DOI:10.32604/csse.2022.023481

| Computer Systems Science & Engineering DOI:10.32604/csse.2022.023481 |  |
| Article |
Energy-Efficient Cluster in Wireless Sensor Network Using Life Time Delay Clustering Algorithms
1Department of Computer Science and Engineering, Knowledge Institute of Technology, Salem, India
2Department of Computer Science and Engineering, Christ University, Bangalore, India
3Department of Computer Science and Engineering, Kongu Engineering College, Perundurai, India
*Corresponding Author: V. Kumar. Email: vkumarme@gmail.com
Received: 09 September 2021; Accepted: 22 October 2021
Abstract: Through Wireless Sensor Networks (WSN) formation, industrial and academic communities have seen remarkable development in recent decades. One of the most common techniques to derive the best out of wireless sensor networks is to upgrade the operating group. The most important problem is the arrangement of optimal number of sensor nodes as clusters to discuss clustering method. In this method, new client nodes and dynamic methods are used to determine the optimal number of clusters and cluster heads which are to be better organized and proposed to classify each round. Parameters of effective energy use and the ability to decide the best method of attachments are included. The Problem coverage find change ability network route due to which traffic and delays keep the performance to be very high. A newer version of Gravity Analysis Algorithm (GAA) is used to solve this problem. This proposed new approach GAA is introduced to improve network lifetime, increase system energy efficiency and end delay performance. Simulation results show that modified GAA performance is better than other networks and it has more advanced Life Time Delay Clustering Algorithms-LTDCA protocols. The proposed method provides a set of data collection and increased throughput in wireless sensor networks.
Keywords: WSNs; Gravity analysis algorithm–GAA; life time delay clustering algorithms-LTDCA; end to end delay; energy efficient
The Wireless Sensor Network (WSN) will change the distributed network’s design to a highly self-organized network. In its network, the WSN integrates several smaller sensor nodes. It may feel possible to collect these events as soon as they are detected and generate areas to transmit survey results with access points, because it gives a significant generalization of the environment. The first and most important reason is the sensor network data. The WSN of the router protocols must interact with each other for different algorithms. The simplest possibility is that with a successful partnership, the routing protocol equipment can provide product estimates of energy contact costs. Data processing is a technology that transfers data to the center because data obtained from different nodes are strongly correlated and unnecessary information are avoided in the system.
Fig. 1 shows the total transmission distance using second sensor nodes. Each in their meeting with sensor node, sends their information to the base station. The sensor is located in proximity to the base station node. Therefore, long-distance data transmission can be performed through cluster heads. One of the well-known collection techniques has been proposed namely Low Energy Adaptive Clustering (LEACH) to increase the life of the network. The packet size is 1000 bytes. Packet overhead depends on the type of communication. The LEACH has two methods to improve clusters and cluster heads’ performance which uses a central method to determine the base station. This method reduces energy consumption and increases the rate of data packet transfer. In general clutseirng algorithms are categorized as Connectivity-based, Centroids-based, Distribution-based, Density-based, Fuzzy based and Constraint-based.
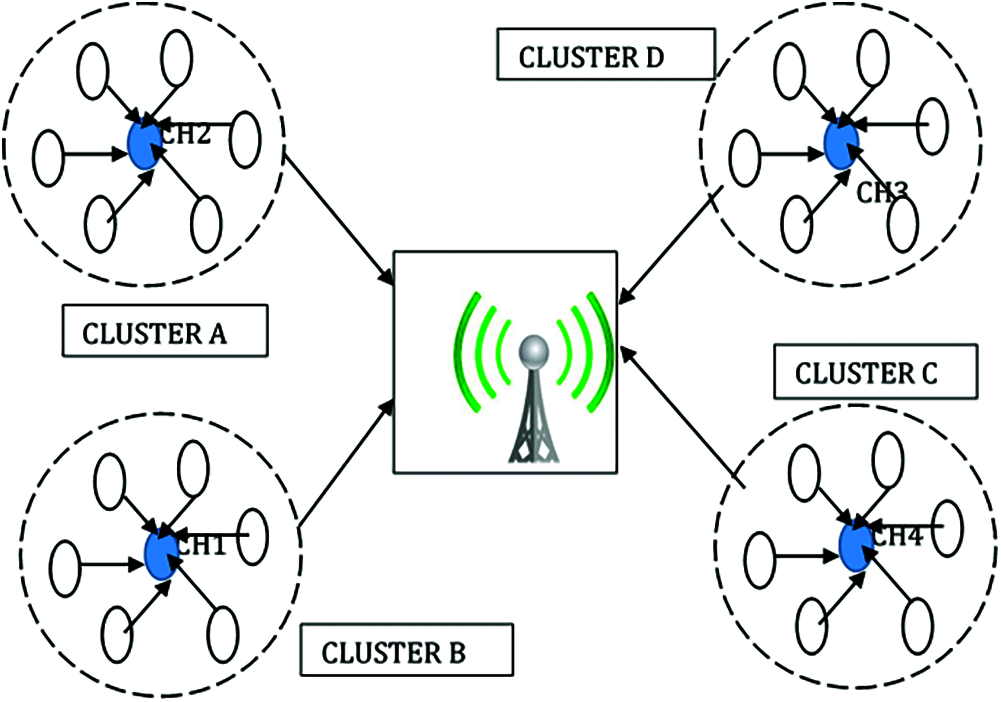
Figure 1: General architecture
The number of nodes is settled and the heroes of the time will not change in the process. It has also been proven to be an NP optimization problem for clustering methods. One of the most obvious problems is finding a set of cluster head nodes. Therefore, in traditional methods, the classic optimization algorithm could not solve this problem. To find an effective solution to this problem, commonly used optimization algorithms and formulas are not effective. Pattern recognition and economic evolution algorithms are used to solve classification problems in a strong search space. Traditional and theoretical methods do not provide timely solutions. Over the last twenty years, these technologies have become very popular. Many real-world issues including Things Internet usage can be solved with the currently available systems.
Heuristic search technology has been used for wireless sensor networks typically to improve the energy efficiency of processing clusters. The Particle Swarm Optimization (PSO) algorithm, using the system, has suggested a hierarchical set of remaining energy cluster heads in the cluster which fit the function’s exact purpose which is defined in the system. A new method is developed to improve the network’s efficiency by using a particle swarm algorithm for an optimal number of cluster heads. Eligible members for the multi-objective function are defined as the effective evaluation of nozzles. Then, to find an acceptable solution to this fitness activity, the taboo search algorithm is incorporated into the public safety algorithm. The proposed algorithm is used especially in systems that are effective for medical facility managers. Chapter 1 describes the WSN concept and feature analysis, followed by the proposed clustering time series model planned for real-time records analysis.
Because of the size of traditional WSN, virtualization technology [1] has become incompetent and the Hardware/software limitations and heterogeneity occur. To overcome the software agency system implements in this policy [2], it is expected to overcome vague clusters of structures. In this task, the interference plus noise ratio is selected based on the interference plus noise ratio information details [3].
In the existing work, sensor nodes can easily fail. Their energy is lower and the coverage of the wireless sensor networks link scheduling and format of the key. There are many studies in which different deployment strategies and node focuses are discussed [4,5]. This exploration provides the energy balance of practical and theoretical engineering. Shortcut keys are wired, hence, wireless sensor networks are used in flood monitoring and tracking applications on the battlefield. Network loss in the shortcut leads to damaging of the data [6].
For the long geological data acquisition [7], the population of reflection and wireless sensor network (WSN) are suitable [8]. In this article, some sensor networks can be used for the actual design and implementation of the complete wireless sensor network architecture. The significant improvement, with the current ensemble’s structure in the season, there are more challenging issues [9] Many methods have been proposed to improve the collection efficiency [10,11]. The methods of data collection, such as the stated size of the previous task and the formatting of this data making manual analysis impossible, are encouraging in the event movement [12]. Due to the wide range of potential applications and their unique challenges, wireless sensor networks (WSN) have attracted many researchers [13].
This paper presents the way to select CH nodes and data transfer details to get the shortest path between the base stations including the initial network system. MHEECA algorithm is shown in detail [14,15]. In this paper, a centralized PA protocol is proposed for wireless sensor networks. The purpose of this protocol is to find the optimal number of cluster heads [16]. In addition, the deal seeks to increase network range [17], energy efficiency and output. We are investigating the proposed protocol for the actual network and energy consumption patterns used [18]. In the previous paper discussion, the data analytical model proposed get an average delay of distribution of information with some numerical examples [19]. In another previous method, the main focus was to consider the use of many attributes to make CH specialized decisions in order to efficiently select production and technology for data routing [20]. The existing work’s system performance is dependent on the allocation of a delay element with a different end-to-end delay, thereby the overall system performance may get affected as the delay allocation of one component affects the other components [21]. The surevy provides the following conclusions:
a.The dynamic nature of node mobility need to be considered
b.The motion nature of the nodes can be related to the gravity aspects of the environment
c.The model can be evaluated in terms of throughput and delay
3 Implementation of the Proposed Method
Current technology and standard Gravity Analysis Algorithm (GAA) are used in equipment processing and some relevant preliminary data from the sample application are also discussed in this section. Many devices at the edge of the mosaic are located approximately in the target area [22]. In this method, a strategic plan is devised to maximize throughput and improve Life Time Delay Clustering Algorithms [23]. The corresponding clusters with pointed ends are divided into blocks. Each sensor node collects some environmental information and each node consists of a small battery cell and a fixed location based on the end of the area which learns the ultimate delay reduction and energy saving. The Network life time is based on the communication and overhead in communication [24]. The nodes will go to sleep stage during non transmissions. The LDTC proposed in the paper will handle the infrastructure related problems in communication. The proposed work differs from exisiting one in providing a network life time that is connected to the delay in communication [8].
In Fig. 2, Stage 1 describes the construction of several spatial scales on the WSN network in detail. Stage 2 describes the imbalance distribution and bandwidth usage in the WSN service and GAA. In stage 3, LDTC service support provides a balance of infrastructure reconstruction site security. GAA sets lifetime delay clustering algorithms. It has cluster node details network function. The various advantages of the entire network lifecycle are restoring throughput and end-to-end delay at the end of the package which increases the measuring performance and reduces the network of energy saving’s networks.
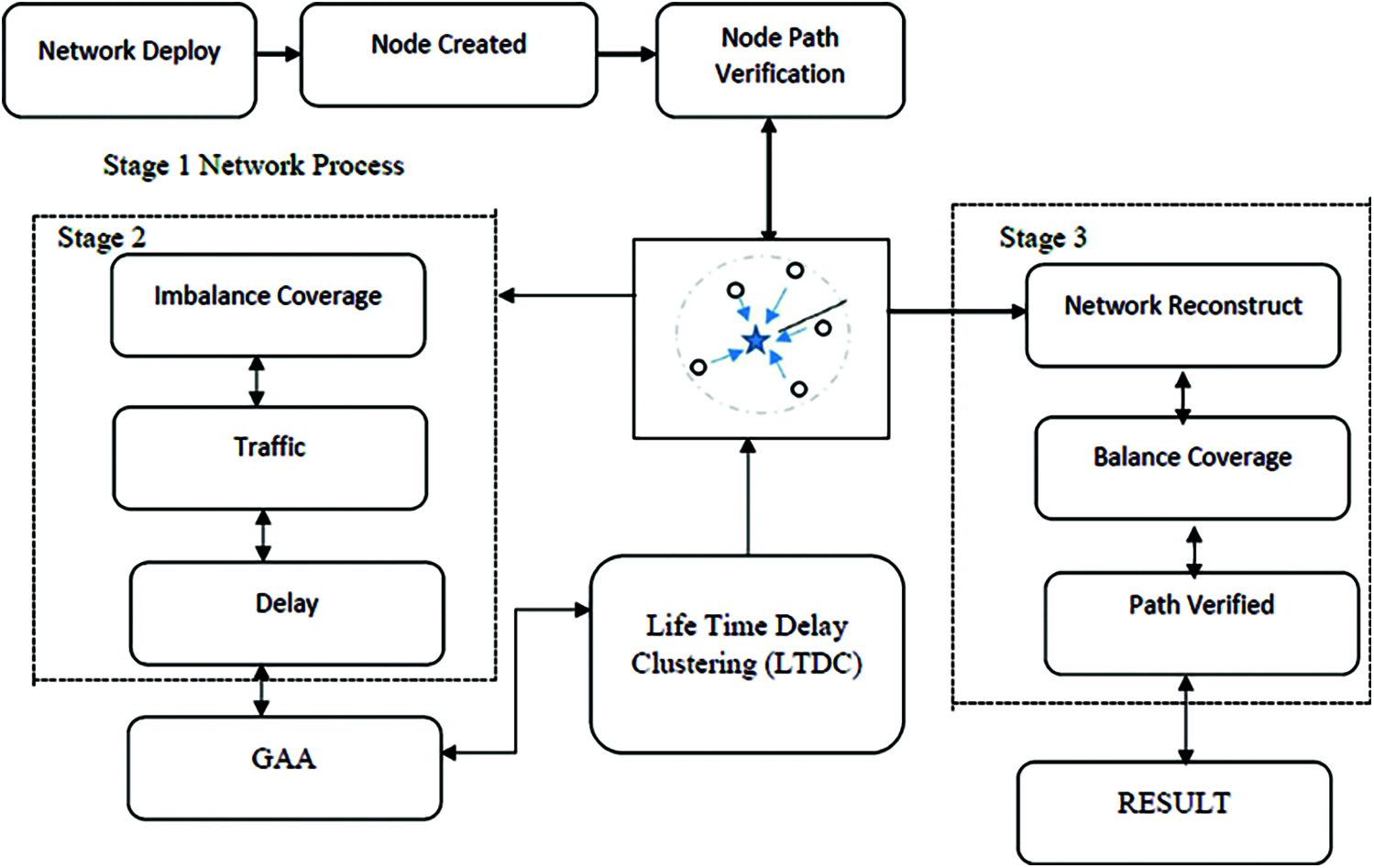
Figure 2: Proposed diagram using gravity analysis algorithm
3.1 Network Construction Model
WSN network construction model supported by data transfer nodes are set in different ways under different user’s conditions, once the realization is closely linked together with personal realizations. Whenever the system configuration is known, the network system state is reasonably stable. It indicates that the cluster head is clearly in storage and it has adequate fixed usage. The LTDCA algorithm is demonstrated to be effective, portable, and fully functional in prescribed application tests, even though the system can bring a little flexibility.
3.2 Imbalance Network Coverage Problem
The Imbalance Network Coverage Problem is based on direct or indirect high-quality WSN network. The WSN Networks need low energy consumption and connecting to such a list will be effective and will ensure safe data transmission [16]. However, the network does not guarantee access to the performance modes. Therefore, to maintain adequate execution, all the channel allocation issues need to be analyzed. Another issue is the difference in the execution of wireless sensor networks and network news reports. Cluster-based routing in wireless sensor networks and sensor nodes reduce power consumption and provide an effective method to improve life and durability. When evaluated to find an effective team, a wireless sensor network, network coverage, and capacity come up in a more energy-efficient manner. The nodes energy are set with a delat value that is based on the thteshold. However the nodes energy gets reduced and be available for communication. Each communication request can allow for node joining and node leaving based on packet transamission and loss. In this regard energy efficiency is handled by the model [11].
The parameters that are evaluated in general are:
Packet Delivery Ratio: Eq. (1) calculates packet delivery ratio. It is the ratio between the number of packets successfully received and number of packets attempted for transmission. It represents the success ratio of transmission over the wireless medium.
Delay: Delay refers to the average time taken to complete the end to end transmission of data packets from source to destination in the network using Eq. (2).
where n is number of transmitted packets
Throughput: Throughput outcomes the number of bits transmitted per unit time. It is calculated from the size of the data packet and total number of received data packets with the transmission duration using the Eq. (3).
3.3 Network Reconstruction Based on GAA
The Network reconstruction is supported network traffic issues like hard node issues, one of the most advanced gravity study algorithms such as a complete search for space in the security area, and the classic techniques. To find the best solution at the right time, they will actively use the GAA, a reasonable choice than to close. They can be either continuous or differentiated. The gravity algorithms are efficient as they communicate and interconnect using the motion characteristics of the network model. The node mobility can be learnt based on the motion. The clustering algorithms do not consider the motion of the nodes. Hence their measures do not connect to the node mobility [3]. By maintaining the configuration parameters during monitoring and calculation, the gravity analysis method is used to improve efficiency. To find a good method, it is necessary to read the file browser that launches every Life Time Delay Clustering Algorithm (LTDCA). Therefore, the research capability of the system is to be very strong.
First, the Life Time Delay Clustering Algorithms:
The Network Coverage Area (NCA) is measured as follows:
Finally, Network Traffic (NT) input data is measured as follows:
The traffic can be categorized as regular and random traffic. The random traffic can be related to a distribution that can be varying over time. The model performance is improved in the proposed approach as gravity based algorithms consider the motion of the nodes in the network [10]. The packet drop is also reduced in the proposed algorithm. The traffic is also learnt at the cluster level and the error in transmission is minized.
3.4 Life Time Delay Clustering–LTDC Approach
In addition to the centralized approach, the supply distribution system that utilizes the benefits of implementing assistance can be found to solve the problems, the research clusters WSN reservation if the issue conforms with the study and life in response to the delayed group. The Network imbalance is reduced. This is done by increasing the path coverage using the verification method. The network path is also dependant on the verification process. The GAA parameter also considers the motion that controls the network traffic. End-to-end delay improves the cluster’s performance, efficiency, reduces energy-saving standards and demonstrates the process.
The sender generates the random number for the Network Construct (NC) and Network Reconstruct (NR),
The NC is a Network Construct to previous less energy of Network Reconstruction was formed.
If the verification succeeds, then the route path verification m is Network Construct then network,
The same Eq. (12) if extended to nodes with mobility can handle the dynamic nature of the network. However the network should also consider the speed of nodes as a factor while calculating the LTDC parameter.
The findings are being used to conduct research methodologies and computational efficiency to running from the NS2 Simulation tool. The parameters are presented in Tab. 1 for the different variables considered throughout the experiment. The parameters are presented in Tab. 1 for the different variables considered throughout the experiment. The NS2 is choosen as the existing Leach Algorithms is implemented in the same platform. The version also supports facility for new model generation with different distributions. 100 Sensor network nodes are connected to the network level. The wireless sensor nodes around the whole complex must travel at a frequency of 1.5 meters per second during the experiment. Network construction is dynamic with nodes energy being dynamically updated over time. The node behaviour is also supported by passion distribution based traffic in the network [5].
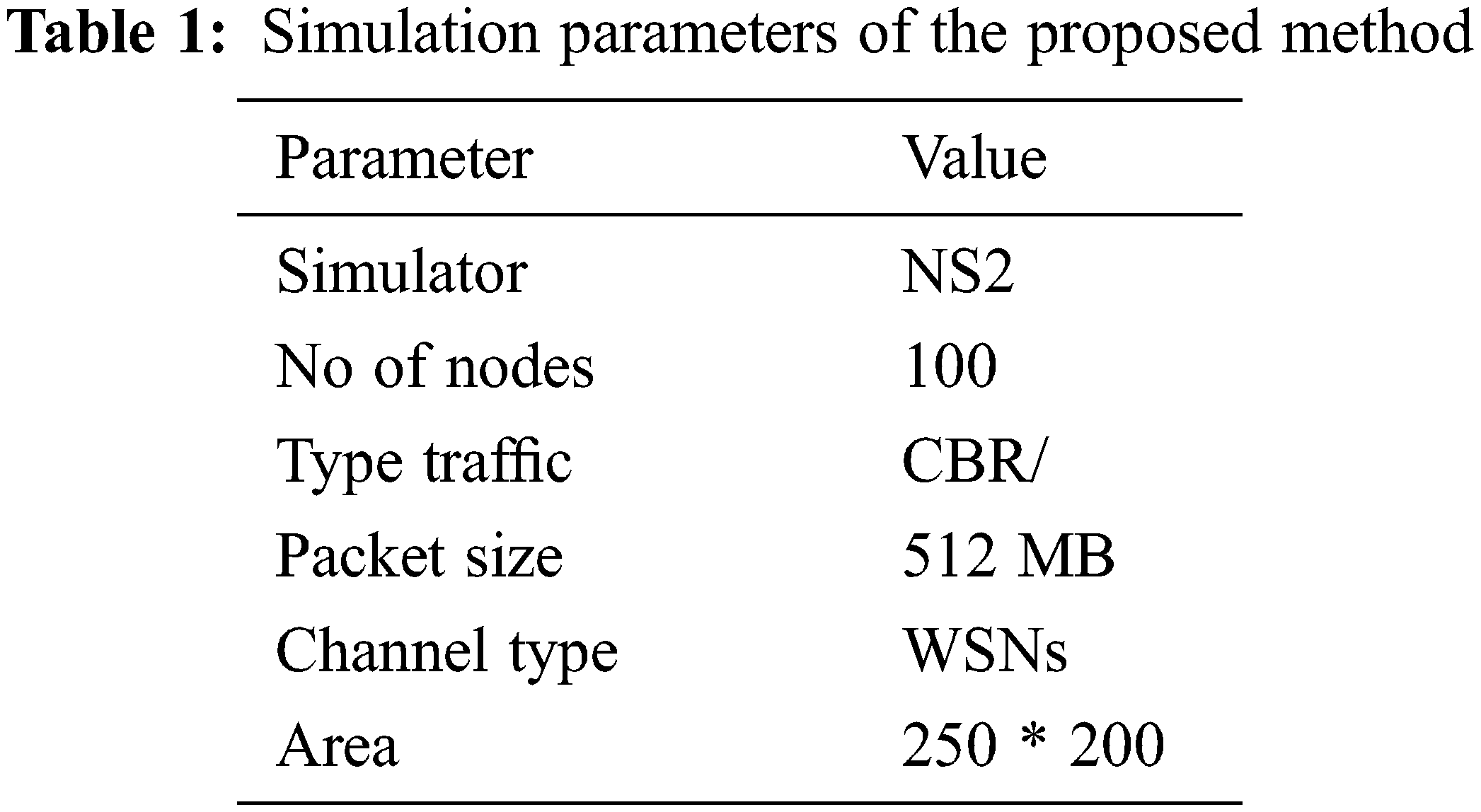
Tab. 1 shows the simulation parameters for performance evaluation of the proposed system. It is improved throughput and network performance
Fig. 3 shows the NS2 simulation result substantially, data for Life Time Delay Clustering (LTDC) data transfer for cluster routing processing performance. Therefore, it uses GAA, which reduces traffic with routing not supported in network simulation results, so the proposed system LTDC method efficient level of data energy is dealt with using only output.
Figure 3: NS2 simulation result
Fig. 4 shows the throughput performance ratio for the numbers of packets sends at a specific time. The simulations are presented in varying units of 20 to a maximum of 100 nodes. It is not extended beyond that as the gravity algorithms result in the node communication converged to local maxima and results in collisions. Hence the simulations are provided for a maximum of 100 nodes. The transmission packet between a sources to destination nodes can be calculated at the received time. In the proposed methods, LTDC is 97% of improving the throughput performance rather than Existing methods are SMDSRNG is 78%, SDSM is, and SLBR is 33%. The amount of packets transmitted has increseased with reduction in packet loss as shown in Fig. 4. The dynamic nature of the nodes have not reduced the performance of network.
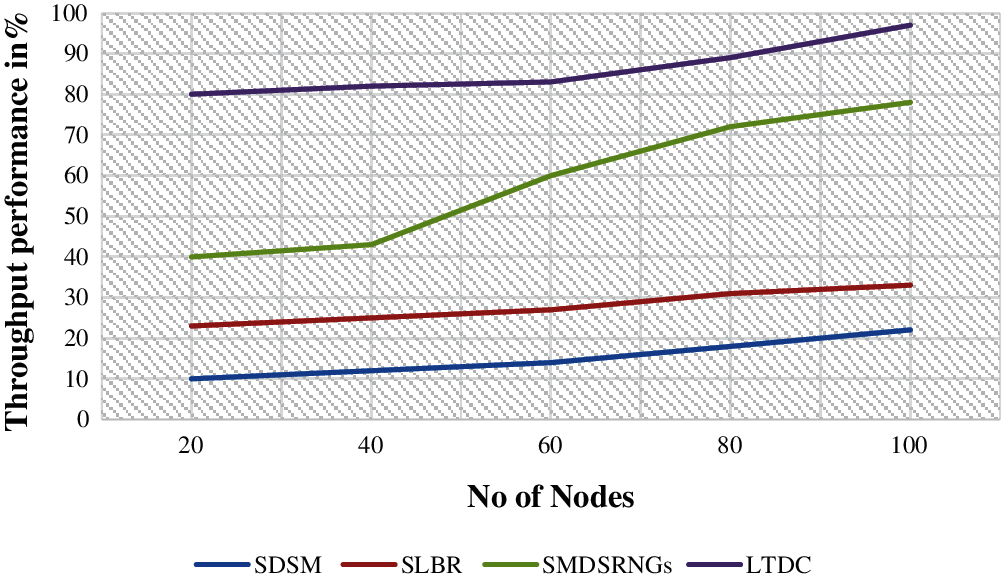
Figure 4: Throughput performance
Fig. 5 shows the Energy-efficient of the different methods compared to the previous and proposed methods; the total energy efficiency is successive matches with a 10-channel success cycle per second for 100 nodes. The energy efficiency is varying due to the gravity parameters that is varied from time time to time. The clustering mechanism in LTDC has a higher delay between 60 to 80 nodes. The proposed method of LTDC has reduced energy consumption, and it gave the high scalability.
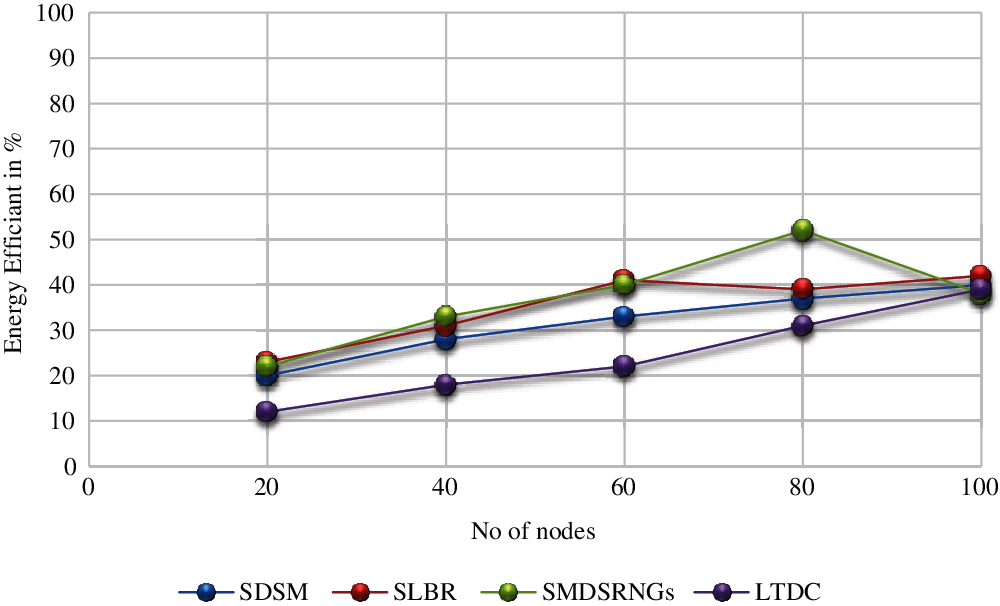
Figure 5: The energy efficient of different method
Fig. 6 shows the increased network lifetime compared to the previous methods. The existing methods are SDSM, SLBR, SMDSRNG is the minimum range of network lifetime performance. The proposed method of LTDC is the maximum range of increased life network lifetime.
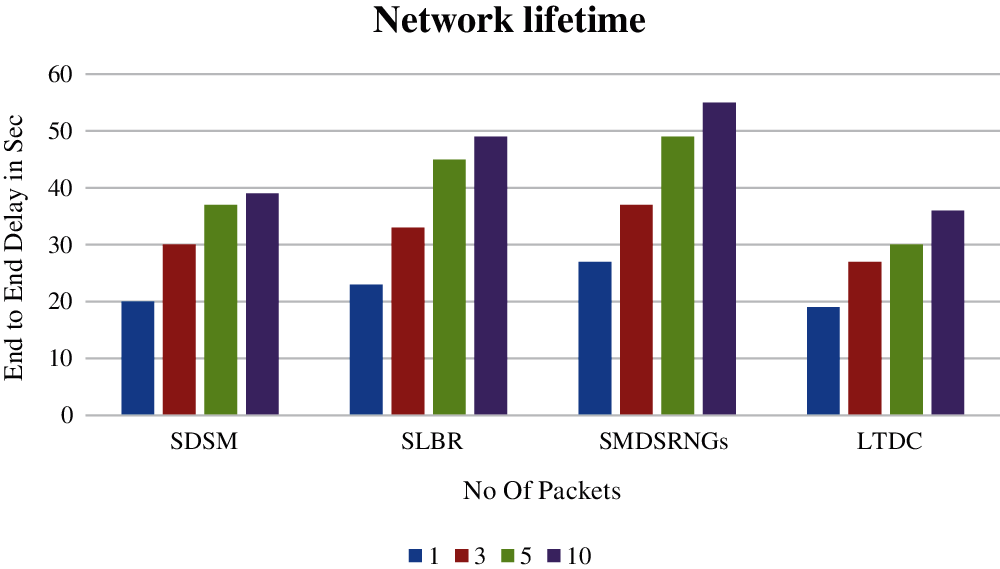
Figure 6: Network lifetime
The proposed method supports LTDC regular data collection methodology; it introduced new energy storage and load balancing. Simulation results also extend the network lifetime based on Life Time Delay Clustering Algorithms-(LTDCA) network nodes and have a balanced energy level. In terms of energy savings and offsets, the proposed method shows excellent performance as LTDC, the existing algorithms SMDSRNGs, SLBR and state-of-art clustering algorithms are compared SDSM. Simulation results were followed by the study of nearly 97% proposed method than the LTDC process for improved throughput performance. The previous method, SMDSRNG, pointed out that 78% SDSM compared to SLBR 33%. LTDC graphical raised in terms of throughput. The future enhancements include dynamic scheduling, hybrid energy management and election node based scheduling. The proposed algorithm can be extended to a real time application and the performance can be analyzed.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. G. Yıldırım and Y. Tatar, “Simplified agent-based resource sharing approach for WSN-WSN interaction in IoT/CPS projects,” IEEE Access, vol. 6, pp. 78077–78091, 2018. [Google Scholar]
2. I. S. Akila and R. Venkatesan, “A fuzzy based energy-aware clustering architecture for cooperative communication in WSN,” The Computer Journal, vol. 59, no. 10, pp. 1551–1562, 2016. [Google Scholar]
3. H. Feng and J. Dong, “Reliability analysis for WSN based on a modular k-out-of-n system,” Journal of Systems Engineering and Electronics, vol. 28, no. 2, pp. 407–412, 2017. [Google Scholar]
4. O. J. Pandey and R. M. Hegde, “Low-latency and energy-balanced data transmission over cognitive small world WSN,” IEEE Transactions on Vehicular Technology, vol. 67, no. 8, pp. 7719–7733, 2018. [Google Scholar]
5. M. T. Lazarescu, “Design of a WSN platform for long-term environmental monitoring for IoT applications,” IEEE Journal on Emerging and Selected Topics in Circuits and Systems, vol. 3, no. 1, pp. 45–54, 2013. [Google Scholar]
6. D. Huang, C.-D. Wang, H. Peng, J. Lai and C.-K. Kwoh, “Enhanced ensemble clustering via fast propagation of cluster-wise similarities,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 51, no. 1, pp. 508–520, 2021. [Google Scholar]
7. A. Ben Ayed, M. Ben Halima and A. M. Alimi, “Adaptive fuzzy exponent cluster ensemble system based feature selection and spectral clustering,” in 2017 IEEE Int. Conf. on Fuzzy Systems (FUZZ-IEEE), Naples, 2017. [Google Scholar]
8. D. Huang, C. Wang, J. Wu, J. Lai and C. Kwoh, “Ultra-scalable spectral clustering and ensemble clustering,” IEEE Transactions on Knowledge Data Engineering, vol. 32, no. 6, pp. 1212–1226, 2020. [Google Scholar]
9. J. Franklin, S. Wenke, S. Quasem, L. A. Carraher and P. A. Wilsey, “Streaming RPHash: Random projection clustering of high-dimensional data in a mapreduce framework,” in 2016 IEEE Int. Conf. on Cluster Computing (CLUSTER), Taipei, Taiwan, pp. 168–169, 2016. [Google Scholar]
10. Y. Zhang, H. Gao, S. Cheng and J. Li, “An efficient EH-wSN energy management mechanism,” Tsinghua Science and Technology, vol. 23, no. 4, pp. 406–418, 2018. [Google Scholar]
11. L. Han, “A multiple-hop energy efficient clustered algorithm for heterogeneous WSN,” in 2012 Fourth Int. Conf. on Multimedia Information Networking and Security, Nanjing, China, pp. 183–186, 2012. [Google Scholar]
12. R. S. Elhabyan and M. C. E. Yagoub, “Energy-efficient clustering protocol for WSN using PSO,” in 2014 Global Information Infrastructure and Networking Symposium (GIIS), Montreal, QC, Canada, pp. 1–3, 2014. [Google Scholar]
13. M. Ohnishi, C. Minamiguchi and H. Ohsaki, “On the performance of end-to-end routing in complex networks with intermittent links,” in 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, pp. 1157–1162, 2020. [Google Scholar]
14. Z. Ullah, “Energy-efficient harvested-aware clustering and cooperative routing protocol for WBAN (E-HARP),” IEEE Access, vol. 7, pp. 100036–100050, 2019. [Google Scholar]
15. C. Li, H. Xiong and D. Wu, “Delay–rate-distortion optimized rate control for end-to-end video communication over wireless channels,” in IEEE Transactions on Circuits and Systems for Video Technology, vol. 25, no. 10, pp. 1665–1681, 2015. [Google Scholar]
16. K. M. Daniel, R. Baalamurugan, Vijay and K. P. Arjun, “Energy aware clustering with multihop routing algorithm for wireless sensor networks,” Intelligent Automation & Soft Computing, vol. 29, no. 1, pp. 233–246, 2021. [Google Scholar]
17. K. M. Baalamurugan, D. Vinotha and S. Premkumar, “An efficient ant colony-based self-adaptive routing strategy for iot network model,” In: Bindhu V., Tavares J. M. R. S., Boulogeorgos A. A. A., Vuppalapati C. (edsInt. Conf. on Communication, Computing and Electronics Systems, Lecture Notes in Electrical Engineering, Springer, vol. 733, pp. 753–764, 2020. [Google Scholar]
18. S. Murugesan, T. Senthil Kumar, U. Priyanka, Sree and K. Abinaya, “Towards an approach for improved security in wireless networks,” International Journal of Computer Applications, vol. 1, pp. 9–13, 2013. [Google Scholar]
19. X. Yin, K. Q. Zhang, B. Li, A. K. Sangaiah and J. Wang, “A task allocation strategy for complex applications in heterogeneous cluster-based wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 14, no. 8, pp. 759–768, 2018. [Google Scholar]
20. Z. Tang, K. K. Liu, J. B. Xiao, L. Yang and Z. Xiao, “A parallel k-means clustering algorithm based on redundance elimination and extreme points optimization employing mapReduce,” Concurrency and Computation: Practice and Experience, vol. 29, no. 20, 2017. [Google Scholar]
21. U. Kanimozhi and D. Manjula, “An intelligent incremental filtering feature selection and clustering algorithm for effective classification,” Intelligent Automation and Soft Computing, vol. 24, no. 4, pp. 701–709, 2018. [Google Scholar]
22. A.Vishnu Priya, A. Kumar Srivastava and V. Arun, “Hybrid optimal energy management for clustering in wireless sensor network,” Computers and Electrical Engineering, vol. 86, no. 9, pp. 1–10, 2020. [Google Scholar]
23. K. Imed, K. Ahmed and L. Pierre, “A clustering-based approach for balancing and scheduling bicycle-sharing systems,” Intelligent Automation and Soft Computing, vol. 24, no. 2, pp. 421–430, 2018. [Google Scholar]
24. S. S. Li, T. J. Cui and J. Liu, “Research on the clustering analysis and similarity in factor space,” Computer Systems Science and Engineering, vol. 33, no. 5, pp. 397–404, 2018. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |