DOI:10.32604/csse.2023.024251

| Computer Systems Science & Engineering DOI:10.32604/csse.2023.024251 |  |
| Article |
Modelling a Learning-Based Dynamic Tree Routing Model for Wireless Mesh Access Networks
1Department of Computer Science and Engineering, Sri Shakthi Institute of Engineering and Technology, Coimbatore, India
2School of Engineering, Presidency University, Bengaluru, India
3Department of Information Technology, Bannari Amman Institute of Technology, Sathyamangalam, India
*Corresponding Author: N. Krishnammal. Email: krishnasenthil0606111@gmail.com
Received: 11 October 2021; Accepted: 19 January 2022
Abstract: Link asymmetry in wireless mesh access networks (WMAN) of Mobile ad-hoc Networks (MANETs) is due mesh routers’ transmission range. It is depicted as significant research challenges that pose during the design of network protocol in wireless networks. Based on the extensive review, it is noted that the substantial link percentage is symmetric, i.e., many links are unidirectional. It is identified that the synchronous acknowledgement reliability is higher than the asynchronous message. Therefore, the process of establishing bidirectional link quality through asynchronous beacons underrates the link reliability of asymmetric links. It paves the way to exploit an investigation on asymmetric links to enhance network functions through link estimation. Here, a novel Learning-based Dynamic Tree routing (LDTR) model is proposed to improve network performance and delay. For the evaluation of delay measures, asymmetric link, interference, probability of transmission failure is evaluated. The proportion of energy consumed is used for monitoring energy conditions based on the total energy capacity. This learning model is a productive way for resolving the routing issues over the network model during uncertainty. The asymmetric path is chosen to achieve exploitation and exploration iteratively. The learning-based Dynamic Tree routing model is utilized to resolve the multi-objective routing problem. Here, the simulation is done with MATLAB 2020a simulation environment and path with energy-efficiency and lesser E2E delay is evaluated and compared with existing approaches like the Dyna-Q-network model (DQN), asymmetric MAC model (AMAC), and cooperative asymmetric MAC model (CAMAC) model. The simulation outcomes demonstrate that the anticipated LDTR model attains superior network performance compared to others. The average energy consumption is 250 J, packet energy consumption is 6.5 J, PRR is 50 bits/sec, 95% PDR, average delay percentage is 20%.
Keywords: Wireless mesh access networks; mobile ad-hoc network; reinforcement learning; multi-objective constraint; asymmetric link
Wireless Mesh Access Network (WMAN) is modelled explicitly for broadband access technology with its emergence in industry and academic research [1]. It is adopted to extend internet access. Fig. 1 depicts the typical link asymmetric model. The figure shows that the preliminary tier of WMAN is gateways that establish the connection between the mesh to the internet. Next is the wireless mess composed of several routers [2]. The mesh router performs a relay operation and provides traffic from the gateway to internet connectivity directly [3]. Finally, the access network is composed of clients. The wireless connection access point and mesh connection among the mesh backbone and client is considered. In WMAN, mobile ad-hoc networks (MANET), wireless network models and cellular networks are three diverse access models [4]. Some standards like IEEE 802.16, IEEE 802.15, and IEEE 802.11 a/b/g are merged with WMANs [5]. In WMAN, MAC protocol acts a substantial role in integrating or integrating wireless channel access reasonably and efficiently. Recently, the development of the MAC protocol has gained the attention of various researchers [6]. Moreover, some of the prevailing research works intend to enhance the functionality of the mesh network model, and only a few researchers concentrate on mess access networks. It shows the availability of several clients and routers over the mesh. The mesh routers transmission range is typically higher than the client. It projects the traces of link asymmetry over the mesh access network model [7]. The MAC protocol is adopted in these network models to establish channel access coordination in the multi-hop environment [8]. The standard IEEE 802.11-based MAC model is significantly modelled for coordinating the channel access among the hoping environment. It cannot deal with link asymmetry in WMAN through an ad-hoc network model. Based on the researcher’s perspective, link asymmetry poses enormous research challenges like the heterogeneous hidden problem, unidirectional link problem and heterogeneous issues, which substantially reduces network performance [9–10]. These issues are extensively identified in MANET; however, the WMAN shows a somewhat slight difference compared to MANET, where the existing model developed for MANET is not feasible for WMAN. It triggers us to deal with the link asymmetry issues in WMAN and resolves these issues simultaneously, enhancing network performance [11–13].
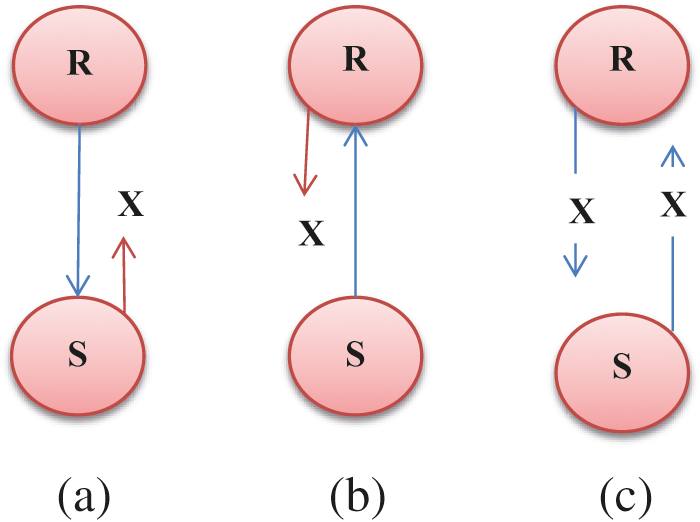
Figure 1: a) Sender to the receiver (asymmetry); b) (Receiver to sender); c) Between sender and receiver
For a specific traffic scenario in WMAN, routing predicts an effectual and path from source to destination to attain superior network performance. It is substantially essential during network design, and broadcast communication is utilized to transfer control packets while predicting the route. The connected nodes are intended to exchange information with neighbour to acquire essential information. The broadcast control can diminish energy consumption and network overhead. Some investigators concentrate on single-objective constraints like packet loss, delay and throughput. Also, load balancing is considered explicitly for eliminating congestion, and network resources such as energy are consumed [14]. Moreover, with the faster incremental demands from the user-side, the single-objective model flops to enhance performance. The multi-objective routing model has grabbed researchers’ attention. Some general multi-objective routing approaches merge various targets into a single formula with weighted cost. In some cases, the weighted values of diverse goals need to be handled in advance. Some researchers set objective constraints independently to eliminate the weighted value problem and model enhanced algorithms to resolve the multi-objective issues [15]. Specifically, addressing some of these research challenges with metrics like energy efficiency and delay are highly solicited. This research anticipates a novel learning-based Dynamic Tree routing (LDTR) model to enhance both network performance and delay without considering the weighted values owing to the benefits of the LDTR model, which is a productive learning model with faster convergence speed. The significant contributions of this research are summarized as:
1) Construct a novel multi-objective approach by analyzing metrics like energy and delay. The delay is interpreted with the asymmetric link by determining the transmission failure probability, bandwidth, and interference.
2) Here, a novel learning-based Dynamic Tree routing (LDTR) model is designed and adapted to the provision optimization model. It is depicted as a productive way for resolving the routing issues when there is any network uncertainty. Here, the model provides a dynamic learning rate to iteration and visiting count. The exploration is evaluated based on the probable actions.
3) The anticipated learning model is utilized for predicting the path, and it can also be adopted in various complex and dynamic network environments. The network condition over the real-time environment can be learned and pretends to predict the most acceptable path adaptively based on the simulation environment. Additionally, the target of this model is to reduce energy consumption and reduces delay
The work is organized as: In Section 2, various existing approaches related to link asymmetry is analyzed, and the outcomes are validated to provide the drawbacks with those methods. It paves the way to establish a roadmap for our research idea. Section 3 discusses the anticipated model in a detailed manner and resolves the multi-objective constraints effectually. In Section 4, the numerical outcomes of the expected model are provided, and the results are analyzed with various existing approaches to highlight the significance of the LDTR model. The work summary is provided in Section 5 with the idea to extend the research in the future.
Recently, various researchers have anticipated diverse MAC protocol which attempts to diminish the nodes’ energy consumption. The predominant model considered for this work is duty-cycling which includes intermittently turning off the transceivers to reduce the total energy consumed. Subsequently, the sender initiates the protocol function to grab the receiver’s attention in a long-term preamble manner. It poses enormous benefits over synchronous MAC protocol as the nodes over this protocol model do not perform synchronization (clock) to produce a schedule. However, a higher collision rate and added overhead are introduced [16]. Subsequently, the long-time preamble is transformed into packets. X-MAC is depicted as the famous and widespread protocol which performs preamble packets. It poses a shorter warm-up of longer one and facilitates the receiver to transfer acknowledgement among the preambles earlier. Moreover, shorter preambles cannot be overcome the added overhead completely. After the extensive analysis of this protocol, a sender-based protocol concept is initiated. Here, the receiver intends to initiate contact and pretends to transfer the beacon to acquire the sender’s attention. It shows substantially a lower overhead than the preambles transferred in the sender-based protocol model. Moreover, based on the review, it is noted that the prevailing protocols do not consider link asymmetry for research purposes. Thus the method does not work promptly whenever they encounter asymmetric links during real-time deployment [17]. Generally, asymmetric links can substantially diminish the low-powered WSNs performance. It is the primary cause that the researchers rely on the asymmetric link over the network layer. Sudhakar et al. [18] anticipated a novel asymmetric geographic forwarding model to discover asymmetric links during beacon broadcasting in the network. The author noted the drastic increase in asymmetric stability by preserving neighbourhood tables. At last, the author proposes a novel route-based data delivery model known as the asymmetric convergence case routing model [19]. The author utilized hop information to choose the intermediate, exploit acknowledgement and data transfer. Moreover, hopping information over the routing model triggers the computational complexity. Also, owing to the memory limitations, holding some essential information over the table in the dense network environment is challenging. Mitterer et al. [20] modelled a novel asymmetric-MAC along with a duty cycle. It merges both the sender and receiver-based MAC protocol model. However, the system functionality relies on the receiver-based model in default. When the sender cannot acquire a beacon, it has to wait for ‘t’ time and then transfers to sender-based mode while it intends to transmit data along with wake-up time. Moreover, when the sender acquires beacon from the receiver; however, sender fails to transform data owing to link asymmetry; its functionality is entirely useless. The working mechanism of this model includes two diverse operations: T-mode and R-mode. The later model is considered as the default model where receiver-based MAC protocol is adopted. The anticipated protocol switches the mode to T-model when it is not sure to acquire the packet from the receiver. The switching process is induced by the timeout factor (elapsed time) indeed of receiving packets. During T-mode functionality, transmitter needs to transfer packets to alert the receiver of during data transfer. When receiver acquires ongoing transmission signal of packets; also, it acquires data from sender. Pau et al. [21] intend to resolve the issues over the asymmetric link using dual-tree and LQI topology. The author adopts link quality estimators to develop tree structure includes dissemination and collection tree. Tripathi et al. [22] use ERPro for performing reverse routing process for handling asymmetric link issues. It considers link quality information and residual energy to choose a legitimate reverse path. Kobo et al. [23] anticipate dynamic hierarchical agglomerative clustering protocol for asymmetric link consideration. However, some researchers consider WSN, which deals with asymmetric links over wireless mesh network and underwater sensor network model. Baccour et al. [24] monitors the asymmetry link issues over duty-cycle industrial WSNs. When the link asymmetry increases, then the nodes sleeping state is reduced. Therefore, the network lifetime reduces. Based on the discussion, the anticipated protocol model poses some default nodes for receiver-initiates mode. When the sender cannot acquire beacon from the receiver due to the asymmetric link, it transfer the method to sender-based and transmit preambles to receiver model. Data transmission follows it. However, there are some issues with this protocol design. Siddiqui et al. [25] discuss the collision factors that happen among the preamble and data when the nodes switch among the sender-based mode. When the beacon is transferred to sender 1 and 2 by the receiver, sender two can predict the beacon; however, sender two does not indicate the beacon due to the available asymmetric link. Then, the sender needs to switch to the sender-based model and initiates preamble transmission. The collision among the data is transferred to sender 2 of receiver 1. Lee et al. [26] anticipate a network scenario with 15 nodes where the protocol model initiates massive data collisions. Moreover, in the expected protocol, there is no transmission between the sender and receiver initiation mode. Thus, this kind of collision is not noted in this proposed model. As link asymmetry occurs at both ends, the asymmetric link is predicted when sender 1 intends to transfer data to receiver. This model does not determine how the sender transmits this condition, and it considers link asymmetry and occurs at the end system. Therefore, this model can deal with data loss and nodes that switch among the sender-based mode transfer longer preambles, generating added overhead. Thus, the packet preamble process is avoided to deal with the link asymmetry condition. All the existing methods fails to fulfil reliability, idle listening, clock synchronization and extra preamble. The various existing approaches does not show efficiency towards the link asymmetry which is addressed effectually with the hierarchical routing model. Tab. 1 depicts the comparison of various existing WMAN protocol models.
This section considers a hierarchical tree structure to select its child node (relay node) when there is the substantial growth of the tree to avoid the link asymmetry problem. The primary research modelling includes three essential phases: 1) system modelling, 2) learning-based hierarchical tree structure, and 3) data transmission module.
Consider ‘N’ as the network nodes that are deployed randomly over the simulation environment with graph model G = (V, E) where E specifies set of edges and V = (v1, v2, …, v3) defines the set of vertices for establishing the communication among the provided nodes. Here, BS is positioned on the central region of simulated environment. In this setup, the links are not in an asymmetric manner.
3.2 Learning-Based Hierarchical Tree Model
In MANET, nodes are randomly deployed over the sensing region, and the data transmission among the nodes and BS are performed in a bi-directional manner [26]. Here, the tree structuring is done hierarchically. It includes three sub-phases like 1) the distance among the nodes and BS are computed based on the one-hop count; every node should possess its parent node (based on neighbourhood information) under the current simulation condition. Some hieratical insertions of nodes are considered sub-tree (child nodes) inserted in an imbalanced manner. Therefore, node balancing needs to be performed in the third sub-phase. In the initial phase, every node needs to evaluate its communication distance (BS, di) from the BS. The centralized BS generates a ‘HELLO’ message and transfer it to every node connected to the network [27]. The connected nodes need to move the request for the first-hop count over the coverage region ri. Based on the BS request, the node that receives the earlier acknowledgement (ACK) is determined as the node with the first hop count. This primary hop count node transfers the request for message forwarding to its successive neighbourhood nodes [28]. It includes(hop count node id, distance from BS, hop count). The network-connected node needs to know its corresponding parent node, and the selection process is shown in Algorithm 1:

Every network-connected node should be aware of its successive neighbour to validate the process of parent selection. The node which initially predicts the request forwarding message acts as a parent node. Then, the consecutive verification of incoming requests is substantially needed in every phase. At last, the node holds its temporary parent node. The first hop count node receives a communication request from the consecutive neighbourhood nodes. When all the incoming requests are provided with the response, it leads to the formation of the unordered tree structure. To handle issues with these unordered tree structures, the network node facilitates only a certain amount of nodes based on authorized acknowledgement [29].
Generally, a watchdog timer or duty cycling is considered the best way to handle the amount of energy consumed by the connected nodes [30–32]. Based on the extensive analysis, some best-suited methods are adopted for scheduling purposes based on sub-tree node depth without any significant concern towards the distance, residual energy and so on. Here, multi-level node scheduling is used to select relay nodes (it can be done with the network connected nodes) for forwarding data. In the proposed hierarchical tree structuring, the watchdog timer for every node is evaluated with the multiplication of the wake-up time of nodes over the successive levels of the sub-tree δ. It is mathematically expressed as in Eq. (1):
The back-off value of the network connectivity is measured using the following Eq. (2):
where,
Here, the constant values (∝ , β, γ) are (0.4, 0.4, 0.2) for optimal outcomes. The periodic wake-up time is depicted as the summation of watchdog time and back off values.
In the conventional protocol model, back-off is adopted for transmission delaying (sender) when multiple senders are intended for transmission. This back-off reduces the collision probability over the network model. Thus, the transmission time is closely connected with back-off time. It is considered for differentiating the wake-up schedule among the siblings. Therefore, nodes with higher factor values need to transfer the beacon first. In this research, distance is also considered the essential factor for selecting the finest node as the relay node. The scheduling process is different from the neighbourhood nodes, thus leads to lesser collision probability. The pseudo-code for this scheduling process is given below: 1) Compute the channel state information with the use of distance from the parent node and residual energy; 2) Evaluate factor value with constant values (∝ , β, γ), residual energy and the distance to the BS from the source; 3) Measure back-off value using the factorial of factor value; 4) Compute wake up time by summing up watchdog timer and back-off values; 5) End the process.
This section explains the process of data transmission among the connected network model. However, the transmission process is analyzed for both the symmetric and asymmetric conditions.
Case study 1 (symmetric link): The parent initiates the transmission of beacons to the sub-tree (children) by triggering the waking up time to perform channel evaluation. When the channel is free, then the information is performed by the child. When it is not available, the sub-tree (child) node needs to wait for a prolonged time until it receives a beacon from the parent. When the receiver wakes up, it initiates the transmission of beacons. The sender with lower back-off time wins packet control overhead. Then, it transfers the data and waits for the acknowledgement from the receiver time.
Case study 2 (asymmetric link without data loss): When the sub-tree node is ready to transfer some data, it needs to wait until it receives the beacon from the parent node. The sender needs to wait for ‘t’ time to transmit the beacon. When the child cannot accept the beacon from the consecutive parent node due to link asymmetry, the sub-tree node adopts cooperative transmission among the nodes (relay node) for message forwarding (See Fig. 2). Cooperative communication is performed by the siblings or connected nodes in the network with an equal hop count. In the heterogeneous network condition, preserving routing information and other information is complex due to its memory constraint. Here, no routing table information is considered. In the beacon message, hop count and parent ID is included. Based on this available information, the sub-tree node performs the data forwarding process. When the provided time is exceeded, the sub-tree needs to wait for the beacon from its siblings. Every sibling poses its corresponding channel information, distance from parent to BS and residual energy. After the waiting time, the sub-tree resumes the transmission again. In the hierarchical tree structure, both the parent and the child can receive a message from the successive neighbours. The children transfer’s data to their siblings, then it includes the parent ID for reference. When the child does not receive any beacon within ‘t’ time from the siblings, it waits for its neighbour’s beacon with a lesser hop count towards the BS. When the child receives a neighbourhood beacon, it initiates the transmission by referring to it as a relay node where no packet is discarded from the network connectivity.
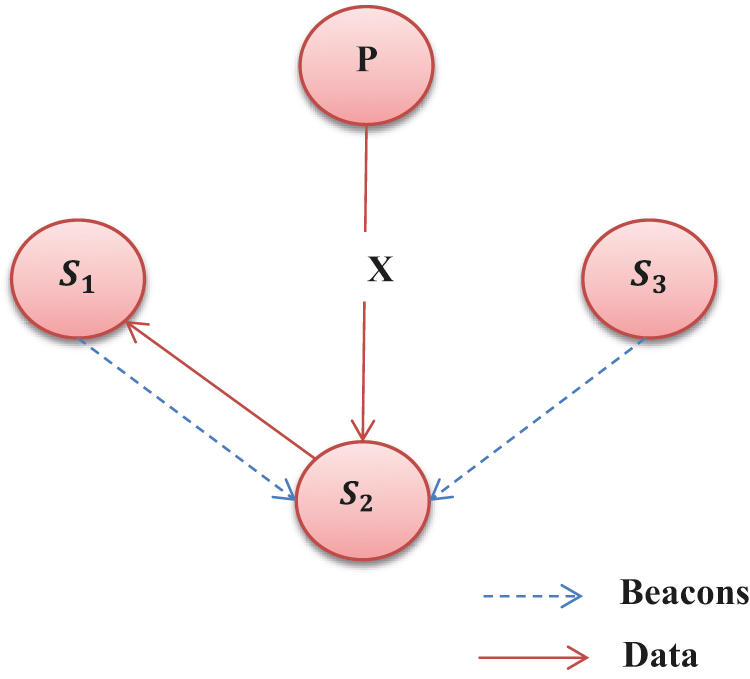
Figure 2: Relay node selection process
Case study 3 (link asymmetry with data loss): The crucial link asymmetry occurs from the children to the parent. In some cases, the child waits for the beacon from parents to initiate data transmission. When the channel space is available successfully, then the child performs communication. However, the parent fails to receive the due the link asymmetry condition. Thus, the sender considers a link asymmetry; therefore, it leads to data transmission failure even after ‘t’ waiting time. It does not acquire any acknowledgement from the receiver side also. Later, the child needs to perform cooperative transmission among the nodes to handle the asymmetric link condition effectively.

This section evaluates and compares the anticipated LDTR model with the prediction of asymmetry links using the MATLAB 2020a environment. Some essential metrics considered for measuring the significance are the network’s energy consumption, energy consumption/node, packet delivery ratio (PDR), packet reception ratio (PRR), average delay/packet, control packet overhead and system throughput with link asymmetry. The network simulation uses a sink node and 100 nodes with an environment 1000*1000 m2 region. The MAC protocol functions under this simulation setup (See Tab. 2). Here, data generation time is uniformly distributed, i.e., till 0.99 s. Here, any application that receives periodic data is considered, and the model is simulated over this environment with a uniform time interval. Generally, these applications need a constant monitoring environment and packets are generated over a continuous time interval. The time required for transmitting the data from the sender to the receiver relies on the MAC protocol with ‘t’ waiting time. Generally, energy is considered as the critical aspect while performing simulation with any sort of network model. It is well-known that substantial energy loss significantly occurs due to the occurrence of link asymmetry. Tabs. 3 and 4 depicts the average energy consumption and energy consumption/packet for 100 available nodes. The evaluation is done among the DQN, AMAC, CAMAC and LDTR models. The energy consumed by the LDTR model is comparatively lesser than the DQN, AMAC and CAMAC models. Similarly, the energy consumption/packet of LDTR is also drastically lesser than DQN, AMAC and CAMAC models. The average energy consumed by the network is defined as the total energy (idle listening, data packets, and control packets) used by the network nodes to the full nodes over the simulated network model. The asymmetric link proportion may vary due to the availability of the network population. Along with this, energy consumption/per packet is depicted as energy consumed by network model to the transmitted total packets successfully. It is mathematically expressed as in Eq. (4):

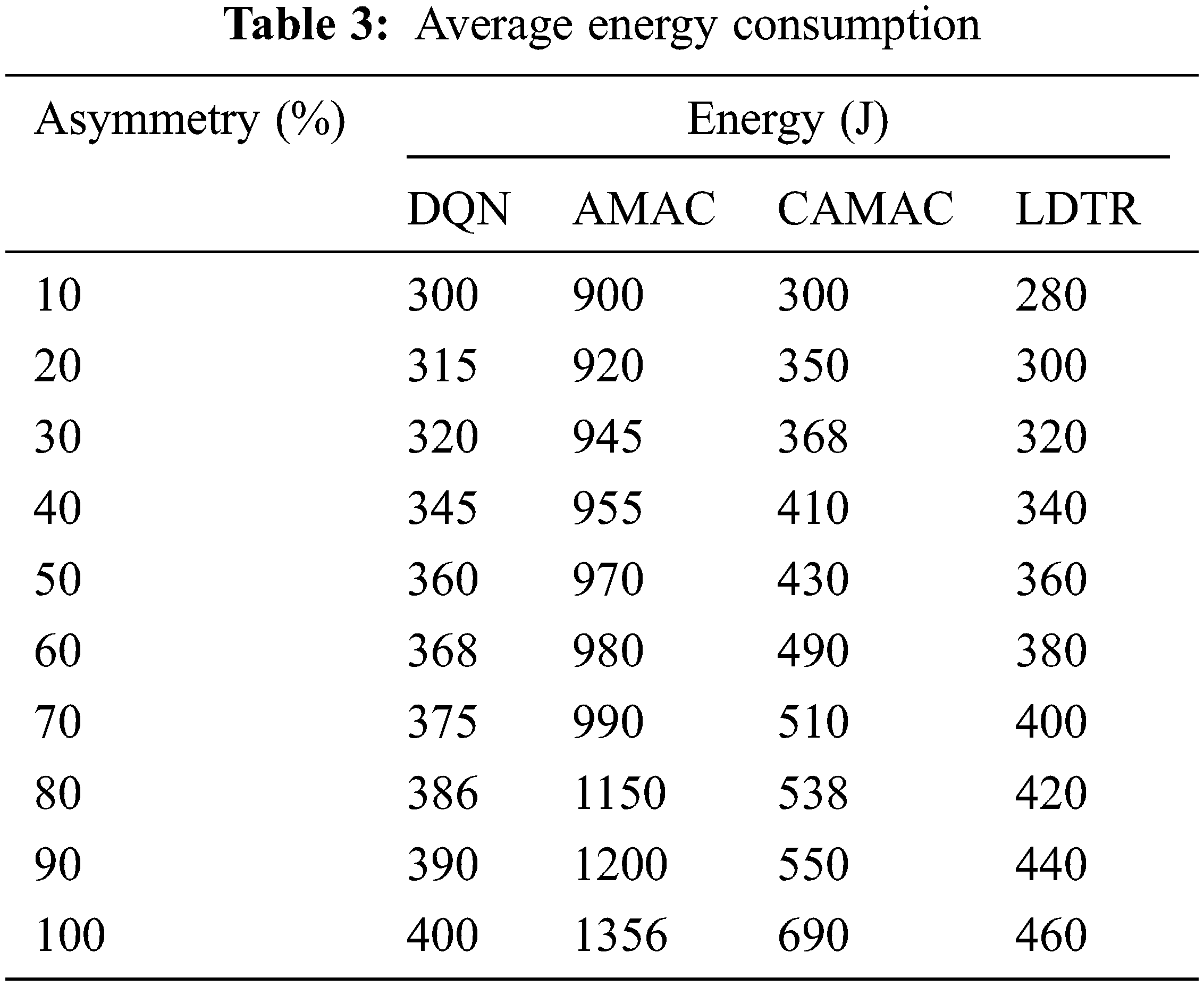

From Eq. (4), EAverage specifies average energy consumption/node, Edata specifies energy consumed during data transmission, EControl packets specifies energy consumed by the control packets, Eidle listening specifies energy consumed during idle listening, and ‘N’ specifies a total number of network nodes. Fig. 3 depicts the relationship between the average energy consumption to asymmetry (%). From the analysis, it is known that the power consumption is directly proportional to asymmetric link, i.e., when asymmetric link increases, it leads to increased power consumption. The preamble transfers node that switches from sender mode with the provided MAC protocol where the neighbourhood node is unaware of this process. It causes collision among the beacon and preamble with increased energy consumption. Some extra overhead is added with energy consumption because of the preamble. If the link asymmetry occurs only 50%, then the energy consumption is reduced by 50% substantially. The average energy consumed by the packets is expressed as in Eq. (5):
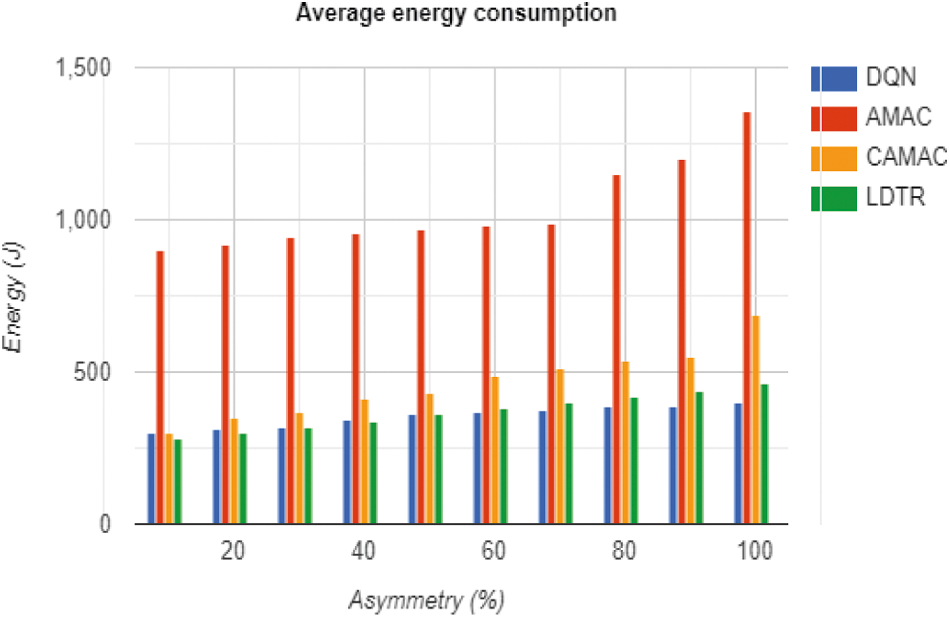
Figure 3: Total average energy consumption computation
Here, Epacket specifies energy consumed by a packet, and Econsumption establishes total energy consumed by the network. From Fig. 4, it is known that the average energy consumed by a packet increases with the increase in link asymmetry. Alike in the previous case, if the link asymmetry is reduced by 50%, it is automatically reflected in the energy consumption per packet, i.e., energy consumed by packets is reduced.
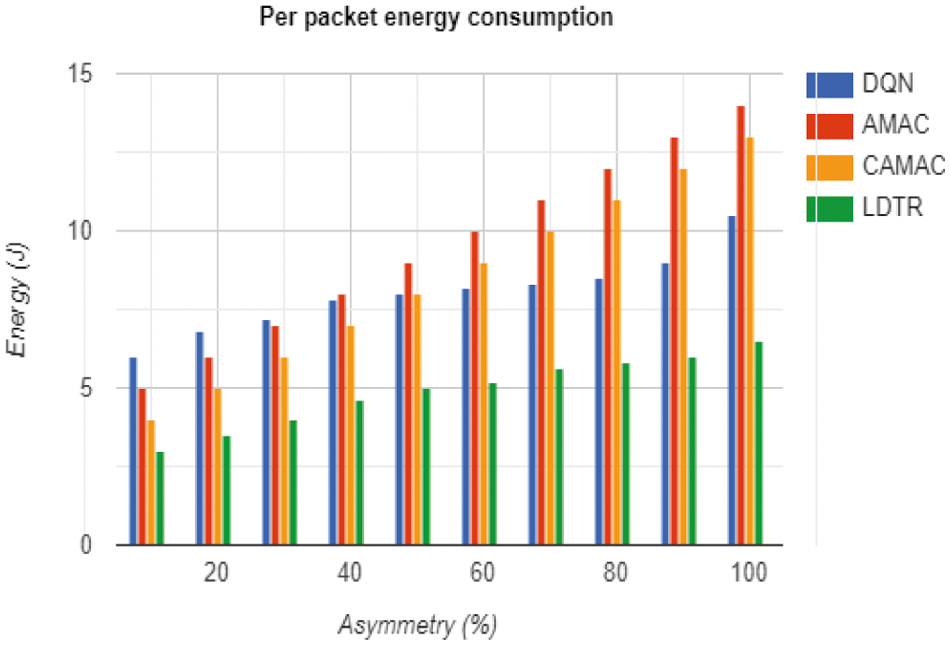
Figure 4: Per packet energy consumption
Packet Reception Ratio (PRR) is depicted as the percentage of totally received packets to the total number of packets transmitted. Fig. 5 shows the comparison of PRR with the asymmetric links. If the asymmetric link is below 30%, the PRR curve declines rapidly than the other models (See Tab. 5). It is mathematically expressed as in Eq. (6):
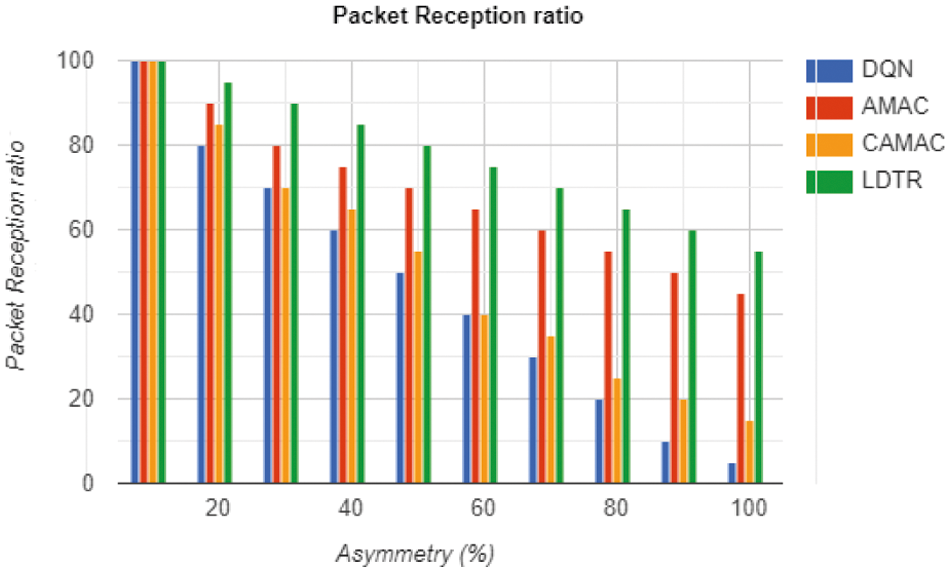
Figure 5: PRR computation

It is well-known that link asymmetry is generally identified from the sender to the receiver model. Here, the PRR of MAC protocol remains the same; moreover, if the link asymmetry occurs in a bi-directional manner, then the PRR is better for the proposed LDTR model than the other approaches. It is compared to the protocol design of existing approaches with changing asymmetric nodes. The PRR of LDTR is superior than DQN, AMAC and CAMAC because these approaches do not receive any packets in case of link asymmetry. As well, the anticipated LDTR model handles this issue with the adoption of a cooperative communication mode. The sender needs to wait for ‘t’ time and initiates a more extended preamble transmission. After capturing the receivers’ insight, then the transmission process is initiated. In some worst-case scenarios, the receiver acquires only lesser packets compared to the total transmitted packets. When the link asymmetry percentage increases, then the data reception rate decreases substantially. This condition is well-opted for the existing approaches like DQN, AMAC and CAMAC; however, in the case of LDTR, the model waits for ‘t’ time and initiates the transmission process so that the receiver can receivers the transmitted data packets. However, in 95% of link asymmetry, the LDTR works well with cooperative communication, which is better than the other approaches. The PDR is depicted as the percentage of transmitted packets successfully to the total number of generated packets. It is expressed as in Eq. (7):
Fig. 6 depicts PDR during link asymmetry. The anticipated LDTR model enhances the PDR by setting the link asymmetry percentage from 15% to 95% (See Tab. 6). The PDR of LDTR is higher than DQN, AMAC, and CAMAC models. The condition identified in PRR is adopted over the PDR also, i.e., if the sender is not capable of transmitting the data to receiver. It waits for ‘t’ time for transferring data to receiver with a preamble model. Alike of this, if sender cannot receive beacons from receiver, it waits for ‘t’ time to get beacons from the neighbourhood nodes. When the beacon is obtained from its neighbour, the neighbourhood node is transformed into the parent node to handle the link asymmetry issue effectively. As an outcome, the PDR of the LDTR model is higher than the other approaches. The PDR of LDTR is substantially higher than the existing approaches, with an average of 2% for the available 100 nodes with 95% link asymmetry.
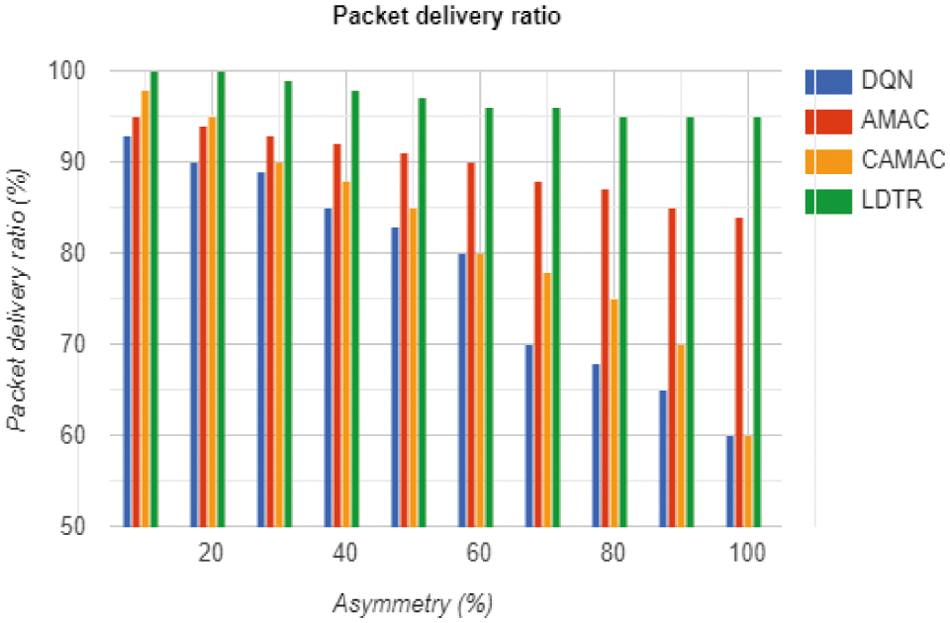
Figure 6: PDR computation

Next, the delay parameter is highly solicited even in the case of critically monitoring applications. Average delay/packet is evaluated as the sum of time duration taken by the packets to reach BS to the total number of successfully generated packets. It is also termed as E2E delay, and the relationship is mathematically expressed as in Eq. (8):
Based on the analysis, it is well-known that the average delay is reduced by 10% to 15% compared to existing approaches like DQN, AMAC, CAMAC, and LDTR model as in Tab. 7. When the link asymmetry is encountered for about 80%, node connectivity searches for the relay node to transfer data to the receiver as in Fig. 7. When the LDTR model fails to transfer data to the receiver because of link asymmetry, then the mode is transferred to sender-based mode and once again initiates the transmission process with a longer time preamble. As an outcome, the average delay diminishes compared to other approaches. It attains a 7% to 10% reduction in average E2E delay even in 95% link asymmetry.

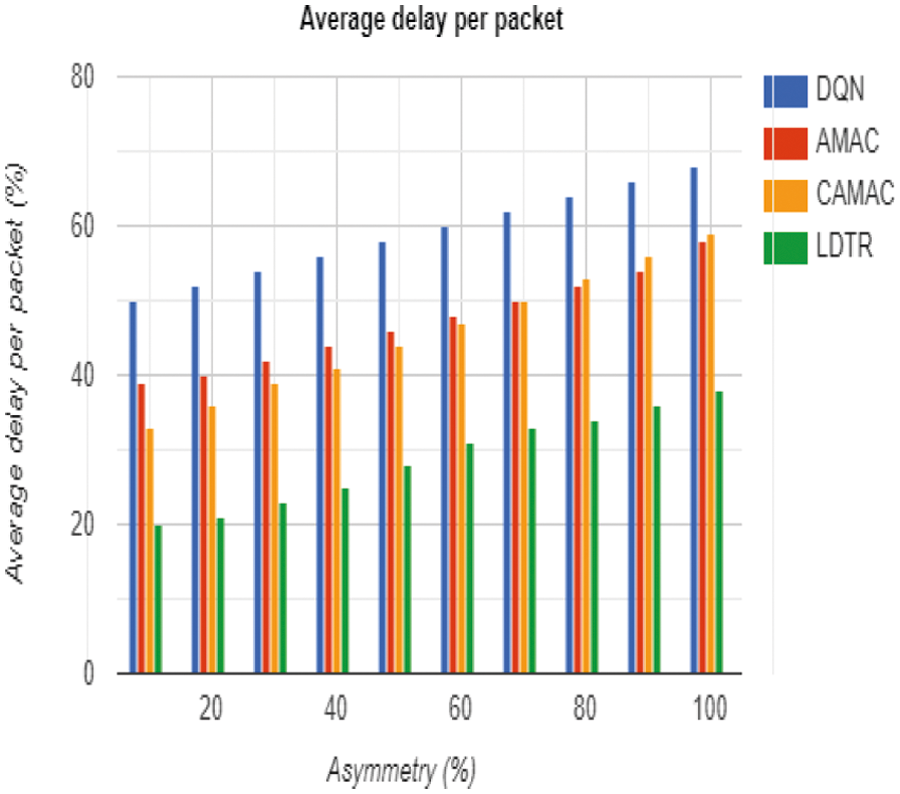
Figure 7: Average delay per packet computation
Next, throughput is depicted as total amount of packets acquired by receiver from the sender based on a specific period. Tab. 8 and Fig. 8 shows the average throughput comparison of the anticipated model during link asymmetry. The predicted model enhances the throughput by 20% compared to other approaches during the occurrence of link asymmetry. With the 95% link asymmetry, the anticipated LDTR shows an average of 15% higher throughput than other models like DQN, AMAC, and CAMAC, respectively, as in Tab. 9. It is due to the adoption of cooperative communication established during the crucial condition, i.e., the parent node is changed instead of changing the control packets. When this changing condition is encountered during the execution time, the link asymmetry issue is resolved entirely. It means that the transmission is done without any control packets, which is the cause of increased throughput. It is expressed as in Eq. (9):

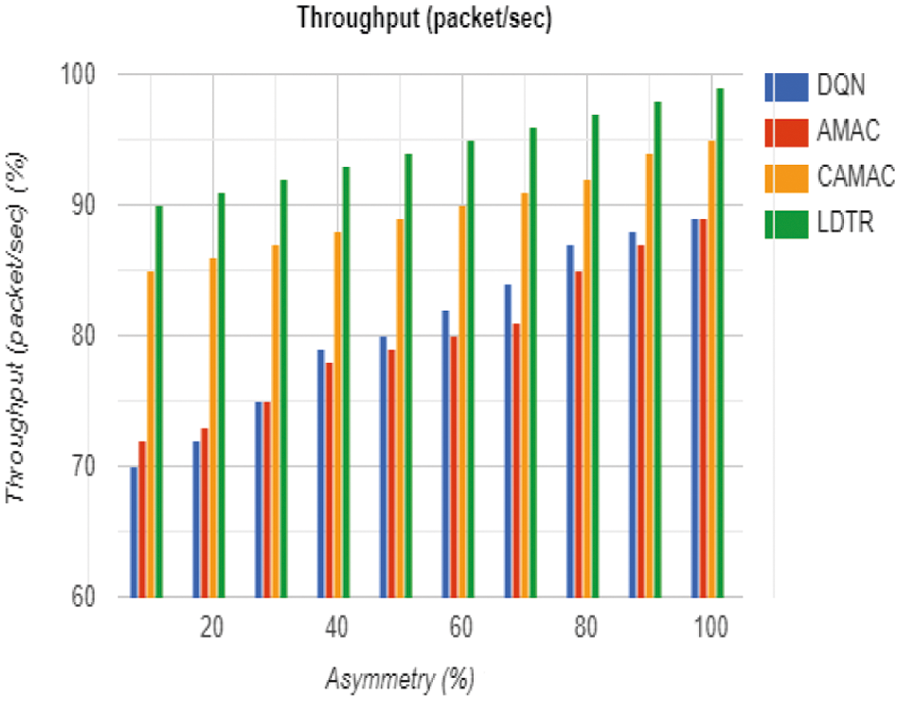
Figure 8: Throughput computation

The control overhead needs to be reduced with the effectual relay selection process as depicted in Fig. 9 and reduce the transmission of control packets immensely among the overall network model. The node initiates the transmission using the sender-based transmission mode to the receiver-based transmission mode in the anticipated model. It transfers burst preamble to grab the receiver’s attention and occurs every time during the transmission process, as in Tab. 9. Here, the node waits for the neighbourhood beacons to adopt cooperative communication. When the beacon is not received from its siblings, it needs to wait for the neighbourhood beacon whose hopping condition is lesser than other nodes. It transfers data using the establishment of a cooperative node and changes it as the parent node completely. Therefore, the control packets are not used for next time. The anticipated model reduced control overhead by 45% compared to other approaches.
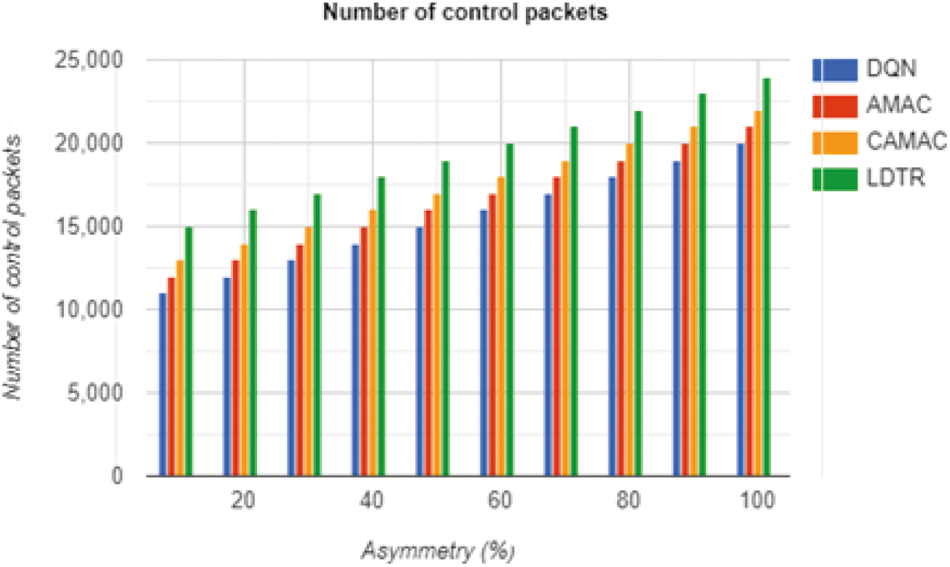
Figure 9: Number of control packets computation
Link asymmetry is considered the major research challenge in WMAN working in MANET. Here, a novel Learning-based Dynamic Tree routing (LDTR) model is designed to handle this issue and improve network performance with reduced delay and better PRR, PDR, etc. The existing approaches like DQN, CAMAC, and AMAC works poorly during link asymmetry. In contrast, the anticipated LDTR model outperforms these current approaches by adopting cooperative communication among the neighbourhood nodes. This model intends to reduce the adverse consequences of asymmetric links and substantially ensures the users’ requirements. Here, the learning model is constructed in a hierarchical tree structure with the ability to hide the node that causes link asymmetric condition, which highly influences some essential metrics like PDR, delay, PRR, energy consumption, etc. The anticipated model triggers the wake-up time, waiting time, and duty cycle of the nodes to perform cooperative communication during the collision. The simulation is done in the MATLAB 2020a environment and attains superior performance by evaluating PDR, PRR, delay, the energy consumption of nodes, average energy consumption, and control overhead. The model outperforms the prevailing approaches and establishes the trade-off among them with better performance. The primary research constraints are the analysis with the existing protocols and simulation with nodes higher than 200. Similarly, the major constraint is the optimality measure of the network. It can be achieved with meta-heuristic optimization approach. In the future, this work will be extended with the option of modern meta-heuristic optimization approaches to acquire the global solution.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. H. T. Cheng and W. Zhuang, “Qos-driven MAC-layer resource allocation for wireless mesh networks with non-altruistic node cooperation and service differentiation,” IEEE Transactions on Wireless Communications, vol. 8, no. 12, pp. 6089–6103, 2009. [Google Scholar]
2. S. Y. Wang, “PC-CTS: A power-controlled-CTS MAC scheme to improve spatial reuse in wireless mesh networks,” in Proc. 12th IEEE ISCC, Aveiro, Portugal, pp. 290–295, 2007. [Google Scholar]
3. M. T. Thai, R. Tiwari and D. Z. Du, “On the construction of virtual backbone in wireless ad hoc networks with unidirectional links,” IEEE Transactions on Mobile Computing, vol. 7, no. 9, pp. 1098–1109, 2008. [Google Scholar]
4. S. Chen, M. Hao, M. Zhang, M. C. Chan and A. L. Ananda, “DEAL: Discover and exploit asymmetric links in dense wireless sensor networks,” in 6th Annual IEEE Communications Society Conf. on Sensor, Mesh and Ad Hoc Communications and Networks, Rome, Italy, pp. 1–9, 2009. [Google Scholar]
5. K. Bicakci, H. Gultekin and B. Tavli, “The impact of one-time energy costs on network lifetime in wireless sensor networks,” IEEE Communications Letters, vol. 13, no. 12, pp. 905–907, 2009. [Google Scholar]
6. Z. Cheng, M. Perillo and W. B. Heinzelman, “General network lifetime and cost models for evaluating sensor network deployment strategies,” IEEE Transactions on Mobile Computing, vol. 7, no. 4, pp. 484–497, 2008. [Google Scholar]
7. Y. Z. Ding, Y. C. Li, Y. C. Xu, Y. Z. Zhou and Y. L. Zhang, “An opportunistic routing protocol for mobile ad hoc networks based on stable ideology,” Wireless Personal Communications, vol. 97, no. 1, pp. 309–331, 2017. [Google Scholar]
8. H. Liu, B. Zhang, H. T. Mouftah, X. Shen and J. Ma, “Opportunistic routing for wireless ad hoc and sensor networks: Present and future directions,” IEEE Communications Magazine, vol. 47, no. 12, pp. 103–109, 2009. [Google Scholar]
9. G. Y. Lee and Z. J. Haas, “Simple, practical, and effective opportunistic routing for short-haul multi-hop wireless networks,” IEEE Transactions on Wireless Communications, vol. 10, no. 11, pp. 3583–3588, 2011. [Google Scholar]
10. D. K. Sharma, S. K. Dhurandher, I. Woungang, R. K. Srivastava, A. Mohananey et al., “A machine learning-based protocol for efficient routing in opportunistic networks,” IEEE Systems Journal, vol. 12, no. 3, pp. 2207–2213, 2018. [Google Scholar]
11. W. S. Jung, J. Yim and Y. Ko, “QGeo: Q-learning-based geographic ad hoc routing protocol for unmanned robotic networks,” IEEE Communications Letters, vol. 21, no. 10, pp. 2258–2261, 2017. [Google Scholar]
12. C. Wu, T. Yoshinaga, Y. Ji and Y. Zhang, “Computational intelligence inspired data delivery for vehicle-to-roadside communications,” IEEE Transactions on Vehicular Technology, vol. 67, no. 12, pp. 12038–12048, 2018. [Google Scholar]
13. S. B. Lahlah, F. Semchedine and L. B. Medjkoune, “Geographic routing protocols for vehicular ad hoc NETworks (VANETsA survey,” Elsevier Vehicular Communications, vol. 11, pp. 20–31, 2018. [Google Scholar]
14. A. Alshehri, H. Huang and S. Parvin, “Cooperative hybrid and scalable opportunistic routing scheme for mobile large-scale wireless network,” Journal of Computer Engineering & Information Technology, vol. 9, no. 1, pp. 1–10, 2020. [Google Scholar]
15. X. Zhang, Z. Qian, T. Li, L. Qian, C. Fu et al., “An efficient routing protocol for heterogeneous wireless ad hoc networks,” in Proc. of the 2011 IEEE Int. Conf. on Multimedia Technology, Hangzhou, China, pp. 172–175, 2011. [Google Scholar]
16. H. Dalman, N. Güzel and M. Sivri, “A fuzzy set-based approach to multi-objective multi-item solid transportation problem under uncertainty,” International Journal of Fuzzy Systems, vol. 18, no. 4, pp. 716–729, 2016. [Google Scholar]
17. C. Wu, S. Ohzahata and T. Kato, “Flexible, portable, and practicable solution for routing in VANETs: A fuzzy constraint Q-learning approach,” IEEE Transactions on Vehicular Technology, vol. 62, no. 9, pp. 4251–4263, 2013. [Google Scholar]
18. C. Sudhakar, T. Ramesh and K. Waghmare, “Path-based optimization of mpi collective communication operation in the cloud,” in Proc. Int. Conf. on Computing, Power and Communication Technologies (GUCON), Greater Noida, Uttar Pradesh, India, pp. 595–599, 2018. [Google Scholar]
19. M. K. M. Rabby, M. S. Alam and M. Shawkat, “A priority-based energy harvesting scheme for charging embedded sensor nodes in wireless body area networks,” PLoS One, vol. 14, no. 4, pp. 1–22, 2019. [Google Scholar]
20. T. Mitterer, H. Gietler, L. M. Faller and H. Zangl, “Artificial landmarks for autonomous vehicles based on magnetic sensors,” in Proc. of Eurosensors Conference, Graz, Austria, pp. 1–4, 2018. [Google Scholar]
21. G. Pau and V. M. Salerno, “Wireless sensor networks for smart homes: A fuzzy-based solution for an energy-effective duty cycle,” Electronics, vol. 8, no. 2, pp. 131, 2019. [Google Scholar]
22. A. Tripathi, H. P. Gupta, T. Dutta, R. Mishra, K. Shukla et al., “Coverage and connectivity in WSNs: A survey, research issues and challenges,” IEEE Access, vol. 6, pp. 26971–26992, 2018. [Google Scholar]
23. H. I. Kobo, A. M. Abu-Mahfouz and G. P. Hancke “A survey on software-defined wireless sensor networks: Challenges and design requirements,” IEEE Access, vol. 5, pp. 1872–1899, 2017. [Google Scholar]
24. N. Baccour, A. Koubâa, L. Mottola, M. A. Zúñiga, H. Youssef et al., “Radio link quality estimation in wireless sensor networks: A survey,” ACM Transactions on Sensor Networks (TSON), vol. 8, no. 4, pp. 1–33, 2012. [Google Scholar]
25. S. Siddiqui, S. Ghani and A. A. Khan, “ADP-MAC: An adaptive and dynamic polling-based MAC protocol for wireless sensor networks,” IEEE Sensors Journal, vol. 18, no. 2, pp. 860–874, 2017. [Google Scholar]
26. J. Lee and S. Kim, “EnRI-MAC: An enhanced receiver-initiated MAC protocol for various traffic types in wireless sensor networks,” Wireless Networks, vol. 26, no. 2, pp. 1193–1202, 2020. [Google Scholar]
27. S. S. Nath and K. H. Prabha, “Energy efficient reverse path routing protocol for asymmetric links in wireless sensor networks,” Asian Journal of Research in Social Sciences and Humanities, vol. 7, no. 1, pp. 501–525, 2017. [Google Scholar]
28. M. Won, T. Park and S. H. Son, “Asym-MAC: A MAC protocol for low-power duty-cycled wireless sensor networks with asymmetric links,” IEEE Communications Letters, vol. 18, no. 5, pp. 809–812, 2014. [Google Scholar]
29. Y. Sun, O. Gurewitz and D. B. Johnson, “RI-MAC: A receiver-initiated asynchronous duty cycle MAC protocol for dynamic traffic loads in wireless sensor networks,” in Proc. of the 6th ACM Conf. on Embedded Network Sensor Systems, Raleigh, NC, USA, pp. 1–14, 2008. [Google Scholar]
30. Y. Li, Y. Q. Song, R. Schott, Z. Wang and Y. Sun, “Impact of link unreliability and asymmetry on the quality of connectivity in large-scale sensor networks,” Sensors, vol. 8, no. 10, pp. 6674–6691, 2008. [Google Scholar]
31. C. Narmatha, “A new neural network-based intrusion detection system for detecting malicious nodes in WSNs,” Journal of Computational Science and Intelligent Technologies, vol. 1, no. 3, pp. 1–8, 2020. [Google Scholar]
32. R. Jayamma, “Improving the performances of WSN using data scheduler and hierarchical tree,” Journal of Computational Science and Intelligent Technologies, vol. 2, no. 2, pp. 7–16, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |