DOI:10.32604/iasc.2022.019348

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2022.019348 |  |
| Article |
Visual Protection Using RC5 Selective Encryption in Telemedicine
1Department of Information Technology, College of Computers and Information Technology, Taif University, P.O. Box 11099, Taif 21944, Saudi Arabia
2Department of Computer Science and Engineering, Faculty of Electronic Engineering, Menoufia University, Menouf, 32952, Egypt
3Department of Electrical Engineering, Faculty of Engineering, Menoufia University, Shebin El-Kom, 32511, Egypt
*Corresponding Author: Osama S. Faragallah. Email: o.salah@tu.edu.sa
Received: 09 April 2021; Accepted: 10 May 2021
Abstract: The dissemination of the COVID-19 viruses now extends the usage of video consultations to share perspectives and virtual medical consultations, save expenses and health procedures, track the success of care proposals with detail, consistency, and ease from moment to time. The research aims to study the security of video consultations. We will also present the advantages and disadvantages of video consultations and the complications of their implementation. This paper mainly proposes a practical, high-efficiency video encoding technique for the new video encoding technique (HEVC) used in video consultations. The technology offered uses the RC5 block encryption algorithm for encrypting the sensitive bits of HEVC with low complexity, short encoding times in real-time implementations, format-compliant HEVC, and constant bitrate. In addition, this paper presents experimental results comparing the proposed HEVC RC5-based selective encryption (SE) algorithm with the other algorithms used in various operating modes using the Advanced Encryption Standard (AES). Also, this paper provides the security analysis of the proposed HEVC RC5-based SE algorithm for video consultation, including; the correlation analysis between the ciphered video and the original one, the histogram of the ciphered video, and the cipher cycle analysis. The security analysis results ensured that the proposed HEVC RC5-based SE algorithm for video consultation is safe and stable.
Keywords: RC5; telemedicine; HEVC; video encryption
Before the COVID-19 pandemic, there were increasing interactive consultations with several health systems promoting a telemedicine consultation approach. At the pandemic beginning, many GPs, clinicians and individuals were consulted on the video to minimize patient traffic and restrict contagious exposures through healthcare facilities. Video and telephone consultations will also encourage medical practitioners to maintain their medical services whether they are well-insulated or fall in high-risk categories and need protection. The spectrum of long-term video appointments encompasses diabetes, depression, arthritis, stroke, mental disorders, cancer and chronic pain. A broad number of acute conditions, including eye emergency triage, can also be used for online consultations and triage. According to the COVID-19 pandemic, healthcare methods have been quickly developed, such as video consultancy, to deliver healthcare security and minimize growth risk.
With the COVID-19 virus apparition, health care facilities became extremely difficult to provide. The accelerated dissemination of this virus represents telemedicine [1] and video consultation strategies [2] to keep health services without increasing possible interaction with patients and physicians. Prior patient separation becomes an essential technique for the health care regulator before arrival in the emergency room. In addition, video consultations are helpful to stone and support contact between physicians and patients via cell phones and electronic websites [3].
Video consultations on healthcare exchange health data from one location to another using video appointments to improve patient's health. In addition, given the COVID-19 apparition, the use of video appointments must be expanded to help patients who need to be monitored in time, while preserving access to the requisite health services by recipients with mild symptoms at home. In addition to decreasing the number of other patients and physicians in touch, the growth in the COVID-19 population reduces the distribution of COVID-19 [4].
The following elements include a video consultation on healthcare [3]:
1. The online consultations in healthcare are carried out using video appointments.
2. Video information on healthcare is transmitted online between patients and healthcare specialists.
3. Physicians develop professional expertise to offer both expert and consumer healthcare and reviews.
Telemedicine is used to supply distance health services through telecommunications systems [1]. This approach has numerous variations: Internet consultations, cellular or videoconferencing, telemonitoring/screenings of critical signals for the patient and GPS sensors. This method can also be followed in various ways. Video consultations are the most widely used. Hypertension, diabetes, coronary illness, asthma, chronic obstructive pulmonary disease and elderly patients are the primary medical disorders needing video consultations [5]. Therefore, video consultation has been used frequently in patients with common chronic illnesses and needing primary care, regarding the future of healthcare. In particular, healthcare practitioners have used video consulting to follow-up patients, infectious illness patients, cancer families and premature neonates. Compared to in-person health consultations, telemedicine has seen similar effects in health care and has increased access to health services [6,7].
It is not unique to the symptomatology of COVID-19 that makes it clinically indiscernible from other viral diseases of respiration [8]. However, the latest systematic findings suggest that flu, cough, joints and/or weakness, dyspnoeic, headache, throat and gastrointestinal symptoms and skin lesions with varying clinical attributes are the most frequent symptoms associated with illness. Furthermore, COVID-19 can worsen some cardiovascular symptoms and lead to cardiovascular complications [9].
Finally, during this pandemic, some psychiatric illnesses were also exacerbated. In this way, the treatment of affected patients and caregivers are central to the prevention of COVID-19. In extreme COVID-19 cases, children get first-hand care and track outpatients in community environments and update on the epidemic to patients and the general public. However, the accelerated growth of COVID-19 worldwide, highlighting the exercise of social distancing interventions like quarantine times, had been a significant problem for health organizations and policies [10].
Since every practitioner is vulnerable to infection, new treatment methods arise to ensure that patients don't get face to face and get care. In addition, the development of healthy medical environments has been a priority because policymakers have encouraged social distancing to deter the danger of the disease from spreading [11]. Video consultations in this respect are seen as the best solution during the global pandemic and are encouraged to minimize their effect on public health and the use of healthcare. In line with COVID-19, for example, services were promoted in the area of online mental health [12].
Over the years, user video conferencing has tackled the challenges of bringing up video conferencing in terms of the advantages of their respective businesses. Videoconferencing organizations, businesses and government departments pose one of the biggest problems of protection. Before introducing coronavirus, video conference applications impacted the fear that video conversations can be recorded through the Internet. Various defensive and main processes have been established, which are considered for video security purposes, to deter attacks by eavesdropping, denial of service, spoofing or repudiation or falsification [13]. More businesses also use the Internet to distribute their wireless applications, including online appointments with healthcare professionals. In multimedia security [14], the protection of multimedia information from unauthenticated attacks plays a significant role.
Naive Encryption (NEA) is an introductory video encryption technique. It uses standard video data encryption [15]. However, the NEA technology has several disadvantages like encryption cost of HD video and it is not possible to perform extra operations on the encrypted video.
Due to the NEA disadvantages, researchers employed another strategy called selective video encryption. The selective encryption techniques encrypt the most sensitive bits of video that can ensure the tunability, visual degradation, security, encryption ratio, and format compliance [16]. Many approaches use standard algorithms to encrypt video bits like DES, RC6 and AES for selective video encryption. A selective encryption system for successful health video consultation is the key aim of this initiative. This initiative introduces an effective SE strategy for the HEVC standard for video coding, which can be used for video consultations with health care in real-time [17].
The suggested technique uses the RC5 block cipher algorithm to encrypt sign bits and the Motion Vector Difference (MVD) suffixes bits and Discrete Cosine Transform (DCT) suffixes. The proposed HEVC RC5-based SE for video consultation allows the video essential bits to be encrypted at low delays and the enforcement of HEVC bitrate and format compliance. This technique would ensure the easy posting of health video meetings on the internet is kept confidential. Video consultations are required to assist patients at home with the protection of access to healthcare with COVID-19 distributed. The reduction of COVID-19 will prevent COVID-19 from being disseminated [18].
This paper is structured according to the following: Section 2 presents the previous relevant HEVC encryption schemes. Then, the suggested HEVC RC5-based SE scheme for video consultation is introduced in Section 3. Next, section 4 offers a comparative study between the HEVC RC5-based SE scheme for video consultation and other algorithms using AES in various operating modes and explains the security of the HEVC RC5-based SE for video consultation. Finally, the conclusion of the paper is described in Section 5.
This article aims to establish selective algorithms for video coding for the new standards (HEVC). In this section, we offer brief background information on what we have suggested. The privacy of video consultation in healthcare is exciting to protect the content of video consultations from threats while storing or distributing it over the Internet [19]. The easiest way to secure video information is by using NEA to encrypt all video information with the aid of standard encryption strategies. However, long waits for encryption/ decryption can be triggered when large-sized video data is not ideal in online applications. Selective encryption algorithms were designed to replace NEA algorithms. It just relies on the video coding architecture and the encryption for the best critical bits. Many proposals have been proposed to integrate the SE into the HEVC, including:
• Heinz Hofbauer developed a selective HEVC encryption method, which encrypts the AC DCT Coefficients sign bits. The AC DCT symbol bits depend on the bitstream signature proportion [20].
• To improve Heinz’s system Yiqi Tew encrypts the skip-signal and sign bits of the AC DCT coefficients with hidden key input [21].
• Shahid created a selective HEVC system encryption algorithm for DCT truncated rice binstrings, using the CFB mode with AES encryption [22].
• By encoding certain syntax elements to ensure consistency with the video format, such as DCT sign-bits, filter parameters and QP information, Glenn created a selective HEVC encryption process in which, the random number and XORed AES encoding algorithm are employed [23].
• J. Li developed an HEVC selective encrypting system by encrypting the TR code parameter R and the residual sign [24].
• By encrypting luma IPM in addition to the parameter R of TR code, B. Boyadjis improved J. Li and set up a limited encryption scheme and a residual sign [25].
• Farajallah has configured the DCT value, DCT sign bits, MVD, MVD sign bits and DQP sign to provide SHVC with a selective encryption schema [26].
• Meyer and Gadengast proposed to encrypt the MPEG-1 series and slice headers as stable MPEGs [27].
• Aegis uses DES to encrypt the I-frame of MPEG video alone, serial header and IOS end code [28].
• VEA has split the video stream into parts. Any segment is broken down into impressive, even and odd lists. The even list is enciphered, and the odd list is streamed based on XOR [29].
• Nithin offers a selective H.264 encoding algorithm with the transforming coefficient and motion vector sign bits. The encryption algorithm is flexible according to the software properties. Sign bit encryption is ideally suited for mobile telephone systems and online, high-tech applications [30].
3 The Proposed HEVC RC5-based SE Scheme for Video Consultation
The proposed HEVC RC5-based SE scheme for video consultation depends on encrypting several HEVC syntax elements and delivers efficient performance with a slight bitrate increase that can be utilized for real-time video consultations in the medical system. The proposed HEVC RC5-based SE scheme for video consultation encrypts some syntax elements of the CABAC binstrings that achieves adequate encryption, low latency, and video format compliance. These syntax elements are Residual sign, Residual value, MVD sign, and MVD value.
The proposed HEVC RC5-based SE scheme uses the RC5 block encryption algorithm, one of the most common block cipher algorithms. The RC5 algorithm has the advantages of its speed and simplicity, so it is valuable for encrypting real-time video consultations. Fig. 1 illustrates the flowchart of the proposed HEVC RC5-based SE scheme for video consultation. The proposed HEVC RC5-based SE scheme for video consultation has the following description:
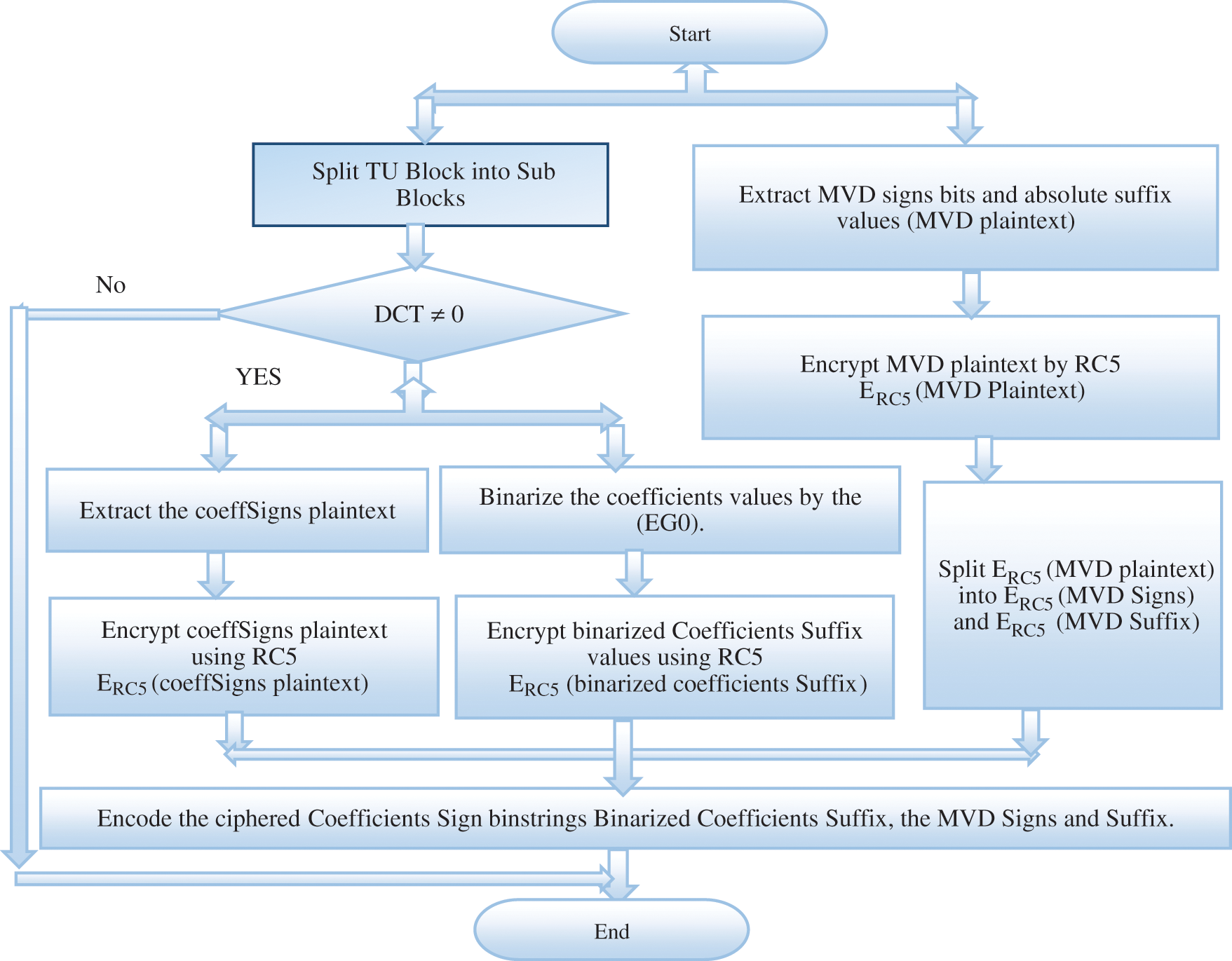
Figure 1: The Flowchart for the introduced HEVC RC5-based SE scheme for video consultation
1. For every non-zero DCT coefficients:
• Split the NxN block transforming unit (TU) into 4x4 subblocks containing DCT coefficients.
• Prepare the DCT coefficients for each subblock to render the plaintext bitstring for every subblock.
• Prepare the DCT Coefficients signs plaintext for every subblock.
• Prepare the DCT Coefficients suffix plaintext for every subblock.
2. Prepare the plaintext by adding the horizontal/vertical MVD symbol bits with the absolute values of MVD horizontal/vertical suffixes (MVDPlain).
3. Employ plaintext encryption using the RC5 block encryption algorithm to produce the encrypted binstring.
4. Encode the encrypted binstring instead of the actual bins in the entropy stage during the video encoding process.
The improvement of the proposed HEVC RC5-based SE scheme for video consultation lies in encrypting HEVC video consultations with maintaining the real-time, same bitrate, and format compliance constraints as follows:
• The RC5 block encryption algorithm has a short and straightforward algorithm structure and achieves a real-time restriction.
• Employ binstrings encryption in encryption space, which uses the BAC Bypass mode during the entropy stage, does not change the HEVC video code layout to fulfil the format compliance.
• Encryption of DCT and MVD sign bits and suffix absolute values ensures that the encrypted bins have equal lengths to their actual bins, achieves the same bit-rate constraint.
The technical features of the proposed HEVC RC5-based SE scheme for video consultation should maintain the constant bitrate of video and video format compliance. The selective encryption approach proposed for health video consultation is developed using the HM16.0 Reference programme selective encryption algorithm used as a testing platform for applying the HEVC specification [31,32].
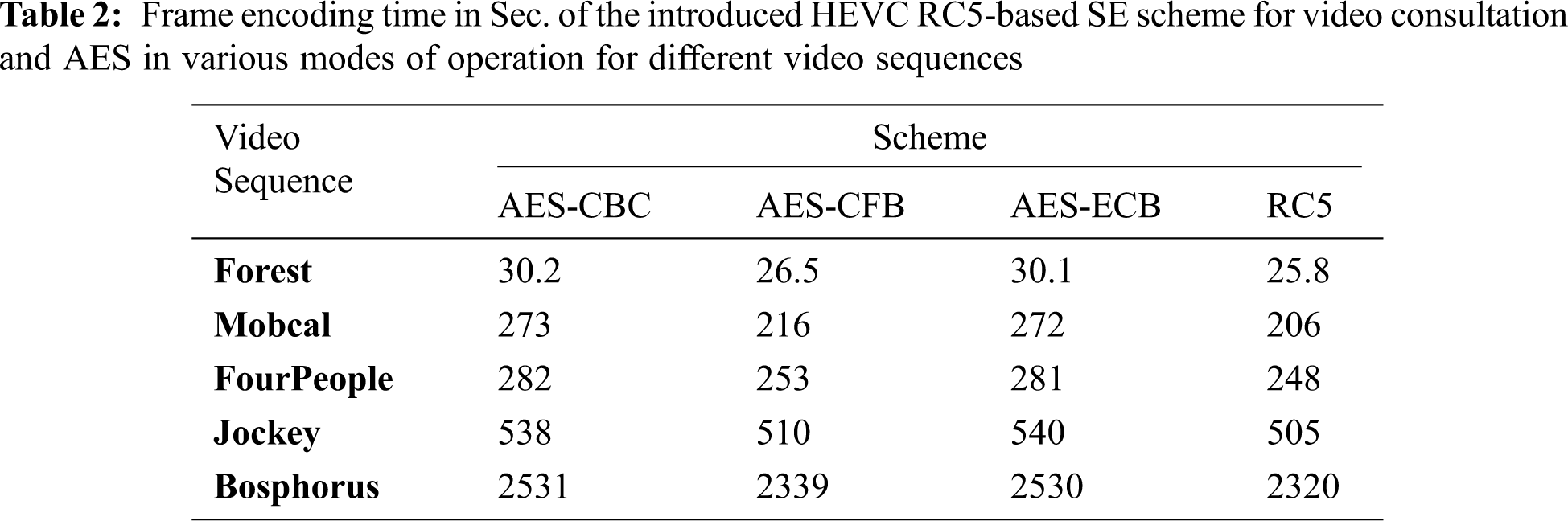
Tab. 2 provides the time in Sec. of the introduced HEVC RC5-based SE scheme for video consultation and AES encryption in various modes of operation to encode one frame for different video sequences defined by the entire video dataset listed in Tab. 1. Also, compares between the proposed HEVC RC5-based SE scheme for video consultation and other methods that use AES encryption algorithm in different operation mode. As a result, Tab. 2 reveals a saving in frame encoding time by 0.7 seconds in Forest low-resolution video to 19 seconds in Bosphorus high-resolution video. This ensures and confirms that implementing the low delay RC5 algorithm in the introduced HEVC RC5-based SE scheme for video consultation saves this time.
The PSNR and SSIM scores of the introduced HEVC RC5-based SE for video consultation and other schemes that employ the AES encryption algorithm in different operation modes for tested videos are listed in Tabs. 3 and 4. For efficient encryption of HEVC, it must obtain lower values for both the PSNR and SSIM. The PSNR values in Tab. 3 illustrate that the proposed HEVC RC5-based SE scheme for video consultation has lower PSNR values than AES in various operation modes for different video sequences. This can guarantee the superiority of the introduced HEVC RC5-based SE scheme to HEVC SE using AES in various operation modes for the different video sequences. Tab. 4 illustrates SSIM values for the proposed HEVC RC5-based SE. The proposed HEVC RC5-based SE has lower SSIM scores than HEVC SE using AES in various modes of operation for the different video sequences. Again, this ensures the superiority of the proposed HEVC RC5-based SE scheme to HEVC SE using AES in various modes of operation for different video sequences.
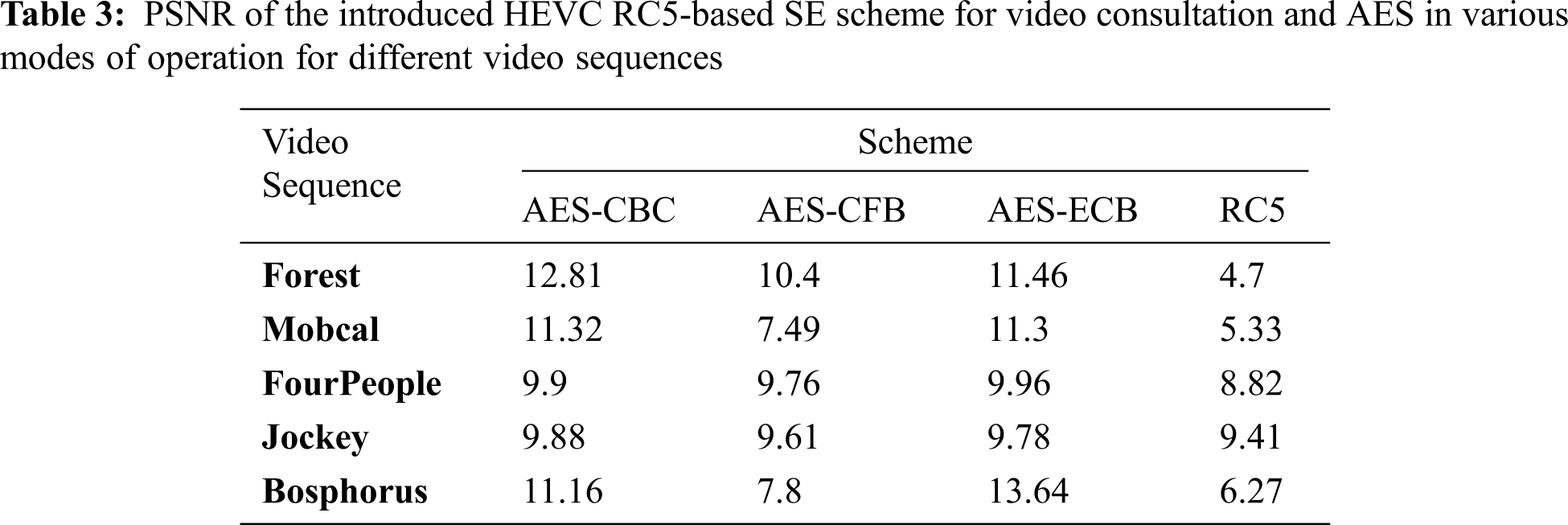
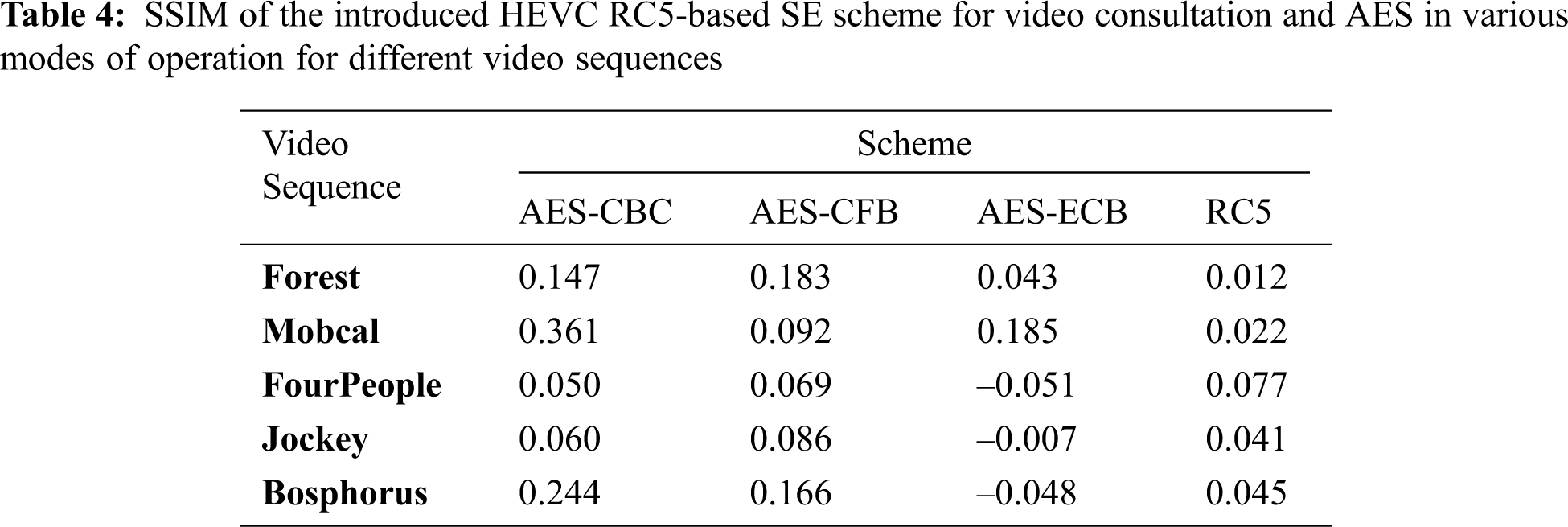
Fig. 2 shows the Histograms of the plain and ciphered videos for frame number 50 of the FourPeople using the introduced HEVC RC5-based SE at several QP values. From the outcomes, it was evident that the histograms of encrypted frame number 50 of the FourPeople using the introduced HEVC RC5-based SE scheme are entirely different from the histogram of plainvideo for frame number 50 of the FourPeople at several QP values. Again, these findings guarantee the superiority of the introduced HEVC RC5-based SE scheme for video consultation at several QP values.
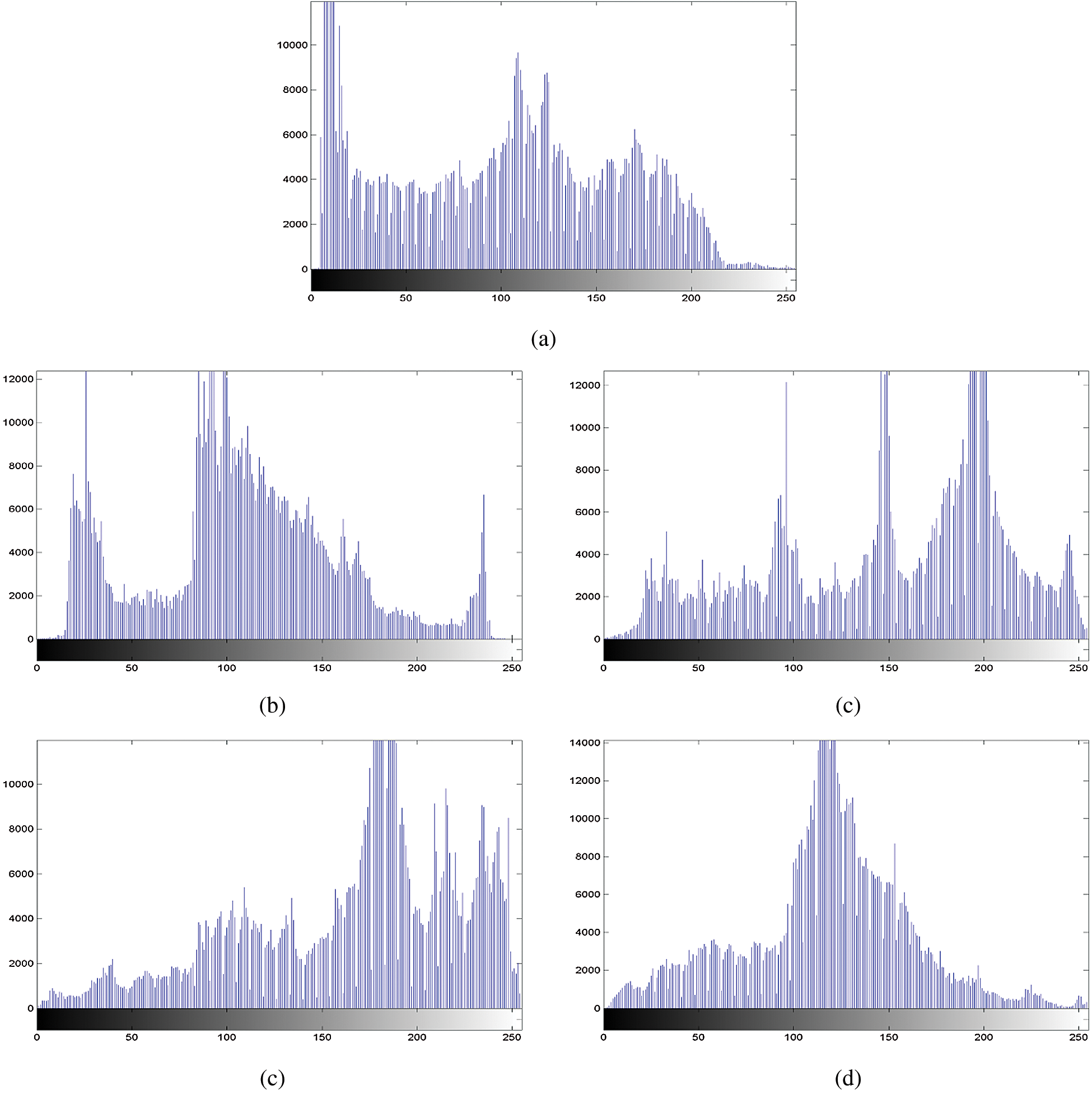
Figure 2: Histogram outcomes of plainvideo and ciphervideos for frame number 50 of FourPeople sequence using the introduced HEVC RC5-based SE for video consultation at several QP values a) Histogram of original FourPeople video sequence frame number 50 b) Histogram of encrypted FourPeople video sequence frame number 50 at QP = 37 c) Histogram of encrypted FourPeople video sequence frame number 50 at QP = 32 d) Histogram of encrypted FourPeople video sequence frame number 50 at QP = 27 e) Histogram of encrypted FourPeople video sequence frame number 50 at QP = 22
4.3 Correlation Coefficient Analysis
Fig. 3 and Tab. 5 indicate that in different directions, the suggested framework has low correlation values that guarantee an appropriate video visual distortion that holds video consultation private in real-time. The correlation coefficients of the proposed HEVC RC5-based SE scheme in different directions for different video sequences are listed in Tab. 5. Also, Fig. 3 shows the correlation coefficients of the introduced HEVC RC5-based SE scheme for the different video sequences. From the illustrated results in both Tab. 5 and Fig. 3, the proposed HEVC RC5-based SE scheme achieves lower correlation coefficient values in all directions, which guarantees a satisfactory level of visual distortion for HEVC sequences and confirms the confidentiality and secrecy of the introduced HEVC RC5-based SE scheme for online video consultations.
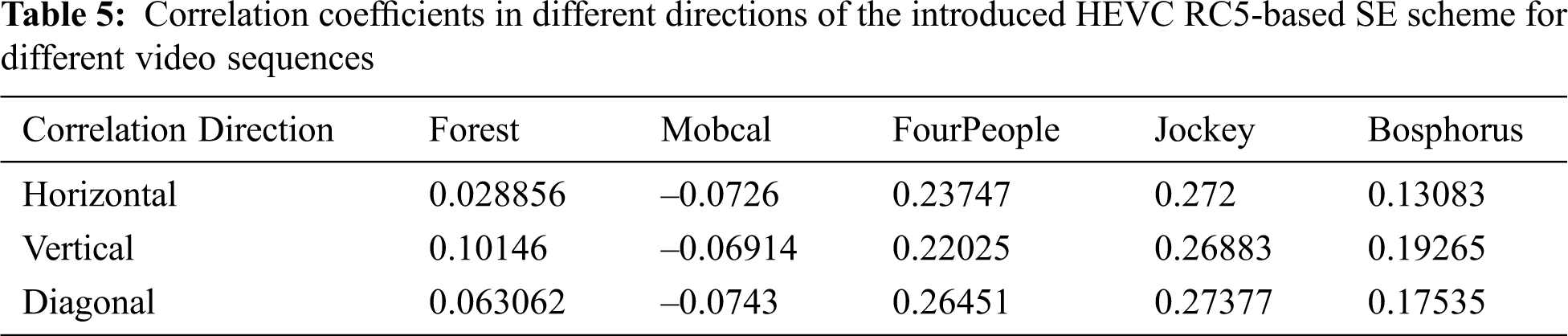
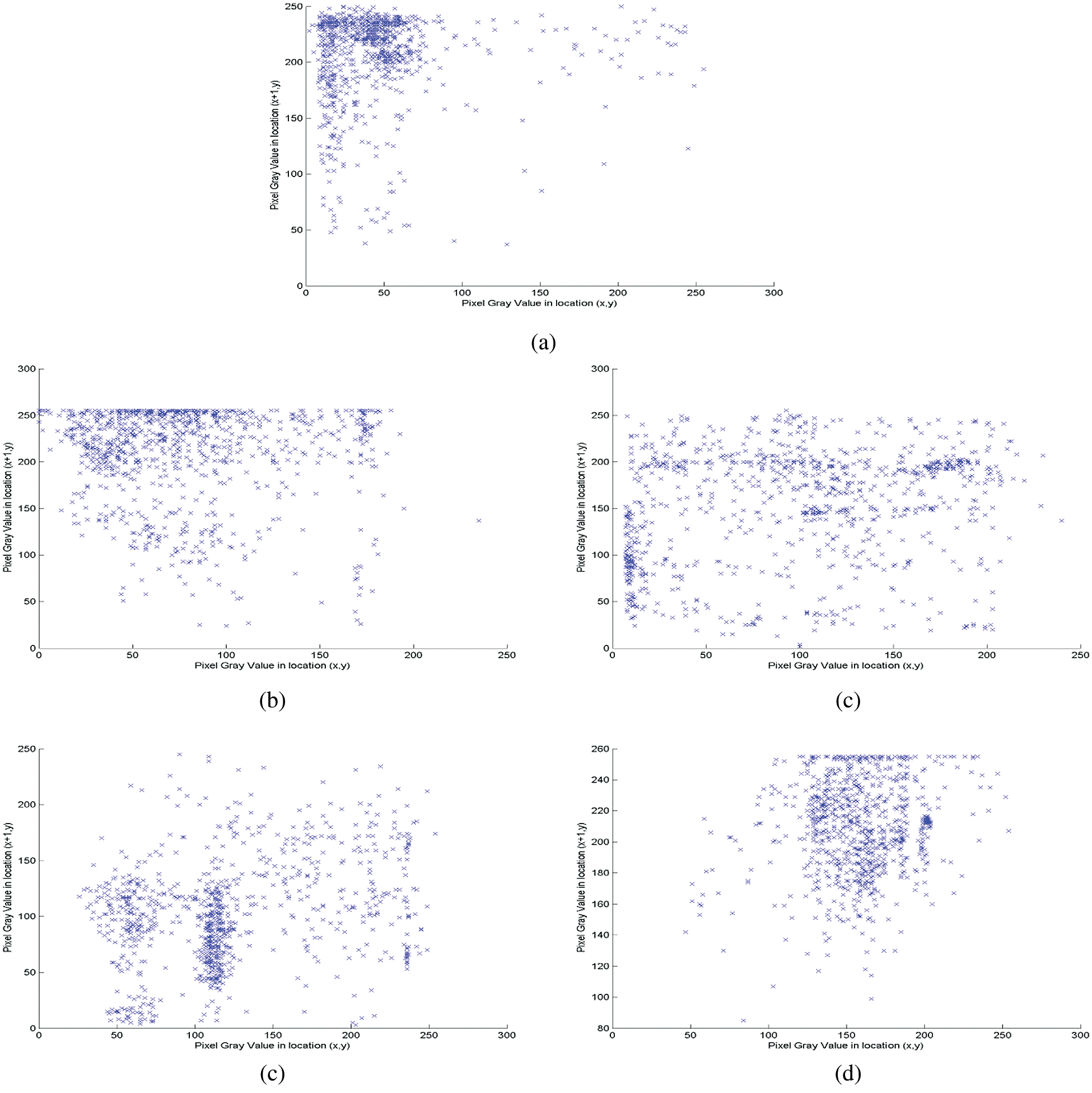
Figure 3: Correlation coefficients of the introduced HEVC RC5-based SE scheme for different video sequences a) Forest b) Mobcal c) FourPeople d) Jockey e) Bosphorus
The video encoding scheme should be sensitive to tiny slight alternations in the utilized secret key in the introduced HEVC RC5-based SE scheme. Therefore, the following steps are taken to investigate the key sensitivity of the introduced HEVC RC5-based SE scheme:
a) Frame number 50 of the FourPeople plainvideo in Fig. 4a is encrypted with the key “1844674407370951610” using the introduced HEVC RC5-based SE scheme, and the encryption result is illustrated in Fig. 4b.
b) The same frame number 50 of the FourPeople plainvideo in Fig. 4a is encrypted with the key “0844674407370951610” using the introduced HEVC RC5-based SE scheme, and the encryption result is illustrated in Fig. 4c.
c) Calculate the correlation coefficient of encryption results in Figs. 4b and 4c.
Fig. 5 shows the correlation coefficient between the two encryption results of encrypting frames number 50 of FourPeople plainvideo sequence using the introduced HEVC RC5-based SE scheme with two slightly different keys as illustrated in Figs. 4b and 4c that are primarily equal except in the most significant bit position. The achieved correlation coefficient result, which is slightly minimal guarantees and proves the high sensitivity of the introduced HEVC RC5-based SE scheme to tiny changes in the secret key.
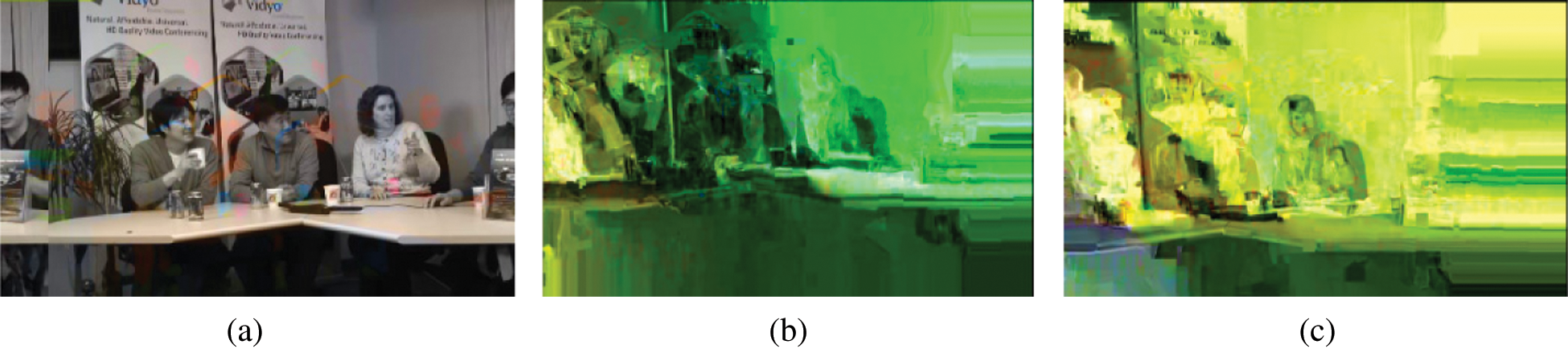
Figure 4: Key sensitivity test of the introduced HEVC RC5-based SE scheme a) Frame number 50 of FourPeople plainvideo sequence b) Encrypted frame number 50 of FourPeople plainvideo sequence with key “18446744073709551610” c) Encrypted frame number 50 of FourPeople plainvideo sequence with key “08446744073709551610”
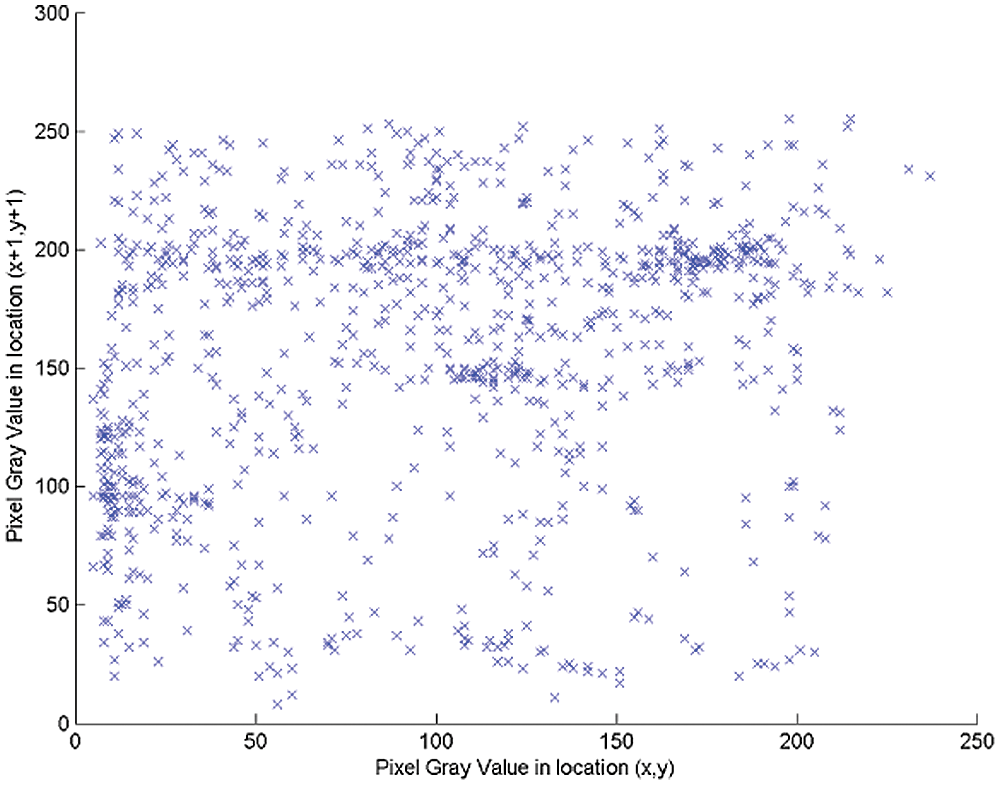
Figure 5: Correlation coefficient between the two encryption results of encrypting frame number 50 of FourPeople plainvideo sequence using the introduced HEVC RC5-based SE scheme with two slightly different keys as illustrated in Figs. 4b and 4c
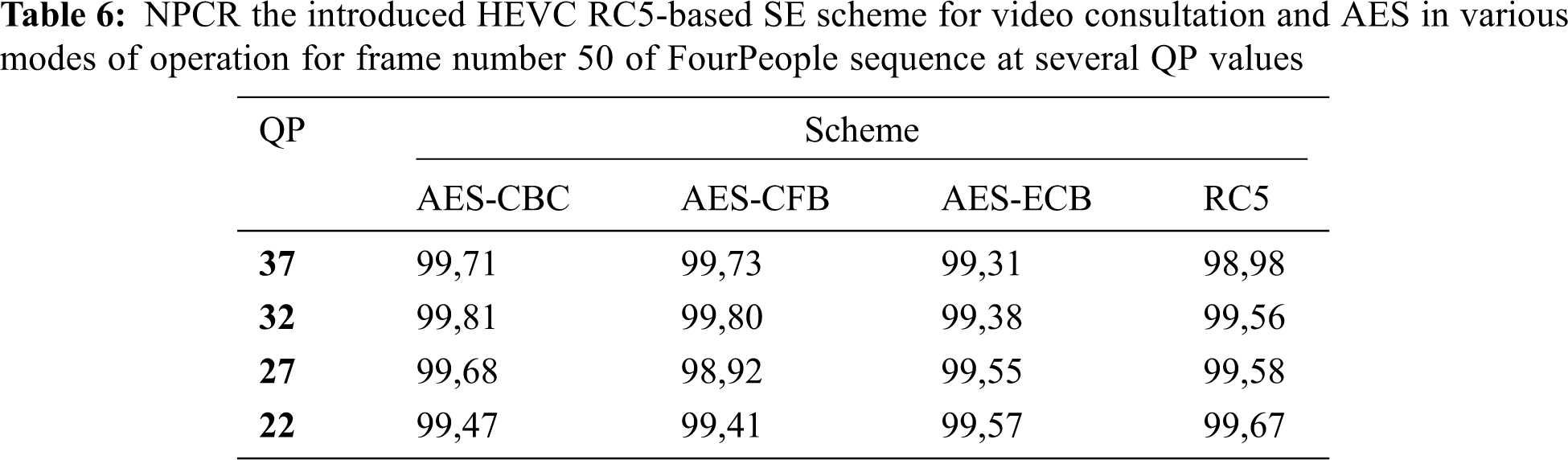
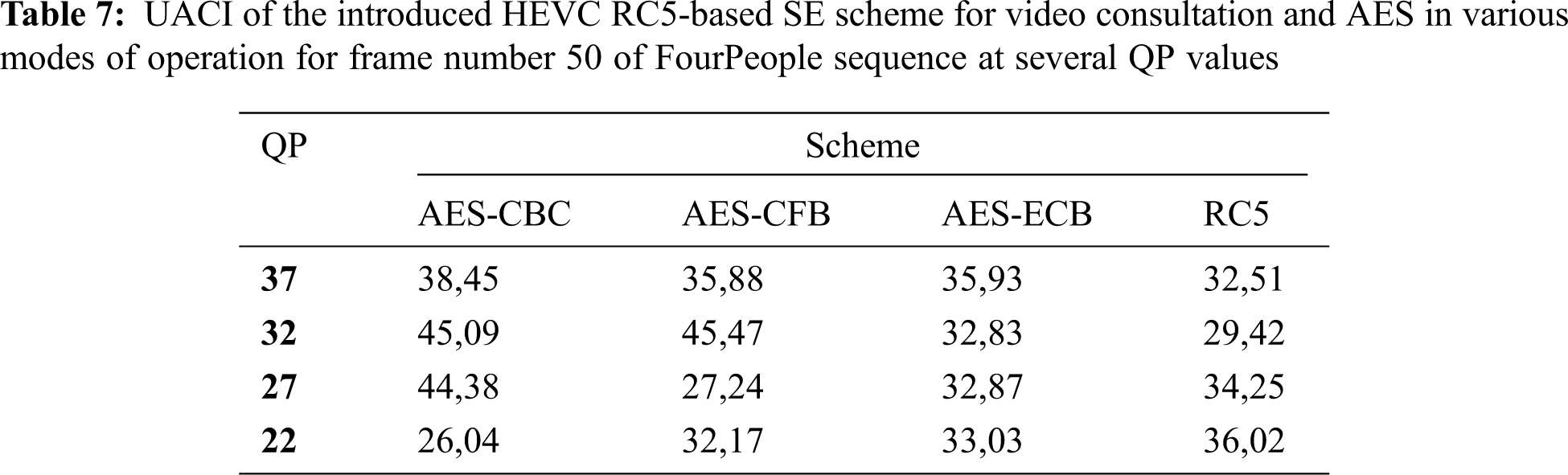
The NPCR and UACI scores of the introduced HEVC RC5-based SE scheme and other schemes that employ the AES encryption algorithm in different operation modes for frame number 50 of the FourPeople sequence at several QP values are listed in Tabs. 6 and 7. For efficient encryption of HEVC, it must obtain higher values for both the NPCR and UACI. The NPCR values in Tab. 6 illustrate that the introduced HEVC RC5-based SE scheme for video consultation has higher NPCR values than AES in various modes of operation for frame #number 50 of the FourPeople at several QP values. Again, this proves the superiority of the introduced HEVC RC5-based SE scheme to HEVC SE using AES in various modes of operation for frame #50 of the FourPeople sequence at different QP values. The UACI values in Tab. 7 illustrate that the introduced HEVC RC5-based SE scheme for video consultation has higher UACI values than AES in various modes of operation for frame number 50 of the FourPeople at several QP values. Again, this proves the superiority of the introduced HEVC RC5-based SE scheme to HEVC SE using AES in various operation modes for frame number 50 of the FourPeople at several QP values.
Video meetings in healthcare include the sharing of clinical data across sites through video appointments to optimize the health of the patient. Moreover, with the COVID-19 apparition, people needing regular treatment should expand the usage in their home of video appointments, thus holding recipients with temperate symptoms in need of medical care open. In addition to minimizing interactions with other patients and physicians, the COVID-19 spread would slow down by reducing the population rise. The dissemination of the coronavirus caused unique health care needs. The accelerated dissemination of the virus has restored telemedicine to sustain healthcare without raising the likelihood of probable contact between patients and physicians. This research reflects the confidential security of the more recent digital video coding (HEVC) used in the most recent framework for health video consultations. This research will primarily develop a selective HEVC encryption strategy with functionality to maintain the video format compliance, equivalent bitrate and protection with low device complexity constraints in online video consulting applications. Conformity to the format is defined as keeping the HEVC coding structure encrypted video, which any standard HEVC decoder can decrypt. By encrypting such HEVC syntax functions, the methodology suggested ensures specification compliance that any alteration would not modify the format and preserve equivalent bitrate. In addition, the RC5 provides an effective method for encryption of DCT and MVD sign bits and suffix absolute values in the HEVC video encoding entropy process. RC5 is employed to encrypt sensitive parts of the video, which provides low time delay, maintains the HEVC bitrate and format enforcement, and helps with the HEVC selective encryption. We equate the video consultation framework suggested with the AES in the CFB mode scheme in this article. This contrast shows that the time required for low-resolution videos and high-resolution videos decreases by 0.7 and 19 seconds, respectively, in the introduced HEVC RC5-based SE scheme for video consultation. The protection review also revealed an adequate HEVC visual distortion under the introduced HEVC RC5-based SE scheme for video consultation that can protect against the remote attacks in real-time.
Acknowledgement: This study was funded by the Deanship of Scientific Research, Taif University Researchers Supporting Project number (TURSP-2020/08), Taif University, Taif, Saudi Arabia.
Funding Statement: This study was funded by the Deanship of Scientific Research, Taif University Researchers Supporting Project number (TURSP-2020/08), Taif University, Taif, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Zhao, Z. C. Yang, X. G. Zhou, X. Z. Ling, L. S. Mora et al., “Design, fabrication, characterization and simulation of PIP-SiC/SiC composites,” Computers, Materials & Continua, vol. 42, no. 2, pp. 103–124, 2014. [Google Scholar]
2. J. E. Hollander, “Carr BG. Virtually Perfect? Telemedicine for Covid-19,” N Engle J Med, vol. 382, no. 18, pp. 1679–1681, 2020. [Google Scholar]
3. T. Greenhalgh, J. Wherton, S. Shaw and C. Morrison, “Video consultations for COVID-19,” BMJ, vol. 368, m998, pp. 1–2, 2020. [Google Scholar]
4. N. Lurie and B. G. Carr, “The role of telehealth in the medical response to disasters,” Jama Internal Medicine, vol. 178, pp. 745–746, 2018. [Google Scholar]
5. J. G. Zamora, J. L. Alave, D. F. Corvino and A. Fernandez, “Video conferences of infectious diseases: An educational tool that transcends borders. A useful tool also for the current COVID-19 pandemic,” Le infezioni in medicina, vol. 28, no. 2, pp. 135–138, 2020. [Google Scholar]
6. G. Flodgren, A. Rachas, A. J. Farmer, M. Inzitari and S. Shepperd, “Interactive telemedicine: Effects on professional practice and health care outcomes,” Cochrane Database Syst., vol. 9, pp. 1–3, 2015. [Google Scholar]
7. J. Vidal-Alaball, R. Acosta-Roja, N. P. Hernández, U. S. Luque, D. Morrison et al., “Telemedicine in the face of the COVID-19 pandemic,” Atención Primaria, vol. 52, pp. 418–422, 2020. [Google Scholar]
8. C. Bertoncello, M. Colucci, T. Baldovin, A. Buja and V. Baldo, “How does it work? factors involved in telemedicine home-interventions effectiveness: A review of reviews,” PLoS One, vol. 13, no. 11, pp. e0207332, 2018. [Google Scholar]
9. J. A. Mallow, T. Petitte, G. Narsavage, E. R. Barnes, E. Theeke et al., “The use of video conferencing for persons with chronic conditions: A systematic review,” E-Health Telecommun. Syst. Netw., vol. 5, pp. 39–56, 2016. [Google Scholar]
10. L. Peters, G. Greenfield, A. Majeed and B. Hayhoe, “The impact of private online video consulting in primary care,” J. R. Soc. Med, vol. 111, pp. 162–166, 2018. [Google Scholar]
11. D. Spence, “Bad medicine: The future is video consulting,” Br J Gen Pract, vol. 68, no. 674, pp. 437, 2018. [Google Scholar]
12. B. Nordtug, H. V. Brataas and L. Rygg, “The use of videoconferencing in nursing for people in their homes,” Nurs. Rep, vol. 8, no. 1, pp. 1–8, 2018. [Google Scholar]
13. A. Ignatowicz, H. Atherton, C. J. Bernstein, C. Bryce, R. Court et al., “Internet videoconferencing for patient-clinician consultations in long-term conditions: A review of reviews and applications in line with guidelines and recommendations,” Digit. Health, vol. 5, pp. 1–27, 2019. [Google Scholar]
14. B. Furht and D. Socek, “A survey of multimedia security,” Technical Report, pp. 1–24, 2003. [Google Scholar]
15. Y. Tew and K. Wong, “An overview of information hiding in H.264/AVC compressed video,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 24, no. 2, pp. 305–319, 2014. [Google Scholar]
16. X. Ma, W. Zeng, L. Yang, D. Zou and H. Jin, “Lossless ROI privacy protection of H.264/AVC compressed surveillance videos,” IEEE Transactions on Emerging Topics in Computing, vol. 4, no. 3, pp. 349–363, 2016. [Google Scholar]
17. F. Liu and H. Koenig, “A survey of video encryption algorithms,” Journal of Computers & Security, vol. 19, no. 1, pp. 3–15, 2010. [Google Scholar]
18. K. Goswami, J. Lee and B. Kim, “Fast algorithm for the high efficiency video coding (HEVC) encoder using texture analysis,” Information Sciences, vol. 364, no. 1, pp. 72–90, 2016. [Google Scholar]
19. M. Asghar, R. Kousar, H. Majid and M. Fleury, “Transparent encryption with scalable video communication: Lower-latency, CABAC-based schemes,” Journal of Visual Communication and Image Representation, vol. 45, no. 1, pp. 122–136, 2017. [Google Scholar]
20. M. Abomhara, O. Zakaria and O. O. Khalifa, “An overview of video encryption techniques,” International Journal of Computer Theory and Engineering, vol. 2, no. 1, pp. 103–110, 2010. [Google Scholar]
21. H. Hofbauer, A. Unterweger and A. Uhl, “Transparent encryption for HEVC using bit-stream-based selective coefficient sign encryption,” in Proc. of IEEE Int. Conf. on Acoustics, Speech and Signal Processing (ICASSPpp. 1986–1990, 2014. [Google Scholar]
22. Y. Tew, K. Minemura and K. Wong, “HEVC selective encryption using transform skip signal and sign bin,” in Proc. of APSIPA Annual Summit and Conf., pp. 963–970, 2015. [Google Scholar]
23. Z. Shahid and W. Puech, “Visual protection of HEVC video by selective encryption of CABAC binstrings,” IEEE Transactions on Multimedia, vol. 16, no. 1, pp. 24–36, 2014. [Google Scholar]
24. J. V. Wallendael, A. Boho, J. D. Cock, A. Munteanu and R. V. Walle, “Encryption for high efficiency video coding with video adaptation capabilities,” IEEE Transactions on Consumer Electronics, vol. 59, no. 3, pp. 634–642, 2013. [Google Scholar]
25. J. Li, C. Wang, X. Chen, Z. Tang, G. Hui et al., “A selective encryption scheme of CABAC based on video context in high efficiency video coding,” Multimedia Tools Appl, vol. 77, no. 10, pp. 12837–12851, 2018. [Google Scholar]
26. W. Hamidouche, M. Farajallah, N. Ould-Sidaty, S. El Assad and O. Déforges, “Real-time selective video encryption based on the chaos system in scalable HEVC extension,” Signal Processing: Image Communication, vol. 58, pp. 73–86, 2017. [Google Scholar]
27. B. Boyadjis, C. Bergeron, B. Pesquet-Popescu and F. Dufaux, “Extended selective encryption of H.264/AVC (CABAC) and HEVC-encoded video streams,” IEEE Trans. Circuits Syst. Video Technol, vol. 27, no. 4, pp. 892–906, 2017. [Google Scholar]
28. J. Meyer and F. Gadegast, “Security mechanisms for multimedia data with the example MPEG-1 video,” Project Description of SECMPEG. Berlin: Technical University of Berlin, 1995. [Google Scholar]
29. C. Shi and B. Bhargava, “A fast MPEG video encryption algorithm,” in Proc. of the 6th Int. Multimedia Conf., Bristol, UK, pp. 81–88, 1998. [Google Scholar]
30. M. Nithin, L. Damien and R. David, “A novel secure H.264 transcoder using selective encryption,” in Proc. of the IEEE Int. Conf. on Image Processing, pp. 85–88, 2017. [Google Scholar]
31. A. Hore and D. Ziou, “Image quality metrics: PSNR vs. SSIM,” in Proc. of IEEE Int. Conf. on Pattern Recognition, pp. 2366–2369, 2010. [Google Scholar]
32. MSU Graphics and Media Lab, Video Group, MSU codecs, www.compression.ru/video/. Access Date: 1/6/2020. [Google Scholar]
33. https://media.xiph.org/, Access Date: 1/6/2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |