DOI:10.32604/iasc.2023.026289

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2023.026289 |  |
| Article |
Automated Irrigation System Using Improved Fuzzy Neural Network in Wireless Sensor Networks
1Department of Computer Science and Engineering, Sona College of Technology, Salem 636005, Tamilnadu, India
2Department of Computer Science and Engineering, Adhiyamaan College of Engineering, Hosur 635109, Tamilnadu, India
*Corresponding Author: V. Vivekanandhan. Email: acevivek76771@gmail.com
Received: 21 December 2021; Accepted: 19 February 2022
Abstract: Irrigation plays a significant role in various agricultural cropping methods deployed in semiarid and arid regions where valuable water applications and managing are considered crucial concerns. Multiple factors such as weather, soil, water, and crop data need to be considered for irrigation maintenance in an efficient besides uniform manner from multifaceted and different information-based systems. A Multi-Agent System (MAS) has been proposed recently based on diverse agent subsystems with definite objectives for attaining global MAS objective and is deployed on Cloud Computing paradigm capable of gathering information from Wireless Sensor Networks (WSNs) positioned in rice, cotton, cassava crops for knowledge discovery and decision making. The radial basis function network has been used for irrigation prediction. However, in recent work, the security of data has not focused on where intruder involvement might corrupt the data at the time of data transferring to the cloud, which would affect the accuracy of decision making. To handle the above mentioned issues, an efficient method for irrigation prediction is used in this work. The factors considered for decision making are soil moisture, temperature, plant height, root depth. The above-mentioned data will be gathered from the sensors that are attached to the crop field. Sensed data will be forwarded to the local server, where data encryption will be performed using Adaptive Elliptic Curve Cryptography (AECC). After the encryption process, the data will be forwarded to the cloud. Then the data stored in the cloud will be decrypted key before being given to the decision-making module. Finally, the uniform distribution-based fuzzy neural network is formulated based on the received data information in the decision-making module. The final decision regarding the level of water required for crop fields would be taken. Based on this outcome, the water volve opening duration and the level of fertilizers required will be considered. Experimental results demonstrate the effectiveness of the proposed model for the United States Geological Survey (USGS) database in terms of precision, accuracy, recall, and packet delivery ratio.
Keywords: Irrigation; multi-agent system; precision irrigation; accuracy; elliptic curve cryptography; encryption; wireless sensor networks; fertilizers
Agriculture plays a key role in human civilization progress and a strategic role in the nation’s economic growth process. Irrigation is a challenging approach in dry and scarce rainfall areas. A crucial aspect in ensuring the worthy profits and high-quality food production to feed the rising world population, and through irrigation population can stabilize i.e., increase food production besides boosts livestock breeding development, processing, and other economy branches. And irrigated land in entire world food production will rise in coming days. But irrigation systems do not often give the expected results because much of the water evaporates rather than feeding plants without revealing leaks besides other losses. Thus, it is necessary and obligatory to use new technologies to achieve a lot of benefits [1–3].
Irrigation management helps determine water levels for the budding crop for attaining definite management purposes and is considered a multifaceted decision-making method. The existing conditions will be informed when the farmer is remote from the agricultural land [4]. The major precision irrigation objectives are increasing water efficiency and crop productivity through technology like wireless sensor networks, mobile devices, remote sensing, real-time control, information systems, etc., [5]. Among those technologies, Wireless Sensors Network (WSN) has been used in many fields like monitoring climate and soil nutrient data for crops health prediction and agricultural products quality. In recent work, a multi-agent system (MAS) has been utilized for automatic gathering and information management from rice, cotton, and cassava crops to implement an accurate irrigation system. A novel MAS has been proposed very recently based on diverse agent subsystems with definite purposes for attaining global MAS objective.
This MAS has been deployed on the Cloud Computing paradigm, which can gather data from wireless sensor networks (WSNs) found in rice, cotton, cassava crops for knowledge discovery besides decision making. However, in this security of data that has been sensed has not focused where at the time of data transferring to cloud for decision, intruder involvement might corrupt the data, affecting the accuracy of decision making [6]. A radial basis function type of neural network is formulated to predict hourly soil moisture content (MC) requirement and required soil evapotranspiration using Blaney–Criddle method [7]. In this work, a fuzzy logic-based weather-dependent irrigation control mechanism is also proposed. The aggregated real-time agriculture data is input to the radial basis function type neural network model (Mohapatra et al., 2019). The predicted soil Multi Computer (MC) data is input into the Decision Support System (DSS) model for suitable Short Message Service (SMS) notification generation for the farmer’s handset. However, the method has an issue with packet delivery ratio and accuracy.
To hanlde the issue mentioned above, an efficient method for irrigation prediction is proposed in this work. In the proposed work, the factors considered for decision making are soil moisture, temperature, plant height, root depth. The data mentioned above will be gathered from the sensors that are attached to the crop field. Data that are gathered from the crop field will be immediately transferred to the cloud for future use. To avoid the intruder, sensor data will be forwarded to the local server first, where data encryption, where data encryption will be performed [8,9]. In this work, Adaptive Elliptic curve cryptography-based encryption is conducted to encrypt the sensed data. After the encryption process [10], the encrypted data will be forwarded to the cloud. And then, the data decryption is done, and the output is forwarded to the decision-making module. In the decision-making module, a uniform distribution-based uniform distribution-based fuzzy neural network will be applied for the final decision regarding irrigation prediction for crop fields. Based on this outcome, the water volve opening duration and the level of fertilizers required will be considered.
In this research work, Section I analyses the significance of irrigation prediction, Section 2 provides the overview of the classical approaches that are employed for irrigation prediction, Section 3 provides the design methodology for the proposed irrigation prediction model, Section 4 discusses the results of the simulation. The conclusion and work intended for the future are discussed in Section 5.
This section reviews the automated irrigation systems to increase crop yield by using different machine learning methods with intelligent technologies.
Sidhu [2020] traditional machine learning methods have been used to predict the irrigation schedule of rice daily. The year 2013–2015 is used to train the models and further optimize them. The data from 2016–2017 is used for testing the models. Correlation thresholds are used for feature selection which helps in reducing the number of input parameters from the initial 26 to the final 11. The models estimated the crop water demand as a function of weather parameters. Results show that Adaboost performed consistently well with an average accuracy of 71% compared to other models for predicting the irrigation schedule. Hamouda and Msallam [11] proposed a system called Smart heterogeneous precision agriculture (SHPA), which uses a WSN for low-energy sensor nodes in an agricultural field divided into many heterogeneous agricultural regions. The Kalman filter extension is used at each step to estimate and predict agricultural variables such as soil moisture and temperature, removing the noise associated with noisy data. As a result, it is demonstrated that the proposed SHPA system surpasses previous techniques in terms of measurements, the lifetime of the network, sensing accuracy, crop production. Hamouda and Phillips [12] proposed a wireless sensor network-based optimally heterogeneous irrigation (OHI) method for agricultural water irrigation. An area, including a field, is divided into multiple heterogeneous agricultural regions. The Kalman filter extension uses associated noisy data for the filtering system state, including sensed soil moisture and temperature. Suboptimal water quantity for every area is determined by theby the random bit climbing optimization technique to attainto attain the suggested purposes. It is substantiated through simulation outcome that the suggested OHI system enhances water utilization, attaining heterogeneous crop necessities, managing diverse soil types, prioritizes crop classes, and enriches crop yields.
Ramdoo et al. [13] presented a consistent and adaptable WSN system for precision agriculture in a tomato greenhouse by combining heterogeneous environmental sensor data streams. It is primarily intended to monitor ever-changing greenhouse ecological conditions and provide farmers with real-time and historical greenhouse statistics. A qualitative methodology is used for the system assessment. At last, WSN design challenges and future research for precision agriculture are recognized.
Pandiyaraju et al. [14] presented a new intelligent routing protocol to improve the network lifetime and provide energy efficiency in the routing process that provides data to the irrigation system. This novel intelligent energy-efficient routing protocol uses fuzzy rules, and the protocol is called Terrain-based Routing using Fuzzy rules for precision agriculture. The fuzzy inference system developed in this work has been used to make decisions for routing. The system has been implemented and compared with two routing algorithms called Region-Based Routing and Equalized Cluster Head Election Routing Protocol. The experimental results show that the proposed algorithm performs better than the other existing algorithms.
Stoochnoff et al. [15] presented irrigation prediction model based on the predicted plant water status thresholds correlated to cumulative daily environmental conditions tested on Serviceberry (Amelanchier laevis) grown in a drip-irrigated pot-in-pot production system. Three irrigation treatments were applied: (1) conventional practice (control), (2) moderate restriction/stress, and (3) high restriction/stress. The moderate and high treatments reduced water consumption by 46% and 63%, respectively. Trees within the control and moderate irrigation treatments did not differ in stem caliper, while trees within the high-stress treatment trees grew slower but otherwise appeared healthy. This study demonstrated that irrigation schedules based on predicted PWS thresholds significantly reduced water use without impacting plant growth and quality.
Subathra et al. [16] aimed to address the water scarcity prevalent in the country through intelligent irrigation practices. The authors have considered certain environmental factors such as soil moisture content to create a sustainable and intelligent irrigation system in this work. An Artificial Neural Network approach is adopted to run the software part using the environmental parameters. The output obtained from the Artificial Neural Network (ANN) method with the minor RMSE error is considered for the ETo value. The computational models’ reliability is based on the results achieved through two main empirical methods. These include the Penman-Monteith equation and Hargreaves equation and compare their respective Mean Square Errors (MSE) and the Root Mean Square Errors (RMSE). Hargreaves method is suitable with the least RMSE error. In the hardware approach, the Hargreaves method has been implemented using Raspberry PI controller. The real-time data from the field controller is relayed to a hardware setup at the local base station. This is done through a wireless ZigBee protocol which eventually transmits the necessary data via a General Packet Radio Service (GPRS) link to the remote station. The output volumetric water content was calculated using Crop coefficient ETC. Solenoid valves are remotely controlled to release a computed value of water based on the data acquired at the local base station. This method of automated irrigation will mitigate the problems usually associated with farming and will finally result in greater yields of crop production.
The existing works conclude that the research community has put two irrigation approaches, named mathematical models and artificial intelligence (AI) models. The mathematical model formulates the empirical and semi-empirical equations to estimate the reference evapotranspiration (ETO) based on collected meteorological variables. However, the mathematical models usually require many climatic variables as input data, like the maximum and minimum temperature, relative humidity, solar radiation, and wind speed. And in existing AI model provides lesser accuracy and consumes more time in predicting irrigation. And the existing works did not provide any security for crop data.
The proposed automated irrigation system is focused on increasing crop productivity. The proposed model consists of four modules. Firstly, the crop and soil-related information is gathered using a wireless sensor network for the planted crops such as rice, cotton, and cassava. Secondly, the collected data is first sent to the local server to encrypt the sensed data using the elliptic curve cryptography method to avoid intruders. This encrypted data is sent to the cloud. Thirdly, the received data will be decrypted using the decryption method. Finally, the decision-making module based on the fuzzy neural network is deployed to the received data information. The final decision regarding the level of water required for crop fields would be considered. The overall proposed work architecture is presented in Fig. 1.
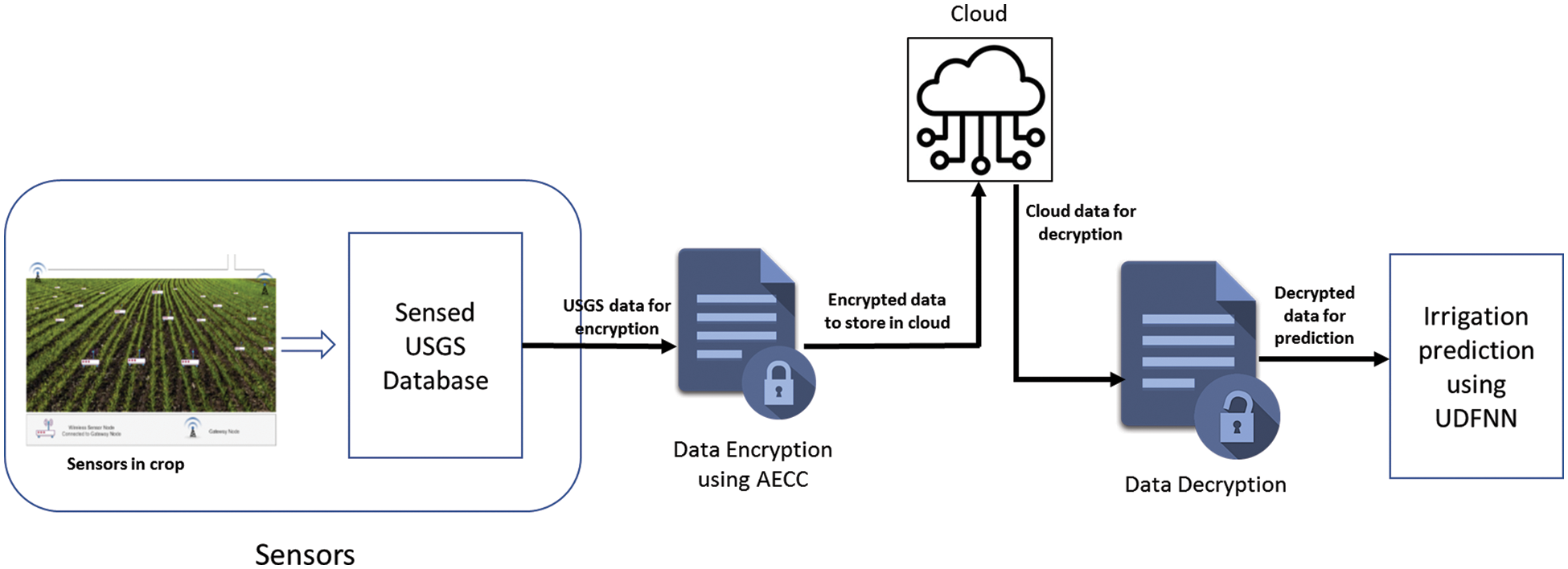
Figure 1: Overall architecture of the proposed work
A wireless sensor network has a large number of sensor nodes. Sensor nodes are used to monitor various physical phenomena like temperature, humidity, and moisture. Wireless Moisture Sensor Network (WMSN) connects moisture sensors to a wireless sensor network (WSN). The moisture data is relayed to the nearest network every hour by the sensor node. Agriculture lands could be divided into a few parts and named to be stored in the irrigation system to know the received moisture data location. Based on this location information, the particular area is rinsed with the required level of water. In this work, information such as soil moisture, crop root depth, temperature, and humidity for the plants like rice, cotton, and cassava are already sensed using WSN and stored in the based station. And then, it is sent to the local server for data encryption to avoid intrusion.
3.1 Intrusion Prevention Using Adaptive Elliptic Curve Digital Signature Algorithm (ECDSA)
After WSN senses data, it is encrypted using ECC. ECC is very fast in the key generation since it uses smaller keys. An elliptic curve was primarily utilized in H.W. Lenstra’s elliptical curve factoring method for cryptography, which inspired random elliptic curve usage. The elliptical curve cryptography substantial benefit is that smaller key usage offers the same security level. ECC provides the same security with 164-bit key, which is provided by 1024-bit key. It is extensively utilized for various applications since it offers extraordinary security with minimal computing power and battery resources. ECC is a public-key cryptosystem for generating public and private keys for the data encryption and decryption based on the mathematical complexity of resolving elliptic curve discrete logarithm concerns for handling issues involved in computing the number of steps or hops for moving from one point to another on the elliptic curve [17–19].
Elliptic curves are nothing but binary curves as well as symmetrical over x-axis whose definition is given below
where x and y represent standard variables defining function while as a, b denotes constant coefficients defining curve. As a, b values change, elliptical curve also get changed.
The basic elliptic curve cryptography consumes more energy and time less. In addition provides lesser security, due its used public key for encryption/decryption.
Adaptive Elliptic Curve Cryptography
To overcome these issues, data encryption is formulated through elliptic curve cryptography technology and a digital signature. A public key encryption method on the basis of elliptical curves theory exploits the elliptic curve properties for generating keys rather than deploying conventional keys generation approach. Existing systems use large keys to get the necessary security and thus, get slow in key generation. The proposed method used for encryption and decryption is called an adaptive elliptic curve cryptography method. A pair of shared keys are used between two hosts, which Elliptic Curve Cryptography Diffie–Hellman deduces. Deducing two secret keys will generate two pairs of (private and public) keys for each party and exchange those public keys between them to create shared secret keys. That will show in the next steps of the algorithm.
Key Generation
1. Initiate connection between Users Client and Network Server.
2. Client = (Cp, c) is a peer keys of Client.
3. Network Server = (Np, n) is a peer keys of Network Server.
4. Client = (Cp1, c1) is a peer keys of Client.
5. Network Server = (Np1, n1) is a peer keys of Network Server.
6. Client sends the (points) public keys Cp, Cp1 to Network Server.
7. Network Server sends the (points) public keys Np, Np1 to Client
Encryption
1. Client Compute the two secret keys by Np and Np1 let S1(xS1, yS1) = (c.Np), and S2(xS2, yS2) = (c1.NP1).
2. Compute d is a distance between S1x and S2x.
3. Give a1 = S1x, a2 = S2x.
4. Compute cipher soil, water, and crop data = a1 ⊕ a2 ⊕ message.
5. The client sends cipher message to a network server.
6. For the next section, the client changes the values a1 to a1 + d, and a2 to a2 + d. Based on the above procedure data will be encrypted and send it to the cloud to store for future use
Decryption
1. Network Server Compute two secret keys by Cp, Cp1 let S1 (xS1, yS1) = (n.Cp), S2(xS2, yS2) = (n1.Cp1).
2. Compute d is a distance between S1x and S2x.
3. Give a1 = S1x, a2 = S2x.
• Finally computes plain soil, water, and crop data = a1 ⊕ a⊕ Cipher message.
For the next section, Network Server changes the values a1 to a1 + d, a2 to a2 + d. Now decryption is done in cloud on basis of above process.
3.1.1 Elliptic Curve Digital Signature Key Generation
It’s a crucial phase wherein a method is used to generate the public and private keys. Data encryption is accomplished by the sender using the public key of receiver, while data decryption is accomplished by the receiver using its private key.
Step (i). A sender selects a random value dA from the interval [1, n − 1] as the sender’s private key.Where integer order of G means that n × G = 0 where 0 is the identity element.
Step (ii). The sender generates a public key using the formula PA = dA*G.
Step (iii). Similarly, the receiver selects a private key dB and generates a public key PB = dB*G.
Step (iv). The security key “K = dA*PB” is generated by sender and receiver also creates security key “K = dB*PA”.
The following procedures are carried out for message m signing by the sender:-
Step i. calculating a cryptographic hash function,
where for authenticating the sender of soil, water, and crop data, and vice-versa, hashing technique is used. Secure Hash Algorithm (SHA-1) produces 160-bit of message digest and performs 80 rounds of operation. The purpose of incorporating SHA-1 is its reduced key size which provides improved level of security at a reduced encryption overhead. The input data is divided into 32-bit blocks and left shift is done with variable n. The value of n varies at each operation resulting into new left rotation every time. This value is XORed with the round constant of the current iteration. The plaintext is hashed.
Step i. A sender next selects an integer k from the range [1, n − 1].
Step ii. Then it generates a pair of numbers (r, s)
Step iii. r = x1 (mod n) here (x1, y1) = k*G
Step iv. s = k − 1(e + dA*r)
Step v. The pair (r, s) describes signature
Step vi. The signature is forwarded to the receiver.
Encryption Procedure
Assume the sender intends to deliver the message m to the receiver.
Step i. Assume m has any elliptic curve point M.
Step ii. Sender selects a random value k from the range [1, n − 1].
Step iii. The generated cipher soil, water, and crop data would be points pair (B1, B2
where
Based on the above procedure data will be encrypted and send it to the cloud to store for future use.
Decryption Algorithm
In cloud server the receive data will be decrypted for further process by the following procedure.
For cipher soil, water, and crop data decryption, subsequent steps are executed:-
Step i. B1 and the receiver’s private key product are calculated by the receiver.
Step ii. After then, the receiver deducts this product from the second B2 point
Original data supplied by sender is denoted by M.
Signature Verification
For signature authentication of sender, knowledge about sender’s public key PA should be known to receiver
Step i. For authentication receiver desires for pair (r, s) verification in the [1, n−1] range
Step ii. After that, the receiver computes the hash function e, as in signature creation.
Step iii. The receiver then makes an approximation of w = s − 1 mod (n)
Step iv. After that, calculate u1 = e*w (mod n), u2 = r*w (mod n)
Step v. Compute (x1, y1) = u1*G + u2*PA
Step vi. If x1 = r (mod n), then signature is valid.
Now decryption is done in cloud on basis of aboveprocess.
3.2 Irrigation Control Using Uniform Distribution Based Fuzzy Neural Network (UDFNN)
Data that are stored in the cloud will be decrypted in this work using Fuzzy neural network is used for irrigation decision-making and fertilizer requirements based on the received decrypted data. The disadvantage of neural networks is that they cannot demonstrate implicit knowledge, whereas fuzzy logic systems are subjective and heuristic. The basic Fuzzy Neural Network (FNN) uses Gaussian distribution for membership calculation, but one of the disadvantages of using the normal distribution for reliability calculations is the fact that the normal distribution starts at negative infinity. This can result in negative values for some of the results.
To overcome the above-mentioned issues, this work uses uniform distribution to compute the membership value in the second layer as shown in Fig. 2.
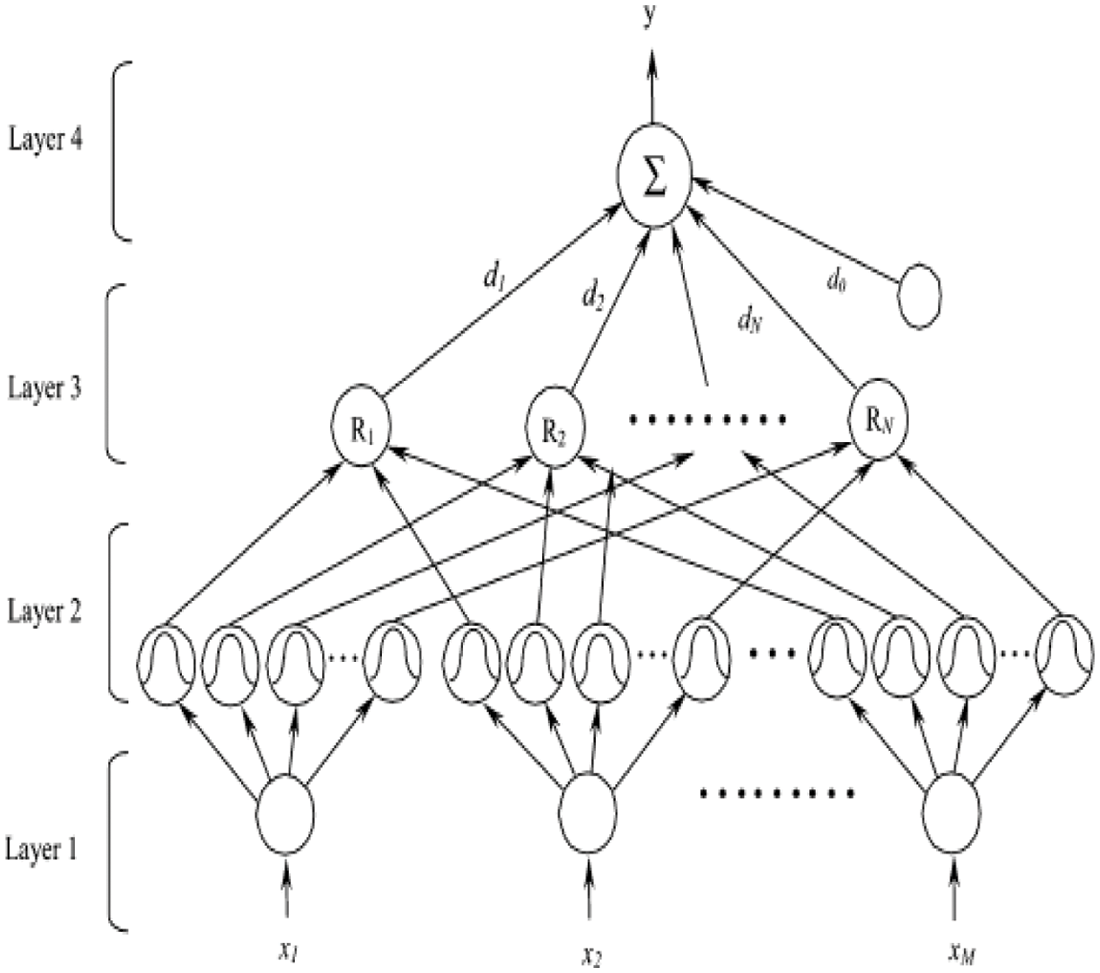
Figure 2: Four-layered fuzzy neural network structure
Uniform Distribution Based Fuzzy Neural Network (UDFNN)
The selection of fuzzy rules, input and output scaling factors, and membership functions is mainly based on trial and error, making the design of a fuzzy logic system a time-consuming job. The disadvantages of neural networks as well as fuzzy logic systems are minimized by integrating neural network learning capabilities with the resilience of fuzzy logic systems in such a manner that fuzzy logic ideas are embedded in network structure. A natural context for merging numerical data in input/output pairs form and linguistic information is offered in IF–THEN rules form uniformly [20–24].
Fuzzy neural network contains 4 layers,
Layer I—Input layer: This layer has no computations. Every node of this layer corresponds to a single input variable, and it simply passes input soil, weather, and root attributesvalues to the next layer.
Here xi, i = 1, 2, …, M, denotes FNN input variables.
Layer II—Membership function layer: Every node of this layer is a membership function which resembles one of the input variables in Layer 1’s linguistic labels (– for example, fast, slow, and so on.). Layer 2 computes membership value, which represents the degree to which an input value is suited to a fuzzy set.
where a = the lowest value of x and b = the highest value of x
Layer III—Rule layer: One fuzzy logic rule is represented by a node of this layer, which performs rule precondition matching. For each Layer 2 node, the AND operation is now used.
where Dj = diag
Layer IV—Output layer: For overall output computation as all input signals summing, the single node o(4) in this layer is designated with.
where connecting weight is Layer 4 output action strength connected with Layer 3 rule and scalar is a bias. Based on the output action strength of the above procedure, irrigation necessity is found for all crops. If an area needs water, the water valve gets open automatically, besides agronomist determines the water level for particular crops. The system gets acknowledged with the required level of the water as regards crop irrigation based on water level feedback obtained. Accordingly, the utilization of Nitrogen in the roots may be impacted by excessive water in the soil. Simultaneously, the deficiency of oxygen occurs at the roots. In general, different water levels must be maintained for each crop type since the moisture level might vary according to the crop type, which is the indication factor of the required water level. For instance, 35 VMC (Volumetric Water Content) is the required water level for chilli tree. Agronomist defines the required moisture level. An Agronomist defines the level of moisture required. Based on this water valve opening time duration will be decided and will automatically be closed if the time duration is completed.
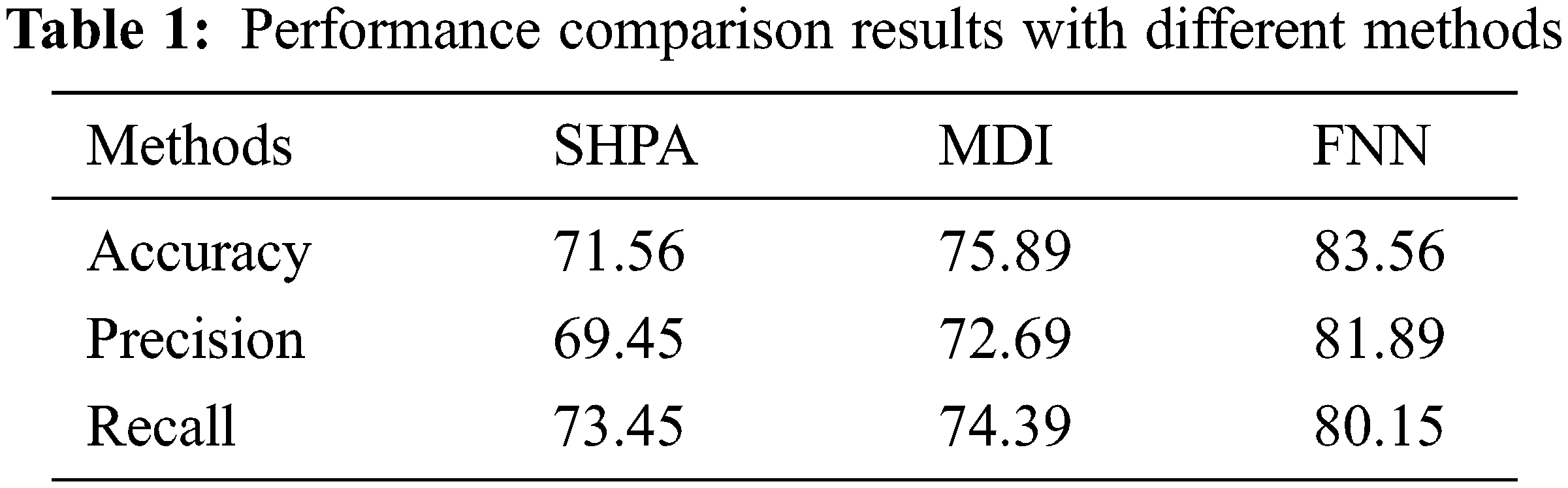
The proposed framework is comprehensively evaluated in this segment, where the implementation is carried out under MATLAB2013 simulator. Based on the performance metrics, like precision, recall, accuracy and f-measure, the Smart heterogeneous precision agriculture (SHPA), Markov-Decision based Irrigation (MDI), and proposed fuzzy Neural Network (FNN) [25–27] are compared for the dataset of USGS. In the field studies of the Andover Branch watershed and Bucks Branch watershed, the USGS Scientific Investigations Report 2018–5020 is backed by this data. At two different locations, and from two domains, the data collection has been carried out, including crop soil chemistry. On the Delmarva Peninsula, the two agricultural fields are selected from the Nanticoke and Chester River watersheds to gather the chemistry analysis results within the period of 2013–2016 regarding crop soil material. The properties of the dataset are plant root depth and pH Water. The Adams-Evans buffer (AE buffer) method is the typical lime requirement method used in Coastal Plain soils, Loss on ignition (LOI) is one of the most widely used methods for measuring organic matter (OM) content in soil (OM by LOI),M3-P,M3-K, M3-Ca, M3-Mg,M3-Mn, M3-Zn, M3-Cu, M3-Fe, M3-B, M3-S, M3-Al, Est. CEC, Base Sat, P Sat. ratio, Total N, Total C, NH4-N, NO3-N,CN ratio the final class label Irrigation which belongs to zero and one.
i) Precision
Precision refers to the percentage of the results which are relevant and defined as
ii) Recall
Recall refers to the percentage of total relevant results correctly classified by the proposed algorithm which is defined as
iii) Accuracy
Accuracy metric is widely used for evaluating the classification models. Informally, accuracy is the fraction of accurately predicted samples. Formally, accuracy has the following definition:
iv) Packet Delivery Ratio
Packet Delivery Ratio means the number of successfully received packets to the total number of packets sent by sender.
where DR means data received, DL means data loss.
In Fig. 3, the Precision results individually obtained by the proposed FNN method and the existing SHPA and MDI methods are compared in Tab. 1. In the above fig, the evaluation approaches are taken in the X-axis, and the precision results are taken as the Y-axis. In the fig, the graphical evaluation clearly shows that, the proposed FNN model outperformed the existing methods by obtaining 81.89%. The precision rate of the existing SHPA and MDI methods obtained 69.45% and 72.69% of precision rates, respectively.
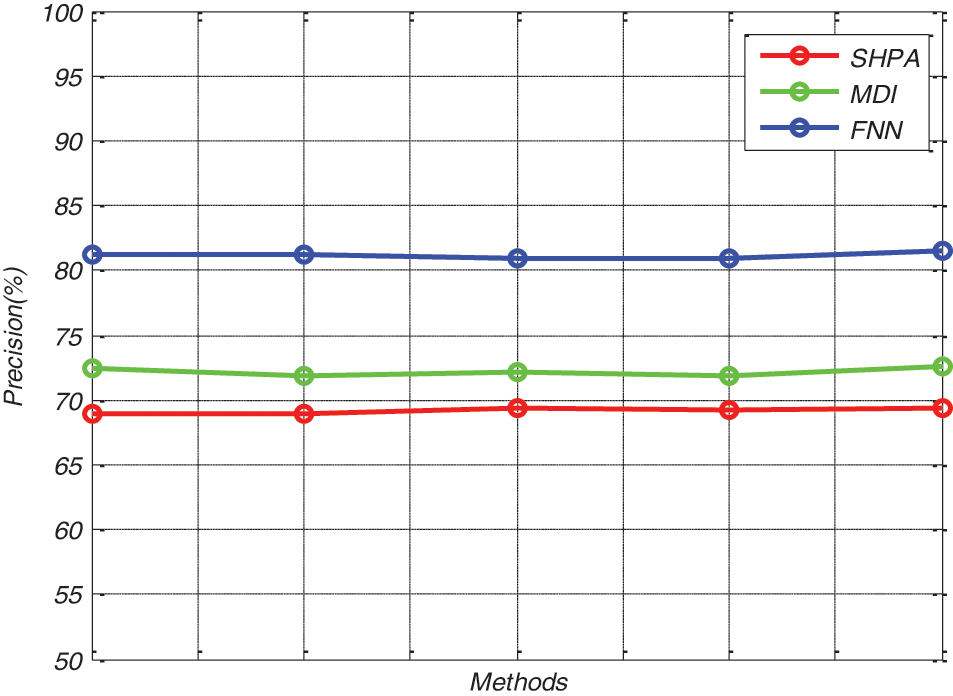
Figure 3: Precision results of different methods
The Recall results of the Proposed FNN method and the existing methods are compared in the above Fig. 4 to show the efficiency of the proposed work. It is clearly observed from the graphical results that the proposed FNN model potentially outperformed the existing methods, by obtaining 80.15% Recall rate. Alternatively, the existing SHPA and MDI methods solely deliver recall rates of 73.45%, and 74.39% correspondingly, which are comparatively lesser than the proposed method.
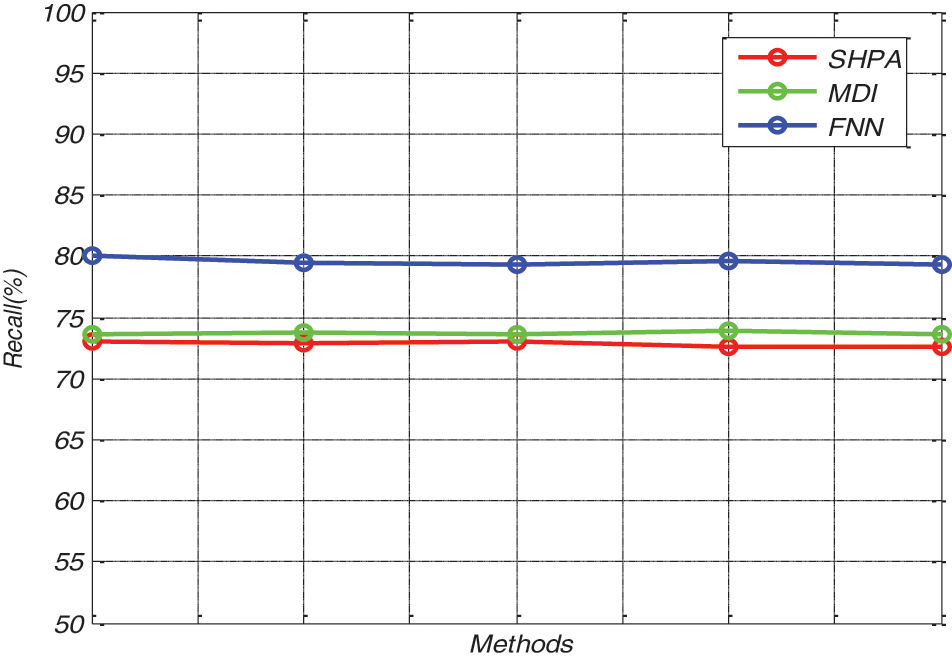
Figure 4: Recall results of various methods
In Fig. 5, accuracy outcomes obtained by proposed FNN method and the existing SHPA and MDI methods are compared. The membership function of the proposed FNN increases the true positive rate and thus, the accuracy will automatically be improved. The Accuracy obtained by the proposed FNN model is 83.56% accuracy rate. Alternatively, the existing SHPA and MDI methods resulted in the accuracy rates of 71.56% and 75.89%, respectively, which are much lesser than the proposed method.
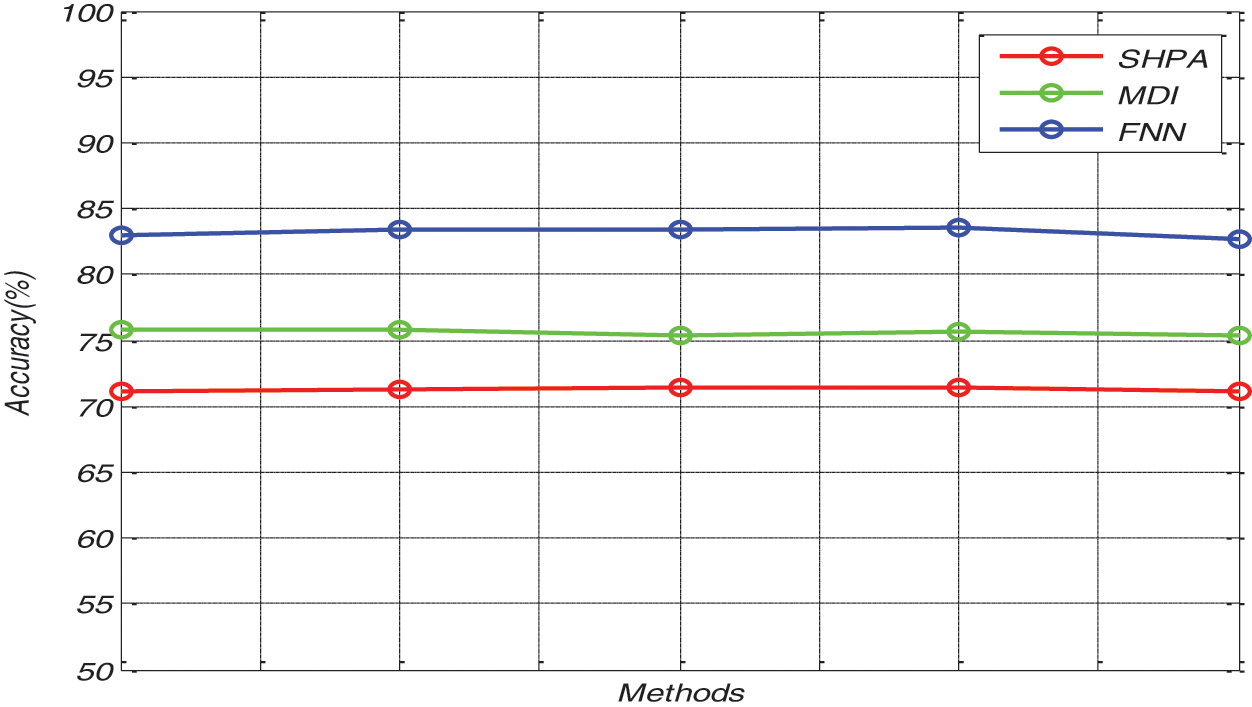
Figure 5: Accuracy outcomes of various methods
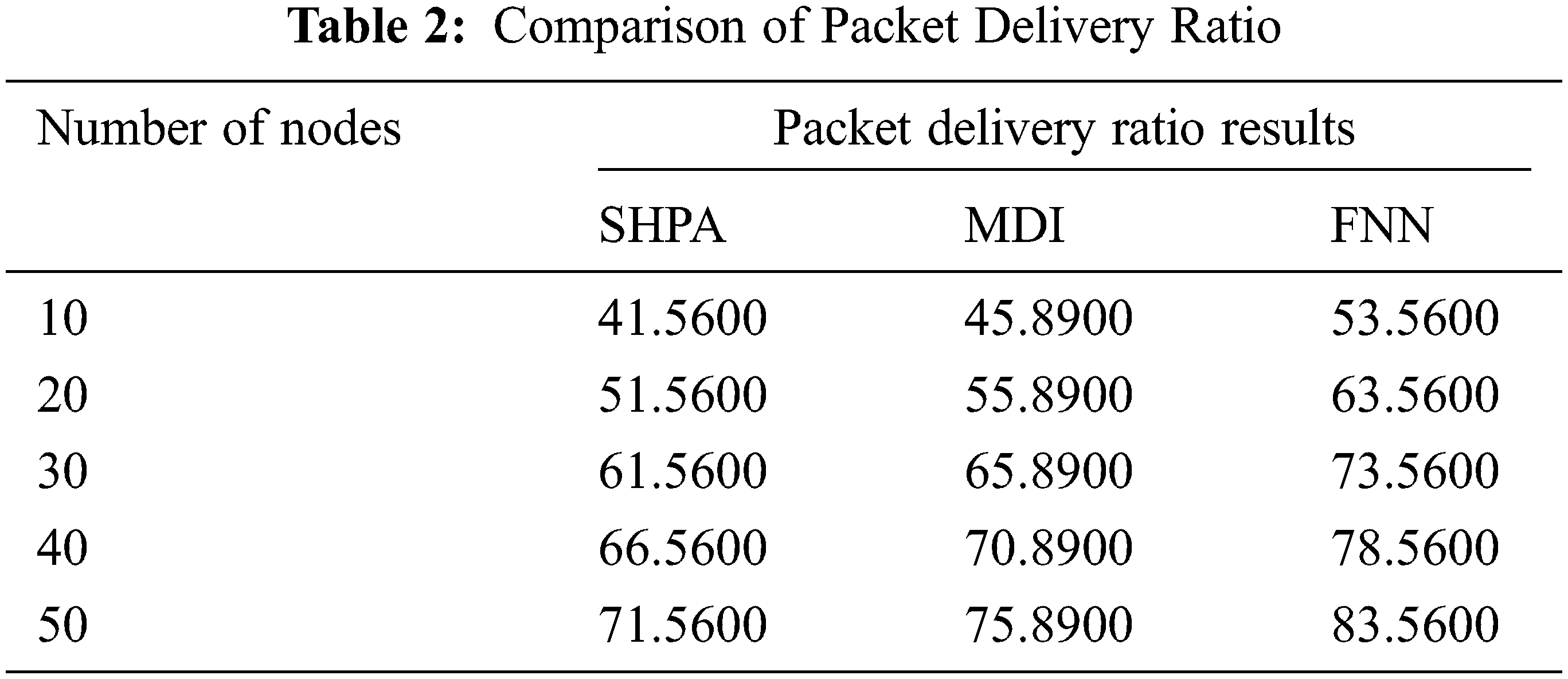
The performance evaluation of the proposed approach in terms of Packet delivery ratio is shown in Fig. 6. The packet delivery ratio of the proposed work is compared with the existing SHPA and MDI approaches. From the results, it is concluded that the proposed FNN model resulted in 83.65% PDR whereas the existing SHPA and MDI methods attains lesser PDR of 71.56%and 75.89%, respectively. The security aspects of the proposed Advanced Elliptical Digital Signature Algorithm in preserving the agriculture data provides high level of security [28,29] as the “x1, y1 and m” values are known only to the registered users and cannot be duplicated as shown in Tab 2. Thus the Advanced Elliptical Digital Signature Algorithm proves to be highly rigid against network vulnerabilities.
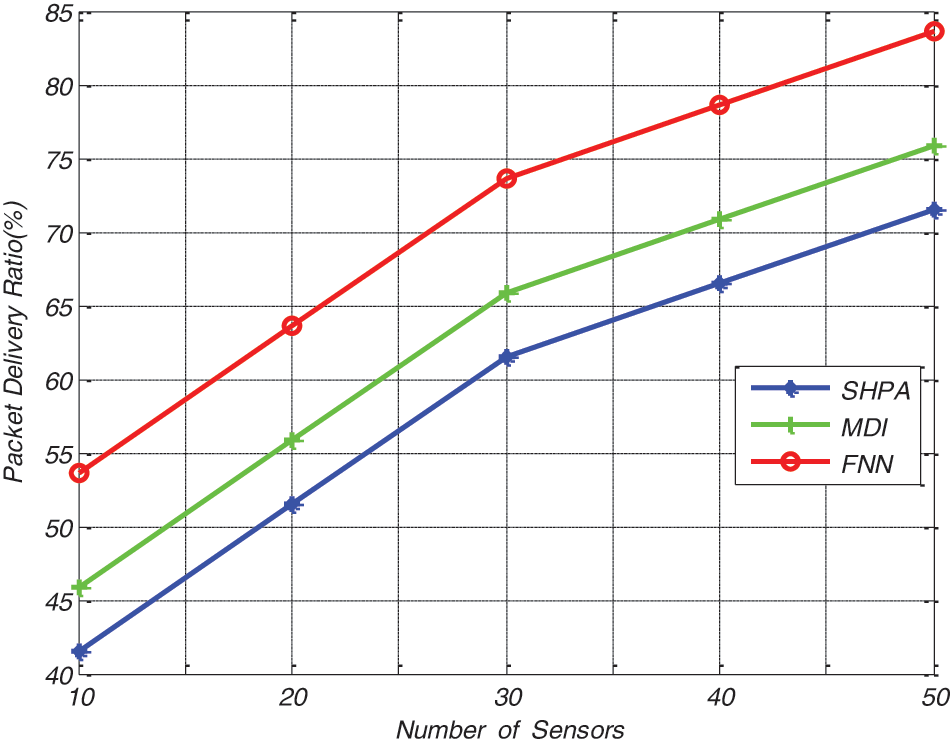
Figure 6: Packet delivery ratio results of different methods
Irrigation is crucial in a range of agricultural cropping systems used in semiarid and arid regions where water management and application are significant issues. Numerous components of irrigation management, such as weather, soil, water, and crop data, must be addressed effectively and uniformly from varied and dissimilar information-based systems. Recently, a Multi-Agent System (MAS) was presented that is composed of varied agent subsystems with distinct goals for achieving the MAS’s global goal. The MAS is cloud-based and is capable of collecting data from Wireless Sensor Networks (WSNs) installed in rice, cotton, and cassava crops for the purpose of knowledge discovery and decision making. A radial basis function network was utilised to predict irrigation. However, present data security research has not concentrated on locations where an intrusion could contaminate data during transmission to the cloud, degrading decision-making accuracy. To overcome the aforementioned obstacles, this work employs an excellent irrigation prediction technique. While making a selection, soil moisture, temperature, plant height, and root depth are all considered. Sensors attached to the crop field will collect the data indicated above. Sensitive data is transferred to a local server, which uses Adaptive Elliptic Curve Cryptography to encrypt it (AECC). The data is then encrypted and transferred to the cloud. After decrypting the cloud-based data, it will be transferred to the decision-making module. Finally, a fuzzy neural network with a uniform distribution is formed using the decision-making module’s data information. Finally, the amount of water required for crop fields would be determined. This outcome will dictate the duration of the water volve opening and the amount of fertiliser required. Experiments demonstrate the proposed model’s performance on the United States Geological Survey (USGS) database in terms of precision, accuracy, recall, and packet delivery ratio.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. E. Avşar, K. Buluş, M. A. Saridaş and B. Kapur, “Development of a cloud-based automatic irrigation system: A case study on strawberry cultivation,” in Proc. 7th Int. Conf. on Modern Circuits and Systems Technologies (MOCAST), Thessaloniki, Greece, vol. 12, pp. 1–4, 2018. [Google Scholar]
2. M. F. M. Jaafar, H. Hussin, R. Rosman, T. Y. Kheng and M. J. A. Hussin, “Smart cocoa nursery monitoring system using irt for automatic drip irrigation,” in Proc. IEEE 13th Int. Conf. on Telecommunication Systems, Services, and Applications (TSSA), Bali, Indonesia, vol. 4, pp. 108–113, 2019. [Google Scholar]
3. K. VinothKumar, T. Jayasankar, M. Prabhakaran and V. Srinivasan, “Crop based irrigation system with plot selection,” Journal of Social, Technological and Environmental Science, vol. 6, no. 2, pp. 265–273, 2017. [Google Scholar]
4. Chunduri, K. and Menaka R. “Agricultural monitoring and controlling system using wireless sensor network,” Soft Computing and Signal Processing, vol. 7, pp. 47–56, 2019. [Google Scholar]
5. S. Rajendrakumar and V. K. Parvati, “Automation of irrigation system through embedded computing technology,” in Proc. of the 3rd Int. Conf. on Cryptography, Security and Privacy, Chen Chang, vol. 5, pp. 289–293, 2019. [Google Scholar]
6. S. Kaur, “An automatic irrigation system for different crops with WSN,” in 2017 6th Int. Conf. on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, vol. 4, pp. 406–411, 2017. [Google Scholar]
7. M. H. A. E. Wahed and T. Ali, “Estimating reference evapotranspiration using modified blaney-criddle equation in arid region,” Bothalia Journal, vol. 44, no. 7, pp. 183–195, 2015. [Google Scholar]
8. S. Gobhinath and K. Durga, “Smart irrigation with field protection and crop health monitoring system using autonomous rover,” in 2019 5th Int. Conf. on Advanced Computing & Communication Systems (ICACCS), Coimbatore, India, vol. 12, pp. 198–203, 2019. [Google Scholar]
9. A. Sabo, S. M. Qaisar, A. Subasi and K. A. Rambo, “An event driven wireless sensors network for monitoring of plants health and larva activities,” in 2018 21st Saudi Computer Society National Computer Conf. (NCC), Riyadh, Saudi Arabia, vol. 3, pp. 1–7, 2018. [Google Scholar]
10. N. S. Martins, A. C. M. d. Rosário, J. A. Pombo and S. J. Mariano, “Blueberries field irrigation management and monitoring system using PLC based control and wireless sensor network,” in 2016 IEEE 16th Int. Conf. on Environment and Electrical Engineering (EEEIC), Florence, Italy, vol. 7, pp. 1–6, 2016. [Google Scholar]
11. A. Dahane, B. Kechar, Y. Meddah and O. Benabdellah, “Automated irrigation management platform using a wireless sensor network,” in 2019 Sixth Int. Conf. on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, vol. 15, pp. 610–615, 2019. [Google Scholar]
12. Y. E. Hamouda and M. M. Msallam, “Smart heterogeneous precision agriculture using wireless sensor network based on extended kalman filter,” Neural Computing and Applications, vol. 31, no. 9, pp. 5653–5669, 2019. [Google Scholar]
13. Y. E. Hamouda and C. Phillips, “Optimally heterogeneous irrigation for precision agriculture using wireless sensor networks,” Arabian Journal for Science and Engineering, vol. 44, no. 4, pp. 3183–3195, 2019. [Google Scholar]
14. V. D. Ramdoo, K. K. Khedo and V. Bhoyroo, “A flexible and reliable wireless sensor network architecture for precision agriculture in a tomato greenhouse,” in Information Systems Design and Intelligent Applications, Singapore, Springer, vol. 11, pp. 119–129, 2019. [Google Scholar]
15. Y. E. Hamouda, “Smart irrigation decision support based on fuzzy logic using wireless sensor network,” in Proc. Int. Conf. on Promising Electronic Technologies (ICPET), Deir El-Balah, Palestine, vol. 4, pp. 109–113, 2017. [Google Scholar]
16. T. T. Huong, N. H. Thanh, N. T. Van, N. T. Dat, N. Van Long et al., “Water and energy-efficient irrigation based on markov decision model for precision agriculture,” in Proc. IEEE Seventh Int. Conf. on Communications and Electronics (ICCE), Hue, Vietnam, vol. 6, pp. 51–56, 2018. [Google Scholar]
17. S. Joseph and J. IgnatiousMonterio, “Self configuring wireless sensor network for precision irrigation,” in Government College of Engineering Kannur, Int. Conf. on Systems, Energy & Environment (ICSEE), Trivandrum, vol. 14, pp. 327–345, 2019. [Google Scholar]
18. J. Louw, G. Niezen, T. D. Ramotsoela and A. M. Abu-Mahfouz, “A key distribution scheme using elliptic curve cryptography in wireless sensor networks,” in 2016 IEEE 14th Int. Conf. on Industrial Informatics (INDIN), Poitiers, France, vol. 6, pp. 1166–1170, 2016. [Google Scholar]
19. Y. Zhang, N. Kumar, J. Chen and J. J. Rodrigues, “A secure energy-efficient access control scheme for wireless sensor networks based on elliptic curve cryptography,” Security and Communication Networks, vol. 9, no. 17, pp. 3944–3951, 2017. [Google Scholar]
20. C. Deepa and B. Latha, “An energy efficient secure routing (eesr) using elliptic curve cryptography for wireless sensor networks,” in Proc. Second Int. Conf. on Inventive Communication and Computational Technologies (ICICCT), Coimbatore, India, vol. 5, pp. 1603–1608, 2018. [Google Scholar]
21. Y. L. Prasanna and E. M. Reddy, “A theoretical study of elliptic curve cryptography for location based services,” in Proc. Int. Conf. on Big Data Analytics and Computational Intelligence (ICBDAC), Chirala, Andhra Pradesh, vol. 8, pp. 404–407, 2017. [Google Scholar]
22. C. Sun, H. Gao, W. He and Y. Yu, “Fuzzy neural network control of a flexible robotic manipulator using assumed mode method,” IEEE Transactions on Neural Networks and Learning Systems, vol. 29, no. 11, pp. 5214–5227, 2018. [Google Scholar]
23. H. Han, X. Wu, Z. Liu and J. Qiao, “Data-knowledge-based fuzzy neural network for nonlinear system identification,” IEEE Transactions on Fuzzy Systems, vol. 8, no. 9, pp. 2209–2221, 2019. [Google Scholar]
24. A. A. Khater, A. M. El-Nagar, M. El-Bardini and N. El-Rabaie, “A novel structure of actor-critic learning based on an interval type-2 tsk fuzzy neural network,” IEEE Transactions on Fuzzy Systems, vol. 28, no. 11, pp. 3047–3061, 2019. [Google Scholar]
25. G. Mohapatra, G. Ambarish, L. Saroj Kumar and B. Keswani. “Neural network and fuzzy logic based smart dss model for irrigation notification and control in precision agriculture.” in Proc. of the National Academy of Sciences, India Section A: Physical Sciences, Singapore, vol. 89, no. 1, pp. 67–76, 2019. [Google Scholar]
26. P. Parida, C. Pradhan, X. Z. Gao, D. S. Roy and R. K. Barik, “Image encryption and authentication with elliptic curve cryptography and multidimensional chaotic maps,” IEEE Access, vol. 9, pp. 76191–76204, 2021. [Google Scholar]
27. D. Prabakaran and S. Ramachandran, “Multi-factor authentication for secured financial transactions in cloud environment,” Computers, Materials & Continua, vol. 70, no. 1, pp. 1781–1798, 2022. [Google Scholar]
28. S. Kim, “Complete analysis of implementing isogeny-based cryptography using huff form of elliptic curves,” IEEE Access, vol. 9, pp. 154500–154512, 2021. [Google Scholar]
29. R. Kumar, P. Kumar, R. Tripathi, G. P. Gupta, T. R. Gadekalu et al., “SP2F: A secured privacy-preserving framework for smart agricultural unmanned aerial vehicles,” Computer Networks, vol. 187, pp. 1–14, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |