DOI:10.32604/cmc.2022.024619

| Computers, Materials & Continua DOI:10.32604/cmc.2022.024619 |  |
| Article |
Deep Learning with Image Classification Based Secure CPS for Healthcare Sector
1Department of Information Systems, College of Computer and Information Sciences, Prince Sultan University, Riyadh, 12435, Saudi Arabia
2Department of Information Systems, College of Science and Arts, King Khalid University, Mahayil Asir, 62529,Saudi Arabia
3Department of Cybersecurity, College of Computer Science and Engineering, University of Jeddah, Jeddah, 21959,Saudi Arabia
4Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, 16278, Saudi Arabia
5Department of Computer Science, Community College, King Khalid University, Mahayil Asir, 62529, Saudi Arabia
*Corresponding Author: Manar Ahmed Hamza. Email: ma.hamza@psau.edu.sa
Received: 25 October 2021; Accepted: 04 January 2022
Abstract: Cyber-Physical System (CPS) involves the combination of physical processes with computation and communication systems. The recent advancements made in cloud computing, Wireless Sensor Network (WSN), healthcare sensors, etc. tend to develop CPS as a proficient model for healthcare applications especially, home patient care. Though several techniques have been proposed earlier related to CPS structures, only a handful of studies has focused on the design of CPS models for health care sector. So, the proposal for a dedicated CPS model for healthcare sector necessitates a significant interest to ensure data privacy. To overcome the challenges, the current research paper designs a Deep Learning-based Intrusion Detection and Image Classification for Secure CPS (DLIDIC-SCPS) model for healthcare sector. The aim of the proposed DLIDIC-SCPS model is to achieve secure image transmission and image classification process for CPS in healthcare sector. Primarily, data acquisition takes place with the help of sensors and detection of intrusions is performed using Fuzzy Deep Neural Network (FDNN) technique. Besides, Multiple Share Creation (MSC) approach is used to create several shares of medical image so as to accomplish security. Also, blockchain is employed as a distributed data storage entity to create a ledger that provides access to the client. For image classification, Inception v3 with Fuzzy Wavelet Neural Network (FWNN) is utilized that diagnose the disease from the applied medical image. Finally, Salp Swarm Algorithm (SSA) is utilized to fine tune the parameters involved in WNN model, thereby boosting its classification performance. A wide range of simulations was carried out to highlight the superiority of the proposed DLIDIC-SCPS technique. The simulation outcomes confirm that DLIDIC-SCPS approach demonstrates promising results in terms of security, privacy, and image classification outcomes over recent state-of-the-art techniques.
Keywords: Cyber Physical Systems; healthcare; cybersecurity; deep learning; share creation; image classification
Cyber-Physical System (CPS) is a structural framework which encompasses communication technologies and pervasive sensing and offers loads of advantages to both society and the country's economy. In other terms, it can be defined as an engineered structure in which the physical processes/systems get increased with cyber components like communication networks, computational hardware, etc. [1]. These components are closely connected with one another; hence the functionality of individual components is decided based on another component. In recent years, the penetration of CPS has gradually increased in the fields of Industrial Internet of Things (IIoT), energy, health, and transportation. The main focus of this research is the development of a system that is flexible, smart, efficient and possess reliability, stability, security, privacy, and robustness [2]. But tremendous growth in adoption of this technology has also exposed this system to have profound and serious risks. When these risks are not managed, it tend to lose the remarkable benefits which it could offer [3].
At the moment, blockchain healthcare is the most commonly used application to keep healthcare information, secure and safe. Security is a key challenge in the medical sector [4]. Between 2009 and 2017, the healthcare records of around 176 million patients got revealed in security breaches. These perpetrators stole health and genomic testing records, banking and credit card data. However, Blockchain technology has the capacity to keep transparent, incorruptible and decentralized logs of information about each patient. This characteristic makes it a technology apt for security application. In addition, blockchain is private as well as transparent that can hide the identity of a person using secure and complex codes and can secure the sensitivity of healthcare information too [5]. Since the technology is decentralized in nature, it enables doctors, medical service providers, and patients to share similar data amongst themselves securely and rapidly. The key challenge, when handling such medical data, is to guarantee data security from different sorts of cyberattacks namely, tampering and unauthorized access.
Blockchain has secured the position of a digital ledger which is configured to record transactions in finance and other sectors, where the preservation of historical records of e-transaction is critical in nature. Blockchain is the main technology behind bitcoin, a kind of cryptocurrency. Bitcoin is invented after the financial crisis of 2009, as an alternative to conventional currency [6]. One of the main reasons behind the introduction of this technology is the failure of centralized bank in terms of preserving financial records. Financial institutions, for a known period of time, have distinguished the requirement for a distributed decision-making method. However, such methods were not implemented, until the emergence of crypto-currency fueled by blockchain technology [7].
In this study, the aim of the proposed model is to achieve secure image transmission and image classification for CPS in healthcare sector.
1.2 Contributions of the Study
The current study designs a Deep Learning-based Intrusion Detection and Image Classification for Secure CPS (DLIDIC-SCPS) model to be applied in healthcare sector. Primarily, data acquisition takes place using sensors and the detection of intrusions is performed usig Fuzzy Deep Neural Network (FDNN) model. Besides, Multiple Share Creation (MSC) approach is used to create multiple shares of medical image to accomplish security. Also, blockchain is employed as a distributed data storage to create a ledger that provides access to the client. For image classification, Inception v3 with Fuzzy Wavelet Neural Network (FWNN) is utilized for disease diagnosis from the applied medical image. Finally, Salp Swarm Algorithm (SSA) is applied to fine tune the parameters involved in WNN model, thereby improving its classification performance. A wide range of simulations was carried out to highlight the superiority of the proposed DLIDIC-SCPS model.
Rest of the study is arranged as follows. Section 2 briefs the recently-developed models related to the study domain. Section 3 introduces the proposed model and Section 4 validates the performance of the proposed model. Lastly, Section 5 draws the conclusion.
Shu et al. [8] described a 2-phase architecture in which the healthcare records are shared on-blockchain and stored off-blockchain. Additionally, a multi-trapdoor hash function was also presented in this study. The objective is to realize the validation of medical apps, medical staff, and medical equipment, to guarantee the integrity of healthcare information, and to assist in sharing healthcare data and secured storage. The presented system is computationally effective, since it does not utilize exponential operations and bi-linear maps. Verma et al. [9] proposed a novel Internet of Things (IoT)-Fog-Cloud enabled CPS model for diagnoses and classification of Ulcerative Colitis using Naïve Bayes (NB) and Deep Neural Network (DNN) classifiers correspondingly. Lastly, the compiled healthcare data was analyzed and the results of all the users were stored on cloud.
The aim of the study conducted by Hussain et al. [10] is to measure the possibilities of a cyber-physical cardiac monitoring scheme so as to categorize stroke patients from healthy adults with altered cardiac activity. Xu et al. [11] introduced a certificateless signature system based on N-th degree Truncated polynomial Ring Units (NTRU) lattice. The latter is constructed based on the complexity of small integer solutions in NTRU lattice and is recognized as quantum attack resilience. Performance evaluation and security analyses of the model demonstrate that the presented method considerably decreased the computation cost and communication.
Ali et al. [12] proposed a method in which the researchers used criticality analysis, failure modes, and effects, i.e., a prominent hazard analyses method to have a better understanding about failure and risk avoidance. In this method, the authors transformed Criticality Analysis model, Failure Modes and Effects into Unified Modeling Language (UML) class diagram. Later, a knowledge base was created on the basis of derived UML class diagram. Patan et al. [13] designed a holistic DNN-driven IoT smart medical system named Grey Filter Bayesian Convolution Neural Network (GFB-CNN) based on real-time analysis. In this work, the authors proposed a holistic Artificial Intelligence (AI)-driven IoT eHealth framework based on GFB-CNN while the essential quality of services (QoS) parameters such as overhead and time got decreased by a high rate of accuracy.
In this study, a novel DLIDIC-SCPS technique is derived for intrusion detection and image management in blockchain-enabled CPS healthcare sector. The proposed model encompasses different processes such as data acquisition, FDNN-based intrusion detection, MSC-based share creation, data transmission, Inception-based feature extraction, FWNN-based classification, and SSA-based parameter tuning. These processes are discussed clearly in the following sections.
3.1 FDNN-Based Intrusion Detection
Initially, the healthcare data collected from different sources is fed as input into FDNN model to detect the existence of intrusions. FDNN method is applied for concurrent extraction of neural and fuzzy depiction data. The knowledge, acquired from these two factors, is then incorporated in fusion layer so as to attain the last depiction and classify the data. Fuzzy-based representation reduces uncertainty whereas neural representation discards the noise that may be present in the input data. FDNN method utilizes two efficient depictions to create a fused representation for end classification. This method includes l as a layer number,

Figure 1: Structure of FDNN
Fusion concept depends on the principle of multi-modal learning [15] that imposes feature extraction from a separate view which is not sufficient for capturing complex framework of higher content data. It generates a set of features from numerous views and synthesizes it to a higher-level depiction for the implementation of classification. In FDNN, both neural and fuzzy parts are employed to seek an efficient depiction by reducing noises and uncertainties of input data. Additionally, fuzzy and neural learning parts are organized in neural network. Hence, it is instinctive to develop the feature fusion phase. Now, the widely-employed multi-model Neural Network (NN) is applied in the integration of fuzzy and neural depictions with densely-connected fusion layers.
where the outputs from deeper depiction term (
3.2 Process Involved in MSC Technique
At this stage, the medical images are fed into MSC approach to create many shares. When intrusion is resolved from the captured information, secure image broadcast method is initiated for cloud servers. Primarily, MSC technique is implemented for the creation of four shares of all individual images attained under physical device. The projected MSC technique broadcasts the image to cloud servers from secured and secret techniques. The image is sent as a share while every share is combined with reconstruction of a novel input image. MSC technique generates the share in pixel value. It removes the pixel value in image and is employed in the creation of several shares. At last, the shares are separated as blocks and the blocks are securely transferred based on blockchain approach. The procedures followed in MSC technique are discussed herewith. The actual pixel value of input image is resolved as follows.
where
Each pixel, present in the input image, is regarded as the framework of n transformed techniques and is named as share. Each share includes a fixed number of sub-pixels as Red-Green-Blue (RGB) images [16]. The share towards RGB is separately denoted as Rsh, Gsh, and Bsh and are determined as follows.
where a and b refers to the place of matrix,
After the creation and broadcasting of the shares to cloud servers, share reconstruction occurs in which every share is combined to retrieve the actual image. Image reconstruction is performed as follows.
After the shares are reconstructed, the input image is recovered effectively. At that time, the attained image endures classification procedure for identifying as well as classifying the presence of diseases.
3.3 Blockchain-Enabled Secure Transmission
MSC-based share generation procedure creates several shares for all the images. Afterwards, the shares are divided as blocks while these blocks are securely transferred to cloud servers by following blockchain approach. Therefore, an intruder record could not change as all the blocks are collected with cryptographic value of recent blocks. In blockchain method, all the transactions are cryptographically employed with hash values and are validated by miners. It has repeating measures of entire ledger and blocks of all transactions. Fig. 2 illustrates the architecture of blockchain [17]. Blockchain has the ability to distribute the ledger of data from decentralization, shared, safe, and trusted approaches.

Figure 2: Structure of Blockchain
Decentralization storing is a kind of blockchain. It is executed to store the maximum data linked to existing and preceding blocks with the help of smart contract codes. SiacoinDB, BigchainDB, Swarm, MoneroDB, InterPlanetary File System (IPFS), LitecoinDB, and so on, are executed as decentralized databases in recent times. IPFS is determined as a Point to Point, decentralized and shared database that is well connected as well as has forward standard files. IPFS is an important storage which is employed by blockchain technique in IoT function to acquire the maximum throughput.
3.4 Design of Image Classification Process
In this final stage, the classification of medical images takes place through three sub-processes namely, Inception-based feature extraction, FWNN-based classification, and SSA-based parameter tuning.
3.4.1 Inception Based Feature Extraction
GoogLeNet technique is termed as Inception network since its main goal is to have the development of an inception network framework [18]. It comprises of maximal GoogLeNet versions i.e., categorized under distinct forms of Inception v1, v2, v3, v4, and Inception-ResNet. Therefore, inception commonly consists of three distinct sizes of convolutional and maximal pooling layers. The results from the previous layer in the network are determined as the channel is gathered after finishing the convolutional operation. In the meantime, a non-linear fusion is performed. Likewise, the expression function of this network and the feasibility for different scales get improved while the overfitting problems are removed. Inception v3 represents a network architecture placed by Keras i.e., pretrained in Image Net. The input size of the central images is 299 * 299 using three channels. In contrast to Inception v1, v2 and v3 network architecture, convolutional kernel splitting methodology is applied to divide a huge amount of integrals to minimal convolution. E.g., a 3 * 3 convolutional layer is separated into 1 * 3 and 3 * 1 convolution. With this splitting technique, the amount of attributes can be restricted; therefore, network training speed can be triggered during spatial feature extraction in this efficient method. Instantaneously, Inception v3 enhances the Inception network architecture through three distinct-sized grids such as 8 * 8, 35 * 35, and 17 * 17.
3.4.2 FWNN Based Classification
The derived features are then passed onto FWNN model to allot proper class labels. FWNN method is made up of seven layers as discussed below.
Layer 1: There is no processing in this layer. In that way, each node straightforwardly sends the input value to next layer.
Layer 2: The measure of input variable is fuzzified and each node represents a single fuzzy set. Therefore, the resultant two layers illustrate the membership values of input variable to respective fuzzy set based on the determined Membership Function (MF).
Layer 3: It accepts the MF of input, derived from present layer, to design the antecedent part of each fuzzy rule, where each node defines a single fuzzy rule. The experimental result can be calculated using Eq. (7):
Layer 4: The nodes present in four layers are called as ‘consequent nodes’ since it corresponds to the last part of fuzzy rule. Each node consists of wavelet function
Layer 5: It is an integration of 3rd and 4th layers. The resultant values are calculated by maximizing the experimental result of 3rd layer with the outcomes of 4th layer as given herewith.
Layer 6: The result includes two major parts. At first,
Layer 7: It refers to defuzzifier where the whole outcomes of FWNN are estimated through
3.4.3 SSA Based Parameter Tuning
For optimal fine tuning of the parameters in FWNN model, SSA is applied. In order to boost the forecasting efficiency of FWNN approach, SSA is utilized for optimum modification of parameters present in FWNN technique. SSA is a bio-inspired optimization approach which is stimulated based on navigation and foraging efficiency of salp chain and is generally initiated from Deep Ocean. In mathematical procedure, salp population is separated into two groups such as leaders and followers. The better salps (optimal solution) are considered for finding the food source while the salp chains follow it. After each iteration, the leader salp alters its location in regard to feed sources. The leader explores and exploits the search space for optimal solutions while the follower salps transfer step-by-step to neighboring leaders. This technique is used by salp in converging to global optimal quickly, but it avoids getting trapped in local optimal.
Salp places are defined from n dimensional search space: Where n refers to the count of decision variables in this problem [20]. Let us assume that food source
A fine balance between exploration as well as exploitation phases from optimization is continued by coefficient
At present,
where;
and
Considering,
Parameter optimization issues found in FWNN are resolved with the help of SSA and the forecasting results showed improvement.
The proposed model was validated for its performance using three datasets namely, International Skin Imaging Collaboration (ISIC) skin lesion dataset [21], NSL-KDD2015, and CIDDS-001 dataset. The details of the dataset are given in Tab. 1 and sample skin lesion images are shown in Fig. 3.

Figure 3: Sample images
The results from overall ID analysis accomplished by the presented FDNN model on the applied two datasets are given in Tab. 2 and Fig. 4. On the applied NSL-KDD 2015 dataset, the FDNN model obtained 99.08%, 98.90%, 99.19%, and 98.43% respectively for the parameters,
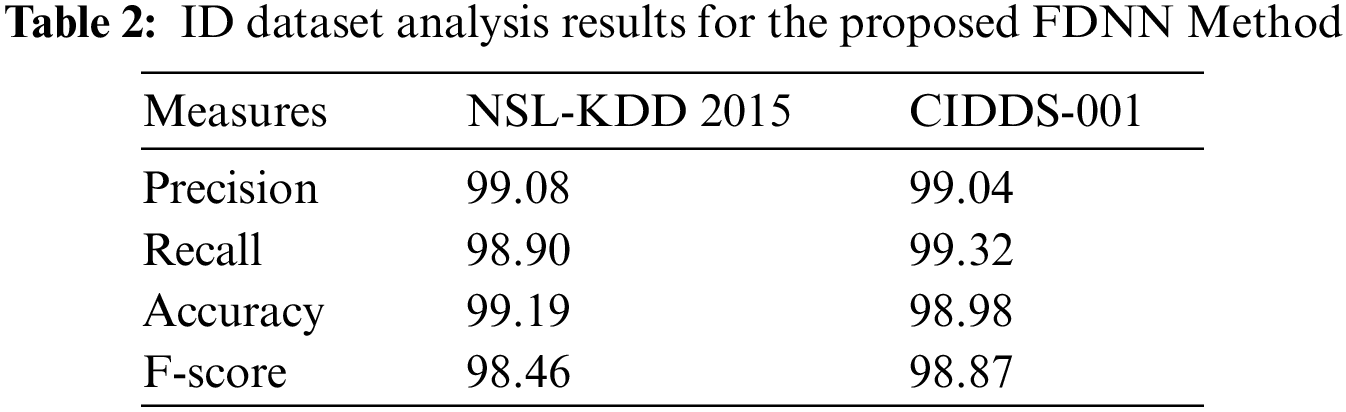

Figure 4: Results of the analysis of FDNN technique under distinct measures
An
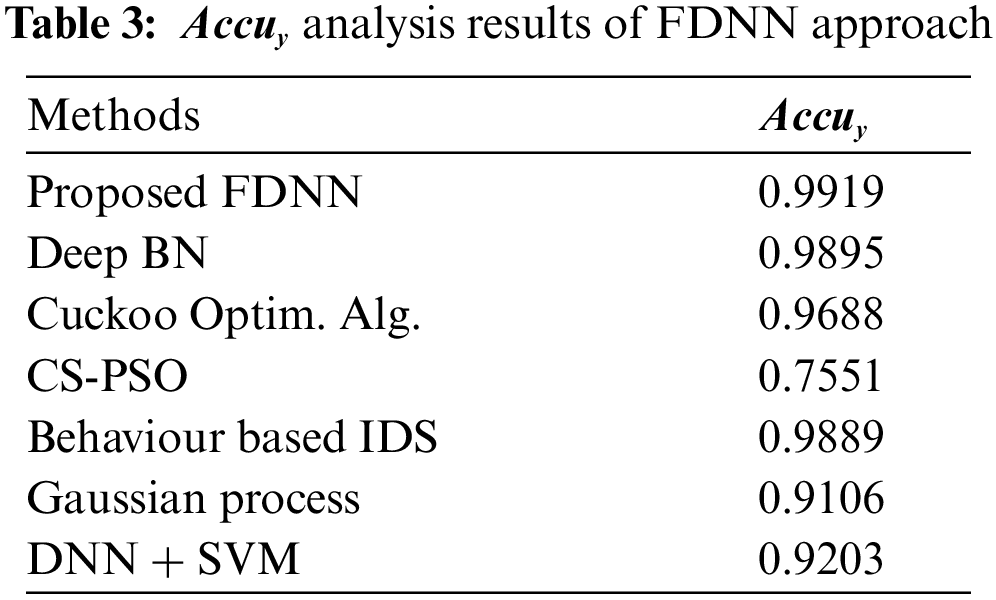

Figure 5: Accuracy analysis results of FDNN technique against existing approaches
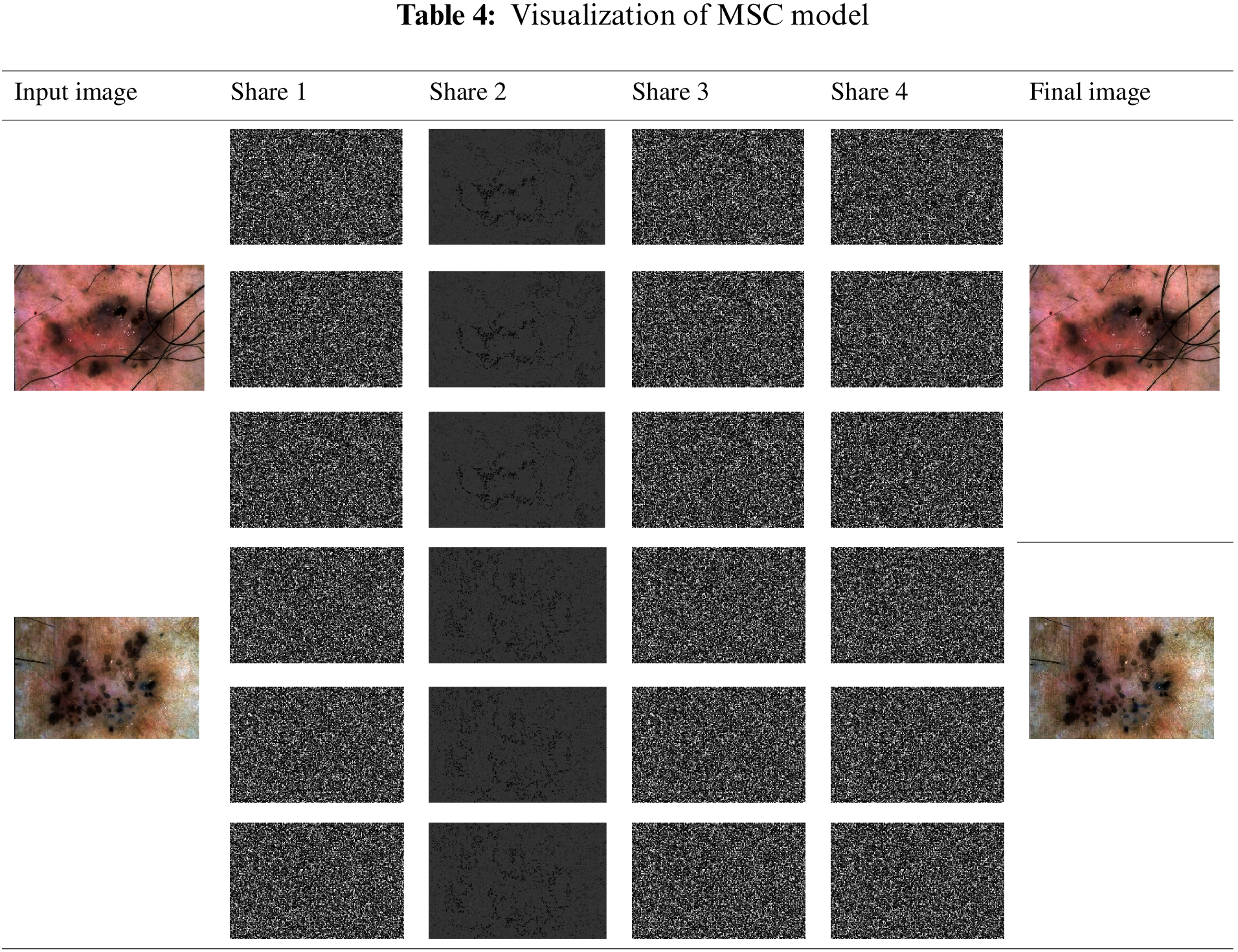
Tab. 4 visualizes share creation results achieved by the presented MSE scheme. The table depicts that the input test image was split into four individual shares and the reconstruction of shares resulted in effective input image with no distortion.
In order to validate the enhanced performance of Inceptionv3 + OWNN technique, a series of comparative analyses was conducted and the results are shown in Tab. 5. Fig. 6 shows the
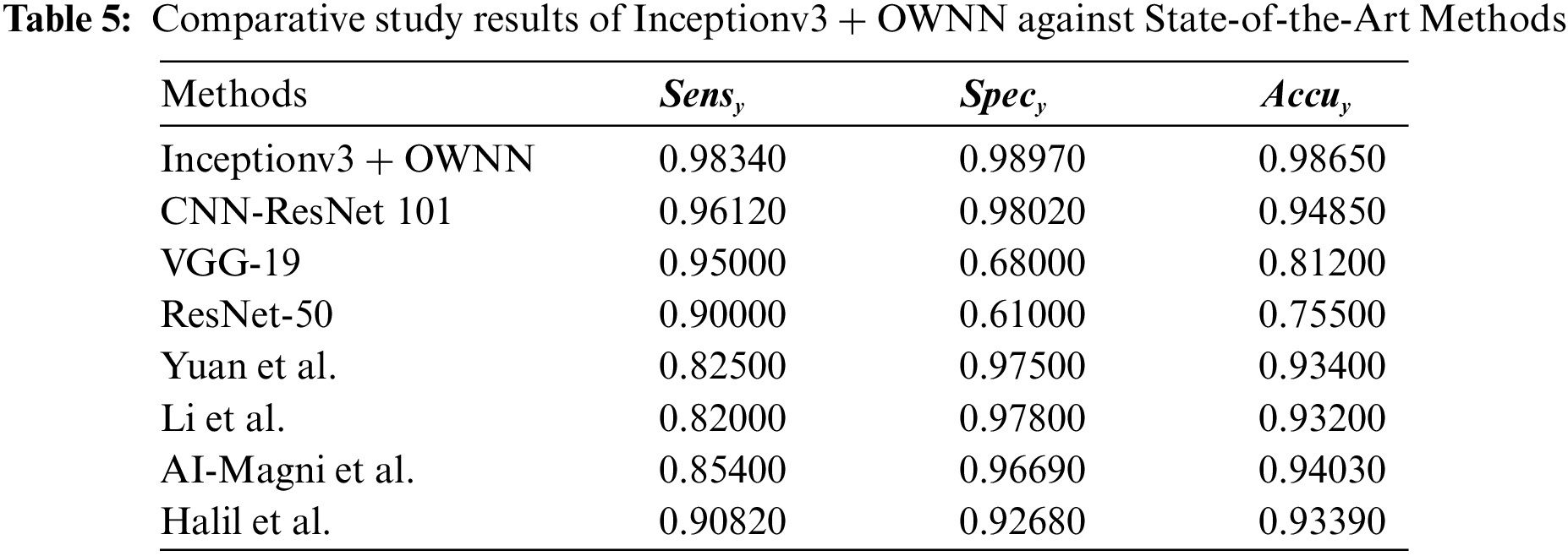

Figure 6: Sensitivity analysis results of inceptionv3 + OWNN technique against existing approaches
Fig. 7 shows the

Figure 7: Specificity analysis results of inceptionv3 + OWNN technique against existing approaches
Finally, Fig. 8 shows the

Figure 8: Accuracy analysis results of inceptionv3 + OWNN technique against existing approaches
In this study, a novel DLIDIC-SCPS technique is derived for intrusion detection and image management in blockchain-enabled CPS for healthcare sector. The proposed model encompasses different processes such as data acquisition, FDNN-based ID, MSC-based share creation, data transmission, and classification. In final stage, the classification of medical images takes place using three sub-processes namely, Inception-based feature extraction, FWNN-based classification, and SSA-based parameter tuning. A comprehensive experimental analysis was conducted to showcase the improved outcomes of DLIDIC-SCPS model. The simulation results established that the proposed DLIDIC-SCPS technique is a promising candidate for intrusion detection and image management in terms of security, privacy, and image classification outcomes over recent state-of-the-art techniques. In future, DLIDIC-SCPS technique can be applied in real-time hospital environment.
Acknowledgement: The authors would like to acknowledge the support of Prince Sultan University for paying the Article Processing Charges (APC) of this publication.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work under Grant Number (RGP.1/127/42). https://www.kku.edu.sa.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. H. Rathore, A. Mohamed and M. Guizani, “A survey of blockchain enabled cyber-physical systems,” Sensors, vol. 20, no. 1, pp. 282, 2020. [Google Scholar]
2. G. N. Nguyen, N. H. L. Viet, M. Elhoseny, K. Shankar, B. B. Gupta et al., “Secure blockchain enabled cyber–physical systems in healthcare using deep belief network with ResNet model,” Journal of Parallel and Distributed Computing, vol. 153, pp. 150–160, 2021. [Google Scholar]
3. A. V. Barenji, Z. Li, W. M. Wang, G. Q. Huang and D. A. G. Zubiaga, “Blockchain-based ubiquitous manufacturing: A secure and reliable cyber-physical system,” International Journal of Production Research, vol. 58, no. 7, pp. 2200–2221, 2020. [Google Scholar]
4. M. Sivaram, E. L. Lydia, I. V. Pustokhina, D. A. Pustokhin, M. Elhoseny et al., “An optimal least square support vector machine based earnings prediction of blockchain financial products,” IEEE Access, vol. 8, pp. 120321–120330, 2020. [Google Scholar]
5. Z. Zhou, B. Wang, M. Dong and K. Ota, “Secure and efficient vehicle-to-grid energy trading in cyber physical systems: Integration of blockchain and edge computing,” IEEE Transactions on Systems, Man, and Cybernetics, vol. 50, no. 1, pp. 43–57, 2020. [Google Scholar]
6. G. P. Joshi, E. Perumal, K. Shankar, U. Tariq, T. Ahmad et al., “Toward blockchain-enabled privacy-preserving data transmission in cluster-based vehicular networks,” Electronics, vol. 9, no. 9, pp. 1358, 2020. [Google Scholar]
7. K. Manavalan, R. K. Saravanan, V. Thiruppathi, R. Rajkumar and K. Balaji, “Blockchain-enabled cyber physical system–A case study: SmartGym,” Smart Cyber Physical Systems, pp. 157–172, 2020. [Google Scholar]
8. H. Shu, P. Qi, Y. Huang, F. Chen, D. Xie et al., “An efficient certificateless aggregate signature scheme for blockchain-based medical cyber physical systems,” Sensors, vol. 20, no. 5, pp. 1521, 2020. [Google Scholar]
9. P. Verma, S. K. Sood and H. Kaur, “A Fog-cloud based cyber physical system for ulcerative colitis diagnosis and stage classification and management,” Microprocessors and Microsystems, vol. 79, pp. 103304, 2020. [Google Scholar]
10. I. Hussain and S. J. Park, “Big-ECG: Cardiographic predictive cyber-physical system for stroke management,” IEEE Access, vol. 9, pp. 123146–123164, 2021. [Google Scholar]
11. Z. Xu, D. He, P. Vijayakumar, K. K. R. Choo and L. Li, “Efficient ntru lattice-based certificateless signature scheme for medical cyber-physical systems,” Journal of Medical Systems, vol. 44, no. 5, pp. 92, 2020. [Google Scholar]
12. N. Ali and J. E. Hong, “Failure detection and prevention for cyber-physical systems using ontology-based knowledge base,” Computers, vol. 7, no. 4, pp. 68, 2018. [Google Scholar]
13. R. Patan, G. S. P. Ghantasala, R. Sekaran, D. Gupta and M. Ramachandran, “Smart healthcare and quality of service in IoT using grey filter convolutional based cyber physical system,” Sustainable Cities and Society, vol. 59, pp. 102141, 2020. [Google Scholar]
14. R. Das, S. Sen and U. Maulik, “A survey on fuzzy deep neural networks,” ACM Computing Surveys, vol. 53, no. 3, pp. 1–25, 2020. [Google Scholar]
15. Y. Deng, Z. Ren, Y. Kong, F. Bao and Q. Dai, “A hierarchical fused fuzzy deep neural network for data classification,” IEEE Transactions on Fuzzy Systems, vol. 25, no. 4, pp. 1006–1012, 2017. [Google Scholar]
16. A. F. S. Devaraj, G. Murugaboopathi, M. Elhoseny, K. Shankar, K. Min et al., “An efficient framework for secure image archival and retrieval system using multiple secret share creation scheme,” IEEE Access, vol. 8, pp. 144310–144320, 2020. [Google Scholar]
17. J. Wang, Q. Wang, N. Zhou and Y. Chi, “A novel electricity transaction mode of microgrids based on blockchain and continuous double auction,” Energies, vol. 10, no. 12, pp. 1971, 2017. [Google Scholar]
18. C. Lin, L. Li, W. Luo, K. C. P. Wang and J. Guo, “Transfer learning based traffic sign recognition using inception-v3 model,” Periodica Polytechnica Transportation Engineering, vol. 47, no. 3, pp. 242–250, 2018. [Google Scholar]
19. R. Cheng and Y. Bai, “A novel approach to fuzzy wavelet neural network modeling and optimization,” International Journal of Electrical Power & Energy Systems, vol. 64, pp. 671–678, 2015. [Google Scholar]
20. R. A. Ibrahim, A. A. Ewees, D. Oliva, M. A. Elaziz and S. Lu, “Improved salp swarm algorithm based on particle swarm optimization for feature selection,” Journal of Ambient Intelligence and Humanized Computing, vol. 10, no. 8, pp. 3155–3169, 2019. [Google Scholar]
21. Dataset: https://challenge.isic-archive.com/, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |