DOI:10.32604/cmc.2022.027118

| Computers, Materials & Continua DOI:10.32604/cmc.2022.027118 |  |
| Article |
Lightweight Authentication Protocol Based on Physical Unclonable Function
1Zhejiang Lab, Hangzhou, 311121, China
2Zhejiang University, Hangzhou, 310058, China
3Tsinghua University, Beijing, 100084, China
4The University of British Columbia, Vancouver, V1V1V7, Canada
*Corresponding Author: Tao Zou. Email: zout@zhejianglab.com
Received: 11 January 2022; Accepted: 04 March 2022
Abstract: In the emerging Industrial Internet of Things (IIoT), authentication problems have become an urgent issue for massive resource-constrained devices because traditional costly security mechanisms are not suitable for them. The security protocol designed for resource-constrained systems should not only be secure but also efficient in terms of usage of energy, storage, and processing. Although recently many lightweight schemes have been proposed, to the best of our knowledge, they are unable to address the problem of privacy preservation with the resistance of Denial of Service (DoS) attacks in a practical way. In this paper, we propose a lightweight authentication protocol based on the Physically Unclonable Function (PUF) to overcome the limitations of existing schemes. The protocol provides an ingenious authentication and synchronization mechanism to solve the contradictions amount forward secrecy, DoS attacks, and resource-constrained. The performance analysis and comparison show that the proposed scheme can better improve the authentication security and efficiency for resource-constrained systems in IIoT.
Keywords: Lightweight; authentication; physically unclonable functions
With the development of Internet of Things (IoT) technology, machine-to-machine (M2M) communication supports various applications for monitoring and control in such areas as eHealth, smart factory, and smart city. The research by Gartner [1] estimates that up to $2.5 million will be spent on sensing devices/actuators in a single minute by 2021, which means that the IoT devices will not only be used in home or office but also deployed in industrial manufacture, known as Industrial IoT or Industrial 4.0. A typical IIoT scenario primarily comprises the sensors, actuators, and other devices that periodically capture data of their immediate surroundings. A specific resource-constrained IIoT system is depicted in Fig. 1.

Figure 1: Typical resource-constrained IIoT system
Since the development of openness and extensive interconnection in IIoT, security has become a global challenge in M2M communication. Although authentication is the cornerstone of providing adequate protection, and numerous schemes have been proposed to ensure security in traditional IT networks [2–10], these schemes cannot be readily applied for IIoT. Because in IIoT, many resource-constrained devices are limited to computation power and communication bandwidth, such as Radio Frequency Identification (RFID) chips, wireless sensors, and so on. Therefore, it is essential to reduce the operational cost while ensuring the authentication protocol’s security for resource-constrained devices. This paper proposes a lightweight authentication protocol based on a series of operations, namely Physically Unclonable Functions (PUF), hash function, and exclusive-OR (XOR) operations, respectively, to provide mutual authentication between resource-constrained IIoT devices and gateway. The proposed protocol guarantees a higher degree of practicality, efficiency, and security than existing schemes.
Over the past years, some lightweight authentication schemes for IIoT have been proposed, which can be divided into two categories: hash-based schemes and PUF based schemes. Hash-based methods are designed only on the hash function, which cannot guarantee security against cloning attacks. On the contrary, PUF based methods add Physically Unclonable Functions to the authentication process on the foundation of a hash-based scheme to resist cloning attacks. A PUF is considered a unique physical feature of an electronic device, just like biometric features like fingerprints. When queried with a challenge C, it generates a response R that depends on both C and the specific physical properties of the device that cannot be reproduced or cloned, i.e.,
In 2012, Kardas et al. [11] proposed an RFID authentication scheme based on PUFs. However, this protocol cannot ensure forward secrecy and resilience of DoS [12] attacks. Hereafter, Akgun et al. [13] proposed another PUF based protocol. Regrettably, their scheme cannot ensure forward secrecy, which is an imperative security requirement for the authentication protocol. In 2017,Esfahani et al. [14] proposed a hash-based authentication scheme for M2M communication, but the protocol is vulnerable to traceability, impersonation, DoS, and cloning attacks. Recently, Gope et al. [15] proposed a novel PUF based scheme and claimed that the protocol is more practical and can overcome the limitations of existing schemes, especially ensuring forward secrecy and resilience of DoS attacks simultaneously. However, according to our analysis, the DoS resistance mechanism of their protocol is impractical. In their scheme, the additional use of emergency challenge and response pairs (i.e., the
To solve the problems in the existing authentication schemes above, we proposed a lightweight PUF based authentication protocol in this paper. Our new method achieves higher security, efficiency, and practicality compared to the existing schemes. Furthermore, our protocol’s novel authenticationand synchronization recovery mechanism can better deal with the problem between forward secrecy and resilience of DoS attacks that cannot be well resolved in the existing schemes.
In this section, we describe the proposed lightweight authentication protocol for resource-constrained devices in IIoT. The proposed scheme has two phases: registration and authentication. The symbols and cryptographic functions used in this article are defined in Tab. 1.

Each resource-constrained device should be registered into the backend server through a secure channel. Firstly, the server generates a random challenge

Figure 2: Registration phase of the proposed scheme
This phase achieves authentication between the resource-constrained devices (abbreviated as D), gateway, and the backend server. Since each gateway is connected to the server through a secure wired link, we consider the gateway and server as a single unit GSU in the authentication phase. For that, the authentication phase consists of the following steps. The details of the authentication phase are depicted in Fig. 3.

Figure 3: Authentication phase of the proposed scheme
(1) The D generates a random number
(2) Upon receiving the
(3) After receiving the GSU’s response message, the D uses
(4) Upon receiving the response message from D, GSU first computes
In the case of the DoS attacks, the resynchronization mechanism will be executed by our scheme. When the GSU rejects the authentication request from D for the first time, where the temporary identity
In this section, the security analysis shows that our scheme can overcome several imperative security properties and the malicious behaviors assumed in the security properties. Through both the rigorous informal and formal security analysis, we figure out that our proposed scheme achieves the desired security features to tolerate various known attacks in authentication in IIoT.
4.1 Informal Security Analysis
Anonymity includes untraceability and unlinkability. Untraceability means that an adversary cannot identify which identities from the same group belong to whom. In comparison, unlinkability implies that an adversary cannot distinguish whether two identities belong to the same user. In our proposed scheme, the devices don’t reveal their real identities or secrets during each authentication instance since all the transmitted messages are computed with a random number. Hence, the devices are not traceable to the adversary with temporary identities or other secrets. Moreover, the temporary identities
The transmitted messages
In the authentication phase, mutual authentication between the D and GSU can be achieved based on the verified messages
An authentication protocol should provide forward secrecy to protect past sessions against future compromises of the secret keys. In our protocol, after completing each successful mutual authentication, the challenge parameter
4.1.5 The Resilience of DoS Attacks
Since both communicators need to update their secret security credentials to ensure forward secrecy, an attacker can cause a desynchronization problem by blocking the messages between two communicators, eventually causing the DoS problem. As mentioned in sect.2, almost all the existing lightweight authentication protocols fail to deal with the problem of forward secrecy and DoS attacks at once. In our proposed scheme, we utilize an ingenious resynchronization mechanism to cope with this problem. Since D and GSU update temporary identity
4.1.6 The Resilience of Clone Card Attack
An attacker can capture a valid device and access secrets stored in it to produce the cloned devices. Since PUF is based on a unique and complex physical characteristic, in our proposed scheme, even if the attackers obtain the device’s memory (i.e., the
This section conducts a formal security verification using the widely accepted Automated Validation of Internet Security Protocols and Applications (AVISPA) [16] tool to demonstrate that our protocol fulfills the required security properties. It provides a modular and expressive formal language for specifying protocols and their security properties and integrates different backends that implement various state-of-the-art automatic analysis techniques. The formal security verification and the results of our protocol using OFMC backend are depicted in Fig. 4. The details of the HLPSL code are provided in the supplementary material at https://github.com/lhguestc/AVISPA.

Figure 4: The result of the analysis of the proposed scheme using OFMC
5 Performance Analysis and Comparison
5.1 Security Feature Comparison
In this section, we compare some critical security properties of our protocol with recently proposed schemes. From Tab. 2, we can see that our protocol can satisfy all the important required security requirements. Particularly, only our scheme can better ensure forward secrecy with the resistance of the DoS attack.
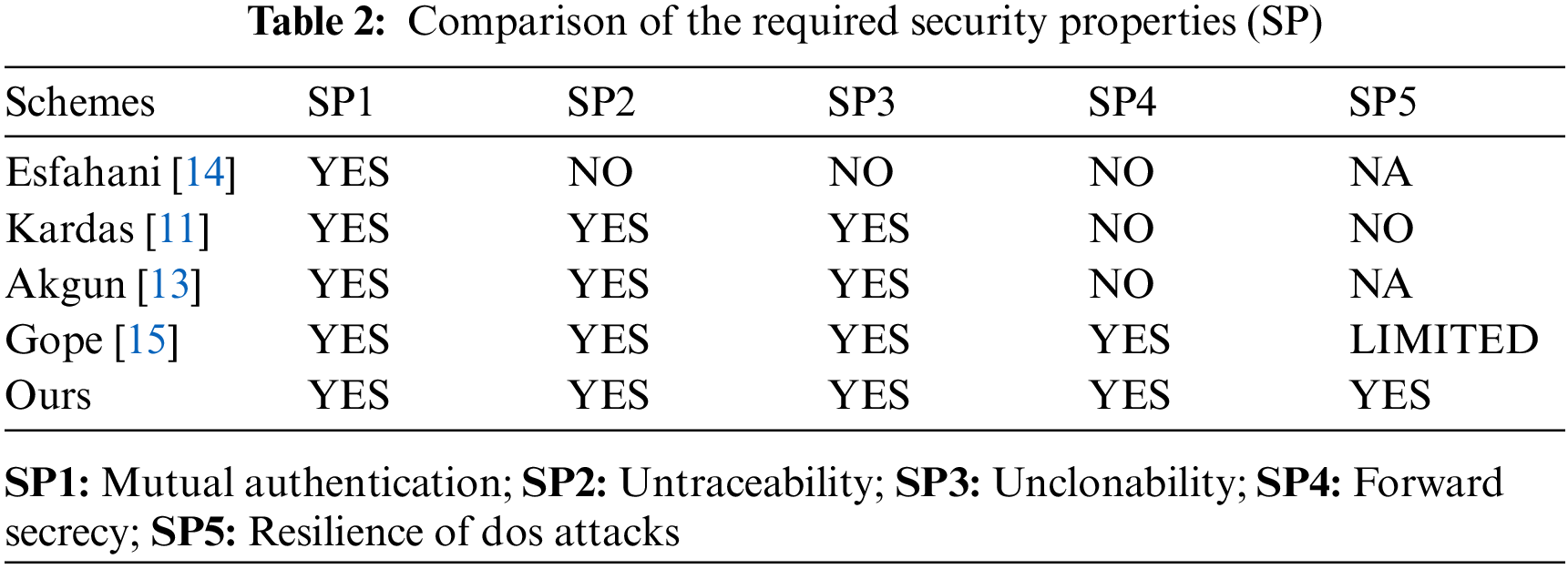
5.2 Computational and Communication Cost Comparison
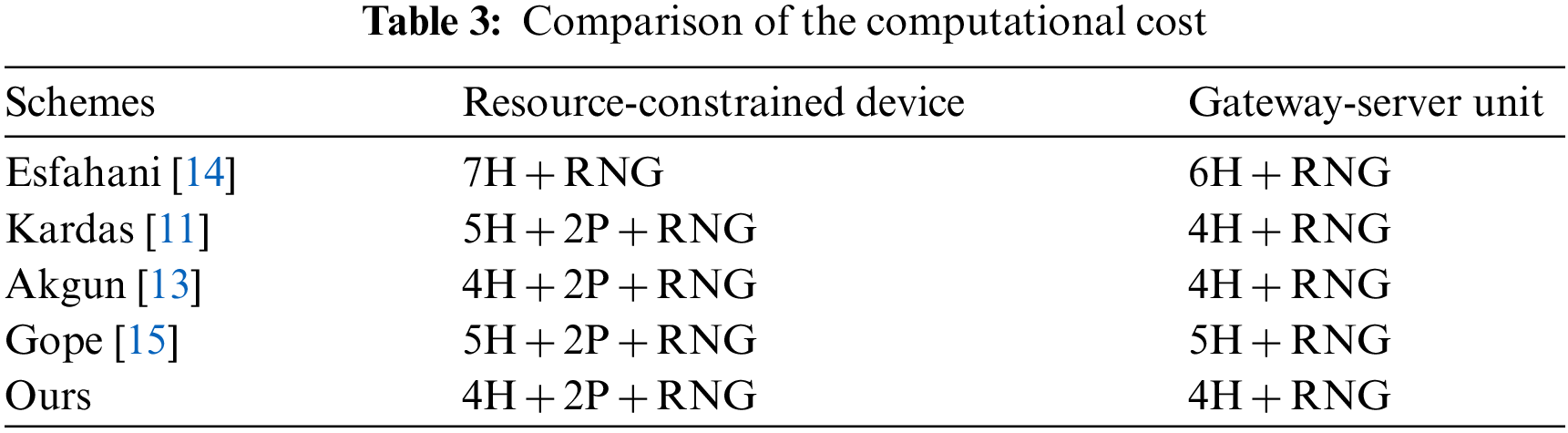
Since resource-constrained devices generally have limited resources such as storage and computation, it is important to consider the efficiency of the proposed scheme. We compare the performance of the proposed scheme in terms of the computation cost as shown in Tab. 3, which illustrates the numbers of operations including hash (denoted by H), PUF (denoted by P), and random number generator (denoted by RNG). Tab. 3 shows that our protocol’s computation overhead is lower than other existing schemes for the same condition. However, it provides better security which is shown earlier in Tab. 2. It is worth mentioning that the computational cost of SHA-256 is similar to 256-bit Arbiter PUF [17], which can provide a reference for the comparison between our scheme and [14].
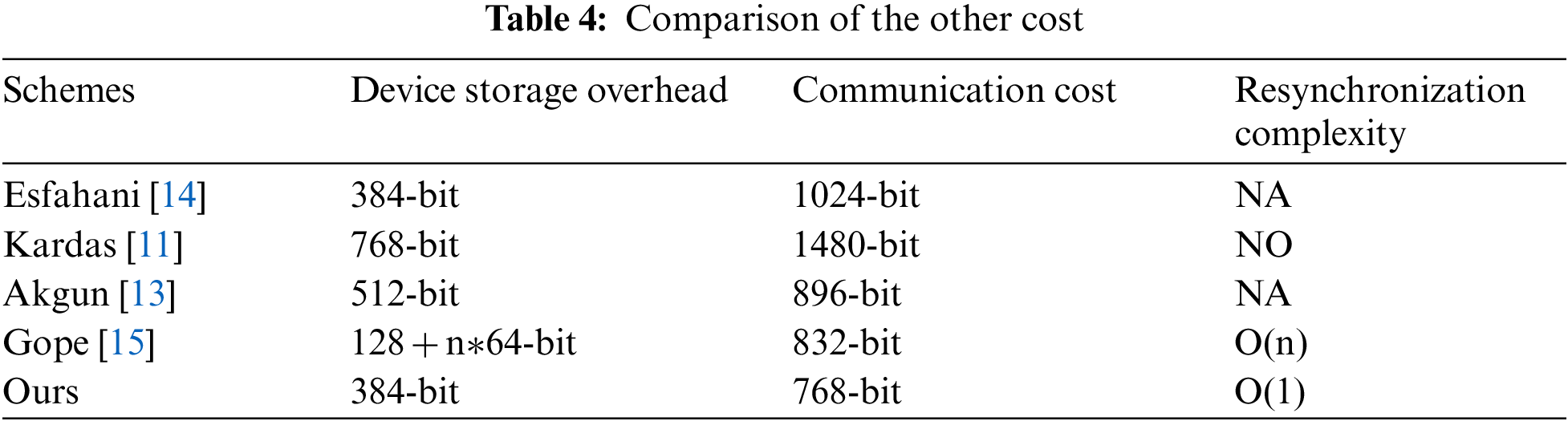
In Tab. 4, we compare the efficiency of our scheme to the existing schemes in terms of device storage overhead, communication cost, and resynchronization complexity. According to [14] and [15], each authentication parameter will cause 128-bit storage or communication costs. Tab. 4 shows that, in our proposed scheme, the device storage overhead and communication costs are 384-bit and 768-bit, which is less than all other existing schemes for the same condition. Furthermore, the proposed protocol’s resynchronization mechanism complexity is less than the latest Gope scheme [15], which claims to be the only scheme to meet the challenge between forward secrecy and DoS attacks.
In this paper, we propose a PUF based lightweight authentication scheme for resource-constrained devices in IIoT. The proposed scheme provides ubiquitous demands for mutual authentication in M2M communication. Formal and informal security analysis shows that the proposed protocol achieves better security features than existing schemes. Moreover, the performance analysis and comparison indicate that our proposed approaches are more practical and suitable for ensuring secure communication in IIoT.
Funding Statement: This work was supported by China Postdoctoral Science Foundation under Grant Nos. 2020M681959 and 2020TQ0291, in part by the national key R&D project under Grant No. 2018YFB2100401, in part by the National Key Research and Development Project No. 2018YFB2100400.
Conflicts of Interest: The authors of this paper declare that there are no conflicts of interest regarding the publication of this paper.
Reference
1. W. Goertz, N. Heudecker, M. Beyer, F. Chesini, H. LeHong et al., “Top strategic predictions for 2017 and beyond: Surviving the storm winds of digital disruption,” Accessed: May 2019. [Online]. Available: https://www.gartner.com/doc/3471568. [Google Scholar]
2. J. -Y. Lee, W. -C. Lin and Y. -H. Huang, “A lightweight authentication protocol for internet of things,” in Proc. ISNE, pp. 1–2, Kwei-Shan Tao-Yuan, Taiwan, 2014. [Google Scholar]
3. W. -L. Chin, Y. -H. Lin and H. -H. Chen, “A framework of machine-to-machine authentication in smart grid: A two-layer approach,” IEEE Communications Magazine, vol. 54, no. 12, pp. 102–107, 2016. [Google Scholar]
4. Y. Qiu and M. Ma, “A mutual authentication and key establishment scheme for M2M communication in 6LoWPAN networks,” IEEE Transactions on Industrial Informatics, vol. 12, no. 6, pp. 2074–2085, 2016. [Google Scholar]
5. H. Luo, G. Wen, J. Su and Z. Huang. “SLAP: Succinct and lightweight authentication protocol for low-cost RFID system,” Wireless Networks, vol. 24, no. 1, pp. 67–78, 2018. [Google Scholar]
6. H. Luo, G. Wen and J. Su, “Lightweight three factor scheme for real-time data access in wireless sensor networks,” Wireless Networks, vol. 26,. no. 2, pp. 955–970, 2020. [Google Scholar]
7. H. Luo, G. Wen, J. Su, Z. Huang and D. Inserra, “Multi-hop distance-bounding for improving security and efficiency of Ad-Hoc networks,” IEEE Internet of Things Journal, vol. 6, no. 3, pp. 5312–5323, 2019. [Google Scholar]
8. S. M. Aljuaid and A. S. Ansari, “Automated teller machine authentication using biometric,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 1009–1025, 2022. [Google Scholar]
9. M. Alshammari and S. Nashwan, “Fully authentication services scheme for nfc mobile payment systems,” Intelligent Automation & Soft Computing, vol. 32, no. 1, pp. 401–428, 2022. [Google Scholar]
10. S. G. Oliver and T. Purusothaman, “Lightweight and secure mutual authentication scheme for iot devices using coap protocol,” Computer Systems Science and Engineering, vol. 41, no. 2, pp. 767–780, 2022. [Google Scholar]
11. S. Kardas, S. Celik and M. Yildiz, “Puf-enhanced offline RFID security and privacy,” Journal of Network and Computer Applications, vol. 35, no. 6, pp. 2059–2067, 2012. [Google Scholar]
12. P. Gope, J. Lee and T. Q. S. Quek, “Resilience of DoS attack in designing anonymous user authentication protocol for wireless sensor networks,” IEEE Sensors Journal, vol. 17, no. 2, pp. 498–503, 2017. [Google Scholar]
13. M. Akgun and M. U. Caglayan, “Providing destructive privacy and scalability in RFID systems using PUFs,” Ad Hoc Networks, vol. 32, pp. 32–42, Sep. 2015. [Google Scholar]
14. A. Esfahani, G. Mantas, R. Matischek, F. B. Saghezchi, J. Rodriguez et al., “A lightweight authentication mechanism for M2M communication in industrial IoT environment,” IEEE Internet of Things Journal, vol. 6, no. 1, pp. 288–296, 2017. [Google Scholar]
15. P. Gope, J. Lee and T. Q. S. Quek, “Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 11, pp. 2831–2843, 2018. [Google Scholar]
16. “AVISPA automated validation of internet security protocols and applications,” Last Accessed on April 25, 2016. [Online]. http://www.avispa-project.org/. [Google Scholar]
17. M. Kaveh and M. Mosavi, “A lightweight mutual authentication for smart grid neighborhood area network communications based on physically unclonable function,” IEEE Systems Journal, vol. 14, no. 3, pp. 4535–4544, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |