| Computers, Materials & Continua DOI:10.32604/cmc.2022.029538 |  |
| Article |
Enhancing Blockchain Security Using Ripple Consensus Algorithm
1School of Computing Science and Engineering, VIT Bhopal University, Bhopal, 466114, India
2Department of Computer Science, Imam Abdulrahman Bin Faisal University, Dammam, 34212, Saudi Arabia
*Corresponding Author: Abeer Abdullah Alsadhan. Email: abeerabdullah2@outlook.com
Received: 06 March 2022; Accepted: 21 April 2022
Abstract: In the development of technology in various fields like big data analysis, data mining, big data, cloud computing, and blockchain technology, security become more constrained. Blockchain is used in providing security by encrypting the sharing of information. Blockchain is applied in the peer-to-peer (P2P) network and it has a decentralized ledger. Providing security against unauthorized breaches in the distributed network is required. To detect unauthorized breaches, there are numerous techniques were developed and those techniques are inefficient and have poor data integrity. Hence, a novel technique needs to be implemented to tackle the new breaches in the distributed network. This paper, proposed a hybrid technique of two fish with a ripple consensus algorithm (TF-RC). To improve the detection time and security, this paper uses efficient transmission of data in the distributed network. The experimental analysis of TF-RC by using the metric measures of performance in terms of latency, throughput, energy efficiency and it produced better performance.
Keywords: Blockchain; security; ripple; breaches; twofish; network
In today’s world, everything is connected with IoT based on the environment. For transmission of data or sharing of information through the network, security plays an important role. Cloud storage offers unlimited storage for computing resources and information by using multiple users [1]. Blockchain technology is one of the models for providing a high level of security based on the concept of cryptographic mechanisms in the decentralized approach which replaces various existing implementations of security. In blockchain technology, the chain of blocks in each block contains information or data which are available in a distributed ledger. It is a software protocol and it could not be implemented without the internet which comprises software applications, databases, and interconnecting various computers [2].
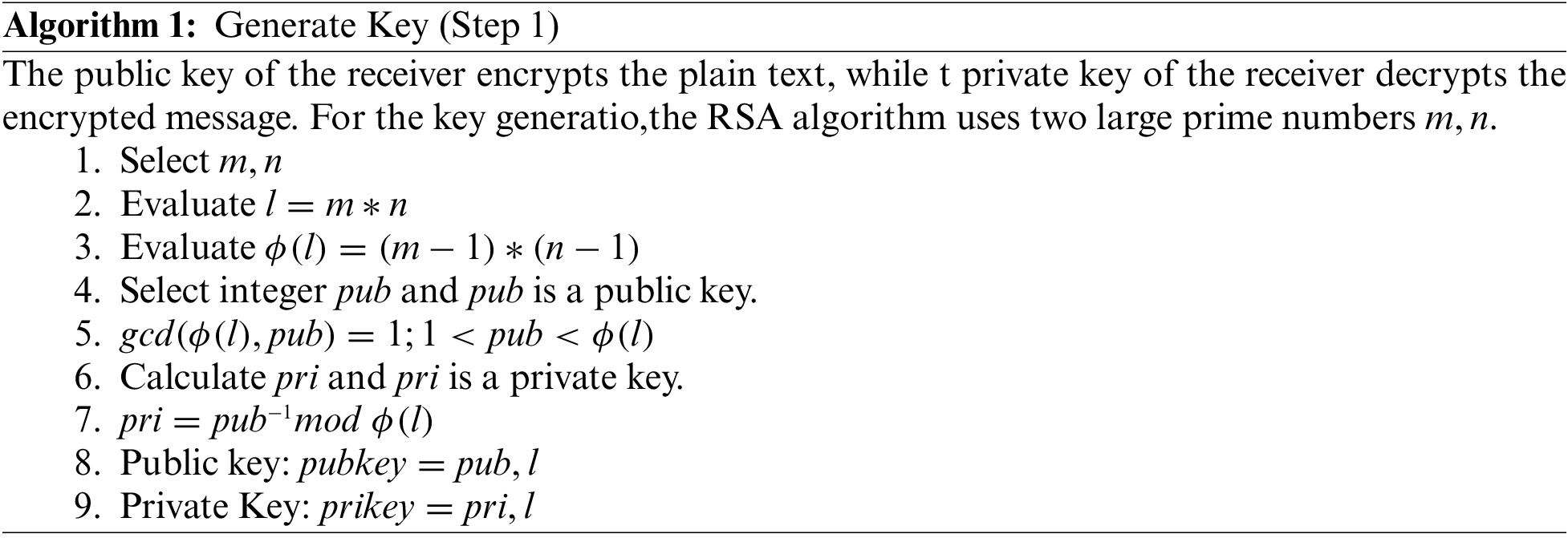
Rivest-Shamir-Adleman (RSA) is one of the cryptographic keys, and it is used to store information as records. The cryptographic technique for encrypting the data using a private key which is different from a decryption key? The concept of Rivest Shamir Adleman (RSA) is asymmetry centric based on the positive product of integer values as a “factoring issue” [3]. In the decentralized-based network, Blockchain allows registering a sequence of transformations potentially despite doing a malicious activity in the minority of peer-to-peer (P2P). Blockchain activities revolutionize different fields like currency-based systems, and payment in the financial sectors which are automatically employed contracts in IoT of massive sharing of data [4–8].
Many research works have been done and applying these techniques and will be insecure and inefficient in the detection of breaches. Therefore, to improve the security and detection of malicious or breaches activities this paper proposed Two fish-based Ripple Consensus algorithms (TF-RC). This TF-RC uses RSA for the authentic registration process and in blockchain technology uses a ripple consensus algorithm. The main contribution of this work is:
1. A novelty and trusted cloud-based system with the implementation of a blockchain using the RSA mechanism will improve the sharing of data overhead by maximizing energy efficiency.
2. Enhancing the security in blockchain technology using a ripple consensus algorithm.
The paper has been organized as follows: Section 2 describes the review of the literature, Section 3 introduces enhancing the blockchain security using the ripple consensus algorithm, Section 4 discusses the experimented results and Section 5 concludes the paper with future directions.
In the modern world, sharing information through the network is essential in preserving the information secure manner. Blockchain is a type of distributed ledger method [9]. Blockchain technology is implemented in the field of bitcoin, cryptocurrency, Monroe, Litecoin, and Zcash [10–12]. The rapid development of the blockchain method can efficiently in providing the reliability, authenticity, and security of information. It is also used in the protection of personal data, preserving data, and allocation of data [13–15]. The smallest unit of blockchain is a block. Each block contains a header, data, and body of blocks which is mainly used for the transmission of data. The transformation of data is done by using a hash function, and it provides security in the blockchain [16].
This paper [17] proposed the contribution of the infrastructure of cloud storage like private clouds and public clouds. Accessing information or data is controlled by registered users in a secure and it is employed in the cloud service provider. The standard encryption scheme used the term frequency-inverse document frequency (TF-IDF) technique which is used in the link of semantic documents and keywords. To ensure security and keep the privacy-preserving by using the encryption scheme of Latent Dirichlet Allocation (LDA). In the LDA, the document is created based on the concept-wise and the relevant matrix with vector query. To improve the efficiency of this implementation of the LDA method by using the “Greedy Depth First Search” algorithm [18].
The paper [19] proposed the transformation of data or information in the P2P network model. In blockchain technology proof of production and stack proof are used in the blockchain credibility. The blockchain concept focused on private provable data possession (PDP) recognizes the security of the customer in the terms of anonymity. For boosting efficiency, it is necessary to discard the certificate authentication technique. In the PDP concept, the blockchain-based analysis uses the private key which provides the information more secure. The various consensus algorithms in blockchain technology are Ripple, decentralized autonomous organization (DAC), proof of stack (PoS), proof of activity (PoA), and proof of work (PoW) [20,21].
Tab. 1 shows the literature survey of block chain.

Storing and sharing data or information using blockchain technology requires security in breaches and reliability of data transactions in the distributed network. The system model of storage of data based on blockchain with the cloud is shown in Fig. 1.
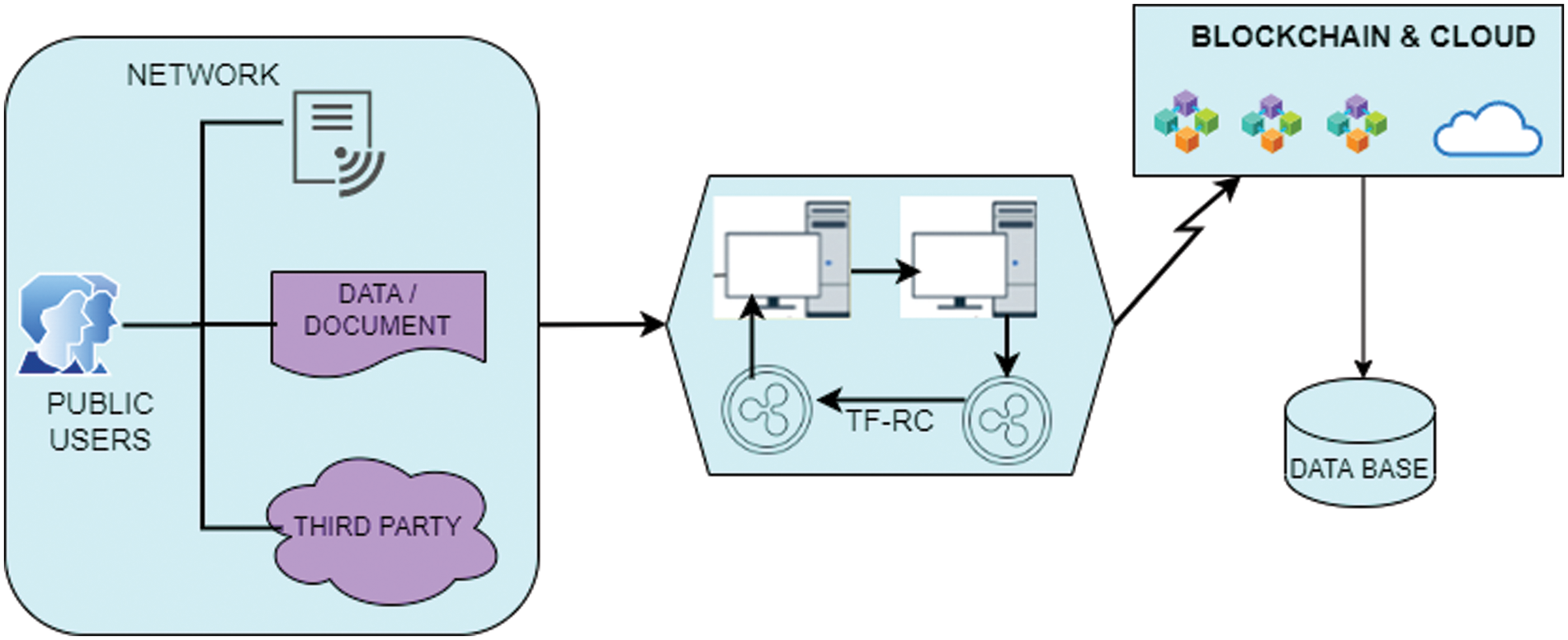
Figure 1: Blockchain-based cloud storage
Fig. 1 describes the blockchain architecture for storing information in high-level security. This proposed work (TF-RC) contains two modules.
Module 1: Registration for user and Verification
Module 2: Data Storage securely using TF-RC
Module 3: Updating Authentic information
Module 4: Detection of Breaches in the distributed network
3.1 Registration Form User and Verification
In this module, the user will do the registration procedure with a certificate authority. Every successfully registered user receives the key for encrypted data. By using the credentials registered users can enter into the system. The credential information contains the id, password, and random key number for the verification. If the verification details are valid then the authentication is granted to the user, otherwise, it will be rejected. The RSA algorithm is implemented for verification. Fig. 2 shows the workflow of the RSA algorithm.
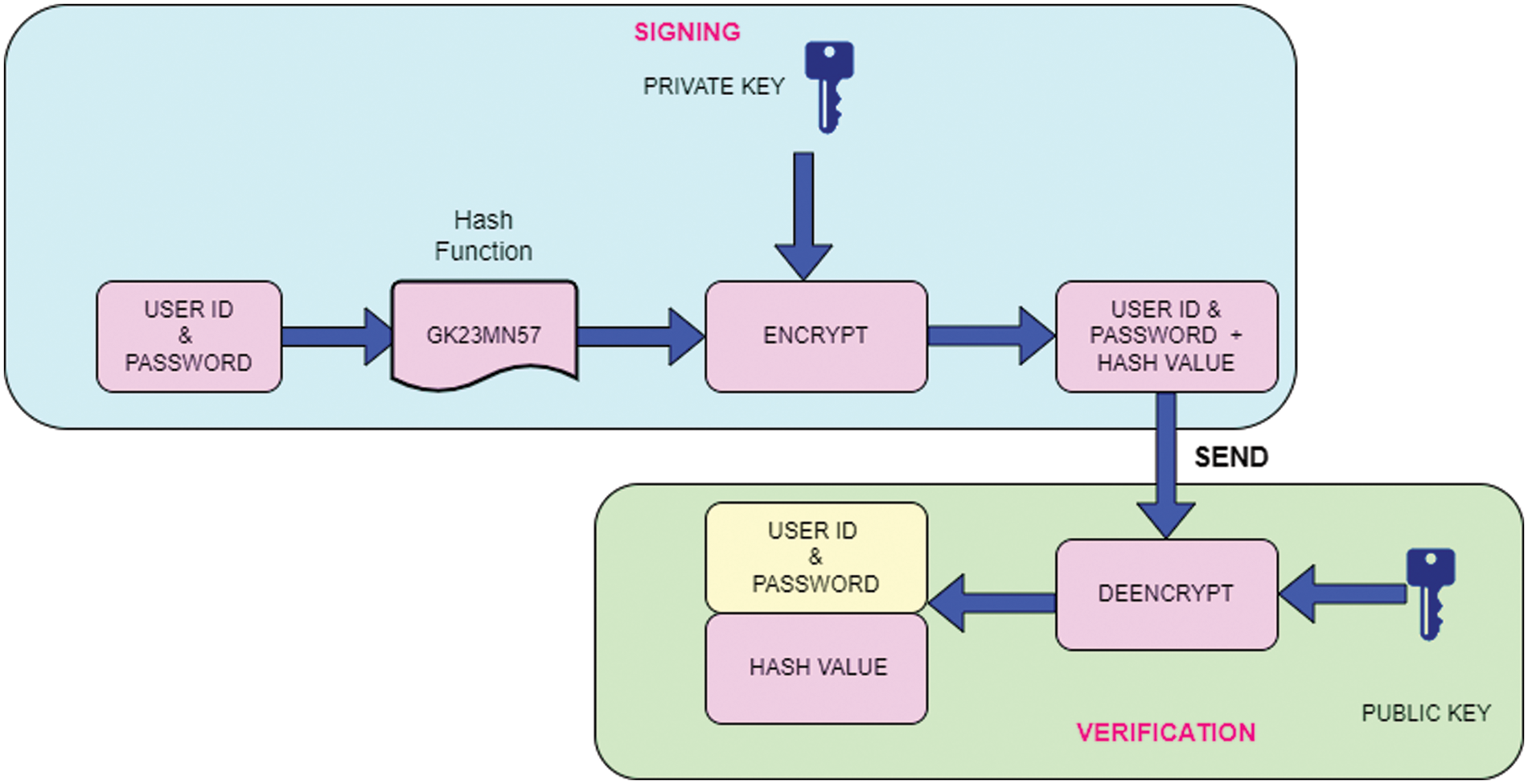
Figure 2: Workflow of the verification process
The working procedure of Fig. 2 describes below.
Step 1: The credential information of user
Step 2: Credential information with hvalue cane
Step 3: Decrypt the information by using the sender’s public key.
Step 4: Once it decrypts the information, it is passed through the same hash function (
In this way, it can store the credential information of the registered user in high-level security. For providing security authentication for sharing information, we used a blockchain of distributed network with all the users (nodes). Each user generates two keys; a public key used by other users to send messages among the nodes, and a private key used to encrypt the information. For the security authentication scheme, in this work, we proposed the RSA algorithm
After the provider generates a pair of public keys and private keys for every user, the security is established. Fig. 3. shows that the proposed hybrid architecture of two fish with RSA.
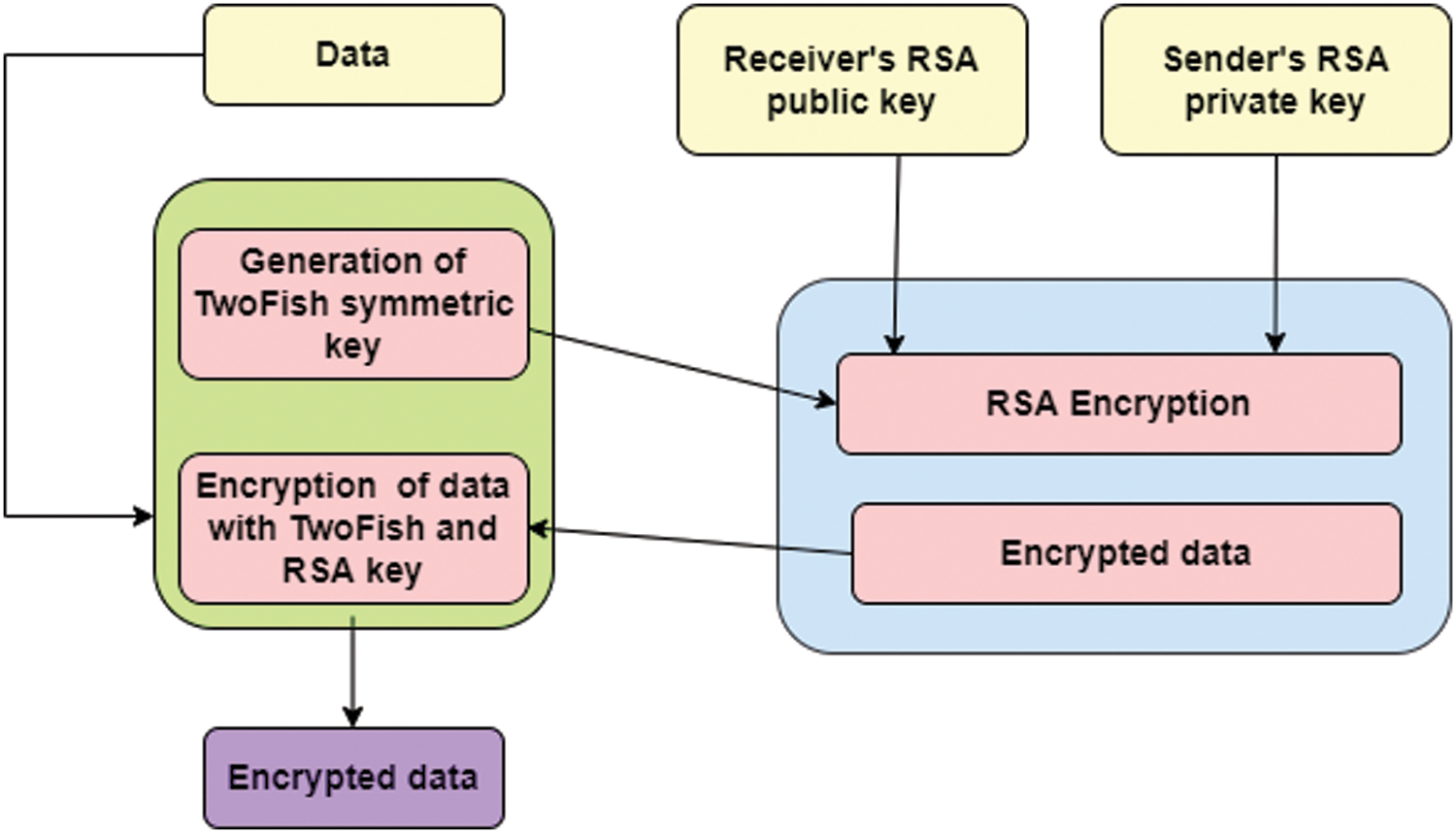
Figure 3: Hybrid architecture of two fish with RSA
To generate the encrypted file F1, user A first uses RSA with its public key. By using the second layer, user B generates the encrypted file F2. Finally, user Auploads two encrypted files: F1 and F2 into the server.
Step 3: Make
Step 4: Calculate ciphertext by using following formula,
Step 5: Construct a decryption key
User A requests the public key from the cloud service provider. The provider will return this public key to User A. User Auses the public key and User B uses a private key to generate the decryption key, and then User Auploads the newly generated decryption key into the server.
Step 6: Calculate the public key and private key
Step 7: The homomorphic Paillier algorithm generates the dciphertextpher text and the public key
Step 8: The public key
Step 9: The cloud server uses the decryption key and the ciphertext uploaded by User A. to conduct proxy decryption computing and generates new ciphertext.
Step 10: User B requests data and
Step 11: User B requests the cloud server to decrypt the data and the corresponding ciphertext. The cloud server sends the decrypted text to Medical Institution Band and uses RSA for decryption to get the original.
3.2 Data Storage Securely Using TF-RC-Proposed
The registered user can upload or download the information in a secure manner. For the secure storage of information encrypt the information and stored it in the cloud. For this encryption, this paper proposes two fish algorithm with a ripple consensus algorithm in the blockchain. Two fish algorithm is implemented as given below:

3.2.1 Components of Ripple Protocol
Step 11: Repeat Steps 4 to 10 until all words are XORed with another set of round keys.
Step 12: Swapping first and second words with third and fourth words effectively. The words are XOR with another set of round keys (