| Computers, Materials & Continua DOI:10.32604/cmc.2022.031613 |  |
| Article |
Artificial Intelligence Based Threat Detection in Industrial Internet of Things Environment
College of Computing and Information Technology, Shaqra University, Sharqa, Saudi Arabia
*Corresponding Author: Fahad F. Alruwaili. Email: alruwaili@su.edu.sa
Received: 22 April 2022; Accepted: 07 June 2022
Abstract: Internet of Things (IoT) is one of the hottest research topics in recent years, thanks to its dynamic working mechanism that integrates physical and digital world into a single system. IoT technology, applied in industries, is termed as Industrial IoT (IIoT). IIoT has been found to be highly susceptible to attacks from adversaries, based on the difficulties observed in IIoT and its increased dependency upon internet and communication network. Intentional or accidental attacks on these approaches result in catastrophic effects like power outage, denial of vital health services, disruption to civil service, etc., Thus, there is a need exists to develop a vibrant and powerful for identification and mitigation of security vulnerabilities in IIoT. In this view, the current study develops an AI-based Threat Detection and Classification model for IIoT, abbreviated as AITDC-IIoT model. The presented AITDC-IIoT model initially pre-processes the input data to transform it into a compatible format. In addition, Whale Optimization Algorithm based Feature Selection (WOA-FS) is used to elect the subset of features. Moreover, Cockroach Swarm Optimization (CSO) is employed with Random Vector Functional Link network (RVFL) technique for threat classification. Finally, CSO algorithm is applied to appropriately adjust the parameters related to RVFL model. The performance of the proposed AITDC-IIoT model was validated under benchmark datasets. The experimental results established the supremacy of the proposed AITDC-IIoT model over recent approaches.
Keywords: Security; industrial internet of things; threat detection; artificial intelligence; feature selection
Internet of Things (IoT) has managed to pervade numerous domains from home automation to industries with crucial frameworks. The contributions of IoT are wide enough started from attaining the final cases or complementing/exchanging the processes involved in industrial control systems. The extensive applicability of IoT gadgets allows the industrial technologies to flourish, in industries with less technical maturity. Few appropriate instances are linked with exploitation of oil and electricity production while both the domains are straightforwardly linked with national cyberdefence [1]. Industrial Internet of Things (IIoT) combines multiple players such as sensors, gadgets, and physical machineries with internet. Then, it utilizes software to conduct deep analytics and convert huge volumes of both structured and unstructured data into powerful insights and information [2]. IIoT emphasizes the application of IoT in manufacturing zones since there is a growing interest among researchers to involve Machine-to-Machine (M2 M) transmission, big data, and Machine Learning (ML) in industry settings. IoT can also be applied in some other domains such as linking wastewater systems and manufacturing of robots, flow gauges, electric meters and other connected systems, and industrial gadgets. With the incorporation of IIoT, institutions as well as manufacturing hubs gain high efficiency and dependability upon its works [3]. Since IoT is capable of linking multiple gadgets with internet, it allows the identification of distinct threats to perform anomalous actions. There is an increasing number of loopholes and susceptibilities found in the protocol utilized by IIoT structure. If it encounters risks, sophisticated attacks can be made at IIoT environment using multiple methods [4]. The intentions of an attacker are multitude in nature such as gaining access to appropriate data, money theft, and source corruption [5].
IoT gadgets have special features with regard to transmission. So, whenever there is an attack made, it tends to provoke the decentralized assaults on any kind of structures [6]. These are the difficulties faced in designing an identification algorithm for IoT which are well known in traditional networks [7,8]. The main goal of machine learning technique is to empower the technologies so that it learns and performs estimation based on the information scheduled earlier. Though the usage of ML in identifying anomalous conduct is an established process, intruder identification domain has been mostly untouched [9]. In conventional techniques, anomaly recognition has been performed by statistical methodologies. Therefore, the increasing penetration of ML methods has unlocked new probabilities for the identification of outlier information, thanks to the accessibility of huge volume of information which might be leveraged using ML methods. In this perspective, such ML methods provide an alluring viewpoint to be applied in IoT application zones. It is challenging to make use of stationary models in this regard [10].
Aboelwafa et al. [11] proposed a novel attack detection methodology via Autoencoder (AE). The study exploited the sensor data in correlation with time and space to sequentially recognize the fabricated dataset. Furthermore, the fabricated dataset is refined by Denoising AE (DAE). The DAE dataset was cleaned in an efficient manner and produced clean datasets from the corrupted (attacked) information. Hassan et al. [12] developed a down sampler-encoder-based collective dataset generator. This model was to ensure the effective collection of real distribution of the attack model for large-scale IIoT attack surfaces. The presented downsampler-based data generator is upgraded simultaneously and confirmed at the time of training Deep Neural Network (DNN) discriminators so as to ensure robustness.
Qureshi et al. [13] presented a secure and novel architecture for identification of security threats in RPL-based IoT and IIoT systems. The presented architecture possesses the ability to identify Version number, HELLO-Flood, Blackhole, and Sinkhole attacks. Hassan et al. [14] enhanced the reliability of IIoT systems using a scalable and reliable cyberattack recognition method i.e., Supervisory Control and Data Acquisition (SCADA) technique. To be specific, an ensemble-learning method, related to the integration of Random Subspace (RS) learning model using Random Tree (RT), was presented to identify SCADA cyberattacks o through network traffic from SCADA-related IIoT architecture. The researchers in the literature [15–19] developed a detection module based on Stacked Variation Auto-Encoder (VAE) with Convolution Neural Network (CNN). This model has the capability to learn about hidden architecture of the scheme’s activity and reveal its ransomware behaviour. Furthermore, a data augmentation technique was proposed based on VAE to generate a novel dataset that can be utilized in training a system and to improve the generalized abilities of the presented method.
The current study develops an AI-based Threat Detection and Classification model for IIoT, named AITDC-IIoT model. The presented AITDC-IIoT model initially pre-processes the input data and transforms it into a compatible format. Then, Whale Optimization Algorithm-based Feature Selection (WOA-FS) model has been involved to elect the subset of features. Moreover, Cockroach Swarm Optimization (CSO) is employed with Random Vector Functional Link network (RVFL) model for classification of threats. Finally, CSO algorithm is applied to appropriately adjust the parameters involved in RVFL model. The performance of the proposed AITDC-IIoT model was validated using benchmark datasets.
In this study, a new AITDC-IIoT model has been developed for proficient threat detection and classification using IIoT. The presented AITDC-IIoT model initially pre-processes the input data to convert it into a compatible format. Followed by, WOA-FS model is applied to elect the subset of features. At last, CSO is employed with RVFL model for classification of threats. Fig. 1 depicts the overall block diagram of AITDC-IIoT technique.

Figure 1: Block diagram of AITDC-IIoT technique
In order to elect the features, WOA is applied in this study. In order to explore the most number of possible solutions for the problem from searching space, whale individuals are utilized from the community [20]. Three functions are applied in WOA such as hunting, encircling, and shrinking. During exploitation stage, both surrounding and shrinking functions are utilized. However, under exploration stage, the hunting function is utilized. To arrive at the optimal solution for Dimension Optimization problem (DO), the processes of
Encircling Operation
Shrinking Operation
Hunting Operation
The arbitrary number in the range of [0 1] is explained through
In WOA, the whale moves from searching space to adapt to the position pointed in the space which is named as ‘constant space’. The transformation can be done using
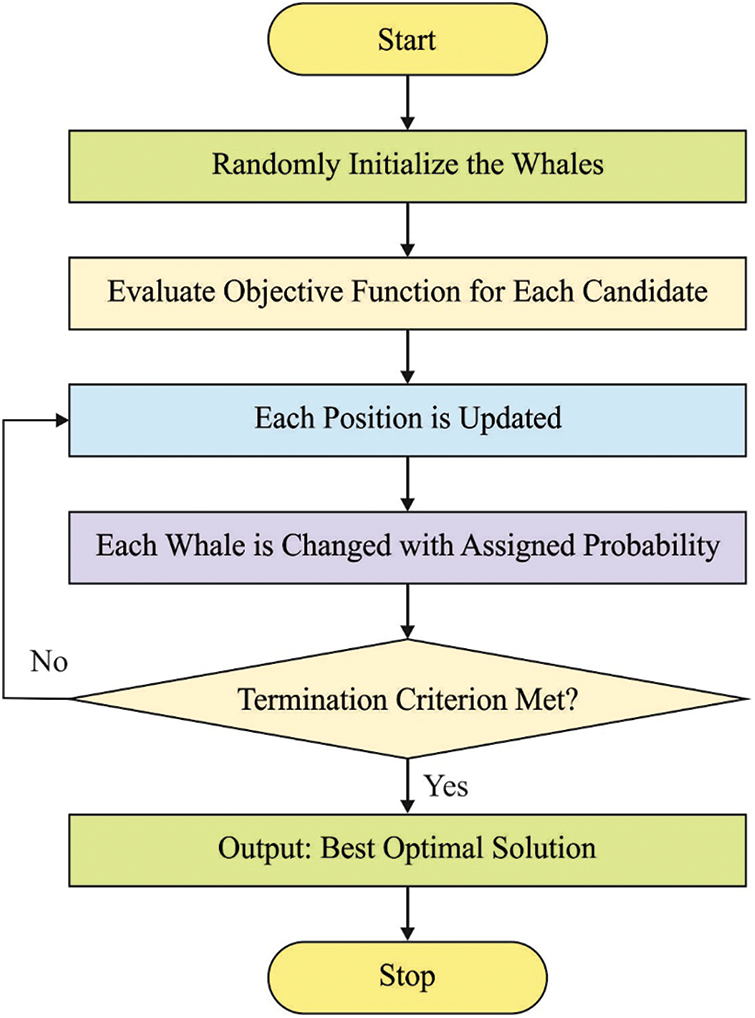
Figure 2: WOA Flowchart
The
2.2 Threat Classification Module
Once the features are selected, they are fed as input in RVFL model for classification purpose. RVFL model depends upon Single Layer Feed Forward Network (SLFN) [21]. In this method, the weights are arbitrarily initialized based on the node and weight is tuned with no iteration. Consider that RVFL network contains J improvement node and
The problem equation for RVFL is stated as
whereas
At novel instance
whereas
2.3 Parameter Optimization Module
In this final stage, CSO algorithm is applied to appropriately adjust the parameters related to RVFL model [22–25]. The CSO model imitates cockroach behavior i.e., dispersing, ruthless, chase-swarming behaviors [26]. In
Chase-Swarming Behavior:
In this equation,
Whereas opt indicates the optimal value.
Dispersion Behaviour:
Now rand(l, D) represents the
Ruthless Behavior
In this formula,
1. Initialize cockroach swarm with uniform distribution of arbitrary numbers and set value for each parameter.
2. Search
3. Implement chase-swarming by Eq. (10)
4. Implement dispersion behaviour by Eq. (13)
5. Implement ruthless behavior by Eq. (14)
6. Repeat the loop until the end condition is obtained.
In this section, the proposed AITDC-IIoT model was experimentally validated using N-BaIoT dataset [27]. The dataset holds 76,200 samples under 9 class labels which are given in Tab. 1.
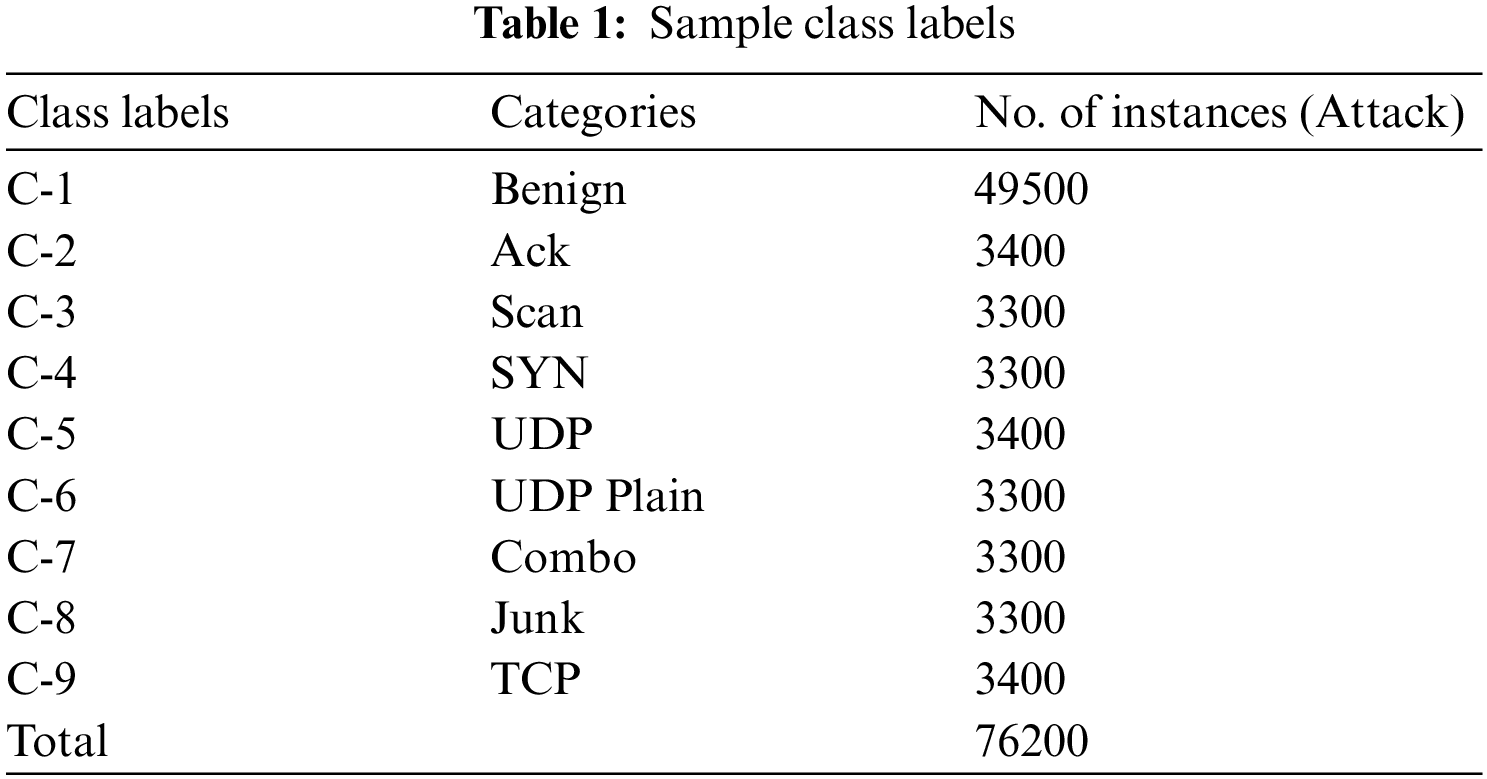
Fig. 3 demonstrates the set of confusion matrices generated by the proposed AITDC-IIoT model on test dataset. The figures imply that the proposed AITDC-IIoT model effectively recognized all the nine classes in the applied dataset.
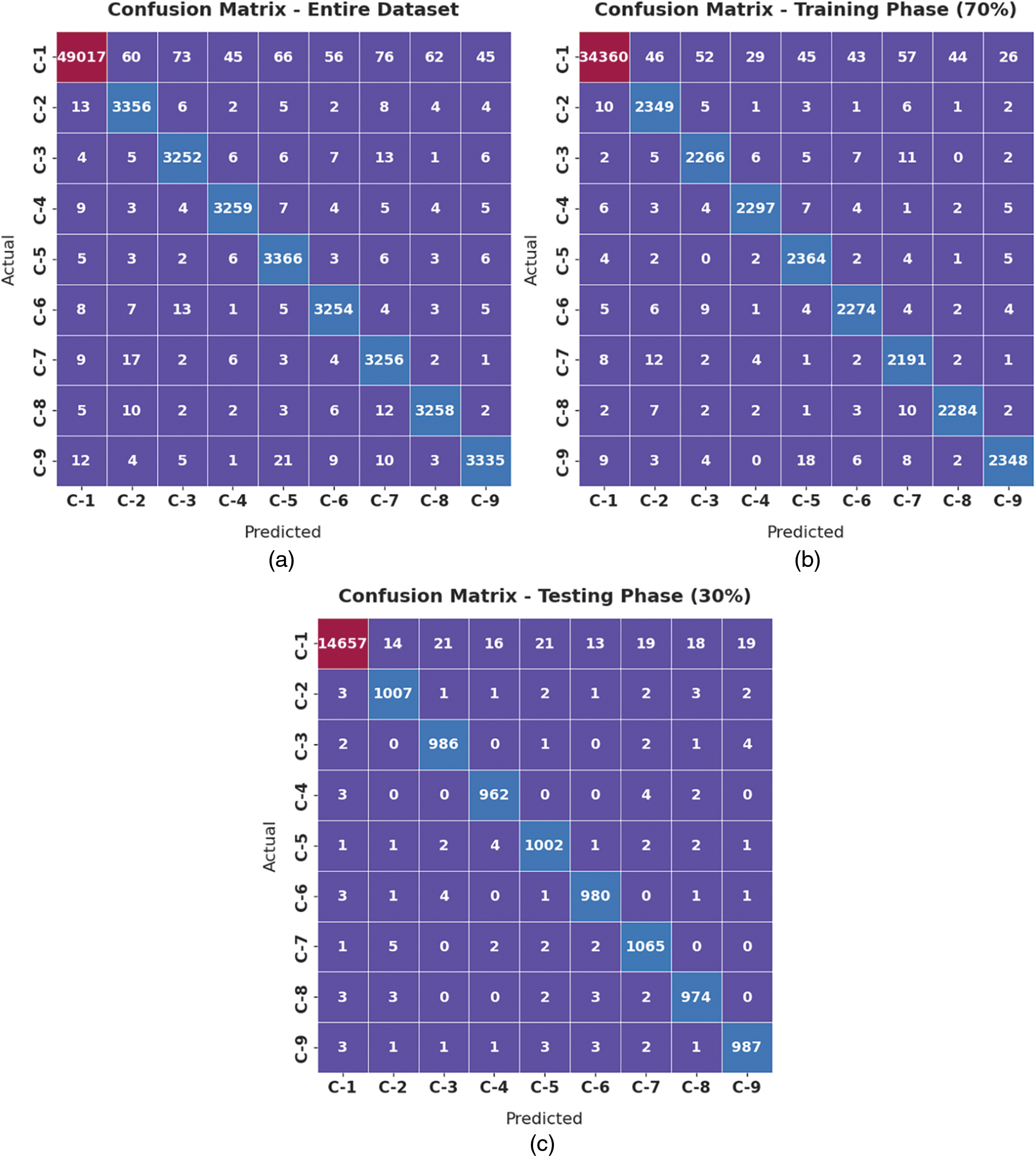
Figure 3: Confusion matrices generated by AITDC-IIoT technique for (a) entire dataset, (b) 70% of TR dataset, and (c) 30% of TS dataset
Tab. 2 illustrates the results offered by AITDC-IIoT model on threat classification in IIoT environment. The results indicate that the proposed AITDC-IIoT model gained significant results under all the classes. For instance, with entire dataset, the proposed AITDC-IIoT model categorized benign classes with
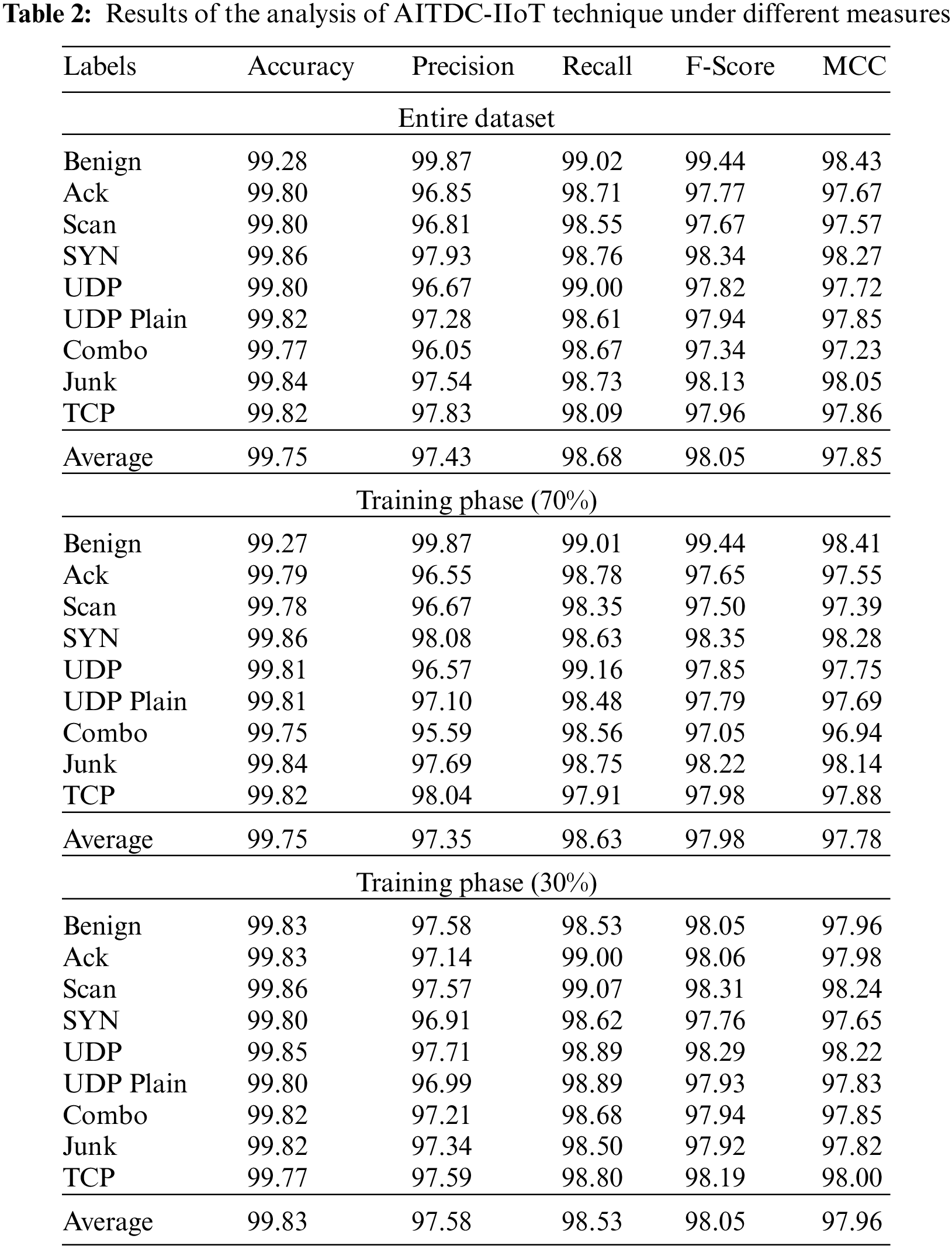
Fig. 4 demonstrates the average threat classification outcomes achieved by the proposed AITDC-IIoT model. Upon entire dataset, AITDC-IIoT model achieved average
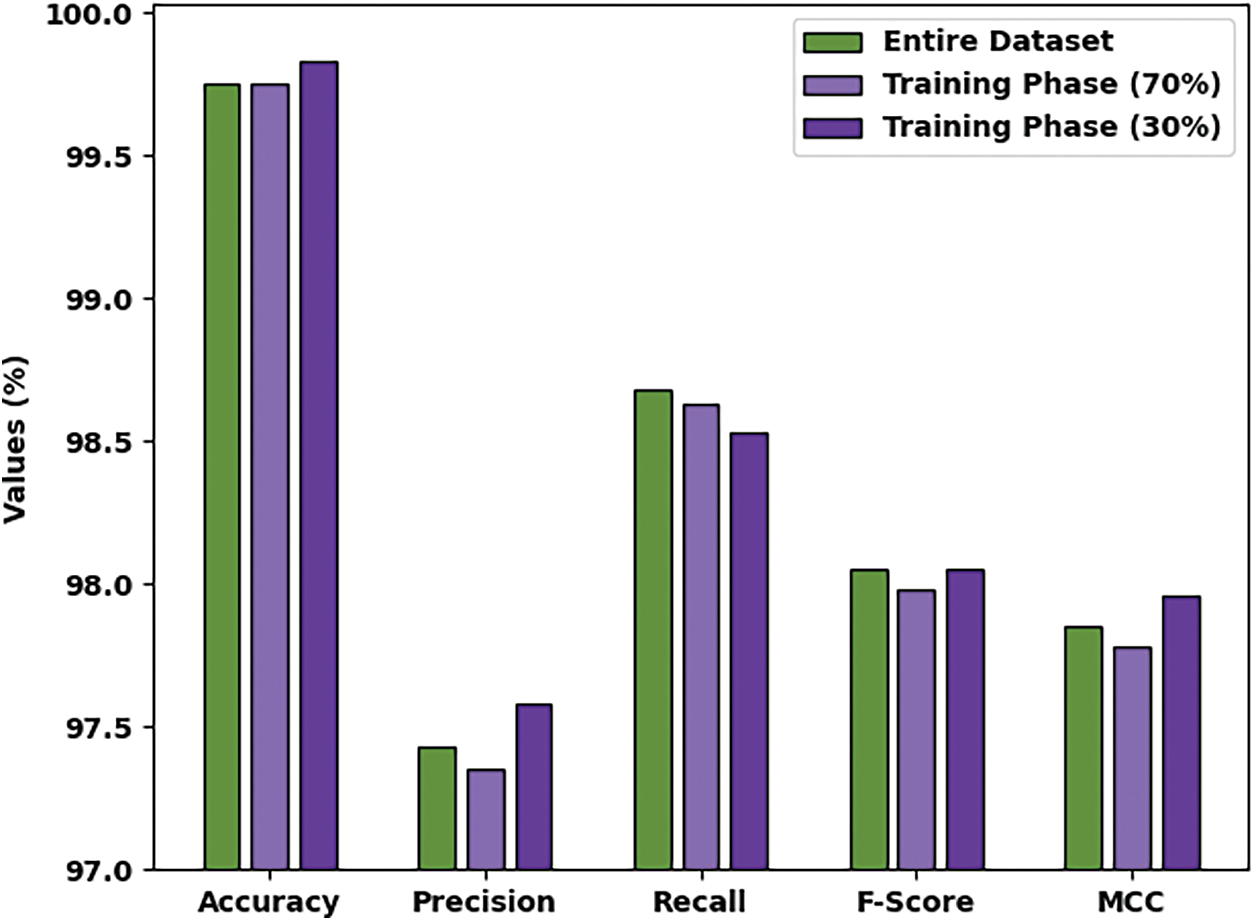
Figure 4: Average analysis results of AITDC-IIoT technique under different measures
A brief precision-recall analysis was conducted upon AITDC-IIoT approach on test dataset and the results are depicted in Fig. 5. As per the figure, it is clear that the proposed AITDC-IIoT method accomplished maximum precision-recall performance under different number of class labels.
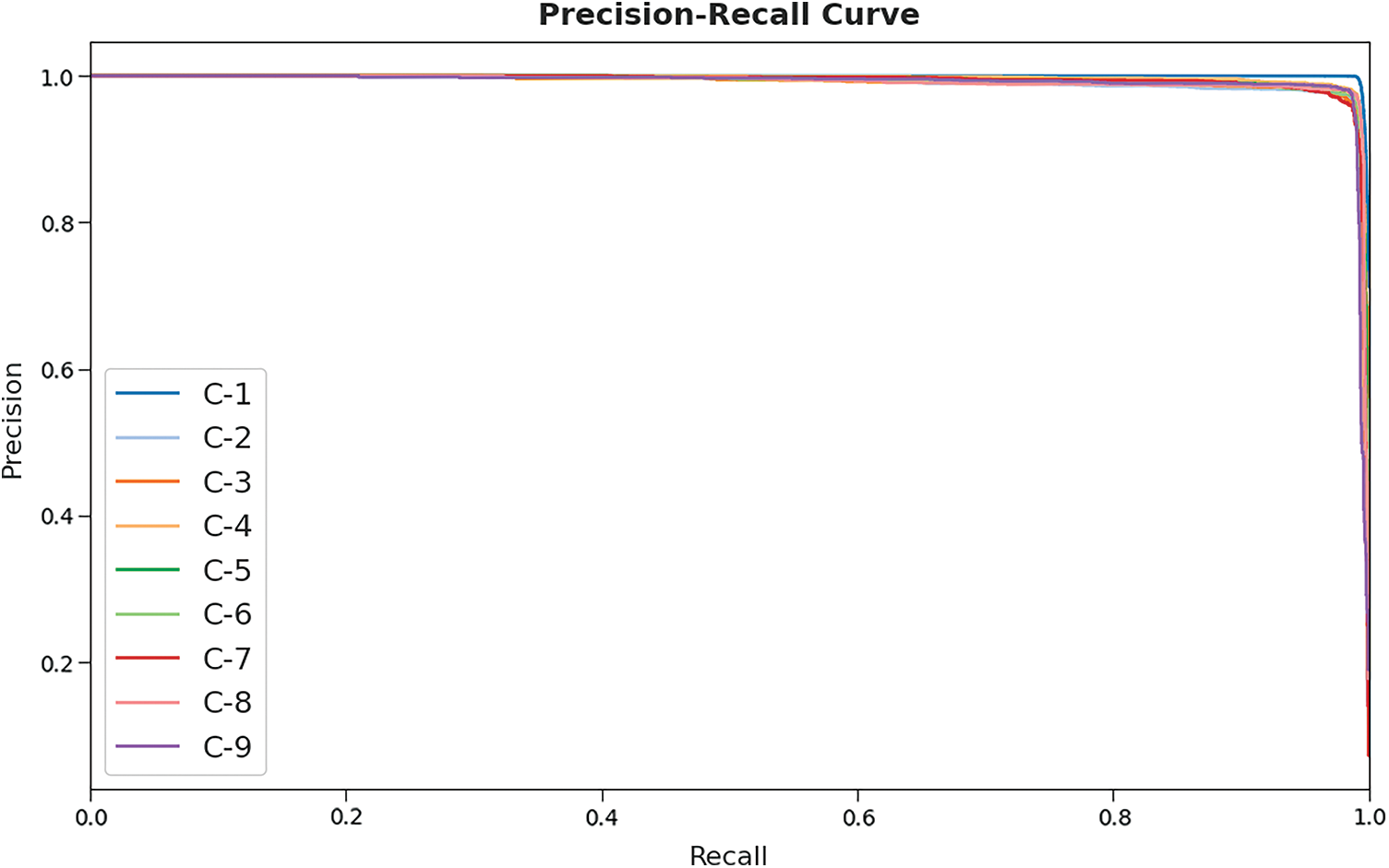
Figure 5: Precision-recall curve analysis results of AITDC-IIoT technique
Training Accuracy (TA) and Validation Accuracy (VA) values, attained by AITDC-IIoT model on test dataset, are demonstrated in Fig. 6. The experimental outcome imply that AITDC-IIoT model gained the maximum TA and VA values. To be specific, VA seemed to be higher than TA.
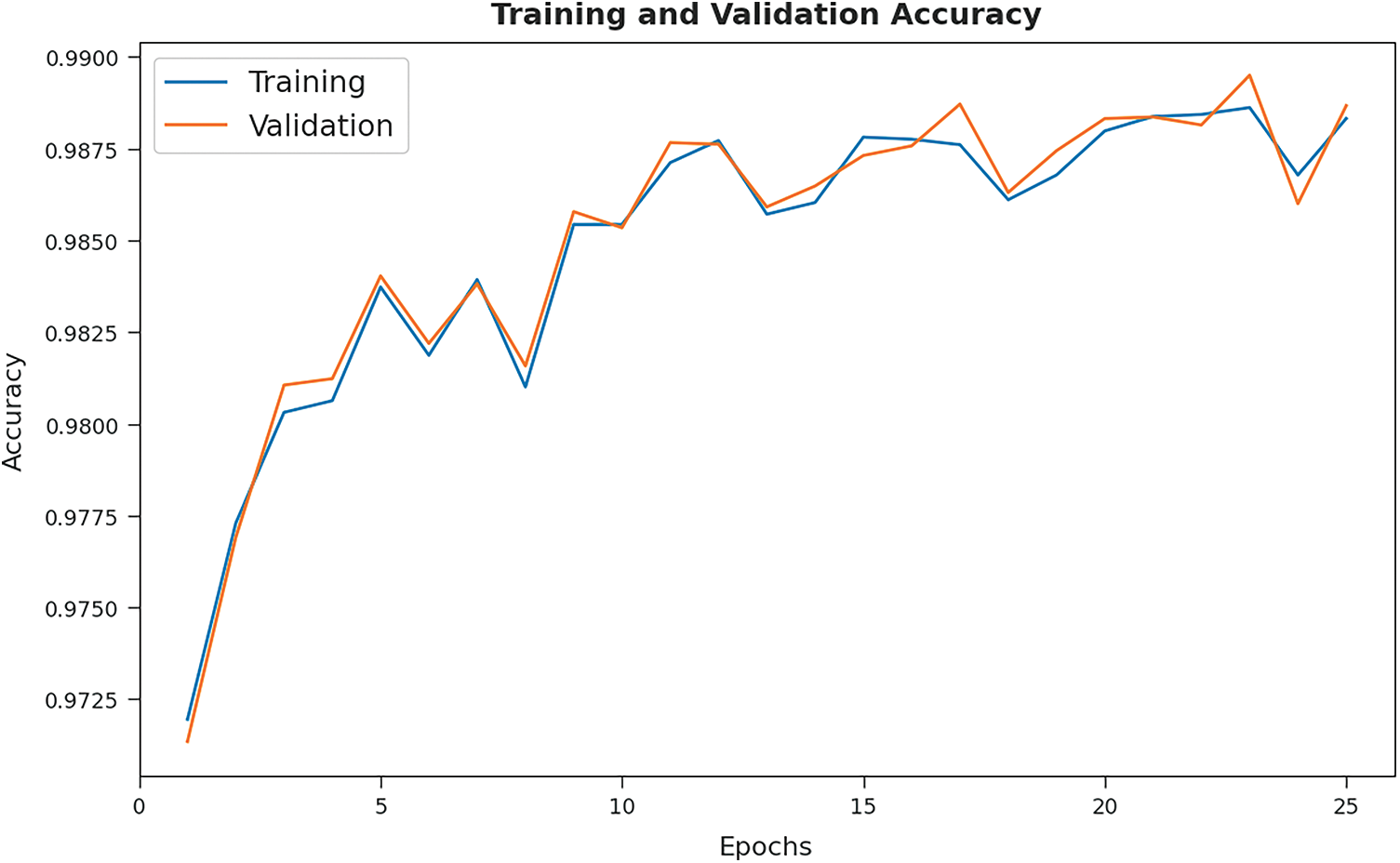
Figure 6: TA and VA graph analyses results of AITDC-IIoT technique
Training Loss (TL) and Validation Loss (VL) values, achieved by the proposed AITDC-IIoT technique on test dataset, are portrayed in Fig. 7. The experimental outcomes infer that AITDC-IIoT model achieved the least TL and VL values. To be specific, VL seemed to be lower than TL.
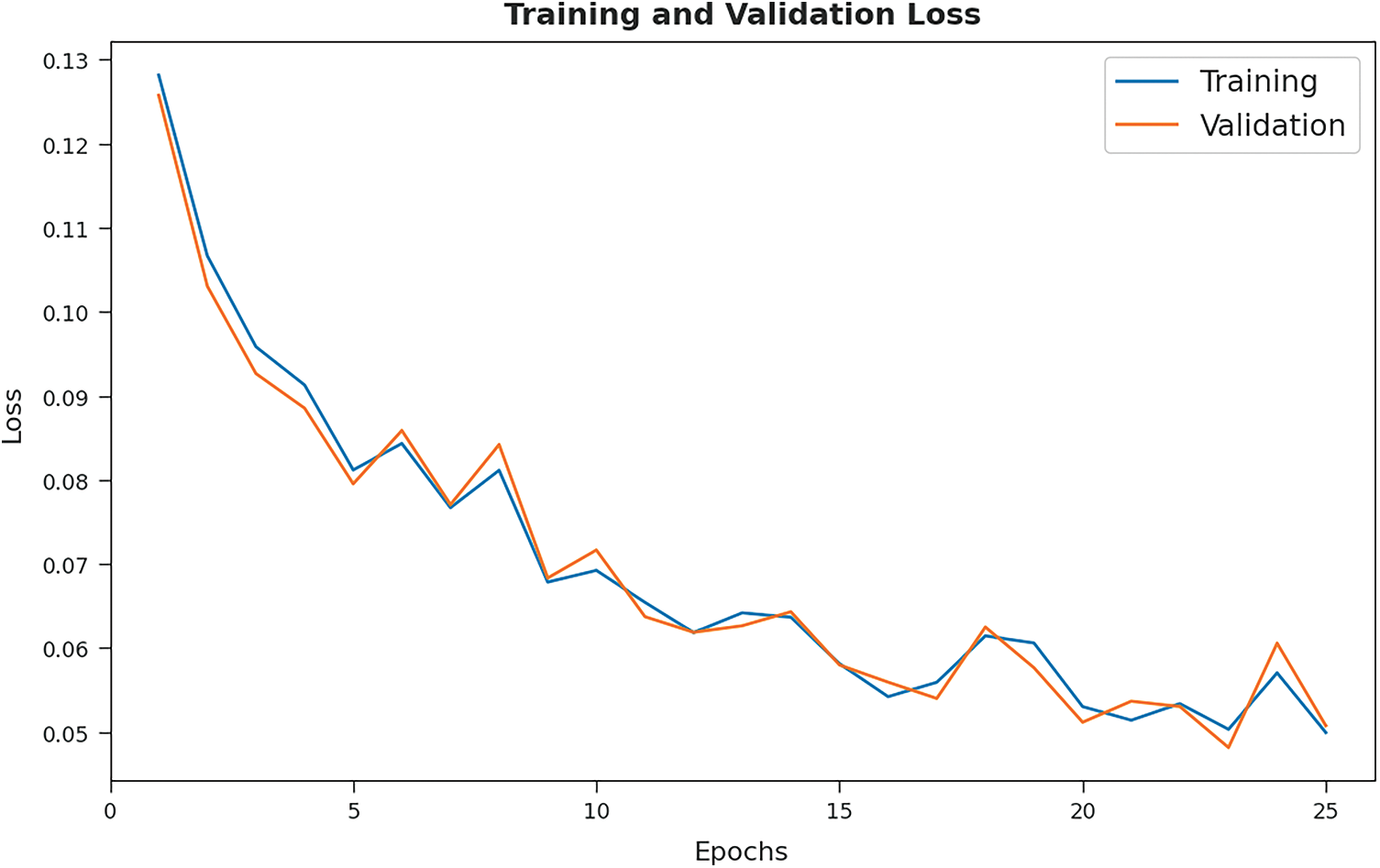
Figure 7: TL and VL graph analyses results of AITDC-IIoT technique
In order to validate the supremacy of the proposed AITDC-IIoT model, a detailed comparative analysis was performed against existing models and the results are shown in Tab. 3 [28].
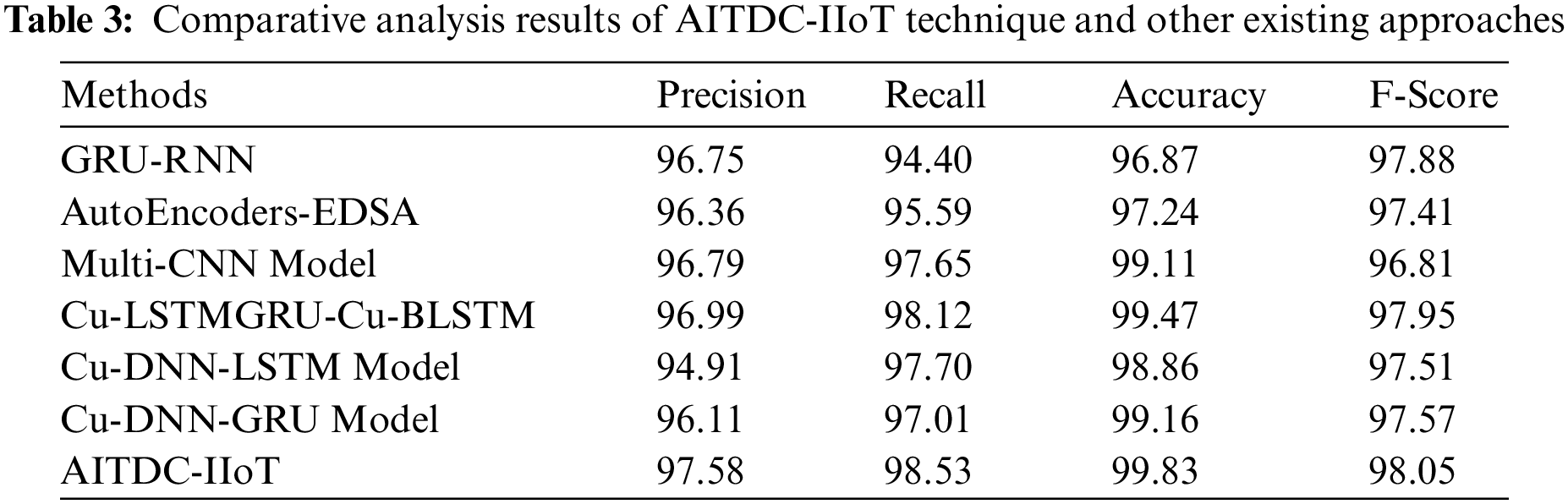
Fig. 8 illustrates the comparative examination results of AITDC-IIoT model and other existing methods in terms of
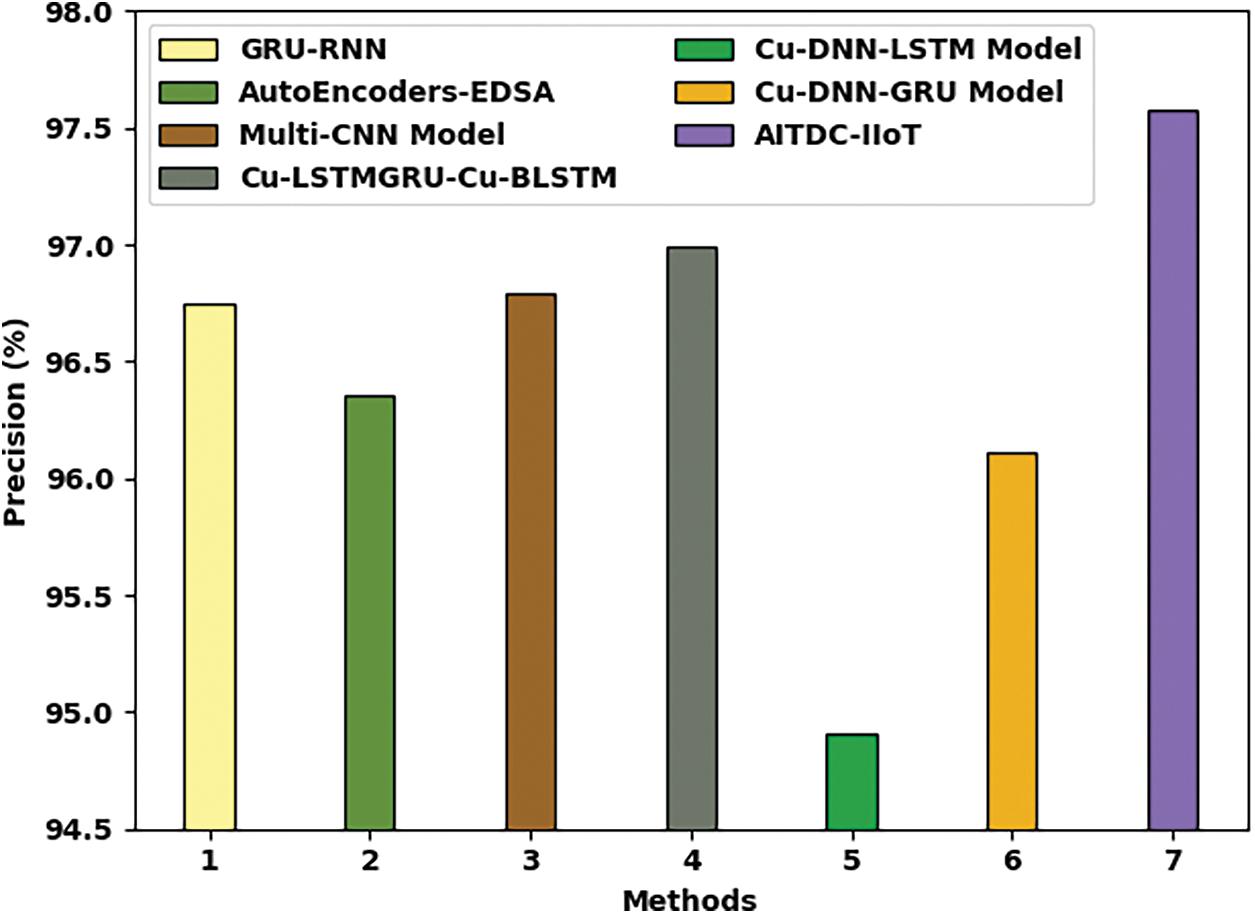
Figure 8:
Fig. 9 showcases the comparative analysis results achieved by the proposed AITDC-IIoT model and other existing methods in terms of
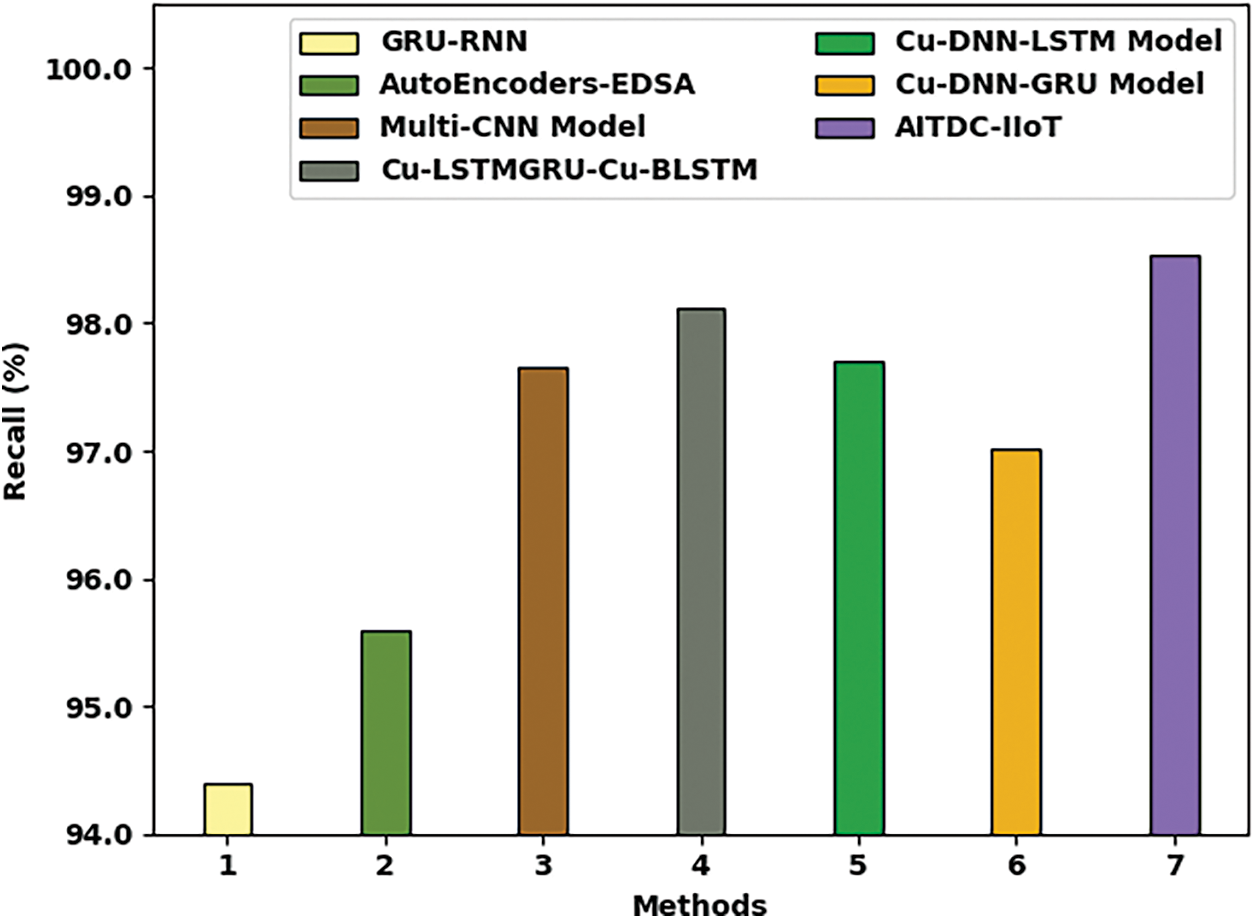
Figure 9:
Fig. 10 depicts the comparative investigation results attained by the proposed AITDC-IIoT approach and other existing methods in terms of
Figure 10:
Fig. 11 demonstrates the comparative analysis results achieved by AITDC-IIoT system and other existing systems in terms of
Based on the results and discussion made above, it is apparent that the proposed AITDC-IIoT model is an excellent performer in terms of threat detection and classification compared to the existing techniques.
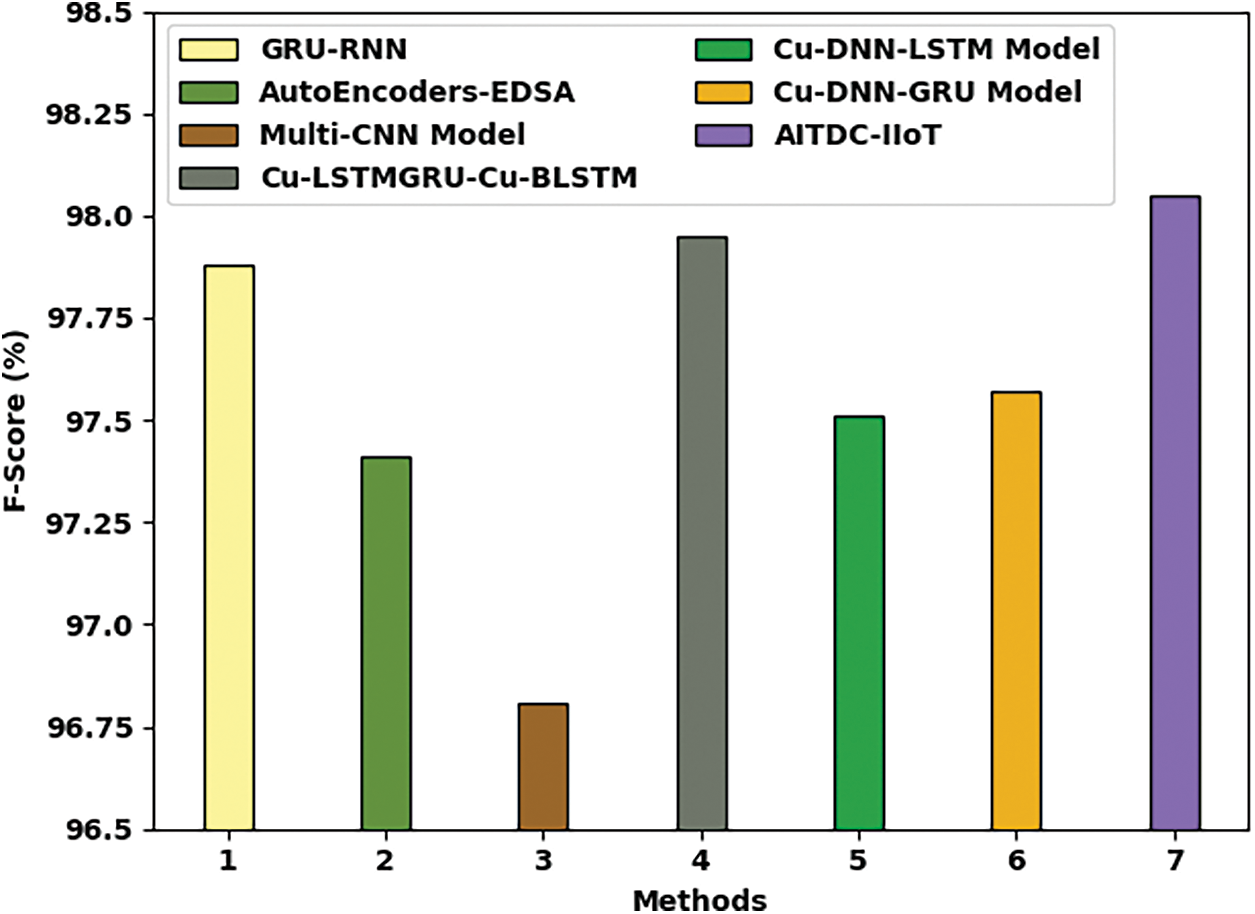
Figure 11:
In this study, a new AITDC-IIoT model has been developed for proficient threat detection and classification. The presented AITDC-IIoT model initially pre-processes the input data so as to convert it to a compatible format. Followed by, WOA-FS model is involved to elect the subset of features. Moreover, CSO is employed with RVFL model for threat classification. Finally, CSO algorithm is applied to appropriately adjust the parameters related to RVFL model. The performance of the proposed AITDC-IIoT model was validated under benchmark datasets. The experimental results established the supremacy of the proposed AITDC-IIoT technique over recent approaches. Thus, AITDC-IIoT model can be employed for effectual threat detection and classification in IIoT environment. In future, the performance of the model can be enhanced by including outlier detection and clustering processes.
Funding Statement: The author received no specific funding for this study.
Conflicts of Interest: The author declares that he has no conflicts of interest to report regarding the present study.
References
1. L. L. Dhirani, E. Armstrong and T. Newe, “Industrial IoT, cyber threats, and standards landscape: Evaluation and roadmap,” Sensors, vol. 21, no. 11, pp. 3901, 2021. [Google Scholar]
2. K. Tsiknas, D. Taketzis, K. Demertzis and C. Skianis, “Cyber threats to industrial iot: A survey on attacks and countermeasures,” IoT, vol. 2, no. 1, pp. 163–186, 2021. [Google Scholar]
3. J. E. Rubio, R. Roman and J. Lopez, “Integration of a threat traceability solution in the industrial internet of things,” IEEE Transactions on Industrial Informatics, vol. 16, no. 10, pp. 6575–6583, 2020. [Google Scholar]
4. H. Naeem, F. Ullah, M. R. Naeem, S. Khalid, D. Vasan et al., “Malware detection in industrial internet of things based on hybrid image visualization and deep learning model,” Ad Hoc Networks, vol. 105, pp. 102154, 2020. [Google Scholar]
5. S. Sharmeen, S. Huda, J. H. Abawajy, W. N. Ismail and M. M. Hassan, “Malware threats and detection for industrial mobile-iot networks,” IEEE Access, vol. 6, pp. 15941–15957, 2018. [Google Scholar]
6. K. Yu, L. Tan, S. Mumtaz, S. A. Rubaye, A. A. Dulaimi et al., “Securing critical infrastructures: Deep-learning-based threat detection in iiot,” IEEE Communications Magazine, vol. 59, no. 10, pp. 76–82, 2021. [Google Scholar]
7. P. Trakadas, P. Simoens, P. Gkonis, L. Sarakis, A. Angelopoulos et al., “An artificial intelligence-based collaboration approach in industrial iot manufacturing: Key concepts, architectural extensions and potential applications,” Sensors, vol. 20, no. 19, pp. 5480, 2020. [Google Scholar]
8. M. A. Hawawreh, F. d. Hartog and E. Sitnikova, “Targeted ransomware: A new cyber threat to edge system of brownfield industrial internet of things,” IEEE Internet Things Journal, vol. 6, no. 4, pp. 7137–7151, 2019. [Google Scholar]
9. G. D. L. T. Parra, P. Rad and K. K. R. Choo, “Implementation of deep packet inspection in smart grids and industrial internet of things: Challenges and opportunities,” Journal of Network and Computer Applications, vol. 135, pp. 32–46, 2019. [Google Scholar]
10. A. H. Muna, N. Moustafa and E. Sitnikova, “Identification of malicious activities in industrial internet of things based on deep learning models,” Journal of Information Security and Applications, vol. 41, pp. 1–11, 2018. [Google Scholar]
11. M. M. N. Aboelwafa, K. G. Seddik, M. H. Eldefrawy, Y. Gadallah and M. Gidlund, “A Machine-learning-based technique for false data injection attacks detection in industrial IoT,” IEEE Internet Things Journal, vol. 7, no. 9, pp. 8462–8471, 2020. [Google Scholar]
12. M. M. Hassan, M. R. Hassan, S. Huda and V. H. C. d. Albuquerque, “A robust deep-learning-enabled trust-boundary protection for adversarial industrial iot environment,” IEEE Internet Things Journal, vol. 8, no. 12, pp. 9611–9621, 2021. [Google Scholar]
13. K. N. Qureshi, S. S. Rana, A. Ahmed and G. Jeon, “A novel and secure attacks detection framework for smart cities industrial internet of things,” Sustainable Cities and Society, vol. 61, pp. 102343, 2020. [Google Scholar]
14. M. M. Hassan, A. Gumaei, S. Huda and A. Almogren, “Increasing the trustworthiness in the industrial iot networks through a reliable cyberattack detection model,” IEEE Transactions on Industrial Informatics, vol. 16, no. 9, pp. 6154–6162, 2020. [Google Scholar]
15. M. A. Hawawreh and E. Sitnikova, “Industrial internet of things based ransomware detection using stacked variational neural network,” in Proc. of the 3rd Int. Conf. on Big Data and Internet of Things, Melbourn VIC Australia, pp. 126–130, 2019. [Google Scholar]
16. A. M. Hilal, J. S. Alzahrani, I. Abunadi, N. Nemri, F. N. Al-Wesabi et al., “Intelligent deep learning model for privacy preserving iiot on 6 g environment,” Computers, Materials & Continua, vol. 72, no. 1, pp. 333–348, 2022. [Google Scholar]
17. M. A. Alohali, F. N. Al-Wesabi, A. M. Hilal, S. Goel, D. Gupta and A. Khanna, “Artificial intelligence enabled intrusion detection systems for cognitive cyber-physical systems in industry 4.0 environment,” Cognitive Neurodynamics, 2022, https://doi.org/10.1007/s11571-022-09780-8. [Google Scholar]
18. A. M. Hilal, M. A. Alohali, F. N. Al-Wesabi, N. Nemri, J. Hasan et al., “Enhancing quality of experience in mobile edge computing using deep learning based data offloading and cyberattack detection technique,” Cluster Computing, 2021, https://doi.org/10.1007/s10586-021-03401-5. [Google Scholar]
19. A. A. Albraikan, S. B. Haj Hassine, S. M. Fati, F. N. Al-Wesabi, A. M. Hilal et al., “Optimal deep learning-based cyberattack detection and classification technique on social networks,” Computers, Materials & Continua, vol. 72, no. 1, pp. 907–923, 2022. [Google Scholar]
20. S. Mirjalili and A. Lewis, “The whale optimization algorithm,” Advances in Engineering Software, vol. 95, pp. 51–67, 2015. [Google Scholar]
21. F. Essa, M. A. Elaziz and A. Elsheikh, “Prediction of power consumption and water productivity of seawater greenhouse system using random vector functional link network integrated with artificial ecosystem-based optimization,” Process Safety and Environmental Protection, vol. 144, pp. 322–329, 2020. [Google Scholar]
22. A. Muthumari, J. Banumathi, S. Rajasekaran, P. Vijayakarthik, K. Shankar et al., “High security for de-duplicated big data using optimal simon cipher,” Computers, Materials & Continua, vol. 67, no. 2, pp. 1863–1879, 2021. [Google Scholar]
23. R. Gopi, P. Muthusamy, P. Suresh, C. G. G. S. Kumar, I. V. Pustokhina et al., “Optimal confidential mechanisms in smart city healthcare,” Computers, Materials & Continua, vol. 70, no. 3, pp. 4883–4896, 2022. [Google Scholar]
24. D. A. Pustokhin, I. V. Pustokhin, P. Rani, V. Kansal, M. Elhoseny et al., “Optimal deep learning approaches and healthcare big data analytics for mobile networks toward 5G,” Computers & Electrical Engineering, vol. 95, pp. 107376, 2021. [Google Scholar]
25. J. A. Alzubi, O. A. Alzubi, M. Beseiso, A. K. Budati and K. Shankar, “Optimal multiple key-based homomorphic encryption with deep neural networks to secure medical data transmission and diagnosis,” Expert Systems, vol. 39, no. 4, pp. e12879, 2022. [Google Scholar]
26. J. Kwiecień and M. Pasieka, “Cockroach swarm optimization algorithm for travel planning,” Entropy, vol. 19, no. 5, pp. 213, 2017. [Google Scholar]
27. A. Abeshu and N. Chilamkurti, “Deep learning: The frontier for distributed attack detection in fog-to-things computing,” IEEE Communications Magazine, vol. 56, no. 2, pp. 169–175, 2018. [Google Scholar]
28. D. Javeed, T. Gao, M. Khan and D. Shoukat, “A hybrid intelligent framework to combat sophisticated threats in secure industries,” Sensors, vol. 22, no. 4, pp. 1582, 2022. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |