DOI:10.32604/cmc.2022.027999

| Computers, Materials & Continua DOI:10.32604/cmc.2022.027999 |  |
| Article |
Securing Copyright Using 3D Objects Blind Watermarking Scheme
1Faculty of Science, New Valley University, El-Kharga 72511, Egypt
2Department of Computer Sciences, College of Computer and Information Science, Princess Nourah Bint Abdulrahman University, Riyadh 11671, Saudi Arabia
*Corresponding Author: Hussein Abulkasim. Email: hussein@scinv.au.edu.eg
Received: 30 January 2022; Accepted: 23 March 2022
Abstract: Recently, securing Copyright has become a hot research topic due to rapidly advancing information technology. As a host cover, watermarking methods are used to conceal or embed sensitive information messages in such a manner that it was undetectable to a human observer in contemporary times. Digital media covers may often take any form, including audio, video, photos, even DNA data sequences. In this work, we present a new methodology for watermarking to hide secret data into 3-D objects. The technique of blind extraction based on reversing the steps of the data embedding process is used. The implemented technique uses the features of the 3-D object vertex’ discrete cosine transform to embed a grayscale image with high capacity. The coefficient of vertex and the encrypted picture pixels are used in the watermarking procedure. Additionally, the extraction approach is fully blind and is dependent on the backward steps of the encoding procedure to get the hidden data. Correlation distance, Euclidean distance, Manhattan distance, and the Cosine distance are used to evaluate and test the performance of the proposed approach. The visibility and imperceptibility of the proposed method are assessed to show the efficiency of our work compared to previous corresponding methods.
Keywords: Discrete cosine transform; 3-D object; copyright; watermarking
A variety of approaches for embedding data into digital media are used in digital watermarking, fingerprinting, digital rights management, and steganography. The embedded data could be used for access control, authentication, annotation, copyright protection, data concealing, and multimedia information modification. The initial item is usually referred to as “cover media,” whereas the watermarked object is referred to as “stego media.” A watermark must meet several criteria, including hidden data to human perception or recognition by technology, as well as resistance to stego media treatment and prospective attacks [1]. Because browsing the internet has become such an important part of our lives, people can easily replicate digital data and objects to create unauthorized and fraudulent copies of the original work. As a result, the development of robust copyright security and/or content verification mechanisms for multimedia data has become a pressing necessity. One method for achieving this purpose is to create and encode an undetectable signal in the original information. The data owners or authorized users/information suppliers might be included in the watermark.
Copyrights are intellectual property protection that the owner provides for all types of digital data and things. As a result, copyright is the owner’s specific legal right to produce copies of original efforts, literary works, and creative expression. Digital artifacts such as e-books, photographs, movies, music, databases, and 3-D objects are referred to as creative, intellectual, and creations of the mind in online technology. 3-D objects are widely used in a variety of medical imaging, computer graphics, manufacturing, including games, applications, and human models. As a result, more requests for the copyright of 3-D objects are needed to encourage investigation into creating protection measures. Copyrighting is one of the most popular recommended strategies for 3-D object intellectual property rights. The watermark must be resistant to unlawful usage to protect copyright [2].
Constructive solid geometry (CSG), polygonal meshes, voxels, or an implicit collection of generalized equations, such as nonhomogeneous logical B-splines (NURBS), or other splines, can all be used to represent a 3-D graphics image. Meshes and parameterized solutions describe the edges of 3-D objects, while voxels include a dimensional characterization [3]. A 3-D object’s polygonal mesh is represented graphically made up of vertex connected by edges and polygons. Unlike all other graphical media portrayals, researchers only have to deal with a small amount of data when modeling 3-D objects with mesh. As the importance of digital 3-D models grew, online content networks such as sketchfab popped up, and thing verse, pin shape, and as the dissemination of 3-D models grew, so did infringement of copyright. Although 3-D printing is booming with new possibilities, copyright difficulties will inevitably arise when technology expands into the content sector, as they have in the past for the music and video industries. The legal system is straining to deal with the legal issues that have arisen as a result of technological advancements.
Watermarking technologies were used as a host cover to hide or incorporate a bit of knowledge that can help in such a way that it was unnoticeable to a human spectator in modern days on a wide variety of technology media [4,5]. Digital media covers can typically accept any amount, including photos, films, audio, even DNA sequences. Even though 3-D objects are generally available and significant, only a few image manipulation approaches exist. The embedding domains such as the feature space, transform domain, and spectral-domain can be used to classify the numerous watermarking approaches for 3-D objects. Fourier, Laplace, cosine, and wavelet transforms are examples of transform domain approaches that give a good trade-off between transparency and resilience [6]. A watermarking technique has been proposed, as well as a mesh registrations approach that requires the original 3-D mesh object. This approach embeds a hidden image representation three times and retrieves the hidden grayscale. The extract method is completely blind and is dependent on the backward stages of something like the encoding process. As a result, new solutions to protect 3-D prints are desperately necessary to maintain the protection of 3-Dimensional content property rights. As a result, new solutions to protect 3-D prints are desperately necessary to maintain the protection of 3-D content property rights.
Throughout this study, A new methodology for watermarking 3-D objects is presented. The proposed methodology uses the features of the 3-D object vertex’ discrete cosine transform (DCT) to encode a hidden grayscale image 3 times. Between the original 3-D object and the watermarked one, many efficiency elements of the approach are evaluated and compared. The remainder of the paper is laid out as follows: A similar work on data hiding and watermarking in 3-D objects is presented in Section 2. The suggested technique’s watermarking system is specified in Section 3. In Section 4, the empirical values are given and analyzed, and a comparative evaluation between both the original 3-D item and the watermarked object is made. Section 5 ends with a summary of the results and analysis.
Reference [7] proposed a watermarking method for embedding data in a 3-D object to identify the owner. Their approach embedded a greyscale image in a 3-D mesh structure. Every one of the three vertexes of the 3-D object may hide one pixel from the hidden image using the optimization methodology. As a watermark, a greyscale image will be inserted in a 3-D mesh object. One pixel from the ciphertext will be held by each of the three vertexes in the 3-D object. Next, the suggested technology utilizes the associated linear transformation to transfer the triangle’s vertex between 3-D to 2-Dimensional domains. Afterward, through using 2-Dimensional coordinates of the triangle vertex and the hidden picture pixel, the embedding procedure will begin. The suggested method offers higher visual quality on both the watermarked item and the retrieved hidden image, according to the experimental outcomes. This technique increases the visual quality of the watermark information material while having a modest influence on the accuracy of the retrieved hidden image, according to the findings of the experiments. Furthermore, the current technique demonstrated its resistance to popular attacks, including 3-D mesh rotations, scaling, and movement.
Reference [8] presented a new methodology for watermarking 3-D objects. The implemented technique uses the features of the 3-D object vertex’ DCT to incorporate a hidden grayscale three times. The vertex coefficients and the encrypted picture pixels are used in the watermarking procedure. Furthermore, the extracting procedure is based on the reverse processes of the embedding process to retrieve the hidden grayscale image and is completely blind. Using Manhattan distance (MD), Euclidean distance (ED), correlation distance, and cosine distance. Several performance elements of the approach are measured and compared between the original 3-D object and the watermark information one. The outcomes reveal that the suggested significantly outperformed the competition in terms of computational efficiency and transparency. The proposed model has been implemented in MATLAB, and the suggested method’s efficiency over time was documented. The suggested method’s maximal capacity for each 3-D object and the accompanying embedded hidden grayscale image is 8 bits per vertex as a consequence (bpv). The suggested method’s imperceptibility and transparency were assessed using Correlation distance, Euclidean distance, cosine distance, and Manhattan distance.
Reference [9] proposed research during the recent decade, three-dimensional (3-D) mesh have been increasingly popular in industrial, medicinal, and entertainment applications. Many investigators, both industry and academia, have become aware of the intellectual property security and verification issues that have arisen as a result of their increased use. This study provided a full overview of 3-D mesh watermarking, which is seen as a viable solution to the two challenges mentioned above. The survey included an overview of the relevant state of the art. An investigation focused on attacks and a list of existing issues and proposed remedies. The specific challenges experienced when applying steganography to 3-D mesh are first described. Then, after differentiating among fragile and robust strategies, researcher presents the findings and an evaluation of the known algorithms. Research also presents an attack-centric perspective of such an advance because attacks play a significant role in the design of 3-D mesh watermarking techniques. Lastly, some suggestions for future research are suggested, focusing on techniques to develop blind and robust algorithms as well as some new, potentially useful watermarking parameter maps.
Reference [10] proposed a method on blind 3-D mesh watermarking which is based on the wavelet of copyright protection. Due to the advancement of computing processing capabilities and internet infrastructure, the three-dimensional mesh is now widely employed in a variety of industrial and commercial applications, medicinal, computer-aided design (CAD), and recreation. Unauthorized customers can quickly modify, replicate, and disseminate 3-D meshes, just as they can with digital photos and movies. When attempting to address this problem, an embedded watermark arose. In this research, a copyright protection strategy for three-dimensional semiregular models using a blind robust watermarking method is introduced. The data is embedded by changing the standard of the wavelet coefficients vectors corresponding to the lowest level of resolution utilizing edge normal standards as synchronising primitives. The results show that, in contrast to other three-dimensional mesh copyrighting methods, the suggested methodology can endure a wide range of threats, such as evolutionary algorithm such as transcription, precession, unified scalability, and their Wavelet coefficients softening, variations, noise addition, and lossy compression, while preserving high classification accuracy.
Reference [11] proposed a method for the distribution of vertex norms on oblivious watermarking. Even though oblivious watermarking techniques are less resilient than nonobvious systems, they are more suitable for a variety of applications where a host signal is not available during the watermark detection phase. Distortion fewer strikes, such as resemblance image is transformed and vertex reorganizing, may be more serious than deformation threats, including adding remeshing, clipping, noise, smoothing, simplification, and so on, from the perspective of oblivious watermarking for a three-dimensional (3-D) polygonal mesh model. Therefore, an oblivious watermarking system that is resistant to both distortion less and distortion assaults is necessary. They offer two oblivious watermarking algorithms for 3-D polygonal mesh models in this research, which adjust the distribution of vertex norms as per the watermark information bit. To change the distribution, statistical mapping algorithms are developed. These mapping functions are designed to make the watermark as invisible as possible. The proposed solutions are resistant against distortion-less attempts because the statistical properties of vertex norms are invariant to such attacks. Furthermore, our techniques use an oblivious watermark approach for detecting that extracts the watermark without using the covering mesh models. The results showed that the presented method is immune against distortionless attack and well-known distortion attacks.
Watermarking a 3-D object entails embedding hidden data into a polygonal mesh object without leaving visible markings or creating organizational modifications. It is often used to recognize and defend the ownership rights of a unique 3-D object against infringement. In light of this unavoidable circumstance, this work suggested a technique for postprocessing a 3-D object that takes control of the DCT features to hide the image of grayscale representation within the 3-D object’s vertex [1].
The suggested watermarking model’s overall procedure is depicted in Fig. 1 Proposed Model of Watermarking Method. To begin, the suggested technique normalizes the vertex of the original 3-D object as well as the hidden grayscale image. This phase allows us to alter the membership functions using the proper fuzzy algorithms. Fuzzification can be done in a variety of ways and for a variety of different purposes. The normalized 3-D object vertex is then preprocessed, with a DCT added to every three vertexes. On the normalized watermark image, reshaping and encryption operations are carried out at that period [3]. After that, using the vertex co-efficient and the encrypted picture pixels, the watermarking procedure will begin. Finally, the watermarked 3-D object will be created using the inverse DCT and focus of this section procedure of altered vertex.

Figure 1: Proposed model of watermarking method
As previously stated, regulating both the primary 3-D object vertex and the hidden grayscale picture is the first step in watermark embedding. Regularization is a common method that constantly increases the range of data values. As a result, regulation modifies the information item. Hence, the regulation changes the data object
Regularization denotes changing the primary 3-D object vertex mutually and the hidden grayscale picture data range with intensities values ranging from [0, 1] in the suggested approach. As a result, the normalization is accomplished using Eq. (2) [12].
The hidden grayscale encoding function is done using seed numbers from a pseudorandom generator for security reasons, which encodes the placement of every pixel in the primary grayscale image. To increase the possibility of encrypting, the encoding procedure is used to the process of reshaping to the grayscale vector. Furthermore, it uses three authentication tokens to adjust the location of the pixel to improve the system’s resilience.
In the preprocessing stage, by using the
From the Fourier related transformation, the DCT is derived and employed in a proposed watermark scheme by [13]. To overcome the problem of repetition, DCT defines a sequence of actual data units into its genuine spectrum. Thus, the DCT is the method of changing a finite sequence of digital signal sample points into the equivalent of the initial digital signal using a sum of cosine functions at various frequencies [14]. Orderly, the discrete cosine function (DCF) is considered as an invertible function
The first formula [13]:
The second formula:
The third formula:
The fourth formula:
where
The suggested approach assumes that the 3-D object has L vertex, each of which is described as
The procedure of watermarking is performed on the normalized coefficients of the vertex after the DCT has been applied to the normalized 3-D object vertex [15]. When using the DCT transform, normalizing the vertex results in the first reliability coefficient being within [0, 2], and the third and second reliability coefficients being within [−1, 1]. These facts can be used to create Eq. (9) for watermarking the hidden grayscale picture in the modified regions of the 3-D object coefficients:
In Eq. (8), 3-D obj(

To retrieve the hidden grayscale image, the phases in the encoding process are often repeated in the extraction procedure. The extraction device’s processes are depicted in Fig. 2 Flowchart of the Extraction method. As a result, the approach begins by regulating the watermarked 3-D object and then determining the vertex’ Discrete transformation breakdown [12]. As a result, given the variables

Figure 2: Flowchart of extraction method
The hidden EcMsg will be recovered from the watermark information 3-D object in a blind manner. Following that, the 3 keys must be used to determine the location of the hidden original pixel.
The image pixels must be denormalized after the normalized process to return to the original integer domain of the image pixels. In Algorithm 2, the exact details of the extracting phase are shown as pseudo-code [17].

Fig. 3 shows the implementation and watermark image used in 3-D Object and Figs. 3a–3f depicts six standard 3-D objects that were utilized to assess the suggested method’s efficiency in the following sets of trials [18]. Fig. 3g also shows the hidden grayscale image that was utilized as a watermark image and has the following dimensions: 1119453, 1728823, 597349, 615473, 11457, 315128. The presented model was constructed with an Intel(R) Core (TM) i7-4700MQ CPU running at 2.40 GHz and 8GB of RAM. In addition, the development was coded using MATLAB version 9.0.0.341360 (R2016b). Three seeds for the random number were chosen in the encoding step: 1987, 1989, and 1993.

Figure 3: Implementation and watermark image used in 3-D object
Methods are compared in the field of data hiding based on numerous characteristics such as capacity and payload. The maximal bits are buried within the 3-D object vertex, which is how capability is defined. The real payload is the ratio of the currently embedded bits to the 3-D object’s capability in bits. For each 3-D object and the accompanying encoded hidden grayscale image, Tab. 1 shows the resulting capability and real payload. Given H vertex in the initial 3-D, the capability in bits per vertex (bpv) and the exact load in percentage (percent) can be calculated as in Eq. (11):
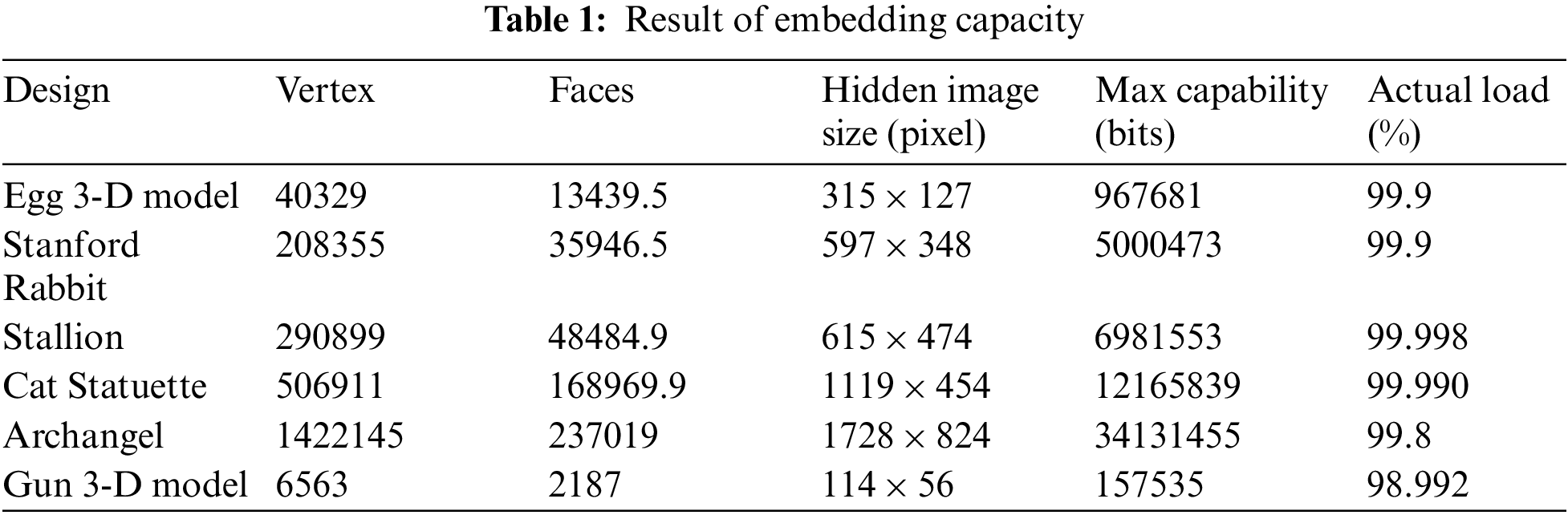
The trials and amount of time it takes to watermark and obtain highest capability for each 3-D object, as well as values within 1000 and 9000, were used to evaluate the suggested method’s response time as indicated as Tab. 2. For the identical 3-D object, the extracting running time is significantly shorter than the watermarking processing time. The estimated duration for watermarking the Rabbit, Stallion, Cat, Egg, Archangel, and Gun models is 18.57, 93.90, 135.14, 226.61, 674.41, and 3.06 s, correspondingly for β = 5000. In the same vein, the mean extraction efficiency for the Egg, Rabbit, Stallion, Cat, Archangel, and Gun models is 12.51, 63.67, 88.90, 146.07, 416.88, and 2.05 s, correspondingly. The variable
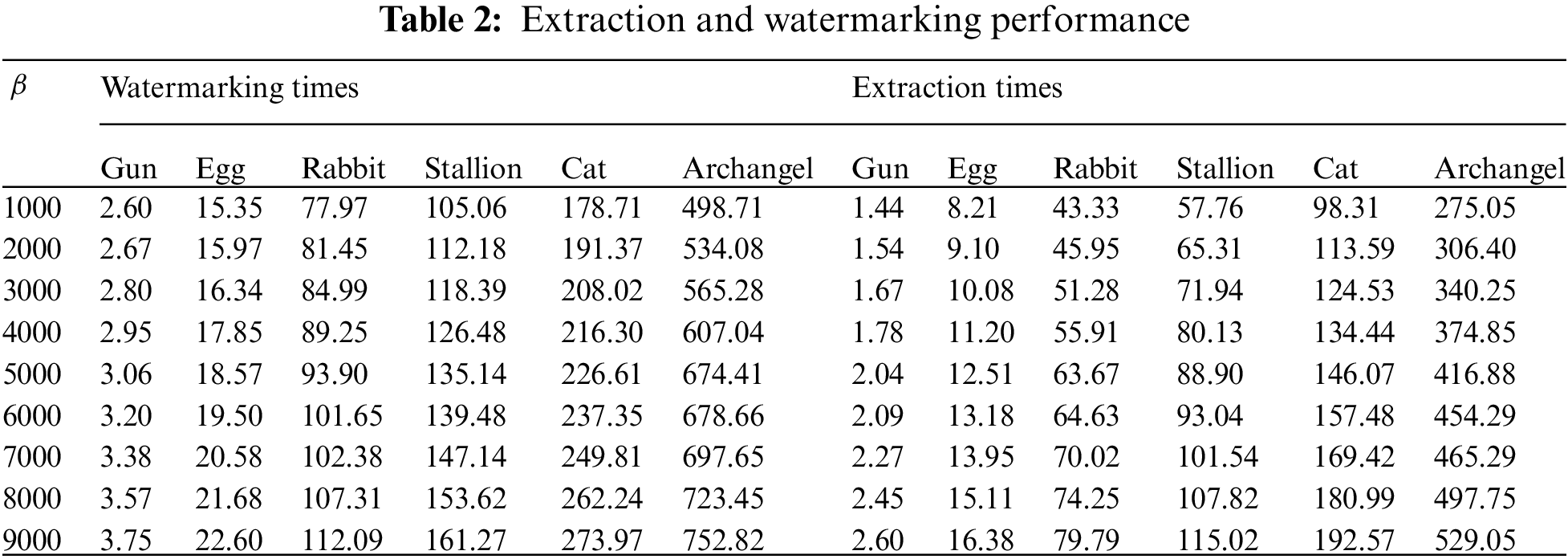
The suggested method’s imperceptibility and transparency were assessed using correlation distance, cosine distance, ED, and MD. The invisibility effectiveness terms were outlined in the following mathematical formulas: Let the original 3-D object be u and the watermark information object be v.
The ED:
The MD:
The cosine distance:
The correlation distance can be described as in Eq. (12):
where
Fig. 4 and Tab. 3 proposed a method on invisibility performance illustrates the calculated MD, ED, correlation distance, and cosine distance to assess the original 3-D object to the watermarked outcome with values
The suggested technique’s primary properties are compared to other existing requirements to ensure its validity and performance [20]. The purpose of the comparative study was to evaluate the suggested differences in various techniques of the cover image, watermark sequences, embedded area, region, capability, and blindness extraction method. A contrast of the documented characteristics of the relevant approaches is shown in Tab. 4.

Figure 4: Proposed method on invisibility efficiency for ED and MD
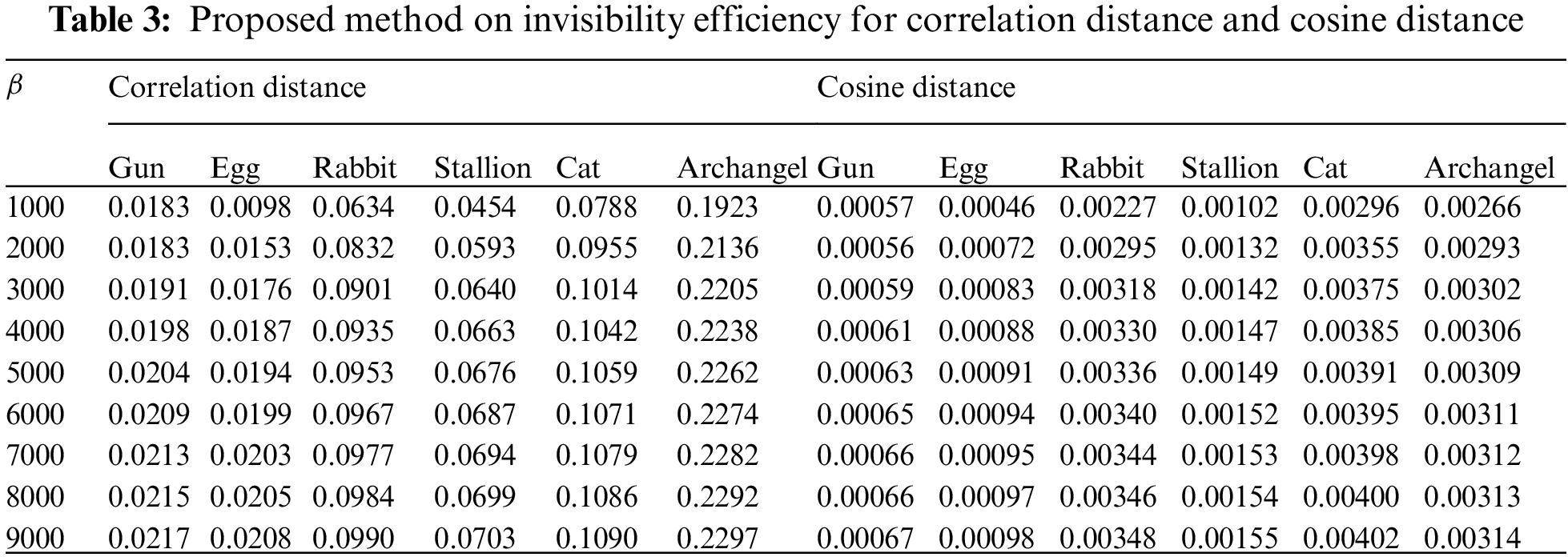
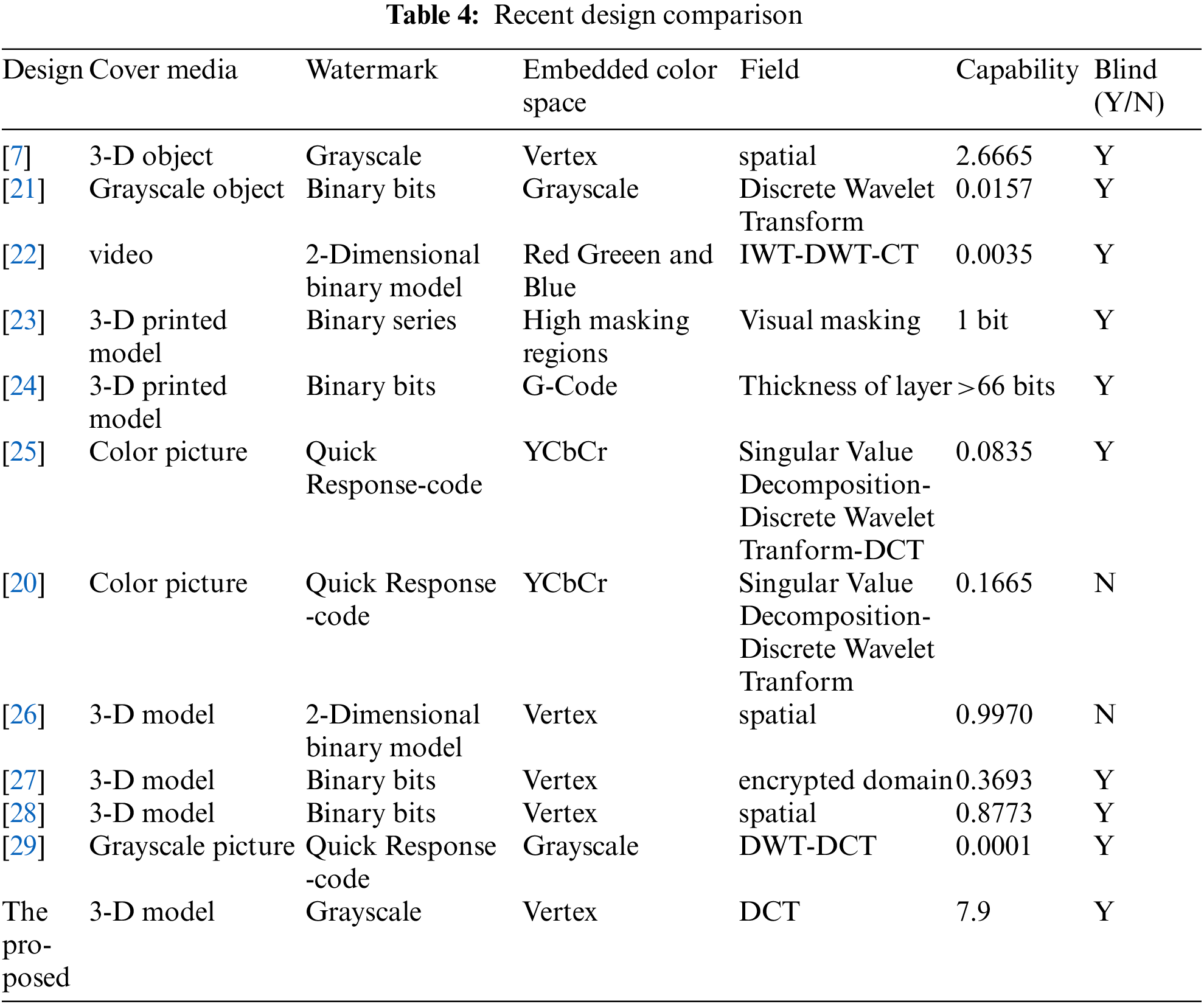
A review of the documented details of the relevant approaches is shown in Tab. 4. The approaches provided were based on embedding quick response codes and binary bits into photos from a variety of areas. Ayubi et al. also demonstrated a video watermarking method based on a 2-D binary picture [26]. The methodologies, on either side, used a different watermark sequence to watermark the 3-D printing technology item, whereas the program to deal used a distinct watermark sequence to watermark the 3-D printed object [29]. The number of bits per pixel (bpp) and the number of bits per vertex (bv) are used to measure the capabilities (bpv). The suggested 3-D Mesh watermarking technology has the benefit of being able to use a large amount of memory per vertice.
A new model for 3-D object watermarking is proposed in this paper. The proposed methodology uses the features of the 3-D shape vertex’ DCT to embed a hidden image representation three times. To retrieve the hidden grayscale, the extract method is completely blind and is dependent on the backward stages of something like the encoding process. The recommended method was constructed in MATLAB, and the recommended method’s effectiveness over time was documented. The proposed method’s maximal capability for each 3-D object and the accompanying embedded hidden grayscale image is 8 bits per vertex as a consequence (bpv). The suggested method’s imperceptibility and visibility were assessed using Cosine distance, Euclidean distance, Manhattan distance, and Correlation distance.
Acknowledgement: The authors acknowledge Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R104), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Funding Statement: Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2022R104), Princess Nourah bint Abdulrahman University, Riyadh,Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. A. G. Bors, “Watermarking mesh-based representations of 3-D objects using local moments,” IEEE Transactions on Image Processing, vol. 15, pp. 687–701, 2006. [Google Scholar]
2. R. Ohbuchi, H. Masuda and M. Aono, “Embedding data in 3D models,” in Int. Workshop on Interactive Distributed Multimedia Systems and Telecommunication Services, Darmstadt, Germany, pp. 1–10, 1997. [Google Scholar]
3. J. M. Konstantinides, A. Mademlis, P. Daras, P. A. Mitkas and M. G. Strintzis, “Blind robust 3-D mesh watermarking based on oblate spheroidal harmonics,” IEEE Transactions on Multimedia, vol. 11, pp. 23–38, 2008. [Google Scholar]
4. X. R. Zhang, W. F. Zhang, W. Sun, X. M. Sun and S. K. Jha, “A robust 3-D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
5. X. R. Zhang, X. Sun, X. M. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
6. M. Corsini, E. D. Gelasca, T. Ebrahimi and M. Barni, “Watermarked 3-D mesh quality assessment,” IEEE Transactions on Multimedia, vol. 9, pp. 247–256, 2007. [Google Scholar]
7. O. Khalil, A. Elhadad and A. Ghareeb, “A blind proposed 3D mesh watermarking technique for copyright protection,” The Imaging Science Journal, vol. 68, pp. 90–99, 2020. [Google Scholar]
8. H. S. Al-Saadi, A. Ghareeb and A. Elhadad, “A blind watermarking model of the 3D object and the polygonal mesh objects for securing copyright,” Computational Intelligence and Neuroscience, vol. 2021, 2021. [Google Scholar]
9. K. Wang, G. Lavoué, F. Denis and A. Baskurt, “A comprehensive survey on three-dimensional mesh watermarking,” IEEE Transactions on Multimedia, vol. 10, pp. 1513–1527, 2008. [Google Scholar]
10. M. Hamidi, M. El Haziti, H. Cherifi and D. Aboutajdine, “A robust blind 3-D mesh watermarking based on wavelet transform for copyright protection,” in 2017 Int. Conf. on Advanced Technologies for Signal and Image Processing (ATSIP), Fez, Morocco, pp. 1–6, 2017. [Google Scholar]
11. J. -W. Cho, R. Prost and H. -Y. Jung, “An oblivious watermarking for 3-D polygonal meshes using distribution of vertex norms,” IEEE Transactions on Signal Processing, vol. 55, pp. 142–155, 2006. [Google Scholar]
12. P. R. Alface, B. Macq and F. Cayre, “Blind and robust watermarking of 3D models: How to withstand the cropping attack?” in 2007 IEEE Int. Conf. on Image Processing, San Antonio, TX, USA,pp. V-465–V-468, 2007. [Google Scholar]
13. N. Ahmed, T. Natarajan and K. R. Rao, “Discrete cosine transform,” IEEE Transactions on Computers, vol. 100, pp. 90–93, 1974. [Google Scholar]
14. M. Rahman and K. Harada, “Parity enhanced topology-based spot area watermarking method for copyright protection of layered 3D triangular mesh data,” International Journal of Computer Science and Network Security, vol. 6, pp. 252–259, 2006. [Google Scholar]
15. H. Garg, K. K. Khandelwal, M. Gupta and S. Agrawal, “Uniform selection of vertices for watermark embedding in 3-d polygon mesh using IEEE754 floating point representation,” in 2014 Fourth Int. Conf. on Communication Systems and Network Technologies, NW Washington, DC, USA, pp. 788–792, 2014. [Google Scholar]
16. B. Macq, P. R. Alface and M. Montanola, “Applicability of watermarking for intellectual property rights protection in a 3D printing scenario,” in Proc. of the 20th Int. Conf. on 3D Web Technology, Heraklion, Crete, Greece, pp. 89–95, 2015. [Google Scholar]
17. S. Zafeiriou, A. Tefas and I. Pitas, “Blind robust watermarking schemes for copyright protection of 3D mesh objects,” IEEE Transactions on Visualization and Computer Graphics, vol. 11, pp. 596–607, 2005. [Google Scholar]
18. H. S. Devi and K. M. Singh, “Red-cyan anaglyph image watermarking using DWT, hadamard transform and singular value decomposition for copyright protection,” Journal of Information Security and Applications, vol. 50, pp. 102424, 2020. [Google Scholar]
19. M. G. Wagner, “Robust watermarking of polygonal meshes,” in Proc. Geometric Modeling and Processing 2000. Theory and Applications, Hong Kong, China, pp. 201–208, 2000. [Google Scholar]
20. C. Patvardhan, P. Kumar and C. V. Lakshmi, “Effective color image watermarking scheme using YCbCr color space and QR code,” Multimedia Tools and Applications, vol. 77, pp. 12655–12677, 2018. [Google Scholar]
21. M. Amini, M. O. Ahmad and M. Swamy, “A robust multibit multiplicative watermark decoder using a vector-based hidden markov model in wavelet domain,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 28, pp. 402–413, 2016. [Google Scholar]
22. P. Ayubi, M. J. Barani, M. Y. Valandar, B. Y. Irani and R. S. M. Sadigh, “A new chaotic complex map for robust video watermarking,” Artificial Intelligence Review, vol. 54, pp. 1237–1280, 2021. [Google Scholar]
23. J. -U. Hou, D. -G. Kim and H. -K. Lee, “Blind 3D mesh watermarking for 3D printed model by analyzing layering artifact,” IEEE Transactions on Information Forensics and Security, vol. 12, pp. 2712–2725, 2017. [Google Scholar]
24. A. Delmotte, K. Tanaka, H. Kubo, T. Funatomi and Y. Mukaigawa, “Blind watermarking for 3-D printed objects by locally modifying layer thickness,” IEEE Transactions on Multimedia, vol. 22, pp. 2780–2791, 2019. [Google Scholar]
25. L. Rosales-Roldan, J. Chao, M. Nakano-Miyatake and H. Perez-Meana, “Color image ownership protection based on spectral domain watermarking using QR codes and QIM,” Multimedia Tools and Applications, vol. 77, pp. 16031–16052, 2018. [Google Scholar]
26. H. -T. Wu and Y. -M. Cheung, “A High-capacity data hiding method for polygonal meshes,” in Int. Workshop on Information Hiding, Alexandria, VA, USA, pp. 188–200, 2006. [Google Scholar]
27. R. Jiang, H. Zhou, W. Zhang and N. Yu, “Reversible data hiding in encrypted three-dimensional mesh models,” IEEE Transactions on Multimedia, vol. 20, pp. 55–67, 2017. [Google Scholar]
28. F. Cayre and B. Macq, “Data hiding on 3-D triangle meshes,” IEEE Transactions on Signal Processing, vol. 51, pp. 939–949, 2003. [Google Scholar]
29. Y. -W. Chow, W. Susilo, J. Tonien and W. Zong, “A QR code watermarking approach based on the DWT-DCT technique,” in Australasian Conf. on Information Security and Privacy, Auckland, New Zealand, pp. 314–331, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |