DOI:10.32604/iasc.2022.025091

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2022.025091 |  |
| Article |
A Secure E-commerce Environment Using Multi-agent System
Computer Science Department, University of Technology, Baghdad, 10011, Iraq
*Corresponding Author: Farah Tawfiq Abdul Hussien. Email: Farah.T.Alhilo@uotechnology.edu.iq
Received: 11 November 2021; Accepted: 10 January 2022
Abstract: Providing security for the customers in the e-commerce system is an essential issue. Providing security for each single online customer at the same time is considered a time consuming process. For a huge websites such task may cause several problems including response delay, losing the customer orders and system deadlock or crash, in which reduce system performance. This paper aims to provide a new prototype structure of multi agent system that solve the problem of providing security and avoid the problems that may reduce system performance. This is done by creating a software agent which is settled into the customer device to be responsible of purchase and encryption process without the customer interfering. The proposed agent avoids the problem of deadlock (i.e., break down) and the loss of requests which provides the required protection for information transmitted among all entities. Experimental results showed that employing software agent to manage purchase and encryption tasks improve system performance by 10% and increase system response time by 30.5%.
Keywords: Software agent; multi agent; e-commerce security; order form; purchase management; encryption management; PEAS
Nowadays e-commerce systems play an essential rule in providing various and huge amount of products and services [1]. Day by day the number of the customers dealing with these systems are increasing due to the facilities provided by these systems [2,3]. Therefore, the amount of information that are transmitted over the internet are increased [4,5]. Some of these information are considered as crucial information especially the payment information that may be exposed to different types of attacks [6]. Therefore, providing security for the e-commerce websites became an essential feature that must be provided to gain the customers confidence [7,8]. Here another issue raise to the surface, that is providing security for each online customer may be a difficult job (especially for huge commercial websites) that may reduce performance and slowing the system responding time speed, this will cause financial problems due to the customers upset from the service quality provided by the website [9,10]. Securing e-commerce systems can be performed using different approaches, one of them is using encryption. There are lots of papers that suggests different and various modifications on different types of encryption algorithm. In this paper the concentration is on how and where to provide security not on encryption algorithm by itself [11]. An agent prototype structure is suggested to be responsible of two main tasks for each customer, purchase and security management that will be discussed later in details. An agent is chosen to perform this tasks due to its’ features which involve, mobility, goal oriented, independent, intelligent, reduce net traffic, and multiple tasks [12–14]. These features made the agent an identical tool to perform two or more tasks effectively [15]. So the main concentration in this paper is to provide a structure that help in reducing traffic of the web site and providing security with efficient performance.
The intelligent e-shopping system has been proposed utilizing data mining in various papers [16,17]. However, it is just too sluggish. The agent technology may be used to cut down on the amount of time that an e-commerce system based on a web application and data mining takes. Amazon, a well-known online book retailer, employs a web-based application that is sluggish and inefficient due to the following drawbacks such as It necessitates direct user interaction, It takes a long time, and Comparing products is challenging.
Besides these, the web based applications are difficult to scale [18], but the agent based applications are very easy to scale. An agent is considered by some authors as a living thing that can communicate and form groups with other living things [19,20]. An agent will have a role or responsibilities in the groups that are established, and he or she may join many groups at the same time [21]. The architecture of an agent is unrestricted; agents may be created to have traits such as reactivity, pro-activeness, cognitiveness, mobility, and others [22,23]. An agent should be able to deliver services to other system entities, and its services should be available via the agent’s identifier [24–26]. As shown previously, there are two main problems resulted from securing the communications, time consuming and deadlock [27–29]. To solve these problems an agent system is designed to be a vendor between the client and the e-commerce website. This is done by settling an agent program in the device of each client dealing with a certain commercial website to collect clients’ orders, ensure that these orders are sent to the website and avoid deadlock that may occur in rush hours by collecting these orders and sending them later as offline [30]. Furthermore, an agent is responsible for security operation (encryption and key management). Moreover, software agents support automated diversity of actions, especially actions that consume time, and thus they reduce the cost of the transaction [31,32]. Therefore, e-commerce is considered more user-friendly, semi-intelligent and human-like. These features aid the enhancement of e-commerce system [33,34].
In another words providing the security for each single customer is time consuming which slows the system speed also in the rush time there will be a huge number of customers to be served especially for huge sites providing the security for each single online customer at the same time may lead to system crush or delay in many orders that will have negative sound. The agent prototype structure which is suggested in this paper aims to solve this problem. Achieving the security of communication among clients and the e-commerce website should take into account the following security dimensions:
a) Integrity–It makes sure that unauthorized persons cannot use, alter or interfere any data or information without clients’ agreement [35].
b) Non-repudiation–It ensures that any selling or buying process cannot be denied [36].
c) Authentication–It ensures that system permits only authorized users to logon [37].
d) Confidentiality–It offers strong encryption for sensitive data that cannot be easily broken [38,39].
e) Privacy–It restricts the ability to gain and use private data [40].
f) Availability–It means that the system software is continuously available, the hardware equipment function correctly, and the ability to recover the system quickly in s disaster situation [41].
According to Abdullah [42], the security strategies of e-commerce handle only two chief problems: the security of business network integrity and the internal systems, and securing transactions among the clients and the seller [43]. There are several threats that face e-commerce websites. These threats are divided into [44–46]:
a) Communication threats which involve: Authentication Attacks, Integrity Attacks, and Confidentiality Attacks.
b) Environment threats which involve: Virus, Trojan Horse, and Worms.
c) Database threats.
As shown previously, there are two main problems resulted from securing the communications, time consuming and deadlock [47–49]. To solve these problems an agent system is designed to be mediator between client and e-commerce website. This is done by putting an agent program in the device of each client dealing with a certain commercial website to collect client order, ensure that these orders are sent to the website and avoid deadlock that may occur in rush hours by collecting these orders and sending them later as offline [50,51]. Furthermore, an agent is responsible for security operation (encryption and key management).
Moreover, software agents support automated diversity of actions, especially actions that consume time, and thus they reduce the cost of the transaction [52–54]. However, software agents vary from “traditional” social and personalized software that are always working in a semiautonomous situation. Therefore, e-commerce is considered more user-friendly, semi-intelligent and human-like. These features aid the enhancement of e-commerce system [55,56].
This study focuses on the importance of the software agent in e-commerce system. The following gaps in e-commerce systems are Time consuming, System deadlock, System throughput, and Response speed (time). For each e-commerce system, providing security becomes an essential need due to the huge size and the importance of transmitted data over the internet which exposed it to different types of attacks. Many papers suggested different approaches to provide security. The key point is that providing security for each single online customer is considered time consuming process that may affect the system performance. This can be seen in the huge websites, in which providing security for huge number of customers at the same time may cause a huge load on system server which is resulted into system deadlock or crash. Another possibility is that providing security for a huge number of customers at the same time may cause delay response or losing some of the requests. This possibility reduced system performance and efficiency. The main contributions of our study are:
a) Design a prototype structure of multi-task software agent. Settling the software agent inside the customer device. The software agent is responsible of two tasks: purchase and encryption management under the control of the e-commerce system. The encryption process is performed without the customer interfering.
b) Generate a special form that contains the purchase details and the customer information and named it as order form.
c) Generate a unique software agent that is responsible of serving a single customer only and connect between them using the customer and the agent IDs.
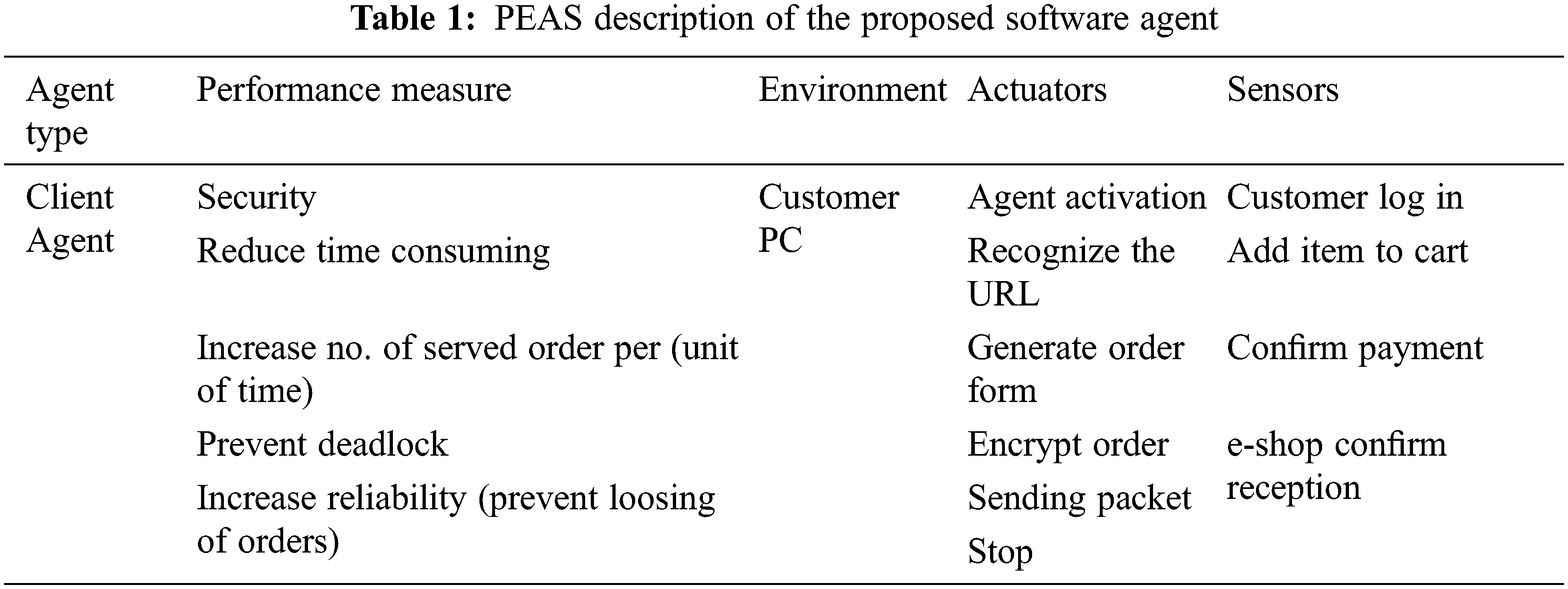
d) Determine system tasks by using the performance, environment, actuators and sensors (PEAS) framework.
The rest organization of this study are: Section 2 presents related works, Section 3 represent the research methodology, Section 4 explains the results and discussion and Section 5 represent the conclusions.
According to [27] suggested an agent-oriented procedure which provides verification to execute security objectives and the requirements of security validation during the various stages of developed system lifecycle. Furthermore, the system requirements to provide mapping for the security list of risks in order to decide if any of the threats in the list can be applied to the system to be improved. A checklist of security is built automatically by the meta-agents to control activities that are taken by client agent. Another study by [28] suggested a multi-agent e-commerce system based on block chain technique. First, the agent technology in e-commerce system was presented, then the concealed risks were explained. Second, information transaction and executive structure is put forward. Lastly, examining the node of verification method in the process of agent transaction. Also [29] suggested a prototype for multi-agent systems security. It was improved depending on the principles and models concerning agent’s role and communication. It offered an effective method for ensuring that the requirements of security and design were integrated with system tasks throughout the development process. Furthermore, attacks and threats were categorized. Some threats were considered such as corrupting mobile agents attack the chief system host, fake agent, and unconfident communication between the platforms in addition to the threats of agent level. That is to say, agent authentication, fake message, alteration of agents’ interaction can be dealt with by changing the transporting information, message injection, and intrusion detection to agents. This study is considered an extension of Gaia methodology with the security model.
Another study proposed by [31] showed the main vulnerabilities that can happen in multi-agent systems in charge of handling e-commerce applications. In addition, they suggested solutions to the main difficulties of security on these platform systems. The major assumptions provided by this study is that security measures should optimize and improve the diverse solutions of security employed in the application of e-commerce to avoid identity robbery, admission to private data, and access controlling, etc. Therefore, it is a vital issue to improve the methods of security that were employed in applications such as e-commerce due to the continued evolving of different types of attacks and threats.
The previous works only discussed the tasks of the agents but did not discussed the structure or description of the used agent. For our software agent we used the performance, environment, actuators, sensors (PEAS) model which will be discussed later. In addition system performance is measured according to what is required in the environment not what the agent is expected to do. Another feature of our system is that the customer is not involved in the encryption process. It is performed under the agent complete control. Also for each customer there is a unique agent which is engaged to the customer via ID. Another feature of our system is that providing security, most of the previous works did not focuses on security issue, only on providing services for the customer depending on the agents. In addition providing security using encryption algorithm in which the encryption process performed and managed by the software agent is not performed before in this pattern. The proposed system suggested to generate a single software agent to be setting inside the customer serving only this customer, No research paper has discussed or submitted the agent’s tasks and structure in this manner before.
This section describes the methods and procedures of the research. Figs. 1 and 2 represent system block diagram that describes system activities and data flow among system entities.
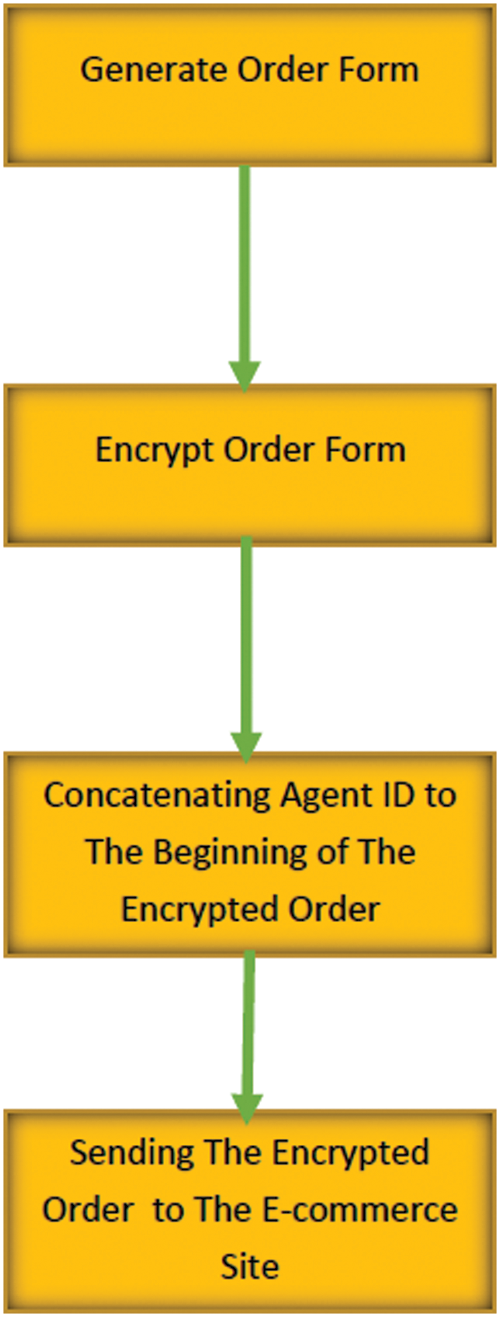
Figure 1: Agent activities at a client’s device when making an order for buying a product
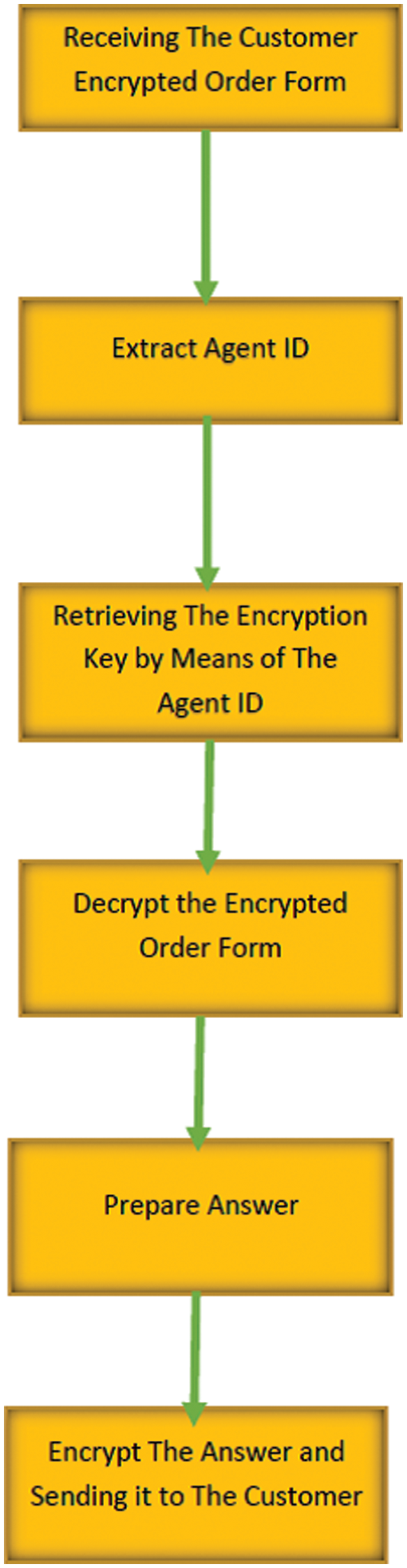
Figure 2: Activities of receiving and decrypting a message at the commercial website
The proposed system aims to build an integrated system that can solve the previous systems’ problems of time consumption, deadlock and unsecured communication channel that decreases clients’ confidence in the e-commerce system. This is designed by setting an agent program into a client’s device such that each client visits and buys from a certain commercial website that provides a means of identity verification of the client. The agent consists of two main parts: the first part is responsible for client requests and orders by converting these orders as a special form that can be submitted to the website at any time and reduce the problem of deadlock by collecting these requests into cloud to prevent orders from being discarded due to website server overload at rush the time. The second part of the proposed system is responsible for securing communication between clients and the commercial website. This is done by providing encryption algorithm (provided by the commercial website) which can be changed periodically together with a key exchange which is provided by the commercial website for each client. This key exchange is also changed periodically to minimize time consumption so as to provide security online for each client reaching the website. For this purpose, security consists of two levels:
a) Key exchange which occur periodically.
b) Higher level of security which is responsible for encryption using certain encryption algorithm which can also be changed periodically as needed.
The essential need to provide security for the transmitted data over the internet especially the payment information represent a critical issue. Providing security for each single customer navigates the e-commerce site at the same time expose the network and the e-commerce server to huge load which may lead to system crush. To reduce and prevent such damage, this paper suggests an agent prototype structure which is responsible of two tasks, purchase and security management. The process can be described as follow:
a) For each customer who has an account, there will be an agent which is settled into his device. This agent is generated by the e-commerce and programmed to manage two tasks purchase and security.
b) The agent is settled into the customer device after his agreement.
c) For each order, the agent will generate a form which is called order form that contains the purchase details as invoice.
d) This invoice is encrypted to protect the customer information from any altering or steal and then is sent to the e-commerce site.
e) The encryption process is achieved using light weight AES to save time.
f) At the receiver the form is decrypted by depending on the agent Id that refers to the customer information. It is a mean to retrieve the encryption password.
g) The encryption process is performed without the customer interfering ( the user does not know the key of the encryption).
h) The encryption key is generated and transformed to the agent without the customer interfering.
i) A symmetric encryption is used because the encryption process is managed by only one side ( the e-commerce site ) the agent which is responsible of the encryption is generated and supported with the password without the customer interfering.
j) The password has an expiry date so it is changed after using it for 10 times then a new encryption key is generated and is sent to the agent and the old one in the e-commerce database is updated or placed by the new one and the user does not need to know it.
k) As an authentication process for the first time using of the agent the customer will be asked to choose a password which is used every time the customer intend to use his password to insure of his identity.
3.2 The Agent Structure Description
The relationship between the agent and the customer in e-commerce environment can be described as follow:
The relation is Tuple <A, C, E> where:
A = set of agents
C = set of customers
E = E-commerce site
Each agent is engaged with a single customer (is settled into his/her device) such that :
∀ ci in {C}, ∃ an ai in {A} such that ai:
a) Has a unique ID.
b) Performs two tasks (purchase and security management).
c) There are set of rules that control the agent behavior :
• ci must has an account in the e-commerce site.
• ci does not interfere with the encryption process.
• ci must use a password to activate the agent tasks.
• only a single ci owns a certain ai (ai can serve only one customer all his life).
The agent works as an authentic vender between the e-commerce and the customer. It is authentic because:
a) It is generated and controlled by the principle of the owner (the e-commerce site).
b) It is authentic because it is settled by the agreement of the customer.
c) It works like cookies to make the URL that is visited before is known to the device and vice versa (to remember the location and the preferences).
d) It is easy because it keeping the password inside it and thus reducing the probabilities to be stolen by any intruder.
e) It is not a token because even if the customer device is stolen it won’t work without inserting the customer activation password.
f) The encryption process is performed according to a policy is generated and employed by the e-commerce system.
g) Eliminate the problem of choosing a week password because it is generated and updated for each single customer with expiry date (10 times to be used).
h) The customer ensures that his crucial information is protected by a certified side due to the common benefits.
The proposed agent is responsible for two main tasks: purchasing management and security management.
When designing an agent the first step must always be to specify the task environment as fully as possible. Task environment is the description of performance, environment, actuators and sensors and referred to as (PEAS). For the proposed system the PEAS description is represented in Tab. 1.
This task can be described by the following steps:
a) A client visits an e-commerce website.
b) A product is chosen to be bought.
c) Conversion of the chosen product to a special form by the agent. This form is called a Record Form that consists of such details as User ID, Agent ID, Product ID, Quantity, Address, and Time. After performing these steps, the form is forwarded to security management as shown in Fig. 3.
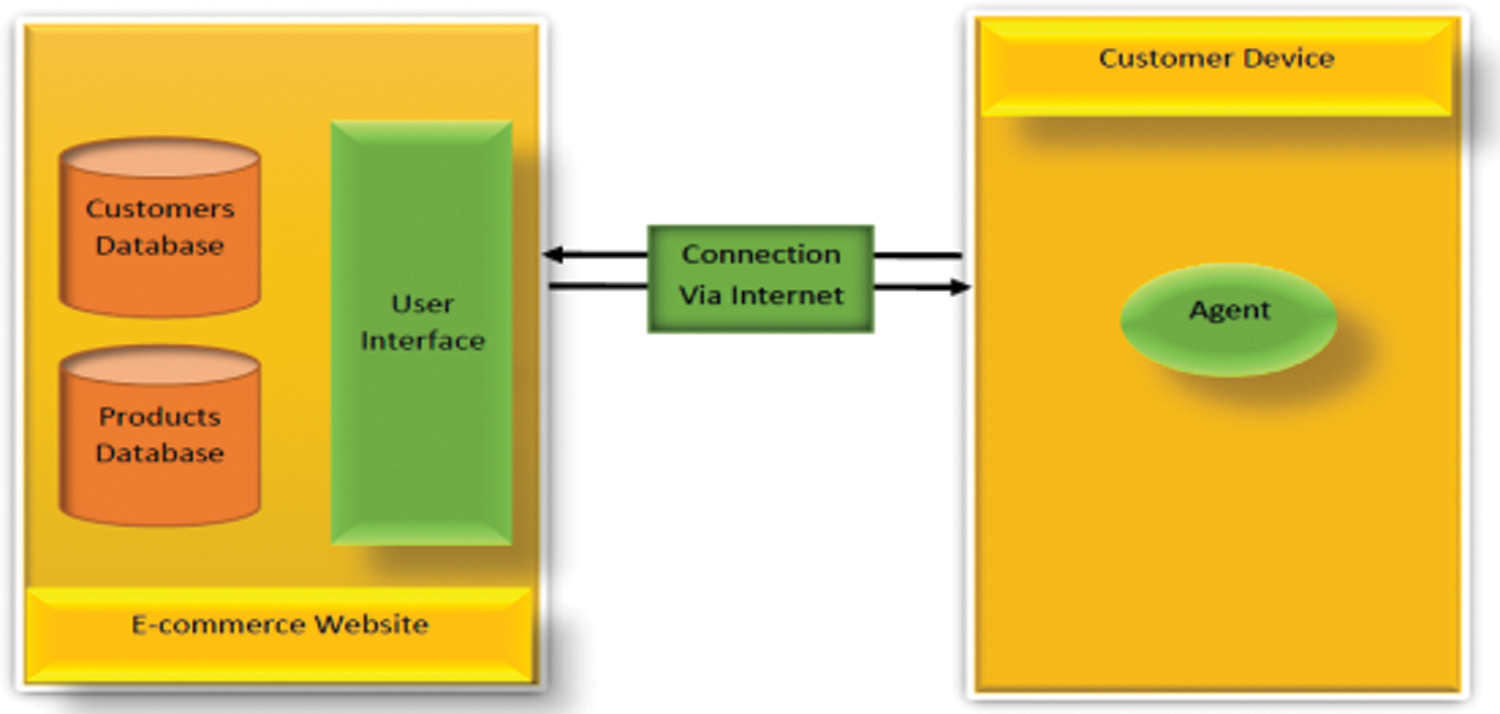
Figure 3: Proposed system design
This task consists of two main processes as follows:
a) Key management: In this phase a unique key is generated and forwarded to each client. This key can be changed periodically. Key generation and exchange are done under the control of the e-commerce website by means of agent aids. The client is not part in this process.
b) Encryption phase: This task involves receiving the order form from the purchasing phase and encrypt it by means of symmetric encryption algorithm and encryption key. After the encryption process is made, the agent id is appended to the cipher text then sent to the commercial website to be decrypted by means the agent id. The correct encryption key will be chosen for decrypting the received message.
This is done because e-commerce website has a database to store information for each client having an account into the site. This information involves agent id, user id, encryption key, and other information. When the e-commerce website sends a response to the client, the response should contain digital signature (which is also encrypted using the same encryption key). The digital signature is used to verify that the response is sent from the e-commerce website.
The processes of the proposed system can be described by these two algorithms: generating and encrypting order form as follows:

All these processes are done without the client intervention. They are done under the control of the e-commerce website by means of the agent at the client device by constructing agent software programmed to have fixed rules to follow. This agent is identified, implemented and activated through client agreements, so when the client visits the website for the first time he\she will be identified by the commercial website. Thus it offers an additional means for verifying the client identity besides other processes that will be performed by the agent to increase security for both the client and the commercial websites. Fig. 4 represent the proposed system design and tasks.

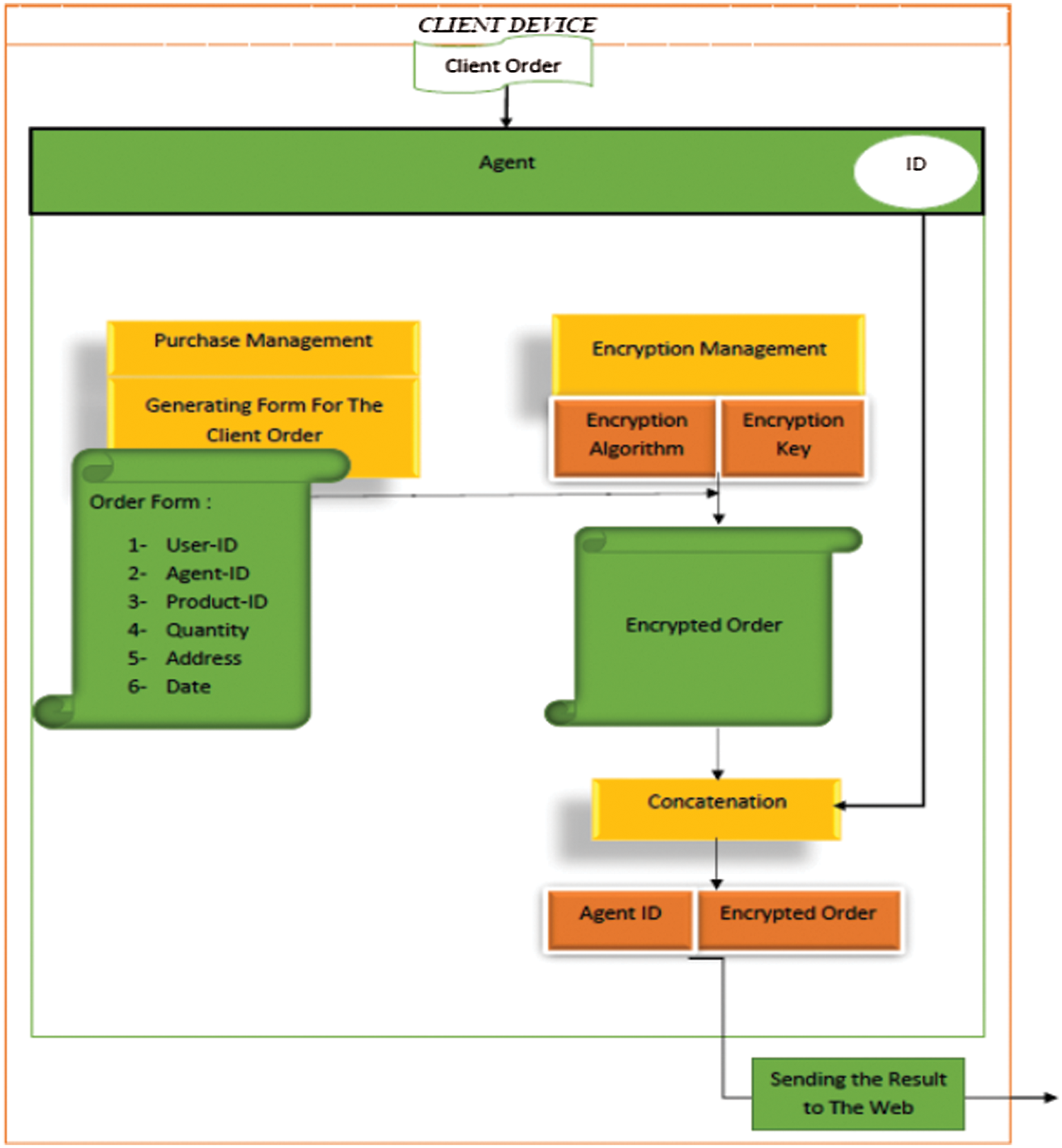
Figure 4: The proposed Agent structure and ingredients
It is better to design or implement performance measures regarding to what is actually required in the environment, rather than according to how one thinks the agent should behave. In the suggested environment the concentration is on reducing the required to provide security for each single online customer in real time to improve system performance and reducing the lost in purchase orders. The experimental results are used to prove the suggested algorithm performance. These criteria involve time consuming, number of orders per seconds and time consuming according to transaction number. The suggested algorithm were written in PHP Laravel Framework and simulated on Intel(R) Core(TM) i5-6200U CPU @ 2.30 GHz, 2.40 GHz with 8 GB RAM and 64-bit operating system, x64-based processor, Windows 10 Pro.
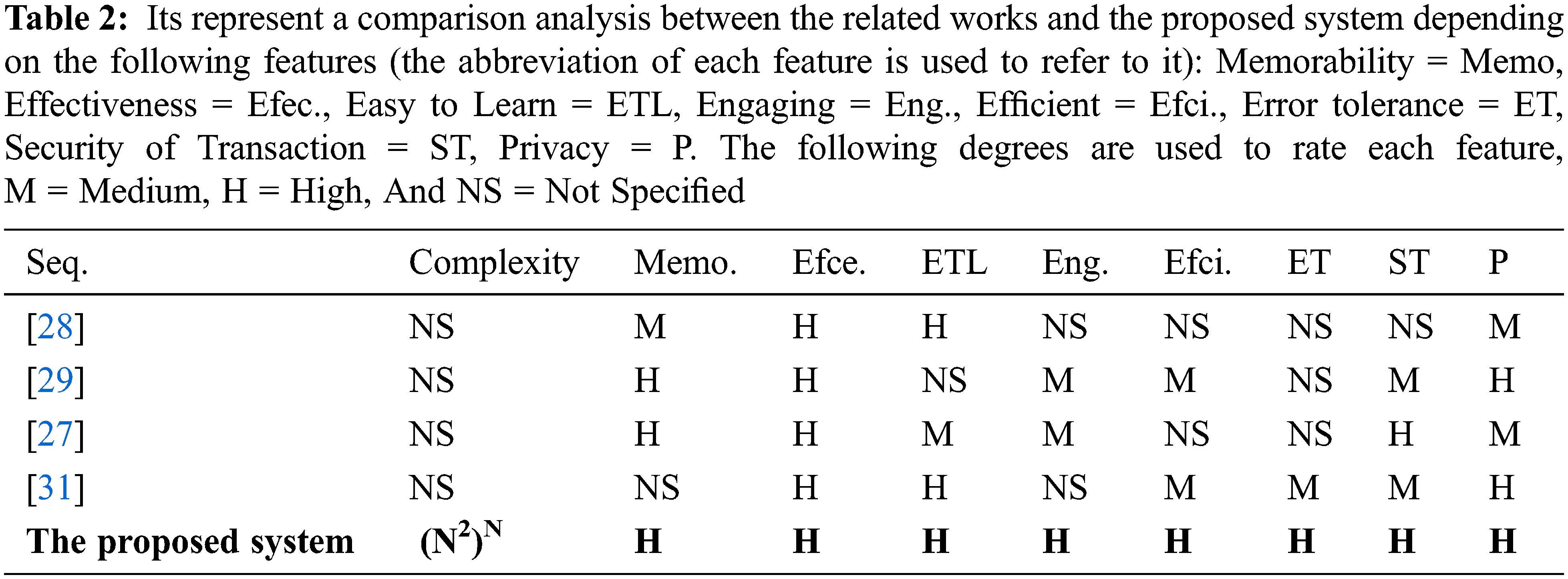
There are several features that should be considered in evaluating different models in e-commerce systems. These features are used to measure strength and weaknesses of each model. The model integrating all or most of these features can be considered as a comprehensive model that provides security and usability at the same time. These features are:
a) Memorability which means that clients can always remember to run a certain program even if it is used infrequently.
b) Effectiveness: Achieving client objectives completely and accurately.
c) Efficiency: Jobs can be completed speedily and accurately.
d) Easy to learn how come the system supports both initial trend and deeper learning.
e) Error tolerance: The ability of the system to prevent errors, and helps a client to recover from anything that occurs.
f) Engaging: To a certain degree, the user interface is interesting, satisfying and pleasing.
g) Security of transaction: keeping transaction information safe.
h) Privacy: keeping clients’ identity safe.
None of the models shown in Tab. 2 below were capable of capturing all the dimensions of usability and security together. However, the system proposed in this research captures all these two dimensions. The comparison shown in Tab. 2 indicates that the problems identified in other models have shown the benefits of the proposed system.
As mentioned previously in Section 4, the best method to evaluate the proposed system is to design performance measure of what is actually required in the environment. So according to the focuses of this study the most important measures are time consuming, system deadlock, system throughput and response time. Therefore, The major measurement of system evaluation is time, so the required time for serving clients is measured for several samples, time is changed and increased as the number of customers to be served increased, but using agent reduce the amount of growth of the required time as shown in Fig. 5. It is obviously shown that the customers serving time is increased as the number of the customers are increased, but using the agent reduces the required time for serving and thus increasing system performance. Because the saved time can be used to serve extra number of customers.
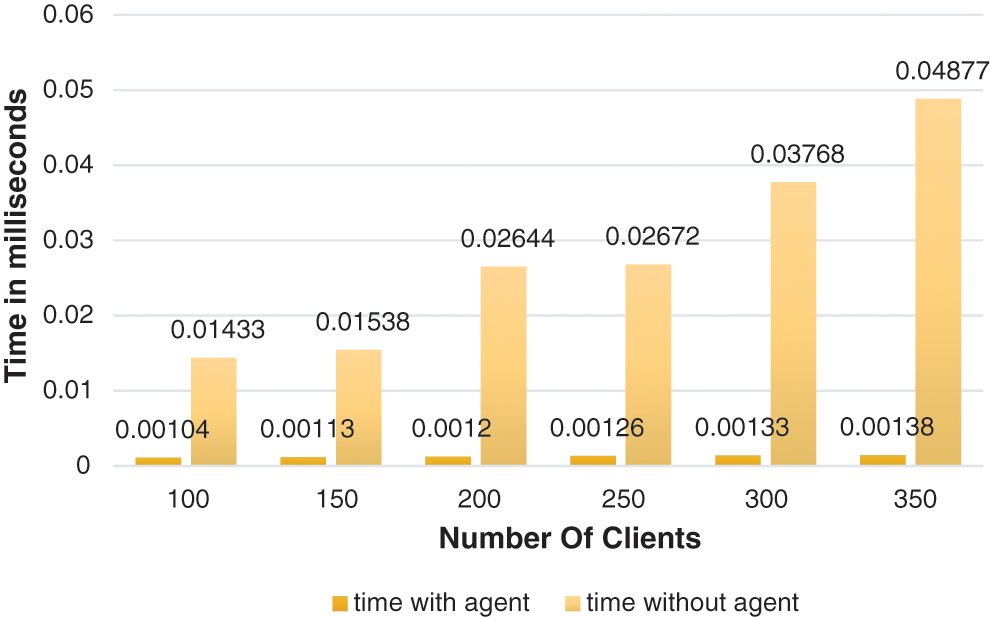
Figure 5: Time consumption for serving clients
The time consuming for serving the clients in the original system as average is reduced by 0.02717 after using the agent. The flow of the tasks should not exhaust the network in order to avoid the delay in processing the critical tasks. Using an agent to provide security for each customer reduces the time required to serve each customer (reduce response time) which in turn increases system performance and eliminates deadlock situation that may be caused due to huge number of customers that may visit the same website at the same time. Fig. 6 shows that the number of orders performed per seconds are increased when using agent more than that without using agent which leads to increase system throughput and system performance. This is the important point increase system performance insures the customers satisfaction and thus ensures the customers return back to visit and purchase from the e-commerce website.
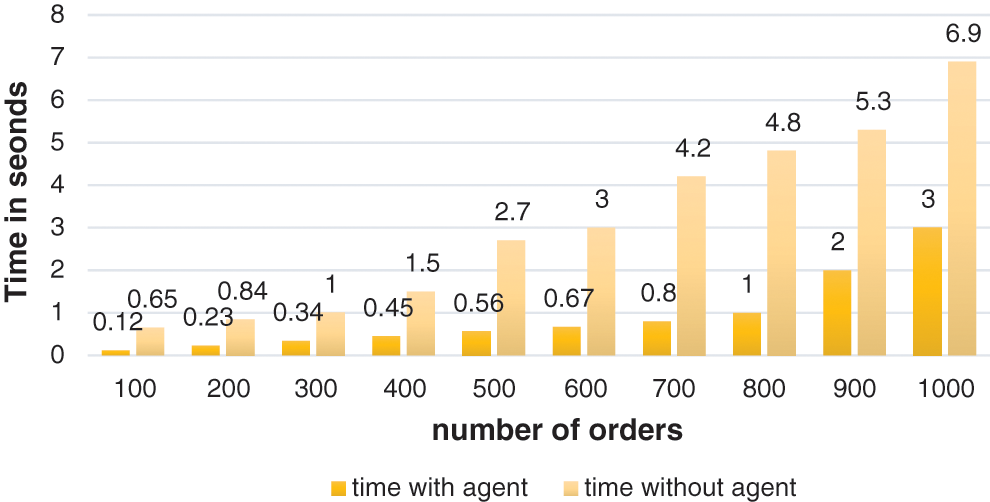
Figure 6: Number of orders per seconds
As average the required time to manage a number of orders in the proposed system is reduced by 2.241 to the same system without using the agent. The network usage describes the workload of the network. In other words, it shows the contribution of the proposed model to balancing the network load while running the critical tasks. Time consumption shown in Fig. 7 is measured by the number of transactions. It shows that the agent plays an important role in reducing network traffic, and thus achieving the optimal usage of the network to eliminate the network overload.
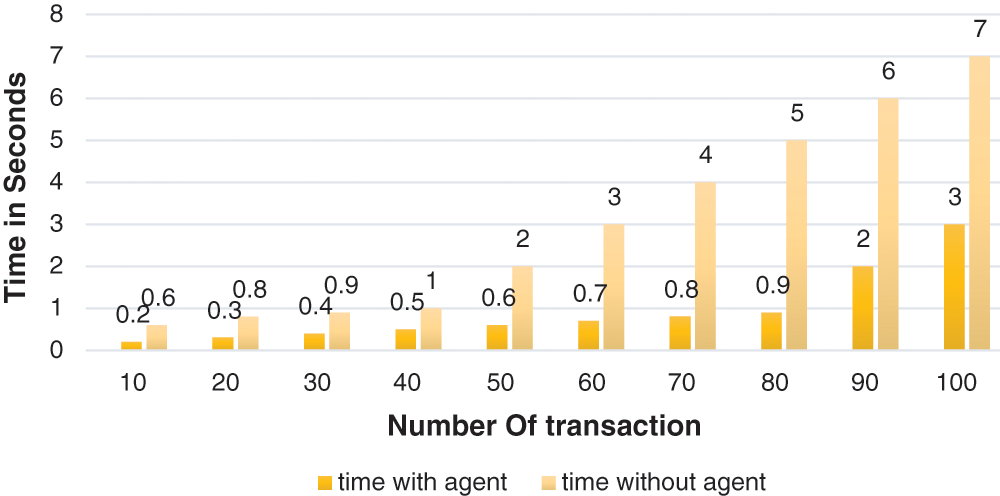
Figure 7: Time consumption according to transactions number
As shown the time required to manage transactions in the proposed system is reduced by 2.49 to as average the same system without implementing the agent.
Providing security to e-commerce systems is an essential issue. But this issue must not conflict with system performance because providing security for each online customer at the same time especially in huge network considered time consuming process that may cause system crash. The proposed agent showed that generating agent for each client to manage purchase and security task proved (by experiments) that this method is efficient to increase system security and system performance as well as solving the problem of system crash, which is the main goal achieved in this research. Also network load is increased which in turn increased the number of transactions and customers to be served. Thus achieve the optimal system performance to ensure the customers satisfactions that leads to customers return back to the same e-commerce website. Secure e-commerce multi agent system employs agents features to achieve high security, high performance and customers satisfactions. Designing the software agent to be setting inside the customer device to manage the purchase and the encryption tasks improve the system performance. This is shown obviously in the experimental results in terms of reducing time consuming for serving the customer by 0.02717, number of orders by 2.241and time for serving the transactions by 2.49 for the proposed system. As future works we are working on employing more complex encryption algorithm to provide a higher level of security. As a limitation, settling the software agent inside the customer device consider as space consuming. It is considered as a process that utilize additional CPU resources.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. A. A. Al-Karkhi, “Task recovery in self-organized multi-agent systems for distributed domains,” Ph.D. Dissertation, University of Essex, England, 2018. [Google Scholar]
2. A. A. Mayyadah, “Providing security for NFC-based payment systems using a management authentication server,” in 4th Int. Conf. on Information Management (ICIM), Oxford, UK, IEEE, pp. 184–187, 2018. [Google Scholar]
3. N. A. Mohd and Z. F. Zaba, “Review of usability and security evaluation model of E-commerce website,” Procedia Computer Science, vol. 161, no. 10, pp. 1199–1205, 2019. [Google Scholar]
4. M. A. Hussain, “A study of information security in E-commerce applications,” International Journal of Computer Engineering Science (IJCES), vol. 3, no. 3, pp. 1–9, 2013. [Google Scholar]
5. R. Canlas, “Capturing security mechanisms applied to E-commerce: An analysis of transaction security,” International Journal of Security and its Applications, vol. 15, no. 2, pp. 1–10, 2021. [Google Scholar]
6. S. Shawon, M. Rahman and R. Luckey, “E-commerce systems security for small businesses,” International Journal of Network Security & Its Applications, vol. 5, no. 2, pp. 193–210, 2013. [Google Scholar]
7. I. A. A. Abdul-Jabbar and S. M. Kadhim, “Copyright protection service for mobile images,” Engineering & Technology Journal, vol. 34, no. 4, pp. 444–450, 2016. [Google Scholar]
8. X. Hao, S. Xiao-Hong and Y. Dian, “Multi-agent system for E-commerce security transaction with block chain technology,” in IEEE Int. Symp. in Sensing and Instrumentation in IoT Era ISSI, Shanghai, China, pp. 123–134, 2018. [Google Scholar]
9. Y. Huang, J. Debnath, M. Iorga, A. Kumar and B. Xie, “CSAT: A user-interactive cyber security architecture tool based on NIST-compliance security controls for risk management,” in IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conf. (UEMCON), New York, USA, pp. 707–697, 2019. [Google Scholar]
10. M. I. ALadan, “E-commerce security challenges: A taxonomy,” Journal of Economics, Business and Management, vol. 4, no. 10, pp. 589–593, 2016. [Google Scholar]
11. P. D. Shah and R. S. Bichkar, “Secret data modification based image steganography technique using genetic algorithm having a flexible chromosome structure,” Engineering Science and Technology, An International Journal, vol. 24, no. 3, pp. 782–794, 2021. [Google Scholar]
12. S. Ehikioya and E. Guillemot, “A critical assessment of the design issues in E-commerce systems development,” Engineering Reports, vol. 2, no. 3, pp. 1–24, 2020. [Google Scholar]
13. P. Palpunavam, H. Foon, T. S. Ono and C. C. Teo, “E-commerce security and identity integrity: The future of virtual shopping,” Journal of Computational and Theoretical Nanoscience, vol. 23, no. 8, pp. 7849–7852, 2017. [Google Scholar]
14. G. Muneeswari and A. Puthussery, “Security and dual OTP system for online transaction against attacks,” in IEEE Third Int. Conf. on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, pp. 221–225, 2019. [Google Scholar]
15. M. Alenezi, A. K. Pandey, R. Verma, M. Faizan, S. Chandra et al., “Evaluating the impact of software security tactics: A design perspective,” Computers, Materials & Continua, vol. 66, no. 3, pp. 2283–2299, 2021. [Google Scholar]
16. A. D. Salman and H. B. Abdulwahab, “Proposed copyright protection systems for 3D video based key frames,” Iraqi Journal of Computers, Communications, Control and System Engineering, vol. 20, no. 3, pp. 1–15, 2021. [Google Scholar]
17. M. Mehmood, T. Javed, J. Nebhen, S. Abbas, R. Abid et al., “A hybrid approach for network intrusion detection,” CMC-Computers, Materials & Continua, vol. 70, no. 1, pp. 91–107, 2022. [Google Scholar]
18. J. Olah, N. Kitukutha, H. Haddad, M. Pakurar, D. Mate et al., “Achieving sustainable E-commerce in environmental, social and economic dimensions by taking possible trade-offs,” Sustainability, vol. 11, no. 89, pp. 1–22, 2019. [Google Scholar]
19. C. Liu, Y. Xiao, V. Javangula, Q. Hu, S. Wang et al., “A blockchain-based normalized autonomous transaction settlement system for IoT-based E-commerce,” IEEE Internet of Things Journal, vol. 6, no. 3, pp. 2327–4662, 2018. [Google Scholar]
20. J. Liu, “Efficient arbitrarily divisible e-cash applicable to secure massive transactions,” IEEE Access Journal, vol. 7, pp. 59299–59310, 2019. [Google Scholar]
21. R. D. Albu and C. E. Gordan, “Authentication and recognition, guarantor for on-line security,” in IEEE 15th Int. Conf. on Engineering of Modern Electric Systems (EMES), Oradea, Romania, pp. 9–12, 2019. [Google Scholar]
22. A. E. Ofosu, Q. A. Kester and A. A. Anyanewah, “A cryptographic algorithm based on AES cipher and nondeterministic algorithm approach for key generation,” in IEEE Int. Conf. on Computing, Computational Modelling and Applications, Cape Coast, Ghana, pp. 105–109, 2019. [Google Scholar]
23. S. J. Pon, S. S. Ramya, A. V. Christal and K. Mythili, “Secured payment gateway for authorizing e-commerce websites and transactions using machine learning algorithm,” in IEEE Int. Conf. on Computer Communication and Informatics (ICCCI), Coimbatore, India, pp. 1–5, 2020. [Google Scholar]
24. C. N. Yang, Y. C. Chen, S. Y. Chen and S. Y. Wu, “A reliable e-commerce business model using block chain based product grading system,” in IEEE 4th Int. Conf. on Big Data Analytics, Suzhou, China, pp. 341–344, 2019. [Google Scholar]
25. X. Hao, S. Xiao-Hong and Y. Dian, “Multi-agent system for E-commerce security transaction with block chain technology,” in Int. Symp. in Sensing and Instrumentation in IoT Era (ISSI), Shanghai, China, pp. 1–6, 2018. [Google Scholar]
26. R. M. Zaki, T. W. A. Khairi and A. E. Ali, “Secure data sharing based on linear congruetial method in cloud computing,” in The Proceeding Next Generation of Internet of Things, Singapore, Springer, pp. 129–140, 2021. [Google Scholar]
27. Y. Hedin and E. Moradian, “Security in multi-agent systems,” Procedia Computer Science, vol. 60, no. 4, pp. 1604–1612, 2015. [Google Scholar]
28. A. G. Briones, P. Chamoso and A. Barriuso, “Review of the main security problems with multi–agent systems used in E-commerce application,” Advances in Distributed Computing and Artificial Intelligence Journal, vol. 5, no. 3, pp. 55–61, 2016. [Google Scholar]
29. M. P. Gupta and A. Dubey, “E-commerce study of privacy, trust and security from consumer’s perspective,” International Journal of Computer Science and Mobile Computing, vol. 5, no. 6, pp. 224–232, 2016. [Google Scholar]
30. I. T. Al-Attar, “A comparative study on security features in manets routing protocols,” Iraqi Journal of Computers, Communications, Control, and System Engineering, vol. 15, no. 3, pp. 25–37, 2015. [Google Scholar]
31. N. Cooharojananone, K. Akasarakul, T. Wongkhamdi, P. Pruetthiwongwanich and K. Atcha, “The study of the local community products (otop) website characteristics toward buyer decision using eye tracking,” in IEEE 12th Int. Conf. for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, pp. 411–416, 2018. [Google Scholar]
32. H. Alshehri and F. Meziane, “The influence of advanced and secure E-commerce environments on customers behaviour: The case of saudis in the UK,” in IEEE 12th Int. Conf. for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, pp. 332–337, 2018. [Google Scholar]
33. R. Aljaljouli, J. Abawaji, M. M. Hassan and A. Alelaiwi, “Secure multi-attribute one-to-many bilateral negotiation framework for E-commerce,” IEEE Transactions on Services Computing, vol. 11, no. 2, pp. 415–429, 2018. [Google Scholar]
34. S. Tanimoto, K. Chiba, H. Sato and A. Kanai, “A study of risk assessment for sharing economy based on a user’s viewpoint,” in IEEE 8th Global Conf. on Consumer Electronics (GCCE), Osaka, Japan, pp. 240– 242, 2020. [Google Scholar]
35. K. P. Kumar and R. C. Cherukuri, “Secured electronic transactions using visual encryption: An E-commerce instance,” in IEEE Int. Conf. on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, pp. 1341–1345, 2019. [Google Scholar]
36. N. Prasad, R. Oruganti, S. Shah, Y. Pavri and P. Churi, “Improvised E-commerce transaction security using jssecure algorithm,” in IEEE Int. Conf. on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, pp. 1–7, 2018. [Google Scholar]
37. A. Kaya and Ö. Aydin, “E-commerce in turkey and sap integrated E-commerce system,” International Journal of eBusiness and eGovernment Studies, vol. 11, no. 2, pp. 207–225, 2019. [Google Scholar]
38. W. Jiang, Y. Wang, Y. Jiang, Y. Xu, J. Chon et al., “Mobil internet mobile agent system dynamic trust model for cloud computing,” Computers, Materials & Continua, vol. 62, no. 1, pp. 123–136, 2020. [Google Scholar]
39. N. Saxena, H. Shen, N. Komninos, K. K. R. Choo, N. S. Chaudhari et al., “VPSMS: A batch verification protocol for end-to-end secure sms for mobile users,” IEEE Transactions on Dependable and Secure Computing, vol. 17, no. 3, pp. 550–565, 2020. [Google Scholar]
40. Z. Wang, Y. Zhao and G. Zhong, “Public-key applications in E-commerce,” IOP Conference Series: Journal of Physics, vol. 1213, no. 4, pp. 1–7, 2019. [Google Scholar]
41. B. A. Scaria and R. K. Megalingam, “Enhanced E-commerce application security using three-factor authentication,” in IEEE Second Int. Conf. on Intelligent Computing and Control Systems (ICICCS), Madurai, India, pp. 1588–1591, 2019. [Google Scholar]
42. M. N. Abdullah, “Active directory monitoring system using optimized web database application and ajax techniques,” Engineering & Technology Journal, vol. 28, no. 18, pp. 5674–5682, 2010. [Google Scholar]
43. B. F. Abed, R. S. Al-Hamadani and S. G. Mohmmed, “Design and implementation of secured E-commerce system,” IOSR Journal of Computer Engineering (IOSR-JCE), vol. 18, no. 1, pp. 63–72, 2016. [Google Scholar]
44. A. S. AL-Karkhi and M. Fasli, “Dealing with permanent agent failure in dynamic agents organization,” in Proc. of the Int. Conf. of Agents and Artificial Intelligent (ICAART), Prague, Czech Republic, 2, pp. 715–723, 2019. [Google Scholar]
45. T. D. Stewart, T. D. Ramotsoela and G. P. Hancke, “Smartcard reader for smartphone E-commerce applications,” in IECON-44th Annual Conf. of the IEEE Industrial Electronics Society, Washington, DC, USA, pp. 5240–5245, 2018. [Google Scholar]
46. B. I.Mohideen and A. MAhendran, “Secured E-commerce transactions through chaotic map,” in 4th IEEE Int. Conf. on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, pp. 6–7, 2017. [Google Scholar]
47. J. Hu, J. Deng, N. Gao and J. Qian, “Application architecture of product information traceability based on block chain technology and a lightweight secure collaborative computing scheme,” in Int. Conf. on E-Commerce and Internet Technology (ECIT), Zhangjiajie, China, pp. 335–340, 2021. [Google Scholar]
48. W. A. Hassan, Y. H. Ali and N. J. Ibraheem, “A survey of latest techniques in medical image classification,” in Int. Conf. on Communication & Information Technology (ICICT), Basrah, Iraq, pp. 1–6, 2021. [Google Scholar]
49. R. Bhagya and R. Reeba, “Secure recommendation system for E-commerce website,” in IEEE Int. Conf. on Circuits Power and Computing Technologies (ICCPCT), Kollam, India, pp. 1–5, 2017. [Google Scholar]
50. S. Lui and J. Wang, “A security-enhanced express delivery system based on NFC,” in 13th Int. Conf. on Solid-State and Integrated Circuit Technology (ICSICT), Hangzhou, China, pp. 1–3, 2017. [Google Scholar]
51. N. Sruthi, R. Nandakumar and P. Rajkumar, “Design and characterization of height crypto core,” in Int.conf. on Signal Processing, Communication, Power and Embedded System (SCOPES), Paralakhemundi, India, pp. 205–209, 2017. [Google Scholar]
52. H. Quas, J. Tarazi and V. Akre, “Secure E-auction system using blockchain: UAE case study,” in Advances in Science and Engineering Technology Int. Conf. (ASET), Dubai, United Arab Emeritus, pp. 1–5, 2020. [Google Scholar]
53. I. M. Alattar and A. M. S. Rahma, “New block cipher algorithm using magic square of order five and galois field arithmetic with dynamic size block,” International Journal of Interactive Mobile Technologies, vol. 15, no. 16, pp. 63–78, 2021. [Google Scholar]
54. N. A. Ali, A. M. S. Rahma and S. H. Shaker, “3D polygon mesh encryption based on 3D lorenz chaotic map,” International Journal of Interactive Mobile Technologies, vol. 15, no. 15, pp. 103–114, 2021. [Google Scholar]
55. S. M. Kareem and A. M. S. Rahma, “New method for improving add round key in the advanced encryption standard algorithm,” Information Security Journal, vol. 30, no. 6, pp. 371–383, 2021. [Google Scholar]
56. F. T. A. Hussien, A. M. S. Rahma and H. B. A. Wahab, “Design and implement a new secure prototype structure of E-commerce system,” International Journal of Electrical and Computer Engineering, vol. 12, no. 1, pp. 560–571, 2022. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |