DOI:10.32604/csse.2022.026948

| Computer Systems Science & Engineering DOI:10.32604/csse.2022.026948 |  |
| Article |
Evidence Mechanism of Power Dispatching Instruction Based on Blockchain
1China Electric Power Research Institute, Nanjing, 210003, China
2Nanjing University of Aeronautics and Astronautics, Nanjing, 210008, China
3State Grid Jibei Electric Power Company, Beijing, 100053, China
4School of Engineering and Technology, University of Hertfordshire, Hertford, AL10 9EU, UK
*Corresponding Author: Jian Geng. Email: wanghaonanhangcs@163.com
Received: 07 January 2022; Accepted: 02 March 2022
Abstract: With the development and application of energy Internet technology, the collaborative interaction of “source network, load and storage” has become the development trend of power grid dispatching. The large-scale access of renewable energy on the load side, the unified management of adjustable loads, and the participation of multiple parties in energy operations have put forward requirements for the safety, credibility, openness, and transparency of the load dispatching environment. Under the environment of carbon emission reduction, the paper proposed an architecture of the scheduling data blockchain, based on the in-depth study of blockchain. Moreover, smart contracts are used to realize the application scenario of load dispatching instruction evidence on the blockchain. The content and storage mode of scheduling instruction evidence on blockchain are studied. And different storage modes are adopted according to the actual needs. And the smart contract system realizes the evidence generation of power dispatching instruction. This is the basis for the normal circulation of power dispatching instruction evidence. The research significance of this paper is highlighted as follows. The data and information generated in the power dispatching process are stored as evidence. On the one hand, it can provide a basis for settlement between power production and dispatching companies and power users. On the other hand, it can prepare for distributed transactions in the power grid under the environment of carbon emission reduction.
Keywords: Evidence mechanism; power dispatching instruction; blockchain
At present, the traditional economic and social development model characterized by the centralized utilization of fossil energy is gradually changing, and the third industrial revolution represented by new energy technology and Internet technology is emerging. At the same time, with the rapid development of ultrahigh-voltage direct-current (UHV DC) and new energy (wind power, photovoltaic) on a large scale, new technologies such as energy storage continue to emerge. While bringing significant economic, social, and environmental benefits, the operation of the power system will face increased uncertainty in the supply and demand balance of the new environmental system, and the existing energy and power will gradually not be able to adapt to the needs and development of future energy structure adjustments [1–3].
Under the traditional “source with load” dispatch mode, the power grid dispatching control method is relatively single, and the power-side regulation method is basically exhausted. However, load-side resources such as electric vehicles, smart building air conditioners, and electric heating are in a dormant state, and the interaction mechanism with the power grid has not yet been established. Therefore, in order to effectively expand the power grid regulation resources and take into account the two 50% requirements of the current and supporting the future national energy strategy transformation, it is urgent to promote the transformation of the traditional “source-on-load” dispatching model to the “source-network-load-storage coordinated dispatching control” model [4–6].
Different from the access and control of traditional power generation resources, in the future, massive load-side resources will be connected to the dispatching system via the Internet, and the response of load-side resources will have a certain degree of uncertainty. Therefore, in the process of external load resource perception, dispatching instruction issuance, and load resource response, there are problems that need to be solved urgently, such as multi-party mutual trust, data security, and business certification [7–9].
Blockchain technology, which has developed rapidly in recent years, is a distributed database that is maintained by consensus of the entire network and holds all historical transaction data. As a new type of application technology of the “Internet +” new business format, its time stamp, asymmetric encryption, distributed consensus, flexible programming and other technologies enable it to have decentralization, time traceability, autonomy, features such as openness and information that cannot be tampered with [10,11]. It can ensure that by mobilizing the enthusiasm of nodes in the entire network to achieve multi-node undifferentiated records, while ensuring data security, improving data transparency. So as to solve the problems of high cost, low efficiency, and insecure data storage under the traditional centralized mode.
The rest of the paper is organized as follows. Section 2 introduces the current situation and development trend of domestic and foreign research respectively. Section 3 introduces the power dispatching system based on load modeling. Section 4 introduces the evidence mechanism of the blockchain on power dispatching instruction. Section 5 introduces the evidence system of power scheduling instruction based on smart contract. Section 6 makes a final summary.
2.1 The Status Quo and Development Trend of Foreign Research
In recent years, foreign demand response has been transformed from a traditional public utility plan to a very valuable resource. Participation in the wholesale market has been significantly mature, which is conducive to maintaining grid stability and long-term resource adequacy and reliability. The foreign market mechanism is relatively mature, especially the incentive policies of load regulation are developing very rapidly [12,13]. Paid load response is the current mainstream load control mechanism including: 1) Fixed-rate peak shaving mechanism. Chile, Argentina, and Spain have adopted this peak shaving mechanism to pay additional fees for effective adjustable capacity during peak load periods to incentivize generators to invest in capacity. 2) Dynamic capacity rate mechanism. The British power market adopts this peak shaving mechanism, under which the tariff grades obtained by the generators are determined by the remaining available capacity of the system. In theory, it is a mechanism that is more attractive to power generation investors. 3) Capacity obligation mechanism. The pennsylvania-new jersey-maryland (PJM) power market and New England power pool (NEPOOL) power market in the United States can be classified into this category. The capacity obligations of the members of these markets are determined by a series of detailed market rules, and in the capacity market, the members undertake their capacity obligations by buying and selling capacity usage rights. 4) Only the electricity charge mechanism. The Norwegian and California electricity markets do not have a clear capacity fee, but in their integrated ancillary service market, marginal capacity providers will be increased. Of course, this is only a secondary function of the ancillary service market. Its primary purpose is also to provide the necessary resources for the safe and efficient operation of the system.
At present, a mature power market mechanism has been established abroad, and on this basis, the focus is on the research of demand-side response and response models. Literature [14] regarded the demand response resource as the correction resource for the intraday dispatch plan, which is used to balance the deviation of the day-ahead power generation plan and the load measurement in the intraday forward-looking time window and uses a weighted method to control the impact of the forecast error on the system cost with the change of the time scale. On this basis, a forward-looking scheduling model that takes into account demand response was proposed. Literature [15] analyzed critical peak pricing with load control (CPPLC) method, and built a multi-objective mixed integer linear program (MMILP), and obtained the lowest cost day-ahead unit combination considering the peak electricity price load control through the ε-constraint multi-objective optimization method. Some provinces and cities in my country also implemented a peak electricity price mechanism for large industrial users during the summer and winter peak periods and achieved good peak shifting effects. Literature [16] modeled the load with multi-period response characteristics. According to the response characteristics of the load to real-time electricity prices, a safety-constrained unit commitment model under real-time demand response was established. The calculation example analysis showed that demand response can reduce peak load. To reduce system operating costs and carbon emissions, users can further reduce network congestion by changing electricity consumption behavior. Literature [17] regarded dispatchable users and distributed power sources as participants in the electricity market and established a joint dispatch model for distributed generation and demand response. 66 distributed power sources and 218 users were optimally dispatched. Literature [18] proposed an aggregation model of air-conditioning load and designed a control strategy for air-conditioning load group participation in demand response. Through verification on the GridLAB-D platform, it was found that large-scale air-conditioning load group participation in demand response can achieve power system frequency correction. And shaving peaks and filling valleys. Literature [19] studied the residential load dispatching under the real-time electricity price environment. Through refined modeling of different types of residential loads, while considering the uncertainty of electricity price and photovoltaic output, the residential load was established with the goal of minimizing electricity costs. Optimize the scheduling model. Literature [20] established a day-ahead optimal scheduling model for electric vehicles to participate in demand response. The model focused on the interaction strategy between electric vehicles and the grid and designed a variety of demand response projects such as load reduction and load transfer.
Generally speaking, foreign research on load regulation mainly focuses on incentive policies, load dispatch, and the use of flexible load resources to participate in load peak shaving, etc. There are relatively rich research cases. Measures such as the introduction of various incentive policies, the establishment and optimization of load response models, and the adjustment of electricity prices in different periods have effectively improved the flexibility of load regulation.
2.2 Current Status and Development Trend in China
In terms of load control, the domestic started late, but some research results have also been achieved. Literature [21] proposed the concept of power dispatch, considering the integration of power use incentives, interruptible loads, electricity price response and other power dispatch methods, established an integrated power generation and use dispatch model with wind power systems, and used heuristic dynamic programming algorithms to the model was solved. Literature [22] considered the diversity of power consumption patterns and the willingness to choose, based on the load curve predicted by the user response principle of the time-of-use electricity price based on consumer psychology, and considered the coordination and optimization of interruptible reserve and generation-side reserve. Comprehensively weigh the interests of all parties, select the optimal time-of-use electricity price and optimal interruptible reserve capacity that minimize the cost of power generation, and formulate a power generation dispatch plan based on this, and establish a power generation dispatch model that takes into account user-side interaction under the smart grid. Literature [23] based on the establishment of electricity price and incentive demand response models, taking into account the uncertainty of wind power output, established a wind power consumption opportunity constraint model based on demand response, and proposed to use stochastic simulation particle swarm algorithm to solve the model. Literature [24] was to jointly optimize the operation of electric vehicles and dispatchable loads, and still obtained better market competitiveness through mutual complementation. Literature [25] carried out research on the flexibility of power system dispatching specifically for virtual power plants connected to the distribution network. In order to study the scheduling flexibility of its access to the distribution network, the flexibility mathematical models of thermal power and Energy Storage System (ESS) were established respectively. Aiming at the risk of wind curtailment and load shedding of vector packet processing (VPP), an economic dispatch model for VPP access to the distribution network is established, and the system's comprehensive dispatch flexibility index was proposed to reflect the complementarity of flexible resources in the system. Literature [26] aimed at the provincial power grids with a relatively high proportion of nuclear power units. In order to improve the safety and flexibility of its operation, the power generation side and demand side peak shaving resources were combined. A three-stage joint peak shaving model of nuclear-fired-virtual power plant was established. The model adopted the equivalent load method to deal with the output of wind turbines, and introduced a carbon trading mechanism, analyzes operating costs from both economic and low-carbon aspects, and took the lowest cost of system joint peak shaving as the optimization goal. A three-stage scheduling method was adopted to determine the optimal peak-shaving mode and peak-shaving depth of the nuclear power unit according to the system requirements, and effectively smooth the forecast error of the equivalent load. Through the coordination and optimization of dispatching between virtual power plant and nuclear power-thermal power, the system's peak shaving pressure can be relieved, the start-stop peak shaving of thermal power units can be reduced, and the frequent output changes of generator units due to load forecast errors can be effectively avoided, which reduces the operating cost of the system. Carbon emissions balance economic and environmental benefits. Literature [27] proposed the concept of power utilization scheduling, considering the integration of power utilization incentives, interruptible loads, electricity price response and other power utilization scheduling methods, established an integrated power generation and utilization scheduling model including wind power systems, and used heuristic dynamic programming algorithms to the model was solved. Literature [28] first established a user peak avoidance scheduling potential index system and divided multiple users into different scheduling groups through cluster analysis. Based on the schedulable potential and peak avoidance willingness, the peak avoidance scheduling sequence was formed, and the peak avoidance scheduling sequence was formed for one hour respectively. A secondary group coordination optimization strategy of the standby group and the control group was proposed after 4 h.
In summary, the domestic research in the direction of load regulation started relatively late, but there are still many research results in this area. Many domestic research scholars focus on combining load characteristics with my country's electricity market mechanism and have made greater breakthroughs in theoretical research than in the past. China is currently in the initial stage of market development, and there are inevitably some problems in load regulation research [29]. At present, the focus of domestic load regulation is to solve the safety problem and cannot make full use of the flexible characteristics of load regulation. The lack of a complete market incentive mechanism, mostly load regulation is led by the government and State Grid Corporation. In general, domestically, focusing on the safety of large power grids and day-ahead power balance, exploration and practice have been carried out in precise load control and load dispatching, but there are obvious shortcomings in the coordinated control of source network load and storage, and the construction of market guarantee mechanisms.
3 Power Dispatching System Based on Load Modeling
Load modeling is the basis of power system analysis and control. Traditional load modeling studies mostly focus on the scale of nodes and divide the load into dynamic load and static load. For static loads, the “constant impedance + constant current + constant power” model (ZIP) is used to describe the voltage-current characteristics of the load, while the dynamic load model requires the use of differential algebraic equations to describe the complete characteristics of the load. General load nodes include both static load and dynamic load, and a synthetic load model (SLM) composed of static load + motor is often used to describe load characteristics. For various types of loads, the parameters can be identified through the observation data after the disturbance test. For static load, it is necessary to determine the voltage factor, frequency factor and the proportion of each ZIP and other parameters. For the motor, it is necessary to determine the various parameters of its equivalent circuit. For the SLM, it is necessary to determine the dynamic and static load. For the static load, it is necessary to determine the voltage factor, frequency factor and the proportion of each ZIP. With the expansion of the scale of the system, it is neither realistic nor necessary to establish detailed models for each node and analyze them separately, and the modeling technology has gradually developed to the stage of wide-area overall modeling. One solution for wide-area overall modeling is to first determine the feature amount of node classification. Secondly, classify the nodes of the whole system according to the characteristics of each node. In each type of node, select typical nodes to conduct in-depth modeling research and determine the parameters of typical nodes. Finally, the typical parameters are extended to all nodes of this type.
3.2 Static Model of Comprehensive Load
In the power system simulation calculation, the set of all users supplied by the bus or line of the substation is called the comprehensive load. The relationship between the power absorbed by the integrated load from the grid and the bus voltage and system frequency is called the integrated load characteristic, and the mathematical equation describing this characteristic is the static load model.
The basic form of the power function model is
where U is the actual operating voltage; U0 is the normal operating voltage when there is no disturbance, generally the rated voltage UN; f0 is the normal operating frequency when there is no disturbance, generally the rated frequency of the system is 50 Hz; P and Q are actual active power and reactive power; P0 and Q0 are the load power corresponding to U0, f0 or (UN, fN), that is, the power when the voltage and frequency are at the rated value; pu, qu, pf and qf are static characteristic parameters.
According to practical experience, a number of surveyed users who can reflect the production characteristics of the industry are selected for investigation in each industry. Then through fuzzy clustering method, the actual atypical users are removed, and the surveyed users are classified and clustered.
In order to determine the industry's load structure, the capacity-weighted average method is used to calculate the component ratio of the industry's comprehensive users.
Assuming that each typical user has n types of components (electrical equipment), then there are
where Kj represents the proportion of the capacity of type j components in the industry; kij represents the capacity ratio of the j-th component of the i-th typical user; Pi represents the total component capacity of the i-th typical user;
Once the industry user's load structure, that is, the component types and corresponding proportions, is determined, and the average characteristics of the components are known, a comprehensive load model for the industry can be established.
Assuming that there are n types of electrical equipment in the industry. The power of the i-th electrical equipment is Pi, Qi. The static characteristic coefficients are pui, qui, pfi, qfi. Then the characteristics of category i electrical equipment are
The total load power of the industry is
So as to obtain
where
4 Evidence Mechanism of Blockchain on Power Dispatching Instruction
4.1 Evidence Architecture of Power Dispatching Instruction
Comprehensively consider the characteristics of controllable load data storage in different load regulation scenarios such as peak shaving, frequency modulation, and standby, and design the chain range of dispatching instruction vouchers. Taking into account the cost of data storage and the degree of privacy of information, while considering the technical characteristics of content storage, hash value storage, and address storage, research the method of scheduling instruction vouchers on the chain.
By adopting the methods of content storage, hash value storage, and address storage certificate on-chain, a load-control-oriented dispatching instruction on-chain certificate storage system is constructed, and a load-control-oriented response alliance chain is deployed. After each node reaches a consensus after the dispatching instruction is issued, the dispatching certificate on-chain function is called to execute the chain. In the load response stage, the response result is executed by the on-chain function; the process framework of the whole process is shown in Fig. 1.
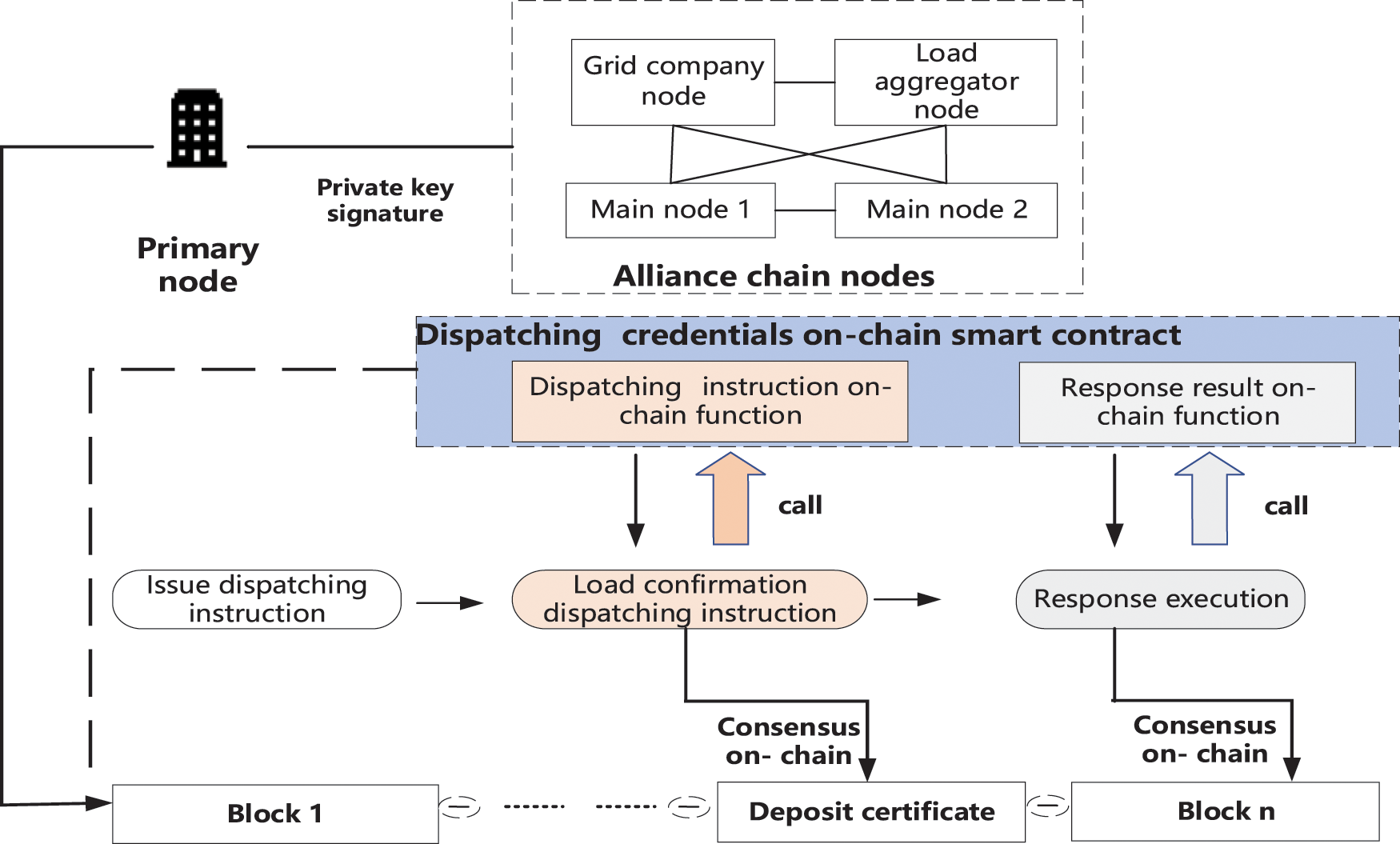
Figure 1: Architecture diagram of evidence for power dispatching instruction based on blockchain
4.2 Storage Mode of Power Dispatching Instruction on Blockchain
Through smart contracts, the certificate contents on the chain in different application scenarios are comprehensively analyzed. The smart contract is used to complete the establishment of the scope of the certificate on the chain, and comprehensively consider the characteristics of controllable load data storage in different load regulation scenarios such as peak shaving, frequency modulation, and backup. The architecture diagram on the certificate chain of blockchain-based regulatory commands is shown in Fig. 2.
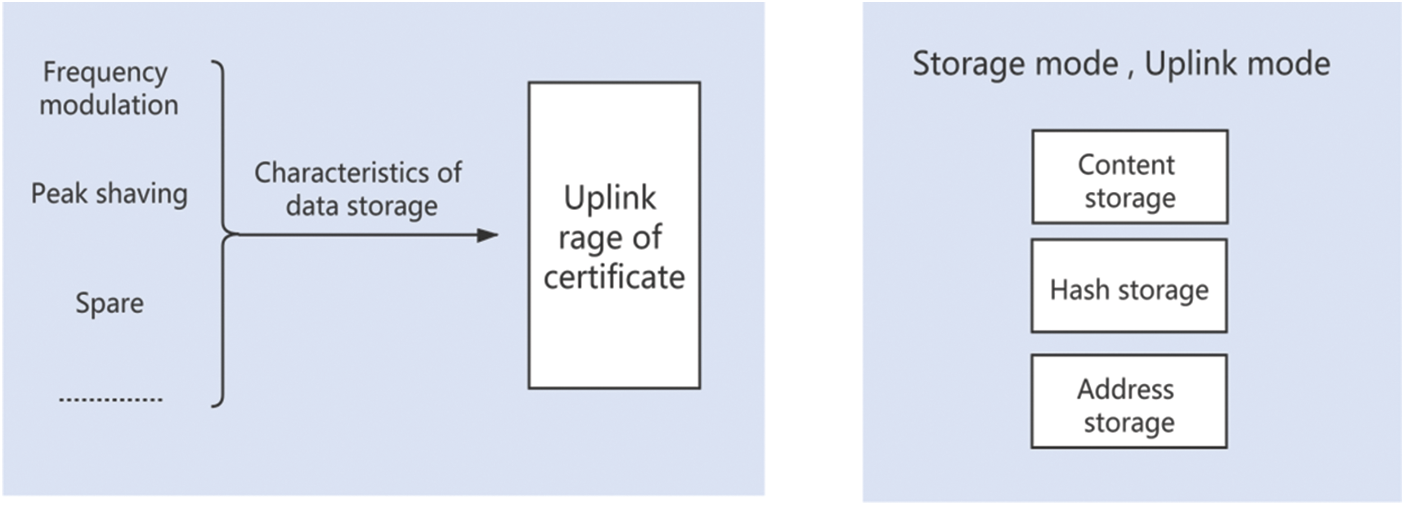
Figure 2: Blockchain-based regulatory command certificate on-chain architecture diagram
Storage Mode of Power Dispatching Instruction
Content storage: decentralized distributed storage
Hash certificate: storage on the blockchain
Address storage: on-chain storage
Use decentralized distributed storage to complete the on-chain storage of data. The storage structure is shown in Fig. 3.
① Create data fragments: The storage system divides the content certificate into several small fragments and distributes these fragments on the alliance chain nodes.
② Encryption of fragments: After the fragmentation is completed, each alliance chain node encrypts the local data fragments to ensure that no one other than the content owner can view or modify the data, no matter where the data is located, whether it is dynamic or static.
③ Generate Hash for each fragment: After completing the fragmentation operation, perform a Hash operation on the data fragment of each node, and generate a Hash ciphertext—a fixed-length encrypted string according to the data content and public and private key pairs.
④ Encryption of the fragments: After the fragmentation is completed, each alliance chain node encrypts the local data fragments to ensure that no one other than the content owner can view or modify the data, no matter where the data is located, whether it is dynamic or static.
⑤ Store the fragment node address information: After completing the hash calculation of the fragment information, the encrypted information and address information are packaged together to generate a result set and signed on the chain.
⑥ Generating and distributing fragment copies: After the node completes the encryption, it generates several copies of the encrypted fragmentation information and randomly distributes them to other nodes for storage. No single entity can own all storage resources or control the storage infrastructure. Only content owners have full access to all their data, no matter where these nodes are located.
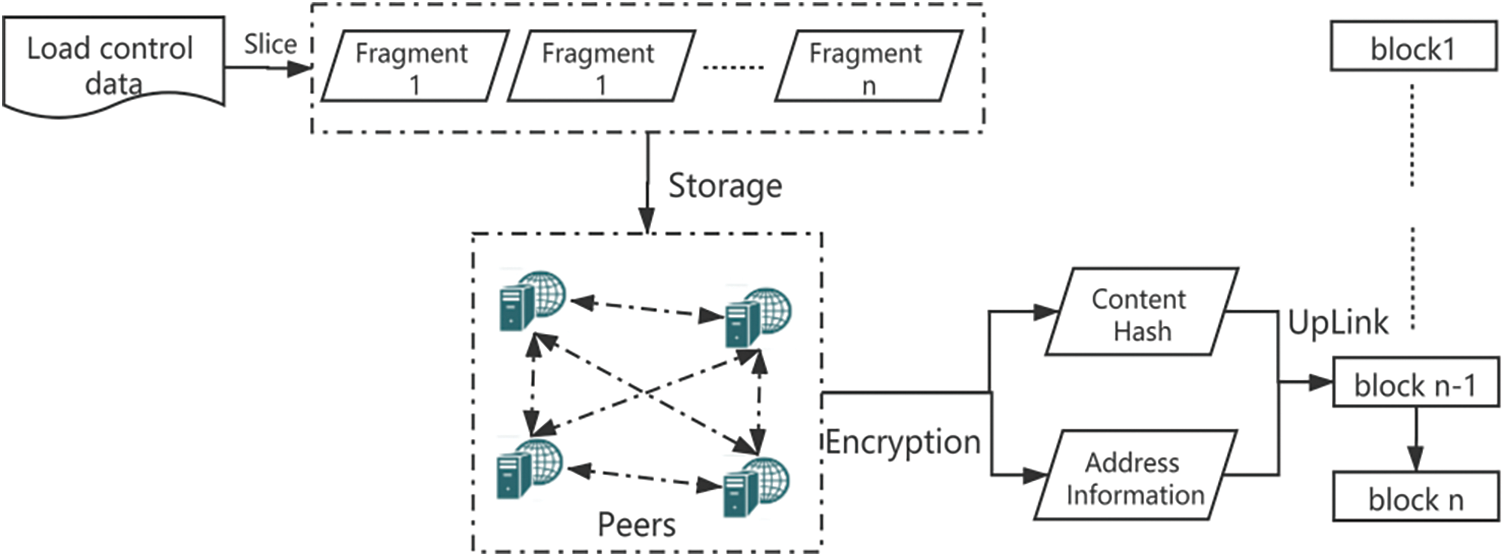
Figure 3: Load scheduling data storage structure
4.3 Advantages of Decentralized Storage
The centralized network can be simply understood as the existing cloud storage, which is a storage system with data storage and management as its core, which stores data into a storage space through the network. Users can access the space at any time and place through any networkable device. At the same time, the centralized storage method has many shortcomings.
(1) Data leakage problem
Centralized distributed storage stores the data in the server database, and the administrator of the network disk can directly view and even modify the content stored by the user from the management terminal. In view of this centralized management mechanism, it is difficult to guarantee the personal privacy of users, which has also led to various real cases of privacy leakage in the society.
(2) Transmission efficiency problem
With the development of the network world, the continuous increase of users and the continuous improvement of demand will bring great challenges to the storage network composed of only one or a few servers. With the increase of download/upload users, transmission efficiency has become an important issue.
(3) The risk of service suspension
In addition to the above risks, if the storage function provided by the server provider goes bankrupt or suspends the service, it will cause irreversible harm to the user.
In comparison, for data storage based on blockchain, a decentralized distributed approach will be a better choice. Decentralized distributed storage is to distribute data fragments to multiple network nodes. Each node in the blockchain only takes a part of its own storage space for distributed storage, and the server uses smart contracts to automatically allocate data storage.
In this mode, a large file will be divided into several small files for separate storage, and the storage host will perform operations such as encryption and copying. Compared with centralized storage, many advantages of this model are more suitable for data storage based on alliance chains.
(a) Privacy protection
In this mode, each node is only assigned to store a small piece of data and encrypt it autonomously. In this case, the content of the entire file cannot be cracked through one or two separate fragments, which not only ensures the privacy of the file, but also ensures that the data has a better ability to resist cracking in the case of hacker attacks.
(b) Lower cost/higher efficiency
Decentralized storage can give full play to the advantages of the sharing economy, mainly by using users’ remaining free hard disk space and unused upload bandwidth. In this way, these resources can be fully utilized, and while the owners of storage resources can obtain benefits, it also saves the construction cost of centralized storage and improves storage efficiency.
(c) Better scalability
Decentralized distributed storage can be well applied to the data storage of the alliance chain. On the one hand, it is a powerful data protection function, and on the other hand, it is good scalability. The data will not have a major impact as the nodes in the alliance chain are updated, and it perfectly meets the needs of the expansion and deletion of nodes in the alliance chain.
5 Evidence System of Power Dispatching Instruction Based on Smart Contract
5.1 Overall of the Prototype System
In the alliance chain, each service call is a process completed by the cooperation of the endorsement node, the ordering node, and the accounting node. The client first submits an application to the endorsement node for a simulated transaction. After obtaining enough endorsement responses, submit a formal transaction to the sorting node. And under the work of the sorting node and the accounting node, the block is generated, and the chain and the update of the database are completed. Taking the most representative Hyperledger as an example, the execution process is shown in Fig. 4.

Figure 4: Hyperledger execution process
(1) Endorsement
First, the server issues an application for load control credentials, performs endorsement operations, and submits information such as peak shaving, frequency modulation, and backup to the endorsement node, and the endorsement node verifies the information format, content, signature and other information. When enough endorsing node responses are collected, a formal transaction is generated.
(2) Test
After the official transaction is generated, the test smart contract is automatically executed. According to the content, format, structure and other information of the scheduling instruction, select the appropriate load control experimental scene, and perform simulation tests based on the test platform. In the test, the average upload time, capacity, throughput rate and other indicators of the on-chain certificate data are analyzed to verify the feasibility, reliability and completeness of the analysis of scheduling instructions on the chain. Finally, the result is returned to the server, and the server node decides whether the scheduling instruction is on the chain or not according to the received feedback information.
(3) Dispatching instructions on the chain function
In the case that the test result passes, the system executes the load confirmation scheduling instruction. In this instruction, run the smart contract for scheduling the voucher on the chain, and the contract completes the sharding, encryption, hash value calculation, and address value acquisition of the voucher data according to the data storage mode and on-chain method in 2.2. Finally, the data is signed, packaged and written into the blockchain.
(4) Response result on-chain function
After the load confirms that the execution of the scheduling instruction is completed and the result returned by the smart contract is received, the response operation is performed, and the response result on-chain function is called at this stage. After the execution of the smart contract on the chain in response to the result is completed, the result and data consensus are uploaded to the chain and written into the next block.
(5) Sort
Broadcast the result to the sorting node for sorting. The role of the sorting node is to sort the transactions transmitted by each channel according to the time and channel ID, generate new blocks, and broadcast them to the accounting nodes of the entire network.
(6) Accounting
After receiving the broadcast, the accounting node confirms the information, which includes functions such as verification of the legality and correctness of the smart contract and endorsement node signature, verification of the format of the proposed transaction request, and verification of the operation authority of each node. Finally, a new block is generated, and the block is linked to the chain to notify other nodes of the update of the block chain. At this point, the data on the chain is completed.
Different types of load control data voucher generation methods, structures, and voucher content are designed. Second, it clarifies the storage format of multiple copies of the load control data voucher for multi-party principal nodes. Third, it realizes the voucherization of load control scheduling instructions and response results. By designing the chain range of scheduling instruction vouchers, an encrypted storage mode and chaining method of load-controlled scheduling data are established. In addition, it has developed a load control-oriented scheduling instruction on-chain storage certificate test program and realized load control data certificate on-chain and on-chain data query.
Funding Statement: This work is supported by Science and Technology Program of State Grid Corporation of China under Grant (No. 5100-202155319A-0-0-00). Jian Geng and Hao Wang received the grant and the URLs to sponsors’ websites is http://www.sgcc.com.cn.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. X. Z. Tu, J. Xu and S. Y. Liao, “Power characteristic modeling for iron and steel industry,” Automation of Electric Power Systems, vol. 42, no. 2, pp. 114–120, 2018. [Google Scholar]
2. Y. J. Ren, J. Qi, Y. P. Cheng, J. Wang and O. Alfarraj, “Digital continuity guarantee approach of electronic record based on data quality theory,” Computers, Materials & Continua, vol. 63, no. 3, pp. 1471–1483, 2020. [Google Scholar]
3. C. P. Ge, W. Susilo, J. Baek, Z. Liu, J. Y. Xia et al., “A verifiable and fair attribute-based proxy re-encryption scheme for data sharing in clouds,” IEEE Transactions on Dependable and Secure Computing, vol. 21, no. 7, pp. 1–12, 2021. [Google Scholar]
4. X. P. Pan, X. X. Feng and P. Ju, “Generalized load modeling of distribution network integrated with direct–drive permanent–magnet wind farms,” Automation of Electric Power Systems, vol. 41, no. 4, pp. 62–68, 2017. [Google Scholar]
5. X. Qu, X. R. Li and J. Y. Song, “Composite load model considering voltage regulation of distribution network,” Transactions of China Electrotechnical Society, vol. 33, no. 4, pp. 759–770, 2018. [Google Scholar]
6. Y. J. Ren, K. Zhu, Y. Q. Gao, J. Y. Xia, S. Zhou et al., “Long-term preservation of electronic record based on digital continuity in smart cities,” Computers, Materials & Continua, vol. 66, no. 3, pp. 3271–3287, 2021. [Google Scholar]
7. K. Q. Zhang, H. Zhu and S. M. Guo, “Dependency analysis and improved parameter estimation for dynamic composite load modeling,” IEEE Transactions on Power Systems, vol. 32, no. 4, pp. 3287–3297, 2017. [Google Scholar]
8. C. P. Ge, W. Susilo, Z. Liu, J. Y. Xia, L. M. Fang et al., “Secure keyword search and data sharing mechanism for cloud computing,” IEEE Transactions on Dependable and Secure Computing, vol. 18, no. 6, pp. 2787–2800, 2021. [Google Scholar]
9. Y. J. Ren, J. Qi, Y. P. Liu, J. Wang and G. Kim, “Integrity verification mechanism of sensor data based on bilinear map accumulator,” ACM Transactions on Internet Technology, vol. 21, no. 1, pp. 1–20, 2021. [Google Scholar]
10. Y. J. Ren, Y. Leng, J. Qi, K. S. Pradip, J. Wang et al., “Multiple cloud storage mechanism based on blockchain in smart homes,” Future Generation Computer Systems, vol. 115, pp. 304–313, 2021. [Google Scholar]
11. T. Li, Q. Qian, Y. J. Ren, Y. Z. Ren and J. Y. Xia, “Privacy-preserving recommendation based on kernel method in cloud computing,” Computers, Materials & Continua, vol. 66, no. 1, pp. 779–791, 2021. [Google Scholar]
12. P. Ju, Z. L. Zhang and X. P. Pan, “Parameter observability analysis and its application to power load model,” Automation of Electric Power Systems, vol. 40, no. 5, pp. 32–37, 2016. [Google Scholar]
13. J. J. Hu, G. Y. Yang and K. Kok, “Transactive control: A framework for operating power systems characterized by high penetration of distributed energy resources,” Journal of Modern Power Systems and Clean Energy, vol. 5, no. 3, pp. 451–464, 2017. [Google Scholar]
14. Y. J. Ren, F. J. Zhu, S. P. Kumar, T. Wang, J. Wang et al., “Data query mechanism based on hash computing power of blockchain in internet of things,” Sensors, vol. 20, no. 1, pp. 1–22, 2020. [Google Scholar]
15. L. M. Fang, M. H. Li, Z. Liu, C. T. Lin, S. L. Ji et al., “A secure and authenticated mobile payment protocol against off-site attack strategy,” IEEE Transactions on Dependable and Secure Computing, vol. 21, no. 2, pp. 1–12, 2021. [Google Scholar]
16. J. J. Hu, G. Y. Yang and H. W. Bindner, “Application of network–constrained transactive control to electric vehicle charging for secure grid operation,” IEEE Transactions on Sustainable Energy, vol. 8, no. 2, pp. 505–515, 2017. [Google Scholar]
17. C. P. Ge, Z. Liu, J. Y. Xia and L. M. Fang, “Revocable identity-based broadcast proxy re-encryption for data sharing in clouds,” IEEE Transactions on Dependable and Secure Computing, vol. 18, no. 3, pp. 1214–1226, 2021. [Google Scholar]
18. Y. J. Ren, Y. Leng, Y. P. Cheng and J. Wang, “Secure data storage based on blockchain and coding in edge computing,” Mathematical Biosciences and Engineering, vol. 16, no. 4, pp. 1874–1892, 2019. [Google Scholar]
19. Z. L. Yang, K. Li and Q. Niu, “A comprehensive study of economic unit commitment of power systems integrating various renewable generations and plug–in electric vehicles,” Energy Conversion and Management, vol. 132, pp. 460–481, 2017. [Google Scholar]
20. M. Song, C. W. Gao and W. H. Su, “Modeling and controlling of air–conditioning load for demand response applications,” Automation of Electric Power Systems, vol. 40, no. 14, pp. 158–167, 2016. [Google Scholar]
21. C. P. Ge, W. Susilo, J. Baek, Z. Liu, J. Y. Xia et al., “Revocable attribute-based encryption with data integrity in clouds,” IEEE Transactions on Dependable and Secure Computing, vol. 99, pp. 1, 2021. [Google Scholar]
22. K. Mckenna and A. Keane, “Residential load modeling of price–based demand response for network impact studies,” IEEE Transactions on Smart Grid, vol. 7, no. 5, pp. 2285–2294, 2016. [Google Scholar]
23. J. Song, X. Pan and C. Lu, “A simulation–based optimization method for hybrid frequency regulation system configuration,” Energies, vol. 10, no. 9, pp. 1302, 2017. [Google Scholar]
24. Y. J. Ren, F. Zhu, J. Wang, P. Sharma and U. Ghosh, “Novel vote scheme for decision-making feedback based on blockchain in internet of vehicles,” IEEE Transactions on Intelligent Transportation Systems, vol. 23, no. 2, pp. 1639–1648, 2022. [Google Scholar]
25. J. J. Yang, J. H. Zhao and F. S. Wen, “Residential appliance identification and load modeling based on big data mining in smart grid environment,” Electric Power Construction, vol. 37, no. 12, pp. 11–23, 2016. [Google Scholar]
26. X. R. Zhang, X. Sun, X. M. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
27. X. Zhou, K. L. Li, Y. T. Zhou and K. Q. Li, “Adaptive processing for distributed skyline queries over uncertain data,” IEEE Transactions on Knowledge & Data Engineering, vol. 28, no. 2, pp. 371–384, 2016. [Google Scholar]
28. J. Y. Hu, K. L. Li, C. B. Liu and K. Q. Li, “A game–based price bidding algorithm for multi–attribute cloud resource provision,” IEEE Transactions on Services Computing, vol. 14, no. 4, pp. 1111–1122, 2018. [Google Scholar]
29. X. R. Zhang, W. F. Zhang, W. Sun, X. M. Sun and S. K. Jha, “A robust 3–D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |