DOI:10.32604/csse.2022.021845

| Computer Systems Science & Engineering DOI:10.32604/csse.2022.021845 |  |
| Article |
Secure Key Management Based Mobile Authentication in Cloud
1Department of Computer Science and Engineering, M.I.E.T Engineering College, Trichy, Tamilnadu, India
2Department of Computer Science and Engineering, Cihan University, Duhok, Kurdistan Region, Iraq
3Department of Computer Science and Engineering, Bapatla Engineering College, Bapatla, Andhra Pradesh, India
4Department of Computer Science and Engineering, Rajagiri School of Engineering and Technology, Kakkanad, Kerala, India
5Department Electronics and Communication Engineering, SACS MAVMM Engineering College, Madurai, Tamilnadu, India
6Department of Information Technology, Karaikal Polytechnic College, Varichikudy-Karaikal, India
7Department of Computer Science and Engineering, SACS MAVMM Engineering College, Madurai, India
*Corresponding Author: D. Yuvaraj. Email: yuva.r.d@gmail.com
Received: 16 July 2021; Accepted: 16 November 2021
Abstract: Authentication is important to the security of user data in a mobile cloud environment. Because of the server’s user credentials, it is subject to attacks. To maintain data authentication, a novel authentication mechanism is proposed. It consists of three independent phases: Registration, login, and authentication and key agreement. The user registers with the Registration Center (RC) by producing a secret number that isn’t stored in the phone, which protects against privileged insider attacks. The user and server generate a nonce for dynamic user identity and agree on a session secret key for safe communication. The passwords are not stored on the computer or provided in plain text, they are resistant to replay, guessing, and stolen verification attacks. The suggested protocol uses a one-way hash function and XOR operations, with the client having remote access to a large number of servers over a secure communication channel. Concentrates on HMAC and SHA3 for Collision Free Hashing and to overcome length extension attacks. HMACs are substantially less affected by collisions than their underlying hashing algorithms alone. So adding an HMAC to an MD5 or SHA hash would make it substantially more difficult to break via a rainbow table.
Keywords: Registration center; SIM; IMEI
Comprehension and characterizing client verification and approval among cloud Actors is another basic component of cloud engineering. The information housed by a cloud Ecosystem is not secured by cloud Actors [1]. Cloud customers decide a suitable cloud engineering and organization model to comprehend who are the clients, what information they are attempting to access and how the information is put away.
Authentication of the user is the process of identifying the user, by allowing them to enter the valid username and password (key). The user is authorized by the authorization server by comparing the user stored credentials at the database [2]. If the user credentials match then the client has benefits to get to the cloud administrations. If the user identifications do not match then the user is not permitted to access the cloud services.
Location-based authentication is a type of authentication given to a user based on the geographical location of the user. If there is a cloud customer in the U.S. and the user wishes to access the cloud services via a Web application or browser in his personal computer, the users are allowed to enter their credentials [3].
But in the background, the system verifies the geo-location and IP address, etc. If the user moves to another location the system identifies contrasting geo-location. After receiving the information from the user’s device, the program receives additional information for the next authentication stage before the identity is validated.
Implementing rules such as how a user should access resources or facilities is the key component of user authorisation. It comes within the context of user authorization. An authorized user can access various cloud system services providing user authorization is applied to each aspect of a cloud ecosystem’s lowest common denominator. Ensuring data security within the cloud information system is important [4]. It can undermine a program by giving users more power than they need. Protecting user information from the centre is important and must be incorporated in a security authorisation program’s security policies.
Execution of approval approaches is troublesome in a cloud framework. The client validation and approval server can execute the arrangements. The cloud foundation design is answerable for dealing with the application and verifying and supporting clients. The cloud infrastructure architecture is in control of managing, authenticating and approving users [5]. Cloud clients need to choose the best answer for their cloud framework, as client validation and approval procedures, strategies and systems are fundamental to making sure about their information in a cloud environment.
As technological advances as a standardized solution for fulfilling the operational needs of many organizations forms as cloud computing. There are different methods to authenticate users in the cloud environment, such as username and password, Mobile Trusted Module (MTM), Single Sign on (SSO), multifaceted confirmation, Public Key Infrastructure (PKI), just as biometric verification. This study proposes a key agreement protocol scheme for user authentication in the mobile cloud environment [6].
1.1 Mutual Authentication System
Industry and academia are more concerned about the concept of cloud computing. Cloud computing security has become a vulnerability hotspot, which is the main concern of current users worldwide regarding cloud computing [7]. To access the cloud services the cloud computing service centre is used to store and process the user credentials. The safety of the cloud computing system is affected if any private information is leaked or lost. To transmit data among clients and the server and ensure a private correspondence channel is required. In authentication, Identity is the cornerstone of the complete security architecture and the core technique for maintaining cloud computing system security [8].
For secure communication between users and servers, both entities have to authenticate each other by providing their identities. A secure private communication channel is created after the client proves his identity to the server and vice versa [9]. This method is broadly used by clients, as it helps to reduce online threats. Mutual Authentication is an effective tool for creating a stable client-server connection.
A discreet result of mutual authentication provides a secure channel to protect data from various online frauds such as denial of service and many more [10].
1.2 User Authentication System
In network security trusted computing technology has developed. In trusted cloud computing a sort of smart card password authentication is proposed [11]. This provides a secure communication channel for generating a final session key and guarantees the reality of cloud servers and user individualities and lets genuine users check the reliable position of the cloud server. It can also efficiently address the problem of uniqueness of the user in authentication and secure transmission between the server and the user in the cloud environment [12].
In the field of medicine, trustworthy protection schemes in cloud computing are crucial. The current medical system is introducing online services and digital technology to treat patients worldwide [13]. The use of MR images in brain tumour detection has been analysed in recent research [14]. The process for safe transmission of MR images through a cloud system has been shown.
A data security model that includes OTP generation for user authentication using HMAC (Hash-based message authentication code). It gives a comparative study of MD5 and SHA algorithms. This uses encryption algorithms to transform the original text into a hashed form that the third party can not anticipate. Eventually, Data quality can be seen as a major problem, which is seen as a threat to the cloud environment [15]. The proposed model typically replicates our data and stores it in different locations to overcome this problem.
The concept of a less public key cryptography certificate, which lies between identity-based approaches with the traditional PKI [16]. The concept is built from linear maps. This paper exposed about the appropriate model of the CL-PKE scheme is stable, assuming the Generalized Bilinear Diffie Hellman Problem (GBDHP) is difficult [17].
The various authentication methods to verify the user before granting access to resources has been analysed [18]. And also analysed authentication techniques together with the existing methods. Pron and Cons of each method are analysed to aware the experts who use the cloud services up to a maximum level [19].
It provides an overview of cloud computing, components (the cloud infrastructure and cloud applications [20] and discusses the problems of cloud computing in mobile applications and their possible solutions. A new authentication system for mobile customers using certified public keys by the user [21]. The mobile client was able to change the password with the registration center and analysed that the system will withstand different possible multi-server attacks.
The novel approach in the multi-server environment with an authenticated key agreement using smart cards with an efficient password [22]. The effective upgrade of greater security over Liao – Wang’s scheme [23]. The enhanced scheme’s stability, productivity and computational costs are well adapted to the practical application environment.
A protocol that would be practical and computationally efficient to implement. It only uses nonce, one-way hash functions are used with XOR operations in the implementation [24]. A protected method is proposed for the modification of the user credentials. The dynamic id based authentication was proposed for a multi-server environment [25]. The cloud user id can be changed dynamically and the session key is generated for further communication [26–28].
3 Proposed Authentication Protocol
The authentication protocol suggested the following participants are considered to be present. The Centre for Registration (RC), Ui and Sj Server. The proposed procedure consists of three different stages,
• User Registration,
• Login Stage
• Authentication Stage
As per the assumption given above, Ui’s registration with the RC is a one-time operation carried out via private communication through a secure channel.
Step 1: Ui chooses an identity IDi, Password PWi and generates a random number b to compute Ai = h(IDi⊕ b ⊕PWi). Ui then transmits IDi and Ai via the protected private communication channel to the RC for registration purposes.
Step 2: The RC computes Bi = h(Ai || x), Ci = h(IDi || h(y) || Ai), Di = h(Bi || h(x||y)), and Ei = Bi⊕ h(x||y). The RC stores {Ci, Di, Ei, h(y), h(.)} on the User’s smart phone.
Step 3: Now Ui computes Li = b ⊕ h(IMEI || SIM ||IDi || PWi) and keys Li into the smartphone. Now the phone contains the following details {Ci, Di, Ei, Li h(y), h(.)}. Here the secret random number b is not stored in the phone, instead, it computes Li and This helps us counter the privileged assault on the attack.
The above steps are shown in Fig. 1.
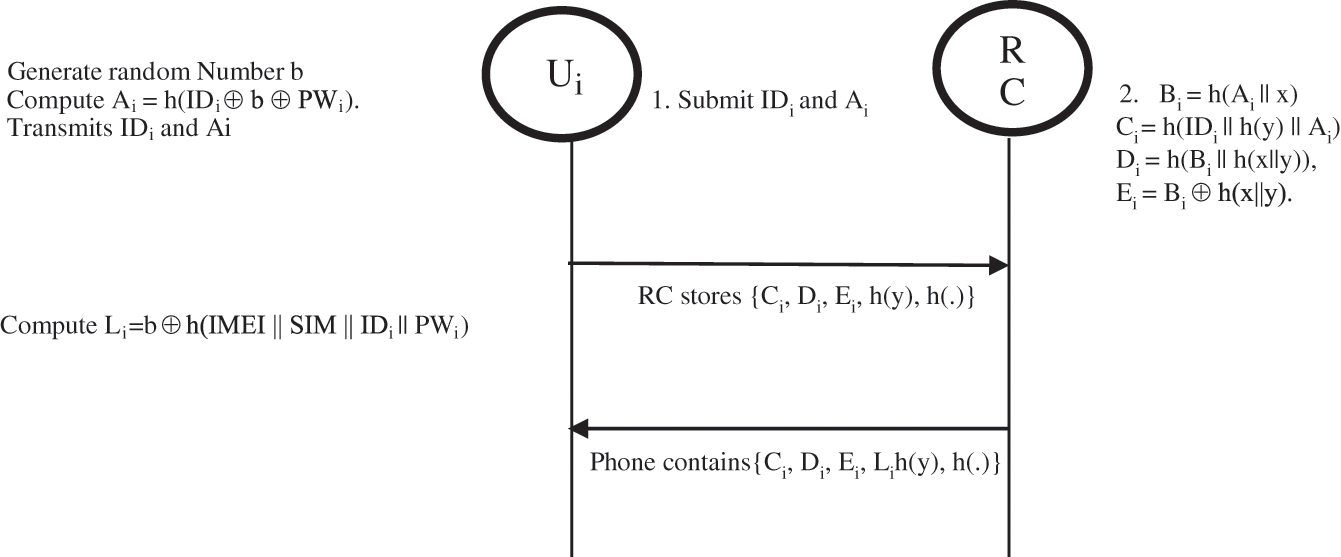
Figure 1: Registration phase
Here the User sends the Server a login request message.
Step 1: Uses the smartphone to initiate the login process by inputting the IDi and the PWi.
Step 2: The smartphone performs the computation b = Li ⊕ h(IMEI || SIM || IDi || PWi). It computes Ai = h(IDi⊕ b ⊕PWi) and Ci = h(IDi || h(y) || Ai) and matches whether the computed value Ci* matches with the Ci which is already available in the smartphone. If there is no match the session will be aborted.
Step 3: If match is found the smart phone will generate a nonce Ni based on the IMEI and the SIM number. The phone then computes CIDi = Ai⊕ h(Di || SIDj || Ni), Pij = Ei⊕ h(h(SIDj || h(y) || Ni), M1 = h(Pij || CIDi || Ai || Ni), and M2 = h(SIDj || h(y)) ⊕ Ni.
Step 4: User Ui sends a login request message {CIDi, Pij, M1, M2} to Sj via a public channel.
The above steps are shown in Fig. 2.
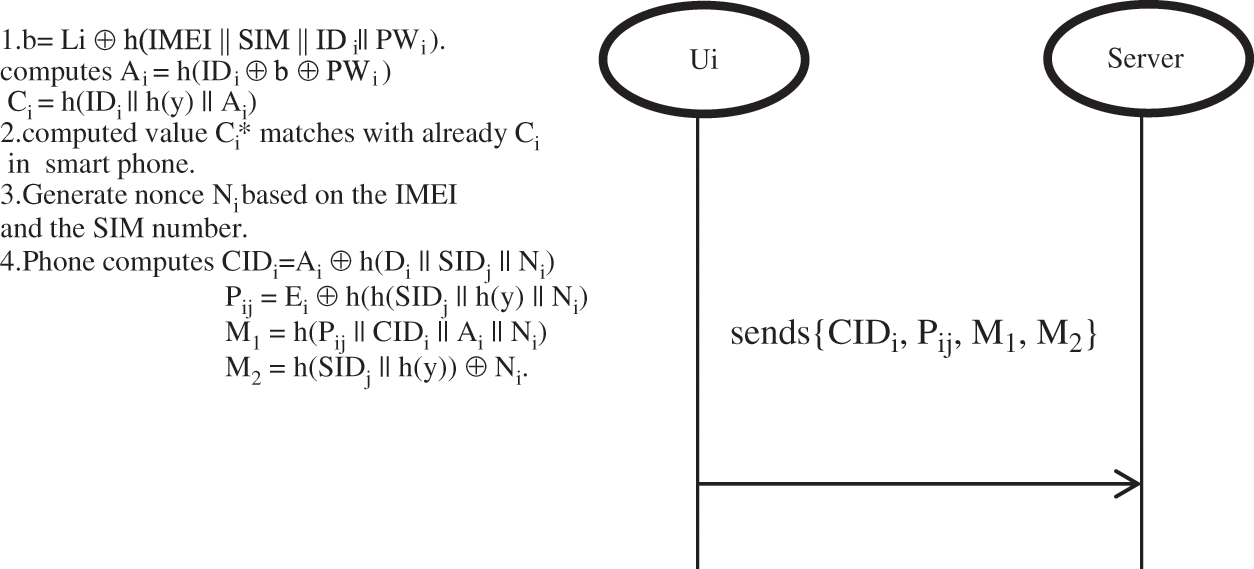
Figure 2: Login phase
3.3 Authentication and Key Agreement Phase
The steps to validate the login request and calculate the shared authentication challenge-response message must take by the server and the user, and both will settle on a SKeyij session secret key for further secure communication.
Step 1: The server Sj computes Ni = h(SIDj || h(y)) ⊕ M2, Ei = Pij⊕ h(h(SIDj || h(y)) || Ni), Bi = Ei⊕ h(x || y), Di = h(Bi || h(x || y)), Ai = CIDi⊕ h(Di || SIDj|| Ni) using the message credentials {Pij, CIDi, Ai,Ni} and the known credentials h(x || y), h(y).
Step 2: Sj computes h(Pij || CIDi || Ai || Ni) and matches it with M1. If it doesn’t match the server won’t accept the request and stop the session. The login request message is accepted and a nonce is created Nj. Sj computes SKij = h(h(Bi || h(x || y)) || Ai), M3 = h(SKij, || Ai || SIDj || Nj) and M4 = SKij⊕ Nj. Next the Server Sj sends the message {M3, M4} to Ui via a public communication channel.
Step 3: After received {M3, M4} from Sj, the user Ui computes SKij = h(Di || Ai), and extracts the nonce Nj by computing Nj = SKij⊕ M4 and checks whether h(SKij ||Ai ||SIDj || Nj) is equal to M3. If they are found to be equal, Ui successfully authenticates Sj. Further Ui computes M5 = h(SKij, || Ai || SIDj || Ni || Nj) and sends the message {M5} to Sj via a public channel. If it doesn’t match, the session is terminated.
Step 4: Sj calculates h(SKij,) and compares it to M5. If they match, the mutual authentication will be complete. Now they will both compute a common secret session key SKeyij = h(SKij, || Ai || SIDj || Ni || Di || Nj) for their secure future communication.
Further, if there is any need to change the Password or Device (IMEI) or SIM, then the user must provide a request from the smartphone by providing the current credentials and the new credentials and compute a new value for Linew = b ⊕ h(IMEInew || SIMnew || IDi || PWinew) and key in the Linew into the smartphone for further authentication [24]. The protocol authentication information is being shown in Fig. 3.
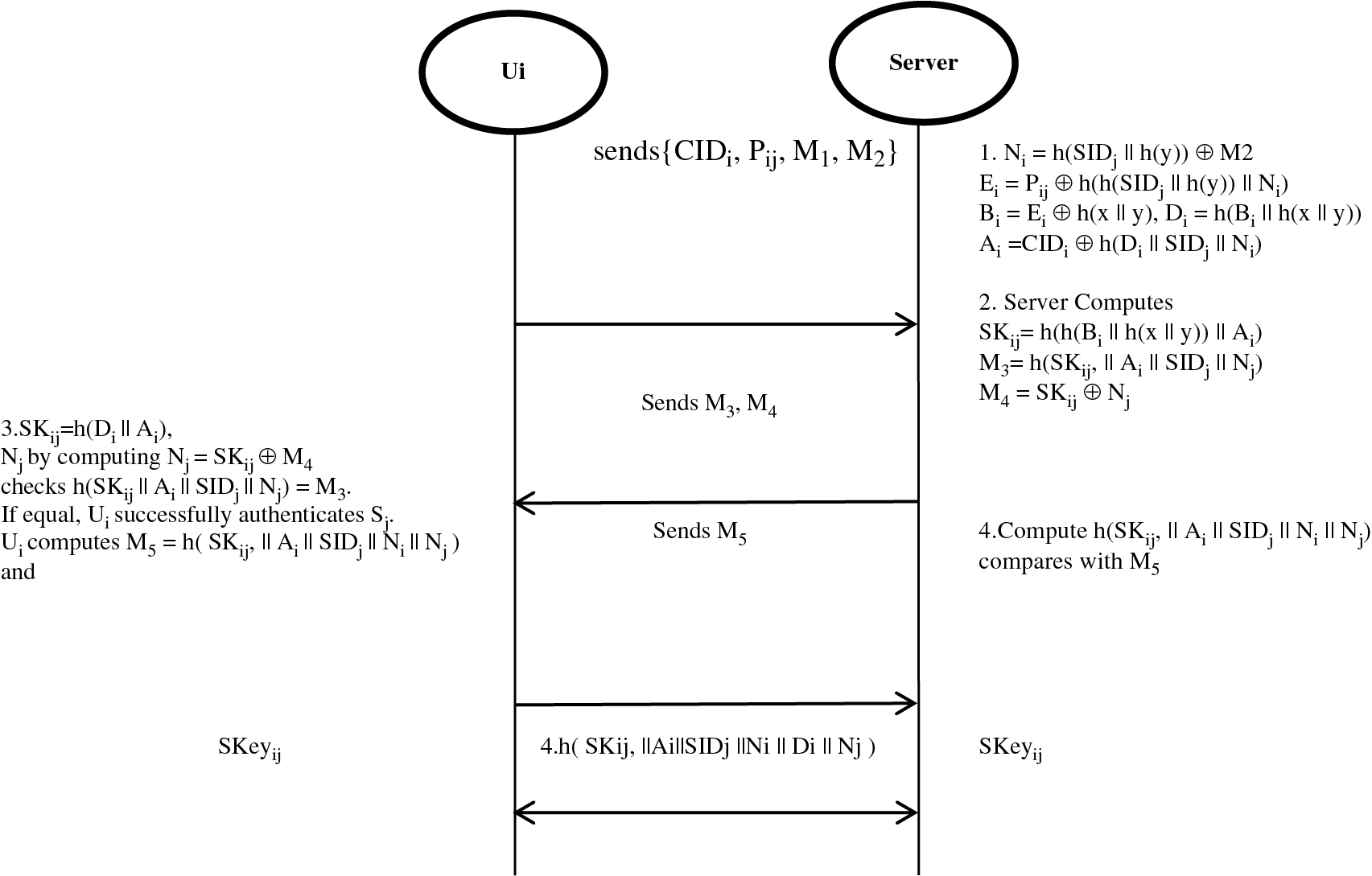
Figure 3: Authentication and key agreement phase
3.4 Hash-Based Message Authentication Code
Here we can concentrate on HMAC and SHA3 for Collision Free Hashing and overcome length extension attacks. HMACs are less affected by collisions than their underlying hashing algorithms alone. So adding an HMAC to an MD5 or SHA hash would make it substantially more difficult to break via a rainbow table. Further, HMAC is not susceptible to length extension attacks. Tab. 1 shows a Comparison of Hash functions and Their Collision and Security Features. Tab. 2 shows the Comparison of Security Features.


4.1 Efficient Mechanism for Password Verification
In the Scheme proposed, the feedback of the user can be checked effectively. The correct credentials like ID, Password, etc. Also, it is possible to make sure that the login request is sent from the authorized device using the approved mobile number, as we are utilizing IMEI and SIM to calculate Li which is in turn used to compute b. If the computed Ci* doesn’t match with Ci stored in the phone then the request will be rejected and the session terminated. This allows the proposed protocol to verify the credentials effectively
In the proposed protocol for authentication, the server received from the user as a login entry and that doesn’t contain the user ID since the IDi sent to the server is computed for every session dynamically. Thus the anonymity of the user Ui is preserved. That parameter is related to a nonce is kept securely through the hash function that makes that process dynamic.
4.3 Stolen Phone/Device Attack
If the User Ui’s mobile device is stolen or lost. The hacker can extricate the put-away information {Ci, Di, Ei, Li, h(y), h(.)} from the telephone. But still, the adversary cannot make use of this information as the adversary still lacks the user ID (IDi) and the password (PWi). It is presumed that the opponent cannot simultaneously guess both the ID and the password, and that they are also protected by one type of hashing functions. Further, the user can block the SIM and IMEI and hence the adversary cannot receive the OTP and hence the proposed protocol provides protection against stolen phone/device attacks.
This scheme is capable of withstanding password predicting attacks as the user Ui needs to input both the ID and Password into the device during a login request. Calculated values like b, Ai, and Ci * are also provided by a one-way hashing function. Further, the additional dependency on IMEI and SIM coupled with the OTP process makes it difficult to do a brute force guessing attack.
4.5 Replay and the Middle Attacks
The use of the two Ni nonce numbers generated by the user device (depending on IMEI and SIM) and the server-generated Nj will keep All messages for that session are dynamic and valid only. and hence it is impossible to do a replay attack. Further, even if the adversary captures the previous login request, without the Ni, Di and Ai, it is not possible to compute M5. Further, the IMEI and SIM numbers are obtained from the device directly, The opponent cannot calculate b. The authentication will therefore fail and The proposed protocol offers effective protection against replay and man attacks in the centre.
The attacker can eavesdrop to fool the server with a legitimate login request. The opponent will not be able to create a legitimate login request-response even if it is done without understanding Ei, Ai, Di and Ni. Since it requires the IMEI and SIM numbers as well, the adversary can’t do it from another device. Even if the device of the user is stolen, without the Password and ID the attacker won’t be able to request a server login message. Thus the proposed protocol can withstand forgery attacks.
4.7 Spoofing Attacks on Servers and Registration Centres
If the attacker is a legal but malicious insider, or if the opponent is a legal system server, they cannot masquerade other server’s secret information h(SIDj || h(y)) and without that, the challenger cannot compute a valid response message {M3, M4}. Further, the dependency on the device IMEI and SIM make the process further complicated and impossible.
Any other session keys should not be compromised. In the proposed model the nonce Ni and Nj and the need for SKij, Di, and Ai, makes it impossible to obtain other keys. Also, all these keys are hashed by one-way hash functions. The proposed protocol is immune to known key secrecy attacks.
In the proposed protocol, by understanding the IDi, Password PWi, random key b, the opponent cannot compute any session key. Thus the proposed model maintains forward secrecy effectively.
In this method, the server verifies the user’s legitimacy and once checked, the mutual authentication is done between the server and the user and this model is therefore protected against this type of attack.
One of the most desirable features of a strong security system is its Reparability. It is the ability to revoke a lost or stolen phone or device. In this case, the user has the option to block the SIM and the IMEI number and without the knowledge of IDi and Password PWi, the adversary will not be able to make use of the information in that device. The proposed model is further guaranteeing user anonymity and resists stolen device attacks and hence is considered to be a model with good reparability.
The proposed authentication scheme is a robust user authentication for a cloud environment. The main advantages of this scheme are the Registration of one-time users at the registration centre to use the services from appropriate servers. The proposed work does not store the user credentials at the server. The passwords can be chosen by the users and can change if needed. The cost of computing and transfer the message is very low. The session key is used for mutual authentication between server and client. The scheme proposed is a nonce-based scheme that has no serious time synchronization problem and nonce is created using the mobile client’s IMEI and SIM number. The scheme satisfies all essential requirements. The scheme will withstand any potential attacks in the cloud environment. The above scheme is well suitable for mobile devices to improve their performance with fewer energy resources and computational capabilities.
Acknowledgement: We show gratitude to anonymous referees for their useful ideas.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. S. Al-Riyami and K. G. Paterson, “Certificateless public key cryptography,” In: Laih CS. (eds) in Advances in Cryptology-ASIACRYPT 2003 Lecture Notes in Computer Science, vol. 2894. Berlin, Heidelberg: Springer, 2003. [Google Scholar]
2. C. Wang, X. Zhang and Z. Zhiming, “Cryptanalysis and improvement of a biometric-based multi-server authentication and key agreement scheme,” Plos one, vol. 11, no. 2, 2016. https://doi.org/10.1371/journal.pone.0149173. [Google Scholar]
3. D. Sahu, S. Sharma, V. Dubey and A. Tripathi, “Cloud computing in mobile applications,” International Journal of Scientific and Research Publications, vol. 2, no. 8, pp. 1–9, 2012. [Google Scholar]
4. G. Yi, Y. A. Heo, H. Byun and Y. S. Jeong, “MRM: Mobile resource management scheme on mobile cloud computing,” Journal of Ambient Intelligence and Humanized Computing, vol. 9, no. 4, pp. 1245–1257, 2018. [Google Scholar]
5. H. Shen, C. Gao, D. He and L. Wu, “New biometrics-based authentication scheme for multi-server environment in critical systems,” J Ambient Intell Human Computing, vol. 6, pp. 825–834, 2015. [Google Scholar]
6. H. C. Hsiang and W. K. Shih, “Improvement of the secure dynamic ID based remote user authentication scheme for the multi-server environment,” Computer Standards & Interfaces, vol. 31, no. 6, pp. 1118–1123, 2009. [Google Scholar]
7. H. Farooq, “A review on cloud computing security using authentication techniques,” International Journal of Advanced Research in Computer Science, vol. 8, no. 2, pp. 19–22, 2017. [Google Scholar]
8. W. C. Ku and S. M. Chen, “Weaknesses and improvements of an efficient password-based remote user authentication scheme using smart cards,” IEEE Transactions on Consumer Electronics, vol. 50, no. 1, pp. 204–207, 2004. [Google Scholar]
9. C. C. Lee, Y. M. Lai and C. T. Li, “An improved secure dynamic ID-based remote user authentication scheme for multi-server environment,” International Journal of Security and Its Applications, vol. 6, no. 2, pp. 203–210, 2012. [Google Scholar]
10. X. Li, J. Ma, W. Wang, Y. Xiong and J. Zhang, “A novel smart card and dynamic ID based remote user authentication scheme for multi-server environments,” Mathematical and Computer Modelling, vol. 58, no. 1–2, pp. 85–95, 2013. [Google Scholar]
11. R. Chow, M. Jakobsson, R. Masuoka, J. Molina, Y. Niu et al., “Authentication in the clouds: A framework and its application to mobile users,” in Proc. of ACM Workshop on Cloud Computing Security Workshop, Chicago Illinois, USA, pp. 1–6, 2010. [Google Scholar]
12. S. K. Sood, A. K. Sarje and K. Singh, “A secure dynamic identity-based authentication protocol for multi-server architecture,” Journal of Network and Computer Applications, vol. 34, no. 2, pp. 609–618, 2011. [Google Scholar]
13. S. Gokulakrishnan and J. M. Gnanasekar, “Data integrity management for detection of redundancy and recurrence patterns in cloud,” Journal of Ambient Intelligence and Humanized Computing, 2019. https://doi.org/10.1007/s12652-019-01530-9. [Google Scholar]
14. S. Sneha, L. Nath and M. Gladence, “Security for bicycle and investigation of health of bicycle rider using IoT,” Journal of Advanced Research in Dynamical and Control Systems, vol. 16, pp. 1298–1303, 2017. [Google Scholar]
15. S. M. Shetty and S. Shetty, “Analysis of load balancing in cloud data centres,” Journal of Ambient Intelligence and Humanized Computing, 2019. https://doi.org/10.1007/s12652-018-1106-7. [Google Scholar]
16. W. S. Juang, “Efficient multi-server password authenticated key agreement using smart cards,” IEEE Transactions on Consumer Electronics, vol. 50, no. 1, pp. 251–255, 2004. [Google Scholar]
17. X. Li, Y. Xiong, J. Ma and W. Wang, “An efficient and security dynamic identity-based authentication protocol for multi-server architecture using smart cards,” Journal of Network and Computer Applications, vol. 35, no. 2, pp. 763–769, 2012. [Google Scholar]
18. Y. P. Liao and S. S. Wang, “A secure dynamic ID based remote user authentication scheme for the multi-server environment,” Computer Standards & Interfaces, vol. 31, no. 1, pp. 24–29, 2009. [Google Scholar]
19. Y. P. Liao and C. M. Hsiao, “A ovel multi-server remote user authentication scheme using self-certified public keys for mobile clients,” Future Generation Computer Systems, vol. 29, no. 3, pp. 886–900, 2013. [Google Scholar]
20. Y. H. Chuang and Y. M. Tseng, “CAKE: Compatible authentication and key exchange protocol for a smart city in 5G networks,” Symmetry, vol. 13, no. 4, pp. 698, 2021. [Google Scholar]
21. P. Sudhakaran, S. Swaminathan, D. Yuvaraj and S. S. Priya, “Load predicting model of mobile cloud computing based on glowworm swarm optimization LSTM network,” International Association of Online Engineering, vol. 14, no. 5, pp. 150–163, 2020. [Google Scholar]
22. D. Yuvaraj, N. R. Dharunyaa, S. Nandhini,V. Priyadharshini and A. Supriya, “Enhanced data security through data integrity on cloud computing,” International Journal of Pure and Applied Mathematics, vol. 118, no. 22, pp. 1079–1083, 2018. [Google Scholar]
23. B. Bazeer Ahamed, D. Yuvaraj and V. Manikandan, “Computation of testing approach in cloud mobility service,” International Journal of Cloud Computing, vol. 10, no. 1/2, pp. 158–177, 2020. [Google Scholar]
24. B. B. Ahamed and D. Yuvaraj, “Dynamic secure power management system in mobile wireless sensor network,” in Int. Conf. on Intelligent Computing & Optimization, Thailand, Springer, pp. 549–558, 2018. [Google Scholar]
25. D. Yuvaraj, M. Sivaram, A. Mohamed Uvaze Ahamed and S. Nageswari, “Some investigation on DDOS attack models in mobile networks,” International Journal of Interactive Mobile Technologies, vol. 13, no. 10, pp. 71–88, 2018. [Google Scholar]
26. S. Shanmugapriya, A. Valarmathi and D. Yuvaraj, “The personal authentication service and security enhancement for an optimal strong password,” Concurrency and Computation: Practice and Experience, vol. 31, no. 13, pp. 5009–5014, 2018. [Google Scholar]
27. S. J. Hussain, U. Ahmed, H. Liaquat, S. Mir, N. Jhanjhi and M. Humayun, “IMIAD: Intelligent malware identification for android platform,” in Int. Conf. on Computer and Information Sciences (ICCIS), Saudi Arabia, 2019. [Google Scholar]
28. Z. A. Almusaylim and N. Z. Jhanjhi, “Comprehensive review: Privacy protection of user in location-aware services of mobile cloud computing,” Wireless Pers Commun, vol. 111, pp. 541–564, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |