DOI:10.32604/cmc.2022.027437

| Computers, Materials & Continua DOI:10.32604/cmc.2022.027437 |  |
| Article |
Quantum Remote State Preparation Based on Quantum Network Coding
1School of Information Engineering, Beijing Institute of Graphic Communication, Beijing, 102600, China
2School of Computer Science and Information Engineering, Zhejiang Gongshang University, Hangzhou, 310018, China
3Information Security Center, State key Laboratory of Networking and Switching Technology, Beijing University of Posts and Telecommunications, Beijing, 100876, China
4Department of Computer Science, National Textile University, Faisalabad, 37610, Pakistan
5School of Information Science and Technology, North China University of Technology, Beijing, 100144, China
6Advanced Cryptography and System Security Key Laboratory of Sichuan Province, China
*Corresponding Author: Yi-Ru Sun. Email: syr@mail.zjgsu.edu.cn
Received: 18 January 2022; Accepted: 08 March 2022
Abstract: As an innovative theory and technology, quantum network coding has become the research hotspot in quantum network communications. In this paper, a quantum remote state preparation scheme based on quantum network coding is proposed. Comparing with the general quantum remote state preparation schemes, our proposed scheme brings an arbitrary unknown quantum state finally prepared remotely through the quantum network, by designing the appropriate encoding and decoding steps for quantum network coding. What is worth mentioning, from the network model, this scheme is built on the quantum k-pair network which is the expansion of the typical bottleneck network—butterfly network. Accordingly, it can be treated as an efficient quantum network preparation scheme due to the characteristics of network coding, and it also makes the proposed scheme more applicable to the large-scale quantum networks. In addition, the fact of an arbitrary unknown quantum state remotely prepared means that the senders do not need to know the desired quantum state. Thus, the security of the proposed scheme is higher. Moreover, this scheme can always achieve the success probability of 1 and 1-max flow of value k. Thus, the communication efficiency of the proposed scheme is higher. Therefore, the proposed scheme turns out to be practicable, secure and efficient, which helps to effectively enrich the theory of quantum remote state preparation.
Keywords: Quantum remote state preparation; quantum network coding; quantum k-pair network
In 2000, quantum remote state preparation (RSP) was first proposed by Lo [1]. RSP enables the senders to prepare known states for remote receivers with the assistance of entangled resources [2,3] and classical communications [4,5]. With so many years of development, RSP has already made significant advances in theories [6–8] and applications [9–11]. In these researches, respect to the different target state, such as Bell state [12], GHZ state [13], W state [14], cluster state [15] and so on, various kinds of RSP schemes have been proposed. In addition, respect to the different implementation techniques, such as deterministic RSP [16], joint RSP [17] and controlled RSP [18], several schemes have also been proposed.
However, with the development of quantum communication and the requirement for multi-user’s quantum communication, point-to-point communication mode will necessarily toward to the direction of network communication. Thus, the research of RSP over the quantum network have become a meaningful task. In quantum network communications, as a breakthrough technology, quantum network coding (QNC) can effectively improve the quantum communication efficiency and quantum network throughput as compared to the traditional technology of routing. Since the first QNC scheme proposed by Hayashi et al. [19] in 2006, a series of QNC schemes have been put forward in theories [20–23] and applications [24–26] over the past decade. By QNC, the intermediate nodes are allowed to encode the received information and ultimately the destination nodes can recover the original unknown quantum state by decoding. Therefore, it is reasonable to believe that if combining RSP and QNC, the problem of quantum state preparation over quantum networks can be solved effectively.
In this paper, a novel RSP scheme based on QNC is proposed. This scheme is assisted by the resource of prior entanglement and classical communication, and the specified encoding or decoding operations are performed at the corresponding nodes. In terms of the quantum state, an arbitrary unknown quantum state possessed by the source nodes are finally prepared at the sink nodes; in terms of the success probability, this scheme can always achieve the success probability of 1; in terms of the network model, the quantum k-pair network as an expansion of the typical bottleneck network—butterfly network [27–29] in QNC is constructed to propose the scheme. Thus, the proposed scheme can effectively improve the communication efficiency and is more applicable to the scenarios of large-scale quantum networks, which can enrich the theory of quantum remote state preparation over quantum network.
The remainder of this paper is organized as follows. In Section 2, preliminaries including notations, quantum k-pair network, quantum operators and quantum measurements are presented. In Section 3, the specific RSP scheme based on QNC is proposed. In Section 4, the performance analyses including correctness, security, practicability and achievable rate region are discussed. At last, some concluding remarks are given in Section 5.
The following notations will be used throughout this paper:
Let us consider a directed acyclic graph (DAG) G = (V,E), where V is the set of nodes and E is the set of edges that connect pairs of nodes in V. K pairs of nodes
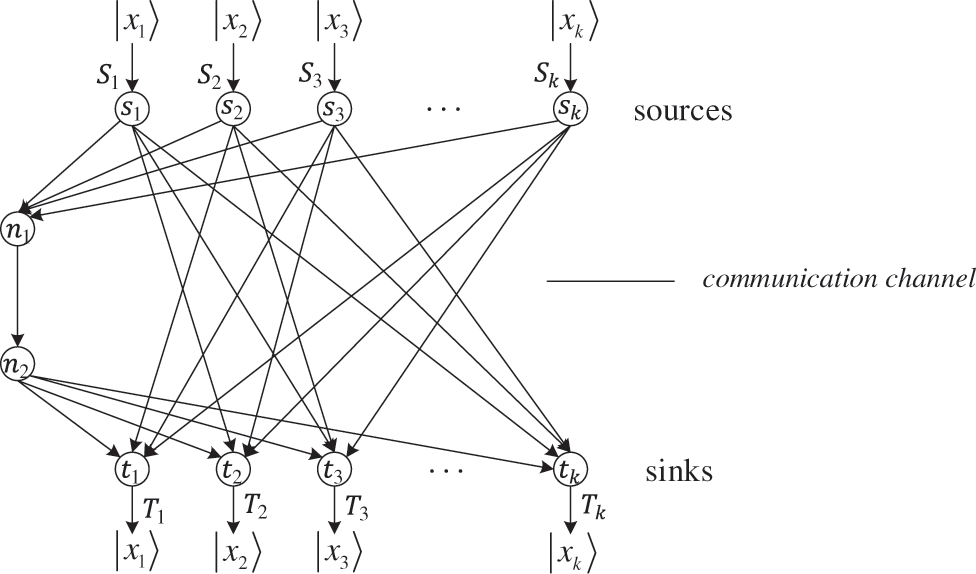
Figure 1: Quantum k-pair network
In this figure, the solid lines represent the quantum physical channels and the arrows indicate the transmission direction of the quantum information. Let
Firstly, let us introduce the controlled-X operation on a d-dimension quantum system
where
Then, another quantum operation named controlled-R operation on d-dimension quantum system
where
In the quantum system
where
In the quantum system
Hence, the basis states
3 A Quantum Remote Preparation Scheme Based on Quantum Network Coding
Suppose that the arbitrary k-qudit quantum state originally possessed at the source nodes
where all the amplitude coefficient
where for
Thus, the whole quantum system now becomes as
According to the task of RSP over the quantum k-pair network
Step 1: At each source node
Then, for
Step 2: At the intermediate node
Then, the quantum register
Step 3: At the intermediate node
Then, k quantum registers
Step 4: For each sink node
Step 5: At the intermediate node
we have the quantum state:
Then,
Step 6: At each source node
we obtain the quantum state:
Then,
Step 7: At the sink node
Afterwards,
Step 8: At the intermediate node
Then,
Step 9: At the sink node
Next, the phase is corrected by performing the quantum unitary operator mapping of the state
That is, the arbitrary k-qudit quantum state originally possessed by the source nodes is successfully prepared remotely at the sink nodes.
3.2 Example: The Butterfly Network Over
For the quantum k-pair network
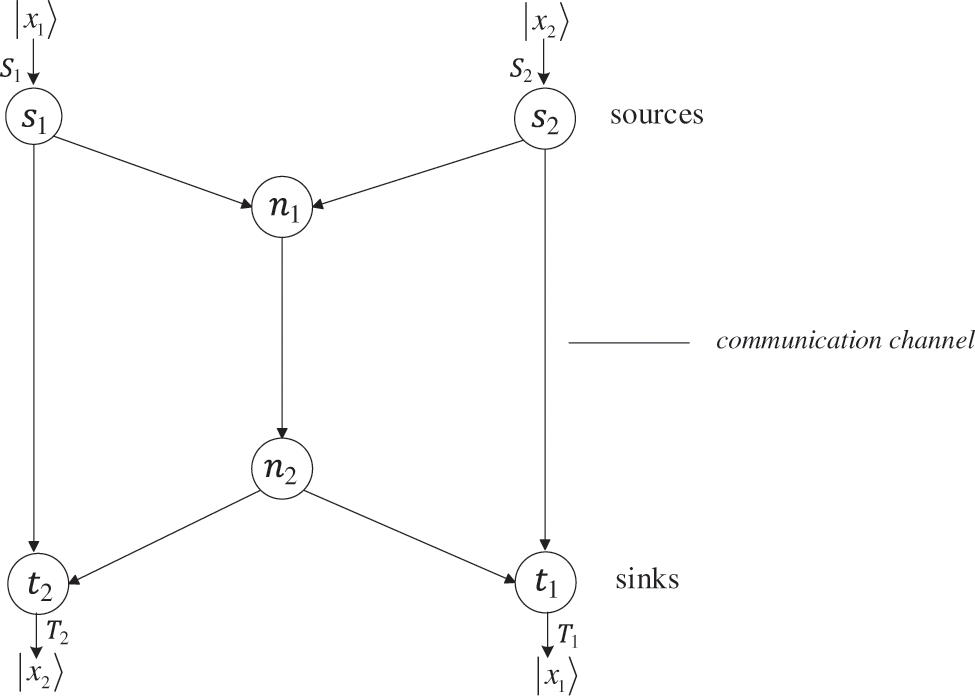
Figure 2: Quantum butterfly network
Here, the arbitrary 2-qubit quantum state originally possessed at the source nodes
And the source nodes
Thus, the initial quantum state of the whole system is
Hereafter, we proceed to the specific steps of the RSP scheme based on QNC. For step 1-step 4, it can be considered as the encoding process and the object is to make the particles in the quantum registers mutually entangled. The corresponding schematic diagram of quantum circuit can be shown in Fig. 3.
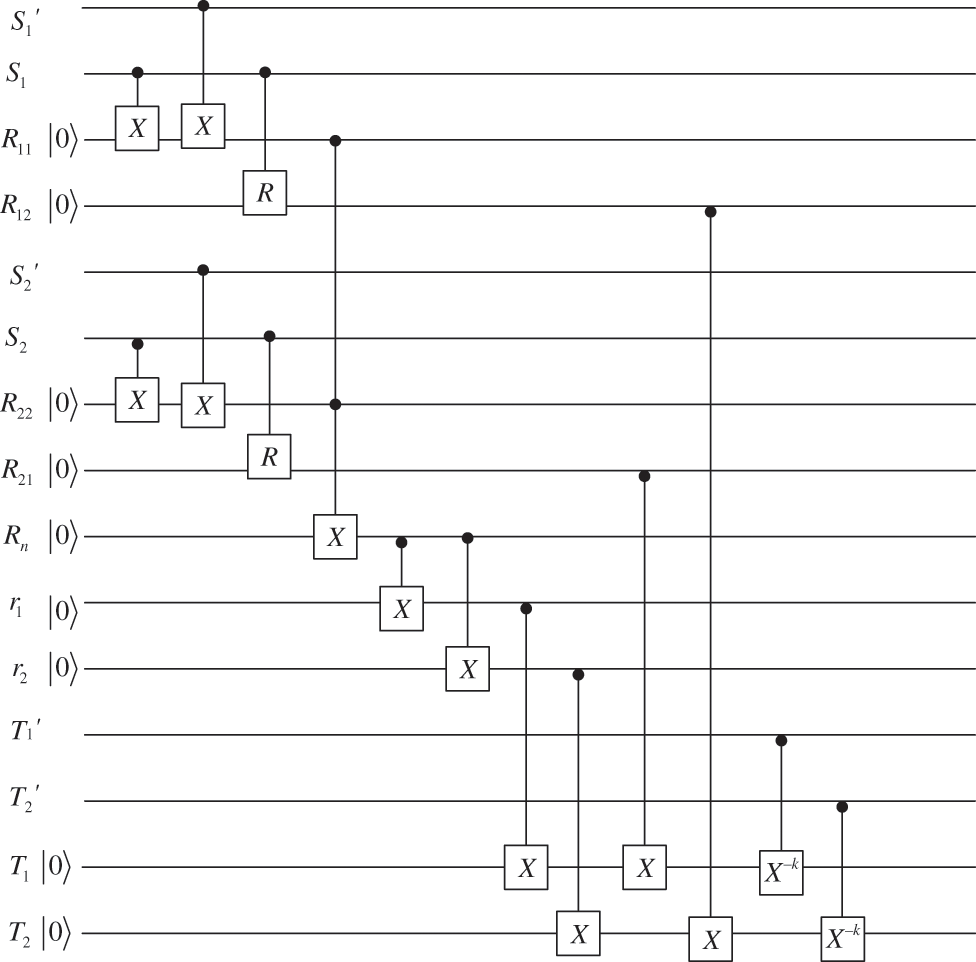
Figure 3: Schematic diagram of quantum circuit for steps 1–4
According to the specific calculations, after Step 1–4, the quantum states of the of the whole system becomes
Then, For Step 5-Step 9, it can be considered as the decoding process and the object is to remove the particles in the unnecessary quantum registers. The corresponding schematic diagram of quantum circuit can be shown in Fig. 4.

Figure 4: Schematic diagram of quantum circuit for steps 5–9
According to the specific calculations, the quantum states of Step 5–9 are detailed as follows:
Here, the global phases 1/2 can be ignored during computation, so the final quantum state at the sink nodes
That is, the arbitrary 2-qubit quantum state originally possessed by the source nodes is successfully prepared remotely at the sink nodes.
The correctness of the proposed RSP scheme based on QNC can be verified by the specific steps. From Section 2, in the Step 1–4, the particles at every network node are entangled to the whole quantum system by applying relevant quantum encoding operations. The resulting quantum state after the entanglement of each time is presented specifically. In the Step 5–9, by applying relevant quantum measurements called decoding operations, all the unnecessary particles are disentangled from the whole quantum system and leave alone the certain particles on the sink nodes. The resulting quantum state after the disentanglement of each time is also presented specifically. Thus, after all the encoding and decoding steps, the final quantum state at the sink nodes formed
In the existing RSP schemes [12–18], the quantum state desired to be prepared remotely is known for the senders, i.e., the amplitude coefficient and the phase coefficient is known. However, in many actual scenarios, if the senders are not honest, then the final quantum state prepared remotely is likely to be mistaken. In this paper, the proposed RSP scheme is based on QNC, which means that the senders do not need to know the desired quantum state and finally it can be prepared remotely. Therefore, the security of the proposed RSP scheme here is higher.
In the existing RSP schemes [12–18], the point-to-point communication mode is used. With the development of quantum communication, quantum network communication containing more users has become a necessity. In this paper, the proposed RSP scheme based on QNC is established over the quantum k-pair network which is the typical bottleneck network model. Using this scheme, the quantum network congestion can be solved effectively and the communication efficiency is higher. Thus, the proposed scheme can be more applicable to the scenarios of large-scale quantum networks.
As is known, the communication rate [34] between
Accordingly, in the presented RSP scheme based on QNC above, the desired arbitrary unknown quantum state is finally prepared successfully over the quantum k-pair network in single use of the network. Thus, the 1-flow [34] value reaches
under the condition that the capacity
In this paper, we propose a novel RSP scheme based on QNC over the quantum k-pair network. In terms of the quantum state, an arbitrary unknown quantum state is finally prepared at the sink nodes; in terms of the success probability, this scheme can always achieve the success probability of 1; in terms of the network model, the quantum k-pair network is the expansion of the typical bottleneck network—butterfly network. Thus, the proposed scheme can effectively improve the security and communication efficiency, and is more applicable to the large-scale quantum networks, which can enrich the theory of quantum remote state preparation.
Acknowledgement: We express our heartfelt thanks to the Beijing Institute of Graphic Communication for funding this study, as well as to the State Key Laboratory of Networking and Switching Technology for offering technical support.
Funding Statement: This work is supported by the National Natural Science Foundation of China (Grant Nos. 61370188, 62176273, 61962009), the Scientific Research Common Program of Beijing Municipal Commission of Education (KM202010015009, KM202110015004), Initial Funding for the Doctoral Program of BIGC (27170121001/009), the Open Foundation of State key Laboratory of Networking and Switching Technology (Beijing University of Posts and Telecommunications) (SKLNST-2021-1-16), the Open Fund of Advanced Cryptography and System Security Key Laboratory of Sichuan Province (Grant No. SKLACSS-202101) , the Fundamental Research Funds for Beijing Municipal Commission of Education, Beijing Urban Governance Research Base of North China University of Technology, and the Natural Science Foundation of Inner Mongolia (2021MS06006).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. H. K. Lo, “Classical communication cost in distributed quantum information processing-A generalization of quantum communication complexity,” Physical Review A, vol. 62, no. 1, pp. 012313, 2000. [Google Scholar]
2. Z. G. Qu, Y. M. Huang and M. Zheng, “A novel coherence-based quantum steganalysis protocol,” Quantum Information Processing, vol. 19, no. 362, pp. 1–19, 2020. [Google Scholar]
3. X. B. Chen, Y. R. Sun, G. Xu and Y. X. Yang, “Quantum homomorphic encryption scheme with flexible number of evaluator based on (k, n)-threshold quantum state sharing,” Information Sciences, vol. 501, pp. 172–181, 2019. [Google Scholar]
4. Z. G. Qu, H. R. Sun and M. Zheng, “An efficient quantum image steganography protocol based on improved EMD algorithm,” Quantum Information Processing, vol. 20, no. 53, pp. 1–29, 2021. [Google Scholar]
5. L. Sun, Y. L. Wang, Z. G. Qu and N. N. Xiong, “BeatClass: A sustainable ECG classification system in IoT-based eHealth,” IEEE Internet of Things Journal, 2021. DOI 10.1109/JIOT.2021.3108792. [Google Scholar] [CrossRef]
6. C. H. Bennett, D. P. DiVincenzo, P. W. Shor, J. A. Smolin, B. M. Terhal et al., “Remote state preparation,” Physical Review Letters, vol. 87, no. 7, pp. 077902, 2001. [Google Scholar]
7. A. K. Pati, “Minimum classical bit for remote preparation and measurement of a qubit,” Physical Review A, vol. 63, no. 1, pp. 014302, 2000. [Google Scholar]
8. I. Devetak and T. Berger, “Low-entanglement remote state preparation,” Physical Review Letters, vol. 87, no. 19, pp. 197901, 2001. [Google Scholar]
9. D. W. Berry and B. C. Sanders, “Optimal remote state preparation,” Physical Review Letters, vol. 90, no. 5, pp. 057901, 2003. [Google Scholar]
10. N. A. Peters, J. T. Barreiro, M. E. Goggin, T. C. Wei and P. G. Kwiat, “Remote state preparation: Arbitrary remote control of photon polarization,” Physical Review Letters, vol. 94, no. 15, pp. 150502, 2005. [Google Scholar]
11. X. Peng, X. Zhu, X. Fang, M. Feng, M. Liu et al., “Experimental implementation of remote state preparation by nuclear magnetic resonance,” Physics Letters A, vol. 306, no. 5-6, pp. 271–276, 2003. [Google Scholar]
12. D. W. Leung and P. W. Shor, “Oblivious remote state preparation,” Physical Review Letters, vol. 90, no. 12, pp. 127905, 2003. [Google Scholar]
13. Y. Xia, J. Song and H. S. Song, “Remote preparation of the N-particle GHZ state using quantum statistics,” Optics Communications, vol. 277, no. 1, pp. 219–222, 2007. [Google Scholar]
14. N. N. Wu and M. Jiang, “A highly efficient scheme for joint remote preparation of multi-qubit W state with minimum quantum resource,” Quantum Information Processing, vol. 17, no. 12, pp. 1–17, 2018. [Google Scholar]
15. K. Hou, “Joint remote preparation of four-qubit cluster-type states with multiparty,” Quantum Information processing,” vol. 12, no. 12, pp. 3821–3833, 2013. [Google Scholar]
16. S. Y. Ma, C. Gao, P. Zhang and Z. G. Qu, “Deterministic remote preparation via the brown state,” Quantum Information Processing, vol. 16, no. 4, pp. 1–22, 2017. [Google Scholar]
17. N. B. An, “Joint remote state preparation via W and W-type states,” Optics Communications, vol. 283, no. 20, pp. 4113–4117, 2010. [Google Scholar]
18. X. B. Chen, S. Y. Ma, Y. Su, R. Zhang and Y. X. Yang, “Controlled remote state preparation of arbitrary two and three qubit states via the brown state,” Quantum Information Processing, vol. 11, no. 6, pp. 1653–1667, 2012. [Google Scholar]
19. M. Hayashi, K. Iwama and H. Nishimura, “Quantum network coding,” in Proc. Symp. Theoretical Aspects of Computer Science, Lecture Notes in Computer Science, Aachen, Germany, vol. 4393, pp. 610–621, 2006. [Google Scholar]
20. M. Hayashi, “Prior entanglement between senders enables perfect quantum network coding with modification,” Physical Review A, vol. 76, no. 4, pp. 040301(R2007. [Google Scholar]
21. H. Kobayashi, F. Le Gall, H. Nishimura and M. Roetteler, “General scheme for perfect quantum network coding with free classical communication,” in Proc. of the 36th Int. Colloquium on Automata, Languages and Programming, Lecture Note in Computer Science, Rhodes, Greece, pp. 622–633, 2009. [Google Scholar]
22. H. Kobayashi, F. Le Gall, H. Nishimura and M. Roetteler, “Constructing quantum network coding schemes from classical nonlinear protocols,” in Proc. of the 2011 IEEE Int. Symp. Information Theory (ISIT), St. Petersburg, Russia, pp. 109–113, 2011. [Google Scholar]
23. S. Chen, G. Xu, X. Chen, H. Ahmad and Y. Chen, “Measurement-based quantum repeater network coding,” Intelligent Automation & Soft Computing, vol. 30, no.1, pp. 273–284, 2021. [Google Scholar]
24. P. Pathumsoot, T. Matsuo, T. Satoh, M. Hajdušek, S. Suwanna et al., “Modeling of measurement-based quantum network coding on a superconducting quantum processor,” Physical Review A, vol. 101, no. 5, pp. 052301, 2020. [Google Scholar]
25. Z. Li, Z. Li, X. Chen, Z. Qu, X. Wang et al., “A practical quantum network coding protocol based on non-maximally entangled state,” Computers, Materials & Continua, vol. 68, no. 2, pp. 2651–2663, 2021. [Google Scholar]
26. X. Pan, X. Chen, G. Xu, H. Ahmad, T. Shang et al., “Controlled quantum network coding without loss of information,” Computers, Materials & Continua, vol. 69, no. 3, pp. 3967–3979, 2021. [Google Scholar]
27. T. Satoh, F. Le Gall and H. Imai, “Quantum network coding for quantum repeaters,” Physical Review A, vol. 86, no. 3, pp. 032331, 2012. [Google Scholar]
28. T. Satoh, K. Ishizaki, S. Nagayamaand and R. Van Meter, “Analysis of quantum network coding for realistic repeater networks,” Physical Review A, vol. 93, no. 3, 032302, 2016. [Google Scholar]
29. Z. X. Zhang and Z. G. Qu, “Anti-noise quantum network coding protocol based on bell states and butterfly network model,” Journal of Quantum Computing, vol. 1, no. 2, pp. 89–109, 2019. [Google Scholar]
30. M. A. Nielsen and I. L. Chuang, “Quantum Computation and Quantum Information,” Cambridge University Press, Cambridge, 2000. [Google Scholar]
31. G. Xu, Y. Cao, S. Xu, K. Xiao, X. Liu et al., “A novel post-quantum blind signature for log system in blockchain,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 945–958, 2022. [Google Scholar]
32. M. Bellare, R. Canetti and H. Krawczyk, “Message authentication using hash functions: The HMAC construction,” RSA Laboratories’ CryptoBytes, vol. 2, no. 1, pp. 12–15, 1996. [Google Scholar]
33. J. Black, S. Halevi, H. Krawczyk, T. Krovetz and P. Rogaway, “UMAC: Fast and secure message authentication,” in Proc. of Annual Int. Cryptology Conf., California, USA, pp. 216–233, 1999. [Google Scholar]
34. S. Akibue and M. Murao, “Network coding for distributed quantum computation over cluster and butterfly networks,” IEEE Transactions on Information Theory, vol. 62, no. 11, pp. 6620–6637, 2016. [Google Scholar]
35. A. Jain, M. Franceschetti and D. A. Meyer, “On quantum network coding,” Journal of Mathematical Physics, vol. 52, no. 3, pp. 032201, 2011. [Google Scholar]
36. H. Nishimura, “Quantum network coding–how can network coding be applied to quantum information?,” in Proceeding of the 2013 IEEE Int. Symposium on Network Coding, Calgary, AB, Canada, pp. 1–5, 2013. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |