DOI:10.32604/cmc.2022.025727

| Computers, Materials & Continua DOI:10.32604/cmc.2022.025727 |  |
| Article |
Improved Multi-party Quantum Key Agreement with Four-qubit Cluster States
1Faculty of Science, New Valley University, El-Kharga & the Academy of Scientific Research and Technology, Cairo, Egypt
2College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia
3Faculty of Computer and Information Sciences, Ain Shams University, Cairo, Egypt
*Corresponding Author: Hussein Abulkasim. Email: abulkasim@scinv.au.edu.eg
Received: 02 December 2021; Accepted: 11 January 2022
Abstract: Quantum key agreement is a promising key establishing protocol that can play a significant role in securing 5G/6G communication networks. Recently, Liu et al. (Quantum Information Processing 18(8):1-10, 2019) proposed a multi-party quantum key agreement protocol based on four-qubit cluster states was proposed. The aim of their protocol is to agree on a shared secret key among multiple remote participants. Liu et al. employed four-qubit cluster states to be the quantum resources and the X operation to securely share a secret key. In addition, Liu et al.'s protocol guarantees that each participant makes an equal contribution to the final key. The authors also claimed that the proposed protocol is secure against participant attack and dishonest participants cannot generate the final shared key alone. However, we show here that Liu et al. protocol is insecure against a collusive attack, where dishonest participants can retrieve the private inputs of a trustworthy participant without being caught. Additionally, the corresponding modifications are presented to address these security flaws in Liu et al.'s protocol.
Keywords: Quantum key agreement; 5G/6G communication networks; collusive attacks; quantum cryptography
The recent advancement of quantum technology threatens the ability of classical cryptosystems, including 5G/6G communication networks to secure data and communications against growing security attacks [1,2]. In this context, the concept of quantum cryptography or quantum key distribution (QKD) was introduced by Bennet and Brassard [3]. Thanks to the principle of quantum physics, quantum cryptography can provide unconditional security solutions whose security has been proven by [4]. These solutions may be adopted to secure 5G/6G communication networks [5–7]. Subsequently, scholars focused their attention and passion on quantum communication and quantum cryptography, and various quantum protocols were investigated, including quantum secure direct communication [8,9], quantum secret sharing [10–13], quantum teleportation [14], quantum private computation [15–17], quantum signature [18], quantum key agreement (QKA) [19–23], and so on. Currently, QKA is one of the most significant aspects that may be used to generate a secured shared key between two or more distance users using a public quantum channel. It differs from the QKD protocol, which predetermines the key and then distributes it to the users in that no user or subgroup can independently identify the shared key.
In 2004, Zhou et al. [19] presented the pioneering work of the QKA protocol. Several QKA schemes have also been introduced throughout time [20–23]. In the same year, another QKA protocol was proposed based on entangled quantum states. Unfortunately, as Chong et al. [24] pointed out, it was not a true QKA protocol since malicious users may derive the final shared key independently and entirely. In 2010, a QKA protocol based on the BB84 protocol was suggested, which is proved to be secure against inside and outside attacks [24]. In 2014, the authors in [25] developed an efficient two-user QKA protocol using four-qubit cluster quantum states. However, the authors could not extend their protocol to the multi-party case. The multi-party case of the QKA protocol is more complicated, but it is more suitable for real applications. As a result, the multi-party case of the QKA protocol has gotten a lot of interest [26–33].
Recently, Liu et al. [34] (Liu-QKA protocol) presented an interesting multi-party QKA protocol with four-qubit quantum cluster states. Their protocol adopted the four-qubit quantum cluster state as a quantum resource and a unitary operation to generate and share a secure key. Liu-QKA protocol generated and shared quantum key with high efficiency. The authors claimed that their protocol is secure against the outsider and participant attacks. However, our work shows that Liu-QKA protocol cannot resist the collusive attack. Two or more malicious participants can drive the private inputs of the honest ones and execute the protocol without being caught. The rest of this manuscript is organized as follows. A review of Liu-QKA protocol is presented in Section 2. Sections 3 introduces the suggested attack strategy on Liu=-QKA protocol and the suggested improvement. Finally, Section 4 concludes this work.
This subsection introduces a brief background of Liu-QKA protocol.
Liu-QKA protocol used the X operation to flip qubits, where
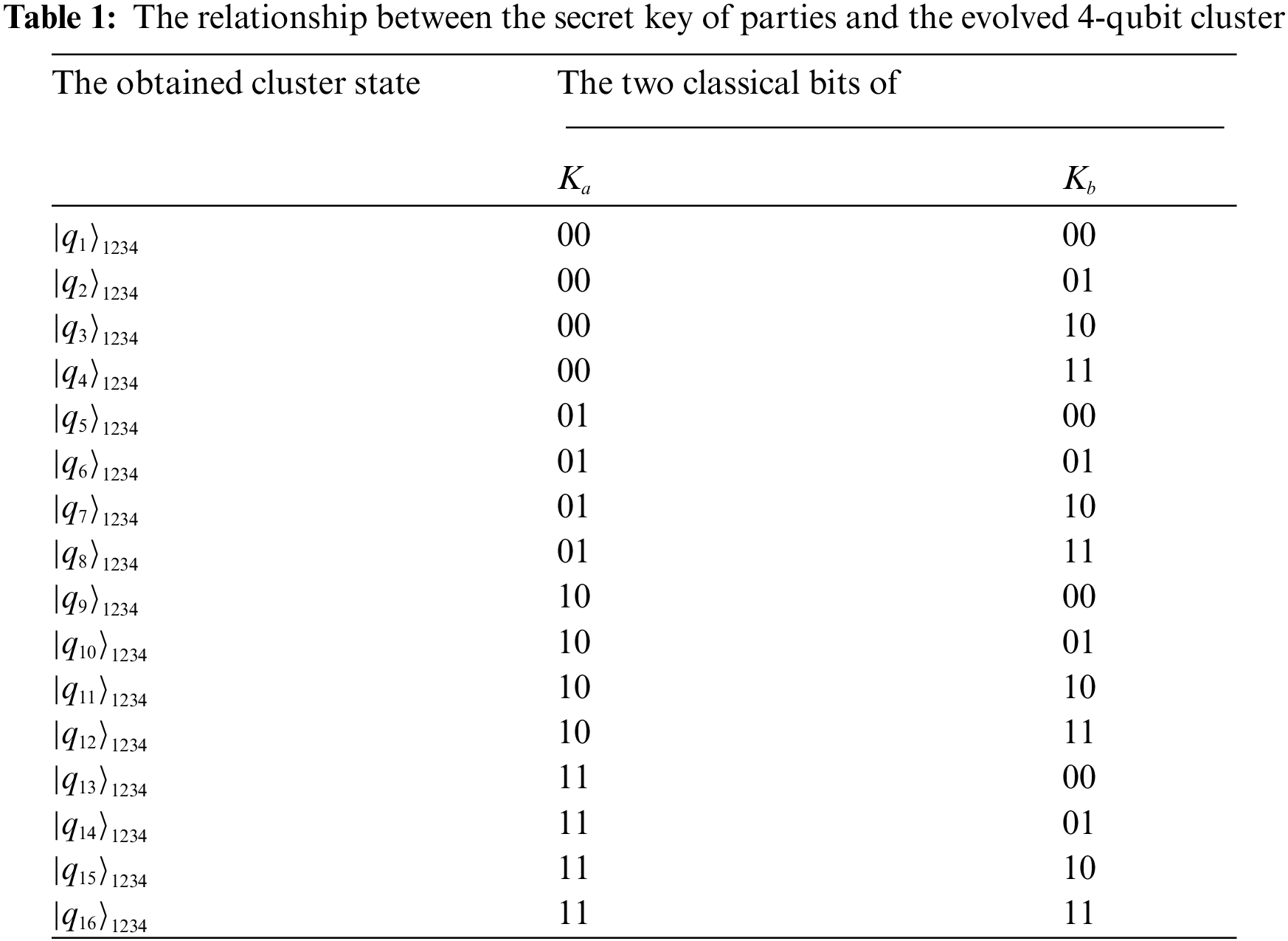
Assume that two parties Alice and Bob have two random secret keys
The relationship between secret key of parties and the evolved 4-qubit cluster is indicated in Tab. 1.
The steps of Liu-QKA's protocol can be described as follows:
(1) Each party (
(2) Upon
(3)
(4)
(5)
(6)
(7) After each
3 Collusive Attack on Liu-QKA Protocol and Improvement
We show in this section that Liu-QKA Protocol is vulnerable to a collusive attack, in which two dishonest players can obtain the secret information of an honest participant. Then, to address this flaw, an improvement is provided.
3.1 The Collusive Attack on Liu-QKA Protocol
The collusive attack on Liu-QKA scheme can be described as follows. Assume that we have three participants
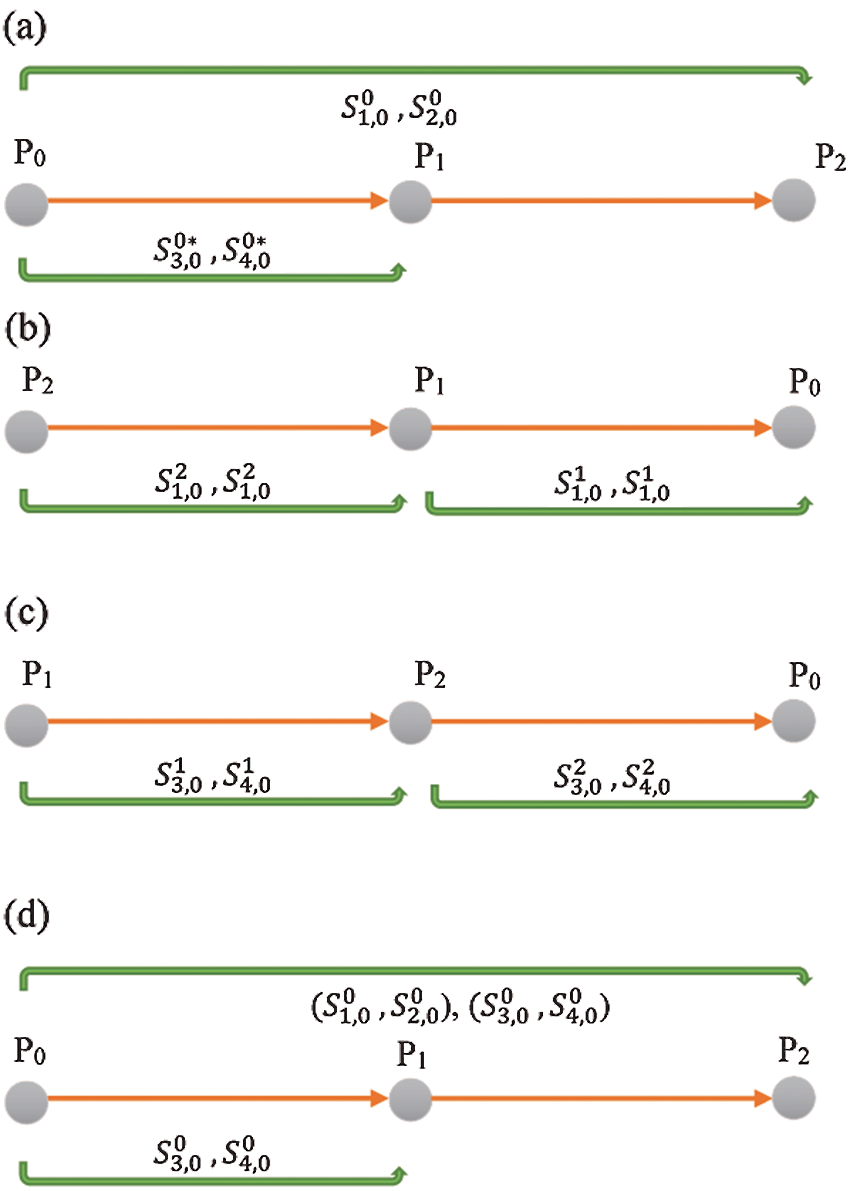
Figure 1: (a), (b), and (c) represent an example of the three-party Liu-QKA protocol, while (d) represents the collusive attack on Liu-QKA's protocol of three participants
3.2 Improvement on Liu-QKA Protocol
A third party is adopted in many exists circular multi-party QKA protocol, such as in Ref. [35] to provide participants random sequences of single-particle quantum states to cover their private keys, and in Ref. [36] to detect dishonest participants. In this work, we adopt a semi-honest third party (TP) with a certain task to address the security pitfall in Liu-QKA's protocol. Semi-honest means here that the TP executes the protocol honestly but not allowed to collude with other dishonest participants. The TP will collaborate with participants to detect internal attacks including the collusive attack. TP generates n random secret keys (
Steps (
The remaining steps should be modified as follows:
Liu et al. presented an interesting quantum key agreement protocol with four-qubit cluster quantum states, which could be used as an unconditional security solution for enhancing the security of 5G/6G networks against the increasing cyber-attacks. However, this work shows that Liu et al.'s protocol is vulnerable to collusive attacks, where dishonest participants can conspire together to obtain the private information of a trustworthy participant without being caught. With the help of a third party, we suggested an additional process to protect participants’ private data from leakage. Finally, an improvement is suggested to address the security loopholes in Liu et al.'s protocol.
Acknowledgement: The authors acknowledge the Academy of Scientific Research & Technology (ASRT) in Egypt for their financial support.
Funding Statement: This project was financially supported by the Academy of Scientific Research and Technology (ASRT) in Egypt, under the project of Science Up, Grant no. 6626.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. D. J. Bernstein and T. Lange, “Post-quantum cryptography,” Nature, vol. 549, no. 7671, pp. 188–194, 2017. [Google Scholar]
2. P. Porambage, G. Gür, D. P. M. Osorio, M. Liyanage, A. Gurtov et al.., “The roadmap to 6G security and privacy,” IEEE Open Journal of the Communications Society, vol. 2, pp. 1094–1122, 2021. [Google Scholar]
3. C. H. Bennett and G. Brassard, “Quantum cryptography: Public key distribution and coin tossing,” in Conf. on Computers, Systems and Signal Processing, Bangalore, India, vol. 175, 1984. [Google Scholar]
4. P. W. Shor and J. Preskill, “Simple proof of security of the BB84 quantum key distribution protocol,” Physical Review Letters, vol. 85, no. 2, p. 441, 2000. [Google Scholar]
5. S. J. Nawaz, S. K. Sharma, S. Wyne, M. N. Patwary and M. Asaduzzaman, “Quantum machine learning for 6G communication networks: State-of-the-art and vision for the future,” IEEE Access, vol. 7, pp. 46317–46350, 2019. [Google Scholar]
6. A. Manzalini, “Quantum communications in future networks and services,” Quantum Reports, vol. 2, no. 1, pp. 221–232, 2020. [Google Scholar]
7. I. B. Djordjevic, “On global quantum communication networking,” Entropy, vol. 22, no. 8, p. 831, 2020. [Google Scholar]
8. C. Wang, F. -G. Deng, Y. -S. Li, X. -S. Liu and G. L. Long, “Quantum secure direct communication with high-dimension quantum superdense coding,” Physical Review A, vol. 71, no. 4, p. 044305, 2005. [Google Scholar]
9. R. Qi, Z. Sun, Z. Lin, P. Niu, W. Hao et al., “Implementation and security analysis of practical quantum secure direct communication,” Light: Science & Applications, vol. 8, no. 1, pp. 1–8, 2019. [Google Scholar]
10. H. Abulkasim, S. Hamad, K. El Bahnasy and S. Z. Rida, “Authenticated quantum secret sharing with quantum dialogue based on Bell states,” Physica Scripta, vol. 91, no. 8, p. 085101, 2016. [Google Scholar]
11. H. Abulkasim, S. Hamad, A. Khalifa and K. El Bahnasy, “Quantum secret sharing with identity authentication based on Bell states,” International Journal of Quantum Information, vol. 15, no. 4, p. 1750023, 2017. [Google Scholar]
12. G. Gao, Y. Wang, D. Wang and L. Ye, “Comment on ‘Authenticated quantum secret sharing with quantum dialogue based on Bell states’,” Physica Scripta, vol. 93, no. 2, p. 027002, 2018. [Google Scholar]
13. H. Abulkasim, S. Hamad and A. Elhadad, “Reply to Comment on ‘Authenticated quantum secret sharing with quantum dialogue based on Bell states’,” Physica Scripta, vol. 93, no. 2, p. 027001, 2018. [Google Scholar]
14. D. Bouwmeester, J. -W. Pan, K. Mattle, M. Eibl, H. Weinfurter et al.., “Experimental quantum teleportation,” Nature, vol. 390, no. 6660, pp. 575–579, 1997. [Google Scholar]
15. H. Abulkasim, A. Mashatan and S. Ghose, “Quantum-based privacy-preserving sealed-bid auction on the blockchain,” Optik, vol. 242, p. 167039, 2021. [Google Scholar]
16. H. Abulkasim, A. Farouk, S. Hamad, A. Mashatan and S. Ghose, “Secure dynamic multiparty quantum private comparison,” Scientific Reports, vol. 9, no. 1, pp. 1–16, 2019. [Google Scholar]
17. H. Abulkasim, H. N. Alsuqaih, W. F. Hamdan, S. Hamad, A. Farouk et al., “Improved dynamic multi-party quantum private comparison for next-generation mobile network,” IEEE Access, vol. 7, pp. 17917–17926, 2019. [Google Scholar]
18. G. Zeng and C. H. Keitel, “Arbitrated quantum-signature scheme,” Physical Review A, vol. 65, no. 4, p. 042312, 2002. [Google Scholar]
19. N. Zhou, G. Zeng and J. Xiong, “Quantum key agreement protocol,” Electronics Letters, vol. 40, no. 18, pp. 1149–1150, 2004. [Google Scholar]
20. H. Abulkasim, A. Mashatan and S. Ghose, “Secure multiparty quantum key agreement against collusive attacks,” Scientific Reports, vol. 11, no. 1, pp. 1–8, 2021. [Google Scholar]
21. A. Elhadad, S. Abbas, H. Abulkasim and S. Hamad, “Improving the security of multi-party quantum key agreement with five-qubit brown states,” Computer Communications, vol. 159, pp. 155–160, 2020. [Google Scholar]
22. H. Abulkasim and A. Alotaibi, “Improvement on ‘multiparty quantum key agreement with four-qubit symmetric w state’,” International Journal of Theoretical Physics, vol. 58, no. 12, pp. 4235–4240, 2019. [Google Scholar]
23. H. Abulkasim, A. Farouk, H. Alsuqaih, W. Hamdan, S. Hamad et al.., “Improving the security of quantum key agreement protocols with single photon in both polarization and spatial-mode degrees of freedom,” Quantum Information Processing, vol. 17, no. 11, pp. 1–11, 2018. [Google Scholar]
24. S. -K. Chong, C. -W. Tsai and T. Hwang, “Improvement on “quantum key agreement protocol with maximally entangled states”, International Journal of Theoretical Physics, vol. 50, no. 6, pp. 1793–1802, 2011. [Google Scholar]
25. D. -S. Shen, W. -P. Ma and L. -l. Wang, “Two-party quantum key agreement with four-qubit cluster states,” Quantum Information Processing, vol. 13, no. 10, pp. 2313–2324, 2014. [Google Scholar]
26. H. Zhu, Z. Li, X. Wang and L. Chen, “Multi-party quantum key agreement protocol for smart home environment,” International Journal of Theoretical Physics, vol. 60, no. 10, pp. 3948–3960, 2021. [Google Scholar]
27. J. Tang, L. Shi, J. Wei, Y. Xue and H. Yu, “Novel multi-party quantum key agreement protocols under collective noise,” Modern Physics Letters B, vol. 35, no. 8, p. 2150137, 2021. [Google Scholar]
28. L. Li and Z. Li, “A verifiable multi-party quantum key distribution protocol based on repetitive codes,” Information Sciences, vol. 585, pp. 232–245, 2021. [Google Scholar]
29. X. Ma, C. Wang, Z. Li and H. Zhu, “Multi-party quantum key distribution protocol with new bell states encoding mode,” International Journal of Theoretical Physics, vol. 60, no. 4, pp. 1328–1338, 2021. [Google Scholar]
30. W. Zhao, R. Shi, Y. Feng and X. Ruan, “Conference key agreement based on continuous-variable quantum key distribution,” Laser Physics Letters, vol. 18, no. 7, p. 075205, 2021. [Google Scholar]
31. L. -J. Liu and Z. -H. Li, “A verifiable quantum key agreement protocol based on six-qubit cluster states,” The European Physical Journal D, vol. 75, no. 7, pp. 1–10, 2021. [Google Scholar]
32. J. Kim, “Entanglement of formation and monogamy of multi-party quantum entanglement,” Scientific Reports, vol. 11, no. 1, pp. 1–9, 2021. [Google Scholar]
33. Z. Cai, S. Liu, Z. Han and R. Wang, “A quantum blind multi-signature method for the industrial blockchain,” Entropy, vol. 23, no. 11, p. 1520, 2021. [Google Scholar]
34. H. -N. Liu, X. -Q. Liang, D. -H. Jiang, G. -B. Xu and W. -M. Zheng, “Multi-party quantum key agreement with four-qubit cluster states,” Quantum Information Processing, vol. 18, no. 8, pp. 1–10, 2019. [Google Scholar]
35. H. Cao and W. Ma, “Multi-party traveling-mode quantum key agreement protocols immune to collusive attack,” Quantum Information Processing, vol. 17, no. 9, pp. 1–14, 2018. [Google Scholar]
36. W. -C. Huang, Y. -K. Yang, D. Jiang, C. -H. Gao and L. -J. Chen, “Designing secure quantum key agreement protocols against dishonest participants,” International Journal of Theoretical Physics, vol. 58, no. 12, pp. 4093–4104, 2019. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |