DOI:10.32604/cmc.2022.028990

| Computers, Materials & Continua DOI:10.32604/cmc.2022.028990 |  |
| Article |
Computer Vision Technology for Fault Detection Systems Using Image Processing
Computer Science Department, Prince Sattam Bin Abdulaziz University, Aflaj, Kingdom of Saudi Arabia
*Corresponding Author: Abed Saif Alghawli. Email: alghauly@yahoo.com
Received: 22 February 2022; Accepted: 19 April 2022
Abstract: In the period of Industries 4.0, cyber-physical systems (CPSs) were a major study area. Such systems frequently occur in manufacturing processes and people’s everyday lives, and they communicate intensely among physical elements and lead to inconsistency. Due to the magnitude and importance of the systems they support, the cyber quantum models must function effectively. In this paper, an image-processing-based anomalous mobility detecting approach is suggested that may be added to systems at any time. The expense of glitches, failures or destroyed products is decreased when anomalous activities are detected and unplanned scenarios are avoided. The presently offered techniques are not well suited to these operations, which necessitate information systems for issue treatment and classification at a degree of complexity that is distinct from technology. To overcome such challenges in industrial cyber-physical systems, the Image Processing aided Computer Vision Technology for Fault Detection System (IM-CVFD) is proposed in this research. The Uncertainty Management technique is introduced in addition to achieving optimum knowledge in terms of latency and effectiveness. A thorough simulation was performed in an appropriate processing facility. The study results suggest that the IM-CVFD has a high performance, low error frequency, low energy consumption, and low delay with a strategy that provides. In comparison to traditional approaches, the IM-CVFD produces a more efficient outcome.
Keywords: Cyber-physical system; image processing; computer vision; fault detection
Cyber-Physical Systems (CPS) are networks of cooperating intellectual entities that are in close contact also with the physical universe and its project requirements, while also delivering and utilizing Internet-based statistics and internet connectivity. In other terms, “engineering and physical networks whose functions are analyzed, managed, integrated, and connected by a computational and communication core” is a broad definition of CPS [1]. The interplay among the cyber security aspects is crucial: “CPS is really about the junction, not just the unification, of the physically and the digital,” says the author. It’s not enough to identify the condition and mathematical elements individually; you also need to know how they connect.” CPS, an Industrial revolution 4.0 term, is made up of computing and networking layers [2]. Whereas this cyber surface is where computations and equations are performed, the physical layer is where the wearable sensors are located. Although these two levels are divided, modulation schemes allow them to communicate closely. Fig. 1. shows a simplified block representation of the CPS architecture.
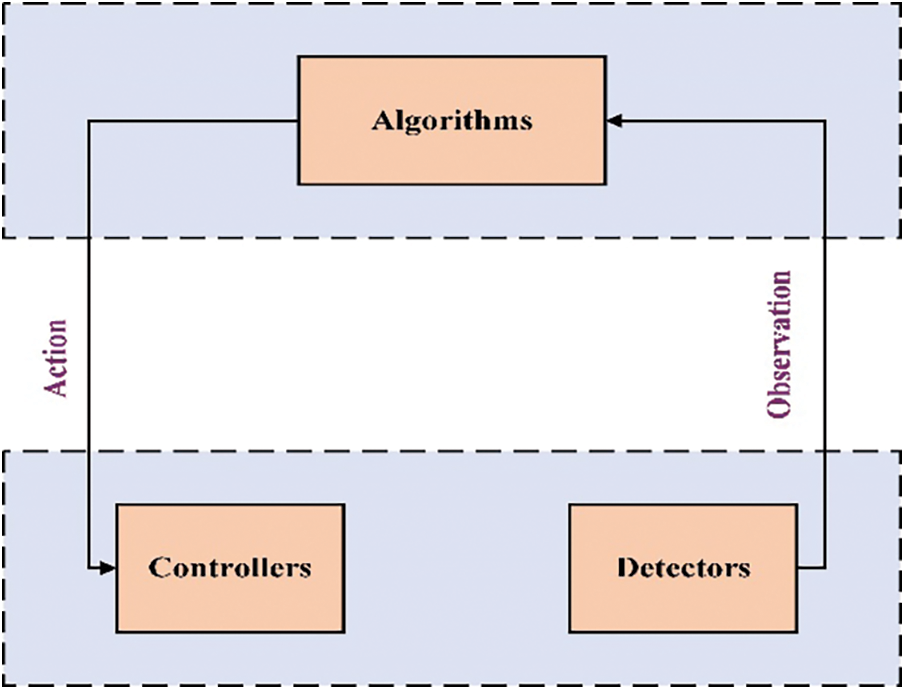
Figure 1: CPS design
Modern manufacturing networking, physiological, and computer vision methods were all established as part of defect monitoring and diagnostic technologies. There will be a large increase in the number of exposed physical processes, as well as continuous connectivity with local management data to respond effectively and more efficiently, posing several problems to both historically stable and separated network infrastructures [3]. CPS seems to have a hierarchical architecture and networking protocols are used to communicate across the levels, the systems may be vulnerable to networking or physical sensor intrusions. As a result, investigations on security are critical for spreading the CPS and ensuring its safe use, particularly in industrial contexts. The industry is also another sector where CPS will be used due to the general benefits it gives [4]. The CPS is favored over embedded systems due to the ease of usage of complex controllers including such fuzzy logic controllers. Moreover, cyber and physical layers are divided; any modification to the control scheme is considerably easier than with integrated devices. It is chosen by commercial processes where movement is critical since it makes the process live. Industry 4.0, which employs CPS in the workplace, is the clearest example of this [5]. Much research has been published in the literature to develop a CPS-based economy. Either of this research tries to verify information sent within real-time as from protocol stack to the cyberspace surface.
CPS’s success is determined by how the physical layer is represented in the cyber surface. Unpredictable events, like uncertainty, pose a hazard to any system, irrespective of how thoroughly it is designed. CPS is employed in critical systems, its proper operation is vital. The goal of this research is to identify abnormal motions that may develop as a result of probable uncertainty. The system is brought to a halt when an abnormal movement is detected [6]. As a result, potential costs can be avoided. In contrast to the previous study, the Image Processing Aided Computer Vision Technology for Fault Detection Technique (IM-CVFD) is examined and estimated using end–end aspects of the distributed infrastructure such as group activating mappings and uncertainty minimization. A CPS is made up of sensing, motors, computer systems, and networking that analyze and/or regulate the physical attributes of an artifact, such as the plant [7]. A CPS’s main feature is period transitioning. Unlike a quantum computer, which generates only a few state variables, CPS must nevertheless monitor and manage the time gap in-between areas.
The inherent complexity, diversity, and interdisciplinary character of cyber-physical systems (CPS) development are some of the most difficult difficulties [8]. Physical stability, management, computer vision, and error management are just a few of the heterogeneous features that are being integrated into information required CPS. Network elements are also frequently dispersed over many different places, physical hardware, and communications infrastructure. Even though model-based design (MBD) has greatly enhanced the creative process, CPS design poses a significant challenge. Modeling is supposed to help people comprehend a system better, but when they get too sophisticated, this feature is lost. This study illustrates how to leverage MBD’s aspect-oriented (AO) modeling tools to separate areas of knowledge and cross-cutting problems in a logical approach. Illustrate these principles using actor-oriented representations of automated robotic swarm applications and show how to control complexity using AO modeling tools. Demonstrate when to use AO modeling to explore system design.
The Cyber-Physical System (CPS) provides for the collection of various monitoring and alarm information from a wide range of manufacturing plant units. Reference [9] Propose new failures detection method based on machine learning and the world’s knowledge using alert information for this study. Several forms of alert information that revealed an operational breakdown in the Hyundai Steel plant were gathered as the initial stage in designing this new technology. With the help of 35 domain knowledge, examined and evaluated the alarm data. This suggests a Ripple Down Rule-based experience and understanding network based on the information. Machine learning is used to collect information, which is then preserved by human professionals. The assessment revealed that employing machine learning approaches, the suggested fault diagnosis approach may decrease the time and expense of acquiring human knowledge as well as the cost of fixing over-generalization and over-fitting concerns.
Traditional manufacturing providers are rapidly combining the cyber and physical domains for greater speed and adaptability in monitoring, administration, and control [10]. However, as these industrial cyber-physical systems become more integrated, possible security threats become much more severe. The frontal passive layer of the intrusion detection system plays a vital role in system security. Conventional means, on the other hand, tended to focus on cyberspace material with a structure of a typical physical property’s peculiarities, resulting in some restrictions. For industrialized cyber-physical systems, this study proposes an observable orientated zone partitioning mechanism for physical systems as well as a zone-based feature extraction strategy. First, an automatic zone partitioning technique is created to ensure that critical system variables could be expressed in more than a region. Then, even without a previous understanding of the physical environment, a method for creating zone functioning models and assessing linguistic factors on zone data is described. Finally, a real tested is built to ensure that the design strategy is useful. The experiments demonstrated that the proposed technique has a high degree of precision and real-time effectiveness.
Incorporation of humans into cyberspace Physical settings can indeed be supplemented electronically in a variety of ways [11]. To attain more successful procession networks, therefore, merging human skills and concrete knowledge necessitates techniques and technology programs that create personnel involvement inside system components in ways that make use of or enhance their cognitive capacities. This paper provides a fresh viewpoint for allowing the person in the loop involvement connected to cognitive skills, emphasizing the significance of context systems integration in engineering processes, after reviewing previous research. It also includes examples of technological solutions for bringing humans into the circle in a variety of application scenarios important to the manufacturing environment. The joint administration of connected data collected and expertise, as well as the capacity of learning algorithms for asset monitoring with embedding action recognition and IoT-driven analysis for product development processes, are all advantages of such a location.
Industrial analytics proposed system covers the process industry’s difficulties, as well as the conceptual design of industry Big Data analytical strategies that take into account the unique methodology of incorporating Information Mining into industrial cyber-physical systems (iCPS) [12]. This essay aims to assist in the creation of metrics Big Data applications for iCPS for database design, prescriptive analytics, inferential of critical success factors, and real-time business intelligence, by proposing a structure that will assist the incorporation of IIoT environment, communication services, and the platform as a service within iCPS. Building design information has been collected using an attribute-driven design (ADD) technique based on smart supply chain, process technology surveillance, and activities planned maintenance, replacement, and overhauling situations. The information management strategies described take into account modern Big Data modeling and analytics methodologies, demonstrating that data is a viable resource in iCPS. The author proposes a design and architecture standard for a Data Analytics system. In the iCPS setting, the previously described architecture enables the Industrial Internet of Things (IIoT) ecosystem, connectivity, and the clouds. The included changes are used to satisfy the meets specified objectives for Big Data technology in iCPS in a fault detection research study.
3.1 Cyber-Physical System (CPS) Architecture
The majority of scholars attribute CPS to integrated devices, that are characterized as a computer network integrated within an electrical or mechanical device that is supposed to execute devoted specified functions under real-time computation restrictions [13]. The close association and synchronization of computational and physical methods distinguish these intelligent systems [14]. Embedded systems technologies are connected in CPS to detect, analyze, and activate physical components in the actual environment, according to this notion. “The proposed research on Cyber-Physical Systems explores new scientific bases and technology to support the fast and effective adoption and implementation of technology and information-centric engineering and physical devices,” according to the meeting scheduled. The initiative’s purpose is to bring in a future generation of designed systems that are extremely reliable, cost-effectively manufactured, and competent in additional information, computing, communications, and networks that allow. The external layout is sensed and manipulated remotely, while management and quantitative measurements are enabled through a virtualized environment in a secure, accessible, and reliable manner. “Globally Virtually, Local Material” is the term used to describe this capacity.
The research is divided into two sections. The first step is to set up a prototype industrial CPS system, as described in the preceding section. However, the system may not function well due to a variety of factors. Here are a few examples:
• Incomplete or Incorrect information transmission
• Error synchronization
• Discover various things in the environment
If the process responds in ways that aren’t predicted, this could result in irreparable harm to the system’s components [15]. Then, the second half of this research focuses on detecting anomalous movement. Thus install a camera seeing the systems first to achieve this goal. To make the method work, need to make sure the sensor is secure and the lighting is consistent. After obtaining the standard environment, the static camera began recording. Following that, the system executes the motions required by the current instruction. To identify motion information, each frame of this motion is removed from the source images. Later, to improve the resilience of the distant vehicles, low values, that are most likely noise, are removed. After that, histogram equalization is performed to boost the image’s brightness. The data is resized to black and white (binary), and the image data contains important components [16]. The little elements in the image pixels are removed, and a binary mask is created. The mask is then dot produced with the underlying gray scale image, resulting in powerful objects moving remaining in the picture.
After obtaining the gray scale motion information, the feature was calculated using the image pixels of each image. The sum of all adjacent pixels in robust motion image pixels is used to generate the characteristic for each frame. This method is continued until motion is complete, and the attributes for each image are saved in an array because the movie comprises successive frames. Whenever the procedure is completed, a signal is constructed from the characteristics of each frame [17]. Establish a correlation matrix by correlating the resulting signal with the reference voltage that was established at the start. Between −1 and 1 seems to be the regression coefficients. And the highest number indicates that the impulses seem to be more comparable to one another. When it’s close to 0, it suggests the signals don’t have any relationship. Then, utilize threshold information to calculate whether or not the motion is predicted. The mechanism is suspended if the motion is unexpected, and the next order is not issued to the hardware elements. If there are no problems, the next instruction is fetched and transmitted to the core network elements. The steps are repeated, but the reference voltage is replaced with the signaling format of the valid and reliable group’s properties. Fig. 2. shows a comprehensive block diagram that explains the methods described.
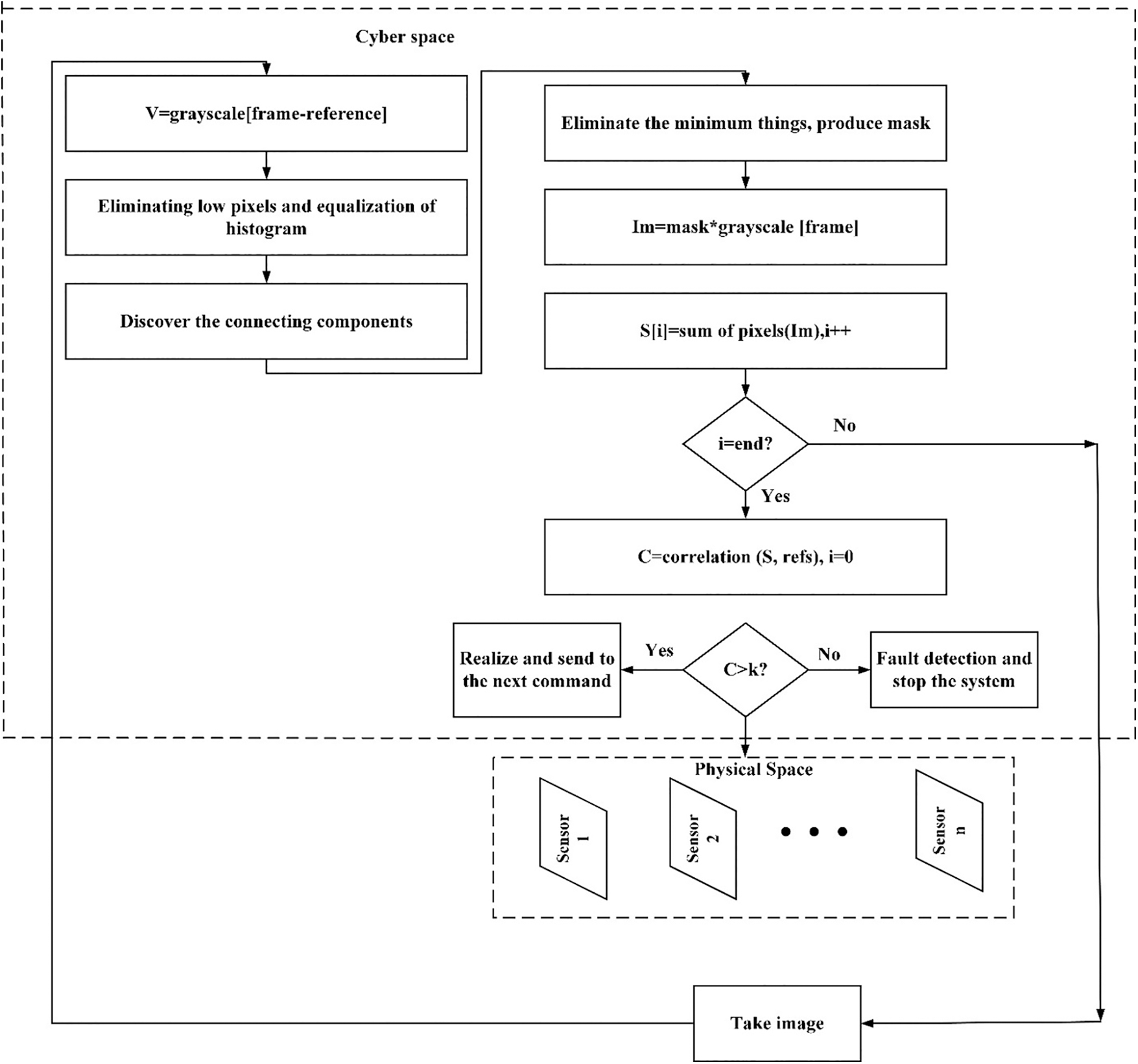
Figure 2: Image processing CPS
3.3 Computer Vision Technology for Fault Detection System
During the IM-CVFD, the cyber-physical system’s connections are arranged hierarchically, as seen in Fig. 3. The processing components are generally connected to each device, such as detectors, by a damage detection structure using stochastic and cyclic image processing via a computer vision network [18]. The processor groups are connected to a manufacturer’s network, which might connect these to a regionally organized sector. Because the CPS methods used at various rates and by various divisions aren’t intrinsically compatible, network nodes for information sharing may be required. In real-time, a firewall connects two manufacturing estates. Cyber-Real Systems (CPS) is networks of cooperative computing elements that would provide information and data processing services through the Network connection while being close to the physical world and its processes. The Cyber-Physical System (CPS), a new crop of communications circuits, focuses on intricate interdependencies and interactions among physics and cyber. A CPS is made up of a computer, communication, control, and physical components that are all closely interconnected. Because faulty loops and diagnosis could be synchronized, delay can happen. The following are the specific explanations for the components.
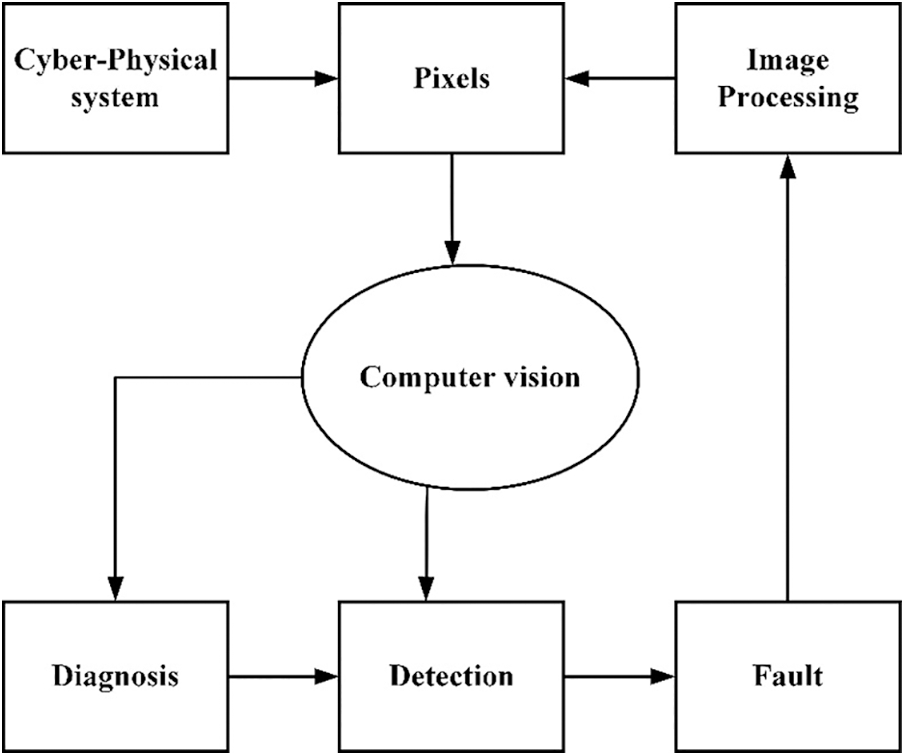
Figure 3: IM-CVFD model
The confidentially detecting networks are computer vision fault location solutions with set processing times, or each component comprises pre-allocated and defined detection components [19]. The factory units’ components, for example, comprise a controller that communicates with a specific implementation via a closed-loop control scheme, as shown in Fig. 4. As computer vision picture diagnostics and recognition procedures migrate into an output vector, sensors are frequently required to get sharper and occasionally generate disturbance if image levels approach fixed pixels. Furthermore, the requirements differ from the security devices detailed in the previous area, along with the better chance in that area. Distance, speed, effectiveness, and utilization are all factors to consider. This has been discovered that a circumstance consists of one probability computer vision conducted to examine the effect of conveying
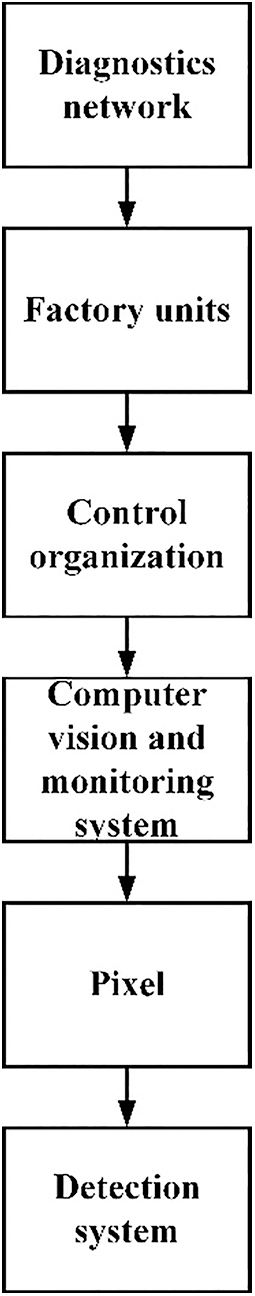
Figure 4: Diagnostics units
A CPS is made up of sensing; actuators, computer systems, and networking that analyze and/or regulate the physical features of an artifact, such as the factory. A CPS’s major characteristic is time transitioning. Unlike classical computing, which generates only a few state variables, CPS all must monitor and manage that time gap between such countries in particular. The CPS distribution is fixed. In a normal industrial economy, applications are assigned to secret data over time based on the data they send. The information is again assigned mechanistically, and contact faults are the sole determinant of trustworthiness. Assume that the program is furnished with confidential information for unpredictable implementation. To ignore diagnostic and also other possible errors, as well as to assume that extra identification is not lost, the state’s dependability signifies n is the chance that
Despite considering delay time
where, m has been normalized to offer at least single communication
Furthermore, if two or more transactions traverse the very same sensitive information like in Eq. (4), an occasional breakdown, similar to the preceding technique:
The fault detection of the automotive steering system is addressed in this paper. Because the objects under consideration contain significant dynamics and fluctuations, both online monitoring techniques and ensembles learning methods are viable options for data-driven fault detection systems development [23]. It’s worth noting that the online tracking approaches and ensemble learning systems are used to solve two different fault detection problems: the Performance indicators challenge and the employments adaption problem. Because the focus of this work is on KPI-based detection of faults, the earlier concept will be developed further in the following part, but this will also be briefly covered here. The different designs are summarized to demonstrate the theory’s reliability. The collective learning strategy is as follows: The real-time observations are gathered first. Next, sample data from such a group of local methods are presented to criteria, and the selection logic is linked to surroundings detection methods. A training block has been included to allow for the possibility of dealing with changing conditions for workers. Finally, the sample data from the model parameters are analyzed further. Every localized modeling only includes a portion of the distributions knowledge since it represents the input vector with a restricted number of measurements. In terms of pattern classification, every localized framework establishes a local classification model, which is an ineffective sensor due to the limited datasets used to create them. The likelihood of the four causes of identification of image
The result of a fault detection functional that does not incorporate uncertainty, described as a “standard functional” in this section,
The planned Group Activation Mapping (GAM) control strategy has a few essential terms. By using GAM, every system is selected and assigned a path that meets its QoS criteria. There at end of this process, the low output to every section is determined. Finally, depending on the method GAMGCSR for internally and externally detection of defects, the preserved data is normally assigned to the representation.
3.4.1 Group Activation Mapping (GAM)
The information is defined to meet their aims by urgency, energy, and performance criteria, due to the high complexity of fault detection facilities. The suggested design is made up of three different production simulations. The first, High-Definition Speed and Efficient Critical, receives the most attention and adds the most value in terms of QoS, productivity, and dependability [25]. This necessitates the use of a range of manufacturing computer vision technologies, such as emergency brakes and safety devices. Latency and excellent performance are becoming less important, and efficiency is being prioritized. This state is provided by scale reading apps. The final paragraph of this paper is a low assessment of delay and effectiveness, with assured QoS and production taking second place. It’s a typical word for measuring an Ip address, and it varies from Run stream Time (RTT) in that it only measures one intermediate node [1]. Asymmetrical transmissions among two network elements are possible, but that does not imply forward or reversal latency. Half RTT is an average of backward and forward latencies that could be used to simulate end-to-end deceleration in some cases. The GAM has been used to allocate equipment to the related categories by examining the quantities required as an auditory and online grouping image analysis and computing the bandwidth utilization as shown in Eq. (6). By using a training dataset of labeled images, mathematical classification techniques belonging to supervised learning approaches are developed to reliably identify redundancy, faults, and unusual samples in the event of failure diagnosis and detection. In the last several decades, different categorization and pre-processing methods have been created and suggested in these study fields.
The characteristics of a
3.4.2 Under Color Removal (UCR)
The images of computer vision processors are used to improve and maximize the allocation of internally and externally resources [27]. This is also achieved at this stage by optimizing the
As a result, computer vision signals are used to predict individual and identify errors in economic CPS devices. The examined model process was done to acquire the significant findings.
The proposed technique IM-CVFD has been confirmed by simulations in this chapter. Several weak sensor data have already been designed and improved, according to the findings. Within an area, individuals are usually deployed. The architecture of the IM-CVFD is first discussed. Computer vision seems to have a massive effect on enterprises across all sectors, from commerce to agriculture. While working with difficulties that necessitate the use of a visual system to evaluate the damage, it is advantageous. A large number of computer vision tasks have not been discovered or expanded due to numerous flaws in those standards. Cameras have been used to monitor the activity of the skeletal system without the need for typical optical indicators or specialized cameras. Capturing sports that do not require additional capturing apparel or technology is critical. This would impose the GAM algorithm’s Fixed Configuration for pixel mappings. The simulated requirements for any such are the same; however, there is no QoS limitation. The goal is to use the UCR algorithms to investigate the QoS potential for reducing approach results and compare it to traditional power consumption, transmission latencies, and suitable design. In response to directives from the cyber layer, the structural components have already been effectively implemented. The photos are then delivered to a computer, which receives control instructions and performs a fault movement detection approach on the shots. As a result, the fault movement’s outcome is obtained. Tab. 1 shows the instruction loop being sent from such a home computer. With repeated instructions, the design allows a continual start taking motion.

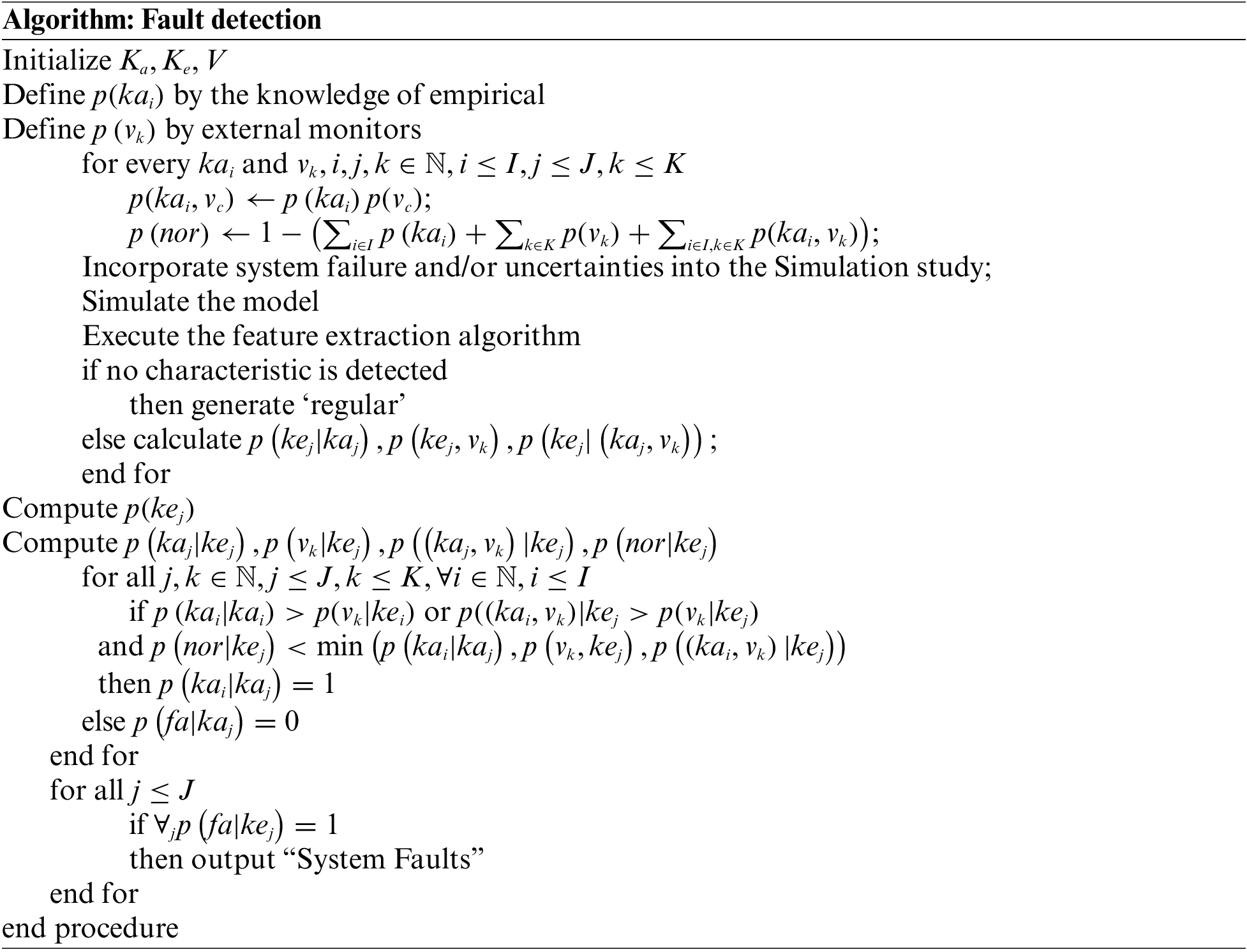
The implementation of the developed IM-CVFD in terms of detection and treatment is evaluated using the parameter simulation model shown in Fig. 5. The results of the investigation demonstrate that the suggested approach is well adapted for defect detection in the managing sector of the private computer vision CPS program. When opposed to prior network tactics, the product’s usable condition is a pinnacle. In contrast, the IMCVFD architecture is still first, and it is a new method of developing CPS programs that are built on it. Fig. 5 depicts the IM-superior CVFD’s performance as well as the most modeling.
The effectiveness of the presented IM-CVFD is shown in Fig. 6. It detects inefficient pixel faults with great precision. The algorithm is examined statistically to determine which method produces the best results with varied numbers of pixels. It offers superior results to the pre-existing algorithmic technique. The number of feasible cases is increased by focusing on delay dispersion constraints rather than precision efficiency. Even though numerous traffic arriving distributions can be used, they are not appropriate for traffic models. The focus of the theory is on the distribution and functionality models that relate to work throughout a queue.
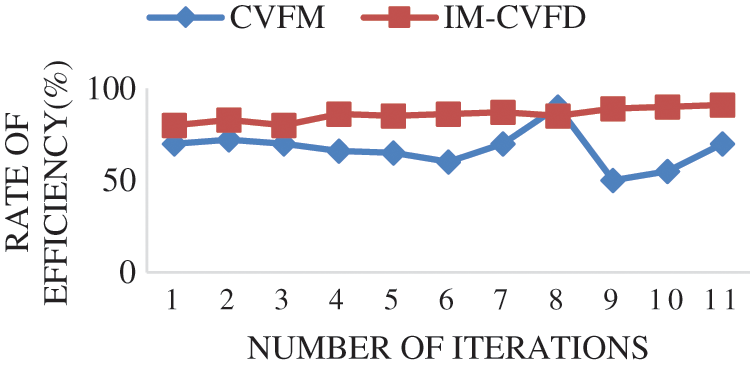
Figure 5: IM-CVFD efficiency rate
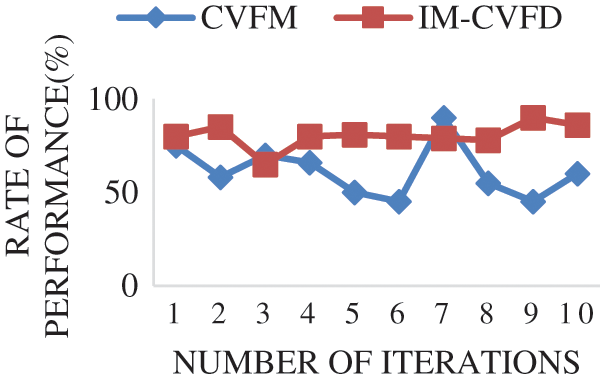
Figure 6: IM-CVFD performance rate
Using safety caution, Fig. 7 represents the overall failure rate of the IM-CVFD procedure in the CPS system. It provides a lower process error rate than conventional techniques. It is clear from the figure that the total failure rate in the IM-CVFD procedure is relatively low. It displays the failure rate of the UCR application’s fault-finding procedure. It, like the IM-CVFD, achieves a good performance. It provides greater performance than previous approaches when the failure rate drops. The present fault diagnosis CPS approaches benefit the environment in the distributed information pixels. The simulations are used to recommend and run IM-CVFD to reduce unauthorized access. Analytical model, Fig. 8 concluded that using the suggested strategy, resource access may be reduced. Because of the increase in application, the source of energy has increased. To reduce undesired access to the growing number of applications, the proposed solution uses a lower consumption proportion than other alternatives.
Figure 7: IM-CVFD Failure rate
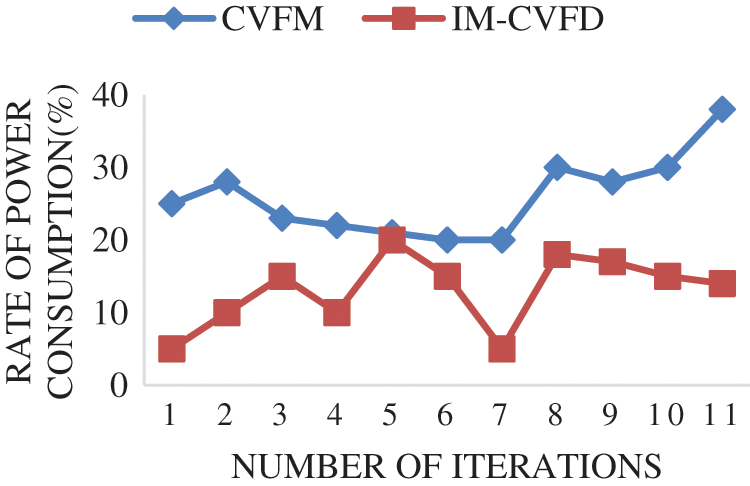
Figure 8: Rate of power consumption
Its error may be excessively low in comparison to traditional models, as seen in Fig. 9. Because the UCR was implemented in CPS safety’s developing design, the error rate has decreased twofold, indicating that the data is being processed more efficiently. Traditional systems have a higher failure rate than the proposed methods. As the error rate decreases, the model’s favorable aspects improve, and the suggested method’s viability for succeeding generations of industry sectors improves. As seen in Fig. 10, the parametric latency is reduced. After applying the IM-CVFD and GAM algorithms, there is no discernible latency within information identification of CPS errors, as shown in the graphs. The main strategy was based on existing ways to demonstrate its superiority, and it is proven. The manufacturing groups are connected to either a system of producers, which can attach these to such a regionally structured industry. Because the CPS methods used at various rates and by various divisions are not intrinsically compatible, network nodes for organizational learning may be required.
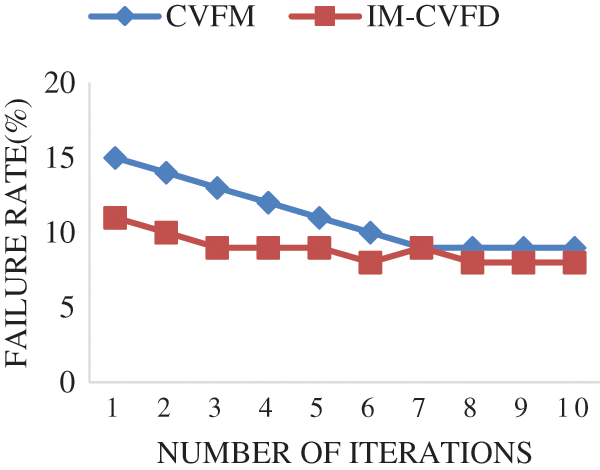
Figure 9: UCR failure rate
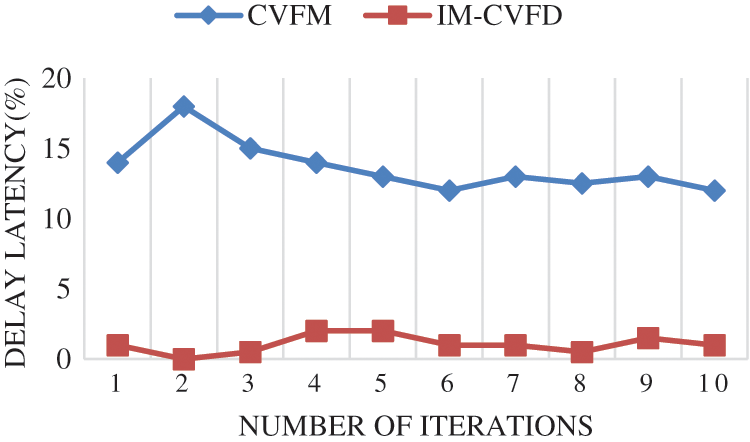
Figure 10: Parametric latency
The durability of CPS is significant as mission-critical and large-scale systems like them. Sudden changes in systems can arise due to a variety of factors. To meet the needs for great results, the design security benefits should be used. In this context, a networking IM-CVFD approach has been introduced to comply automatically and interactively with effectiveness requirements using computer vision data. To begin with, the IM-CVFD has suggested allocating the necessary sections to meet the demands and calculate the average capacity sections’ requirements. Second, particular procedures have now been required to ensure that the Group activation mapping (GAM) and UCR algorithms are effectively assigned to the pixel’s representations. The results of the simulations demonstrate that the proposed method is valid for privacy protection in the fault diagnosis CPS system when compared to the core of the system. The signal acquisition is related to the existing signals, as well as the device is determined to be functional for each step of motion. As a result, the state’s scale operations are ensured, and the CPS’s durability is strengthened. This research also serves as an alternative means of control for Industrial 4.0, which strives for completely autonomous manufacturing.
Funding Statement: The author received no specific funding for this study.
Conflicts of Interest: The author declare that he has no conflicts of interest to report regarding the present study.
1. Y. He, B. Nie, J. Zhang, P. M. Kumar and B. Muthu, “Fault detection and diagnosis of cyber-physical system using the computer vision and image processing,” Wireless Personal Communications, vol. 5, no. 4, pp. 1–20, 2021. [Google Scholar]
2. Y. Chen, R. S. Blum, B. M. Sadler and J. Zhang, “Testing the structure of a gaussian graphical model with reduced transmissions in a distributed setting,” IEEE Transactions on Signal Processing, vol. 67, no. 20, pp. 5391–5401, 2019. [Google Scholar]
3. M. Karaköse and H. Yetiş, “A cyberphysical system based mass-customization approach with integration of industry 4.0 and smart city,” Wireless Communications and Mobile Computing, vol. 2017, pp. 1–9, 2017. [Google Scholar]
4. L. Monostori, B. Kadar, T. Bauernhansl, S. Kondoh, S. Kumara et al., “Cyber-physical systems in manufacturing,” CIRP Annals, vol. 65, no. 2, pp. 621–641, 2016. [Google Scholar]
5. Y. Jiang and S. Yin, “Recursive total principle component regression based fault detection and its application to vehicular cyber-physical systems,” IEEE Transactions on Industrial Informatics, vol. 14, no. 4, pp. 1415–1423, 2018. [Google Scholar]
6. M. Kadar, R. Jardim-Goncalves, C. Covaciu and S. Bullon, “Intelligent defect management system for porcelain industry through cyber-physical systems,” in 2017 Int. Conf. on Engineering, Technology and Innovation (ICE/ITMC), Funchal, pp. 1338–1343, 2017. [Google Scholar]
7. C.-C. Sun, C.-C. Liu and J. Xie, “Cyber-physical system security of a power grid: State-of-the-art,” Electronics, vol. 5, no. 4, pp. 40, 2016. [Google Scholar]
8. I. Akkaya, P. Derler, S. Emoto and E. A. Lee, “Systems engineering for industrial cyber-physical systems using aspects,” Proceedings of the IEEE, vol. 104, no. 5, pp. 997–1012, 2016. [Google Scholar]
9. D. Kim, S. C. Han, Y. Lin, B. H. Kang and S. Lee, “RDR-based knowledge based system to the failure detection in industrial cyber physical systems,” Knowledge-Based Systems, vol. 150, no. 5, pp. 1–13, 2018. [Google Scholar]
10. J. Yang, C. Zhou, S. Yang, H. Xu and B. Hu, “Anomaly detection based on zone partition for security protection of industrial cyber-physical systems,” IEEE Transactions on Industrial Electronics, vol. 65, no. 5, pp. 4257–4267, 2018. [Google Scholar]
11. C. Emmanouilidis, P. Pistofidis, L. Bertoncelj, V. Katsouros, A. Fournaris et al., “Enabling the human in the loop: Linked data and knowledge in industrial cyber-physical systems,” Annual Reviews in Control, vol. 47, no. 5, pp. 249–265, 2019. [Google Scholar]
12. E. A. Hinojosa-Palafox, O. M. Rodríguez-Elías, J. A. Hoyo-Montaño, J. H. Pacheco-Ramírez and J. M. Nieto-Jalil, “An analytics environment architecture for industrial cyber-physical systems big data solutions,” Sensors, vol. 21, no. 13, pp. 4282, 2021. [Google Scholar]
13. C. Liu and P. Jiang, “A cyber-physical system architecture in shop floor for intelligent manufacturing,” Procedia CIRP, vol. 56, no. 2, pp. 372–377, 2016. [Google Scholar]
14. X. Zhang, X. Sun, W. Sun, T. Xu, P. Wang et al., “Deformation expression of soft tissue based on BP neural network,” Intelligent Automation & Soft Computing, vol. 32, no. 2, pp. 1041–1053, 2022. [Google Scholar]
15. J. Herwan, S. Kano, R. Oleg, H. Sawada and N. Kasashima, “Cyber-physical system architecture for machining production line,” in 2018 IEEE Industrial Cyber-Physical Systems (ICPS), St. Petersburg, Russia, pp. 387–391, 2018. [Google Scholar]
16. X. Zhang, X. Chen, W. Sun and X. He, “Vehicle re-identification model based on optimized densenet121 with joint loss,” Computers, Materials & Continua, vol. 67, no. 3, pp. 3933–3948, 2021. [Google Scholar]
17. S. ur Rehman and V. Gruhn, “Recommended architecture for car parking management system based on cyber-physical system,” in 2017 Int. Conf. on Engineering & MIS (ICEMIS), Monastir, pp. 1–6, 2017. [Google Scholar]
18. H. Wang, J. Liu and J. Han, “RS-CPS: A distributed architecture of robotic surveillance cyber-physical system in the nature environment,” in 2015 IEEE Int. Conf. on Cyber Technology in Automation, Control, and Intelligent Systems (CYBER), Shenyang, China, pp. 1287–1292, 2015. [Google Scholar]
19. P. J. Mosterman and J. Zander, “Industry 4.0 as a cyber-physical system study,” Software and Systems Modeling, vol. 15, no. 1, pp. 17–29, 2016. [Google Scholar]
20. J. Jamaludin and J. M. Rohani, “Cyber-physical system (CPSState of the art,” in 2018 Int. Conf. on Computing, Electronic and Electrical Engineering (ICE Cube), Quetta, Pakistan, pp. 1–5, 2018. [Google Scholar]
21. E.-Y. Kang, D. Mu, L. Huang and Q. Lan, “Verification and validation of a cyber-physical system in the automotive domain,” in 2017 IEEE Int. Conf. on Software Quality, Reliability and Security Companion (QRS-C), Prague, Czech Republic, pp. 326–333, 2017. [Google Scholar]
22. P. Guo, P. O. Dusadeerungsikul and S. Y. Nof, “Agricultural cyber physical system collaboration for greenhouse stress management,” Computers and Electronics in Agriculture, vol. 150, no. 1, pp. 439–454, 2018. [Google Scholar]
23. C. Yu, S. Jing and X. Li, “An architecture of cyber physical system based on service,” in 2012 Int. Conf. on Computer Science and Service System, Nanjing, China, pp. 1409–1412, 2012. [Google Scholar]
24. L. Wang and Y. Zhang, “Linear approximation fuzzy model for fault detection in cyber-physical system for supply chain management,” Enterprise Information Systems, vol. 15, no. 7, pp. 966–983, 2021. [Google Scholar]
25. L. V. Calderita, A. Vega, S. Barroso-Ramírez, P. Bustos and P. Núñez, “Designing a cyber-physical system for ambient assisted living: A use-case analysis for social robot navigation in caregiving centers,” Sensors, vol. 20, no. 14, pp. 4005, 2020. [Google Scholar]
26. J. Lee, B. Bagheri and H.-A. Kao, “A cyber-physical systems architecture for industry 4.0-based manufacturing systems,” Manufacturing Letters, vol. 3, pp. 18–23, 2015. [Google Scholar]
27. L. J. Camp, G. Amvrosiadis, A. R. Butt, V. Tarasov, E. Zadok et al., “Failures of dynamic control systems,” 2019. [Online]. Available: https://www.usenix.org/system/files/login/issues/login_winter19_issue.pdf. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |