DOI:10.32604/cmc.2022.026307

| Computers, Materials & Continua DOI:10.32604/cmc.2022.026307 |  |
| Article |
Cost and Efficiency Analysis of Steganography in the IEEE 802.11ah IoT Protocol
1Automobile Transportation Department, South Ural State University, Chelyabinsk, 454080, Russia
2Electrical and Electronics Engineering Department Karabük University, Karabük, 78050, Turkey
3Department of Electrical Engineering, Indian Institute of Technology Ropar, Punjab, 140001, India
4Department of Computer and Network Engineering, University of Jeddah, Jeddah, 23218, Saudi Arabia
5Faculty of Engineering Technology, University Tun Hussein Onn Malaysia, Pagoh Campus, 86400, Malaysia
*Corresponding Author: Akram A. Almohammedi. Email: akrama2810@gmail.com
Received: 21 December 2021; Accepted: 22 February 2022
Abstract: The widespread use of the Internet of Things (IoT) applications has enormously increased the danger level of data leakage and theft in IoT as data transmission occurs through a public channel. As a result, the security of the IoT has become a serious challenge in the field of information security. Steganography on the network is a critical tool for preventing the leakage of private information and enabling secure and encrypted communication. The primary purpose of steganography is to conceal sensitive information in any form of media such as audio, video, text, or photos, and securely transfer it through wireless networks. In this paper, we analyse the performance characteristics of one of the steganography techniques called Hidden Communication System for Corrupted Networks (HCCNETs) for hiding sensitive data. This performance analysis includes the efficiency and the cost of the system in Wireless Local Area Networks (WLANs), specifically in the IEEE 802.11ah IoT protocol. The analysis is mainly based on a two-dimensional Markov chain model in the presence of an error channel. Additionally, the model considers packet arrival rate, back-off timer freezing, back-off stages, and short retry limit to ensure compliance with IEEE 802.11ah requirements. It stresses the importance of taking these elements into consideration while modeling the efficiency and cost of the steganographic channel system. These parameters often result in a high precise channel access estimation, a more accurate and efficient accuracy measurements system, efficient channel utilisation, avoidance of throughput saturation overestimation, and ensuring that no packet is served endlessly. Evaluated results demonstrate that HCCNETs is an effective approach at low cost.
Keywords: IoT; HCCNETs; steganography; markov chain model
Nowadays, Internet of Things (IoT) technologies are widely used in a variety of applications such as healthcare, industrial control, identification technology, ubiquitous computing and military investigation, etc [1,2]. The IoT architecture broadly contains three elements: cloud, device terminal, and mobile terminal. By establishing a link between a mobile terminal and the cloud, an instruction is given to a device terminal via the cloud, resulting in the realisation of the connectivity between entities and the network [3]. Thereby, high-performance servers are often expected continue providing public-service computing [3], which is a costly proposition. Meanwhile, to properly manage network congestion in the IoT, emergency packets are employed and upgraded [4–6]. Due to the presence of many cloud platforms and terminal devices, there will be a large amount of service quality data, which may lead to sensitive information leakage [7]. Furthermore, because IoT devices, such as video surveillance, car localisation, smart bracelets, and other similar devices, are so near to users’ lives, the majority of the data is related to user privacy. Sensitive data is likely more prone to exposure and monitoring than non-sensitive data. So, data protection is a big issue for many people [8–10], and the privacy-preserving challenges posed by IoT systems are serious problems that must be addressed. Information concealing methods can be used to protect communication between a machine and the server or application programmes, in addition to encrypting the transmitted message. Secret communication is desperately required in order to ensure the privacy or crucial data protection while also resisting the possibility of being disclosure. The term “steganography scheme” refers to a secret communication manner in which confidential data is invisibly integrated into a carrier and then broadcast publicly. It is possible to generate the secret carrier known as stego by concealing confidential information in the common communication medium such as images, text, video, and audio, etc. It is difficult to detect anomalies by the monitoring device in the stego transmission process, so that confidential information can be delivered secretly. As a result, researchers are using steganography techniques to the IoT in an effort to protect communications. In [11], the authors developed a novel approach for securing data in fog cloud IoT. Within the architecture, a user embeds important data in one area using the suggested quantum steganography protocol and uploads the covered data to the fog cloud. The intended receiver, located at a different location, retrieves the data in the fog cloud and extracts the desired content using the suggested extraction technique. Additionally, the authors provide a unique quantum steganography technique based on the hash function and quantum entangled states. The authors in [1] proposed a unique steganography method based on image-to-image translation by incorporating a steganography and steganalysis module into CycleGAN, which is suited for the secret communication and privacy preservation requirements of the Internet of Things. The purpose of the steganalysis network is to enhance the stego image's anti-detection capability. Additionally, CycleGAN’s cycle consistency ensures the resulting image’s quality.
The authors in [12] proposed a steganography approach for IEEE 802.11 via using intentionally corrupted checksums frames to set up hidden communications. However, the authors in [12] assumed saturated condition and such assumption leads to unstable network. The steganography in IEEE 802.11 OFDM symbols was analysed in [13,14]. The authors in [13,14] proposed a model based on 2-D Markov chain to analyse the network throughput of steganographic method of IEEE 802.11 a/g standards within a non-ideal channel. Nevertheless, the authors in [13,14] considered saturated situations and analysed it within basic access method. In [15], the authors presented and described the elliptic Galois cryptography scheme. A cryptography approach was employed in this study to secure private data obtained from a variety of medical sources. Following that the encrypted data was embedded into a low complexity picture using a Matrix XOR encoding steganography approach. Additionally, the suggested work in [15] used an optimization approach called Adaptive Firefly to improve the image’s cover block selection. In [16], the authors described a method for concealing secret messages by mapping numerous steganographic methods to complicated texture objects. To begin, complicated texture patches are chosen using an object recognition technique. Second, three distinct steganographic techniques were utilised to conceal a hidden message inside the block area chosen. The authors in [17] developed a novel approach for detecting steganography in network protocols. The technique was developed using machine learning algorithms and was based on a multilayer approach for the selective examination of derived and aggregated metrics. The primary purpose was to enable steganalysis on networks with a high density of devices and connections. The authors in [18] introduced a large-capacity secure authenticated quantum video steganography scheme. This approach allows for the embedding of secret quantum information into carrier quantum video, significantly increasing the embedding capacity. Additionally, it accomplishes quantum information steganography via the use of video’s unique properties, as well as an authentication system for increased security. In [19], the authors presented CloudSteg, a steganographic technique that establishes a covert channel between two cloud instances that share a physical computer through hard disc contention. In [20], the authors offered a coverless information concealing approach in which original pictures with traits capable of expressing hidden information are employed directly as stegoimages. Additionally, the authors developed a revolutionary coverless information concealment technique for images utilising Faster Region-based Convolutional Neural Networks (Faster-RCNN). The authors used Faster-RCNN to recognise and locate objects in pictures and to convey hidden information through the labels of these things. The authors of [21] also employed deep neural network to conceal numerous speech signals under a single cover using multiple decoders or a single conditional decoder. Three distinct networks were used in [21]. The encoder network takes as inputs a carrier and a message and creates a combined latent network for both signals. This is subsequently passed via a carrier decoder network, which outputs the carrier embedded with the message. Finally, the message decoder network reconstructs the concealed message signal from the embedded signal. They discovered that the decoded signals are indistinguishable, however this approach has the disadvantage of not operating in other audio domains outside speech.
The work presented in this paper focuses on one of steganography techniques, called the Hidden Communication System for Corrupted Networks (HCCNETs) for hidden sensitive data. The significance of HCCNETs lies on the use of a protected communications network equipped with cryptographic techniques to offer a steganography system and suggestion of new protocol with bandwidth allocation on the basis of corrupted frames. The system’s primary innovation is the use of frames with intentionally erroneous checksums to create concealed communication. This study is an extension of the existing study in [12], by adding an idle state to the model to reflect the empty queue at the MAC layer when no packet is available for transmission. The important contributions of this work are as follows: 1) An analytical model based on a two-dimensional Markov chain under unsaturated situations is developed. The primary advantages of using unsaturated circumstances in this model are that (i) real networks are predominantly non-saturated, (ii) saturated circumstances often result in an unstable network, and (iii) it allows for the consideration of inter-arriving time and burstiness in the network [22,23]. 2) An error-prone channel is modelled in this work in order to avoid overestimating saturated throughputs. The model also considers packet arrival rate, back-off counter freezing, back-off stages, and short retry limit to ensure compliance with IEEE 802.11ah IoT protocol requirements. It stresses the importance of taking these elements into consideration while modeling the efficiency and cost of the steganographic channel system. These parameters often result in a high precise channel access estimation, a more accurate and efficient accuracy measurements system, efficient channel utilisation, and ensuring that no packet is served endlessly. 3) Derivation of transmission probability, successful transmission probability, and collision probability is performed to express and compute the performance characteristics of the HICCUPS, such as the system’s throughput, efficiency and cost of WLAN usage in the network. The system usage cost (κ) is defined as the reduction of WLAN throughput caused by HICCUPS functioning in corrupted frame mode. The efficiency of a system (ε) is described as the throughput of the system in corrupt frame state.
The rest of the paper is arranged as follows: Section 2 presents the model analysis including the frame transmission probability in the corrupted frame mode as well as the data transmission time analysis. Section 3 describes the cost analysis κ. Section 4 discusses efficiency analysis ε. Section 5 concludes the paper.
In this section, the medium access procedure for nodes is formulated using two-dimension Markov Chain, then the system’s throughput, efficiency and cost of IEEE 802.11ah communication are derived. In Fig. 1, the Markov Chain model of the 802.11ah backoff mechanism within a Restricted Access Window (RAW) slot is shown in corrupted frame mode. This Markov Chain is adopted from [23–25] for unsaturated circumstances in the presence of error-prone channel. From the HCCNET’s WLAN viewpoint, communication is always unsuccessful due to a lack of valid checksums. Thus, steganogram transmission occurs at each stage of the backoff operation which allows us to predict the HCCNETs behaviour using the Markov chain-based model with probability of failure

Figure 1: The packets transmission process using Markov chain model

2.1 Frame Transmission Probability in the Corrupted Frame Mode
As seen in Fig. 1, the 2-D Markov chain model is used to determine the probability of frame transmission in the corrupted frame mode
The first case in Eq. (2) indicates that the back-off counter reduces when the channel is detected idle. The second case in Eq. (2) indicates that when the channel is noticed busy, the back-off counter is frozen. If a packet is not successfully transmitted, the back-off phase moves from
The non-null transition probabilities in this case represent the absence of packet transmission in the buffer that is forwarded to the idle state (I) after successful transmission.
Whenever the repeat limit is reached, the maximum back-off phase m and CW size value are reset to the minimum levels as shown in the first case of Eq. (3). Then, the node goes into idle mode if there are no more packets in the transmission queue. The second case in Eq. (3) denotes that the node stays in the idle mode if no new packets are received at the queue for transmission. The third case in Eq. (3) represents that the node goes from the idle mode to the back-off state k by uniformly selecting a back-off counter value in the range
Assume that
Due to the chain regularities, for each k
Since
Therefore, by applying the condition of stationary distribution normalisation,
We obtain Eq. (10) from Eq. (9), which is dependent on the values of m and
where:
And:
Since we have
Eq. (13) demonstrates that the
During transmission, the error frame probability
where
where the bit error rate
where
The probability of transmitting packets colliding is defined as follows:
We can calculate the packet transmission from Eqs. (13) and (18) by numerically solving the unknown variable
2.2 Data Transmission Time Analysis
In this subsection, the system throughput of HCCNETs in the corrupted frame mode

Figure 2: Time slots length for the packet process of transmission
Fig. 2 illustrates the time slot lengths for the packet process of transmission using the contention-based MAC for DATA frames. Thus, as in Eq. (20), the transmission time is calculated using the unicast mode.
where
Thus, the duration of the logical time slots
Eventually, the system throughput of HCCNETs in the corrupted frame mode
The cost
Assume that frame error rate increases with the fixed value △FER when applying HCCNETs as shown in Fig. 3. The frame error rate for networks without HCCNETs is equal to FER’. It can be seen that △FER ≤ 1 –
Then, it is normalised to R as:
Since the cost curves are derived on S(FER) and appear to be nearly linear, so, we may apply the following approximation formula for small values of △FER, as shown in Fig. 4:

Figure 3: Interpretation of ΔFER [12]

Figure 4: Illustration of the cost κ [12]
The cost values for IEEE 802.11ah (ERP-OFDM) are shown in Tabs. 2 and 3, when n = 10, 20, and R = 6.5 Mbps. These values, when L = 1000 bytes, are obtained from Eq. (26), and are computed for


The efficiency is defined as the
Since
Therefore

Figure 5: The efficiency ε illustration [12]
Eventually
And then normalize it to R as follows:
As cost analysis, we analyse an IEEE 802.11ah (ERP-OFDM) when R = 6.5 Mbps, L = 1000 bytes frames, n = 10, 20, and the same values of △FER (0.01; 0.02; 0.03; 0.04; 0.05). Tab. 4 shows the findings of the experiment.
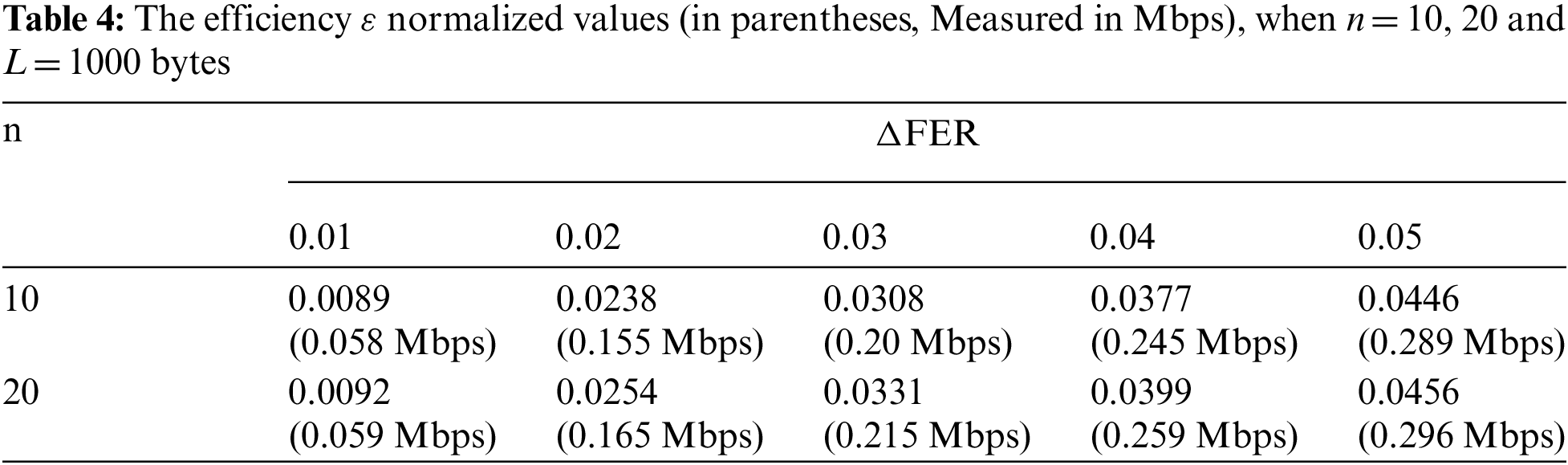
The cost relies on the frame error rate, while the efficiency relies only on the △FER. For instance, in IEEE 802.11ah (ERP-OFDM), when n= 10 stations, and △FER= 0.05 with R = 6.5 Mbps, the efficiency
This paper introduces one of the steganographic techniques called HCCNETs to evaluate the performance efficiency and the cost of system usage of the steganographic channel over IEEE 802.11ah IoT protocol. We begin by analysing the IEEE 802.11ah protocol using a two-dimensional Markov chain model under unsaturated situations with an imperfect transmission channel. The analysis of the 802.11ah IoT protocol is used to determine the transmission probability, successful transmission probability, and collision probability. Then, using these derivatives formulas, performance metrics for throughput, efficiency, and cost of system usage in the network are expressed and calculated. The influence of the channel conditions and node number is examined in order to evaluate and understand the efficiency and the cost of system usage in HICCUPS over 802.11ah IoT protocol. The analytical findings indicate that HICCUPS steganographic technique is significantly efficient with reasonable cost.
Future study will concentrate on simulation analysis of HCCNETs over IoT scheme in order to analyse HCCNETs characteristics in a variety of situations and to provide a comprehensive evaluation of the security of HCCNETs.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. R. Meng, Q. Cui, Z. Zhou, Z. Fu and X. Sun, “A steganography algorithm based on cyclegan for covert communication in the internet of things,” IEEE Access, vol. 7, pp. 90574–90584, 2019. [Google Scholar]
2. S. Doss, J. Paranthaman, S. Gopalakrishnan, A. Duraisamy, S. Pal et al., “Memetic optimization with cryptographic encryption for secure medical data transmission in IoT-based distributed systems,” Computers, Materials & Continua, vol. 66, no. 2, pp. 1577–1594, 2021. [Google Scholar]
3. A. Kamilaris and A. Pitsillides, “Mobile phone computing and the internet of things: A survey,” IEEE Internet of Things Journal, vol. 3, no. 6, pp. 885–898, 2016. [Google Scholar]
4. T. Qiu, R. Qiao and D. O. Wu, “EABS: An event-aware backpressure scheduling scheme for emergency internet of things,” IEEE Transactions on Mobile Computing, vol. 17, no. 1, pp. 72–84, 2017. [Google Scholar]
5. I. Qadeer and M. K. Ehsan, “Improved channel reciprocity for secure communication in next generation wireless systems,” Computers, Materials & Continua, vol. 67, no. 2, pp. 2619–2630, 2021. [Google Scholar]
6. T. Qiu, X. Wang, C. Chen, M. Atiquzzaman and L. Liu, “TMED: A spider-web-like transmission mechanism for emergency data in vehicular ad hoc networks,” IEEE Transactions on Vehicular Technology, vol. 67, no. 9, pp. 8682–8694, 2018. [Google Scholar]
7. Y. Xu, L. Qi, W. Dou and J. Yu, “Privacy-preserving and scalable service recommendation based on simhash in a distributed cloud environment,” Complexity, vol. 2017, pp. 9, 2017. [Google Scholar]
8. L. Qi, R. Wang, C. Hu, S. Li, Q. He et al., “Time-aware distributed service recommendation with privacy-preservation,” Information Sciences, vol. 480, pp. 354–364, 2019. [Google Scholar]
9. C. Hu, W. Li, X. Cheng, J. Yu, S. Wang et al., “A secure and verifiable access control scheme for big data storage in clouds,” IEEE Transactions on Big Data, vol. 4, no. 3, pp. 341–355, 2017. [Google Scholar]
10. L. Qi, S. Meng, X. Zhang, R. Wang, X. Xu et al., “An exception handling approach for privacy-preserving service recommendation failure in a cloud environment,” Sensors, vol. 18, no. 7, pp. 2037, 2018. [Google Scholar]
11. A. A. Abd El-Latif, B. Abd-El-Atty, M. S. Hossain, S. Elmougy and A. Ghoneim, “Secure quantum steganography protocol for fog cloud internet of things,” IEEE Access, vol. 6, pp. 10332–10340, 2018. [Google Scholar]
12. K. Szczypiorski, “A performance analysis of HICCUPS—A steganographic system for WLAN,” Telecommunication Systems, vol. 49, no. 2, pp. 255–259, 2012. [Google Scholar]
13. K. Szczypiorski and W. Mazurczyk, “Steganography in IEEE 802.11 OFDM symbols,” Security and Communication Networks, vol. 9, no. 2, pp. 118–129, 2016. [Google Scholar]
14. K. Szczypiorski and W. Mazurczyk, “Hiding data in OFDM symbols of IEEE 802.11 networks,” in 2010 Int. Conf. on Multimedia Information Networking and Security, pp. 835–840, Nanjing, China, IEEE, 2010. [Google Scholar]
15. M. Khari, A. K. Garg, A. H. Gandomi, R. Gupta, R. Patan et al., “Securing data in internet of things (IoT) using cryptography and steganography techniques,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 50, no. 1, pp. 73–80, 2019. [Google Scholar]
16. R. Meng, S. G. Rice, J. Wang and X. Sun, “A fusion steganographic algorithm based on faster R-CNN,” Computers, Materials & Continua, vol. 55, no. 1, pp. 1–16, 2018. [Google Scholar]
17. M. Smolarczyk, K. Szczypiorski and J. Pawluk, “Multilayer detection of network steganography,” Electronics, vol. 9, no. 12, pp. 2128, 2020. [Google Scholar]
18. S. Chen and Z. Qu, “Novel quantum video steganography and authentication protocol with large payload,” International Journal of Theoretical Physics, vol. 57, no. 12, pp. 3689–3701, 2018. [Google Scholar]
19. B. Lipinski, W. Mazurczyk and K. Szczypiorski, “Improving hard disk contention-based covert channel in cloud computing,” in 2014 IEEE Security and Privacy Workshops, pp. 100–107, San Jose, CA, USA, IEEE, 2014. [Google Scholar]
20. Z. Zhou, Y. Cao, M. Wang, E. Fan and Q. Wu, “Faster-RCNN based robust coverless information hiding system in cloud environment,” IEEE Access, vol. 7, pp. 179891–179897, 2019. [Google Scholar]
21. P. Praveenkumar, M. Nagadinesh, P. Lakshmi, K. Thenmozhi, J. B. Rayappan et al., “Convolution & viterbi EN (DE) coders on OFDM hides, rides & conveys message—A neural STEGO,” in 2013 Int. Conf. on Computer Communication and Informatics, pp. 1–5, Coimbatore, India, IEEE, 2013. [Google Scholar]
22. C. Song, G. Tan, C. Yu, N. Ding and F. Zhang, “APDM: An adaptive multi-priority distributed multichannel MAC protocol for vehicular ad hoc networks in unsaturated conditions,” Computer Communications, vol. 104, pp. 119–133, 2017. [Google Scholar]
23. A. A. Almohammedi and V. Shepelev, “Saturation throughput analysis of steganography in the IEEE 802.11 p protocol in the presence of non-ideal transmission channel,” IEEE Access, vol. 9, pp. 14459–14469, 2021. [Google Scholar]
24. A. A. Almohammedi, N. K. Noordin, A. Sali, F. Hashim, W. A. Jabbar et al., “Modeling and analysis of IEEE 1609.4 MAC in the presence of error-prone channels,” International Journal of Electrical & Computer Engineering, vol. 9, no. 5, pp. 3531–3541, 2019. [Google Scholar]
25. A. A. Almohammedi, N. K. Noordin, A. Sali, F. Hashim and S. Saeed, “A comprehensive performance analysis of IEEE 802.11 p based MAC for vehicular communications under non-saturated conditions,” Journal of ICT Research & Applications, vol. 11, no. 1, pp. 92–113, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |