DOI:10.32604/iasc.2022.025665

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2022.025665 |  |
| Article |
Aggregated PSO for Secure Data Transmission in WSN Using Fog Server
1Department of Computer Science and Engineering, Hindusthan Institute of Technology, Coimbatore, 641032, India
2Department of Computer Science and Engineering, KPR Institute of Engineering and Technology, Coimbatore, 641048, India
*Corresponding Author: M. Manicka Raja. Email: mmanickraja21@outlook.com
Received: 01 December 2021; Accepted: 18 January 2022
Abstract: Privacy of data in Internet of Things (IoT) over fog networks is the biggest challenge in security of Wireless communication networks. In Wireless Sensor Network (WSN), current research on fog computing with IoT is gaining popularity among IoT devices over network. Moreover, the data aggregation will reduce the energy consumption in WSN. Due to the open and hostile nature of WSN, secure data aggregation is the major issue. The existing data aggregation methods in IoT and its associated approaches are lack of limited aggregation functions, heavyweight, issues related to the performance overhead. Besides, the overload on fog node will result in high latency, scalability, storage, degraded reliability and energy overhead. In order to overcome these issues, this proposed work has used two schemes for secure transmission of data over the network and reduce the energy consumption of the transmission. The secret data transferred between the IoT devices and the Fog server are transmitted through the aggregator node. If the aggregator node is placed far away from the Fog node, it may send the data to its neighbor aggregator. And it will append it with the current data and send it to the fog server through aggregator message receiving method. In addition to that, the fog server can extract the data through the fog message extractor method. In order to reduce the transmission cost and energy, Clustered Particle Swarm Optimization (CPSO) method is used to form the clusters. This proposed work can avoid the unnecessary energy consumption during the transmission and ensures secured aggregation so that the base station can know the origin of the sender and the validity of the received message. Therefore, the computation cost of the proposed work in authorization requires1MC+1H and the aggregation requires (n+2) MC+1H which is lesser than the existing methods.
Keywords: Wireless sensor network (WSN); fog; cloud; internet of things; aggregation; particle swarm optimization; energy consumption
IoT is the emerging direction of the society and economy digitization where the objects and people are connected through wireless communication networks. It is mainly composed of sensors to generate the data and server to store, process and manipulating the data for bringing out better decisions [1–3]. Within it, large volume of heterogeneous data are generated and communicated in bidirectional format. Due to its redundancy and lack of bandwidth, fog computing acts as a front-end service for the purpose of storing the distributed data generated from the IoT sensors based on the network storage and services. At the same time, it transfers it in to the cloud servers. There are various applications that are based on IoT which includes smart city [4,5], smart grid [6–8], smart healthcare [9,10], social network [11–14], smart phone [15], smart home [16], smart nation [17] and so on. It is undeniable fact that these applications have changed the human lifestyle in a smart way.
It is really a challengeable one to find an efficient data aggregation method which will satisfy the weakness of existing approaches with low communication cost, computational cost, recoverability, integrity and early filter of false injected data. To overcome all these issues, the proposed model is designed with the following contributions.
• Designs a fog assisted data aggregation method that utilizes peer to peer communication between the sensing devices and the servers. Initially, IoT sensing devices are clustered and the data from the sensing devices are aggregated by the Aggregator Node (AN) of its respective cluster.
• Aggregation node located nearer to the fog server transmits directly the encrypted data to the network server. The data from various AN that are located far away from the server are sent to its neighbor AN for transmission of data.
• Encryption and decryption are carried out using Asymmetric Paillier encryption method. AN aggregate the data with the proposed Aggregator Message Receiving Method (AMRM).
• Neighbor AN are found using the approach Clustered Particle Swarm Optimization (CPSO). This searching scheme finds AN which are nearer to the fog server as well as the source AN which will reduce the energy of the system.
• Fog server extracts the messages from AN using Fog Message Extraction Method (FMEM). This will help the model to monitor the data and save the values in local repository for a timestamp to ensure recoverability and also reduces the communication cost.
• Proposed model is evaluated with the existing schemes and provides the efficient data aggregation scheme with low computation cost, communication cost and minimum energy. Also, it ensures the functionalities such as recoverability, authorized aggregation, filter of false data rejection and data integrity.
Remaining sections of this paper are structured as follows: Section 2 discusses the related data aggregation schemes. Section 3 formulates the problem and the security model. Section 4 explains about the proposed efficient data aggregation method. Section 5 discusses the evaluation of proposed and existing data aggregation methods and Section 6 concludes with the merits of the proposed work with future directions.
This section discusses the literature related to data aggregation method in IoT enabled WSN. Data Aggregation (DA) ensures for the security of message transmission with concatenation of data and avoids recurrent transmission. However, this will affect the energy consumption of WSN [18]. DA utilizes the multi hop path for the collection of data which involves intermediate nodes for data sharing. It will reduce the resource consumption and enhances the lifetime of the network [19]. Mainly, there are two kinds of data aggregation schemes. They include; arrangement-based DA and arrangement free DA. Particularly, the arrangement-based DA has no knowledge about the next hop sensor nodes. Whereas, the arrangement free DA is categorized as tree, cluster, flat network and grid-driven methods [20]. Efficient data aggregation with grouping of clusters has obtained better communication, where more than one node is responsible for sharing the data between the peer and the distant nodes. Light weight-driven privacy preservation using data aggregation schemes are discussed in the referred articles [21–29]. The major problem is that the node selection for aggregation is the big challenge and even sometimes, there exists possibility of choosing inefficient nodes for consideration.
The proposed multidimensional secure data aggregation method involves in the discovery of neighbor key. The entire sensor nodes send the compressed data to the data aggregator. Moreover, the data is divided into two main parts using slicing mechanism and these data are exchanged in the two paths in different neighbor cluster heads until sink node has reached. With the consideration of lead and intermediate nodes, this method is also used for identifying the malicious node using locating mechanism. While sending the data, at certain point, the data is repeated and if the receiver has not received the final data, that particular node is identified as malicious node.
3 Problem Formulation and System Model
The proposed network structure is based on the cluster based aggregation method. The proposed network model of WSN is consisted of of large number of IoT sensor nodes that form a cluster and a common cluster head. Especially, each cluster communicates to the fog server through Aggregator Nodes (AN). In such case, IoT devices can transmit the data to assign AN through Peer to peer communication. Aggregator Node which is located far away from the fog server can transmit the data to the neighbor AN for the avoid of communication cost, threshold delay and sensing bottleneck which is considered to be the common issue in IoT enabled WSN. Huge number of sensing devices generates a large volume of data that leads the bottleneck. In Fig. 1 AN2 and AN3 are directly connected to the fog server. The AN1 is far away from the fog server. Then, the data transmission from AN1 to the fog server leads to the increase in the communication cost. Hence, AN1 can transmit the data to its neighbor aggregators such as AN3 or AN2 for its successful transmission. Within the cluster, all the neighbor sensing nodes of AN can encrypt the plaintext with its public key as CT = E(PK, (M||R)) to the Base station. At the same time, it is accounted as critical for the researchers in resolving these issues.
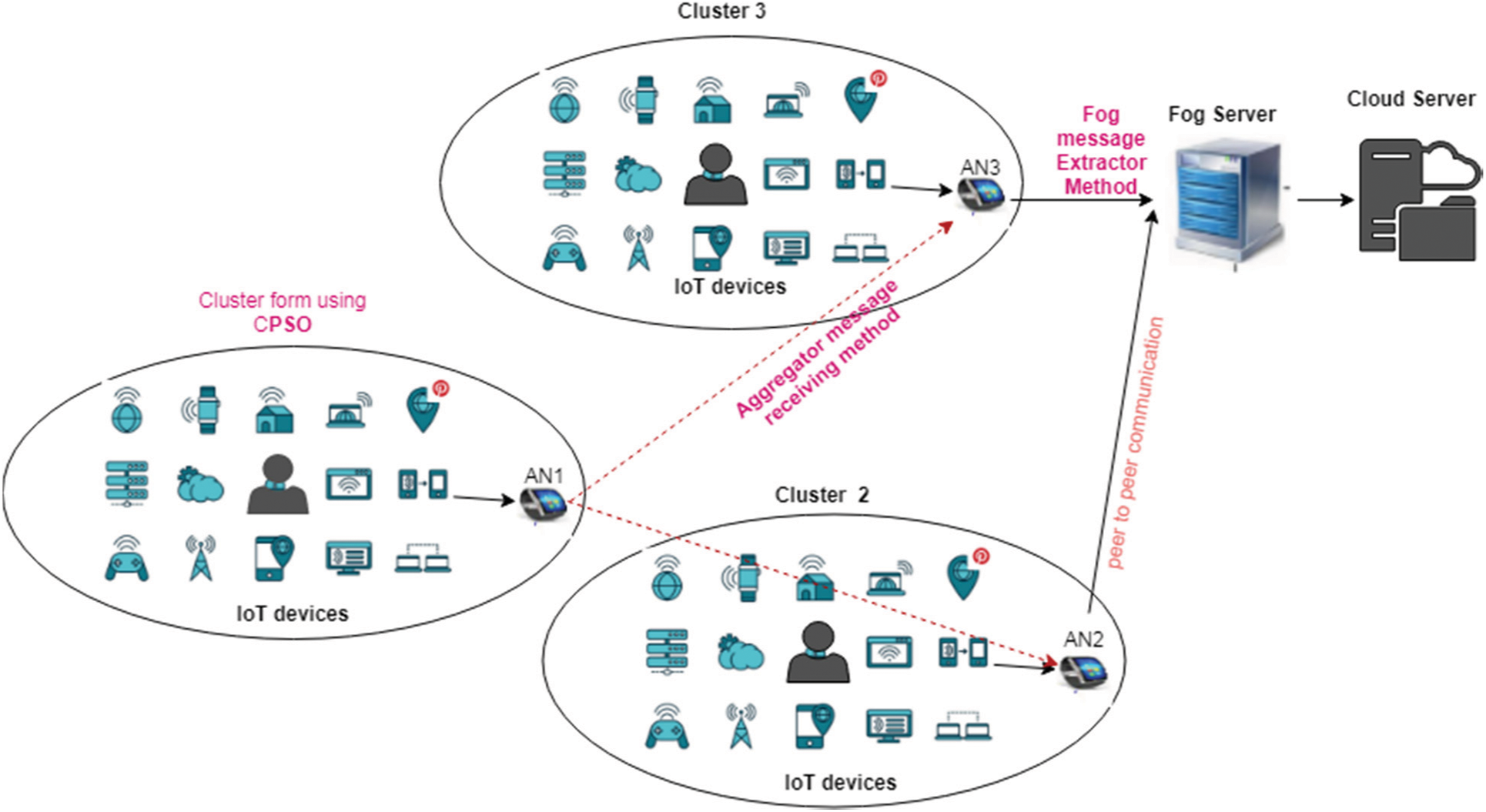
Figure 1: Overview of proposed system
Assume that the fog server is covered with m aggregators and each aggregator is composed of n IoT devices. The structure of Fig. 1 consists of three levels (level) such as Fog server (F), Cloud server (C) and Cluster which consists of IoT sensing devices and aggregator [30].
The proposed network is represented as direct acyclic graph gn = (n, l) where ‘l’ is the link between the nodes. Each node ni ∈ N with i ∈ [0, N−1] which has the characteristics such as
• Leveli in the network from 0 to level
• Capacity of CPU processing cpui in million instruction per second (MIPS)
• Capacity of memory rami in MB
• Energy consumption
Each link lp ∈ L that connects the nodes ni and nj with the following characteristics,
Adversary Model
This adversary model considered the situations that are important for the data privacy during the data aggregation in the IoT enabled fog. AN is connected to the fog server that are fully trusted. The adversary model can also consist of certain characteristics as follows.
Design Objectives: Based on this system model and security needed, the objectives of the proposed work will derive secure, flexible and efficient data aggregation scheme with CPSO. For overcoming the attacks, the proposed work ensures security in terms of AN from one cluster to the neighbor AN that is chosen based on CPSO which will reduce the energy consumption of the network system. This secured energy efficient data aggregation scheme ensures the security constraints such as Privacy preservation: one device cannot infer the other device data to avoid collusion, Authentication: AN ensures that the received device is valid, Data integrity: AN detects the malicious activity by the adversary if it modifies or forges the data, Efficiency: with the implementation of CPSO, the proposed work is energy efficient and through aggregation, computational efficiency is ensured, Flexibility: the proposed work is convenient to add new IoT devices to the application.
4 Proposed Energy Efficient Data Aggregation Method
In order to ensure the data security among the network, the proposed system develops a secure data aggregation method which will overcome all the issues discussed in Section 3. The system mainly consists of four phases which are denoted in Fig. 2. In phase I, all the sensing devices can send the data to its respective AN using Homomorphic Encryption (HE) method. The sensing devices start the data transfer by encryption of data using the key which is preloaded and transfer it to AN which can further send the data to the fog server that are directly connected to AN. In Phase II, AN can receive the encrypted data from the device through AMRM. If AN is not connected to the fog server, nearby AN can be identified through the proposed CPSO scheme that is stated in Phase III. The fog server receives the data from AN using FMEM that is stated in Phase IV.
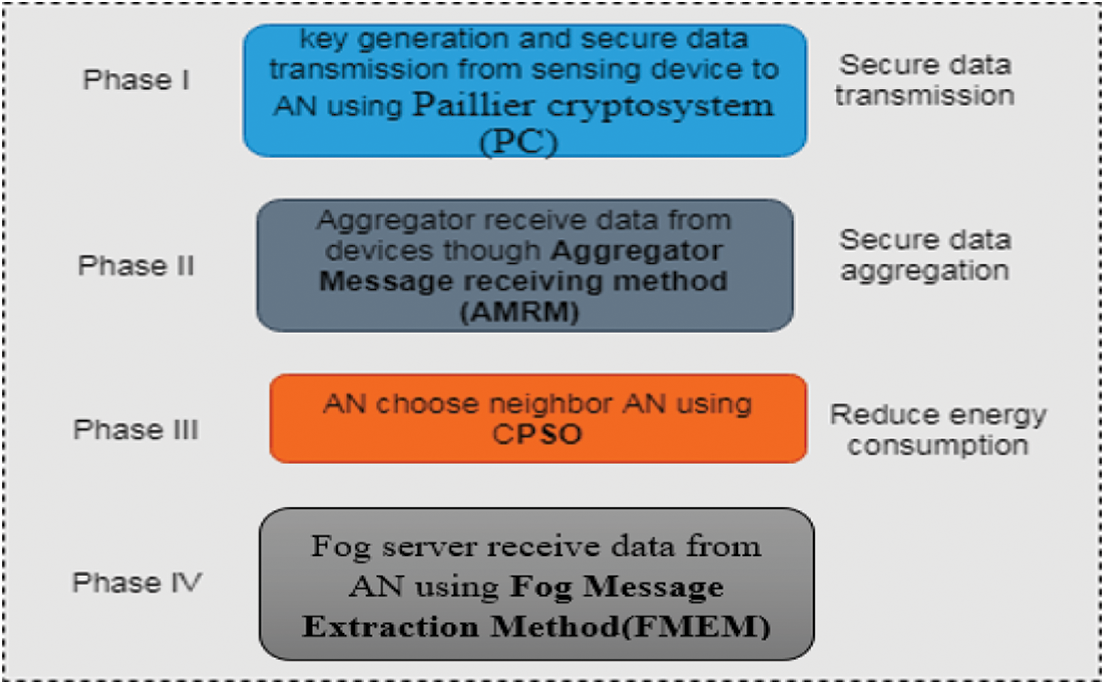
Figure 2: Proposed efficient data aggregation scheme
The sensing devices encrypt the generated data and transfer to it’s AN using Homomorphic Encryption method called Paillier Cryptosystem (PC) [31]. It is the asymmetric algorithm that provides secured and fast encryption and decryption. Based on Paillier Cryptosystem (PC), key generation, encryption and decryption are declared in algorithm 1.

The sensing device sends the message m with the concatenation of Node id (Nid), Timestamp T and encrypted data Ci with (λ, μ). In this phase, AN receives the encrypted message as cmi from devices and concatenate the messages using Aggregator Message Receiving Method (AMRC). The sensor nodes which fulfill the querying scenario can be allowed sending to AN. Notations used in this algorithm are described in Tab. 1.

AN receives the Cyphertext (CT) message (mi) called CTmi from all the sensing devices where i is the node with ID. Now AN calculates the timestamp if the condition in step 3 is true, Cmi is new or else it discards the message. In order to ensure the integrity, AN calculates the hash function of a received message and compares it with the original hash message [32]. If the condition mentioned in step 4 is true, AN aggregates all the messages received by the sensing device. Else the message is discarded. At the end, AN share the aggregated messages with the shared public key to the fog node as
Neighbor AN node finds with CPSO if there is no peer to peer communication between AN and fog server. The aim of this phase is to place the set of AN in the heterogeneous network AN = {AN0, AN1, …ANAN−1}. Minimizing the cost function f with the constraint called
where
Total energy consumption is the summation of energy of each node and communication network ET = EN + EC.
4.3.1 Initialization of Population
Initially, the Particle Swarm PS = {x0, x1,..xp−1} of size PS where xk ∈ P with Tmax iteration. These particles are distributed in the search space.
4.3.2 Particle Position and Velocity Calculation
From Fig. 3, position of k th AN is the CPSO swarm as represented in
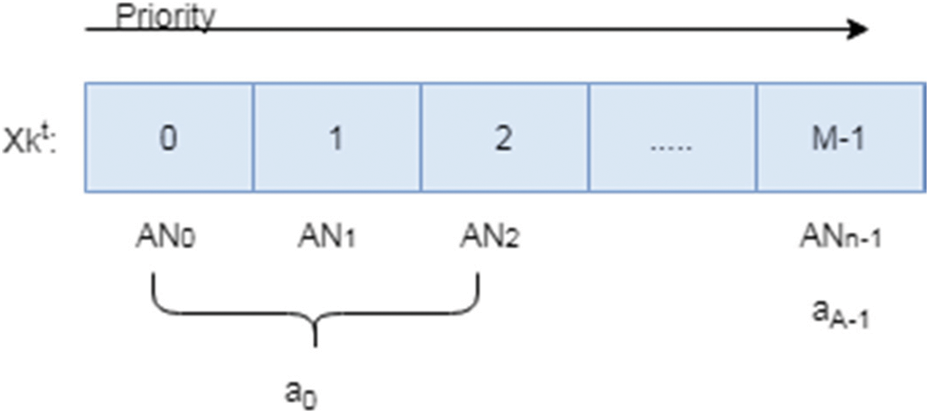
Figure 3: Position of kth AN after t iteration
The particle velocity Vk is the N × M matrix which determines the motion speed of particle Xk. Each element of vk(i, j) ∈ R defines the possibility of connecting ANi to cluster mj. And the position of the particle is updated according to the following equations.
i) New velocity matrix is computed as,
(ii) new particles position vector is updated as in Eqn
(iii) Each ANi ∈ AN has its own subset of neighbor cluster AN and this network topology will reduce the placement possibility constraints of AN. If aggregation node ANi is not connected to AN in the cluster mj∈ M
4.3.3 Neighborhood Clustered Topology
It defines the Particle Swarm communication and finding the best search space for communication. In standard PSO, to find the global best solution, all the particles are exchanged with their possible solutions which lead to local optimum. To avoid this, search space is divided into sub groups called as the clusters and the communication is allowed in between the cluster aggregation nodes. This will deliver the best possible result when compared to the standard approach [34–36]. This neighbor network structure is represented in Fig. 4.

Figure 4: AN neighborhood network structure
In this network, AN from different clusters are communicated through AN to fog server. Aggregation node which is nearer to the fog server are selected from this network. AN, which is far away from the fog server will send its encrypted message. The messages are generated by the device to the fog server through neighbor AN that is found using this CPSO approach. Assume that AN0 and AN1 are far away from the fog server, the messages from cluster 1 is aggregated by AN0 and send through either AN1 or AN3 selected using CPSO approach as stated in algorithm 3.

Fog server receives the aggregated messages from all AN using FMEM. Then, the fog server is responsible for the decryption of the messages individually. Fog server then divides the aggregated data based on time stamp and extracts each AN data. FS extracts the aggregated message
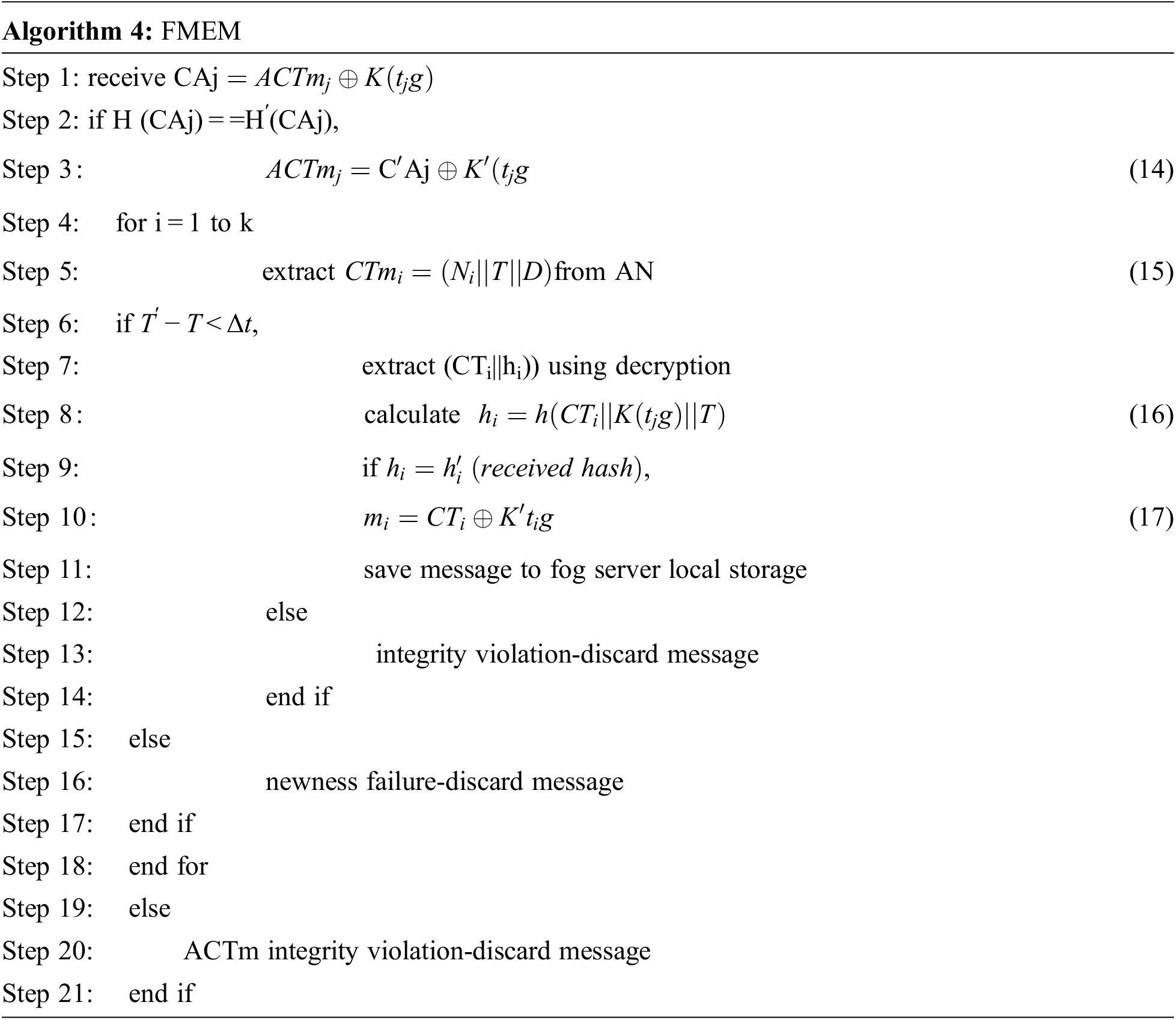
Fog server receives the aggregated cipher text of all the AN and considers XOR operation in step 3 with the key from algorithm 1. Until k which is the number of sensor nodes transmitting the data, it extracts the message in step 5 and checks the timestamp in step 6. If it is true, the hash value is calculated as in step 8. If the calculated hash and received hash value are equal, the original image is extracted using XOR operation as stated in step 10. Or else, the message is discarded due to integrity violation and newness failure. At the end of the execution of this algorithm, the fog node extracts the message sent by the AN and stores it in its local storage [37,38].
5 Performance Analysis and Discussions
This section discusses the evaluation performance of the proposed energy efficient data aggregation scheme called AMRM-CPSO-FMEM. The proposed scheme is evaluated in terms of functionality and cost which includes communication cost, computational cost and energy cost. Further, the method is implemented in iFogSim [39], fog simulator with the CloudSim tool [40]. The proposed work is compared to the existing approaches such as Secure Privacy Preserving Data Aggregation (SPPDA), Concealed Aggregation Scheme for Multiple Application (CDAMA), Recoverable Concealed Aggregation (CDA) with homogeneous WSN (RCDA-HOMO) and Efficient Health Data Aggregation (EHDA) [41–43].
5.1 Evaluation of Functionality
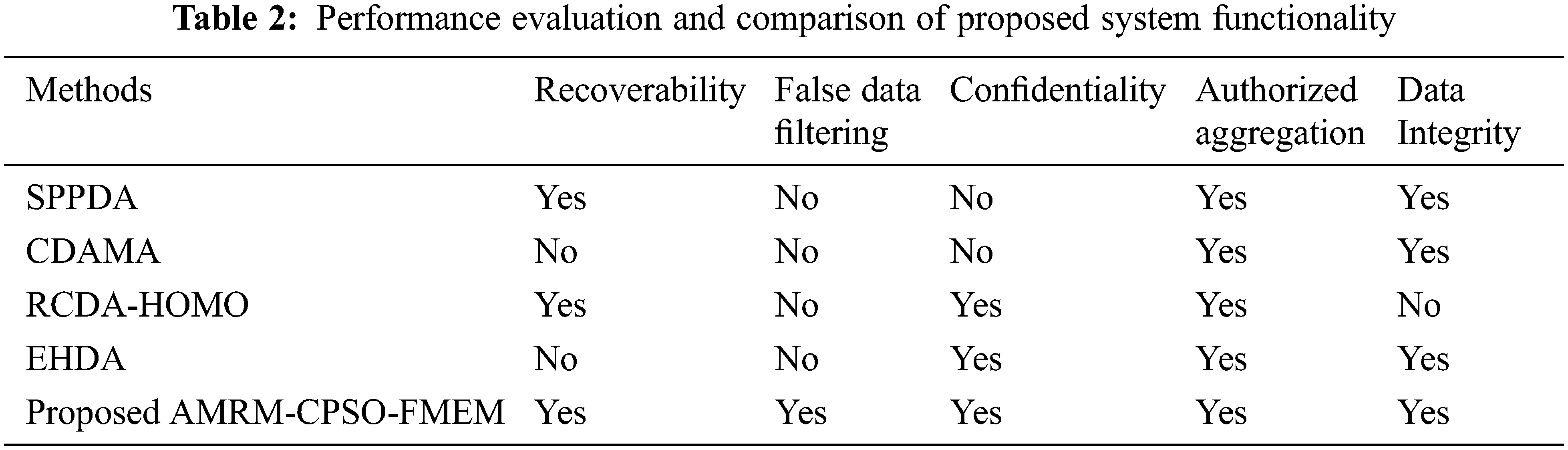
Various data aggregation schemes functionality are evaluated such as recoverability, network false data filtering, peer to peer confidentiality, authorized aggregation and data integrity. Tab. 2 shows the evaluated results. Compared to the other existing approaches, the proposed scheme satisfies the extended functionalities.
5.2 Evaluation of Computational Cost (CC)
Computational cost is calculated based on the notations such as MC (Multiplication Cost), AC (one hop Addition Cost), E (cost of one modular Exponential) and H (cost of one Hash function). The comparison of existing and the proposed aggregation schemes CC are provided in Tab. 3.
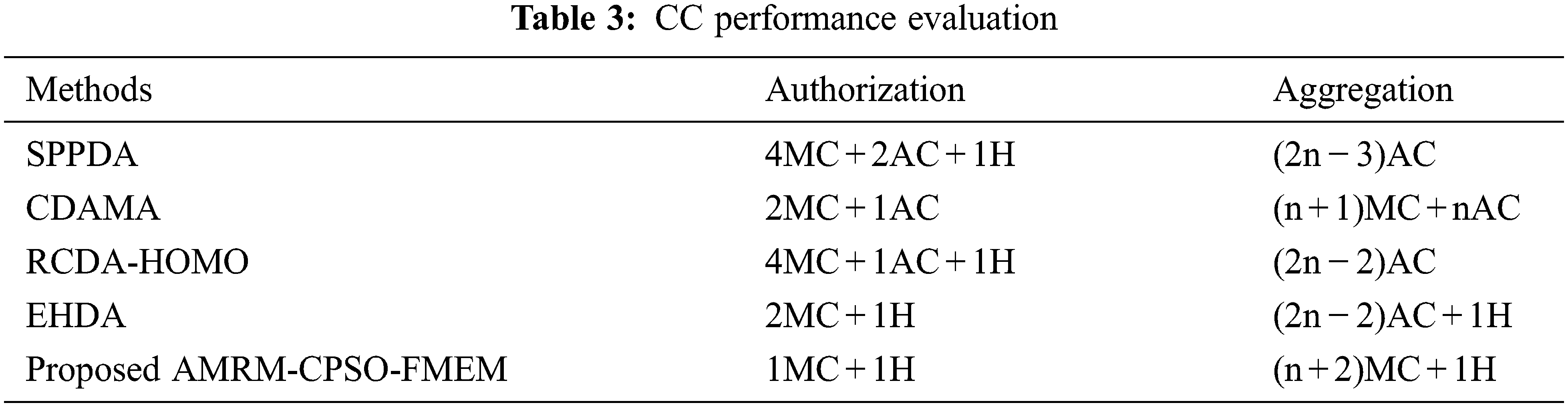
From this evaluation, SPPDA requires 4MC+2AC+1H operations for its authorization phase in order to encrypt the data. For aggregation, the cluster head of each cluster requires (2n − 3) AC operations. For CDAMA, the authorization requires 2MC+1AC operations and the cluster head for aggregation requires (n + 1) MC+nAC operations. For RCDA-HOMO, each member node performs the authorization and requires 4MC+1AC+1H operations and (2n − 2) AC operations are required for the aggregation by the cluster head. For EHDA, each IoT device node performs the authorization which requires 2MC+1H operations and the aggregation by the needs of each cluster head (2n − 2) AC+1H operations. For the proposed scheme, each device node in the cluster needs 1MC+1H operations for encryption and for sending signature and AN in each cluster requires (n + 2) MC+1H operations. While comparing the results, the proposed scheme needs less computational overhead for the data aggregation compared to the other existing approaches. The computational cost operations execution time called time cost is stated in Fig. 5. The computational cost of one IoT device is 0.00023 ms. For N number of IoT devices, time cost is n*(0.00023)ms.

Figure 5: Total computational cost comparison of all IoT devices
In comparison to various aggregation schemes, the proposed data aggregation method requires less time for executing the computational operations for different number of IoT devices. To the maximum of 1000 IoT devices, the time cost of the proposed method is 0.23 ms. The total cost time of the compared approaches such as SPPDA, CDAMA, RCDA-HOMO, EHDA are 0.92, 0.98, 0.8, 0.52 ms respectively. Hence, the proposed efficient data aggregation scheme AMRM-CPSO-FMEM has obtained less cost for the execution of computational operations.
5.3 Evaluation of Communication Cost
In terms of exchange, the aggregated messages between the AN over the wireless network and the communication cost are calculated in terms of message exchange in bytes as shown in Fig. 6. In IoT enabled wireless network, the small message size requires the minimum communication cost. While sending the aggregated messages between the network, the proposed approach consumes its communication cost as 4000 bytes of data for transmitting 20000 bytes of data. Various existing approaches such as SPPDA, CDAMA, RCDA-HOMO, and EHDA are exchanged 5000, 5500, 6500 and 6000 bytes respectively. Comparatively, the proposed algorithm exchanges the data with low communication cost of 4000 bytes.

Figure 6: Comparison of communication cost in terms of bytes
5.4 Evaluation in Terms of Energy Consumption
Total energy consumption of various data aggregation schemes are calculated as in Eq. (16). The evaluated results are shown in Fig. 7.
where,

Figure 7: Comparison of energy consumption
Es-Energy of sending single message, Er-Energy of receiving single message, N-total number of messages, M-total number of messages received, D-number of dropped packet
While sending the maximum of 95 packets in the transmission, the proposed method consumes 15.261μ Joules of energy. The other existing approaches such as SPPDA, CDAMA, RCDA-HOMO, and EHDA consume 21.378 μ Joules, 20.029 μ Joules, 18.028 μ Joules and 17.209 μ Joules respectively. Some of the messages are dropped while sending the messages from AN to the server that is out of the communication range. AN can send the messages directly to the fog server or through neighbor AN using CPSO. This proposed approach consumes less energy due to the use of CPSO method. That is efficiently finding the next neighbor where the packet needs to forward in case of away fog server. At the same time, the searching time is also reduced due to the implementation of CPSO which will further reduce the energy of extra searching devices. This algorithm also finds AN that is nearer to the fog server and efficiently send the messages which will reduce the packet loss.
Energy consumption in terms of number of nodes in one cluster is evaluated as shown in Fig. 8. For the maximum of 100 nodes per cluster, the proposed scheme consumes 4.244 μ Joules. Various other existing approaches such as SPPDA, CDAMA, RCDA-HOMO, and EHDA consume 9.02 μ Joules, 8.387 μ Joules, 7.22 μ Joules and 6.028 μ Joules accordingly. Hence, in terms of all the evaluation processes, the proposed data aggregation approach is confidential, efficient and effective to deliver the message from IoT devices to Fog and Central cloud in secured manner.
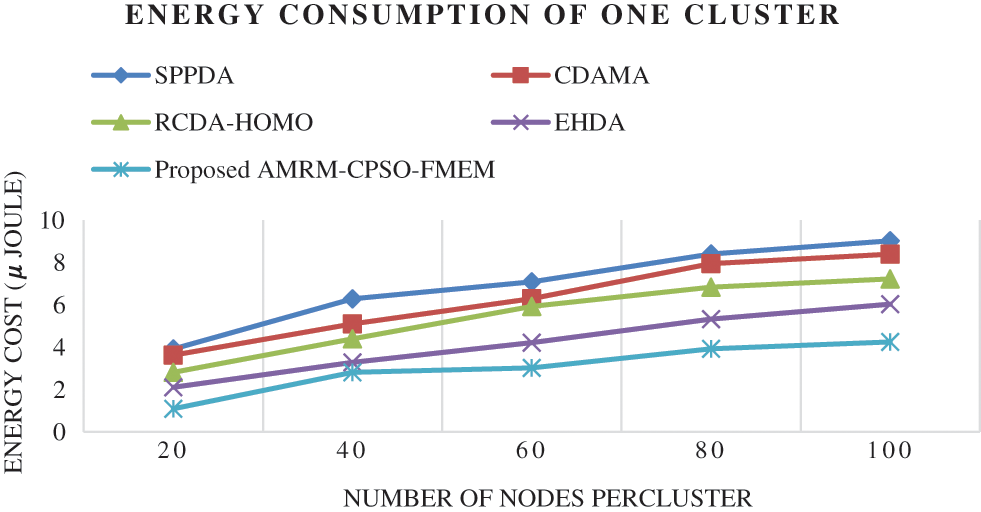
Figure 8: Energy cost of one cluster
In this paper, efficient and effective data aggregation scheme based on asymmetric Paillier Cryptosystem based encryption and decryption between the IoT devices data to aggregator is proposed. In order to ensure the efficiency of the data aggregation, the proposed method incorporates two methods between AN and fog server such as message received by aggregator from IoT device and message extracted by fog server from AN. In addition to that, this proposed scheme ensures the functionalities such as confidentiality, integrity, authorized aggregation and energy saving. The major features of the proposed work are (i) IoT devices are formed as cluster and for each cluster one aggregator node is created which will aggregate the data generated by the corresponding device node through AMRM. (ii) AN far away from the fog server is communicated to the neighbor AN using CPSO searching scheme which will reduce the time and energy cost and also ensures the confidentiality. (iii) Fog server can extract the encrypted data and decrypt the cipher text with the key and extract the messages using FMEM. With different kinds of evaluations, the proposed scheme is the best in terms of communication cost, computational overhead in terms of time and cost, functionality and energy consumption. In future, the proposed scheme is implemented with different region mobility of IoT sensing devices enabled fog.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. C. Cecchinel, M. Jimenez, S. Mosser and M. Riveill, “An architecture to support the collection of big data in the internet of things,” in Proc. 2014 IEEE World Congress on Services, IEEE, Anchorage, AK, USA, pp. 442–449, 2014. [Google Scholar]
2. M. Abu Elkheir, M. Hayajneh and N. Ali, “Data management for the internet of things: Design primitives and solution,” Sensors, vol. 13, no. 11, pp. 15582–15612, 2013. [Google Scholar]
3. C. Perera, R. Ranjan, L. Wang, S. U. Khan and A. Y. Zomaya, “Big data privacy in the internet of things era,” IT Professional, vol. 17, no. 3, pp. 32–39, 2015. [Google Scholar]
4. C. Hu, X. Cheng, J. Yu, Z. Tian, W. Lv. et al., “Achieving privacy preservation and billing via delayed information release,” IEEE/ACM Transactions on Networking, vol. 29, no. 3, pp. 1376–1390, 2019. [Google Scholar]
5. A. Alkhamisi, M. S. H. Nazmudeen and S. M. Buhari, “A Cross-layer framework for sensor data aggregation for iot applications in smart cities,” in Proc. IEEE Int. Smart Cities Conf. (ISC2), pp. 1–6, Trento, Italy, 2016. [Google Scholar]
6. A. Alrawais, A. Alhothaily, C. Hu and X. Cheng, “Fog computing for the internet of things: Security and privacy issues,” IEEE Internet Computing, vol. 21, no. 2, pp. 34–42, 2017. [Google Scholar]
7. Z. Cai and X. Zheng, “A private and efficient mechanism for data uploading in smart cyber-physical systems,” IEEE Transactions on Network Science and Engineering, vol. 7, no. 2, pp. 766–775, 2018. [Google Scholar]
8. H. Chunqiang, L. Hang, M. Liran, Y. Huo, A. Alrawais et al., “A secure and scalable data communication scheme in smart grids,” Wireless Communications and Mobile Computing, vol. 2018, pp. 1–17, no. 17, 2018. [Google Scholar]
9. C. Hu, H. Li, Y. Huo, T. Xiang and X. Liao, “Secure and efficient data communication protocol for wireless body area networks,” IEEE Transactions on Multi-Scale Computing Systems, vol. 2, no. 2, pp. 94–107, 2016. [Google Scholar]
10. T. K. Dasaklis, F. Casino and C. Patsakis, “Blockchain meets smart health: Towards next generation healthcare services,” in Proc. 2018 9th Int. Conf. on Information, Intelligence, Systems and Applications (IISA), Zakynthos, Greece, pp. 1–8, 2018. [Google Scholar]
11. C. Hu, R. Li, W. Li, J. Yu, Z. Tian et al., “Efficient privacy-preserving schemes for dot-product computation in mobile computing,” in Proc. 1st ACM Workshop on Privacy-Aware Mobile Computing, ACM, Paderborn, Germany, pp. 51–59, July 2016. [Google Scholar]
12. Z. Cai, Z. He, X. Guan and Y. Li, “Collective data-sanitization for preventing sensitive information inference attacks in social networks,” IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 4, pp. 577–590, 2018. [Google Scholar]
13. Z. He, Z. Cai and J. Yu, “Latent-data privacy preserving with customized data utility for social network data,” IEEE Transactions on Vehicular Technology, vol. 67, no. 1, pp. 665–673, 2018. [Google Scholar]
14. L. Huang, X. Fan, Y. Huo, C. Hu, Y. Tian et al., “A novel cooperative jamming scheme for wireless social networks without known csi,” IEEE Access, vol. 5, pp. 26476–26486, 2017. [Google Scholar]
15. S. Egelman, A. P. Felt and D. Wagner, “Choice architecture and smartphone privacy: There’s a price for that,” E-Economics of Information Security and Privacy, pp. 211–236, 2013. [Google Scholar]
16. T. Song, R. Li, B. Mei, J. Yu, X. Xing et al., “A privacy preserving communication protocol for IOT applications in smart homes,” IEEE Internet of Things Journal, vol. 4, no. 6, pp. 1844–1852, 2017. [Google Scholar]
17. S. L. Hoe, “Defining a smart nation: The case of Singapore,” Journal of Information, Communication and Ethics in Society, vol. 14, no. 4, pp. 323–333, 2016. [Google Scholar]
18. Y. Huo, Y. Tian, L. Ma, X. Cheng and T. Jing, “Jamming strategies for physical layer security,” IEEE Wireless Communications, vol. 25, no. 1, pp. 148–153, 2018. [Google Scholar]
19. X. Zheng, Z. Cai and Y. Li, “Data linkage in smart iot systems: A consideration from privacy perspective,” IEEE Communications Magazine, vol. 10, no. 2, pp. 12–20, 2018. [Google Scholar]
20. C. Hu, W. Li, X. Cheng, J. Yu, S. Wang et al., “A secure and verifiable access control scheme for big data storage in clouds,” IEEE Transactions on Big Data, vol. 4, no. 3, pp. 341–355, 2018. [Google Scholar]
21. L. Chen, R. Lu, Z. Cao, K. Alharbi and X. Lin, “Muda: Multifunctional data aggregation in privacy-preserving smart grid communications,” Peer-to-Peer Networking and Applications, vol. 8, no. 5, pp. 777–792, 2015. [Google Scholar]
22. C. Li, R. Lu, H. Li, L. Chen and J. Chen, “PDA: A privacy-preserving dual-functional aggregation scheme for smart grid communications,” Security and Communication Networks, vol. 8, no. 15, pp. 2494–2506, 2015. [Google Scholar]
23. H. Bao and R. Lu, “A lightweight data aggregation scheme achieving privacy preservation and data integrity with differential privacy and fault tolerance,” Peer-to-Peer Networking and Applications, vol. 10, no. 1, pp. 106–121, 2017. [Google Scholar]
24. R. Lu, K. Heung, A. H. Lashkari and A. A. Ghorbani, “A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT,” IEEE Access, vol. 5, pp. 3302–3312, 2017. [Google Scholar]
25. P. D. Patel, B. Pranav and V. Ravindra, “Data aggregation in wireless sensor network,” International Journal of Management, IT and Engineering, vol. 2, no. 7, pp. 457–472, 2012. [Google Scholar]
26. C. Zhang, C. Li and J. Zhang, “A secure privacy-preserving data aggregation model in wearable wireless sensor networks,” Journal of Electrical and Computer Engineering, vol. 61, pp. 1–9, 2015. [Google Scholar]
27. W. He, X. Liu, H. Nguyen, K. Nahrstedt and T. Abdelzaher, “Pda: Privacy-preserving data aggregation in wireless sensor networks,” in Proc. of the INFOCOM 2007 26th IEEE Int. Conf. on Computer Communications, Anchorage, AK, USA, pp. 2045–2053, 2007. [Google Scholar]
28. Y. H. Lin, S. Y. Chang and H. M. Sun, “Concealed data aggregation scheme for multiple applications in wireless sensor networks,” IEEE Transactions on Knowledge and Data Engineering, vol. 25, no. 7, pp. 1471–1483, 2013. [Google Scholar]
29. K. A. Shim and C. M. Park, “A secure data aggregation scheme based on appropriate cryptographic primitives in heterogeneous wireless sensor networks,” IEEE Transactions on Parallel and Distributed Systems, vol. 26, no. 8, pp. 2128–2139, 2015. [Google Scholar]
30. Y. Huo, C. Hu, X. Qi and T. Jing, “LoDPD: A location difference-based proximity detection protocol for fog computing,” IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1117–1124, 2017. [Google Scholar]
31. C. Hu, N. Zhang, H. Li, X. Cheng and X. Liao, “Body area network security: A fuzzy attribute-based signcryption scheme,” IEEE Journal on Selected Areas in Communications, vol. 31, no. 9, pp. 37–46, 2013. [Google Scholar]
32. Y. Huo, W. Dong, J. Qian and T. Jing, “Coalition game-based secure and effective clustering communication in vehicular cyber-physical system (vcps),” Sensors, vol. 17, no. 3, pp. 475, 2017. [Google Scholar]
33. Y. Lu, Z. Zhao, B. Zhang, L. Ma, Y. Huo et al., “A Context-aware budget-constrained targeted advertising system for vehicular networks,” IEEE Access, vol. 6, pp. 8704–8713, 2018. [Google Scholar]
34. C. Hu, Y. Huo, L. Ma, H. Liu, S. Deng et al., “An attribute-based secure and scalable scheme for data communications in smart grids,” in Wireless Algorithms, Systems, and Applications (WASA), pp. 469–482, Berlin, Germany: Springer, 2017. [Google Scholar]
35. H. Bao and R. Lu, “Comment on privacy-enhanced data aggregation scheme against internal attackers in smart grid,” IEEE Transactions on Industrial Informatics, vol. 12, no. 1, pp. 2–5, 2016. [Google Scholar]
36. N. Saputro and K. Akkaya, “Performance evaluation of smart grid data aggregation via homomorphic encryption,” in Proc. of the Wireless Communications and Networking Conf. (WCNC), IEEE, Paris, France, pp. 2945–2950, 2012. [Google Scholar]
37. S. Maheswaran, P. G. Kuppusamy, S. M. Ramesh, T. V. P. Sundararajan and P. Yupapin, “Refractive index sensor using dual core photonic crystal fiber–glucose detection applications,” Results Phys, vol. 11, pp. 577–578, 2018. [Google Scholar]
38. S. Maheswaran, B. K. Paul, M. A. Khalek, S. Chakma, K. Ahmed, and M. M. Rajan, “Design of tellurite glass based quasi photonic crystal fiber with high nonlinearity,” Optik, vol. 181, pp. 185–190, 2019. [Google Scholar]
39. Z. Erkin, J. R. Troncoso-Pastoriza, R. L. Lagendijk and F. PerezGonzalez, “Privacy-preserving data aggregation in smart metering systems: An overview,” IEEE Signal Processing Magazine, vol. 30, no. 2, pp. 75–86, 2013. [Google Scholar]
40. R. Lu, “Privacy-enhancing aggregation techniques for smart grid communications,” Wireless Networks, 2016. [Google Scholar]
41. R. Lu, X. Liang, X. Li, X. Lin and X. Shen, “EPPA: An efficient and privacy-preserving aggregation scheme for secure smart grid communications,” IEEE Transactions on Parallel and Distributed Systems, vol. 23, no. 9, pp. 1621–1631, 2012. [Google Scholar]
42. E. Shi, T. H. Chan, E. G. Rieffel, R. Chow and D. Song, “Privacy preserving aggregation of time-series data,” in Proc. of the Network and Distributed System Security Symposium, (NDSS), San Diego, California, USA, 2011. [Google Scholar]
43. K. Alharbi and X. Lin, “LPDA: A lightweight privacy-preserving data aggregation scheme for smart grid,” in Proc. Int. Conf. on Wireless Communications and Signal Processing, WCSP, Huangshan, China, pp. 1–6, 2012. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |