DOI:10.32604/cmc.2022.028765

| Computers, Materials & Continua DOI:10.32604/cmc.2022.028765 |  |
| Article |
Mordell Elliptic Curve Based Design of Nonlinear Component of Block Cipher
1Department of Mathematics, Quaid-i-Azam University, Islamabad, Pakistan
2Department of Mathematics, College of Science, King Khalid University, Abha, Saudi Arabia
3Department of Computer Science, University of Tabuk, Tabuk, 71491, Saudi Arabia
4Department of Information Technology, University of Tabuk, Tabuk, 71491, Saudi Arabia
*Corresponding Author: Hafeez ur Rehman. Email: hrehman@math.qau.edu.pk
Received: 16 February 2022; Accepted: 14 April 2022
Abstract: Elliptic curves (ECs) are deemed one of the most solid structures against modern computational attacks because of their small key size and high security. In many well-known cryptosystems, the substitution box (S-box) is used as the only nonlinear portion of a security system. Recently, it has been shown that using dynamic S-boxes rather than static S-boxes increases the security of a cryptosystem. The conferred study also extends the practical application of ECs in designing the nonlinear components of block ciphers in symmetric key cryptography. In this study, instead of the Mordell elliptic curve (MEC) over the prime field, the Galois field has been engaged in constructing the S-boxes, the main nonlinear component of the block ciphers. Also, the proposed scheme uses the coordinates of MEC and the operation of the Galois field to generate a higher number of S-boxes with optimal nonlinearity, which increases the security of cryptosystems. The proposed S-boxes resilience against prominent algebraic and statistical attacks is evaluated to determine its potential to induce confusion and produce acceptable results compared to other schemes. Also, the majority logic criteria (MLC) are used to assess the new S-boxes usage in the image encryption application, and the outcomes indicate that they have significant cryptographic strength.
Keywords: Galois field; Mordell elliptic curve; nonlinearity; substitution box
When it comes to electronic data transfer, digital technology and network communications have had a significant impact during the past few decades. Various issues about the privacy of sensitive data transmissions through open communication networks arise, as most of these networks are exposed to the public. Cryptography, steganography, and watermarking are the most common methods for securing information. The robust watermarking algorithm is presented in [1,2] to assure the safe transmission and storage of medical data and to prevent the leakage of patient information in telemedicine. Consequently, the security of sensitive data has been a significant focus of cryptography in recent decades. The researchers have proposed various information security strategies to counter the most recent security threats. S-box is a nonlinear component in numerous famous algorithms, especially in advanced encryption standards (AES) [3]. The security of all such cryptosystems is thus reliant on the cryptographic aspects of these S-boxes. Because of this, many researchers have expressed an interest in developing new and more effective S-boxes. The S-box is predicated on algebraic systems, which are impervious to linear and differential cryptanalysis; they have received a lot of interest because of their solid cryptographic properties. Thus, secure transmission based on various classes of S-boxes is always promoted. Like the AES, the affine power affine (APA) S-box is presented to increase algebraic complexity while maintaining accessible encryption features [4]. In [5], the action of the symmetric group
ECs have recently gained a lot of interest in the cryptography sector. The techniques based on ECs are the most extensively used for enhancing information security. We will concentrate on EC-based cryptography and the various methods presented by numeral experts in this domain. Cheon et al. [9] characterized S-boxes by offering the relation between nonlinearity of rational functions over
The following are the key motives for this scheme to boost the performance of ECs based S-boxes and their effectiveness in numerous cryptographic algorithms.
1. S-boxes are typically constructed by considering ECs over prime fields. Yet, the outcomes of these studies remain uncertain. i.e., the algorithms do not invariably output an S-box to every set of specified parameters.
2. Furthermore, the prime field-based S-boxes do not encompass all the S-box possibilities.
3. In [11], the authors design an algorithm by choosing a particular EC over the Galois field
4. In [12], they considered MEC over Galois field
To overcome the shortcomings of current schemes, we have developed a new one. To summarize a lengthy piece of writing, follow these steps:
1. We implemented a simple technique rather than rigorous S-boxes algorithms with exceptional outcomes to construct
2. We utilized MEC over the Galois fields
3. Following the current approach, we used the EC points, prime numbers characteristics that rely on an EC x and y-coordinates, and an Inverse function under a predefined Galois field and PIP.
4. S-box figures can be changed by varying the MEC variable b or by amending the PIP of a degree equivalent to the Galois field
The following documents still need to be executed: Some introductory details are given in Section 2. The proposed algorithm can be found in Section 3. In Section 4, we compared our newly developed S-boxes to other S-boxes already in use. Section 4 also deals with S-boxes in the image encryption technique and the majority logic criterion (MLC). Towards the end of Section 5, there are several compelling arguments.
In this part, several fundamental and crucial notions like ECs, Galois fields, Euler’s phi function, and primitive polynomials are presented.
A mathematical concept is known as finite field, or Galois field is considered the cornerstone of all cryptography theory. The representation of Galois field is
Euler’s phi function offers the coprime numbers to an integer m, denoted as
2.3 Primitive Irreducible Polynomials (PIPs) and Galois Fields
Galois field and PIPs over the Galois field are explained below in [16]. If it isn’t explicitly stated, the base field
For each prime number
An irreducible polynomial in
A polynomial
An EC of the form
2.3.5 Addition, Subtraction, and Multiplication in
The addition and subtraction operations are identical because we are operating in characteristic 2. Adding polynomials in Galois Field [18] is relatively easy. In multiplication let
where
And
Multiplying two polynomials and finding the multiplicative inverse of a polynomial need’s modulo
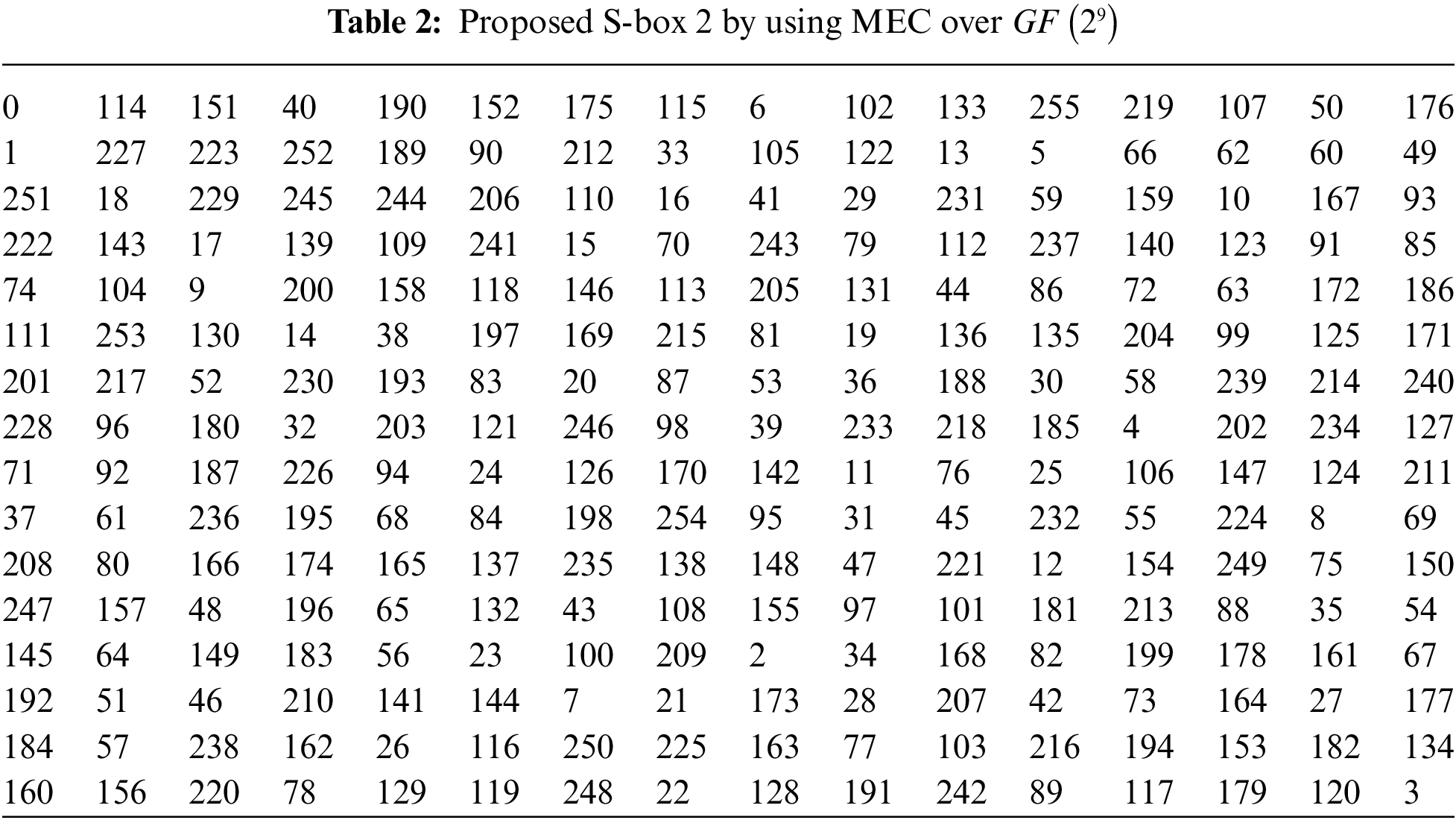
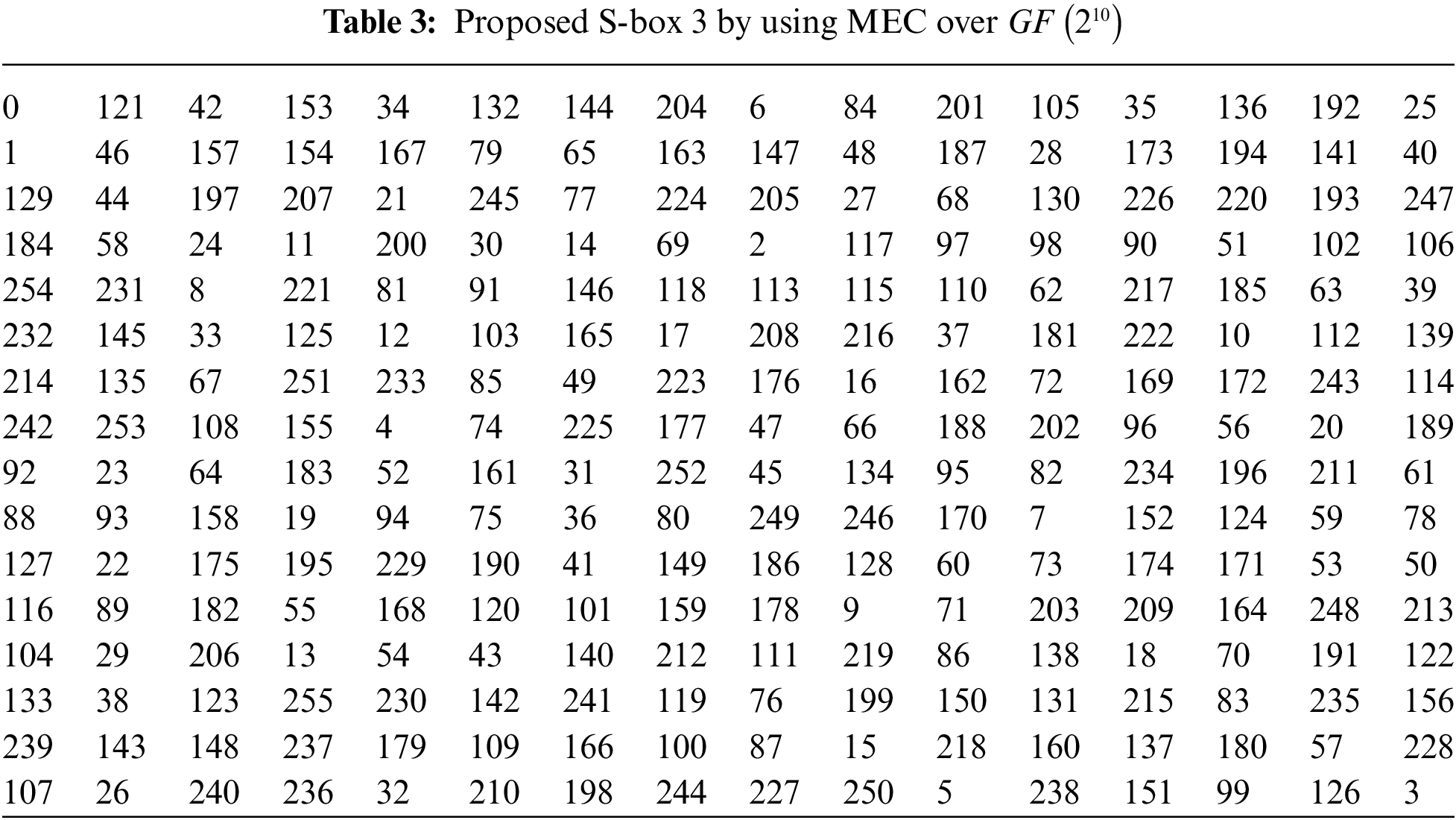
3 S-boxes Design by MEC over
Here, the proposed S-box algorithm is described using two different approaches. In the first technique, we used MEC over Galois field
3.1 Construction of S-box Using MEC over Galois Field
1. Take PIP of degree 8
over the binary field.
2. Choose MEC
where
3. Generate an EC points by utilizing that MEC over the Galois field
4. Calculate how many primes there are between the beginning and current parameter
5. Instead of choosing
6. Adjust the x-coordinates of EC points based on the resulting y-coordinates and parameter
7. Take an inverse under the Galois field
To build a different number of S-boxes, one can adjust the parameters of MEC or the PIP. As the number of PIPs over Galois field
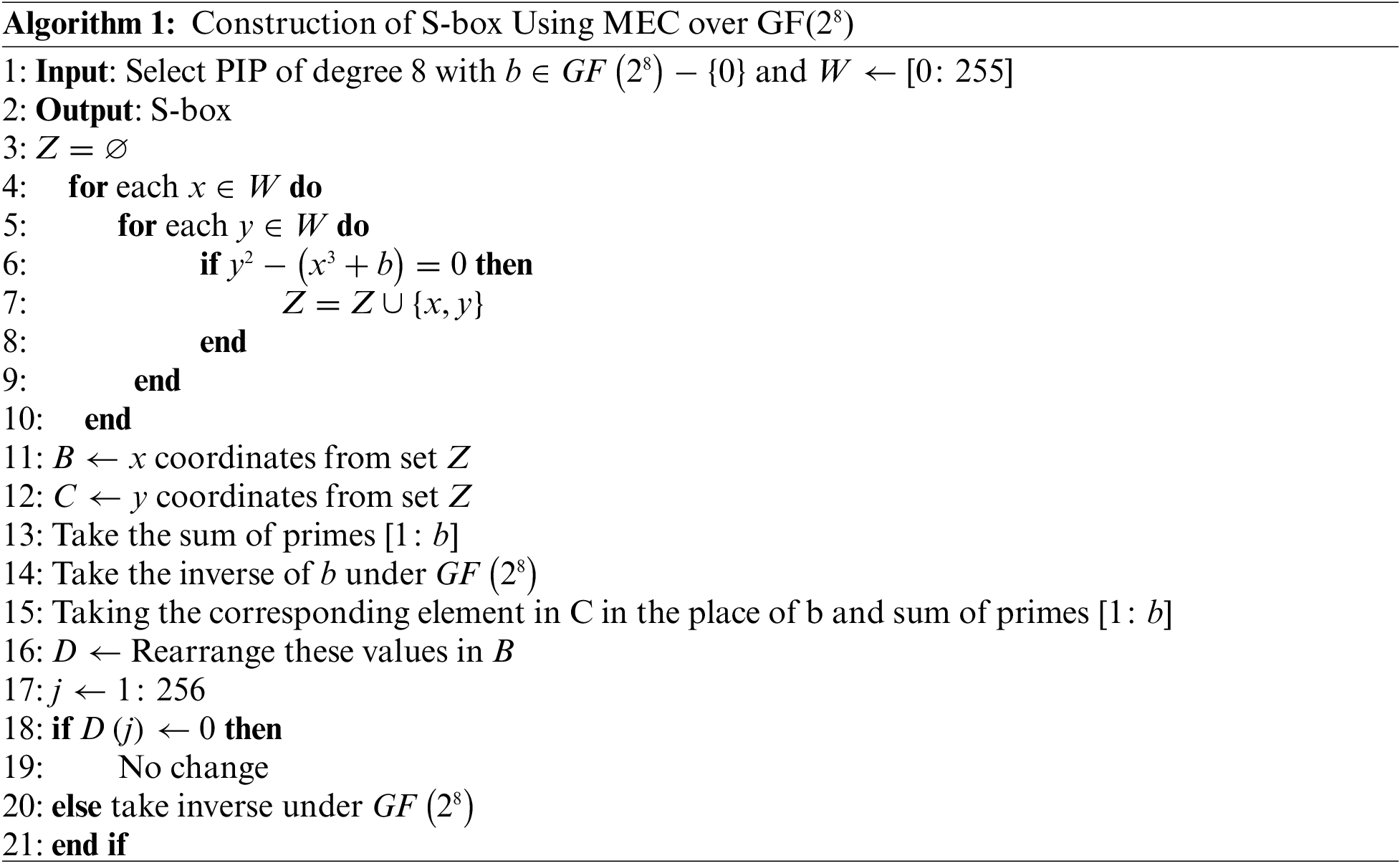
Figure 1: Proposed algorithm using MEC over
3.2 Construction of S-box Using MEC over Galois Field
The Galois fields
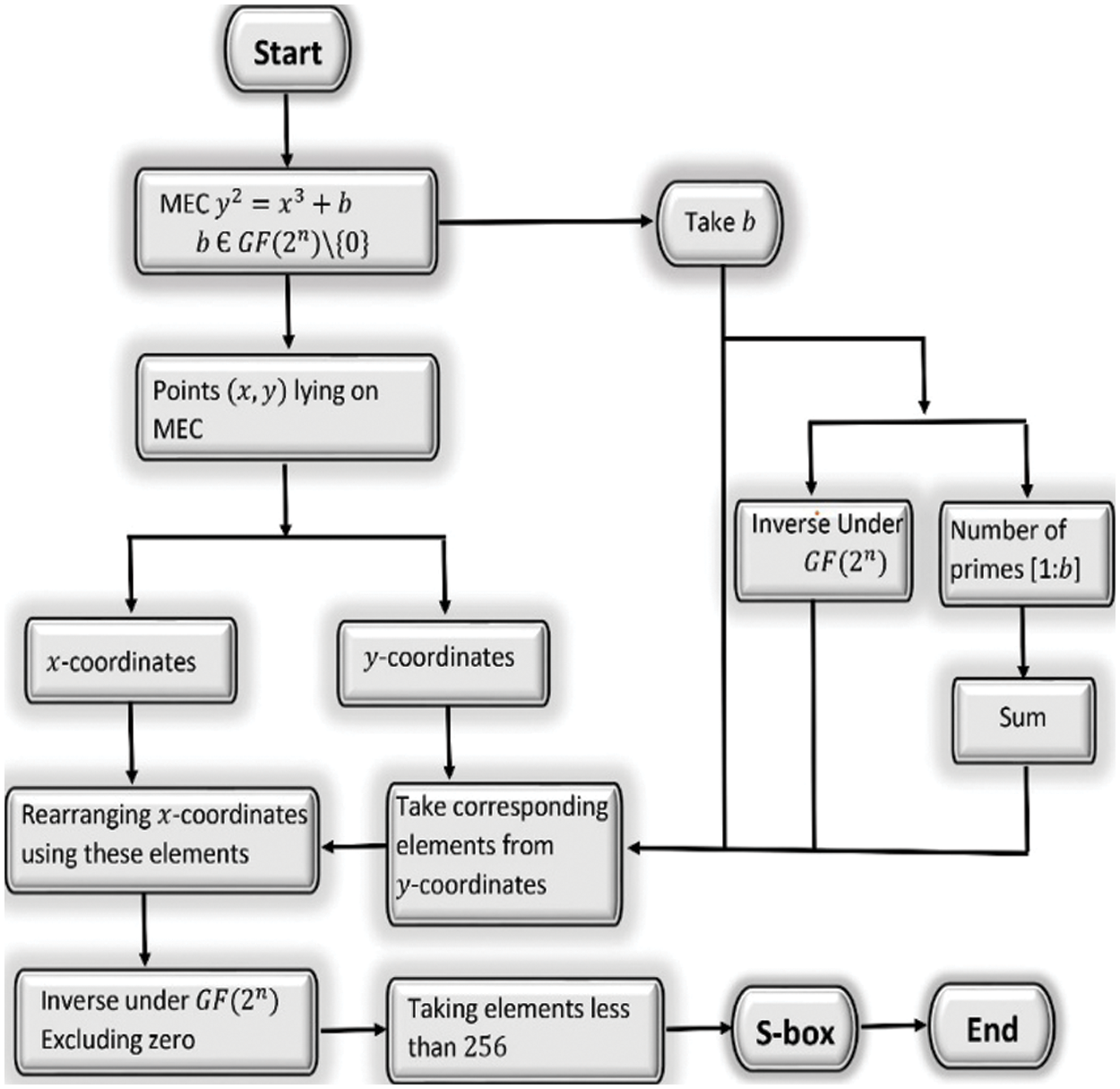
Figure 2: Proposed algorithm using MEC over
3.2.1 Construction of S-box Using MEC over Galois field
1. Choose PIP of order degree
Also, an independently one can take any other PIP of degree 9 over the binary field.
2. Consider MEC
where
3. Utilize MEC over the Galois field
4. Compute the inverse of the parameter
5. Calculate the position of b, its inverse under the Galois field
6. Managing parameter b and the resultant y-coordinates, re-adjust the x-coordinates ofcorresponding EC points.
7. Taking the inverse of each x-coordinate except zero under the Galois field
8. Finally, randomly take those elements less than 256 to construct an S-box.
The number of S-boxes can be varied by modifying the MEC parameter
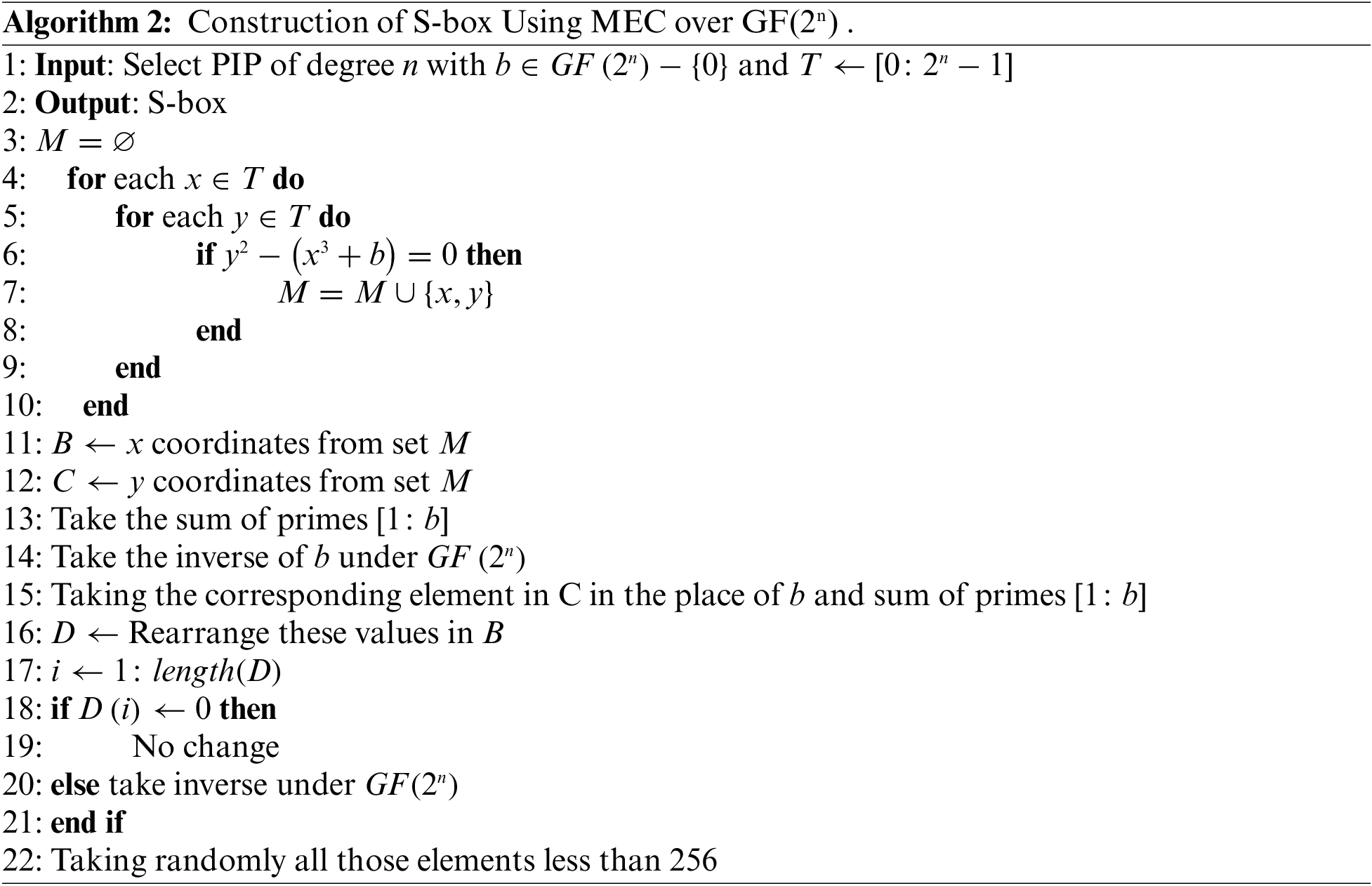
3.2.2 Construction of S-box Using MEC over Galois Field
1. Choose PIP of order degree
2. Consider MEC
where
3. Utilize MEC over the Galois field
4. Compute the inverse of the parameter
5. Calculate the position of
6. Managing parameter b and the resultant y-coordinates, re-adjust the x-coordinates ofcorresponding EC points.
7. Taking the inverse of each x-coordinate except zero under the Galois field
8. Finally, randomly take those elements less than 256 to get an S-box.
The number of S-boxes can be varied by modifying the MEC parameter
The cryptographic integrity of the proposed scheme is obtained using several conventional tests. This section will briefly review these security tests and the offered method’s results compared to other methods.
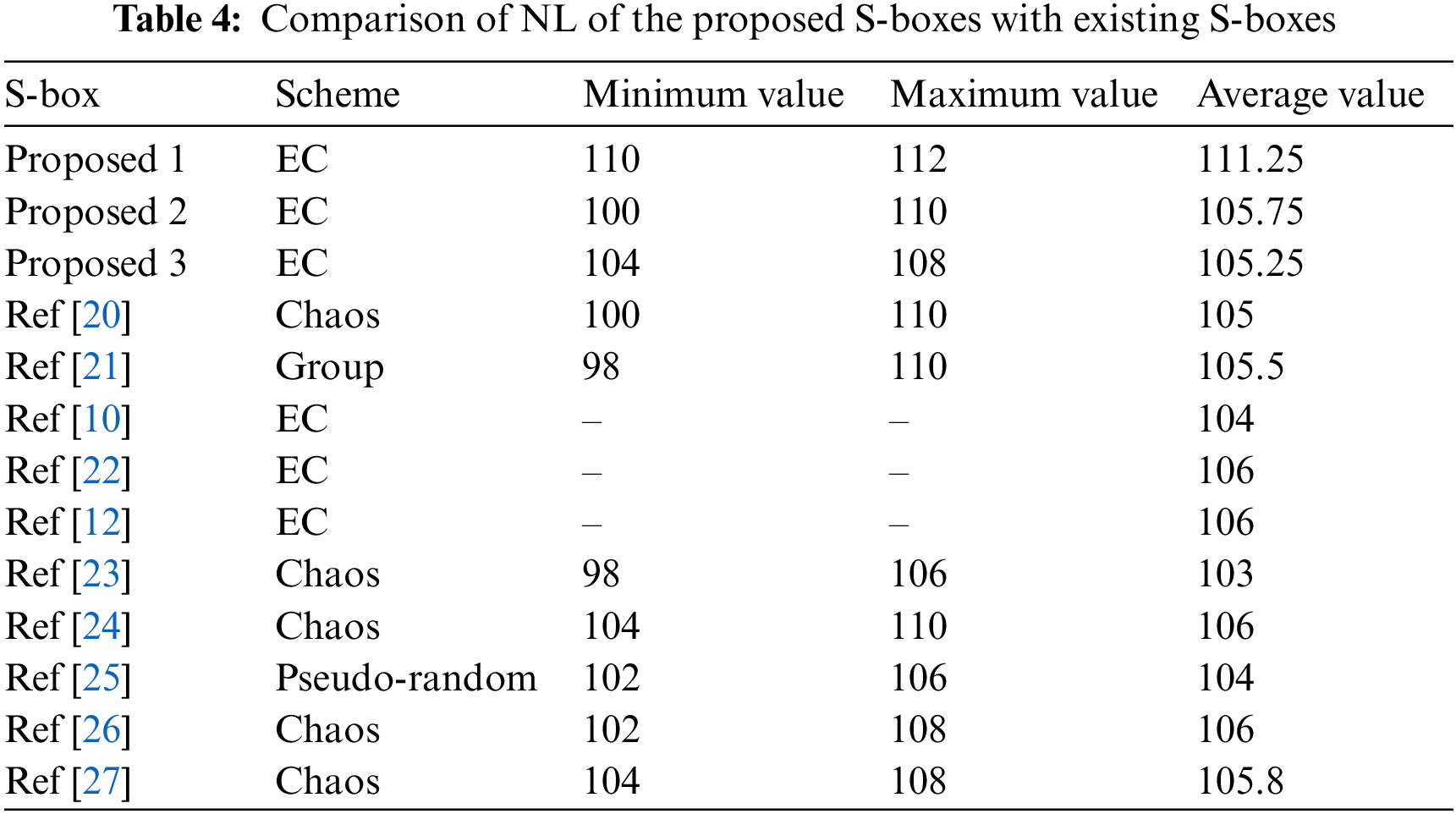
An S-box must confuse the data to a certain amount to keep the data safe from an attacker. The NL security test is a measure that computes the ability of an S-box to confuse the data, as represented in the following
where
An S-box with considerable NL can inflict a lot of data confusion. The optimal value of an
4.2 Strict Avalanche Criterion (SAC)
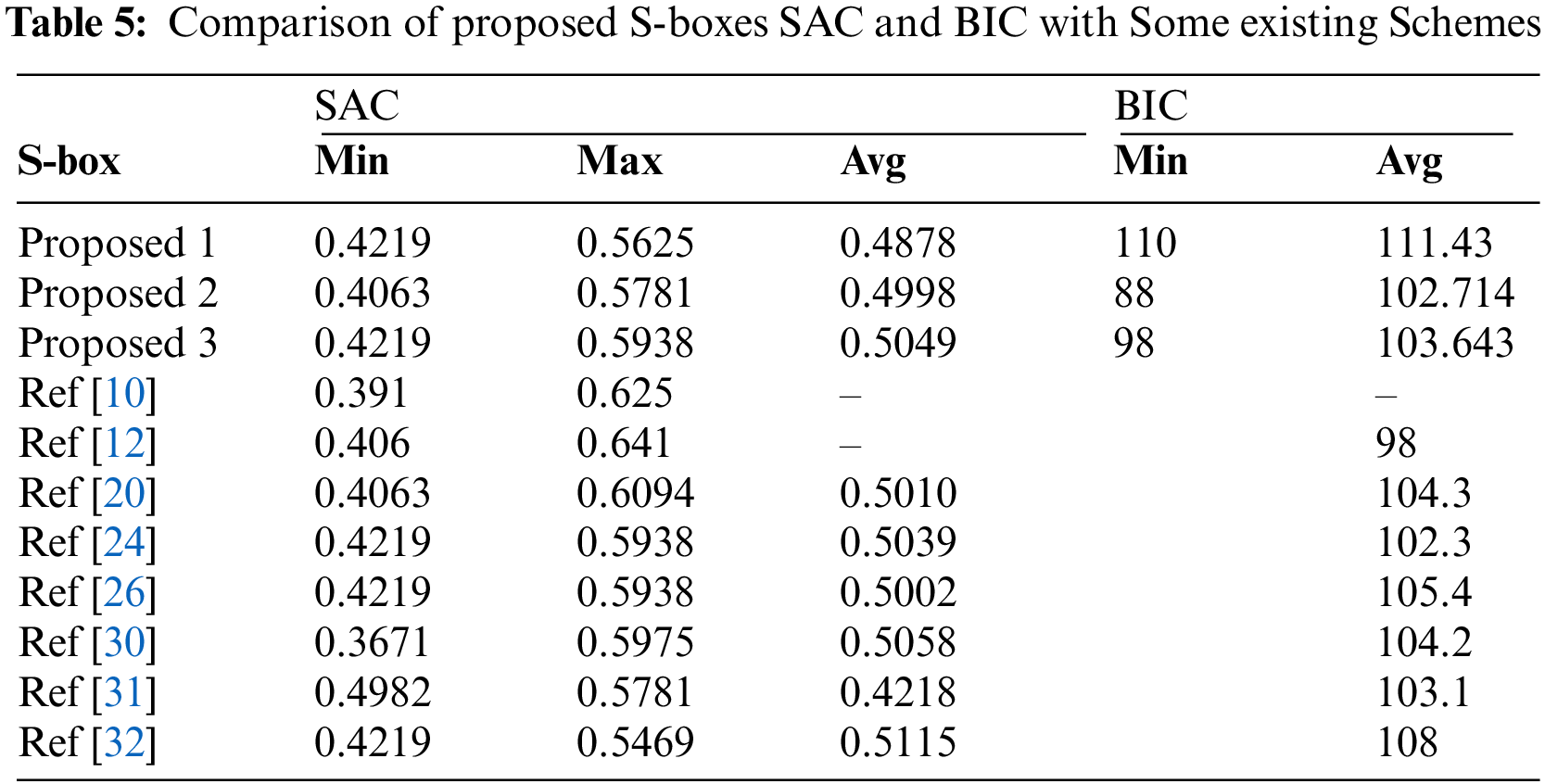
Webster and Tavares [28] were the first to introduce SAC in 1985. The SAC is built on the principles of avalanche and completion. The requirement of SAC is fulfilled when a single bit of information is updated; half of the matching output bits must change. The offered S-boxes meet the SAC criteria according to the calculated performance indexes. In Tab. 5, the proposed S-boxes SAC values are compared to the existing S-boxes, which shows that our S-boxes have an optimal SAC value.
4.3 Bit Independent Criterion (BIC)
The other vital test to study any cryptographic technique is BIC [29], which is operated to evaluate the independence of pair of output bits when the input bit is changed. Tab. 5 displays the outcomes of BIC analysis of the proposed S-boxes, and in the significance of encryption stability, the BIC of the proposed S-boxes is satisfactory. Performance Indexes of S-boxes given in Tab. 5 reveal that the rank of our proposed S-box is comparable with S-boxes from literature, and we marked that the offered S-boxes satisfied BIC close to the satisfactorily probable value.
4.4 Linear Approximation Probability (LP)
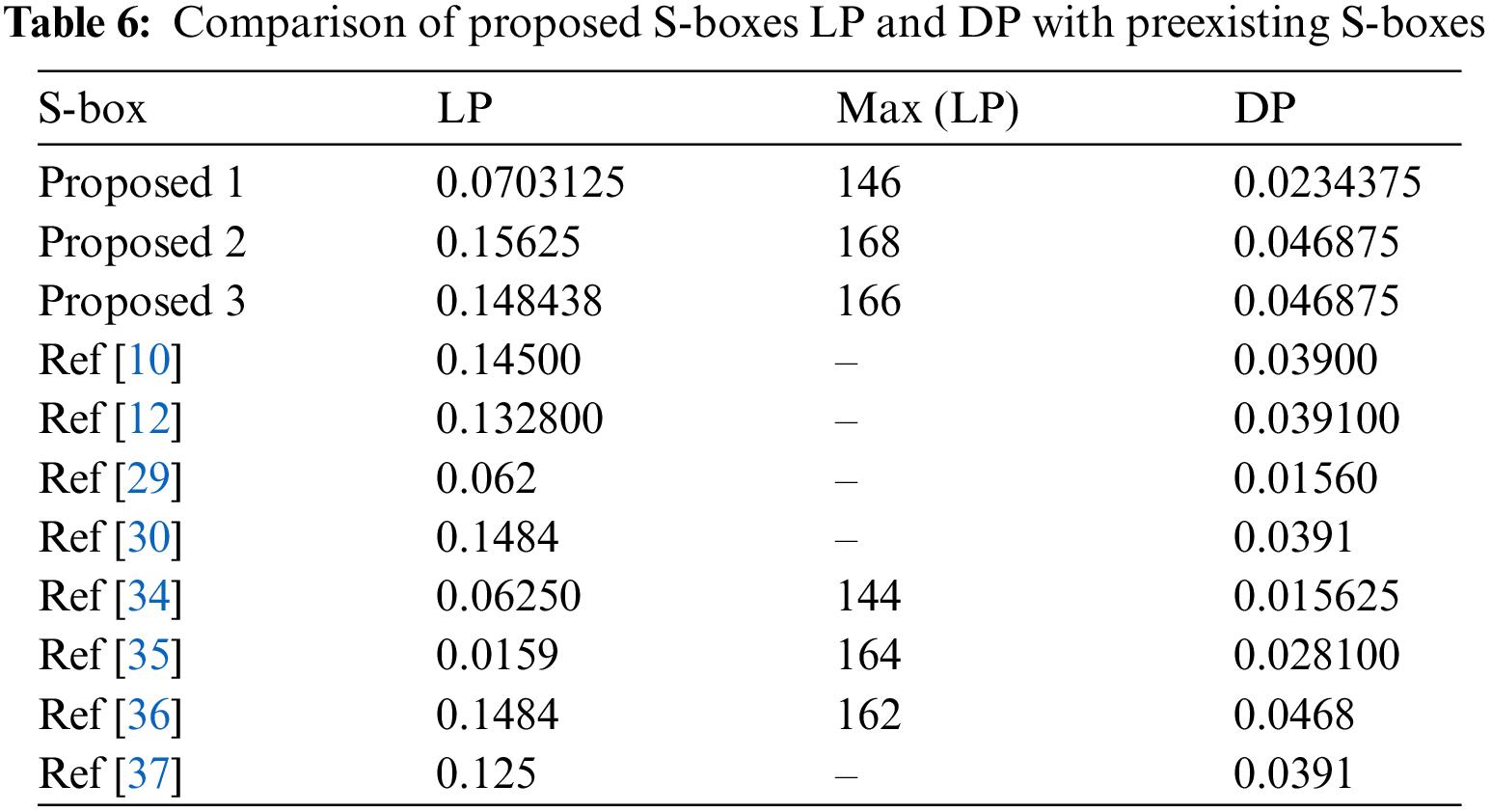
Linear approximation attacks on S-boxes can be approximated by determining the maximum number of coincidental input and output bit pairs. If an S-box has a lower LP, it is extremely resistant to linear attacks [29]. According to Tab. 6, the LP values of the new S-boxes are significantly lower than those of other S-boxes.
4.5 Differential Approximation Probability (DP)
A differential approximation probability is offered in [33] to find the probability impact of a particular disparity in the input bit on the variance of the resulting output bits. The DAP of an S-box S is shown below in the mathematical phrase:
The S-box has more potential against differential attacks if it has a lower value of DP. The experimental outcomes of DP of the newly spawned S-boxes are presented in Tab. 6, which indicates that the newly designed S-boxes have high resistance against differential attacks.
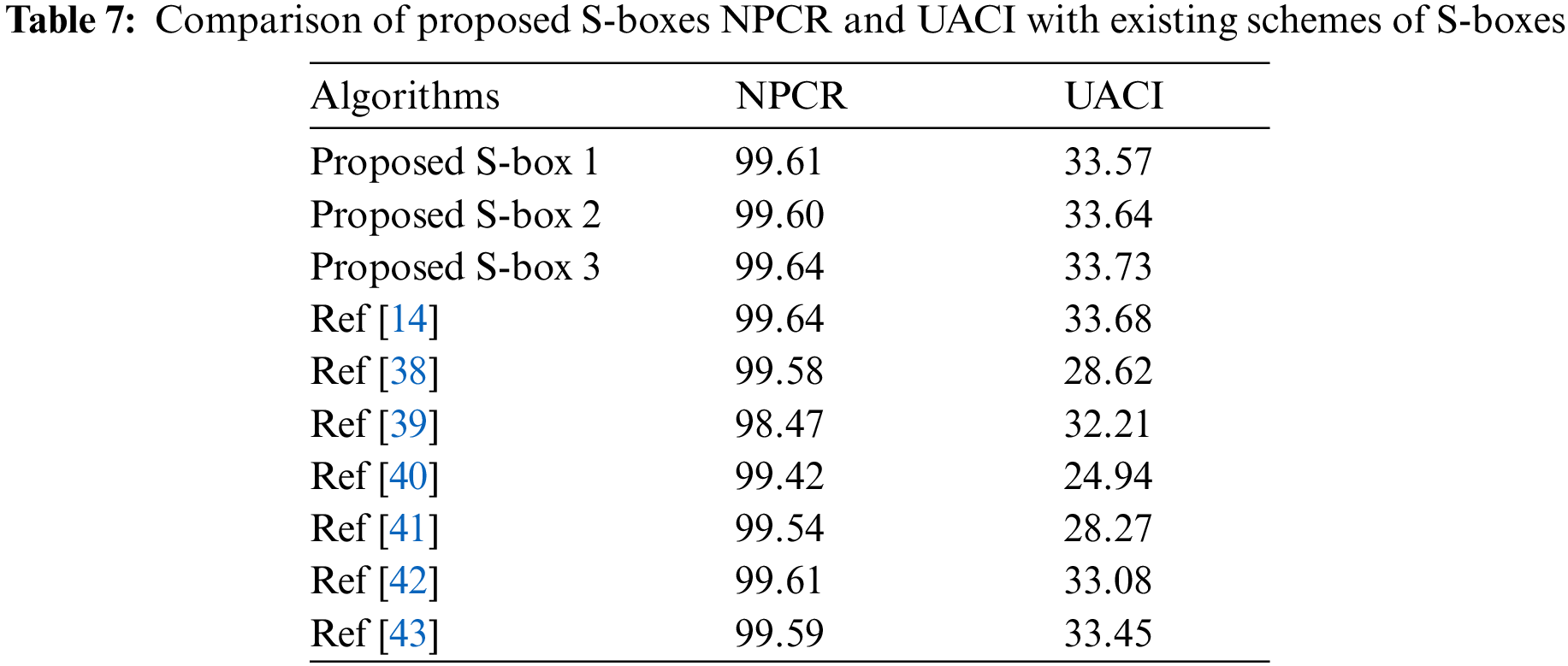
It’s common for hackers to make minor adjustments to an image before using the recommended method. You can compare the original with the substituted image. Using this method, they discovered the relationship between the original and encrypted images. A one-pixel change in the original image considerably impacts the image following substitution. This section combines two key tests, the unified average change intensity (UACI) and the several pixels changing rate (NPCR), to determine the design’s resistance to differential attacks. NPCR can be summed up as
And UACI is defined as
where
When evaluating statistical analyses, one uses the majority logic criteria (MLC) [44]. Also, an S-box is used to encrypt a test image by swapping pixel values in this standard. Even though this isn’t an encryption technology, the actual and encrypted data are analyzed statistically using this criterion. Multiple statistical analyses, including as homogeneity, correlation, contrast, energy, and entropy, can be evaluated using the MLC as a standard. This evaluation determines whether the S-box can be used to encrypt an image or not. Lena's image of
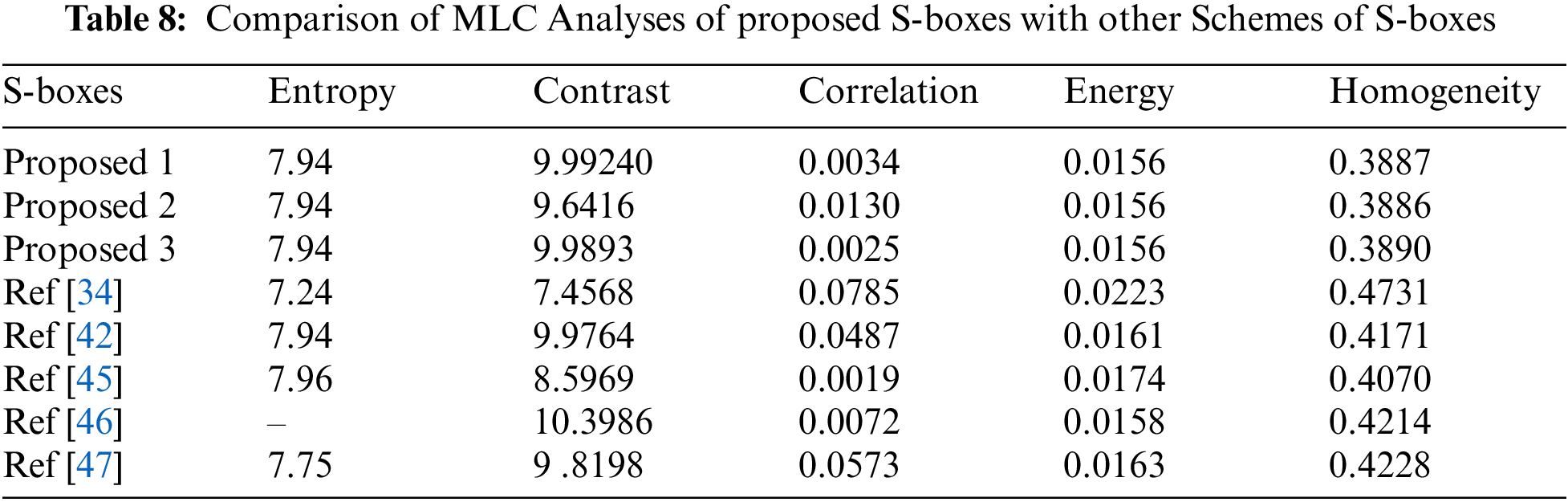
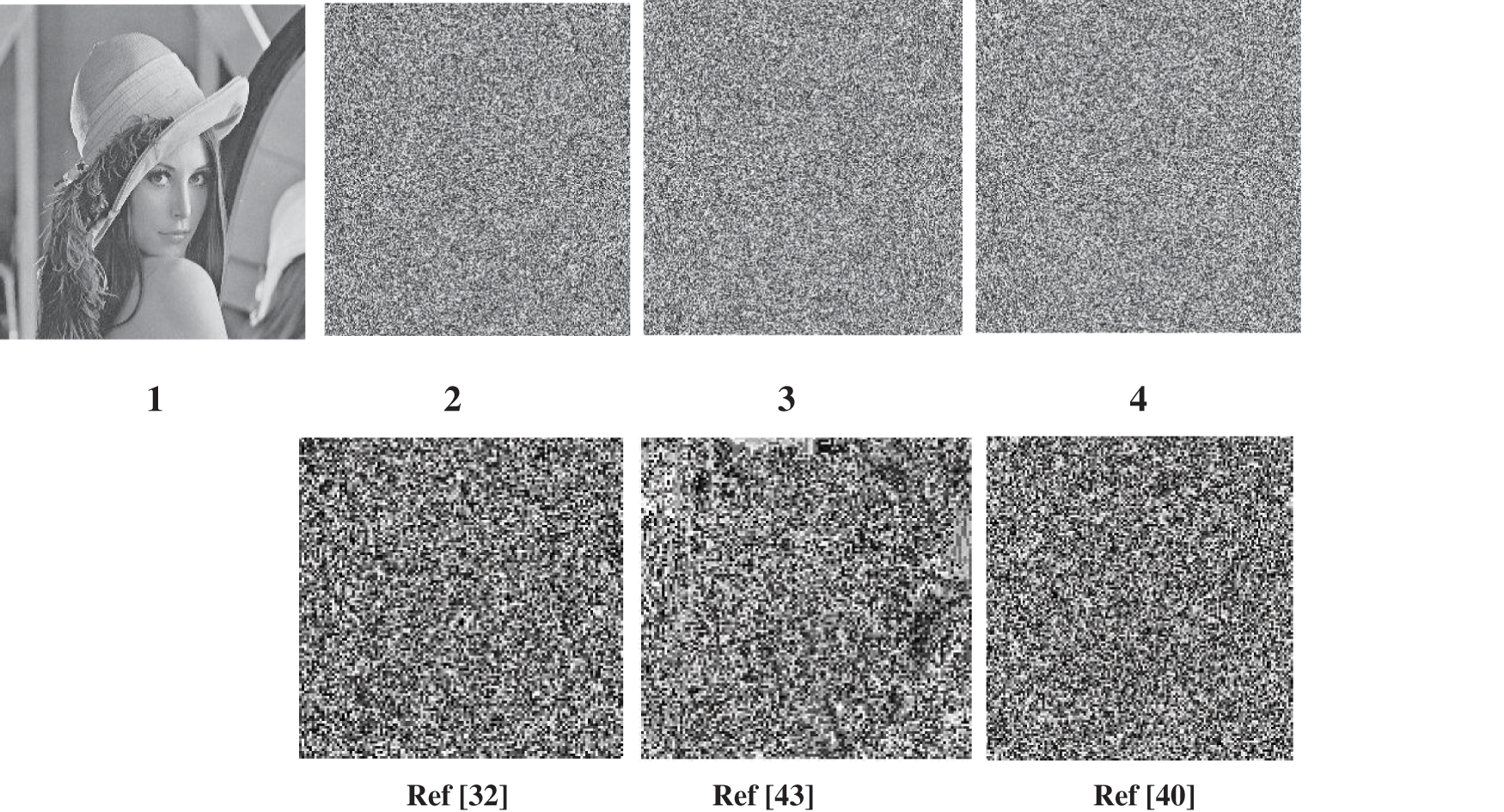
Figure 3: (1) Original Lena Image (2,3,4) Encrypted Lena image using S-box 1, S-box 2, and S-box 3
Various cryptographic tests assess the proposed algorithm to examine its potential against different cryptographic attacks. The comparison of the proposed technique with other algorithms is discussed briefly in the following point-by-point discussion.
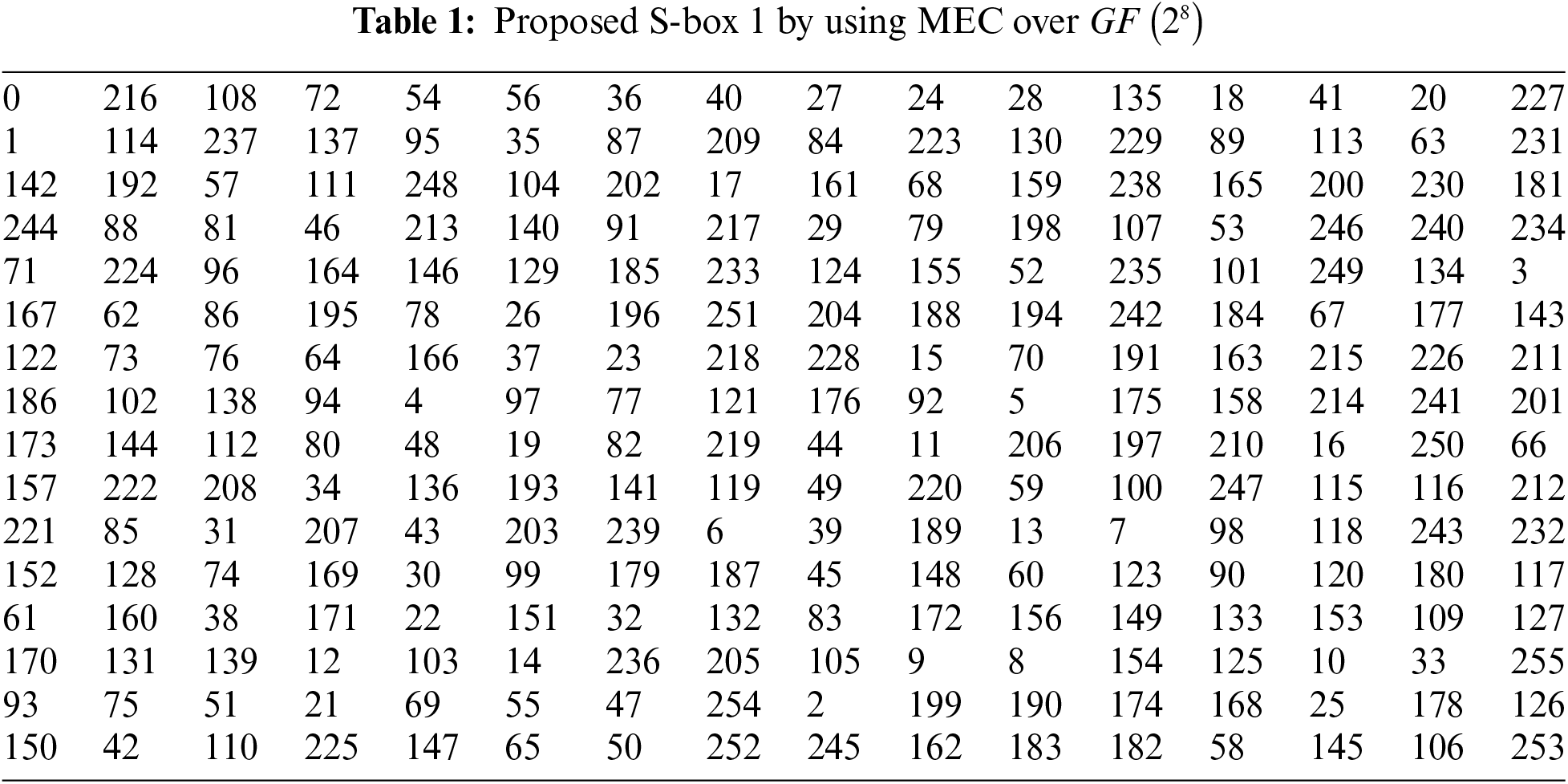
1. In Tab. 4, different algorithms are listed based on Chaos, group, Galois field, and EC. By using MEC over a 256-order Galois field, one can see that we generate 4080 S-boxes having nonlinearity between 110 to 112.The algorithms in [10,12,22] were constructed using EC over the prime field but did not achieve outstanding results compared to our proposed technique.
2. The proposed S-boxes BIC and SAC values are more satisfactory than the algorithms in [10,12,30–32] mentioned in Tab. 5. Furthermore, our BIC and SAC values are optimal, indicating that the offered S-boxes can cause enough diffusion in the data.
3. The proposed S-boxes LP values are also acceptable compared to the different algorithms in Tab. 6. Similarly, the lower value of the DP of the proposed scheme shows that our method is more invulnerable to various attacks.
4. The NPCR and UACI values of the proposed S-boxes are comparatively better than the cited algorithms in Tab. 7. Furthermore, the MLC analysis in Tab. 8 shows that the offered algorithm is more significant for image encryption.
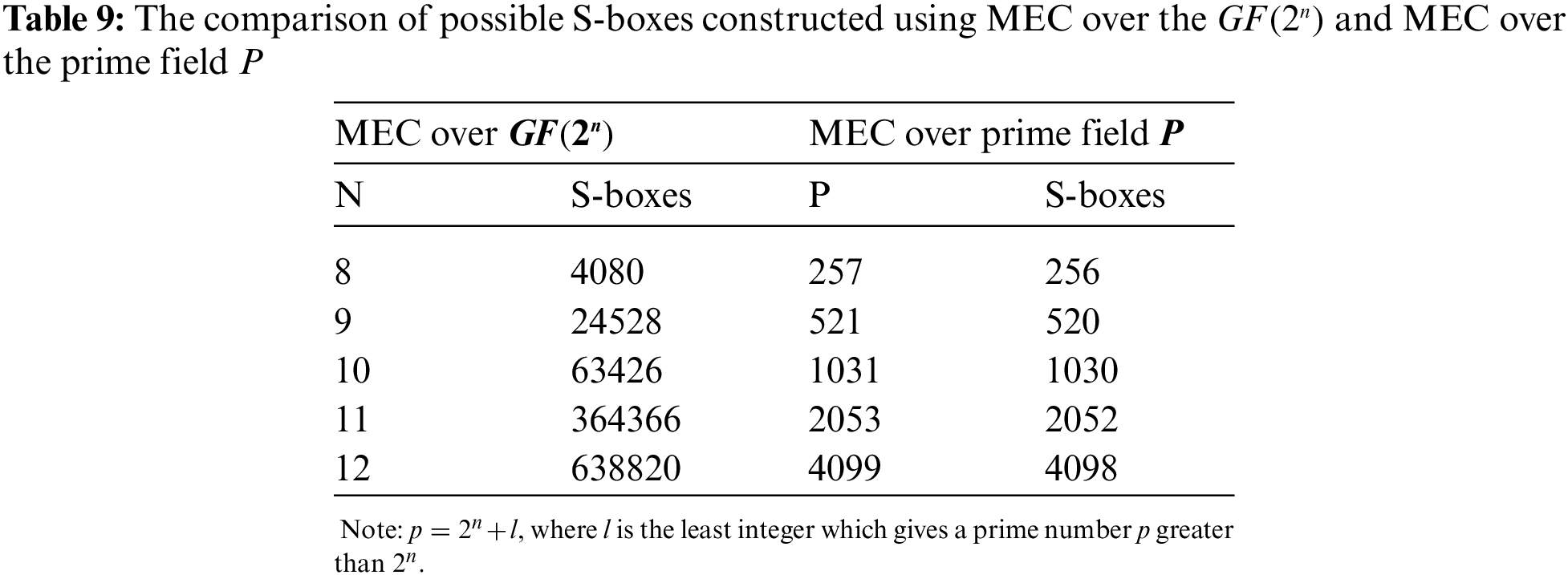
5. The number of S-boxes creation ability of the proposed algorithm is very high compared to other EC-based algorithms noted in Tab. 9, proclaiming that the presented scheme is novel and more significant.
The above analysis shows that the proposed scheme has good resistance against various cryptographic attacks compared to existing algorithms. The results of the MLC tests reveal that the proposed algorithm has good image encryption features.
In this article, we considered MEC over the binary extension field
Funding Statement: The authors extend their gratitude to the Deanship of Scientific Research at King Khalid University for funding this work through the research groups program under grant number R. G. P. 2/109/43.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. X. R. Zhang, W. F. Zhang, W. Sun, X. M. Sun and S. K. Jha, “A robust 3-D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
2. X. R. Zhang, X. Sun, X. M. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
3. C. E. Shannon, “Communication theory of secrecy systems,” The Bell System Technical Journal, vol. 28, no. 4, pp. 656–715, 1949. [Google Scholar]
4. L. Cui and Y. Cao, “A new S-box structure named affine-power-affine,” International Journal of Innovative Computing, Information and Control, vol. 3, no. 3, pp. 751–759, 2007. [Google Scholar]
5. I. Hussain, T. Shah and H. Mahmood, “A new algorithm to construct secure keys for AES,” International Journal of Contemporary Mathematical Sciences, vol. 5, no. 26, pp. 1263–1270, 2010. [Google Scholar]
6. M. T. Tran, D. K. Bui and A. D. Duong, “Gray S-box for advanced encryption standard,” Int. Conf. on Computational Intelligence and Security, IEEE, vol. 1, pp. 253–258, 2008. [Google Scholar]
7. F. Özkaynak and A. B. Özer, “A method for designing strong S-Boxes based on chaotic Lorenz system,” Physics Letters A, vol. 374, no. 36, pp. 3733–3738, 2010. [Google Scholar]
8. Y. Wang, K. W. Wong, C. Li and Y. Li, “A novel method to design S-box based on chaotic map and genetic algorithm,” Physics Letters A, vol. 376, no. 6, pp. 827–833, 2012. [Google Scholar]
9. J. H. Cheon, S. Chee and C. Park, “S-boxes with controllable nonlinearity,” in Int. Conf. on the Theory and Applications of Cryptographic Techniques, Berlin, Heidelberg, Springer, pp. 286–294, 1999. [Google Scholar]
10. U. Hayat, N. A. Azam and M. Asif, “A method of generating 8 × 8 substitution boxes based on elliptic curves,” Wireless Personal Communications, vol. 101, no. 1, pp. 439–451, 2018. [Google Scholar]
11. U. Hayat and N. A. Azam, “A novel image encryption scheme based on an elliptic curve,” Signal Processing, vol. 155, no. 2–3, pp. 391–402, 2019. [Google Scholar]
12. N. A. Azam, U. Hayat and I. Ullah, “Efficient construction of a substitution box based on a Mordell elliptic curve over a finite field,” Frontiers of Information Technology, Electronic Engineering, vol. 20, no. 10, pp. 1378–1389, 2019. [Google Scholar]
13. S. Farwa, A. Sohail and N. Muhammad, “A novel application of elliptic curves in the dynamical components of block ciphers,” Wireless Personal Communications, vol. 115, no. 2, pp. 1309–1316, 2020. [Google Scholar]
14. H. U. Rehman, T. Shah, A. Aljaedi, M. M. Hazzazi and A. R. Alharbi, “Design of nonlinear components over a mordell elliptic curve on galois fields,” Computers, Materials & Continua, vol. 71, no. 1, pp. 1313–1329, 2022. [Google Scholar]
15. E. W. Weisstein, “Totient function,” 2003. [Online]. Available: https://Mathworld.Wolfram.Com/. [Google Scholar]
16. S. Maitra, K. C. Gupta and A. Venkateswarlu, “Results on multiples of primitive polynomials and their products over GF (2),” Theoretical Computer Science, vol. 341, no. 1–3, pp. 311–343, 2005. [Google Scholar]
17. L. C. Washington, “Elliptic curves,” in Number Theory and Cryptography, CRC press, 2008. [Google Scholar]
18. C. J. Benvenuto, “Galois field in cryptography,” University of Washington, vol. 1, no. 1, pp. 1–11, 2012. [Google Scholar]
19. W. Meier and O. Staffelbach, “Nonlinearity criteria for cryptographic functions,” in Workshop on the Theory and Application of Cryptographic Techniques, Berlin, Heidelberg, Springer, pp. 549–562, 1989. [Google Scholar]
20. A. Belazi and A. A. Abd El-Latif, “A simple yet efficient S-box method based on chaotic sine map,” Optik, vol. 130, no. August 3, pp. 1438–1444, 2017. [Google Scholar]
21. M. Khan and T. Shah, “An efficient construction of substitution box with fractional chaotic system,” Signal, Image and Video Processing, vol. 9, no. 6, pp. 1335–1338, 2015. [Google Scholar]
22. N. A. Azam, U. Hayat and I. Ullah, “An injective S-box design scheme over an ordered isomorphic elliptic curve and its characterization,” Security and Communication Networks, vol. 18, no. 2, pp. 9, 2018. [Google Scholar]
23. M. A. Gondal, A. Raheem and I. Hussain, “A scheme for obtaining secure S-boxes based on chaotic Baker’s map,” 3D Research, vol. 5, no. 3, pp. 17, 2014. [Google Scholar]
24. U. Cavusoglu, A. Zengin, I. Pehlivan and S. Kacar, “A novel approach for strong S-box generation algorithm design based on chaotic scaled Zhongtang system,” Nonlinear Dynamics, vol. 87, no. 2, pp. 1081–1094, 2017. [Google Scholar]
25. K. Kazlauskas, G. Vaicekauskas and R. Smaliukas, “An algorithm for key-dependent S-box generation in block cipher system,” Informatica, vol. 26, no. 1, pp. 5165, 2015. [Google Scholar]
26. F. U. Islam and G. Liu, “Designing S-box based on 4D-4wing hyperchaotic system,” 3D Research, vol. 8, no. 1, pp. 9, 2017. [Google Scholar]
27. G. Liu, W. Yang, W. Liu and Y. Dai, “Designing S-boxes based on 3-D four-wing autonomous chaotic system,” Nonlinear Dynamics, vol. 82, no. 4, pp. 1867–1877, 2015. [Google Scholar]
28. A. F. Webster and S. E. Tavares, “On the design of S-boxes,” in Conf. on the Theory and Application of Cryptographic Techniques, Berlin, Heidelberg, Springer, pp. 523–534, 1985. [Google Scholar]
29. C. Adams and S. Tavares, “The structured design of cryptographically good S-boxes,” Journal of Cryptology, vol. 3, no. 1, pp. 27–41, 1990. [Google Scholar]
30. G. Jakimoski and L. Kocarev, “Chaos and cryptography: Block encryption ciphers based on chaotic maps,” IEEE Transactions on Circuits and Systems I: Fundamental Theory and Applications, vol. 48, no. 2, pp. 163–169, 2001. [Google Scholar]
31. F. Özkaynak, V. Çelik and A. B. Özer, “A new S-box construction method based on the fractional-order chaotic Chen system,” Signal, Image and Video Processing, vol. 4, no. 11, pp. 659–664, 2016. [Google Scholar]
32. A. Belazi, A. A. Abd El-Latif, A. V. Diaconu, R. Rhouma and S. Belghith, “Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms,” Optics and Lasers in Engineering, vol. 88, no. 11–12, pp. pp 37–50, 2017. [Google Scholar]
33. E. Biham and A. Shamir, “Differential cryptanalysis of DES-like cryptosystems,” Journal of Cryptology, vol. 4, no. 1, pp. 3–72, 1991. [Google Scholar]
34. S. Farwa, T. Shah and L. Idrees, “A highly nonlinear S-box based on a fractional linear transformation,” Springer Plus, vol. 5, no. 1, pp. 1–12, 2016. [Google Scholar]
35. F. Özkaynak, “Construction of robust substitution boxes based on chaotic systems,” Neural Computing and Applications, vol. 31, no. 8, pp. 3317–3326, 2019. [Google Scholar]
36. A. Razaq, A. Yousaf, U. Shuaib, N. Siddiqui, A. Ullah et al., “A novel construction of substitution box involving coset diagram and a bijective map,” Security and Communication Networks, vol. 2017, no. 48, pp. 1–16, 2017. [Google Scholar]
37. I. Hussain, T. Shah, M. A. Gondal, W. A. Khan and H. Mahmood, “A group theoretic approach to construct cryptographically strong substitution boxes,” Neural Computing and Applications, vol. 23, no. 1, pp. 97–104, 2013. [Google Scholar]
38. K. Loukhaoukha, J. Y. Chouinard and A. Berdai, “A secure image encryption algorithm based on Rubik’s cube principle,” Journal of Electrical and Computer Engineering, vol. 12, no. 7, pp. 7–13, 2012. [Google Scholar]
39. G. A. Sathishkumar and D. N. Sriraam, “Image encryption based on diffusion and multiple chaotic maps,” 2011. [Online]. Available: https://arxiv.org/abs/1103.3792. [Google Scholar]
40. C. K. Huang and H. H. Nien, “Multi chaotic systems-based pixel shuffle for image encryption,” Optics Communications, vol. 282, no. 11, pp. 2123–2127, 2009. [Google Scholar]
41. C. K. Huang, C. W. Liao, S. L. Hsu and Y. C. Jeng, “Implementation of gray image encryption with pixel shuffling and gray-level encryption by single chaotic system,” Telecommunication Systems, vol. 52, no. 2, pp. 563–571, 2013. [Google Scholar]
42. S. Hussain, S. S. Jamal, T. Shah and I. Hussain, “A power associative loop structure for the construction of non-linear components of block cipher,” IEEE Access, vol. 8, pp. 123492–123506, 2020. [Google Scholar]
43. X. Wang, X. Zhu and Y. Zhang, “An image encryption algorithm based on Josephus traversing and mixed chaotic map,” IEEE Access, vol. 6, no. 17, pp. 23733–23746, 2018. [Google Scholar]
44. A. K. Farhan, N. M. Al-Saidi, A. T. Maolood, F. Nazarimehr and I. Hussain, “Entropy analysis and image encryption application based on a new chaotic system crossing a cylinder,” Entropy, vol. 21, no. 10, pp. 958, 2019. [Google Scholar]
45. Y. Naseer, T. Shah, S. Hussain and A. Ali, “Steps towards redesigning cryptosystems by a non-associative algebra of IP-loops,” Wireless Personal Communications, vol. 108, no. 3, pp. 1379–1392, 2019. [Google Scholar]
46. F. Ali Khan, J. Ahmed, J. S. Khan, and J. Ahmad “A new technique for designing 8 × 8 substitution box for image encryption applications,” in 2017 9th Computer Science and Electronic Engineering (CEEC), IEEE, pp. 7–12, 2017. [Google Scholar]
47. Y. Naseer, T. Shah, D. Shah and S. Hussain, “A novel algorithm of constructing highly nonlinear Sp-boxes,” Cryptography, vol. 3, no. 1, pp. 6, 2019. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |