DOI:10.32604/cmc.2022.026820

| Computers, Materials & Continua DOI:10.32604/cmc.2022.026820 |  |
| Article |
Policy-Based Group Signature Scheme from Lattice
1School of Computer Science and Technology, Henan Polytechnic University, Jiaozuo, 454000, China
2School of Electronic Engineering, Dublin City University, Dublin 9, Ireland
*Corresponding Author: Qing Ye. Email: yeqing@hpu.edu.cn
Received: 05 January 2022; Accepted: 23 February 2022
Abstract: Although the existing group signature schemes from lattice have been optimized for efficiency, the signing abilities of each member in the group are relatively single. It may not be suitable for complex applications. Inspired by the pioneering work of Bellare and Fuchsbauer, we present a primitive called policy-based group signature. In policy-based group signatures, group members can on behalf of the group to sign documents that meet their own policies, and the generated signatures will not leak the identity and policies of the signer. Moreover, the group administrator is allowed to reveal the identity of signer when a controversy occurs. Through the analysis of application scenarios, we concluded that the policy-based group signature needs to meet two essential security properties: simulatability and traceability. And we construct a scheme of policy-based group signature from lattice through techniques such as commitment, zero-knowledge proof, rejection sampling. The security of our scheme is proved to be reduced to the module short integer solution (MSIS) and module learning with errors (MLWE) hard assumptions. Furthermore, we make a performance comparison between our scheme and three lattice-based group signature schemes. The result shows that our scheme has more advantages in storage overhead and the sizes of key and signature are decreased roughly by 83.13%, 46.01%, respectively, compared with other schemes.
Keywords: Group signature; policy-based signature; lattice-based cryptography; zero-knowledge proof
Policy-based signature (PBS) is a novel concept of digital signature, which was proposed by Bellare et al. [1] at PKC 2014. PBS requires that signer can only sign documents that satisfy certain policy conditions. The users that do not satisfy the policy conditions cannot possess the ability of legitimate signers, and the signatures will not leak the identity and policy of signers. In [1] introduced two strong security notions: simulatability and extractability. The simulatability means that a legitimate signature is indistinguishable from a simulated signature, which is generated by a signature simulator that does not need signing key or policy; the extractability means that there is an extractor, which is able to extract information of policy and identity from a legitimate signature, but cannot extract from forged signatures generated by an attacker. The simulatability and extractability are strong forms of indistinguishability, and unforgeability respectively according to [1]. With the two security notions, PBS will be effectively applied in hierarchical environment. For instance, in an enterprise, the authority expects that the employees in different departments or positions to have different signing abilities. Specifically, the employees in research department can only sign documents related to the research, and employees in finance department can only sign documents related to the finance. In 2016, Cheng et al. [2] constructed a scheme of PBS from lattice assumptions based on a zero-knowledge argument system and Bonsai tree.
Group signatures (GS) was proposed by Chaum et al. [3], which is an important cryptographic primitive. In GS, legitimate group members can represent the group to sign documents anonymously (anonymity); and the group administrator is allowed to open a signature by the tracking key to obtain the identity of signer (traceability). Due to the two properties of anonymity and traceability, GS can be applied in a variety of scenarios, such as e-commerce systems, trusted computing platforms, electronic voting, and much more.
In recent years, with the breakthroughs in quantum research, GS schemes based on hard assumptions of lattice have attracted the attention of scholars. In 2010, Gordon et al. [4] designed the first GS scheme from lattice in random oracle model (ROM) by the technology of GPV trapdoor, as well as the anonymity and traceability of the scheme can be reduced to the hard assumptions of learning with errors (LWE) and GapSVP respectively. But the storage overhead of keys and signature of their scheme is relatively large, which is linear with the number of group members. In 2013, Laguillaumie et al. [5] constructed a GS scheme with logarithmic size based on the non-interactive zero-knowledge proof of knowledge (NIZKPoK) under the hard assumptions of short integer solution (SIS) and LWE. Since then, a series of GS from lattice based on NIZKPoK have been proposed [6–10], and their storage cost has reached logarithmic size. Later, the constant-size GS are constructed by Ling et al. [11] and Zhang et al. [12]. The former is based on the “confined guessing” technique of Ducas et al. signature scheme [13]; and the latter uses a compact and scalable identity-encoding technique. Their schemes make the storage cost of keys and signatures independent of the number of group members. However, the NIZKPoK in the above GS schemes needs enough parallel repetition during execution due to its soundness error. This will cause a large cost of parameter and time so that the size of the keys and signature is still large, although it is independent of the number of group members. Therefore, Pino et al. [14] designed a new zero-knowledge proof protocol based on the signature scheme of [15] under the hard assumptions of MSIS and MLWE. Since this protocol limits the size of the message and challenge space, it has a smaller cost of parameter and time compared to other zero-knowledge proof protocols. The GS scheme based on this protocol also has more advantages in the storage overhead of the key and signature. Similarly, Boschini et al. [16] constructed a floppy-sized GS scheme by relaxed zero-knowledge proofs under the hard assumptions of ring short integer solution (RSIS) and ring learning with errors (RLWE). In 2019, a GS scheme without NIZK from lattice was designed by Katsumata et al. [17], but this construction requires a combination of attribute-based encryption and signatures. In 2020, Sun et al. [18] and Canard et al. [19] designed an improved scheme based on [17]. In conclusion, with the deepening of research in the field of GS from lattice, the size of GS has been effectively reduced. However, the above GS schemes from lattice are just be applied in the scenarios where the signing capabilities of the group members are relatively consistent. However, the different signing capabilities of each group member are necessary for the GS scheme in actual scenarios, i.e., enterprises involving multiple departments, electronic voting for multiple regions, and much more. Therefore, GS requires a new primitive to be suitable for more extensive scenarios.
In this work, we will define a concept of policy-based group signature (PBGS) based on previous work. Consider the following simple situation: Alice, Bob and Carol are employees of a company. The former two are from the research department and the latter is from the finance department. The authority of the company wants to develop a policy, which Alice, Bob and Carol are only allowed to sign documents that only related to their own department. At the same time, the signatures they generate can represent the company, and the identity of the signer will not be leaked. But if one day a document related to the research department causes a dispute (assuming Bob is the actual signer), the administrator of the company should be allowed to recover the identity of the signer (Bob) by the tracking key. In the above case, Alice, Bob and Carol are required to have different signing capabilities. Thus, the previous GS are not suitable. However, for PBGS, the authority wishes that Alice, Bob and Carol will be distributed signing keys and policies related to the department so that their signing capabilities will differ depending on the policy. The group member will not be able to sign when his policy does not satisfy some relationship with the document to be signed (unforgeability); Alice, Bob, Caro, or other outsiders of the company are unable to know the identity of the signer from a signature (simulatability). Even if given a signature related to the finance department, of which Carol is the only one employee, Carol is still anonymous due to the distribution of policies is a secret. The identity of the signer will be recovered through the PBGS administrator by the tracking key (traceability). In conclusion, the PBGS scheme in the application scenario needs to meet the following security requirements: simulatability, unforgeability and traceability. However, according to the definition of [20], unforgeability is unnecessary for GS because traceability has implied unforgeability. The same is true for the extractability defined in PBS. Therefore, we have extracted two security properties for PBGS: simulatability and traceability. With the above two security properties, PBGS will be applied in a wide range of fields. In addition to the enterprises involving multiple departments, the application of PBGS also includes hierarchical electronic voting for multiple regions, digital copyright management, and much more [21–23].
We show a construction of policy-based group signatures from lattice for the above primitive of PBGS, and it can resist the attacks of existing quantum algorithms. Our scheme satisfies the simulatability and full traceability in ROM under the security model of PBGS defined in Section 3.2. And the simulatability and full traceability are proved to be reduced to MLWE and MSIS assumptions, respectively. In terms of efficiency analysis, our scheme is compared with the three schemes of GS from lattice [11,16,17] in storage overhead. The analysis results show that the storage costs of our scheme are totally independent of the number of group members. The size of the key and signature are of order
At a high level, our PBGS scheme follows a template similar but not identical to the conventional GS defined by Bellare et al. [20]. In conventional GS, the public key, master key and traceability key are generated during the setup phase. But for PBGS, the policy relation also needs to be established to limit the signing ability of group members in the initial phase. After that, the key generation center (KGC) will distribute the policy and the signing key to the group members. During the signature generation process, an efficient NIZKPoK about policy and signing keys is generated by group members. But if the policy of group members cannot satisfy the policy relation with the message to be signed, the signature algorithm will not be executed. Finally, in order to ensure full traceability, a verifiable encryption for identity will be generated by the group members. And then, the group administrator is allowed to decrypt the identity of the signer by the tracking key.
Specifically, we first review the requirements of policy language defined by [2]: (1) the space of message
It satisfies the above requirements of the policy language, and its hardness is based on the LWE hard assumption.
In the signature generation phase, the signer needs to possess policy
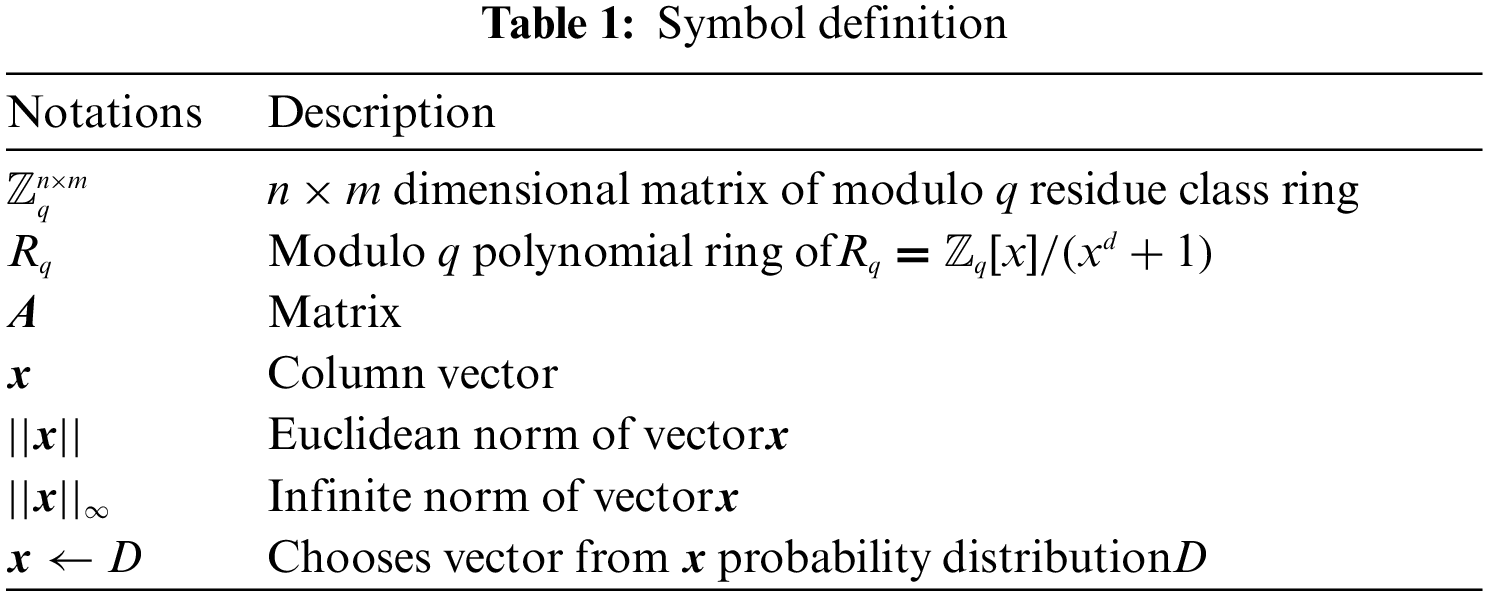
The symbols that appear in this article are described in Tab. 1.
Definition 1 (
Lemma 1 [27] For any
Definition 2 (
Lemma 2 [27] For
As discussed in [28], the practical hardness of the above assumptions is not affected by the parameter m to resist known attacks. Therefore, the assumptions will be simply written
2.3 Discrete Gaussian Distribution and Rejection Sampling
Given any
We will simply write
Lemma 3 [14] For any
(1)
(2)
At EUROCRYPT 2012, Lyubasevsky introduced an algorithm of rejection sampling, which can be executed with a certain probability. The description is as follows:

Lemma 4 [14,29,30] For
Lemma 5 [16,24,31] Given positive integer n, m, q, i, parameter
Definition 3 (Commitment [25]) Given challenge space
If the following equation holds:
We call
Lemma 6 [25] The above commitments have the following properties:
(1) (Binding) Let
(2) (Hiding) For
The detailed proof of the above lemma could be found in the work [14,25].
3 Definition of Policy-Based Group Signature and Security Model
Definition 4 (PBGS) A policy-based group signature composed of five polynomial-time algorithms:
(1) GSetup (
(2) KeyGen (
(3) Sign (
(4) Verify (
(5) Open (
A PBGS scheme should meet three security properties: correctness, simulatability and traceability. Correctness, is defined in Definition 5 detailedly, includes verification correctness and opening correctness. Simulatability implies that the attacker cannot confirm the identity of the signer through a signature because a valid signature is indistinguishable from a simulated signature. Please refer to Definition 6 for details. Traceability means that a valid signature should be opened through group administrator by the tracking key so that the identity of the signer is restored. Our scheme meets full traceability, which is defined in Definition 7 detailedly. Furthermore, anonymity and unforgeability could be unnecessary for PBGS. We will discuss this issue later in Section 3.3.
Definition 5 (Correctness) The correctness of the PBGS contains verification correctness and opening correctness. The verification correctness means that the probability of returning “Invalid” from the algorithm Verify is negligible for a signature generated honestly. That is:
The opening correctness means that the probability of returning
Definition 6 (Simulatability) The simulatability requires that there is a simulator SimSign(M), which generates signatures without the need for any signing key or policy. Then the simulated signatures generated by SimSign(M) are indistinguishable from the signatures generated honestly. The simulatability game
Setup:
Queries:
Challenge:
Finalization:
The advantage of
If
Definition 7 (Full Traceability [20]) Full traceability is a strong form of traceability. It asks that a team of group members who concentrate their signing keys is unable to generate a valid signature, which could not be caught by the open algorithm. Even though the colluding group knows the tracking key of group manager, that is true. The full traceability game
Setup:
Queries:
• Request for the signing key of member
• Request for the signature about any message M on identity i and policy
Finalization:
The advantage of
If
As described in Section 1.3, the anonymity and unforgeability are unnecessary. First, the normal anonymity does not always provide the privacy for the policy relevant to the key and witness [1]. To see this, there is a policy relation such that for every message M, only one policy p satisfies
In this section, we present a ZKPoK protocol
First, fix parameters
•
•
•
The interaction between the two parties is as follows:

Theorem 1 Given
• Correctness: The prover
• Honest-Verifier Zero-Knowledge: An honest verifier can simulate the transcripts with statistically indistinguishable distribution when the protocol is not aborted.
• Special Soundness: A valid opening of commitment
Proof.
Correctness: If
Honest-Verifier Zero-Knowledge: We only show that the protocol
We will get that the transcripts generated by the simulation algorithm
Special Soundness: Let
such that
The protocol
In this section, we show a scheme of PBGS from lattice specifically.
GSetup (
Given a security parameter
(a) Select
(b) Select
(c) Select
(d) Select
(e) Select
(f) Output
KeyGen (
Given group master private key
(a)
(b) Output the signing key
Sign (
Given signing key
(a) If
(b) Select
(c) Set
(d) Select
(e) Set
(f) Set
(g) Generate a NIZKPoK
•
•
•
(h) Output the signature
Verify (
Given gpk, signature
(a) Recover
(b) Perform the verification in Section 4.1. If the verification algorithm accepts the
Open (
Given tracking key gtk and signature
(a) If the algorithm Verify returns “Invalid” for the signature
(b) Select
(c) Set
(d) Compute
Theorem 2 (Correctness) The proposed PBGS scheme is correct with overwhelming probability.
Proof:
1) Verification correctness
For
2) Opening correctness
In signing phase, the signer generates verifiable ciphertext
And the following equation holds:
According to [26], we know that
From which we get
Theorem 3 (Simulatability) The proposed PBGS scheme meets simulatability defined in Definition 6 under ROM, if the
Proof: We will construct a PPT algorithm SimSign, which returns a simulated signature
1) For commitments
2) For NIZKPoK
3) For ciphertext
As a result, the algorithm SimSign is able to generate a simulated signature
After obtaining the algorithm SimSign, challenger
Since the simulated signature
Theorem 4 (Full Traceability) The proposed PBGS scheme meets full traceability defined in Definition 7 under ROM, if the
Proof: Assume that an attacker
Finally,
Multiplying by
where
Then
And the bound on the norm of the solution satisfies:
Hence,
In this section, we choose three schemes of GS from lattice to carry out efficiency analysis and comparison with our scheme. We will perform a detailed analysis of the storage overhead of group public key, administrator tracking key, members signing key and signature. Firstly, we fix the security parameter
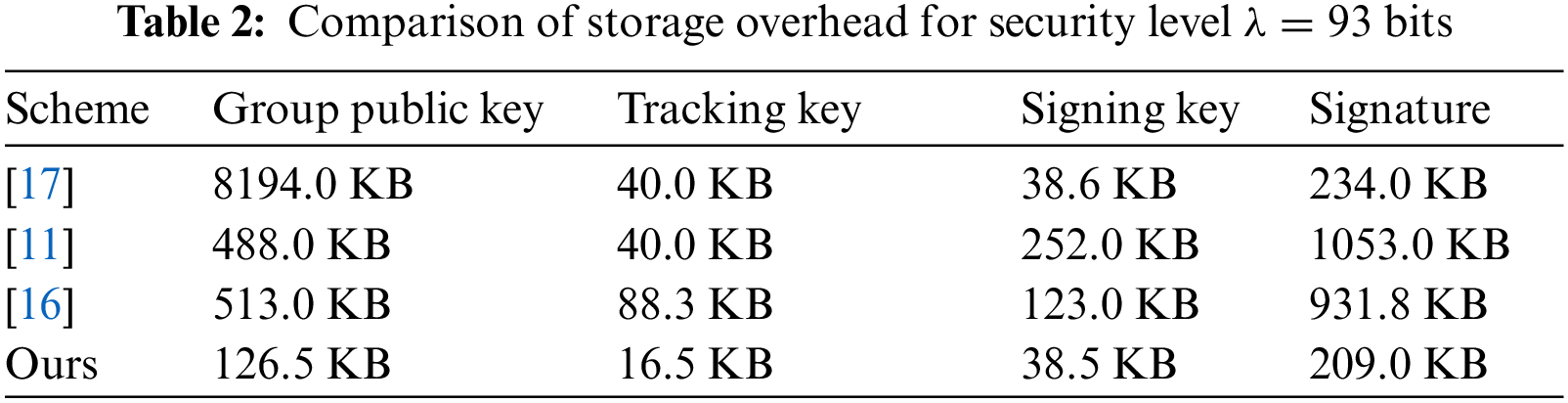
Compared with the above three schemes of GS, our construction has lower storage overhead on key and signature to a certain extent. The size of key decreased roughly by 83.13% and the size of signature is also decreased roughly by 46.01%.
Funding Statement: This work is supported by the National Natural Science Foundation of China (61802117), Support Plan of Scientific and Technological Innovation Team in Universities of Henan Province (20IRTSTHN013), the Youth Backbone Teacher Support Program of Henan Polytechnic University under Grant (2018XQG-10).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. Bellare and G. Fuchsbauer, “Policy-based signatures,” in Public-Key Cryptography, PKC 2014. Proc.: Lecture Notes in Computer Science (LNCS 8383), Berlin, Germany, pp. 520–537, 2014. [Google Scholar]
2. S. Cheng, K. Nguyen and H. Wang, “Policy-based signature scheme from lattices,” Designs, Codes and Cryptography, vol. 81, no. 1, pp. 43–74, 2016. [Google Scholar]
3. D. Chaum and E. V. Heyst, “Group signatures,” in EUROCRYPT 1991. Proc.: Lecture Notes in Computer Science (LNCS 547), Berlin, Germany, pp. 257–265, 1991. [Google Scholar]
4. S. D. Gordon, J. Katz and V. Vaikuntanathan, “A group signature scheme from lattice assumptions,” in ASIACRYPT 2010. Proc.: Lecture Notes in Computer Science (LNCS 6477), Berlin, Germany, pp. 395–412, 2010. [Google Scholar]
5. F. Laguillaumie, A. Langlois, B. Libert and D. Stehlé, “Lattice-based group signatures with logarithmic signature size,” in ASIACRYPT 2013. Proc.: Lecture Notes in Computer Science (LNCS 8270), Berlin, Germany, pp. 41–61, 2013. [Google Scholar]
6. S. Ling, K. Nguyen and H. Wang, “Group signatures from lattices: simpler, tighter, shorter, ring-based,” in Public-Key Cryptography, PKC 2015. Proc.: Lecture Notes in Computer Science (LNCS 9020), Berlin, Germany, pp. 427–449, 2015. [Google Scholar]
7. B. Libert, S. Ling, F. Mouhartem, K. Nguyen and H. Wang, “Signature schemes with efficient protocols and dynamic group signatures from lattice assumptions,” in ASIACRYPT 2016. Proc.: Lecture Notes in Computer Science (LNCS 10032), Berlin, Germany, pp. 373–403, 2016. [Google Scholar]
8. B. Libert, S. Ling, K. Nguyen and H. Wang, “Zero-knowledge arguments for lattice-based accumulators: Logarithmic-size ring signatures and group signatures without trapdoors,” in EUROCRYPT 2016. Proc.: Lecture Notes in Computer Science (LNCS 9666), Berlin, Germany, pp. 1–31, 2016. [Google Scholar]
9. B. Libert, F. Mouhartem and K. Nguyen, “A Lattice-based group signature scheme with message-dependent opening,” in Applied Cryptography and Network Security, ACNS 2016. Proc.: Lecture Notes in Computer Science (LNCS 9696), Cham, Switzerland, pp. 137–155, 2016. [Google Scholar]
10. S. Ling, K. Nguyen, H. Wang and Y. Xu, “Lattice-based group signatures: achieving full dynamicity with ease,” in Applied Cryptography and Network Security, ACNS 2017. Proc.: Lecture Notes in Computer Science (LNCS 10355), Cham, Switzerland, pp. 293–312, 2017. [Google Scholar]
11. S. Ling, K. Nguyen, H. Wang and Y. Xu, “Constant-size group signatures from lattices,” in Public-Key Cryptography, PKC 2018. Proc.: Lecture Notes in Computer Science (LNCS 10770), Cham, Switzerland, pp. 58–88, 2018. [Google Scholar]
12. Y. Zhang, X. Liu, Y. Yin, Q. Zhang and H. Jia, “On new zero-knowledge proofs for fully anonymous lattice-based group signature scheme with verifier-local revocation,” in Applied Cryptography and Network Security, ACNS 2020. Proc.: Lecture Notes in Computer Science (LNCS 12418), Cham, Switzerland, pp. 381–399, 2020. [Google Scholar]
13. L. Ducas and D. Micciancio, “Improved short lattice signatures in the standard model,” in CRYPTO 2014. Proc.: Lecture Notes in Computer Science (LNCS 8616), Berlin, Germany, pp. 335–352, 2014. [Google Scholar]
14. R. Pino, V. Lyubashevsky and G. Seiler, “Lattice-based group signatures and zero-knowledge proofs of automorphism stability,” in Proc. ACM SIGSAC Conf. on Computer and Communications Security, New York City, NY, USA, pp. 574–591, 2018. [Google Scholar]
15. S. Agrawal, D. Boneh and X. Boyen, “Lattice basis delegation in fixed dimension and shorter-ciphertext hierarchical IBE,” in CRYPTO 2010. Proc.: Lecture Notes in Computer Science (LNCS 6223), Berlin, Germany, pp. 98–115, 2010. [Google Scholar]
16. C. Boschini, J. Camenisch and G. Neven, “Floppy-sized group signatures from lattices,” in Applied Cryptography and Network Security, ACNS 2018. Proc.: Lecture Notes in Computer Science (LNCS 10892), Cham, Switzerland, pp. 163–182, 2018. [Google Scholar]
17. S. Katsumata and S. Yamada, “Group signatures without NIZK: from lattices in the standard model,” in EUROCRYPT 2019. Proc.: Lecture Notes in Computer Science (LNCS 11478), Cham, Switzerland, pp. 312–344, 2019. [Google Scholar]
18. Y. Sun and Y. Liu, “A Lattice-based fully dynamic group signature scheme without NIZK,” in Information Security and Cryptology, Inscrypt 2020. Proc.: Lecture Notes in Computer Science (LNCS 12612), Cham, Switzerland, pp. 359–367, 2020. [Google Scholar]
19. S. Canard, A. Georgescu, G. Kaim, A. R. Langlois and J. Traoré, “Constant-size lattice-based group signature with forward security in the standard model,” in Provable and Practical Security, ProvSec 2020. Proc.: Lecture Notes in Computer Science (LNCS 12505), Cham, Switzerland, pp. 24–44, 2020. [Google Scholar]
20. M. Bellare, D. Micciancio and B. Warinschi, “Foundations of group signatures: Formal definitions, simplified requirements, and a construction based on general assumptions,” in EUROCRYPT 2003. Proc.: Lecture Notes in Computer Science (LNCS 2656), Berlin, Germany, pp. 614–629, 2003. [Google Scholar]
21. S. Doss, J. Paranthaman, S. Gopalakrishnan, A. Duraisamy, S. Pal et al., “Memetic optimization with cryptographic encryption for secure medical data transmission in IoT-based distributed systems,” Computers, Materials & Continua, vol. 66, no. 2, pp. 1577–1594, 2021. [Google Scholar]
22. X. Zhang, X. Sun, X. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
23. X. Zhang, W. Zhang, W. Sun, X. Sun and S. K. Jha, “A robust 3-D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
24. D. Micciancio and C. Peikert, “Trapdoors for lattices: Simpler, tighter, faster, smaller,” in EUROCRYPT 2012. Proc.: Lecture Notes in Computer Science (LNCS 7237), Berlin, Germany, pp. 700–718, 2012. [Google Scholar]
25. C. Baum, I. Damgård, V. Lyubashevsky, S. Oechsner and C. Peikert, “More efficient commitments from structured lattice assumptions,” in Security and Cryptography for Networks, SCN 2018. Proc.: Lecture Notes in Computer Science (LNCS 11035), Cham, Switzerland, pp. 614–629, 2018. [Google Scholar]
26. V. Lyubashevsky and G. Neven, “One-shot verifiable encryption from lattices,” in EUROCRYPT 2017. Proc.: Lecture Notes in Computer Science (LNCS 10210), Cham, Switzerland, pp. 293–323, 2017. [Google Scholar]
27. A. Langlois and D. Stehlé, “Worst-case to average-case reductions for module lattices,” Designs, Codes and Cryptography, vol. 75, no. 1, pp. 565–599, 2015. [Google Scholar]
28. V. Lyubashevsky, K. Nguyen and G. Seiler, “Practical lattice-based zero-knowledge proofs for integer relations,” in Proc. ACM SIGSAC Conf. on Computer and Communications Security, New York City, NY, USA, pp. 1051–1070, 2020. [Google Scholar]
29. V. Lyubashevsky, “Lattice signatures without trapdoors,” in EUROCRYPT 2012. Proc.: Lecture Notes in Computer Science (LNCS 7237), Berlin, Germany, pp. 738–755, 2012. [Google Scholar]
30. G. Xu, Y. Cao, S. Xu, K. Xiao, X. Liu et al., “A novel post-quantum blind signature for log system in blockchain,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 945–958, 2022. [Google Scholar]
31. L. Mei, C. Xu, L. Xu, X. Yu and C. Zuo, “Verifiable identity-based encryption with keyword search for IoT from lattice,” Computers, Materials & Continua, vol. 68, no. 2, pp. 2299–2314, 2021. [Google Scholar]
32. M. Bellare and G. Neven, “Multi-signatures in the plain public-key model and a general forking lemma,” in Proc. 13th ACM Conf. on Computer and Communications Security, New York City, NY, USA, pp. 390–399, 2006. [Google Scholar]
33. N. Gama and P. Q. Nguyen, “Predicting lattice reduction,” in EUROCRYPT 2008. Proc.: Lecture Notes in Computer Science (LNCS 4965), Berlin, Germany, pp. 31–51, 2008. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |