| Computers, Materials & Continua DOI:10.32604/cmc.2022.031660 |  |
| Article |
Chaotic Pigeon Inspired Optimization Technique for Clustered Wireless Sensor Networks
1Department of Electrical and Computer Engineering, International Islamic University Malaysia, 53100, Kuala Lumpur, Malaysia
2Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
3Department of Computer Science, College of Science & Art at Mahayil, King Khalid University, Saudi Arabia
4Department of Information Technology, College of Computer and Information Sciences, Princess Nourah Bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
5Department of Industrial Engineering, College of Engineering at Alqunfudah, Umm Al-Qura University, Saudi Arabia
6Department of Information Technology, College of Computers and Information Technology, Taif University, Taif, P.O. Box 11099, Taif, 21944, Saudi Arabia
7Department of Digital Media, Faculty of Computers and Information Technology, Future University in Egypt, New Cairo, 11835, Egypt
*Corresponding Author: Anwer Mustafa Hilal. Email: a.hilal@psau.edu.sa
Received: 23 April 2022; Accepted: 08 June 2022
Abstract: Wireless Sensor Networks (WSN) interlink numerous Sensor Nodes (SN) to support Internet of Things (loT) services. But the data gathered from SNs can be divulged, tempered, and forged. Conventional WSN data processes manage the data in a centralized format at terminal gadgets. These devices are prone to attacks and the security of systems can get compromised. Blockchain is a distributed and decentralized technique that has the ability to handle security issues in WSN. The security issues include transactions that may be copied and spread across numerous nodes in a peer-peer network system. This breaches the mutual trust and allows data immutability which in turn permits the network to go on. At some instances, few nodes die or get compromised due to heavy power utilization. The current article develops an Energy Aware Chaotic Pigeon Inspired Optimization based Clustering scheme for Blockchain assisted WSN technique abbreviated as EACPIO-CB technique. The primary objective of the proposed EACPIO-CB model is to proficiently group the sensor nodes into clusters and exploit Blockchain (BC) for inter-cluster communication in the network. To select Cluster Heads (CHs) and organize the clusters, the presented EACPIO-CB model designs a fitness function that involves distinct input parameters. Further, BC technology enables the communication between one CH and the other and with the Base Station (BS) in the network. The authors conducted comprehensive set of simulations and the outcomes were investigated under different aspects. The simulation results confirmed the better performance of EACPIO-CB method over recent methodologies.
Keywords: Blockchain; wireless sensor networks; clustering; energy efficiency; security; data transmission
Wireless Sensor Network (WSN) encompasses multiple technologies into it such as wireless communication, sensing, and computing [1]. In general, the external targets are observed literally via several kinds of microsensors. These microsensors generate a vast amount of sensitive information at an unexpected rate. Even though it is common to have distinct application phenomenon and hardware positioning, the utmost objective is to collect, transmit and process the collected data. At last, the end users get intriguing information from the data source [2].
Since WSN is regarded as a data-centric network system, it has a basic issue to be resolved i.e., data storage of nodes in WSN [3]. The users are highly concerned about the perception of data than the Sensor Node (SN) and the networks it is made up of. Moreover, WSN system helps in dependable and effective data storage and accessibility over a variety of atmospheres that are mostly unreliable. Storage level and energy consumption of every SN are restricted up to certain limit. So, efficient data storage under storage constraints has become a significant research area in WSN data management. Fig. 1 illustrates the structure of blockchain in WSN.

Figure 1: Blockchain in WSN
Clustering is a main technique applied in achieving lengthy network lifespan. In this process, the sensors are grouped into groups of clusters while a leader i.e., Cluster Head (CH) is selected for every group [4]. Data aggregation, in connection with Compressive Sensing (CS), is different from other approaches since the key objective is to minimize data communication and attain superior power efficiency. In the study conducted earlier [5], Plain-CS was positioned with random sparse projection and hybrid-CS so as to restrict the energy consumption of sensors to a large extent. These models are appropriate for minimizing complete network communication cost. On the other hand, it also recognizes the grouping of routing principles which possesses data aggregation characteristics that tend to increase network’s effectiveness [6]. This method considers ‘power efficiency’ as a basic demand due to power restraints in nodes. Afterwards, minimizing energy consumption and sustaining power efficacy are considered as important problems.
Security menace is one of the most important problems found in WSNs. Since SNs have resource-constraints, they are prone to attacks in a simple manner [7]. In general, WSNs face two kinds of attacks such as physical attacks and internal attacks. In physical attacks, the aggressors have full control over the SNs to perform malevolent actions. In case of internal attacks, SNs act in a selfish manner to preserve its power and memory. So, it becomes highly essential to recognize and eradicate the malignant sensors from the network [8]. Blockchain (BC) technology is the only choice to resolve these problems as discussed above. In this technique, smart contracts are presented in which every agreement is framed in the system. It is an efficient method to maintain a database of transactions amongst various groups [9]. As BC is unchallengeable, it is not possible to tamper the data. In BC, the transaction data remains safe since the blocks are connected by hashes [10].
Sanchez et al. [11] projected a decentralized model to ensure both autonomy and security of IoT model. The presented technique can be utilized for the protection of data integrity and accessibility based on the security benefits provided by BC technique and by using cryptographic tools. The accuracy of the presented technique was evaluated on temperature and humidity sensors on Internet of Things (IoT)-based WSN. She et al. [12] examined a BC Trust Model (BTM) for malicious node detection in WSNs. Primarily, the proposed model offers the entire structure of the trust model. Next, it generates the BC data structure that is utilized in the detection of malicious nodes. At last, it recognizes the malicious nodes from 3D space with the help of BC smart contracts and WSN quadrilateral measurement localization approach.
In the study conducted earlier [13], a BC-based decentralized structure was established in combination with authentication and privacy preserving methods to secure data transmission from WSN-allowed IoTs. Registration, certification, and revocation procedures were utilized for the transmission of data between SN and Base Station (BS) in Cloud Computing (CC) environment. In literature [14], a novel effectual authentication method was proposed for WSNs using BC technique so as to accomplish security. The nodes, present in WSNs, form the IoT network which are expressed as BS, CHs, and normal SN. The structure of a BC network is shaped by a hierarchical BC method that contains small chain and global chain amongst many network nodes. Rahman et al. [15–17] established a layered hierarchical structure to be utilized upon distributed-yet-effectual BC-allowed SDN-IoT structure. This structure ensures effective CH selection and secure network transmission using identification and isolation of rouge switches.
The current study develops an Energy Aware Chaotic Pigeon Inspired Optimization based Clustering Scheme for Blockchain Assisted WSN abbreviated as EACPIO-CB technique. The primary intention of the proposed EACPIO-CB model is to proficiently group the SNs into clusters and exploit BC for inter-cluster communication in the network. To select the CHs and organize the clusters, the presented EACPIO-CB model designs a Fitness Function (FF) with distinct input parameters. In addition, BC technology enables communication between one CH and the other and with the BS in the network. The researchers conducted comprehensive set of simulations and the outcomes were examined under different aspects.
Rest of the study is planned as follows. Section 2 elaborates the proposed model and Section 3 validates the performance of the proposed model. At last, Section 4 draws the concluding remarks.
In this article, a new EACPIO-CB method has been developed to attain security and energy efficiency in WSN. The aim of the proposed EACPIO-CB model is to proficiently group the SNs into clusters and exploit BC for inter-cluster communication in the network. Fig. 2 showcases the block diagram of EACPIO-CB technique.

Figure 2: Overall block diagram of EACPIO-CB technique
2.1 Overview of CPIO Algorithm
PIO approach is a meta-heuristic algorithm that is simulated based on pigeon returning behaviour [18]. The pigeon detects its nest with elements that support its returning such as magnetic field, sun, and landmarks. It can affect the path of entire population. Then, the nearby landmarks assist the pigeons to fly nearby the end of the path. In order to mimic the natural activity of pigeons returning to nest, PIO approach employs two operatives to describe the clustering nature of pigeons. In PIO mode, compass and map operators from the primary stage signify the impact of magnetic field and sun once the landmark operators, in the resulting stage, outline the effect of landmarks on returning home.
When the entire flock is initiated, the amount of pigeons is denoted by
During compass and map operators phase, the entire pigeon population provides a strong global searching ability which professionally prevents the solution from falling into local optima issue.
The original position and the speed of the flock to upgrade the line of attack are as follows.
In the abovementioned equation,
Eq. (5) shows the velocity update formula of Particle Swarm Optimization (PSO) model i.e., the migrant direction of the swarming bird. Eq. (4) is the speed upgrading formula for PIO which simulates the home returning nature of pigeons. The upgraded formula for speed is given in the first stage [19]. In comparison with PSO algorithm, no individual optimal effects exist while there is a strong global searching ability available for the prevention of problems of falling under local optima.
Initially, the population needs to eliminate the pigeons that do not have a direction which they can recognize. Further, the population also should consider the pigeons that prevent them from influencing the iteration path of population as represented in the equation given below. Then, the pigeon is selected based on each leadership from the population as represented in the following equation. At last, the pigeon that results from the entire population is repeated as follows.
In this equation,
In order to enhance the efficacy of PIO approach, chaotic dynamics are integrated to derive the CPIO technique. Because it offers a uniform distribution within [0,1] while the tent mapping illustrates high advantages and heavy iterative speed than the logistic mapping process [20]. Tent map is used to calculate the dynamical systems, since it has different characteristics like simple shape, chaotic orbits, etc. Here, tent mapping is applied to generate the chaos parameter while the tent map can be defined as given below.
Here,
Here,
Chaotic map initiates the swarming of PIO. According to chaotic searching process, chaotic disturbance encompassess
Here,
2.2 Processes Involved in EACPIO-CB Model
The presented EACPIO-CB model designs a FF involving distinct input parameters. The main concept of the proposed EACPIO-CB algorithm on CH selection is to decrease the distance between the selected nodes and CH. Further, it also focuses on reducing the timeline delay to transmit the information from one node to another. On the contrary, network energy has to be higher, i.e., during data transmission, it needs to employ a small amount of energy. At last, the node must tolerate the risks present in the network. The objective function of the adapted CH is demonstrated using Eq. (16), while the value of
Eq. (19) portrays the FF for distance wherein
Eq. (22) details about the FF of energy. The value
The FF of delay
2.3 BC Enabled Inter-Cluster Communication
In this work, BC technology enables communication between one CH and the other and between one CH and BS in the network. In general, BC is hypothesized as a group of blocks; and those blocks contain hash values of the existing blocks, dataset about the transaction (Ethereum, bitcoin), timestamp, and previous block. Furthermore, BC is determined by a common and distributed digital ledger that is employed to store the transaction data under different points. Thus, when attackers attempt to acquire the dataset, it is not possible for them to do so, since each and every block has a cryptographic value of the preceding block. Now, each transaction is performed under the application of cryptographic hash values i.e., confirmed by all the miners. It is taken by the same value of a comprehensive ledger and is encompassed by the block of each transaction. BC offers the capability to share the ledger information in a protective, shared, and private manner. Decentralized storage is an alternative method offered by BC in which huge volumes of information are linked and stored from the present blocks to preceding blocks using a smart contract code. LitecoinDB, Swarm, Interplanetary File System (IPFS), MoneroDB, SiacoinDB, BigchainDB, etc., are employed for decentralized datasets.
The current section deals with experimental validation of the proposed EACPIO-CB model under distinct aspects. Tab. 1 and Fig. 3 shows the PDR analysis results achieved by the proposed EACPIO-CB approach and other recent models such as Red Deer Algorithm (RDA), Genetic Algorithm (GA), Ant Lion Algorithm (ALO), Grey Wolf Algorithm (GWO) and PSO [21]. The results highlight that the proposed EACPIO-CB approach accomplished enhanced PDR values under different number of SNs. For sample, with 100 SNs, the proposed EACPIO-CB model offered a high PDR of 99.43%, while RDA, GA, ALO, GWO, and PSO systems obtained low PDR values such as 97.82%, 96.23%, 94.82%, 93.32%, and 91.07% respectively. Moreover, with 500 SNs, the proposed EACPIO-CB model offered a high PDR of 97.24%, while RDA, GA, ALO, GWO, and PSO methodologies achieved low PDR values such as 96.37%, 94.70%, 92.60%, 90.32%, and 89.42% correspondingly.
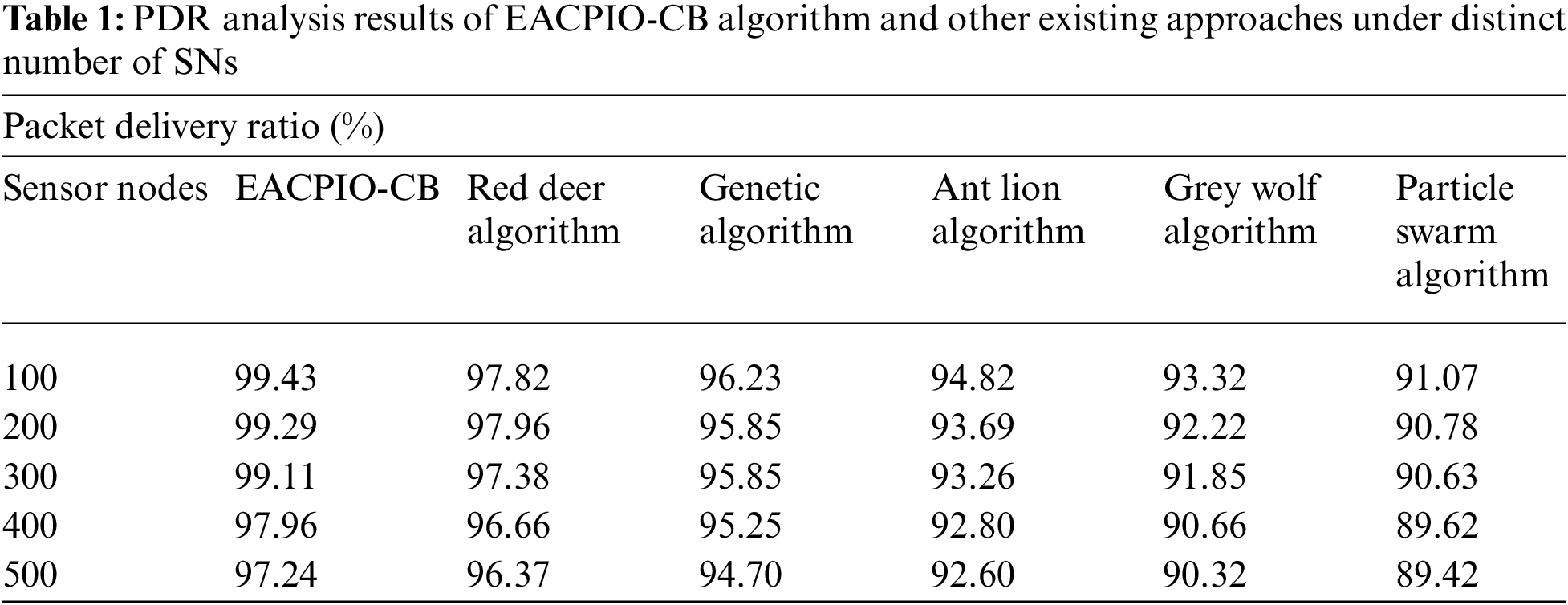

Figure 3: PDR analysis results of EACPIO-CB technique under distinct number of SNs
Comparative Packet Loss Rate (PLR) analysis was conducted between EACPIO-CB model and other existing models and the results are shown in Tab. 2 and Fig. 4. The experimental outcomes imply that the proposed EACPIO-CB technique produced effectual outcomes with low PLR values under all the instances. For instance, with 100 SNs, the proposed EACPIO-CB system attained a minimal PLR of 0.57%, whereas RDA, GA, ALO, GWO, and PSO models demonstrated maximum PLR values such as 2.18%, 3.77%, 5.18%, 6.68%, and 8.93% correspondingly. Also, with 500 SNs, the proposed EACPIO-CB system depicted a minimal PLR of 2.76%, whereas RDA, GA, ALO, GWO, and PSO techniques established maximum PLR values such as 3.63%, 5.30%, 7.40%, 9.68%, and 10.58% correspondingly.


Figure 4: PLR analysis results of EACPIO-CB algorithm under different number of SNs
Tab. 3 and Fig. 5 shows the Throughput (THPT) examination results attained by the proposed EACPIO-CB method and other recent methodologies. The results highlight that EACPIO-CB approach accomplished high THPT values under distinct number of SNs. For instance, with 100 SNs, the proposed EACPIO-CB model offered a high THPT of 98.35%, while RDA, GA, ALO, GWO, and PSO systems obtained the least THPT values such as 89.92%, 86.55%, 79.39%, 74.54%, and 53.26% respectively. Eventually, with 500 SNs, the presented EACPIO-CB method offered an increased THPT of 81.92%, whereas RDA, GA, ALO, GWO, and PSO algorithms obtained minimal THPT values such as 71.80%, 61.90%, 47.15%, 38.30%, and 30.51% respectively.


Figure 5: Throughput analysis results of EACPIO-CB algorithm under different number of SNs
Comparative Energy Consumption (ECM) investigation was conducted between EACPIO-CB method and other existing models and the results are shown in Tab. 4 and Fig. 6. The experimental outcomes denote that the proposed EACPIO-CB model produced effectual outcomes with the least values of ECM. For instance, with 100 SNs, EACPIO-CB system achieved a low ECM of 0.02 mJ, whereas RDA, GA, ALO, GWO, and PSO models attained high ECM values such as 0.04, 0.05, 0.07, 0.09, and 0.15 mJ correspondingly. At last, with 500 SNs, the proposed EACPIO-CB method accomplished a minimum ECM of 0.34 mJ, whereas RDA, GA, ALO, GWO, and PSO models demonstrated maximum ECM values such as 0.52, 0.65, 0.79, 0.88, and 0.97 mJ correspondingly.


Figure 6: ECM analysis results of EACPIO-CB algorithm under different number of SNs
Tab. 5 and Fig. 7 portrays the Network Lifetime (NLT) analysis results accomplished by the proposed EACPIO-CB system and other recent models. The results highlight that the proposed EACPIO-CB system accomplished improved NLT values under different number of SNs. For sample, with 100 SNs, the proposed EACPIO-CB model offered a superior NLT of 1881 rounds, while RDA, GA, ALO, GWO, and PSO techniques obtained lesser NLT values such as 1684, 1621, 1527, 1393, and 1280 rounds correspondingly. Likewise, with 500 SNs, the proposed EACPIO-CB model achieved a high NLT of 3920 rounds, whereas RDA, GA, ALO, GWO, and PSO methodologies obtained minimal NLT values such as 3821, 3787, 3566, 3440, and 3120 rounds correspondingly.


Figure 7: NLT analysis results of EACPIO-CB algorithm under distinct number of SNs
Tab. 6 shows the Number of Alive Sensor Nodes (NOASN) analysis results achieved by the proposed EACPIO-CB model and other recent techniques. The outcomes highlight that the proposed EACPIO-CB approach accomplished high NOASN values under varying number of rounds. For instance, with 400 rounds, the presented EACPIO-CB system obtained the maximum NOASN of 500, whereas RDA, GA, ALO, GWO, and PSO algorithms attained low NOASN values such as 491, 471, 430, 401, and 372 correspondingly.

Furthermore, with 3200 rounds, the proposed EACPIO-CB system offered a high NOASN of 341, whereas RDA, GA, ALO, GWO, and PSO algorithms obtained the least NOASN values such as 289, 251, 172, 38, and 13 correspondingly.
In current study, a novel EACPIO-CB technique has been developed to attain security and energy efficiency in WSN. The aim of the proposed EACPIO-CB model is to proficiently group the SNs into clusters and exploit BC for inter-cluster communication in the network. To choose the CHs and organize the clusters, the presented EACPIO-CB model designs an FF that involves distinct input parameters. In addition, BC technology enables communication between one CH and the other and with BS in the network. The researchers conducted a comprehensive set of simulations and the outcomes were examined under different aspects. The simulation outcomes established the superior performance of the proposed EACPIO-CB technique on recent approaches. In future, multi-hop route planning scheme can also be developed to improve energy efficiency outcomes.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Large Groups Project under grant number (142/43). Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R238), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4340237DSR24).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Z. Cui, F. Xue, S. Zhang, X. Cai, Y. Cao et al., “A hybrid blockchain-based identity authentication scheme for multi-wsn,” IEEE Transactions on Services Computing, vol. 13, no. 2, pp. 241–251, 2020. [Google Scholar]
2. S. Arjunan and P. Sujatha, “Lifetime maximization of wireless sensor network using fuzzy based unequal clustering and ACO based routing hybrid protocol,” Applied Intelligence, vol. 48, no. 8, pp. 2229–2246, 2018. [Google Scholar]
3. Y. Ren, Y. Liu, S. Ji, A. K. Sangaiah and J. Wang, “Incentive mechanism of data storage based on blockchain for wireless sensor networks,” Mobile Information Systems, vol. 2018, pp. 1–10, 2018. [Google Scholar]
4. S. Arjunan and P. Sujatha, “A survey on unequal clustering protocols in wireless sensor networks,” Journal of King Saud University - Computer and Information Sciences, vol. 33, no. 1, pp. 118, 2021. [Google Scholar]
5. S. Famila, A. Jawahar, A. Sariga and K. Shankar, “Improved artificial bee colony optimization based clustering algorithm for SMART sensor environments,” Peer-to-Peer Networking and Applications, vol. 13, no. 4, pp. 1071–1079, 2020. [Google Scholar]
6. S. Verma, S. Kaur, R. Manchanda and D. Pant, “Essence of blockchain technology in wireless sensor network: A brief study,” in 2020 Int. Conf. on Advances in Computing, Communication & Materials (ICACCM), Dehradun, India, pp. 394–398, 2020. [Google Scholar]
7. S. Arjunan, S. Pothula and D. Ponnurangam, “F5 N-based unequal clustering protocol (F5NUCP) for wireless sensor networks,” International Journal of Communication Systems, vol. 31, no. 17, pp. e3811, 2018. [Google Scholar]
8. R. C. Vara, J. Prieto and J. M. Corchado, “How blockchain could improve fraud detection in power distribution grid,” in The 13th Int. Conf. on Soft Computing Models in Industrial and Environmental Applications, Advances in Intelligent Systems and Computing Book Series, Springer, Cham, vol. 771, pp. 67–76, 2018. [Google Scholar]
9. S. Amjad, S. Abbas, Z. Abubaker, M. Alsharif, A. Jahid et al. “Blockchain based authentication and cluster head selection using DDR-leach in internet of sensor things,” Sensors, vol. 22, no. 5, pp. 1972, 2022. [Google Scholar]
10. D. Sivaganesan, “A data driven trust mechanism based on blockchain in IoT sensor networks for detection and mitigation of attacks,” Journal of Trends in Computer Science and Smart Technology (TCSST), vol. 3, no. 1, pp. 59–69, 2021. [Google Scholar]
11. A. E. G. Sanchez, E. A. R. Araiza, J. L. G. Cordoba, M. T. Ayala and A. Takacs, “Blockchain mechanism and symmetric encryption in a wireless sensor network,” Sensors, vol. 20, no. 10, pp. 2798, 2020. [Google Scholar]
12. W. She, Q. Liu, Z. Tian, J. S. Chen, B. Wang et al. “Blockchain trust model for malicious node detection in wireless sensor networks,” IEEE Access, vol. 7, pp. 38947–38956, 2019. [Google Scholar]
13. R. Goyat, G. Kumar, R. Saha, M. Conti, M. K. Rai et al., “Blockchain-based data storage with privacy and authentication in internet-of-things,” IEEE Internet Things Journal, pp. 1–1, 2020, https://doi:10.1109/JIOT.2020.3019074. [Google Scholar]
14. A. Mubarakali, “An efficient authentication scheme using blockchain technology for wireless sensor networks,” Wireless Personal Communications, 2021, https://doi.org/10.1007/s11277-021-08212-w. [Google Scholar]
15. A. Rahman, M. J. Islam, A. Montieri, M. K. Nasir, M. M. Reza et al., “SmartBlock-SDN: An optimized blockchain-sdn framework for resource management in IoT,” IEEE Access, vol. 9, pp. 28361–28376, 2021. [Google Scholar]
16. M. A. A. Almekhlafi, T. A. Elfadil Eisa, F. N. Al-Wesabi, A. Abdelmaboud, M. A. Hamza et al., “Efficiency effect of obstacle margin on line-of-sight in wireless networks,” Computers, Materials & Continua, vol. 72, no. 1, pp. 227–242, 2022. [Google Scholar]
17. F. N. A. Wesabi, M. Obayya, M. Hamza, J. S. Alzahrani, D. Gupta et al., “Energy aware resource optimization using unified metaheuristic optimization algorithm allocation for cloud computing environment,” Sustainable Computing: Informatics and Systems, vol. 35, 2022. [Google Scholar]
18. H. Duan and X. Wang, “Echo state networks with orthogonal pigeon-inspired optimization for image restoration,” IEEE Transactions on Neural Networks and Learning Systems, vol. 27, no. 11, pp. 2413–2425, 2016. [Google Scholar]
19. Z. Cui, J. Zhang, Y. Wang, Y. Cao, X. Cai et al., “A Pigeon-inspired optimization algorithm for many-objective optimization problems,” Science China Information Sciences, vol. 62, no. 7, pp. 70212, 2019. [Google Scholar]
20. J. Zhao, H. Duan, L. Chen and M. Huo, “Leadership hierarchy-based formation control via adaptive chaotic pigeon-inspired optimization,” IFAC-PapersOnLine, vol. 53, no. 2, pp. 9348–9353, 2020. [Google Scholar]
21. G. N. Nguyen, N. H. Le Viet, A. F. S. Devaraj, R. Gobi and K. Shankar, “Blockchain enabled energy efficient red deer algorithm based clustering protocol for pervasive wireless sensor networks,” Sustainable Computing: Informatics and Systems, vol. 28, pp. 100464, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |