DOI:10.32604/iasc.2021.016646

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.016646 |  |
| Article |
Managing Software Security Risks through an Integrated Computational Method
1Department of Information Technology, College of Computers and Information Technology, Taif University, P. O. Box 11099, Taif 21944, Saudi Arabia
2Department of Computer Science, College of Computers and Information Technology, Taif University, P. O. Box 11099, Taif 21944, Saudi Arabia
3Department of Information Technology, Babasaheb Bhimrao Ambedkar University, Lucknow, 226025, India
4Department of Computer Application, Shri Ramswaroop Memorial University, Lucknow, 225003, India
*Corresponding Author: Rajeev Kumar. Email: rs0414@gmail.com
Received: 07 January 2021; Accepted: 07 February 2021
Abstract: Security risk evaluation of web-based healthcare applications is important from a design perspective. The developers as well as the users need to make sure that the applications must be secure. Citing the disastrous effects of unsecured web applications, Accuntix Online states that the IT industry has lost millions of dollars due to security theft and malware attacks. Protecting the integrity of patients’ health data is of utmost importance. Thus, assessing the security risk of web-based healthcare applications should be accorded the highest priority while developing the web applications. To fulfill the security requirements, the developers must meticulously follow the Multi-Criteria Decision-Making (MCDM) methodology in the assortment of the most effective procedure for security assessment right from the developmental phase of the application. To address the security-related issues in web-based healthcare applications, we have followed the fuzzy-based integrated technique to assess the security risk of web-based healthcare applications. Further, the integrated technology is the combination of Analytic Hierarchy Process (F-AHP) and Technique for Order of Preference by Similarity to Ideal Solution (F-TOPSIS) techniques. The F-AHP approach gives the weights of the factors. We classified the risks into two-levels, Level one had the safety measures factors such as access control, integrity, confidentiality, and, authentication. We selected ten different web-based healthcare applications as alternatives. The calculations based on the proposed methodology ranked the pattern system for access control to be the most prioritized attribute. The outcomes of the study and the procedure used in this assessment would support future research and specialists’ initiatives in organizing web applications through advanced supportable safety and security.
Keywords: Web-based healthcare application; fuzzy AHP; fuzzy TOPSIS; security risk; secure web design
Security risk evaluation is a major concern for the Information Technology (IT) industry, specifically in the health care sector. The number of web application users has increased rapidly during the years 2012 to 2020. The security of web-based healthcare applications needs to be revised. India is ranked as one of the highest spam-sending nations on the planet [1,2]. It is shown by an analysis report that recent web based application have more loopholes than the previous ones. This means that the security of the applications is still a major problem in software development. The developers are unable to write secure code. Further, complexity is also a major concern for the developers in current scenario of designing. It is often shown that highly complex application structure has some serious fundamental issues due to its ambiguous nature. Internet of Things (IoT) devices are a significant target of malware attacks and, email spam is the common way to spread malware [3].
The external network connection makes the UK, US, and China more vulnerable [4]. 20% of the files are not protected according to the survey [5]. In the US alone, 43% of the IT industry is a victim of cyber-attacks and the resulting losses are estimated to be 214 million dollars [6]. Preventing the breach and data hijacking in any type of web based healthcare application requires industry’s best practices and approaches of security [7]. However, these steps alone would not be effective enough in securing the web-based healthcare applications. We have to evaluate the design steps of web-based healthcare applications quantitatively from a design perspective to ensure optimum levels of security.
Managing the risk of security in web based healthcare application development is an important process and has a high sensitivity. Besides, every electronic device in healthcare environment has some risk associated with its security. However, these security risks can be minimized or mitigated through planned risk assessment procedures [5]. Furthermore, according to [6], security risk can be categorized into four aspects from a design perspective. On the other hand, a study classifies its security measure in terms of size for web-based healthcare applications [7]. Their definition depends on the number of lines of code in terms of the task and the number of designers involved in the process. Hence, from the perspective of achieving optimal security in the organizations, this examination proposes a consolidated F-AHP-TOPSIS methodology to ascertain the heaviness of each risk model and sub-foundation. A secure web-based healthcare application allows the patients’ data to be stored as records and enables easy accessibility of data. Moreover, a secure web-based healthcare application also highlights the theft and misplacement of data.
Our quantitative research evaluation will essentially concentrate on the risk evaluation level for web-based healthcare applications. Further, the principal target of this survey is to give specialists a conclusive and systematic approach for estimating the present degree of risk evaluation.
2 Security Risk of Web-Based Healthcare Application Design
Healthcare web applications are improving the function of health services. The security and processing of patients’ data is the primary concern of our research. The upsurge in the instances of healthcare data thefts poses a grave danger to the patients’ health and can have fatal consequences. Security risk issues have been rising in different countries across the world. Norway and the USA report 4000 cases of ransomware per day; the spike in the cases in 2018 was estimated to be nearly 300% more than in 2017 [8]. This is creating stress worldwide. The use of smartphones, particularly in the healthcare sector, has empowered the patients as well as the doctors. Healthcare specialists use smartphones for maintaining records, process over the network, for diagnosis and medical prescription. Healthcare web-based applications or software on mobile have reported data breaches because of security measures adopted by the developers. We need to focus on the security of the web-based application. In the present study, we have formulated security at two different levels; level one has four factors F1, F2, F3 and, F4. Further, it can be classified as presented in Fig. 1 and Tab. 1.
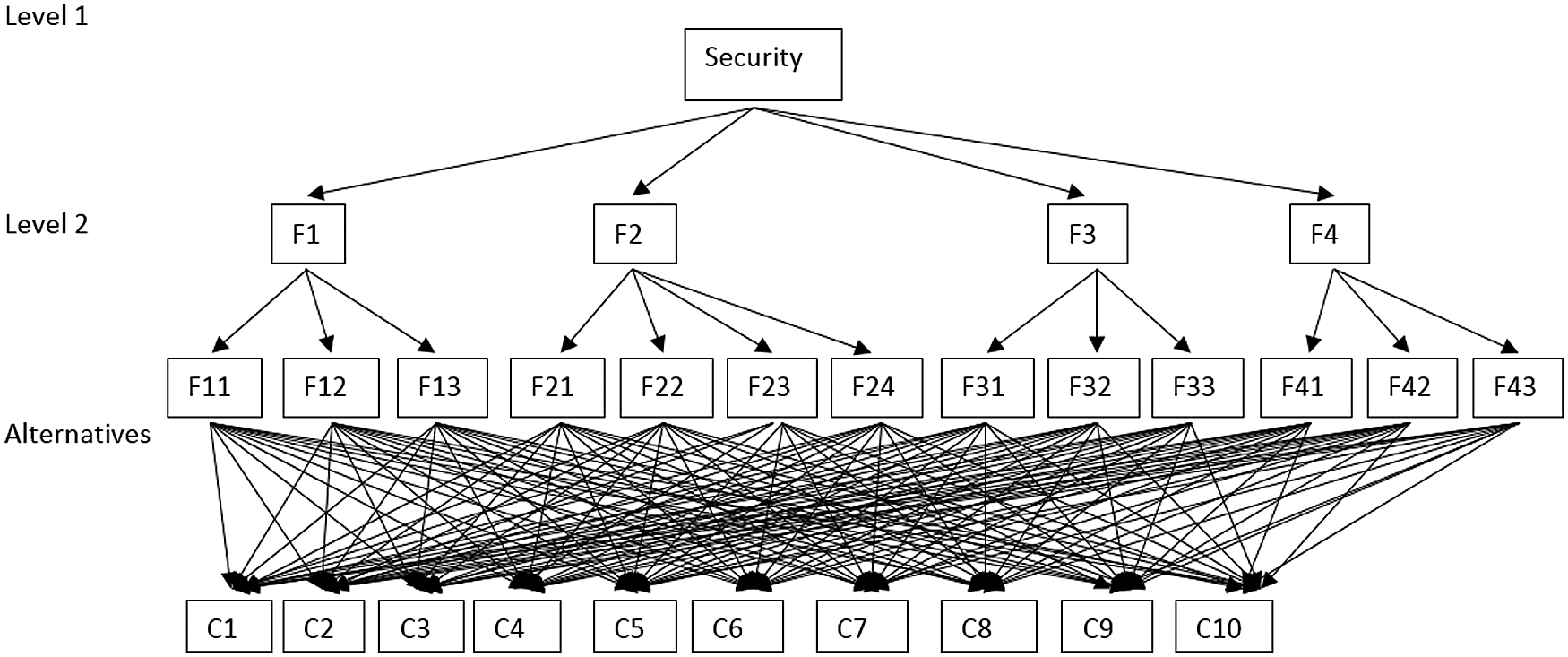
Figure 1: A structure of tree for security risks
Table 1: Security risk of web-based healthcare application factors in the design phase

The factors F1, F2 and, F3 have three different sections, F2 has four different subsections. Further, all the sub-factors are connected to ten different alternatives (web application used in a different hospital).
This is the primary and important step of application on the device. Users access the application by the systematic approach of authentication, authorization, and, accountability. When the user accesses the data, authentication is checked and the location will be verified by the device.
ACPVPM [F11] - In this context, the attacker tries to modify the used variable which contains unpredicted principles. This can interrupt the further fragments of the code. Additionally, if an attacker reads the private variable, it may open up the private information, thus making it convenient for the attacker to invade further.
PCF [F12] - If the password stored in the system is accessed by the intruder, then the hacker can easily gain access to the system and pilfer the data.
APSAC [F13] - Software pattern, encapsulated in software design, explains the pattern of model to access the authorization in software or web-based application.
It ensures the authenticity of the information by verifying if the source of information is genuine.
EITVDS [F21], the healthcare-based web application is hesitant to trust variables that must be initialized outside of its trust limit by the user. If the attackers are able to initialize the variables, they can do what they want with the system.
ICMDOA [F22], the object contains attributes intended for internal use. Undesirable changes cause vulnerability. The software receives input upgradation but does not have proper control over modification in attributes.
DCWICCE [F23], the hacker can execute the malicious code without checking its integrity.
Concurrent execution using SRIS [F24], the program can run with other code and, code sequence require provisional, elite access to a shared resource, but a scheduling space can alter the shared resource by alternative code arrangement that is functioning simultaneously.
It is the set of rules which protect the information from unauthorized access. Information of the healthcare sector is sensitive and needs to be protected. Attackers can steal passwords and control network traffic. All the breaches are not intentional; some can be accidental like sending the mail to the wrong recipient, share private files in the public domain, etc. We have classified the confidentiality in its sub-factors in level 2.
CVDP [F31], web application and software define a critical field, variable to be public when security procedure is required to be private. The problem of security risks is involved in the software or web application (software development life cycle) effectively, thus affecting security by making it more difficult. It makes it easier to introduce vulnerabilities.
USP [F32], a healthcare-based application examines typical resources that are used as an external supply by the search path. This search path cannot be controlled by the application. This makes the attacker execute the malicious program and also access the authentication to modify the path of the application.
SPWAD [F33], the security patterns are the bridge between the developers and security experts. Security patterns capture security expertise for the problem. These patterns capture the strength and weaknesses of web applications and software.
It is defined as the set of rules by which the authorization of access is granted. Authentication has two different levels that maintain the security risk to the web application used in the healthcare sector.
PCF [F41], web application, and healthcare software save the PIN in a configuration file that might be reachable by the attacker. The attackers use the password and make the system useless.
UPC [F42], refers to the setting a new password for the user, the change compromises the authentication of the system.
MACF [F43], web application and software do not execute any verification concerning functionality that needs verifiable operator characteristics or ingests a major quantity of resources. This makes the web application insecure. The cycle of the design process of web applications and software reduces the risk. Further, the factors of healthcare web applications are defined in Section 3.
The different alternatives (C1 to C10) are- MediXcel EMR (C1), Trio HIS (C2), Caresoft HIS (C3), GeniPulse (C4), LiveHealth For diagnostic (C5), Visual Hospital Management (C6), eHospital (C7), Medisteer (C8), HospiLogix (C9) and NextGen (C10). These are the various hospital management web-based applications that we are using as alternatives.
Security factors and their respective alternatives are presented in Fig. 1. The factor levels of security are classified into two-levels which maintain the cycle of calculation and achieve the desirable goal of quantitatively calculating the impact of security risk in healthcare applications. Level 1 has four factors and level two has different factors associated with level 1.
3 Unified F-AHP-TOPSIS Technique
To estimate the risk ratio in web applications of healthcare services, the authors classified and categorized various factors related to security and then evaluated these factors by a well-established fuzzy-based multi-criteria decision-making approach named, fuzzy Analytical Hierarchy Process (AHP). Further, to evaluate the risk ratio of the healthcare web applications, the adopted methodology was used to determine the weights for estimating the risk effectiveness for healthcare web applications and test the adopted results on various selected healthcare application projects as alternatives. Testing of results on various selected projects as alternatives is implemented by another similar approach called fuzzy TOPSIS. The fuzzy TOPSIS approach gives an ability to the examiner for estimating the effect of extracted results from fuzzy AHP methodology by various equations and numerical calculation.
Securing the data and maintaining risk on healthcare web applications is a problem that needs a quick and decision-based solution. Therefore, for managing this type of context, the authors and experts strongly believe that adopted fuzzy AHP-TOPSIS methodology is perfectly appropriate. There are various previous pieces of literature available that portray the significance and usefulness of results extracted from fuzzy AHP methodology. Moreover, it is also evidently drawn by experts that there are some obstacles and implications present in this evaluation methodology. Thus to tackle these implications and obstacles, authors added another effective similar approach, i.e., the fuzzy TOPSIS that gives a complementary advantage to the fuzzy AHP and its results.
Further, as a procedure to evaluate the factor's impact on healthcare web applications, the fuzzy AHP methodology was used to create a systematic tree-like model of various selected factors. Thereafter the numerical equations were applied on these factors. As a second initial step in the evaluation, the examiners converted the original weights of the factors given by experts into the triangular fuzzy set number (TFN). It is also often shown and proven that TFN values for every factor stepped in between 0 and 1 [8,9]. Moreover, to understand the adopted methodology more descriptively, the following headings are discussed:
Step 1: As an initial first step, after the creation of a successful tree model, the examiners developed a function named membership by applying the following Eqs. (1) and (2).
Here, various symbols represent various units like limit 1 denotes the upper limit, mi represents middle and ui portrays lower one.
Step 2: Now as the next step in evaluation, the examiners create the TFN numbers for factors by applying the following formulas.
For estimating the triangular numbers it is important to understand the representation mechanism as Now, the original conversation for TFN [9] is performed by Eq. (3)–(6).
Step 3: The following Eq. (10) is used for evaluation:
Where
Step 4: Further, it’s time to develop a choice-based matrix by applying the following Eq. (12).
Step 5: The following Eq. (13) is used for calculating GM and then Eq. (14) gives an evaluation step for specific weights in tree-based model.
Step 6: Now after identifying the specific weights for every factor, the examiners apply Eqs. (15) and (16) to normalize the values.
Step 7: For estimating the best factor and ranking list of selected attributes, the following Eq. (17) is applied.
This concludes the evaluations done by using the fuzzy AHP methodology. After identifying the ranking list and the weights of the factors, the examiners apply another similar MCDM approach called fuzzy TOPSIS to respectively test the evaluated results. TOPSIS is a methodology that produces a testing plot in the numeric manner which is the same as real-world testing [10–12]. TOPSIS method is a perfect technique for estimating the quality and efficiency of extracted results from fuzzy AHP. To conduct the evaluation steps, the method adopts some applications related to the field of hierarchy and then uses them as an alternative in the calculation process. A brief description of the method is displayed in the following headings:
Step 1: As the first step in evaluation, the examiners assign weights for specific factors to the specific alternatives that are selected by authors.
Step 2: Develop a matrix by applying Eq. (18).
Here
Step 3: Further, after creating a systematic matrix from Eq. (18), the examiners need to normalize the values identified in the previous step and represented as in the following Eqs. (19) and (20).
Here, the value of j is considered between 1 and 0. Further, the process of normalization is frequently applied till the TFN values conversation.
Step 4: By applying the following Eq. (21), the examiner gets a numerical matrix for alternative evaluation.
where,
As a notable point, it is often shown during the evaluation that normalized values represent TFN values that range from 0 and 1.
Step 5: To numerically quantify the +ve and –ve ideal solution value by applying Eqs. (22)–(25).
Here
Step 6: In this concluding step of evaluation, the examiners apply the Eq. (26) to get the ideal gap degree of alternatives values. Calculation of coefficient gap degree needs to be evaluated for perfect alternative testing [13–16].
where,
This abovementioned steps of the evaluation are essential for estimating the ranking and testing of the results. The next section of the paper describes the original numerical analysis of factors selected for the proposed study by applying the process discussed above.
Calculation of the security risk characteristics in the healthcare web application is a challenging job [10–13]. Estimating the quantitative impact of healthcare web application security is a critical process during building secure software or healthcare web application and to prevent the data phishing, vulnerability, and malicious attack from disintegration due to a security risk. From a healthcare perspective, security risk assessment gives successful importance to the characteristics of security as well as alternatives during the development process [14–16]. In this row, the authors of the paper opted for a fuzzy-based combined computational technique based on AHP and TOPSIS for evaluating more accurate results.
For the evaluation of the factors, we used Eqs. (1)–(9) and the scale of a triangular fuzzy number [10]. After using the TFN scale and calculating the values with the help of Eqs. (1)–(9), the authors constructed the pair-wise comparison matrix that is represented in Tab. 2 for level 1 characteristics of security risk. For level 2 each factor is connected to the respective sub factors mentioned in Fig. 1. The individual connection factors are represented by Tabs. 3 to 6. Further, the authors defuzzified the TFN values through Eqs. (7)–(11) and the results are represented in Tabs. 7 to 11. Each factor is represented by the matrix of three variables. Level 2 has F1, F3, F4 which further have 3 sub-factors and F2 has four sub-factors; the pair-wise comparison matrix is evaluated by the Eqs. (12)–(17). Thereafter, the quantitative evaluation of the weights of attributes is done; this has been shown in Tab. 12. Further, with the help of Eqs. (18)–(26), calculated subjective values in numerical form, weighted normalized fuzzy decision matrix and closeness coefficient of the different alternatives are shown in Tabs. 13 to 15, respectively.
Table 2: Aggregated fuzzy-based pairwise judgment matrix at level 1

Table 3: Aggregated fuzzy-based pairwise judgment matrix for F1 at level 2

Table 4: Aggregated fuzzy-based pairwise judgment matrix for F2 at level 2

Table 5: Aggregated fuzzy-based pairwise judgment matrix for F3 at level 2

Table 6: Aggregated fuzzy-based pairwise judgment matrix for F4 at level 2

Table 7: Local weight at level 1

Table 8: Local weight at level 1 for F1

Table 9: Local weight at level 1 for F2

Table 10: Local weight at level 1 for F3

Table 11: Local weight at level 1 for F4

Table 12: Summary of the results

Table 13: Subjective perception outcomes in numerical form

Table 14: The weighted normalized fuzzy decision matrix

Table 15: Closeness coefficient of the different alternatives

Tab. 15 shows the final values of alternatives through F-AHP-TOPSIS. Further, when we use different methodologies, the outputs of the data are different. For the examination of the accuracy of the assessment through one method, the authors have used another method called classical AHP-TOPSIS (C-AHP-TOPSIS). With the help of two or more methods, we can verify the reliability and efficiency of the obtained results through the co-relation coefficient. After the assessment through C-AHP-TOPSIS, Tab. 16 shown the outcomes.
Table 16: Compare the result of classical and F-AHP, F-TOPSIS methods

Tab. 16 shows the difference between outcomes of F-AHP-TOPSIS and C-AHP-TOPSIS. Besides, the outcomes are highly associated (Pearson correlation coefficient is 0.96918). Obtained results through decision-making techniques may be ambiguous; hence, sensitivity analyses should be performed to verify the validity of the outcomes. In this row, the authors of this paper also evaluated the sensitivity analyses as shown in Tab. 17.
Table 17: Sensitivity analysis
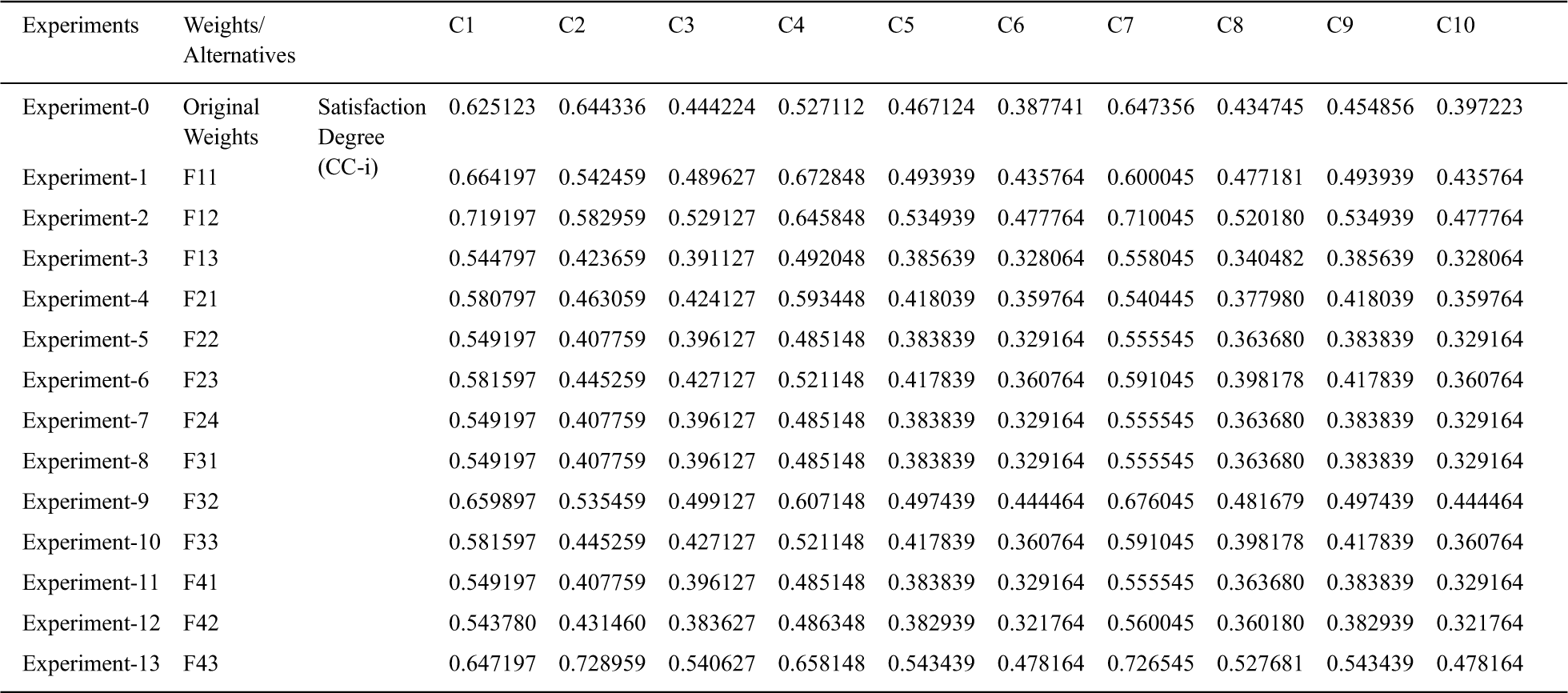
The combined computational technique based on AHP and TOPSIS is the most conclusive approach for verifying the impact of the selected factors in the design of healthcare web application. Integrity, access control, confidentiality, and authentication are primary-level factors, and the secondary level factors have been described in Fig. 1 and Tab. 1 in detail. All are important factors for secure design of web-based healthcare applications. Security concerns associated with WBHMS, and protecting the privacy of the data from different malfunctions and attacks from the design perspective is a subject of imminent attention. The present research paper selected four significant factors of security risk, four primary and three dependent factors of F1, four dependent factors of F2, three dependent factors of F3 and, three dependent factors of F4 in the secondary level, which depend healthcare applications (alternatives) being used in different hospitals. Outcomes of security risk factors represent the momentous effect on the WBHMS in healthcare applications from a design perspective. According to our estimation which was done by using F- AHP, the pattern system for access control in the access control got the highest rank. eHospital got the top rank which was determined by using F-TOPSIS technique. Thereafter, we validated the combined computational technique based on AHP and TOPSIS to deliver the impactful ranking of the security risk factors and quantitative values of alternatives.
Acknowledgement: This research was supported by Taif University Researchers Supporting Project number (TURSP-2020/231), Taif University, Taif, Saudi Arabia.
Funding Statement: Funding for this study was received from the Taif University Researchers Supporting Projects at Taif University, Kingdom of Saudi Arabia under Grant No. TURSP-2020/231.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. K. Sahu and R. K. Srivastava. (2020). “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37, . DOI 10.18576/isl/090105. [Google Scholar] [CrossRef]
2. G. McGraw. (2004). “Software security,” IEEE Security and Privacy, vol. 2, no. 2, pp. 80–83, . DOI 10.1109/MSECP.2004.1281254. [Google Scholar] [CrossRef]
3. K. Sahu and R. K. Srivastava. (2018). “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222. [Google Scholar]
4. A. S. Sodiya, S. A. Onashoga and O. B. Ajayĩ. (2006). “Towards building secure software systems,” Issues in Informing Science and Information Technology, vol. 3, no. 12, pp. 35–42, . DOI 10.28945/920. [Google Scholar] [CrossRef]
5. P. Shamala, R. Ahmad and M. Yusoff. (2013). “A conceptual framework of info structure for information security risk assessment,” Journal of Information Security and Applications, vol. 18, no. 1, pp. 45–52, . DOI 10.1016/j.jisa.2013.07.002. [Google Scholar] [CrossRef]
6. Z. I. Saleh, H. Refai and A. Mashhour. (2011). “Proposed framework for security risk assessment,” Journal of Information Security, vol. 2, no. 2, pp. 85–90, . DOI 10.4236/jis.2011.22008. [Google Scholar] [CrossRef]
7. K. Sahu and R. Shree. (2015). “Helpful and defending actions in software risk management: A security viewpoint,” Integrated Journal of British, vol. 4, no. 5, pp. 1–7. [Google Scholar]
8. M. C. Lee. (2014). “Information security risk analysis methods and research trends: AHP and fuzzy comprehensive method,” International Journal of Computer Science and Information Technology, vol. 6, no. 1, pp. 29–35. [Google Scholar]
9. P. Shedden, R. Scheepers, W. Smith and A. Ahmad. (2011). “Incorporating a knowledge perspective into security risk assessments,” ICIC Express Letters, vol. 12, no. 14, pp. 4567–4573. [Google Scholar]
10. K. Sahu and R. Shree. (2015). “Software security: A risk taxonomy,” International Journal of Computer Science and Engineering Technology, vol. 7, no. 3, pp. 36–41. [Google Scholar]
11. P. Kocher, R. Lee, G. McGraw and A. Raghunathan. (2004). “Security as a new dimension in embedded system design,” in Proc. of the 41st Annual Design Automation Conf., San Diego, CA, USA, pp. 753–760. [Google Scholar]
12. K. Sahu, R. Shree and R. Kumar. (2014). “Risk management perspective in SDLC,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 4, no. 3, pp. 1247–1251. [Google Scholar]
13. K. Sahu and R. Shree. (2015). “Stability: Abstract roadmap of security,” American International Journal of Research in Science, Engineering and Mathematics, vol. 2, no. 9, pp. 183–186. [Google Scholar]
14. P. T. Devanbu and S. Stubblebine. (2000). “Software engineering for security: A roadmap,” in Proc. of the Conf. on the Future of Software Engineering, Limerick, Ireland, pp. 227–239. [Google Scholar]
15. K. Sahu and R. K. Srivastava. (2019). “Revisiting software reliability,” Advances in Intelligent Systems and Computing, vol. 802, pp. 221–235. [Google Scholar]
16. D. M. Mehta. (2007). “Effective Software Security Management,” Technical Report: OWASP, . [Online]. Available: https://www.owasp.org/images/2/28/Effective_Software_Security_Management.pdf. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |