| Computers, Materials & Continua DOI:10.32604/cmc.2022.031887 |  |
| Article |
Feature Selection with Stacked Autoencoder Based Intrusion Detection in Drones Environment
1Department of Electrical Engineering, College of Engineering, Princess Nourah Bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
2Department of Information Systems, College of Computing and Information System, Umm Al-Qura University, Saudi Arabia
3Department of Information Systems, College of Science & Art at Mahayil, King Khalid University, Saudi Arabia
4Department of Computer Science, Faculty of Computers and Information Technology, Future University in Egypt, New Cairo, 11835, Egypt
5Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam Bin Abdulaziz University, AlKharj, Saudi Arabia
*Corresponding Author: Manar Ahmed Hamza. Email: Ma.hamza@psau.edu.sa
Received: 29 April 2022; Accepted: 02 June 2022
Abstract: The Internet of Drones (IoD) offers synchronized access to organized airspace for Unmanned Aerial Vehicles (known as drones). The availability of inexpensive sensors, processors, and wireless communication makes it possible in real time applications. As several applications comprise IoD in real time environment, significant interest has been received by research communications. Since IoD operates in wireless environment, it is needed to design effective intrusion detection system (IDS) to resolve security issues in the IoD environment. This article introduces a metaheuristics feature selection with optimal stacked autoencoder based intrusion detection (MFSOSAE-ID) in the IoD environment. The major intention of the MFSOSAE-ID technique is to identify the occurrence of intrusions in the IoD environment. To do so, the proposed MFSOSAE-ID technique firstly pre-processes the input data into a compatible format. In addition, the presented MFSOSAE-ID technique designs a moth flame optimization based feature selection (MFOFS) technique to elect appropriate features. Moreover, firefly algorithm (FFA) with stacked autoencoder (SAE) model is employed for the recognition and classification of intrusions in which the SAE parameters are optimally tuned with utilize of FFA. The performance validation of the MFSOSAE-ID model was tested utilizing benchmark dataset and the outcomes implied the promising performance of the MFSOSAE-ID model over other techniques with maximum accuracy of 99.72%.
Keywords: Internet of drones; unmanned aerial vehicles; security; intrusion detection; machine learning
The Internet of Drones (IoD) is a layered network control structure devised for organizing the accessibility of several Unmanned Aerial Vehicles (UAVs) (called drones) for controlling airspace and offering navigation facilities [1]. The IoD renders several amenities for drone applications extending from military to civilian application areas, involving rescue and search operations, aerial surveys delivery services, environment, and traffic monitoring. The IoD is being familiar day after day due to its services and guidance to the community [2]. Every drone is fortified with computing unit, transmission module, recorder, sensors and actuators, and energy supply unit [3]. The default sensor nodes in the drone mean the physical criteria, namely concentration and temperature of harmful gases, and the camera which is built-into the UAV captures the images or records videos of the target and forwards every sensing monitored data to drone box through few wireless transmission technologies, like WiFi [4,5]. Every UAV box is linked to the server, server that is linked to control room. The UAVs are microcosm of the Internet of Things (IoT). For technology leaders and businesses to understand the capability of drones in their institutions, a quantity of general IoT-based product engineering difficulties occurs to beat these [6]. Fig. 1 depicts the applications of IoD.
Figure 1: Applications of IoD
Currently, network security is becoming a crucial research field, specifically after advancing transmission and Internet methods. It makes use of various tools like Network Intrusion Detection Systems (NIDSs) and firewalls for security purposes of assets and networks [7]. For monitoring the network traffic for suspicious and worse conduct permanently NIDSs are commonly utilized. IDSs can be divided into three type’s signature-related specification-related or anomaly-related, methods [8]. Anomaly-related approaches can be again categorized as statistical-related, knowledge-related, or machine learning-related [9]. The attack is the distraction among the 2 statistical paradigms they are the current captured and the normal memorized. In knowledge-related anomaly recognition, specialists present more rules in the standard of a fuzzy-related system or expert system for explaining the conduct of usual attacks and connections. The rule-related system is linked to input unit in fuzzy-related anomaly recognition [10]. On the basis of the input data, a subset of the rules is started. In a machine learning-related anomaly IDS, an implicit or explicit algorithm of the observed outlines is formed. Depending on earlier outcomes, these methods are upgraded on a day-to-day basis for enhancing intrusion detection efficiency.
Ouiazzane et al. [11] presented a model dependent upon Muli-Agent System and on ML approaches for detecting Denial of Service (DoS) cyberattacks aiming at the network of drones. The presented method was autonomous, considered by their higher performance, and allows the recognition of known and unknown DoS attacks from UAV networks with higher accuracy and minimal false negative rate (FNR) and false positive rate (FPR). Condomines et al. [12] present a novel IDS, a hybrid technique dependent upon both spectral traffic analysis and robust controlling or observing to anomaly estimate inside UAV network. The presented hybrid technique assumes, as an initial step, a statistical signature of traffic replaced from the networks. With investigative the resulted signature, the variances were utilized for selecting the accurate method to accurate estimation abnormal traffics. Perumalla et al. [13] present a novel approach for secure broadcast from IoD by effectual blockchain (BC) supported access control and ID technique utilizing the recently devised Deep Neuro-Fuzzy Network model. Classically, BC based access control contains mostly 4 stages such as authentication, pre-deployment, access control, and registration stages to transfer the vital data from the IoD environments. Sharma et al. [14] execute the novel functional encryption (FE) approach from the presented UAV supported HetNet method for the dense urban area for securing data against such intrusion. During this network method, UAV performances as relay node to individuals UE that are in non-line-of-sight (NLoS) transmission with macro based station (MBS). Ouiazzane et al. [15–18] present novel methods of IDS to a fleet of UAVs used with ad hoc communication structures. The security of drone fleet was rarely discussed by the scientific community, and one of the research is concentrated on routing protocol and battery autonomy, but ignored the security feature.
This article introduces a metaheuristics feature selection with optimal stacked autoencoder based intrusion detection (MFSOSAE-ID) in the IoD environment. The proposed MFSOSAE-ID technique firstly pre-processes the input data into a compatible format. In addition, the presented MFSOSAE-ID technique designs a moth flame optimization based feature selection (MFOFS) technique to elect appropriate features. Moreover, firefly algorithm (FFA) with stacked autoencoder (SAE) model is employed for the recognition and classification of intrusions in which the SAE parameters are optimally tuned by the use of FFA. The performance validation of the MFSOSAE-ID model is tested using benchmark dataset.
In this study, a new MFSOSAE-ID technique has been developed to determine the existence of intrusions in the IoD environment. The proposed MFSOSAE-ID technique firstly pre-processes the input data into a compatible format. Followed this, the presented MFSOSAE-ID technique designs an MFOFS technique to elect appropriate features. In line with, the FFA-SAE model is employed for the recognition and classification of intrusions. Fig. 2 illustrates the overall process of MFSOSAE-ID technique.
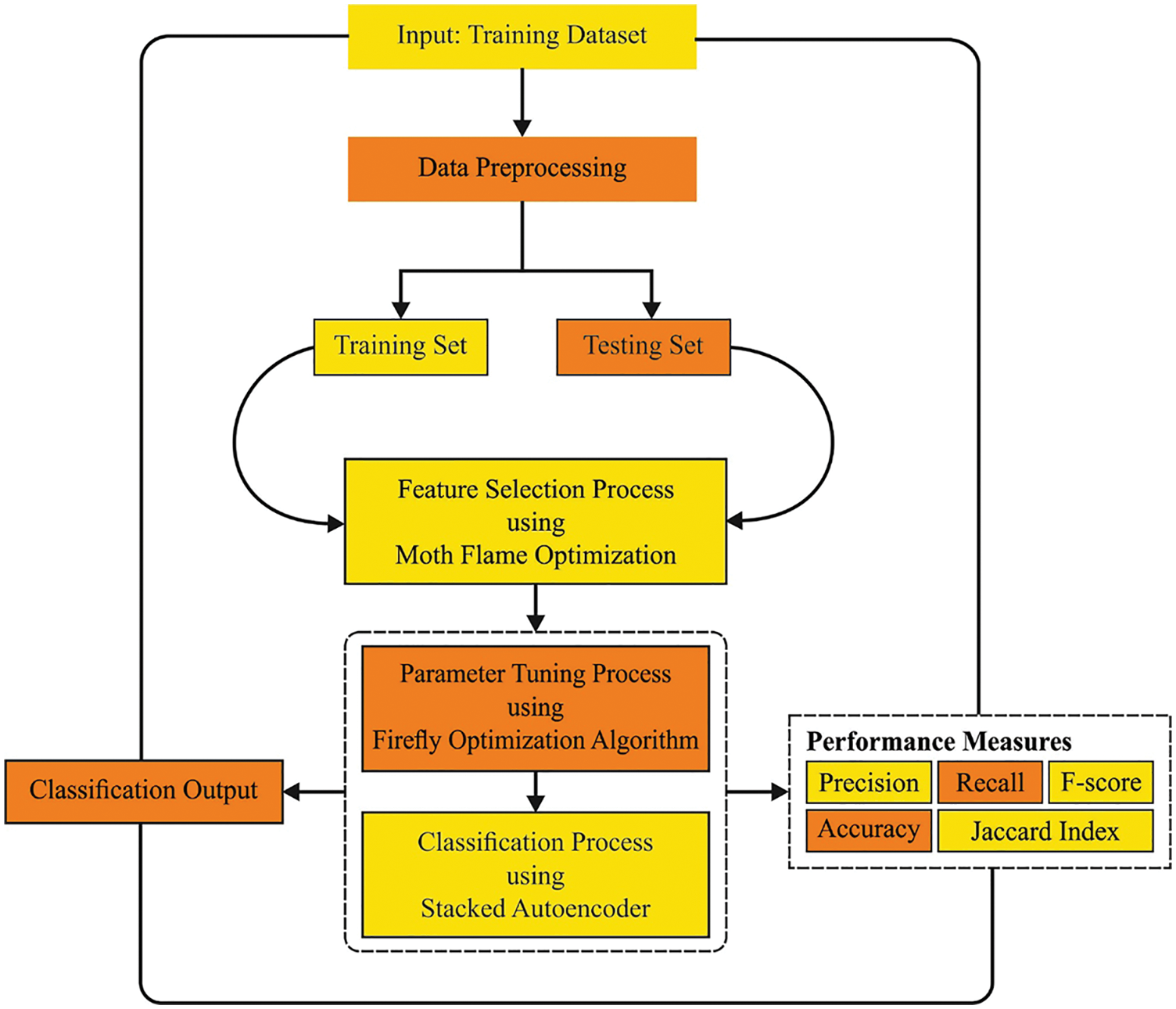
Figure 2: Overall process of MFSOSAE-ID technique
The proposed MFSOSAE-ID technique firstly pre-processes the input data into a compatible format. In a primary phase, the z-score normalized system was developed that estimates the standard deviation (SD) and arithmetic mean of offered gene information. The normalized score reaches were offered in the subsequent:
whereas
2.2 Steps Involved in MFOFS Technique
Next to data pre-processing, the presented MFSO. The MSO procedure is based on the procedure of selecting optimum discriminatory characteristics of mitosis cells. Usually, Moth is a bug which belongs to the family of butterflies named Lepidoptera. About 160,000 moth classes appear worldwide, and it is noticeable during nighttime. With the comparison of moth and alternative species, Levy flight (LF) and phototaxis are found to be significant.
Phototaxis
The fundamental concept of the moth is that; it frequently moves toward the light called phototaxis. There is no precise technique for phototaxis and is comprised of the primary hypotheses to determine the phototaxis method. After that, it is intended to be a substantial hypothesis in the celestial orientation that is implemented in transverse direction during the flying period. Simultaneously, the angle is initiated by the source of light and the moth is directed, but, it is not relevant to obtain the transformation, since the celestial object is considered an external distance. Therefore, it travels to the light, because the moth creates flight direction for gaining the optimal position [19]. A spiral-path was established to approach the light.
Levy flight
Heavy-tailed, non-Gaussian statistics are inspected in traditional ways in variety of applications. On the other hand, Drosophila signifies a Levy flight, but, the flight is evaluated by energy source with features exponent with 3/2. In general, the process can be formulated by,
Now
Fundamentally, moths have the property close to optimum one and fly in an LF method. Otherwise, it instructed the location and employs LF using the below formula, but, moth is maintained by the following equation:
Here,
Next,
In
Learning feature presentation from each three dimensional is considerable for biomarker predictive process from volumetric medical dataset. Nevertheless, it is predictable to employ three dimensional convolutional kernels, from the point of encoded volumetric and spatial datasets. In the comparable volumetric image size of
Here,
Fly straight
The existing moth is detached from light that flusters in straight line towards light. The function of moth
In the Eq. (8),
Otherwise, moth moves out from light source to concluding location. Therefore, the last position of moth
For reliability, the position of moth j is maintained by partial proportion. The best, original, and refreshed position of moth is evaluated by
The MFO purposes for discovering an optimum feature subset to offered dataset which is superior classifier accuracy and lesser features. All these 2 indicators are varying effects on classifier accuracy. At this point, it can be combined with a single weight indicator and use the same fitness function as:
In which,
2.3 SAE Based Intrusion Detection
Next to FS process, the SAE model is employed for the recognition and classification of intrusions in the IoD environment [20]. The hidden layer
whereas
In which
whereas
The AEs are superimposed layer-by-layer for procedure a deep neural network (DNN); i.e., all the hidden layers are obtained as the input of next layer that is progressive still the trained procedure was ended. The introduction of batch normalization (BN) is established as easy primary criterion to train SAE that creates the gradient upgrade in a very shallow path, speeding up the trained method. The labeled signal is bonded with softmax classification, and back propagation (BP) technique was executed for realizing the upgrade of network weighted and fine-tuning of parameters.
2.4 Steps Involved in FFA Based Parameter Optimization
Finally, the SAE parameters are optimally tuned [21–23] by the use of FFA with the fitness function of accomplishing maximum accuracy [24]. FFA was stimulated by the patterns of fireflies (FFs) and flashing behavior in nature. FFA is a meta-heuristic process based on nature and employed in most of the Np-hard and engineering optimization problems. It is a stochastic method. Specifically, random searching is utilized for finding a collection of solutions. At basic levels, the FFA focuses on making solutions within a searching region and chooses the optimal survival solutions. An arbitrary search prevents it from falling into local optimal. In metaheuristic algorithms, exploration refers to determining several solutions within the searching region, whereas exploitation refers to the searching procedure that aims at the optimal nearby solution. The mode and rate of brightness and the time intervals among the transmitted optical signal attract the two sexes to one another. The light intensity I, reduces by rising distance (R) from the light. In the following, the key characteristics of the FFA are given:
The FF movement and attractiveness towards a brighter one is defined as follows:
In Eq. (15),

The experimental validation of the MFSOSAE-ID model is tested using the benchmark UNSW-NB15 dataset [25]. It includes a set of 82332 samples with 10 class labels. The details related to the dataset are given in Tab. 1. The results are executed for four distinct runs. Fig. 3 highlights four confusion matrices offered by the MFSOSAE-ID model on the test UNSW-NB15 dataset. The figure pointed out that the UNSW-NB15 dataset has proficiently recognized all ten class labels under four distinct runs.
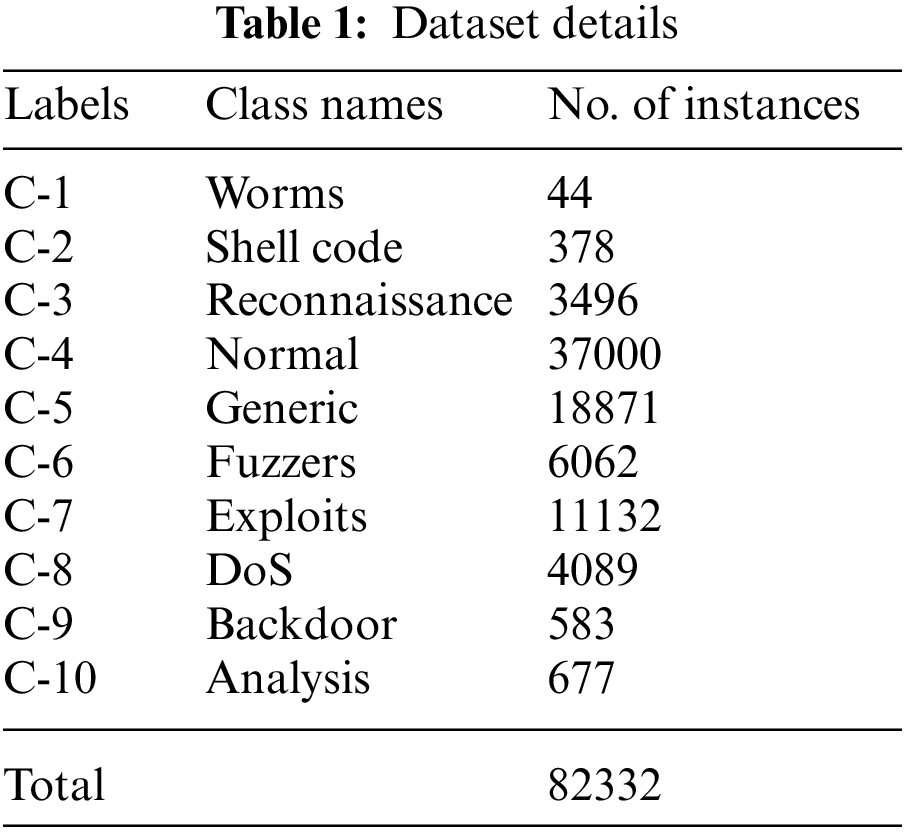
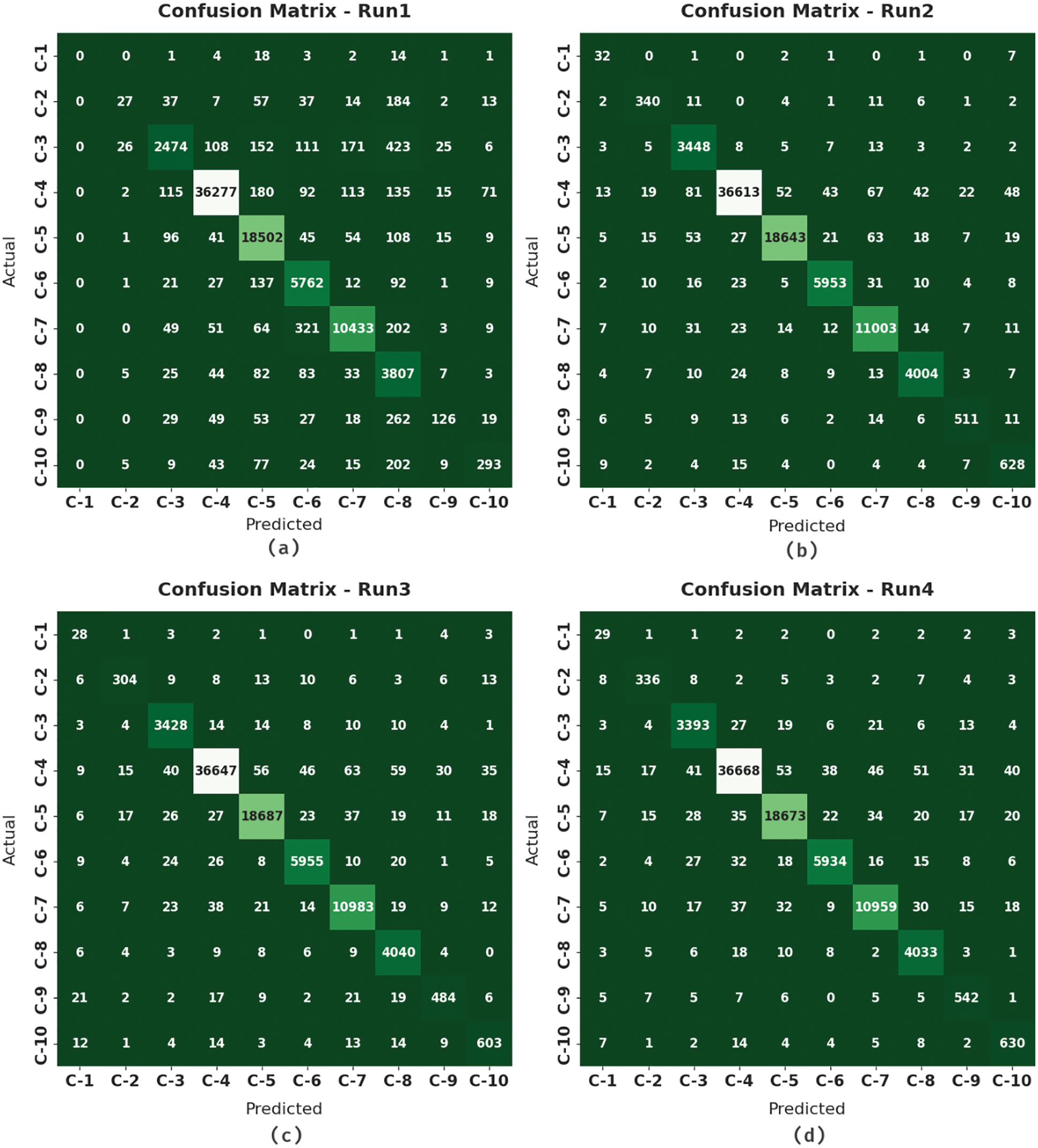
Figure 3: Confusion matrices of MFSOSAE-ID technique (a) run-1, (b) run-2, (c) run-3, and (d) run-4
Tab. 2 demonstrates the classification results offered by the MFSOSAE-ID model on UNSW-NB15 dataset under run-1. The results implied that the MFSOSAE-ID model has resulted in enhanced classifier results under all ten classes. For instance, with class C-3, the MFSOSAE-ID model has provided
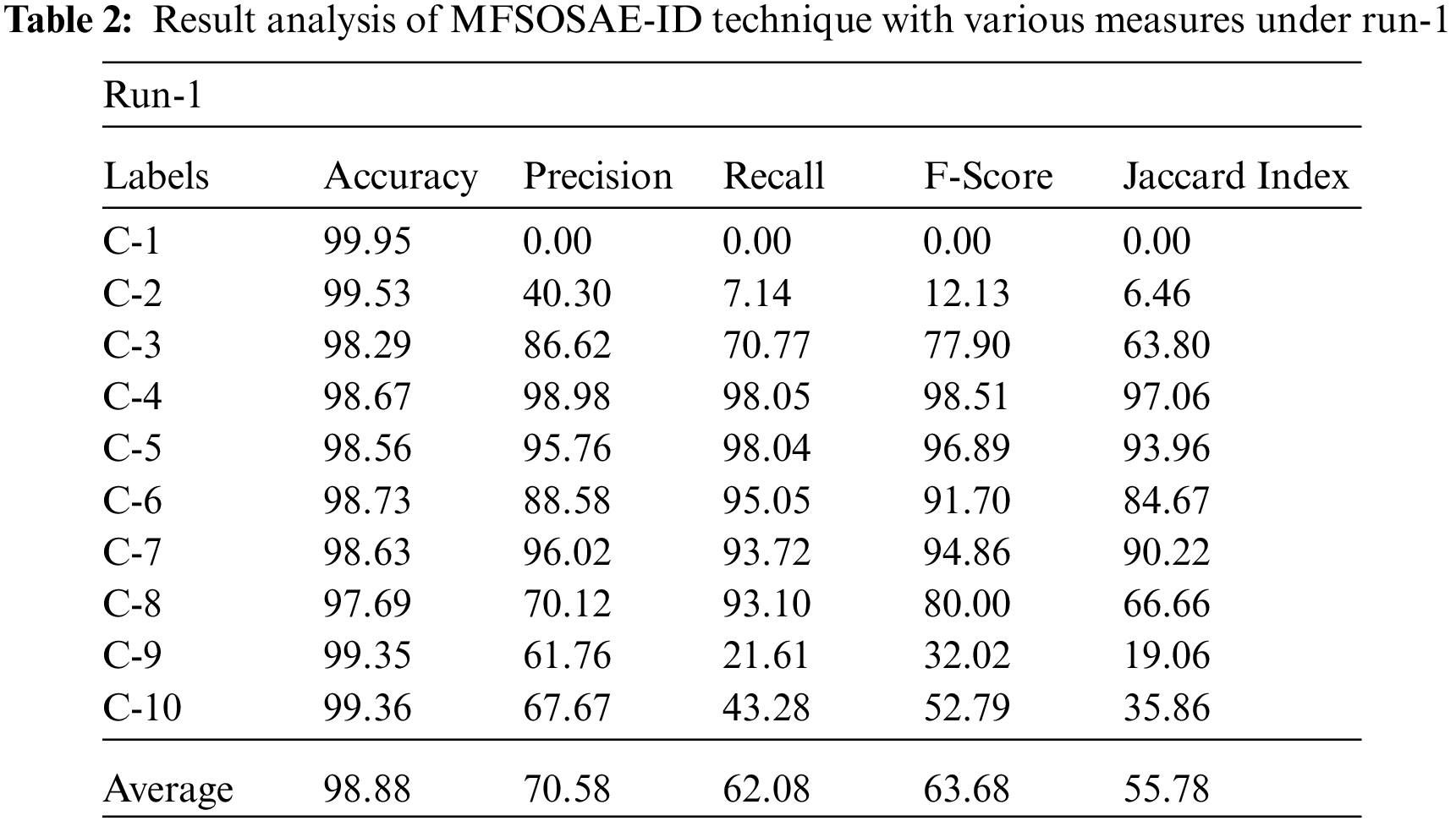
Tab. 3 depicts the classification results presented by the MFSOSAE-ID technique on UNSW-NB15 dataset under run-2. The outcomes implied that the MFSOSAE-ID model has resulted in improved classifier results under all ten classes. For instance, with class C-3, the MFSOSAE-ID system has provided
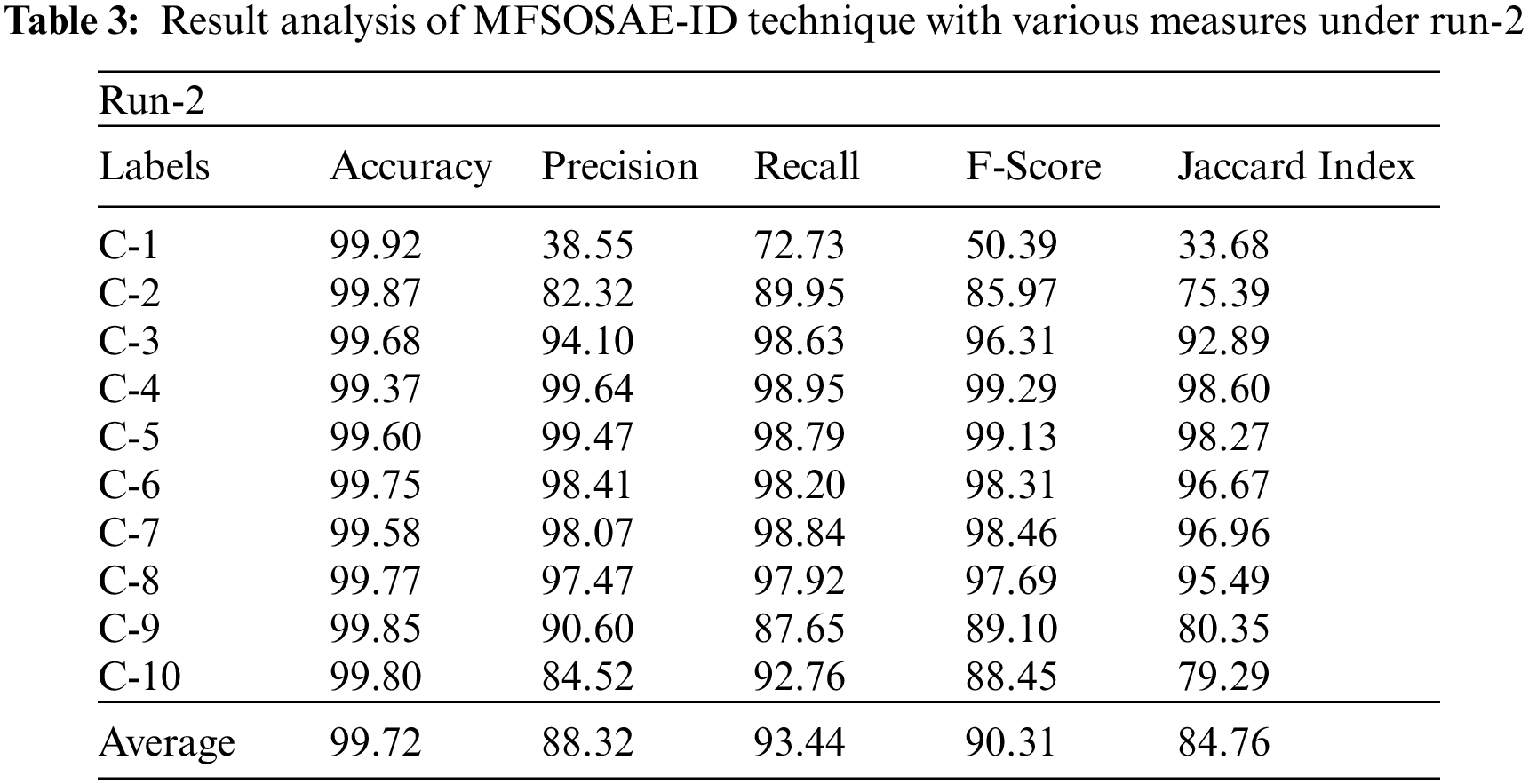
Tab. 4 depicts the classification results obtainable by the MFSOSAE-ID approach on UNSW-NB15 dataset under run-3. The outcomes exposed that the MFSOSAE-ID methodology has resulted in higher classifier results under all ten classes. For instance, with class C-3, the MFSOSAE-ID system has provided
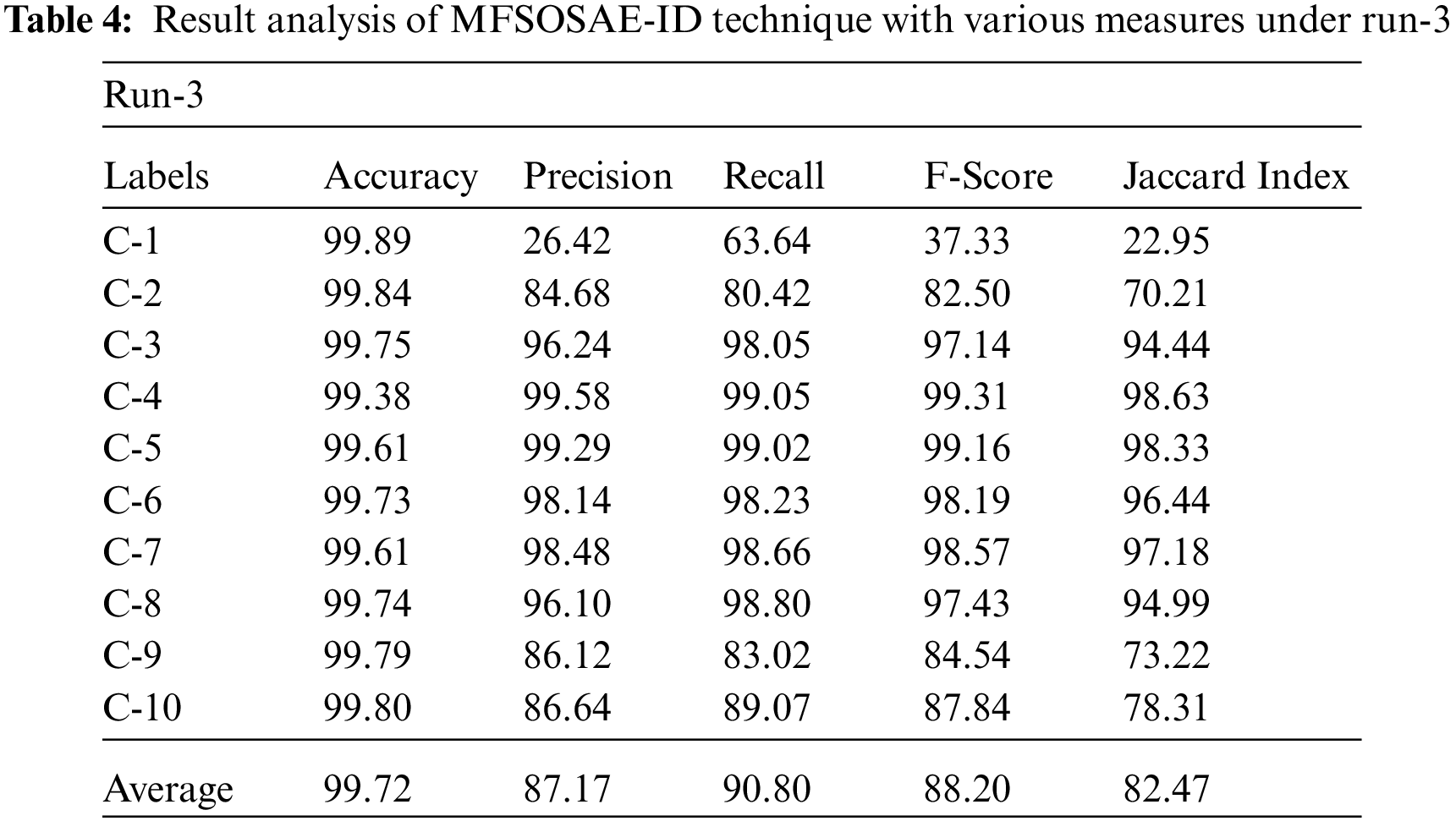
Tab. 5 illustrates the classification results offered by the MFSOSAE-ID system on UNSW-NB15 dataset under run-4. The outcomes revealed that the MFSOSAE-ID algorithm has resulted in maximal classifier results under all ten classes. For sample, with class C-3, the MFSOSAE-ID model has accessible
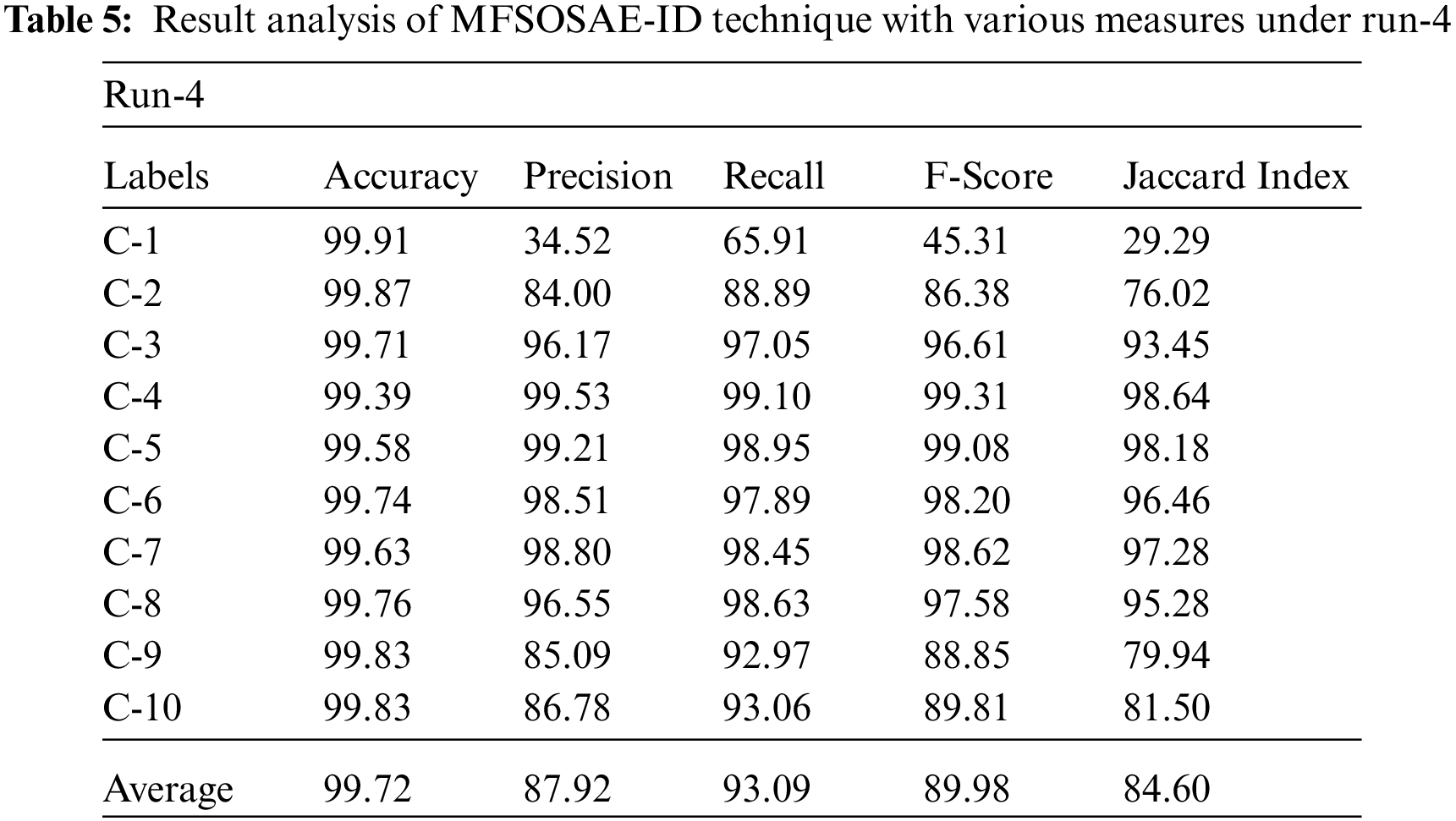
Fig. 4 exhibits a detailed average result obtained by the MFSOSAE-ID model under four runs on UNSW-NB15 dataset. The figure notified that the MFSOSAE-ID model has resulted in maximum classifier outcomes under all runs. For instance, with run-1, the MFSOSAE-ID model has gained average

Figure 4: Average analysis of MFSOSAE-ID technique (a) run-1, (b) run-2, (c) run-3, and (d) run-4
The training accuracy (TA) and validation accuracy (VA) attained by the MFSOSAE-ID system on test dataset is demonstrated in Fig. 5. The experimental outcome implied that the MFSOSAE-ID method has gained maximum values of TA and VA. In specific, the VA seemed to be superior to TA.

Figure 5: TA and VA analysis of MFSOSAE-ID technique
The training loss (TL) and validation loss (VL) achieved by the MFSOSAE-ID approach on test dataset are established in Fig. 6. The experimental outcome inferred that the MFSOSAE-ID methodology has been able least values of TL and VL. In specific, the VL seemed to be lower than TL.

Figure 6: TL and VL analysis of MFSOSAE-ID technique
At last, a comprehensive comparative examination of the MFSOSAE-ID technique with recent methodologies is offered in Tab. 6 [26]. Fig. 7 illustrates a comparison study of the MFSOSAE-ID model with other models interms of
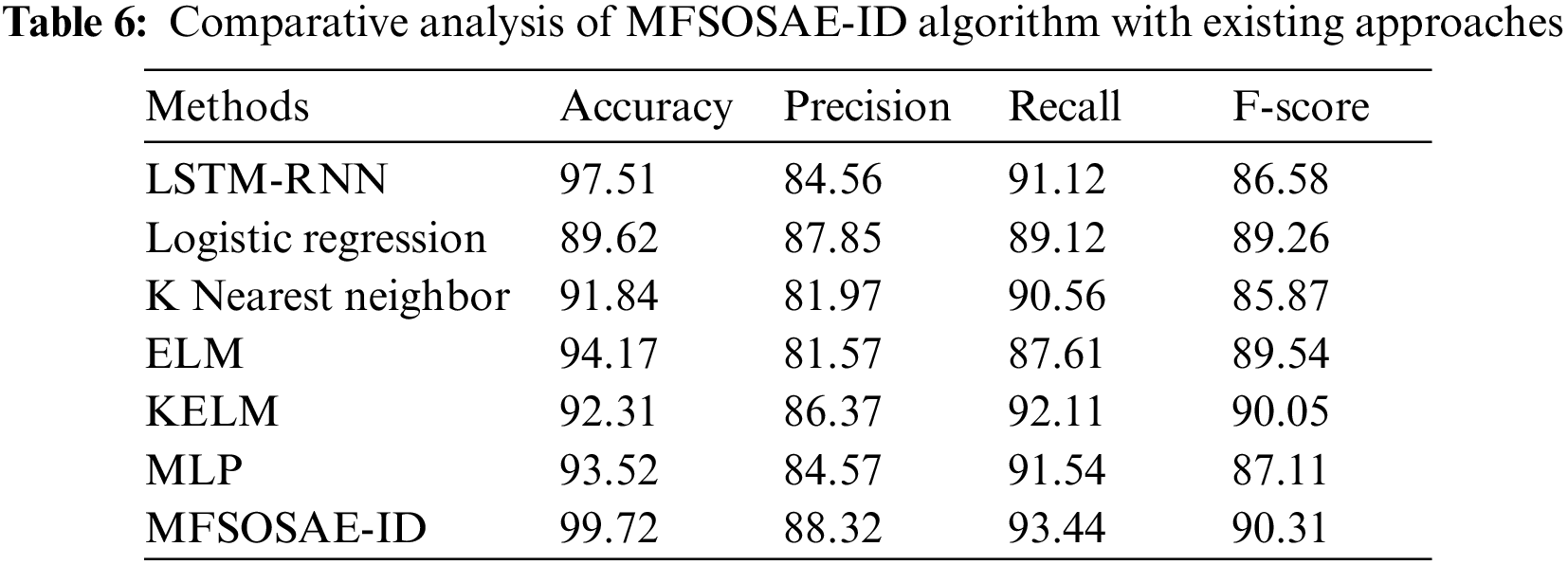

Figure 7:
Fig. 8 showcases a comparison study of the MFSOSAE-ID model with other models with respect to

Figure 8:
In this study, a novel MFSOSAE-ID approach was established to determine the existence of intrusions in the IoD environment. The presented MFSOSAE-ID technique firstly pre-processes the input data into a compatible format. Followed this, the presented MFSOSAE-ID technique designs an MFOFS technique to elect appropriate features. In line with, the SAE model is employed for the recognition and classification of intrusions in which the SAE parameters are optimally tuned with utilize of FFA. The performance validation of the MFSOSAE-ID model is tested utilizing benchmark dataset and the outcomes implied the promising performance of the MFSOSAE-ID model over other techniques. Thus, the presented MFSOSAE-ID technique can be employed to accomplish security in the IoD environment. In future, advanced deep learning (DL) based classification models can be employed to boost detection efficiency of the MFSOSAE-ID model.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Large Groups Project under grant number (158/43). Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R140), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: 22UQU4210118DSR18.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. M. Gharibi, R. Boutaba and S. L. Waslander, “Internet of drones,” IEEE Access, vol. 4, pp. 1148–1162, 2016. [Google Scholar]
2. Z. Lv, “The security of internet of drones,” Computer Communications, vol. 148, no. 2, pp. 208–214, 2019. [Google Scholar]
3. M. Yahuza, K. Dimyati, K. A. Noordin, N. S. M. Shah, S. H. Alsamhi et al., “Internet of drones security and privacy issues: Taxonomy and open challenges,” IEEE Access, vol. 9, pp. 57243–57270, 2021. [Google Scholar]
4. T. Long, M. Ozger, O. Cetinkaya and O. B. Akan, “Energy neutral internet of drones,” IEEE Communications Magazine, vol. 56, no. 1, pp. 22–28, 2018. [Google Scholar]
5. A. Koubâa, B. Qureshi, M. F. Sriti, A. Allouch, Y. Javed et al., “Dronemap Planner: A service-oriented cloud-based management system for the Internet-of-Drones,” Ad Hoc Networks, vol. 86, no. 2, pp. 46–62, 2019. [Google Scholar]
6. A. Abdelmaboud, “The internet of drones: Requirements, taxonomy, recent advances, and challenges of research trends,” Sensors, vol. 21, no. 17, pp. 5718, 2021. [Google Scholar]
7. J. V. Anchitaalagammai, T. Jayasankar, P. Selvaraj, M. Y. Sikkandar, M. Zakarya et al., “Energy efficient cluster-based optimal resource management in iot environment,” Computers, Materials & Continua, vol. 70, no. 1, pp. 1247–1261, 2022. [Google Scholar]
8. M. Wazid, A. K. Das and J. H. Lee, “Authentication protocols for the internet of drones: Taxonomy, analysis and future directions,” Journal of Ambient Intelligence and Humanized Computing, vol. 101, no. 3, pp. 42, 2018. [Google Scholar]
9. M. A. Ferrag, L. Shu, O. Friha and X. Yang, “Cyber security intrusion detection for agriculture 4.0: Machine learning-based solutions, datasets, and future directions,” IEEE/CAA Journal of Automatica Sinica, vol. 9, no. 3, pp. 407–436, 2022. [Google Scholar]
10. I. V. Pustokhina, D. A. Pustokhin, E. L. Lydia, P. Garg, A. Kadian et al., “Hyperparameter search based convolution neural network with Bi-LSTM model for intrusion detection system in multimedia big data environment,” Multimedia Tools and Applications, vol. 13, no. 5, pp. 111, 2021. [Google Scholar]
11. S. Ouiazzane, M. Addou and F. Barramou, “A multiagent and machine learning based denial of service intrusion detection system for drone networks,” in Geospatial Intelligence, Advances in Science, Technology & Innovation Book Series (ASTI). Cham: Springer, pp. 51–65, 2022. [Google Scholar]
12. J. P. Condomines, R. Zhang and N. Larrieu, “Network intrusion detection system for UAV ad-hoc communication: From methodology design to real test validation,” Ad Hoc Networks, vol. 90, no. 2, pp. 101759, 2019. [Google Scholar]
13. S. Perumalla, S. Chatterjee and A. P. S. Kumar, “Block chain-based access control and intrusion detection system in IoD,” in 2021 6th Int. Conf. on Communication and Electronics Systems (ICCES), Coimbatre, India, pp. 511–518, 2021. [Google Scholar]
14. D. Sharma, S. K. Gupta, A. Rashid, S. Gupta, M. Rashid et al., “A novel approach for securing data against intrusion attacks in unmanned aerial vehicles integrated heterogeneous network using functional encryption technique,” Transactions on Emerging Telecommunications Technologies, vol. 32, no. 7, pp. e3667, 2021. [Google Scholar]
15. S. Ouiazzane, F. Barramou and M. Addou, “Towards a multi-agent based network intrusion detection system for a fleet of drones,” International Journal of Advanced Computer Science and Applications, vol. 11, no. 10, 2020. DOI 10.14569/issn.2156-5570. [Google Scholar] [CrossRef]
16. M. A. Hamza, S. B. Haj Hassine, I. Abunadi, F. N. Al-Wesabi, H. Alsolai et al., “Feature selection with optimal stacked sparse autoencoder for data mining,” Computers, Materials & Continua, vol. 72, no. 2, pp. 2581–2596, 2022. [Google Scholar]
17. A. A. Albraikan, S. B. Haj Hassine, S. M. Fati, F. N. Al-Wesabi, A. M. Hilal et al., “Optimal deep learning-based cyberattack detection and classification technique on social networks,” Computers, Materials & Continua, vol. 72, no. 1, pp. 907–923, 2022. [Google Scholar]
18. A. M. Hilal, J. S. Alzahrani, I. Abunadi, N. Nemri, F. N. Al-Wesabi et al., “Intelligent deep learning model for privacy preserving IIoT on 6g environment,” Computers, Materials & Continua, vol. 72, no. 1, pp. 333–348, 2022. [Google Scholar]
19. S. Mirjalili, “Moth-flame optimization algorithm: A novel nature-inspired heuristic paradigm,” Knowledge-Based Systems, vol. 89, pp. 228–249, 2015. [Google Scholar]
20. P. Zhou, J. Han, G. Cheng and B. Zhang, “Learning compact and discriminative stacked autoencoder for hyperspectral image classification,” IEEE Transactions on Geoscience and Remote Sensing, vol. 57, no. 7, pp. 4823–4833, 2019. [Google Scholar]
21. I. V. Pustokhina, D. A. Pustokhin, E. L. Lydia, P. Garg, A. Kadian et al., “Hyperparameter search based convolution neural network with Bi‐LSTM model for intrusion detection system in multimedia big data environment,” Multimedia Tools and Applications, vol. 13, no. 5, pp. 111, 2021. [Google Scholar]
22. K. Shankar, E. Perumal, P. Tiwari, M. Shorfuzzaman and D. Gupta, “Deep learning and evolutionary intelligence with fusion-based feature extraction for detection of COVID-19 from chest X-ray images,” Multimedia Systems, vol. 66, no. 2, pp. 1921, 2021. [Google Scholar]
23. K. Shankar, Y. Zhang, Y. Liu, L. Wu and C. H. Chen, “Hyperparameter tuning deep learning for diabetic retinopathy fundus image classification,” IEEE Access, vol. 8, pp. 118164–118173, 2020. [Google Scholar]
24. X. Yang and X. He, “Firefly algorithm: recent advances and applications,” International Journal of Swarm Intelligence, vol. 1, no. 1, pp. 36, 2013. [Google Scholar]
25. N. Moustafa and J. Slay, “UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set),” in 2015 Military Communications and Information Systems Conf. (MilCIS), Poland, pp. 1–6, 2015. [Google Scholar]
26. R. A. Ramadan, A. H. Emara, M. A. Sarem and M. Elhamahmy, “Internet of drones intrusion detection using deep learning,” Electronics, vol. 10, no. 21, pp. 2633, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |