri Jan Dhan Yojana (PMJDY) acknowledges an Aadhaar card number as the main report adequate to open the ledger. The Indian government has started a computerized locker framework for everyone putting away every single private certification on the administration's server. The proposition visa in 10 days, month-to-month benefits and provident trust are likewise all the while [37–39]. The system for counting people on public transport was discussed in 2018 by Patricia Chato and Nancy Velasco. Single-camera processing of camcorder videos is used to perform an algorithm to identify and count people using artificial neural networking (ANNs). The system is based on a single camera [40]. In [41] author has proposed a deep learning-based model for image classification. In 2021, Lingxiao Zhang was introduced to Zhiping Wang and Zhang concerning image classification using deep learning discussed multi-level neural network-based feature extraction and analytics algorithm. The project focused particularly on the multi-level neural network with the introduction of the extraction feature pipeline [42]. In 2020, Youhui Tian discussed the neural network for the imaging process and established a dual optimization model to optimize the convergence process and the complete connection process in an integrated way [43]. Some other related work trying to optimize the problem is also referred to using fuzzy logic [44] and evolutionary models [45].
Nevertheless, these face recognition techniques cannot perform well in constrained conditions. Principal Component Analysis-Support Vector Machine (PCA-SVM) has demonstrated generalization capabilities in many tasks, including the ability to recognize objects with small or large data samples compared to Principal Component Analysis-Artificial Neural Network (PCA-ANN). However, PCA-SVM is ineffective and inefficient in detecting human faces in cases in which there is poor lighting, long hair, or items covering the subject's face. Some scholars have emphasized the use of feature extraction techniques, while others have proposed improvements in the classification stage. The eigenfaces method is the most prominent research work in face recognition analysis, and research has been conducted on Gabor wavelets to improve the extraction of human facial features. However, these methods still can reduce the accuracy of face recognition. This paper, therefore, proposes a model of face recognition that trains datasets, extracts face features using DCT, and classifies face data using SVM. The knowledge of this research is important to the research community and forward-thinking organizations as it provides insights into the use of modified PCA-Genetic Kernel SVM for face detection.
Face recognition is a key piece of our lives. It is the essential means by which individuals distinguish one another thus it is characteristic to endeavor to instruct PC's to do likewise. The uses of computerized face recognition are various, for example, from biometric confirmation, observation to feature database indexing and seeking. Our consideration is on biometric confirmation. At present, a few techniques are available to accomplish face acknowledgement, for example, primarily based on histograms, the multi-resolution approach, the information theory approach, and the Eigenface approach. Fig. 1 gives a thought regarding the procedure of enlistment, verification and identification of face pictures. Face recognition [7] by machine is essentially a picture investigation issue and is done either by verification or identifications pieces of proof. In verification, we think about a face against an arrangement of countenances. In identification, a face is analyzed against every face in databases. Theoretically, FRS comprises principally three distinct stages.
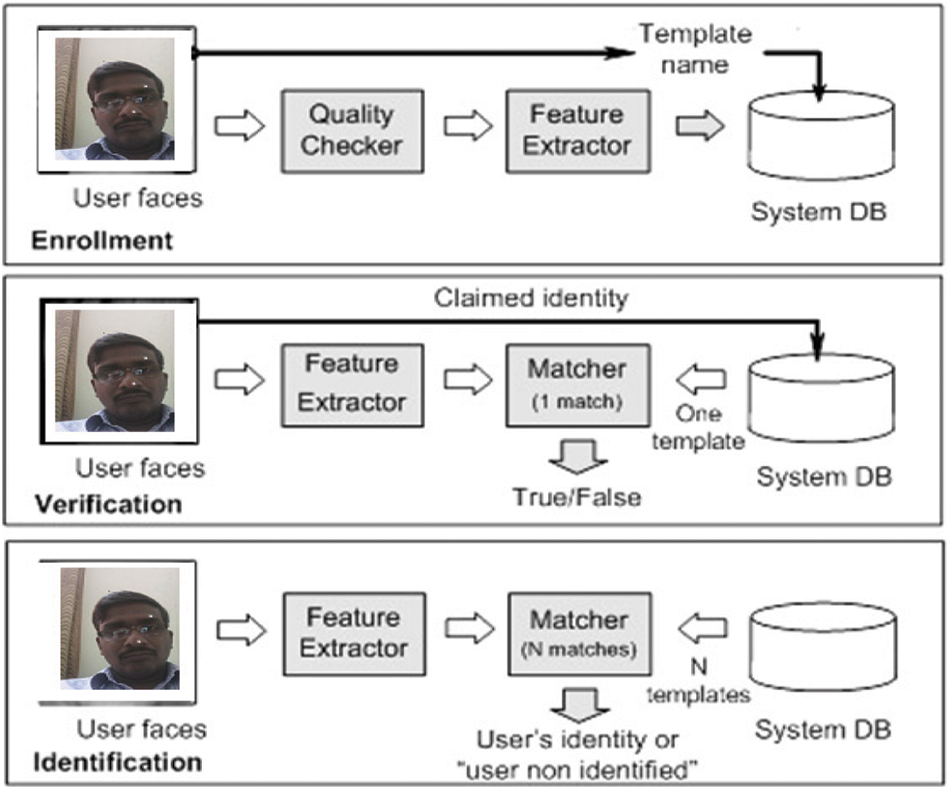
Figure 1: Idea about the FRS
Fig. 2 gives a thought regarding the phase of a generic model of FRS. In the first stage, concentrate features from face pictures utilizing detection procedure. In the second stage, apply the learning algorithm to train the framework. Resulting in training, referred to the instance is given as information for recognition. The classifier doles out the mark accurately if elements are coordinated. Otherwise, it is needed as an erroneous characterization and suggests that more input is obliged to train the classifier.
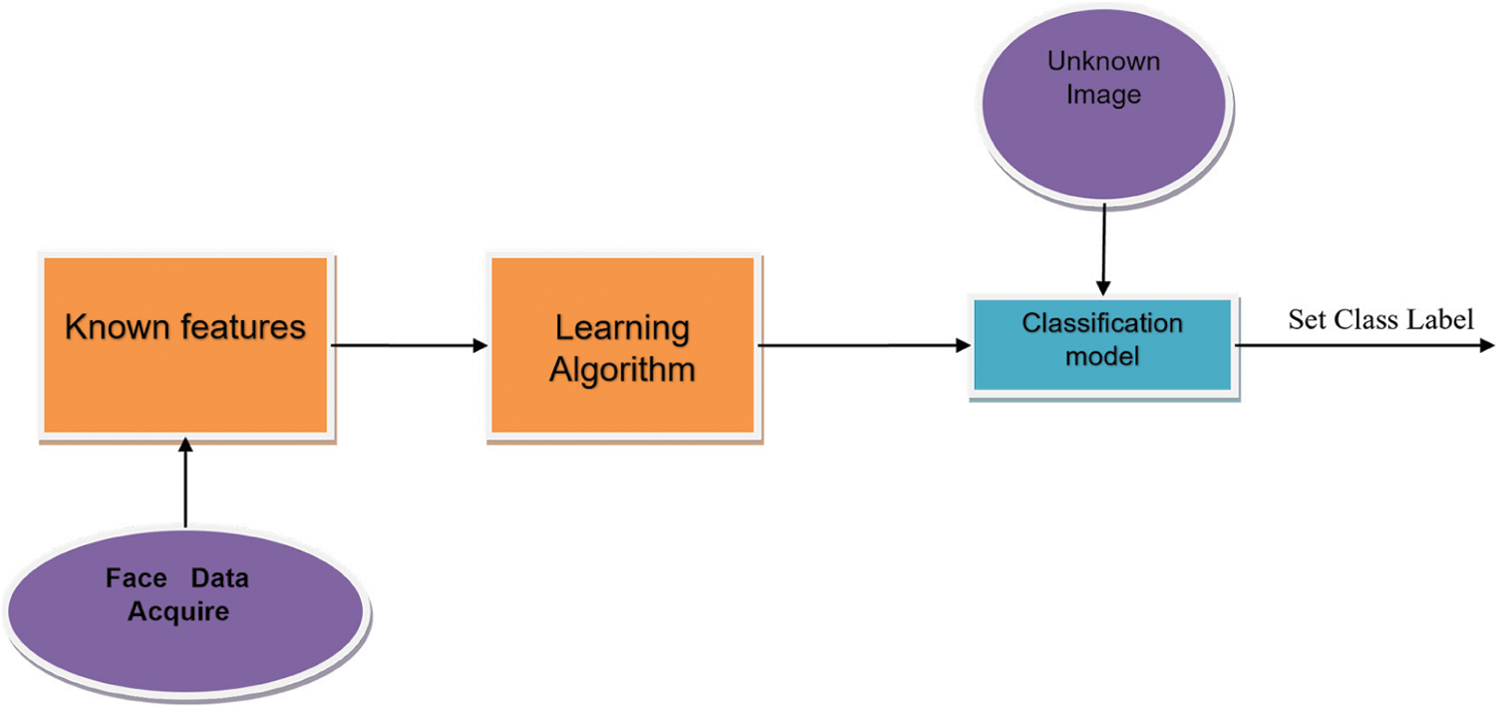
Figure 2: Generic model of FRS
1.3 Framework of a Reorganized FRS
The study in programmed face recognition has been done after the 1960s. This issue is still essentially unsettled. Current years have seen real advances around the inferable from advances in face recognition techniques. The strategy that has been produced for dependable face recognition still proposes an excellent test to computer vision canvases. The different reason has expanded the enthusiasm for face recognition. It comprises public concern toward security, the requirement for identity and verification in the advanced world, the requirement for face analysis methods and a few others.
In the early stage, face affirmation is finished by the simple technique of geometric algorithmic models. At present, the verification way has formed into an exploratory improvement of troublesome geometric representation and indistinguishable procedure. As of late, the advances have upgraded FRS into a lively centre. Researchers are experiencing solid examination on discovering FRS for more extensive territory data, for example, a factual base procedure of feature extraction and classification strategies. We have checked the face recognition in different lighting conditions and areas. Preprocessing, image detection, feature extraction and face recognition are the routines utilized for FRS. In this way, a commonplace FRS contains a sensor to recognize the face picture. A preprocessing component is utilized for improving inputs for feature extraction steps. This stride reduced the span of features. The learning algorithms are utilized to prepare the framework. Succeeding in training performs order to characterize the elements. Later than characterization, we might likewise utilize post-processing strategies to assess the consequences of the framework. For the most part, classification methods are utilized in post-processing.
In Fig. 3, the system is used to speak to in five stages. Firstly, detection may be characterized as obtaining a specimen in which a sensor is obliged to catch an optical picture, then changing over it, into a computerized picture. The second system is preprocessing, which standardized a picture called. The third procedure is feature extraction, where elements are removed from appearances. In fourth, learning provides training to the framework. The fifth procedure is classification, the procedure of masterminding information in gatherings or class as per comparability in attributes is called classification (characterization). At long last, output speaks to yield in a specific structure and the process is called post-processing. As of now, different scrutinies are introducing diverse sorts of face recognition frameworks. Some are offered with change and others through extension. To convey another framework, we have to think about the sorts of FRS.
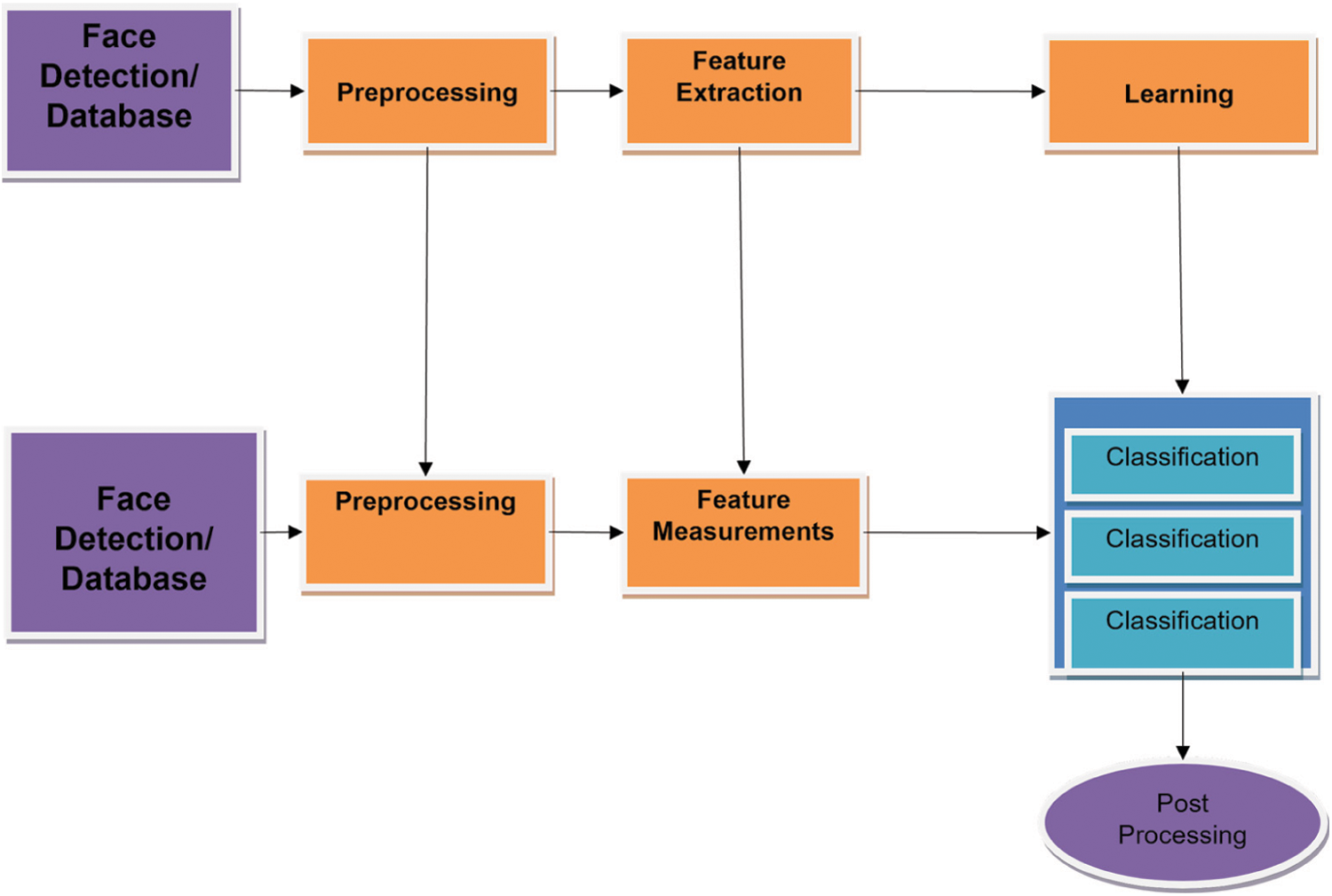
Figure 3: Reorganized FRS
The execution of FRS is influenced by diverse variables, however, in every one of them the feature extraction and classification are the root elements.
Feature extraction is the procedure of characterizing an arrangement of picture qualities, which will most effectively or seriously speak to the data that is essential for investigation and characterization. The objective of feature extraction is to enhance the viability and effectiveness of investigation and arrangement. This may be finished by disposing of repetition in the picture information, taking out variability in the picture information that is of little or no quality in grouping notwithstanding tossing whole pictures if that is fitting, rebuilding the information (in feature space) to improve the classifier's execution, removing spatial data (texture, size, shape) which is pivotal to target distinguishing proof. That is, one might want to minimize the number of components and augment design separation.
In FRS the normal for face elements considers as variation in illumination, poses, expressions, background, and occultation, RTS (Rotation, Scaling and interpretation). The given underneath Tab. 1 illuminate the elements that influence feature extraction ventures of FRS. A few systems of surely understand for feature extraction as mean, standard deviation, kurtosis, histogram, PCA, Independent Component Analysis (ICA) and Linear Discriminant Analysis (LDA).

A face recognition method is the blend of algorithms that includes distinctive strides of the FRS. Since classification is the most vital stride in all strides, hence the classification of face recognition procedures relies on the classifier name. Be that as it may, more often than not, the classifier name is called a face recognition strategy. To build up the classifiers’ consensus, it needs to assess a differing arrangement of expressions, lighting conditions, and subjects. The classification forces of a classifier are expanded utilizing a few changes or augmentation as a part of the existing order algorithm of the classifier. Usually, the methodology used as a district of the configuration of FRS has been to tentatively look into the execution of some classifiers keeping in mind the top goal to decide on the most effective one. Some samples of classifiers are K-neighbors, theorem classifier, PCA, ANN, and SVM. On the opposite hand, a choice methodology visible of consolidating varied classifiers has developed. This technique goes below completely different names, for example, multiple classifier frameworks or committees or ensembles of the classifier. This method is to a fault unpredictable could also be experiencing lower execution.
Face recognition is matched application that consequently recognizes or checks an individual from an advanced picture. In check, the framework looks like a face against a bunch of appearances while in recognizable proof a face is analyzed against each face in information bases. The image recognition framework takes a shot at the base of summed-up advances. Right off the bat distinguishing or choosing improved the countenances. A short time later, makes two arrangements of faces, one of them is preparing the set and another is trying the set. Concentrate the highlights and prepare them with a suitable classifier. At long last, contrast the prepared highlights with the highlights of the test picture and note down the results.
Appearances are distinguished in genuine words or chosen from a setup information base. The framework chips away at two stages, preparing and testing. In preparing, the framework extricates the highlights from appearances of the preparing set. Two sorts of highlight extraction procedures, the spatial area and recurrence space are in patterns. Face acknowledgement is a constant application and thus, it requires quicker calculation. The recurrence area holds the key to the speed and straight forwardness of tasks that are the necessity of quicker calculation. In the spatial area, the estimation of the pixels of the picture change regarding the scene. Though, in the recurrence area, it is treated with the rate at which the pixel esteems are evolving. Spatial space isn't given a lot of data about a face image. Face picture is first changed from spatial area to recurrence area. Different fundamental change methods are utilized, for example, Discrete Wavelet Transformation (DWT) and DCT. DCT [9] is utilized for highlight extraction because of its information compaction property. 2-D DCT is considered as distinct administrator premise work for 8*8 pixels are appeared in condition [1].
2-D DCT is given as with assumption that the data array has finite rectangular support on
for
Where the most elevated frequencies happen at the most elevated indices. Where X is a genuine esteemed sign, in the wake of separating the highlights, a framework prepared these highlights utilizing fitting classifiers. Order strategies are classified into three different ways: measurable, non-factual and hybrid. It is hard to recognize the right element for the acknowledgement of the item. The detailing of highlight vectors utilizing measurable and non-factual methods is hard to arrange the non-distinct highlights. Consequently, cross-breed methods with a blend of measurement and non-static strategies are utilized for acknowledgement, regardless of whether neural network (NN) organization is one of them. NN is a famous strategy utilized for mixture order. As per the study, SVM is more worthwhile than ANN because of its liner or non-direct applicability. SVM takes a shot at the high dimensional element space of double plan terms of the kernel. SVM is utilized as an enormous edge portion-based classifier. It is determined ideal hyperplanes augment the edge between classes. The classification of sample X is given by Eq. (3) of SVM.
Where K is the portion work, xi is the preparation tests and yi (−1, +1) their class names, αi and b is the boundary of the model in the wake of preparing in testing stage extricate the feature from countenances of testing set and look at it from prepared highlights. Thereafter, measures the exhibition of FRS. Taking into account current realities, FRS doesn't work well to consolidate helpless lighting, conceals, long hair, or various articles decently covering the subject's face, and low goal pictures. These requirements give low exactness and more prominent preparing time. Since FRS contains two fundamental advances feature extraction and grouping. The element extractor is answerable for the right and decreased type of info highlight. Classifiers are mindful to prepare and think about the highlights. Subsequently, the blend of feature extractor and classifier are the foundation of FRS. To make a productive FRS, it is required to evaluate the blend of spines contended that DCT as feature extractor and SVM as Classifier.
The greatest issue in face recognition is to streamline the boundaries of a portion of SVM. The exploration is utilized the radial basis function part. It is a decent heuristic to discover the arrangement and the radial basis function piece takes just one information boundary. Another central explanation, when the face order of face information is intricate and the hyperplane follows as a circle then it very well may be utilized. Along these lines, it is utilized. The kernel of the radial basis function is defined as Eq. (4).
Where
In face recognition structure wellness work is described from different perspectives. For instance, the exactness of ID, number of parts and highlight cost be the three rules used to layout a wellness work in face recognition. By making a solitary target wellness work that joins these three destinations into one. Each segment has a substitute component that incurred significant damage in the dataset. If we don't have the included incurred significant damage information, the cost can be set to some consistent regard, for example, 1 or another number. The chromosomes with the most amazing wellness esteem have a high probability to be secured for the following time.
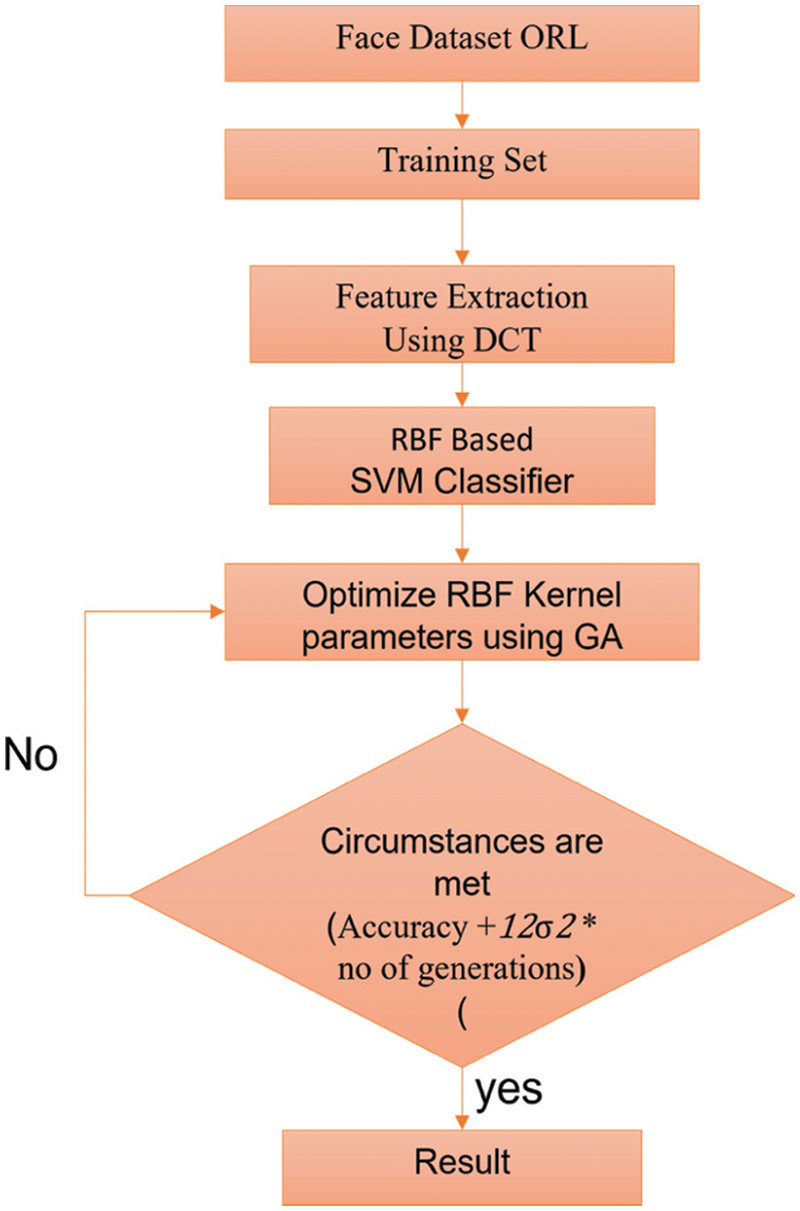
Figure 4: Planned representation of the model
A framework of wellness capacities is given as f= accuracy +
3 Experimental Results and Analysis
The example frontal face pictures have been taken from the AT&T (ORL) information base for the investigation reason. The information base contains ten unique pictures of every one of 40 unmistakable subjects. All the pictures were taken in the same lighting condition with the subjects in an upstanding frontal position. Each picture is of size 112 * 92 pixels. For the trial assessment, scarcely any boundaries were fixed as square size as 8. The resilience, populace size, Maximum age, Maximum time, Minimum sigma and most extreme sigma were set as 0.1, 16, 100, 20, 0.05, and 1 individually. All these were set with standard qualities dependent on the most recent examination results.
Tab. 2 is exhibiting the trial estemates on the ORL information base for the proposed model. The trials were done on the quantity of faces 10, 15, 20, 30, and 40. Six examples of each picture were utilized in all investigations. Test 4 discovered 98.67% precision that is better in all other analyses on 180 pictures. It discovered 3.5212 s training time that is more noteworthy than others. It additionally noticed that .0012 s low testing time in performed tests. It is noted here expanding of the number of faces exactness rate is high however training time expanded. Although testing time is decreasing. Relatively, expiring of testing time makes a degree to decreasing the all-out classification time.

Examine the planned algorithm, we have been contrasted and left approaches PCA-SVM and MODIFIED PCA-GENETIC KERNEL SVM. Five examinations were performed on recently characterized boundaries in the proposed model. Tab. 3 is being showing the exploratory estimations of proficiency boundaries on the ORL information base for past models PCA-SVM, PCA-KGSVM. The most elevated precision for the PCA-SVM blend was discovered 93.33% in experiment no 3. The least training time was found in experiment No 2. For the mix, MODIFIED PCA-GENETIC KERNEL SVM, 98.83% exactness was found in experiment no5. Training time was discovered at 2.3121 s in trial no2. It is noted here expanding of the number of faces accuracy rate is high however training time expanded for this situation moreover. Although, testing time is decreasing. Similarly, expiring of testing time makes a degree to decreasing the total classification time. For a better examination of the planned model with the existing one, we can draw the diagrams of exactness, training time and order time as for the number of appearances. Figs. 5–7 are shown the near examination.

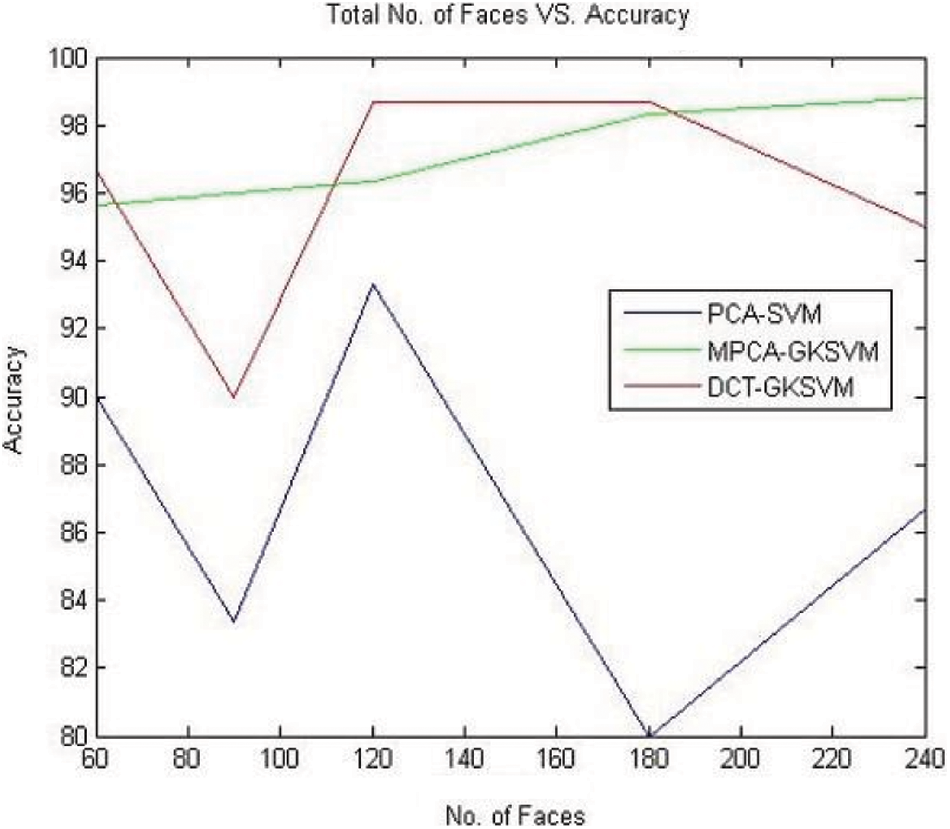
Figure 5: Total number of faces vs. accuracy
Fig. 6. is speaking to a relative chart that is drawn between the number of countenances and precision. The normal exactness of DCT-GENETIC KERNEL SVM is relatively high to the blend PCA-SVM and MODIFIED PCA-GENETIC KERNEL SVM. Even though, the fifth path of MODIFIED PCA-GENETIC KERNEL SVM has discovered 98.83% accuracy that is greatest if MODIFIED PCA-GENETIC KERNEL SVM. Fig. 7 is speaking to a near diagram that indicated the training time relating the number of countenances. The DCT-GENETIC KERNEL SVM is taken less training time relative to PCA-SVM and PCA-GENETIC KERNEL SVM. Fig. 7 is speaking to a relative chart that investigation done among three in the particulars of complete classification time. The DCT GENETIC KERNEL SVM is taken less classification time. Remembering the ultimate objective to additional outline the viability of the proposed, we are made assessments with direct PCA-SVM and MODIFIED PCA-GENETIC KERNEL SVM made strategies. Shown strategies are giving better outcomes. Thus, the preparing season of the proposed model is more prominent than the current model, while the testing time is lesser. The proposed strategy was discovered generally speaking classification time not exactly leaving model. As the number countenances are expanded, the training time is moreover extended in the proposed model. Notwithstanding, the mistake rate has fallen. As we were expanded the information compared to posture and light changes, it has expanded the normal accuracy. Subsequently, the proposed calculation exhibits a strong Classification.

Figure 6: Total number of faces vs. training time
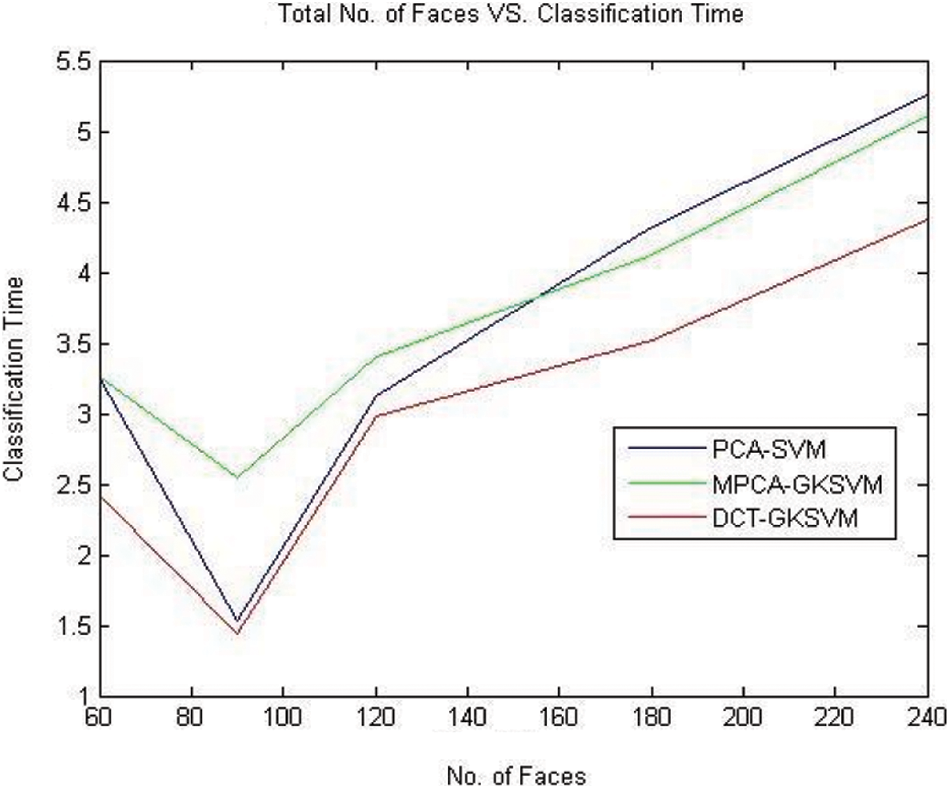
Figure 7: Total number of faces vs. classification time
Test results exhibit the adequacy and proficiency of the proposed strategies. At last, the proposed technique streamlined the piece boundaries of SVM by the generic algorithm with DCT was discovered with agreeable outcomes. The fifth path of MODIFIED PCA-GENETIC KERNEL SVM is discovered with 98.83% accuracy that is most extreme for MODIFIED PCA-GENETIC KERNEL SVM. It discovered more noteworthy accuracy, lower training time and less classification time if there should arise an occurrence of DCT–GENETIC KERNEL SVM. Test outcomes display the sufficiency and proficiency of the planned methodologies. Finally, the planned method smoothened the piece limits of SVM by conventional calculation with DCT and found pleasant results.
In the Future, some accommodation may be changed or added to the planned model. In the arranged model, DCT is utilized as highlight extractor and genetic kernel as Optimization. Both can expand the training time. Some part extractors as changes, dissipating, skewness, kurtosis and others may be utilized as an improvement in the spot of DCT. The phony huge number, underground bug settlement, MEB, cushioned reasoning and different methods may be utilized as headway. The offered structure performs on restricted size and kind of database. Later on, it may apply to huge databases and noisy pictures. In any case, we pondered just factors of lighting, present, illuminating, and verbalization in the database. We may additionally fuse the age and sex-bearing fragments. To make a secure framework, the proposed model may get together with other biometric structures as Iris, Fingerprint, Retina and others.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. J. Kumar, “Face recognition by machines: Is it an effective surveillance tactic?,” IETE Technical Review, vol. 30, no. 2, pp. 93–94, 2013. [Google Scholar]
2. A. K. Jain, S. C. Dass and N. Karthik, “Can soft biometric traits assist user recognition?,” in Proc. of the Society of Photo-Optical Instrumentation Engineers, vol. 5404, pp. 561–572, 2004. [Google Scholar]
3. A. K. Bennett, “Can facial recognition technology Be used to fight the New War against terrorism? Examining the constitutionality of facial recognition surveillance systems,” North Carolina Journal of Law & Technology, vol. 3, no. 1, pp. 115–174, 2001. [Google Scholar]
4. Emelie Rutherford, “Facial-Recognition Tech Has People Pegged,” vol. 7, no. 6 http://www.cnn.com/2001/TECH/ptech/07/17/face.time.idg/index.html (accessed July 17, 2001) [Google Scholar]
5. M. Kraus, “Face the facts facial recognition technology's troubled past-troubling future,” The Free Library, pp. 1–15, 2002. [Google Scholar]
6. R. Johnson and K. Bonsor, “How facial recognition systems work,” How Stuff Works, 2007. [Google Scholar]
7. M. J. Kumar, “Face recognition by machines: Is it an effective surveillance tactic?,” IETE Technical Review, vol. 30, no. 2, pp. 93–94, 2013. [Google Scholar]
8. A. K. Jain, S. C. Dass and N. Karthik, “Can soft biometric traits assist user recognition?,” in Proc. of the Proceedings of SPIE, vol. 5404, pp. 561–572, 2004. [Google Scholar]
9. A. B. Watson, “Image compression using the discrete cosine transform,” Mathematica Journal, vol. 4, no. 1, pp. 81–88, 1994. [Google Scholar]
10. S. A. Khayam, “The discrete cosine transform (DCTTheory and application,” in Technical Report, Michigan State University: India, pp. 1–31, 2003. [Google Scholar]
11. H. A. Rowley, S. Baluja and T. Kanade, “Neural network-based face detection,” IEEE Trans. Pattern Analysis and Machine Intelligence, USA, vol. 20, no. 1, pp. 23–38, 1998. [Google Scholar]
12. Y. Lu, N. Zeng, Y. Liu and N. Zhang, “A hybrid wavelet neural network and switching particle swarm optimization algorithm for face direction recognition,” International Journal on Neurocomputing, vol. 155, pp. 219–224, 2015. [Google Scholar]
13. M. M. Kasar, D. Bhattacharyya and T. H. Kim, “Face recognition using neural network: A review,” International Journal of Security and its Applications, vol. 10, no. 3, pp. 81–100, 2016. [Google Scholar]
14. L. L. Shen, L. Bai and Z. Ji, “A SVM face recognition method based on optimized Gabor features,” in Proc. of the 9th Int. Conf. on Visual Information Systems, Berlin, Heidelberg, pp. 165–174, 2007. [Google Scholar]
15. B. Heisele, P. Ho and T. Poggio, “Face recognition with support vector machines: Global versus component-based approach,” in Proc. of the 8th Int. Conf. on Computer Vision, Vancouver, BC, Canada, vol. 2, pp. 688–694, 2001. [Google Scholar]
16. Z. M. Hafed and M. D. Levine, “Face Recognition Using the Discrete Cosine Transform,” International Journal of Computer Vision, vol. 43, pp. 167–188, 2001. [Google Scholar]
17. G. Guo, S. Z. Li and K. Chan, “Face recognition by support vector machines,” in Proc. of the Int. Conf. on Automatic Face and Gesture Recognition, Grenoble, France, pp. 196–201, 2000. [Google Scholar]
18. P. Philips, “Support Vector Machine Applied to Face Recognition,” in Advances in Neural Information Processing System, Technical Report NISTIR, MIT Press: USA, pp. 803–809, 1999. [Google Scholar]
19. M. H. Yang and M. dam, “Gender classification using support vector machines,” in Proc. of the Int. Conf. on Image Processing, Canada, vol. 2, pp. 471–474, 2000. [Google Scholar]
20. K. I. Kim, K. Jung and H. J. Kim, “Face recognition using kernel principal component analysis,” Signal Processing Letters, IEEE, vol. 9, no. 2, pp. 40–42, 2002. [Google Scholar]
21. O. Déniz, M. Castrillón and M. Hernez, “Face recognition using independent component analysis and support vector machines,” Pattern Recognition Letters Elsevier, vol. 24, no. 13, pp. 2153–2157, 2003. [Google Scholar]
22. X. Zhang, Y. Guan, S. Wang, J. Liang and T. Quan, “Face recognition in color images using principal component analysis and fuzzy support vector machines,” in Proc. of Int. Symp. on Systems and Control in Aerospace and Astronautics, Harbin, China, vol. 10, pp. 42–45, 2011. [Google Scholar]
23. P. Parveen and B. Thuraisingham, “Face recognition using multiple classifiers,” in Proc. of Int. Conf. on Tools with Artificial Intelligence, Arlington, VA, vol. 1, pp. 179–186, 2006. [Google Scholar]
24. H. Wang, S. Yang and W. Liao, “An improved PCA face recognition algorithm based on the discrete wavelet transform, the support vector machines,” in Computational Intelligence, Security Workshops, IEEE: China, vol. 6, pp. 308–311, 2007. [Google Scholar]
25. X. Li, J. Ma and S. Li, “A novel face recognition method based on principal component analysis and kernel partial least squares,” in Robotics and Biometrics, IEEE: USA, pp. 1773–1777, 2007. [Google Scholar]
26. G. Zhang and J. Zhang, “Face recognition using multi-scale PCA and support vector machine,” in 7th World Congress on Intelligent Control, Automation, IEEE: China, vol. 1, pp. 5906–5910, 2008. [Google Scholar]
27. R. Rioux. and T. Simon, “Class redundancy for face recognition by SVM,” in Proc. of the 50th Int. Symp. ELMAR, IEEE: Zadar, Croatia, vol. 1, pp. 117–120, 2008. [Google Scholar]
28. B. C. Becker and E. G. Ortiz, “Evaluate face recognition for application applied to real word application FaceBook,” in Proc. of the Int. Conf. on Automatic Face and Gesture Recognition, Grenoble, France, vol. 14, pp. 1–6, 2008. [Google Scholar]
29. K. Cui, F. Han and P. Wang, “Research on face recognition based on boolean kernel SVM,” Natural Computation, IEEE, vol. 2, pp. 148–152, 2008. [Google Scholar]
30. J. Li, B. Zhao, H. Zhang and J. Jiao “Face recognition system using SVM classifier, feature extraction by PCA, LDA combination,” IEEE, vol. 1, pp. 1–4, 2009. [Google Scholar]
31. M. O. Faruqe and M. A. M. Hasan “Face recognition using PCA, SVM,” Anti-Counterfeiting, Security, Identification in Communication, IEEE, vol. 3, pp. 97–101, 2009. [Google Scholar]
32. Z. Lihong, S. Ying, Z. Yushi, Z. Cheng and Z. Yi, “Face recognition based on multi-class SVM,” in Proc. of Chinese Control and Decision Conf., China, vol. 7, pp. 5871–5873, 2009. [Google Scholar]
33. K. Cui and Y. Du “Applications of boolean kernel function SVM in face recognition,” in Proc. of Int. Conf. on Networks Security, Wireless Communications and Trusted Computing, Hubei, China, vol. 1, pp. 619–622, 2009. [Google Scholar]
34. M. M. Sani, K. A. Ishak and S. A. Samad, “Evaluation of face recognition system using support vector machine,” in Proc. of IEEE Student Conf. on Research and Development (SCOReD), Malaysia, pp. 139–141, 2009. [Google Scholar]
35. L. Lang, F. Xia and X. Wang, “Study of face recognition algorithm based on proximal support vector machine,” in Proc. of Second Int. Conf. on Intelligent Computation Technology and Automation, china, vol. 1, pp. 702–705, 2009. [Google Scholar]
36. M. Mazloom, S. Kasaei and A. H. Neissi, “Construction, application of SVM model, wavelet-PCA for face recognition,” in Proc. of Second Int. Conf. on Computer and Electrical Engineering: ICCEE, Dubai, UAE, vol. 1, pp. 391–398, 2009. [Google Scholar]
37. K. Chen and L. J. Zhao, “The study, implementation of face recognition, tracking system,” in Proc. of Int. Conf. on Computational Intelligence and Software Engineering, IEEE: China, pp. 1–5, 2009. [Google Scholar]
38. I. Frolov and R. Sadykhov, “The techniques for face recognition with support vector machines,” in Proc. of Int. Multiconference on Computer Science and Information Technology (IMCSIT), Mragowo, Poland, pp. 31–36, 2009. [Google Scholar]
39. H. Tao, L. Rui and M. J. Zhang, “Face recognition under complex conditions,” in Proc. of Int. Conf. on Electrical and Control Engineering (ICECE), Wuhan, China, pp. 960–963, 2010. [Google Scholar]
40. P. Chato and N. Velasco “Image processing and artificial neural network for counting people inside public transport,” in Proc. of IEEE Third Ecuador Technical Chapters Meeting (ETCM), Ordoñez Lasso, pp. 1–5, 2018. [Google Scholar]
41. Z. Wang and L. Zhang,“Research on application of deep learning algorithm in image classification,” in Proc. of IEEE Asia-Pacific Conf. on Image Processing, Electronics and Computers (IPEC), Dalian, China, pp. 1122–1125, 2021. [Google Scholar]
42. E. Xi,“Image feature extraction and analysis algorithm based on multi-level neural network,” in Proc. of the Fifth Int. Conf. on Computing Methodologies and Communication (ICCMC 2021), Erode, India, pp. 1062–1065, 2021. [Google Scholar]
43. Y. Tian “Artificial intelligence image recognition method based on convolutional neural network algorithm,” IEEE Access, vol. 8, pp. 125731–125744, 2020. [Google Scholar]
44. L. Li, S. Lijuan, X. Yu, L. Shujing, H. Xuwen et al., “Fuzzy multilevel image thresholding based on the choose improved coyote optimization algorithm.” IEEE Access, vol. 9, pp. 33595–33607, 2020. [Google Scholar]
45. R. F. Mansour, “Evolutionary computing enriched ridge regression model for craniofacial reconstruction,” Multimedia Tools and Applications, vol. 79, no. 31, pp. 22065–22082, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |