DOI:10.32604/csse.2022.020097

| Computer Systems Science & Engineering DOI:10.32604/csse.2022.020097 |  |
| Article |
Healthcare Device Security Assessment through Computational Methodology
1Department of Information Technology, Babasaheb Bhimrao Ambedkar University, Lucknow, 226025, Uttar Pradesh, India
2Department of Information Technology, College of Computers and Information Technology, Taif University, Taif, 21944, Saudi Arabia
3Department of Computer Science, University College of Al Jamoum, Umm Al Qura University, Makkah, 21421, Saudi Arabia
*Corresponding Author: Alka Agrawal. Email: alka_csjmu@yahoo.co.in
Received: 08 May 2021; Accepted: 09 June 2021
Abstract: The current study discusses the different methods used to secure healthcare devices and proposes a quantitative framework to list them in order of significances. The study uses the Hesitant Fuzzy (HF), Analytic Hierarchy Process (AHP) integrated with Fuzzy Technical for Order Preference by Similarities to Ideal Solution (TOPSIS) to classify the best alternatives to security techniques for healthcare devices to securing the devices. The technique is enlisted to rate the alternatives based on the degree of satisfaction of their weights. The ranks of the alternatives consequently decide the order of priority for the techniques. A1 was the most probable alternative of all the alternatives, according to the ranks of the alternatives acquired. This means that the security of A2 healthcare devices is the greatest of all the alternatives picked. A corroborative guide for the developers and the makers in quantitatively determining the security of healthcare devices to engineer efficacious devices will be the findings drawn up with the assistance of the proposed framework. The assessments performed using the proposed framework are systematic, precise, and definitive. Therefore, the results of the present empirical analysis are a stronger and accurate choice than the manual assessment of the device’s security.
Keywords: Healthcare devices; HF-AHP.TOPSIS; device security
Healthcare devices are the virtual lifelines of today’s healthcare systems and are commonly used to avoid, track, or diagnose diseases. However, these devices have also become an easy target for cyber intrusions due to software and design-related vulnerabilities. Ironically, due to cyber-attacks, devices meant to protect the health of patients’ are now becoming a major health threat. Only one among such breaches is the troubling instance of intruders gaining easy access to insulin pumps [1–5]. An exponential increase in attacks on the entire healthcare sector has been reported in the last few years. Security experts suggest that the high demand and cost of healthcare data on the dark web may be the explanation for this increase [6–9]. Several attacks on healthcare devices are carried out, risking not only the effectiveness of the system but also corrupting the data. For example, any running window system can easily target custom worm and infect more than 100 MRI machines at a time.
The FDA drafted a study that examined the security of healthcare devices in 2012 [2] to increasing episodes of breaches. The FDA issued a set of guidelines on the security of healthcare devices’ for manufactures in 2013 [3]. Researchers, developers, and manufacturers are imminently needed to work on more foolproof mechanisms to resolve the threats to healthcare devices. Attempts to incorporate improved security measures right from the healthcare device design and development process would be a pre-emptive step in this direction [10–15].
In addition to the security of healthcare devices, the credibility of the devices [16–21] is yet another fact that needs to be improved. The security element of the device varies from the safety of the healthcare device’s design. Although safety focuses on the hazardous circumstances that may arise accidentally and intensely, the security of the device from modifications to the data contained in the device may be made. Attacks on the healthcare network and network of healthcare devices threaten both the security of devices and the safety of information [22–25]. Due to the network breach of healthcare devices, research studies performed in this area have found many vulnerabilities and safety issues. Implantable Medical Devices (IMDs) [26], wearable devices [27,28] and surgical robots [29] are some of these devices. There are network flaws in the hospital network configuration [30–33], a third party service provider networks (like, laboratories, pharmacies, etc.) [34,35].
All these events allow the attackers to enter the network and take control. To gain access to the healthcare devices and steal the credentials [36–39] and exploit the vulnerabilities the attackers use the network. It is important to remove the efficacy that is sometimes introduced into healthcare devices due to design or software development to maximize the effectiveness of the healthcare devices [40–43]. The healthcare device credibility is thus an essential research premise and assumes greater significance in the efforts to make the medical devices more secure and reliable [44,45].
Against this context, the current research aims to examine the different security checking mechanisms and methodologies that are currently being used to determine the security of healthcare devices. The analysis then draws on the experts’ views on the security of healthcare devices as inputs for the implementation of the proposed methodology. We will outline the relevant method, security examination mechanisms, and methodology for determining the security of the healthcare devices. As an insight into the methodology, we apply the expert’s opinion about the security of the medical devices. And the debate on the empirical analysis of the method and sensitivity analysis of the empirical discussed.
2 Medical Device Security Mechanisms
Healthcare devices are effectively implanted and connected to the body of the patients and collect the body’s sensitive data [46]. The device gathers the patient’s activity of the body and sends it to the experts and laboratories through the network for processing. Network associated, low-power sensor-based devices are more vulnerable to intrusions. Many manufacturers want to supply embedded devices that use less power at a low cost. Therefore, additional safety mechanisms are not favored, which would make the device complex and raise the costs of manufacturing [47–49]. For example, when making on-site medical devices such as X-ray, MRI, and Ultrasound, etc., keeping the device secure and protecting it from hackers is not the priority of the developers.
Developer’s concentrate on the working of the device, as most of them, do not even know about the safety and precautions. In a healthcare device, parts such as hardware and outdated software also invite vulnerabilities in the device that are easy for hackers to exploit [50,51]. Reverse engineering techniques can manipulate on-site devices and easily breach the security and availability of devices. The software and hardware layers are also part of the security needs [52,53]. Integrity, availability, authentication, confidentiality, safety and privacy, unauthorized tampering, are the essential features for developing highly secure healthcare devices. Due to traditional security algorithms that cannot be used because of implantable and sensor devices, maintaining the security of the devices is a tough task challenge.
But in recent years, refreshers have built a new algorithm for the CIA that resolve integrity and security issues. These are not ideal for all forms of cyber-attacks because of certain bars. The on-site healthcare devices (MRI, X-ray, and ultrasound) are also vulnerable to cyber-attacks [26–29]. Various techniques for preserving the security of the devices have been developed. Such approaches have been elucidated in Fig. 1.

Figure 1: Medical devices security methods
Converting the simple characters into some special type of code through a systematic algorithm is called the encryption process [20]. This process has a special position in security mechanics because it gives a special ability of secrecy to the sender’s message or information.
Biometric is human physical or behavioral characteristics that can be used to identify an individual digitally to grant access to systems, devices, or information [21]. Fingerprints, facial expressions, speech, or typing are examples of these biometric signatures.
The method of verifying the identity of a person or system is known as authentication [22]. When a person wants to log in, a typical example is entering a username and password. Entering the correct login information helps that person is accessing the device.
A peripheral system used to gain access to an electronically limited resource is a security token [23]. In addition to or in place of a password, the token is used.
A password, also referred to as a passcode, is a memorized secret, normally a character string generally used to confirm the identity of a user [23].
After accident deletion, formatting, partition mistake, device crash, etc., data recovery software can help restore data [24]. This is used in the integrity of the data.
Access control is a way of ensuring that people are who they say they are and that they have the right access to personal information [25].
A backup is a copy of data taken and stored somewhere so that it can be used during a data loss event to recover the original [26]. Backup is the verb form referring to the method of doing so, while a backup is the noun and adjective form.
Error detection is the method of identifying errors in a communication device that is present in the data transmitted from the transmitter to the receiver [27]. To recognize these errors, we use some redundancy codes by adding them to the data while it is transmitted from the source (transmitter).
The practice of monitoring and handling modifications to software code is version control, often referred to as source control [28]. Version control systems are automated mechanisms that assist software teams to handle source code revisions over time.
Some real-world issues demand unique or multi choice-based solutions that are crucial for real users to conduct without any solid base. To tackle this situation and give an ideal quantitative solution to these issues the adopted MCDM approaches are implemented by various researchers. Specifically adopted AHP approach combined with fuzzy linguistic term set theory is more effective and simple in the comparison of others it is evident from various previous research initiatives [5,9]. If there is more than one option available for evaluation in the technique during the computation process, then this situation influences the calculated results even more strongly. In the context of the proposed article authors adopt a hesitant fuzzy set-based MCDM approach that gives an extra efficiency in results for evaluation. Besides, the TOPSIS approach has been used to assess the security of healthcare devices results obtained. Besides, to get more productive and accurate results, this study adopts the hesitant fuzzy approach. Moreover, for testing the evaluated results adopted the methodology of TOPSIS is the most promised and effective approach available in MCDM approaches. The biggest beneficial advantage of this methodology is that it gives a positive and negative both impact evaluation in the same evaluation and considers it in the calculation.
The authors followed the hesitant fuzzy set approach [15] when decision-makers find the possibility or situation of choosing any other value for numbering besides previously used ones. This type of situation opens a possibility of hesitant value use in evaluation which is prepared and discussed firstly by a study [28] and then modified and more systematically explained by Algarni et al. [14].
In cloud-based security architecture, Torra et al. [28] presented a TOPSIS integrated methodology that yielded successful results. For this article, the methodology adopted can skip and handle ambiguities and other AHP-TOPSIS methodology issues. Besides, by evaluating stock selection on paper, the model often validates its results. Similarly, Torra et al. [28,29] in their study have used the same approach. The authors verified the reliability of this technique by objectively analyzing the security of healthcare devices. Besides, Xu et al. [30] and Kumar et al. [31] have also used the specified technique to generate convincing results for their study in the sense of the energy solution.
In our research, HF-AHP methods were enlisted to estimate the priority of the healthcare device security factors, and then we tested their approach HF-TOPSIS on alternatives for similar factors [32]. A phase by phase methodology, in brief, is discussed below:
Phase 1: The first step in the implemented approach is the hierarchy development of factors.
Phase 2: In Tab. 1, examiners use linguistic terminology to create accurate and beneficial assessment criteria for the decision-makers.

Phase 3: The next step in technique evaluation is the adoption of fuzzy wrappers [29] from Eq. (1).
Same as experts evaluate the trapezoidal numbers
After imposing the Eqs. (3)–(5), the experts decide the first and second form of weights η, i.e., the number between [0, 1] and Eqs. (6)–(7) applied by the experts to obtain these numbers.
1st type weights
2nd type weights
The numerical form for the highest rank in the formula
Phase 4: Eqs. (8)–(9) are used by the experts after evaluating the entire previous approach to satisfy the remaining comparison matrix attributes. Thereafter, experts use Eq. (10) to defuzzify the matrix to determine the comparison matrix.
Phase 5: The phase of defuzzification provides correct values. The experts examine the Consistency Ratio (CR) by applying the Eqs. (11)–(12) to analyse the CR of these values.
Phase 6: In this step, by Eq. (13), the experts assess the geometrical mean of the values.
Phase 7: The most significant criterion in the entire set is evaluated by experts by applying the Eq. (14).
Phase 8: Examiners analyze the defuzzified values by Eq. (15).
Phase 9: By applying the Eq. (16), experts transform the defuzzified values into normalized values or weights.
Now after identifying priority list for selected attributes the second adopted methodology of TOPSIS is used for testing the effectiveness of obtained results. TOPSIS is effective as a MADM technique in recommending the most preferred option for use. The definition of the TOPSIS approach was introduced by Lai et al. The synthesis of positive and negative ideas is the TOPSIS methodology; the most accurate and effective option is the most precise and reliable factor. The worst option, on the other hand, is an irrelevant factor. The authors utilized the hesitant fuzzy AHP TOPSIS approach to test and assess the security of healthcare devices [14]. The TOPSIS method associates the distance between two linguistic values such as H1s and H2s and performs its computations. Below, the procedure has been clarified (Eq. (17)):
Phase 10: The following terms are described as the starting process:
The following written formulas are applied as
Similarly, k is used to show the numeric count of experts in TOPSIS
The equation
The standards are written for TOPSIS to determine the criteria and effect of outcomes:
The standard for TOPSIS evaluation lies in between very poor and very good scale,
For HF matrix, the following formulas are used [9]:
Phase 11: By applying the Eq. (18) formula, the associated combined matrix is created:
Phase 12: The effective factor where most effective factor is indicated by Aj, is shown by alpha in the TOPSIS evaluation, and alpha shows the cost-related preferences. In addition, the latest efficient alternatives need high precision for cost related preferences. The following Eqs. (19)–(22) are used to define and compare cost as well as effective factors:
Phase 13: Experts evaluate TOPISIS +ve and −ve concepts components by applying following Eqs. (23)–(24).
Phase 14: Experts build and assess the closeness of positive and negative factors evaluated by Eqs. (25)–(26).
where
Phase 15: The ranks are allocated to conclude the process, and the tabular forms of options are focused on their assessment of effectiveness.
In further parts of this study, a highly detailed and evaluated numerical assessment of healthcare device security has been conducted.
In this section, authors discussed the analysis of results of the proposed method, and compare the proposed method with existing methods to verdict the proposed method advantages.
Managing security and its characteristic in a system is crucial and challenging task for experts. Security measures for healthcare devices can be enhanced with the aid of quantitative evaluation. But because of growing security breaches and user dissatisfaction, practitioners are often confused during process of development. Therefore, to avoid this situation and manage the security perfectly adopted approach is used for evaluation in this proposed article. Further, it is decision-making challenge to ensure the security of healthcare devices. To quantitatively analyze and solve this kind of dilemma, there are so many decision-making processes.
Firstly, in order to conduct the adopted evaluation approach forty five different experts for academic and industry background are called on a virtual meeting environment for discussion. During this discussion they get briefly introduced by topic of research and then selected attributes in order to achieve the desired objective. O the basis of that introduction and their own experience in relevant field they provide values that work as key decision makers in the evaluation. Further, on the basis of their values authors prepare matrix for evaluation which are portray by them in following headings. At level 1 of the hierarchy, two characteristics are shown according to Fig. 1. In the gathering, both practitioners were given a joint decision. Fuzzy envelops (consistent) for features at level 1 are shown in Tab. 2.

The accuracy of every evaluation was checked by phase 5 and Eqs. (1)–(12) after obtaining the score. The consistency was found to be lower than 0.1 for all groups characteristics of the hierarchy. The results of level 1 function from Tabs. 1 and 2 and Eqs. (1)–(12) were evaluated by the authors as follows:
“B/W EHI and WHI” were designated as the fuzzy envelope (F1). The linguistic values associated with the Triangular Fuzzy Numbers (TFN) are (1, 1, 3) and (1, 3, 5), respectively. The trapezoidal fuzzy numbers

Calculating the fuzzy weights of characteristics, from Eqs. (13)–(14). After that by Eq. (14), the weight of corresponding characteristic can be evaluated. In addition, from Eq. (15), the defuzzified value of respective characteristic is calculated and the weights are finally normalized by Eq. (16).
The same method for evaluating fuzzy local weights as shown in Tab. 3 is used to describe attributes weightage present in next layer of first layer. Further, global weights and ranks of the attributes are shown in Tab. 4. Moreover, Tabs. 5 and 6 are available to present values based on the level and its importance towards usability of device security, with the help of Eqs. (17)–(22). Further, Tab. 7 and Fig. 2 show the satisfaction degree of alternatives and overall impacts obtained by Eqs. (23)–(26).
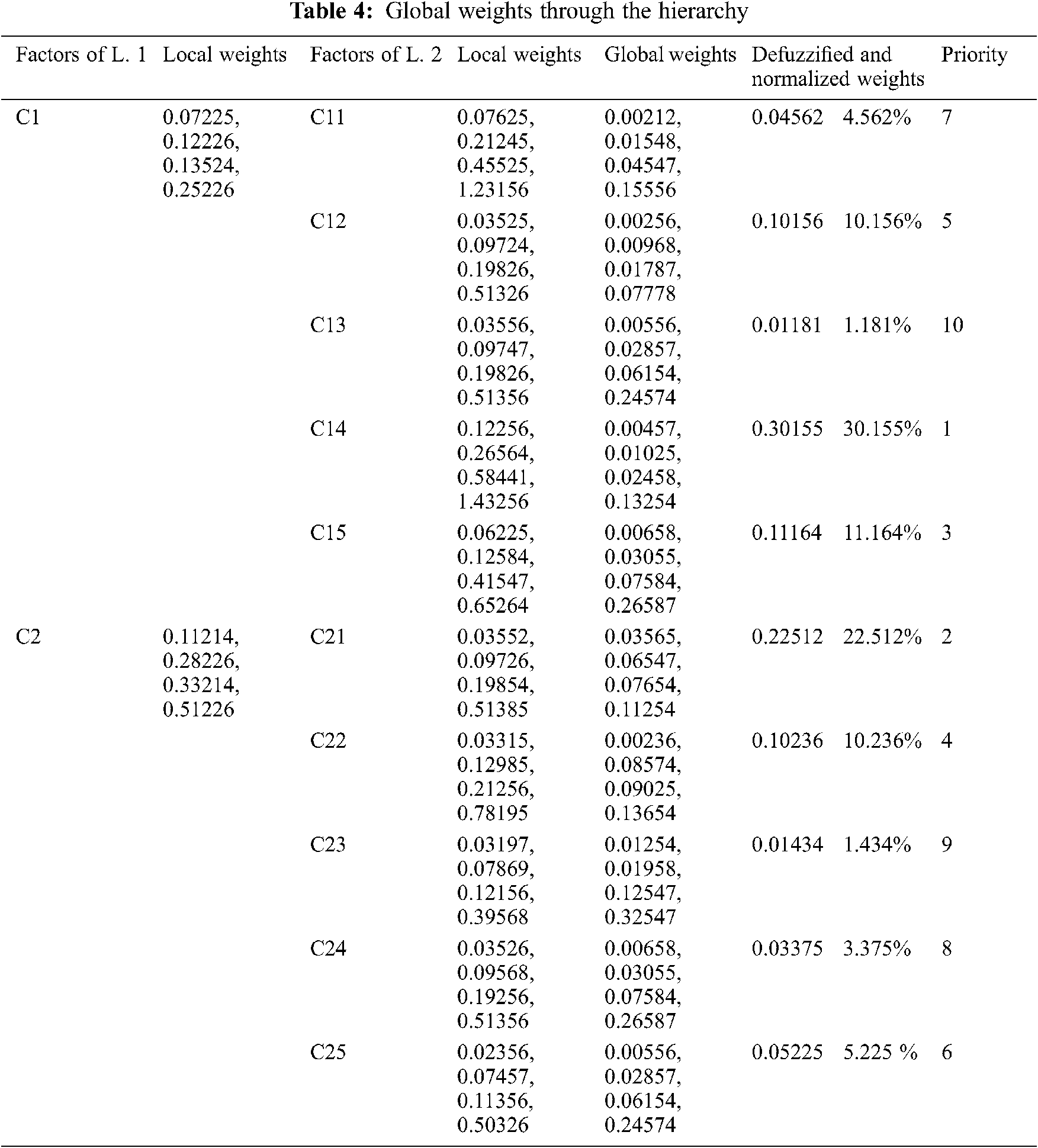


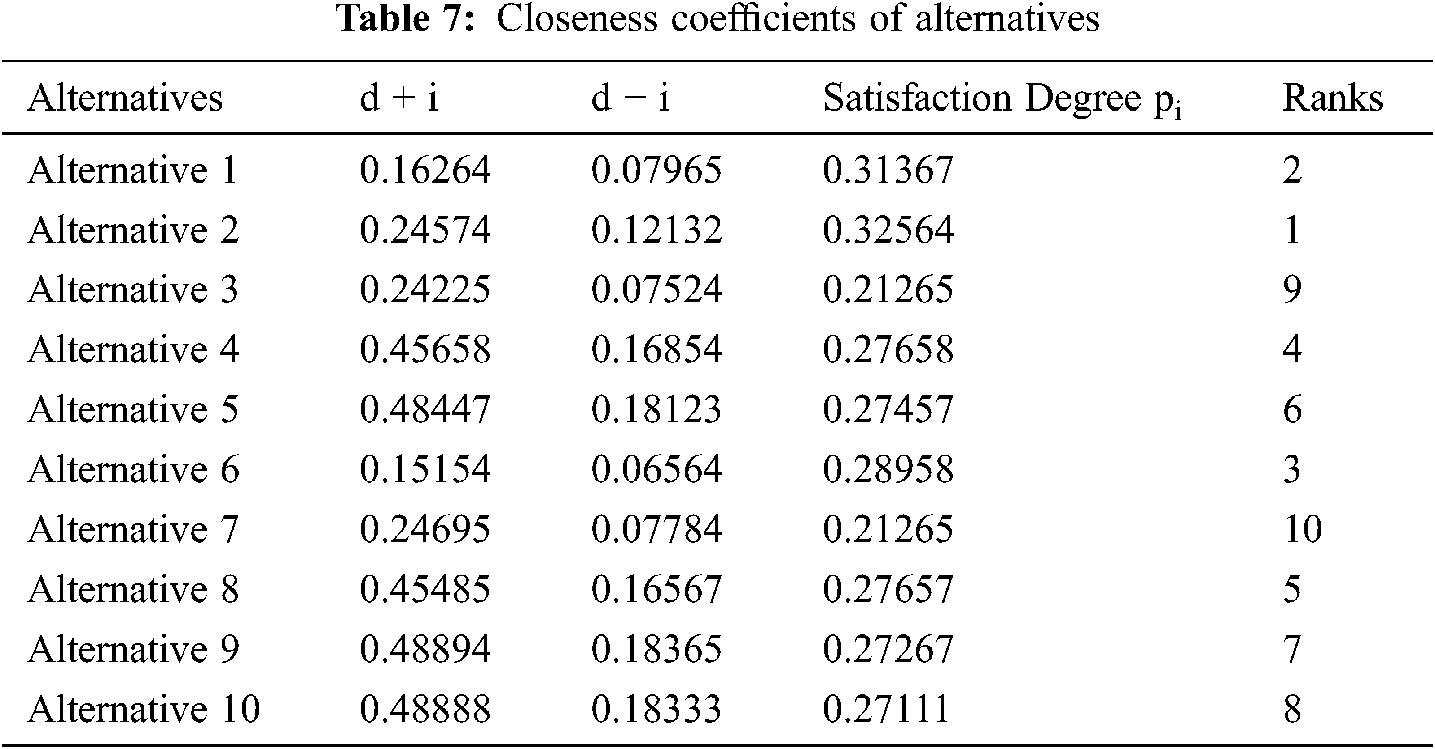

Figure 2: Graphical representation of satisfaction degrees
Tab. 7 and Fig. 2 represent the closeness coefficients of alternatives, in this table distance calculated from a positive and negative ideal solution and satisfaction degree is calculated. According to the satisfaction, degree assigns the ranks and we observed that alternative 2 obtain the highest ranks and best alternative after that A1 obtain the highest priority. After review, we checked the findings of our analysis by adjusting the variable.
4.2 Sensitivity Analysis and Comparison
Authors performed sensitivity analysis of the presented method in order to verified the accuracy and validity of results and compare with Ahmed’s method [33], Algarni method [14] and classical method of both method with presented method in this paper has some advantages with rest method: presented method increase the acceptability/accuracy of the decision making results, easily determined the uncertainty in decision making, presented method can better reflect decision compared to other decision making method. Authors have done sensitivity analysis within 10 experiments because authors have chosen 10 alternatives in the last level of hierarchy of Fig. 1. In order to evaluate, the sensitivity weights of each factors are changed at various times, while the other factors weights and satisfaction levels are remain constant. Sensitivity analysis depicted on Tab. 8.

Authors performed comparison with other existent method; in the comparison same data applied by authors for evaluation the other methods available in the study. Comparison results with other methods is depicted in Tab. 9 and proof is available in results that HF-AHP-TOPSIS (proposed) method gives improved results in compare to other methods available in study.

The security of healthcare devices is compromised at the execution time by the method of data transfer, data storage, and migration process. By updating the software patch, using the hardware security guards and network encryption techniques all these problems can be addressed. Healthcare devices hold confidential information relating to the health and personal data of patients. We have established an approach for quantitative assessment of the security of healthcare devices from the proposed article through HF-AHP.TOPSIS approach in our framework, which is the best decision making and ranting approach. The decision-makers allocated the rating of the healthcare devices based on their security using this approach. The study has enlisted the help of 45 experts in different fields of security. Based on their experiences, they ranked the healthcare devices accordingly. Finally, on the provided data for performance assessment of the healthcare devices, HF.AHP.TOPSIS was applied. The findings of this research work as shows:
• Most researchers work on the security of healthcare devices, but do not have sufficient guidelines for the development and design of the software and security of the device.
• Our approach is systematic and provides the developers with effective guidelines to build the software by adhering to the security rules.
• Security evaluation of healthcare devices will not only ensure the operation of healthcare devices and the personal details of patients but will also improve the device’s technological characteristics.
• Manufacturers and government agencies may use our framework to quantitatively and reliably verify the security of healthcare devices.
In the current situation, dependability on healthcare devices has improved enormously, more so in the aftermath of a health emergency such as the COVID-19 pandemic when home quarantine instead of attending hospitals was recommended to patients. For health care monitoring and treatment, doctors and patients alike depend on medical devices. Healthcare devices submit data from patients to physicians who prescribe the course of care after the data has been checked. However, the confidentiality of the data and system is under consideration. Even a small difference in the data of the patient can lead to an incorrect diagnosis, thus endangering the health and well-being of the patient. Quantitative and automated evaluation of the security of medical devices is an efficient solution for ensuring the security of the healthcare device. In the above observation, the A2 alternative obtains the highest ranks among the best alternatives. In the current analysis, this was done with the help of the HF-AHP.TOPSIS approach. Among the different alternatives, this method is best for decision making and provides corroborative results. This framework is well validated and tested; manufactures may use a tested approach to security checking to protect the healthcare devices.
Acknowledgement: This research was supported by Taif University Researchers Supporting Project number (TURSP-2020/211), Taif University, Taif, Saudi Arabia.
Funding Statement: This Project was funded by the Taif University Researchers Supporting Projects at Taif University, Kingdom of Saudi Arabia, under Grant Number: TURSP-2020/211.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. D. Halperin, T. S. H. Benjamin, B. Ransford, S. S. Clark, B. Defend et al., “Pacemakers and implantable cardiac defibrillators: Software radio attacks and zero-power defenses,” in Proc. of the IEEE Symp. on Security and Privacy, Oakland, CA, USA, pp. 129–142, 2008. [Google Scholar]
2. C. Li, A. Raghunathan and N. Jha, “Hijacking an insulin pump: Security attacks and defenses for a diabetes therapy system,” in Proc. of the 2011 IEEE 13th Int. Conf. on e-Health Networking, Applications and Services, Columbia, MO, USA, pp. 150–156, 2011. [Google Scholar]
3. H. Almohri, L. Cheng, D. Yao and M. Alemzadeh, “On threat modeling and mitigation of medical cyber-physical systems,” in Proc. of the IEEE/ACM Int. Conf. on Connected Health: Applications, System, Philadelphia, PA, USA, pp. 114–119, 2017. [Google Scholar]
4. MassDevice, “Confickered! medical devices and digital medical records are getting hacked,” 2009. [Online]. Available: https://www.massdevice.com/confickered-medical-devices-and-digital-medical-records-are-getting-hacked/. [Google Scholar]
5. Business Wire, “Nomoreclipboard notice to individuals of a data security compromise,” 2015. [Online]. Available: https://www.businesswire.com/news/home/20150610005964/en/NoMoreClipboard-Notice-to-Individuals-of-a-Data-Security-Compromise. [Google Scholar]
6. GAO: U. S. Government Accountability Office, “Medical devices: FDA should expand its consideration of information security for certain types of devices,” 2012. [Online]. Available: https://www.gao.gov/products/GAO-12-816. [Google Scholar]
7. U. S. Food & Drug Administration, “FDA’s role in regulating medical devices,” 2018. [Online]. Available: https://www.fda.gov/medical-devices/home-use-devices/fdas-role-regulating-medical-devices. [Google Scholar]
8. Y. Xu, D. Tran, Y. Tian and H. Alemzadeh, “Poster abstract: Analysis of cyber-security vulnerabilities of interconnected medical devices,” in Proc. of the 2019 IEEE/ACM Int. Conf. on Connected Health: Applications, Systems and Engineering Technologies, Arlington, VA, USA, pp. 23–24, 2019. [Google Scholar]
9. Wired Magazine, “Hospital networks are leaking data, leaving critical devices vulnerable,” 2014. [Online]. Available: https://www.wired.com/2014/06/hospital-networks-leaking-data/. [Google Scholar]
10. T. Bonaci, J. Yan, J. Herron, T. Kohno and H. J. Chizeck, “Experimental analysis of denial-of-service attacks on tele operated robotic systems,” in Proc. of the ACM/IEEE Sixth Int. Conf. on Cyber-Physical Systems, New York, NY, USA, pp. 11–20, 2015. [Google Scholar]
11. T. Yaqoob, H. Abbas and M. Atiquzzaman, “Security vulnerabilities, attacks, countermeasures, and regulations of networked medical devices-a review,” IEEE Communications Surveys & Tutorials, vol. 21, no. 4, pp. 3723–3768, 2019. [Google Scholar]
12. G. McGraw, “Software security,” IEEE Security and Privacy, vol. 2, no. 2, pp. 80–83, 2004. [Google Scholar]
13. A. Algarni, M. Ahmad, A. Attaallah, A. Agrawal, R. Kumar et al., “A hybrid fuzzy rule-based multi-criteria framework for security assessment of medical device software,” International Journal of Intelligent Engineering and Systems, vol. 13, no. 5, pp. 51–62, 2020. [Google Scholar]
14. A. Algarni, A. Attaallah, M. Ahmad, A. Agrawal, R. Kumar et al., “A fuzzy multi-objective covering-based security quantification model for mitigating risk of web based medical image processing system,” International Journal of Advanced Computer Science and Applications, vol. 11, no. 1, pp. 481–489, 2020. [Google Scholar]
15. C. Bresch, S. Chollet and D. Hely, “Towards an inherently secure run-time environment for medical devices,” in Proc. of the IEEE Int. Congress on Internet of Things, San Francisco, USA, pp. 140–147, 2018. [Google Scholar]
16. N. Christoulakis, G. Christou, E. Athanasopoulos and S. Ioannidis, “HCFI: Hardware-enforced control-flow integrity,” in Proc. of the Sixth ACM Conf. on Data and Application Security and Privacy, New York, NY, USA, pp. 38–49, 2016. [Google Scholar]
17. A. I. Newaz, A. K. Sikder, L. Babun and A. S. Uluagac, “HEKA: A novel intrusion detection system for attacks to personal medical devices,” in Proc. of the 2020 IEEE Conf. on Communications and Network Security, Avignon, France, pp. 1–9, 2020. [Google Scholar]
18. L. Zhou and Y. Makris, “HAFIX: Hardware-assisted flow integrity extension,” in Proc. of the 52nd Annual Design Automation Conf., San Francisco, CA, USA, pp. 1550–1555, 2015. [Google Scholar]
19. S. Gao and G. Thamilarasu, “Machine-learning classifiers for security in connected medical devices,” in Proc. of the 2017 26th Int. Conf. on Computer Communication and Networks, Vancouver, BC, Canada, pp. 1–5, 2017. [Google Scholar]
20. A. Ray and C. Rance, “An analysis method for medical device security,” in Proc. of the Symp. and Bootcamp on the Science of Security, New York, NY, USA, pp. 1–2, 2014. [Google Scholar]
21. V. Costan, I. Lebedev and S. Devadas, “Sanctum: Minimal hardware extensions for strong software isolation,” in Proc. of the 25th USENIX Security Symp., USENIX Security 16, Austin, TX, USA, pp. 857–874, 2016. [Google Scholar]
22. A. Ali and F. A. Khan, “Key agreement schemes in wireless body area networks: Taxonomy and state-of-the-art,” Journal of Medical Systems, vol. 39, no. 10, pp. 1–14, 2015. [Google Scholar]
23. D. Karaolan, A. Levi and V. Tuzcu, “Deriving cryptographic keys from physiological signals,” Pervasive and Mobile Computing, vol. 39, no. 4, pp. 65–79, 2017. [Google Scholar]
24. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Hesitant fuzzy sets based symmetrical model of decision-making for estimating the durability of web application,” Symmetry, vol. 12, no. 6, pp. 1770–1792, 2020. [Google Scholar]
25. A. Attaallah, M. Ahmad, M. Tarique, A. K. Pandey, R. Kumar et al., “Device security assessment of internet of healthcare things,” Intelligent Automation & Soft Computing, vol. 27, no. 2, pp. 593–603, 2021. [Google Scholar]
26. S. A. Khan, M. Alenezi, A. Agrawal, R. Kumar and R. A. Khan, “Evaluating performance of software durability through an integrated fuzzy-based symmetrical method of ANP and TOPSIS,” Symmetry, vol. 12, no. 4, pp. 1–15, 2020. [Google Scholar]
27. F. A. Alzahrani, M. Ahmad, M. Nadeem, R. Kumar and R. A. Khan, “Integrity assessment of medical devices for improving hospital services,” Computers, Materials & Continua, vol. 67, no. 3, pp. 3619–3633, 2021. [Google Scholar]
28. V. Torra and Y. Narukawa, “The index and the number of citations: Two fuzzy integrals,” IEEE Transactions on Fuzzy Systems, vol. 16, no. 6, pp. 795–797, 2008. [Google Scholar]
29. W. Alosaimi, R. Kumar, A. Alharbi, H. Alyami, A. Agrawal et al., “Computational technique for effectiveness of treatments used in curing sars-cov-2,” Intelligent Automation & Soft Computing, vol. 28, no. 3, pp. 617–628, 2021. [Google Scholar]
30. X. Xu, Z. Shi and B. Pan, “A new unsupervised hyperspectral band selection method based on multi objective optimization,” IEEE Geoscience and Remote Sensing Letters, vol. 14, no. 11, pp. 2112–2116, 2017. [Google Scholar]
31. R. Kumar, M. Zarour, M. Alenezi, A. Agrawal and R. A. Khan, “Measuring security durability of software through fuzzy-based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642, 2019. [Google Scholar]
32. K. Sahu, F. A. Alzahrani, R. K. Srivastava and R. Kumar, “Evaluating the impact of prediction techniques: Software reliability perspective,” Computers, Materials & Continua, vol. 67, no. 2, pp. 1471–1488, 2021. [Google Scholar]
33. S. Ahmed and A. Alhumam, “Unified computational modeling for healthcare device security assessment,” Computer Systems Science and Engineering, vol. 37, no. 1, pp. 1–18, 2021. [Google Scholar]
34. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al., “An integrated approach of fuzzy logic, AHP and TOPSIS for estimating usable-security of web applications,” IEEE Access, vol. 8, no. 8, pp. 50944–50957, 2020. [Google Scholar]
35. R. Kumar, S. A. Khan and R. A. Khan, “Fuzzy analytic hierarchy process for software durability: Security risks perspective,” Advances in Intelligent Systems and Computing, vol. 508, pp. 469–478, 2017. [Google Scholar]
36. R. Kumar, S. A. Khan and R. A. Khan, “Secure serviceability of software: Durability perspective,” Communications in Computer and Information Science, vol. 628, pp. 104–110, 2016. [Google Scholar]
37. R. Kumar, S. A. Khan and R. A. Khan, “Durability challenges in software engineering,” CrossTalk, vol. 42, no. 4, pp. 29–31, 2016. [Google Scholar]
38. R. Kumar, M. T. J. Ansari, A. Baz, H. Alhakami, A. Agrawal et al., “A multi-perspective benchmarking framework for estimating usable-security of hospital management system software based on fuzzy logic, ANP and TOPSIS methods,” KSII Transactions on Internet and Information Systems, vol. 15, no. 1, pp. 240–263, 2021. [Google Scholar]
39. K. Sahu and R. K. Srivastava, “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222, 2018. [Google Scholar]
40. R. Kumar, M. Zarour, M. Alenezi, A. Agrawal and R. A. Khan, “Measuring security durability of software through fuzzy-based decision-making process,” International Journal of Computational Intelligence Systems, vol. 12, no. 2, pp. 627–642, 2019. [Google Scholar]
41. K. Sahu and R. K. Srivastava, “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37, 2020. [Google Scholar]
42. R. Kumar, S. A. Khan and R. A. Khan, “Revisiting software security: Durability perspective,” International Journal of Hybrid Information Technology, vol. 8, no. 2, pp. 311–322, 2015. [Google Scholar]
43. W. Alosaimi, A. Alharbi, H. Alyami, M. Ahmad, A. K. Pandey et al., “Impact of tools and techniques for securing consultancy services,” Computer Systems Science and Engineering, vol. 37, no. 3, pp. 347–360, 2021. [Google Scholar]
44. R. Kumar, S. A. Khan and R. A. Khan, “Durable security in software development: Needs and importance,” CSI Communications, vol. 10, no. 10, pp. 34–36, 2015. [Google Scholar]
45. R. Kumar, S. A. Khan and R. A. Khan, “Revisiting software security risks,” Journal of Advances in Mathematics and Computer Science, vol. 11, no. 6, pp. 1–10, 2015. [Google Scholar]
46. K. Sahu and R. K. Srivastava, “Revisiting software reliability,” Advances in Intelligent Systems and Computing, vol. 802, pp. 221–235, 2019. [Google Scholar]
47. R. Kumar, S. A. Khan and R. A. Khan, “Analytical network process for software security: A design perspective,” CSI Transactions on ICT, vol. 4, no. 2, pp. 255–258, 2016. [Google Scholar]
48. R. Kumar, S. A. Khan, A. Agrawal and R. A. Khan, “Measuring the security attributes through fuzzy analytic hierarchy process: Durability perspective,” ICIC Express Letters, vol. 12, no. 6, pp. 615–620, 2018. [Google Scholar]
49. K. Sahu and R. K. Srivastava, “‘Predicting software bugs of newly and large datasets through a unified neuro-fuzzy approach: Reliability perspective,” Advances in Mathematics: Scientific Journal, vol. 10, no. 1, pp. 543–555, 2021. [Google Scholar]
50. R. Kumar, S. A. Khan and R. A. Khan, “Software security testing: A pertinent framework,” Journal of Global Research in Computer Science, vol. 5, no. 3, pp. 23–27, 2014. [Google Scholar]
51. R. Kumar, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al., “A knowledge-based integrated system of hesitant fuzzy set, AHP and TOPSIS for evaluating security-durability of web applications,” IEEE Access, vol. 8, no. 8, pp. 48870–48885, 2020. [Google Scholar]
52. M. T. J. Ansari, A. Baz, H. Alhakami, W. Alhakami, R. Kumar et al., “P-STORE: Extension of store methodology to elicit privacy requirements,” Arabian Journal for Science and Engineering, pp. 1–24, Article in press, 2021. [Google Scholar]
53. R. Kumar, A. Baz, H. Alhakami, W. Alhakami, A. Agrawal et al., “A hybrid fuzzy rule-based multi-criteria framework for sustainable-security assessment of web application,” Ain Shams Engineering Journal, pp. 1–21, Article in press, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |