DOI:10.32604/iasc.2023.028852

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2023.028852 |  |
| Article |
Wireless Network Security Using Load Balanced Mobile Sink Technique
1Department of Information Technology, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, P.O. Box 84428, Riyadh 11671, Saudi Arabia
2Department of Mathematics, Faculty of Science, Mansoura University, Mansoura, 35516, Egypt
3Department of Computational Mathematics, Science, and Engineering (CMSE), Michigan State University, East Lansing, 48824, MI, USA
4Department of Computer Science and Engineering, Bannari Amman Institute of Technology, Sathyamangalam, 638401, India
5Department of Computer Science and Engineering, CHRIST (Deemed to be University), Bengaluru, 560074, India
6Department of Computer Sciences, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, P.O. Box 84428, Riyadh 11671, Saudi Arabia
*Corresponding Author: Doaa Sami Khafaga. Email: dskhafga@pnu.edu.sa
Received: 19 February 2022; Accepted: 07 April 2022
Abstract: Real-time applications based on Wireless Sensor Network (WSN) technologies are quickly increasing due to intelligent surroundings. Among the most significant resources in the WSN are battery power and security. Clustering strategies improve the power factor and secure the WSN environment. It takes more electricity to forward data in a WSN. Though numerous clustering methods have been developed to provide energy consumption, there is indeed a risk of unequal load balancing, resulting in a decrease in the network’s lifetime due to network inequalities and less security. These possibilities arise due to the cluster head’s limited life span. These cluster heads (CH) are in charge of all activities and control intra-cluster and inter-cluster interactions. The proposed method uses Lifetime centric load balancing mechanisms (LCLBM) and Cluster-based energy optimization using a mobile sink algorithm (CEOMS). LCLBM emphasizes the selection of CH, system architectures, and optimal distribution of CH. In addition, the LCLBM was added with an assistant cluster head (ACH) for load balancing. Power consumption, communications latency, the frequency of failing nodes, high security, and one-way delay are essential variables to consider while evaluating LCLBM. CEOMS will choose a cluster leader based on the influence of the following parameters on the energy balance of WSNs. According to simulated findings, the suggested LCLBM-CEOMS method increases cluster head selection self-adaptability, improves the network’s lifetime, decreases data latency, and balances network capacity.
Keywords: Wireless sensor network; load balancing mechanism; optimization; power consumption; network’s lifetime
Wireless networks are characterized by the enormous count of a sensor node that is microscopic in size, low in cost, and consumes little energy. WSNs are broadly applied in surveillance systems, climatic and environmental surveillance, natural catastrophe prediction and response, intelligent medical advances, and other disciplines [1]. Depending on the specific kinds of sensors nodes, WSN is classified as static or mobility wireless sensor networks. Once installed, the position of the node in static WSN is permanent. Because nodes with low power near the static sink node may be designated as member nodes regularly, those nodes’ energy consumption will be excessive, resulting in the sensor nodes’ untimely demise. Sensors are used in mobile Ad hoc applications.
The internet of things has wide use, including e-health, e-commerce and transportation, precision farming, smart homes, and smart cities. Nonetheless, these systems necessitate specific characteristics such as reduced latency, safety, and dependability. The mentioned features are critical for optimal IoT utilization, and it has been discovered that new platforms necessitate distinctive features. In the case of e-health and intelligent education, for example, secured, dependable, and private communication is essential. Likewise, ensuring accessibility and a short response time is critical in the event of an emergency. Every application requires energy efficiency; as a result, it creates a link for balancing load to meet standards [2]. The WSN serves as a link between the actual and virtual worlds.
Assuming that the mobile sink linkage with other sites is immutable in a specific time frame, portable WSN can be reduced to static WSN. In this time frame, it allows for effective electricity navigation techniques. These techniques rely on static WSN to mobile WSN [3–5]. The Lower Energy with Adaptive Cluster Hierarchy Protocols (LEACH) is a well-known cluster-based routing method. This program separated nodes in the network into separate groups first and then replaced heads in clusters regularly to balance network energy consumption, resulting in a longer system life span [6,7]. In particular, to decrease energy usage and balance system resources, paper [8] uses the Hybrid, Energy-Efficient, Distributed Cluster technique (HEED), Stable Election Protocols (SEP) for the cluster [9], and LEACH-C) [10] was developed.
Besides sensing, WSNs for IoT confront several challenges, including sensor node deployment in the field, hardware problems, communications manner, limited battery capacity, and growth in computing cost. Aside from these limitations, WSNs designed for IoT have issues with the quality of service (QoS), power management, and privacy [11,12]. Furthermore, energy consumption has been a primary concern when developing the WSN architecture for IoT, prompting the research to dig deeper into ways to reduce power usage [13]. Many concepts, such as sequencing and grouping, have been implemented to reduce energy usage.
There are numerous clusters in a WSN, each with its cluster head, and if one of the clusters heads fails, the network becomes unbalanced, and data transfer continues to fall. Other factors, like energy usage, contribute to network lifetime decrease [14]. An energy depletion equilibrium or load balancing approach was developed. Several load balancing approaches have previously been developed [15,16], even though these techniques confront challenges including high dimensionality, CH lifespan, CH-selection, grouping, and sequencing. The proposed LCLBM-CEOMS method helps to improve the enhanced load-balanced network and develop the WSN lifetime. The main contribution of the work is given below:
Ø The primary aim of LCLBM is to extend the system’s lifetime by balancing a load.
Ø Balancing cluster algorithm for research and analysis.
Ø Initially, a design tailored to the networking topology and energy-based model is created, followed by an adaptable clustering head distribution method.
Ø To allocate nodes initially with good energy and cluster head, functions are used. The density functions of energy comprising factors are the rate of residual energy and density. Based on this rate, adjacent sensor nodes are built. Compared to typical clustering algorithms, the suggested technique considers the residual energy of nodes in the network and the density of nodes in the region. Hence to extend the network’s life, CEMOS is used.
The proposed LCLBM-CEOMS research helps to identify the solutions for:
Ø How does the cluster head selection method address the load-balancing issue?
Ø How the ACH mechanism improves the lifetime?
Ø How the proposed algorithm reduces energy utilization?
The remaining sections of this article are as follows: Section 2 consists of a brief study of existing Wireless Sensor Networks, Cluster Head (CH), Lifetime centric load balancing mechanism (LCLBM), and Cluster-based energy optimization using mobile sink (COMS). Section 3 explains the working principle of the proposed work. Section 4 evaluates the result and gives a comparison of different algorithms. Section 5 finally concludes the research performance.
The static and mobile WSN routing algorithms are a traditional technique that impairs balancing energy and less network life span. This balancing drawback is due to topology changes in mobile WSN during data transfer using portable sinks. Some research scholar develops routing systems that leverage mobile sinks to manage network energy usage. A node can be designated as a meeting point based on the distance from the portable sink to gather data from neighboring nodes and subsequently connect with the mobile sink [17,18].
In [19] devised, a data-gathering routing scheme that allocates the node with the highest cluster head density. This prevents energy transmission over long distances and high battery consumption. It results in network resource balancing using mobile data collection and hierarchical cluster techniques. The author developed a data-gathering method using the tree cluster technique. Specific meeting points and sub meeting points are primarily based on the node’s remaining energy. The number of multi-hops which includes both and data for all meeting spots was gathered by mobile sink [20].
The inventor of WSN [21] uses the particle swarm optimization (PSO) method to improve a load balancing technique, and routing is performed on CH. every specified node sends its data to the sink, which handles load balancing. The PSO-based network routing contains a strategy for effective particles encoding. It introduces a unique PSO-based routing and clustering algorithm for WSNs [21], outperforming the previously submitted approach [22].
The genetic (GA) algorithm was used to tackle clustering techniques in WSNs [23]. The gateway is used for residual energy for clustering, and space between CH and SN is used. The trade-off between forwarding numbers and transmission time is used in routing. Additionally, gateways residual energy is used. The chromosome representation has proven effectively resolve routing and clustering issues. The authors in [24] studies related to local data nodes to overcome the difficulties in clustering and routing techniques in WSN.
The article [25] author uses an artificial bee colony (ABC) to overcome routing technique issues and cluster challenges in WSN. Clusters are created using the method’s data from the neighborhood and SN energy level. The number of paths and energy efficiency help obtain fitness functions for routing issues in ABC. According to [26], the author addressed the clustering and routing problem in WSN by assuming a hotspot. The introduced approach uses the multi-objective immune algorithm to measure residual energy from the sink and thereby splits the network into unequal cluster sizes.
The author discussed routing and clustering methods in WSN [27], in which all stations are diverse. This technique selects the CHs for each round, resulting in fewer heterogeneous nodes. The heterogeneous node and CH were selected to support an SN to transmit data to the sink node. The writer of the paper [28] solved the routing and grouping challenges in WSNs by treating them as a Pareto optimization, a multi-objective problem. Quality links are built using routing tree and Pareto optimization for CH.
In [29], the researchers discussed clustering, utilizing fuzzy rules with a convolutional neural network for WSN. For cluster creation, four parameters are used: CH energy, sink, CH distance, and CH and node distance. They use the CHs degree to construct a cluster, and it is incapable of managing the load sensor nodes among CH. [30] proposed a well dynamically layer dual-CHs routing method based on the Krill herds (KH) used in underwater WSN. The main aim is to keep track of how much electricity CHs use.
Making appropriate usage information about the location and speed of a mobile node to choose a cluster head can help WSNs balance their energy usage [31–43]. The method first categorized sensor nodes before constructing a CH. It is selected using a threshold function based on nodes’ energy. Initially, clustered sensor networks work based on location. The allocated cluster heads to every cluster based on the residual energy of nodes and the distance between nodes. The main problems with existing methods are computation cost is very high due to the formation of clusters and processing. Sensor nodes take individual processing time in cluster head selection.
3 Proposed Load Balanced Mobile Sinking Methodologies
The models of network, energy, CH sharing, motion, assistant cluster head (ACH), and its executions are all addressed in the below sections of the LCLBM-CEOMS. Fig. 1 explains the overall architecture of the new proposed methodology. The proposed method has many models. The system model has a standard LEACH protocol with a mobile sink in WSN.

Figure 1: Overall architecture of the system
The network’s infrastructure in the circular array is developed in this section with the sink center and each layer in the form of squares that does not lose their attributes. The networking topology is divided into a ring form. In the beginning, all nodes are immobilized and deployed, so all clusters than an equal amount of energy. Each sensor network can scathe le range of transmission, and the information of networks are in sinks and their parameters s, l, e and. Similar behavior is used to gather the data. For example, this data is broken down into numerous pieces which control traffic flow and are regarded as a continuous parameter.
The energy model is presented in this portion of the study effort. The first order of energy is being used here, and the optimal energy model was developed in the meantime. The power amplifier and radio circuitry in the transmitter require energy to operate. While broadcasting, the receiver supplies energy to an electronic radio device. The consumption of energy is needed for the bits m to replace at the distance ‘e’. The model’s energy consumption is shown in Eq. (1)
The proportion of transmitters and amplifiers properties is the threshold value e0.
Assuming that the motion models of a mobile sink in a two-dimensional monitoring region is as follows:
where X(Ti) = [X(Ti) X(Ti) Y(Ti) Y(T)] and Y(Ti) = [X(Ti) X(Ti) Y(Ti)] Ti is mobile sink time t; p(t), p(t), q(t), q(t) are mobile sink coordinates and speed in the p and q directions at t time; D is transition matrix state; and noise coefficient matrix; CM(T) ~N(0, G(T)) is the Gaussian noise with covariance G(T); t is sampling time; is angular velocity.
The mobile sink follows the mobility model described above and takes data from all sensor nodes. When the portable sink has collected all of the data from the sensor nodes, the round is over. The portable sink is situated at (X(Rn), Y(Rn)) to begin collecting in the rth game.
This part covers the Assistant CH mechanism to design a perfect inter-communication to achieve load balancing. Cluster head share, conserving energy, and helper CH-mechanism is also included in this part.
Considering range between the CH as ‘eo’ and the sink; additionally, the power will be minimized, if the following condition Eq. (6) is met:

If all of the criteria are true, the distributions are indeed the CH-optimal distributions, and Eq. (6) must be demonstrated. Assuming that area of the other layer is about equal to the number of clusters. The distance and sink are Y. Assume a randomized node that can be distributed at random to provide coordinates, where the given coordinate is CH distance and serves as a member in the cluster. Furthermore, if the square of the distance between cluster members and CH is less than the nominal energy consumption, then the cluster member with appropriate CH is delivered through Eq. (7).

A range between the sink and the cluster member is Z, and the angle middle of the CH and member of cluster is A in Eq. (7). The distance of cluster member and the CH is measured in Eq. (8)

The Eq. (8) can be changed and displayed in a variety of ways Eq. (9).
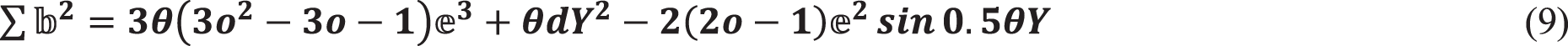
As a result, if you consider Eq. (6), you can reduce the energy overhead by using Eqs. (7) and (8). It’s also worth noting that  is decreased if coordinates are drawn by just using Eq. (10).
is decreased if coordinates are drawn by just using Eq. (10).

As a result, once Eq. (6) is met, the best CH can be chosen.
In this part, the study uses an energy consumption model to select some nodes near the sensor node for establishing a neighborhood set for that node. It designs an energy density function for that set. Furthermore, the CH selector threshold is defined by the energy density function and the movement effectiveness functional, both of which are built using the motion characteristics of the mobile node. Lastly, the cluster heads selector’s threshold can be adapted based on node fatality.
3.5.1 Constructing Density Function of Energy Using Neighborhood Nodes
Assume that Ns sensors are distributed in a monitored region randomly. In each round, KRopt is the node number chosen as cluster heads. The targeted proportion of cluster - heads compared to all nodes is as follows:
3.5.2 Sensor Node Neighborhood Set construction
As is well known, data communication consumes more energy than data sensing and processing. As illustrated [30], this work adopts the first order in the radio model to represent energy usage in nodes. If another packet contains kb bits of data, the energy consumes for transmitting kb bits of ETX data and retrieving kb bits of data ERX can be written as follows:
ETXelec, ERXelec, and ETXamp represent the power consumption of the transmitter, the energy consumption of receivers, and the usage of amplifiers in energy. The coefficient amplifies free space, and correspondingly, the coefficients amplified of multi-path are fs and mp. Kb is the data bits number, d is the transmitter and receiver distance, and d0 is the distance of critical communication. Eelec refers to the power of 1-bit consumption of information execution related to the k node. The data pieces number, transmitter and receiver at ‘d’ distance, and d0 is the critical communication spacing.
3.5.3 Construction of Energy Density Function
The neighboring nodes leftover power rates fe(si) is included as Formula 15 to increase the chance of nodes to have huge energy for consumption. being designated as cluster heads.
Where, the sensor node residual power si is Er(si), the amount of nearest neighbors of a sensed data si is n′, and the average left over energy of sensor node si’s neighborhood node is Eavg.
The neighborhood node density - functional f(si) is proposed here to describe the relationship between cluster head energy consumption and mobile nodes within the clusters.
Equation describes the energy density - functional fe(si) of node si by mixing fe(si) and f(si) Eq. (18).
The relative distance ∆Dsi is introduced the proposed to represent distance changes among a node and a mobile sink.

The CH-Rotation and CH-selection are used to reducing the power consumption. This section focuses on power to range; particularly, it formulates the ratios between both the node’s residual energy and node to CH distance, which is indicated as SF−e; also, Eq. (22) offers the mathematical method for calculation.
3.7 Assistant Cluster Head (ACH)
During the cluster development, it was discovered that CH views traffic differently than its cluster members, causing consume more energy in CH than its members, requiring the consumption of power to be balanced. The CH and CM roles of these sensor nodes are reversed to do this. Furthermore, it has been discovered that when role reversal, energy consumption is higher while sending messages for their function; to address this, assistance CH, i.e., ACH, is utilized. Only ACH and CH reverse roles while using the ACH, increasing power consumption. The node with the most significant SF-e number is chosen first, and the node with the second-highest SF-e value is designated as the ACH.
3.7.1 LBCM Based Inter Cluster Communication Model
The part describes the best inter-cluster communication paradigm, in which each node acts as the player and selects the nearest node as the next hop to save power. As a result, the node with the smallest route from the other nodes is more likely to be selected as the next hop. However, this leads to energy depletion and, as a result, network disintegration. To minimize this, create an ideal inter-cluster-based communication technique. The LCLBM model is divided into levels. The LCLBM strategic approach comprises a set of nodes and information directed toward these nodes’ adjacent layers; also, OICC aids in establishing equilibrium.Further balanced energy is checked. Also, CH builds the choice to forward data to the next on its own. Furthermore, the LCLBM goal can be achieved using Eq. (23).

The node anywhere at arbitrary level n of a given topology of the network are regarded as a set in the LCLBM model; for example, if the nodes are in the nth layer N, the set of OICC is given as Eq. (24)
3.7.2 LCLBM Based CH-Selection
Step 1: Therefore, base stations use network topology parameters, e, S, and l to determine the most efficient distribution.
Step 2: After the optimal sharing of the cluster head is completed, the nodes calculate the output from the cluster head using optimization and the excess energy.
Step 3: Once the distribution of eo has been determined and optimal, the next sensor node computes the matching range et-CH and then gets SF-e using Eq. (19).
Step 4: In addition, the sensor node transmits the selection signal of CH, which holds the data of o, ID, and SF-e. Once the sensor device receives the broadcast television signal, it equates the computed ratio to a particular node ratio. If the given node is high at the balance, it generates a CH alert by recommending itself as cluster head. As a result, we have chosen CH as the node with the highest ratio.
Step 5: Likewise, the respective cluster picks the appropriate bunch Head (CH) via an invite message broadcasted by the CH. This invite message provides data such as id of layer, sender ID, and minimization of energy phenomena.
Step 6: ACH is then picked by ordering all the calculated ratios, with the greatest being chosen as the cluster head.
3.7.3 Assistant CH-Protocol Step
The method is conducted in the following order to decrease the energy and balance the use of the Assistant Cluster Head:
Step 1: After every round, the current CH is checked to the assistant CH’s ratio; if the current CH’s balance is less, a signal is issued.
Step 2: If CH assistance CH chooses to be CH, it transmits the message and waits for cluster members to acknowledge it.
Step 3: After receiving the confirmation, the membership keeps track of data regarding the next ACH.
Step 4: If the ACH ratio is less than the current cluster head, the discarding is triggered, and the cluster head remains CH. As a result, this sub-process is prone to load balancing. It assesses the LCLBM-mechanism in the next step after the mechanisms have been created.
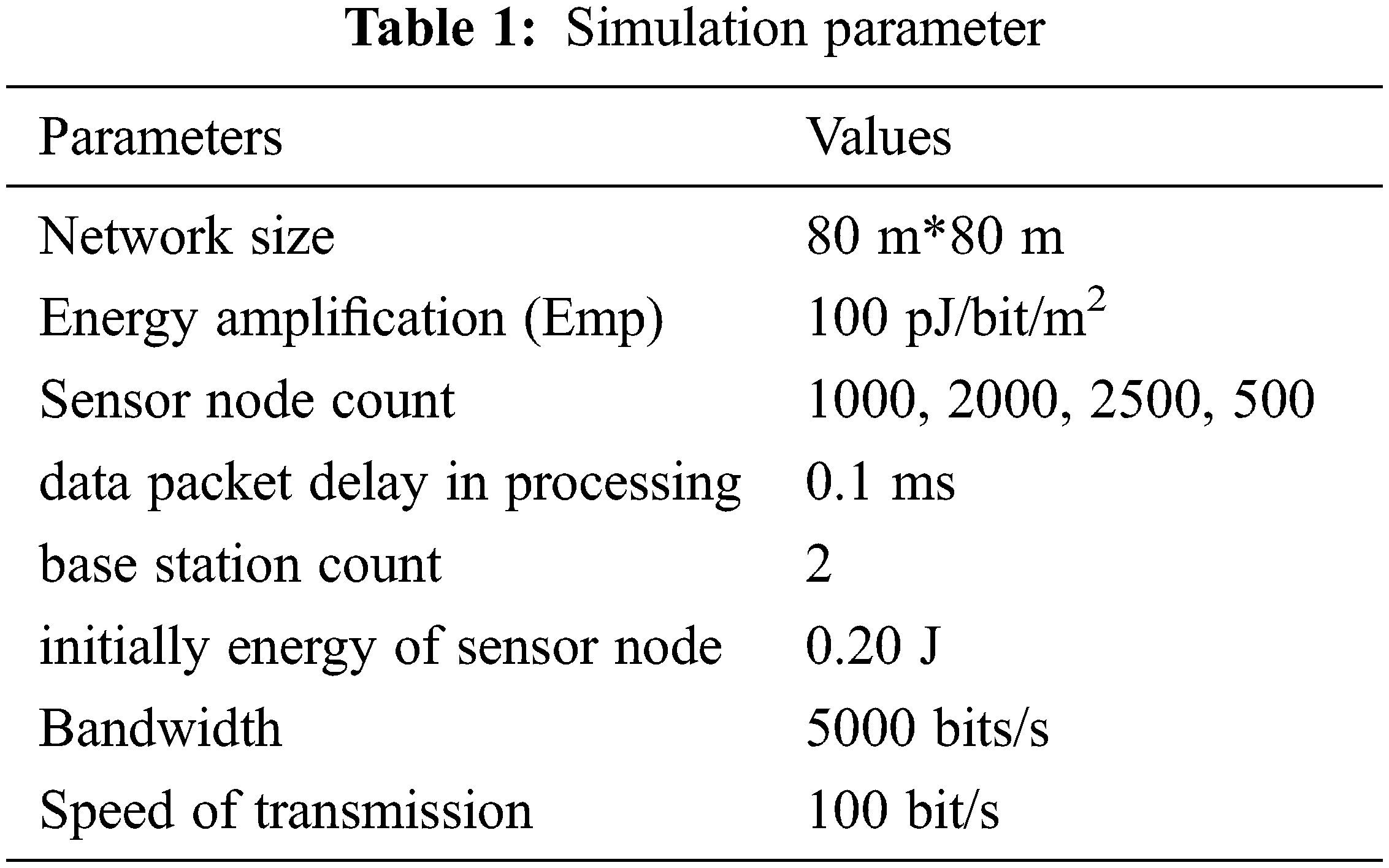
Wireless sensor networks have a lot of applications, and their popularity is growing despite challenges like storing, transmission range, processing capability, and power consumption. The main problem is that it has a shorter lifespan due to higher energy usage. This problem can be solved by load balance, which consumes less energy. In this part, analyze LCLBM-CEOMS utilizing system parameters with Operating System- Windows 10-OS and a 64-bit quad-core CPU and NVIDIA CUDA (2GB) and RAM (16 GB). The sensor simulator [27] is used for simulation, while LCLBM-CEOMS is written in the C# programming language. More information on the system parameters can be found in Tab. 1.
Given the limited quantity of energy available to each sensor, energy efficiency is constantly utilized as a requirement for network longevity. As a result, the network lifespan analysis is done using different nodes in this part. For 500, 1000, 2000 and 2500 nodes, lifetime comparisons are shown in Figs. 2–4. In this example, it is noticed that the network lifetime of an existing model is slightly lower than a current design. As a result, it can be concluded that the suggested model reduces energy usage and thus improves

Figure 2: 500 nodes network lifetime

Figure 3: Network’s lifetime for 1000 nodes

Figure 4: Network’s lifetime for 2000 nodes
The sensor nodes have a certain amount of energy. Thus power consumption is the main factor in evaluating a load balancing system. As a result, energy usage becomes a critical metric. By adjusting the sensor number of nodes to 500, 1000, 2000 and 2500, the present model is compared to the suggested model LCLBM-CEOMS.
Fig. 5 shows the energy consumption of the proposed method LCLBM-CEOMS. Thus, the proposed method increases its energy consumption.

Figure 5: Energy consumption
It’s another LCLBM-CEMOS performance parameter; in balancing load, power is an essential parameter since it must be distributed effectively, and the way of managing load with power may be used with a more significant number of active nodes or nodes that are doing data transfer. As a result, active nodes in large numbers imply that the node is under fewer loads, and energy can be saved. In addition, the network’s lifetime is extended; a graphical comparison is shown in Fig. 6.

Figure 6: Active nodes
This study suggests LCLBM-CEOMS balances network traffic on the Internet of Things. A specialized network is created for an optimal load balancing environment, and then the loads are then balanced with the help of the ACH to improve the network’s lifespan. The LCLBM-CEOMS is compared to the old model on key performance measures like network lifespan, energy usage, length, and overhead. To minimize the randomization of cluster head selection, the suggested approach first established the density function of energy by evaluating the remaining energy rates and neighborhood density radius of nodes. Secondly, the performance of the motion function was created using parameters from the mobile sink’s motion parameters, efficiently balancing bandwidth requirements and reducing data latency.
Furthermore, to change the cluster head selection threshold variables, the adaptive adjustment function associated with the mortality node was presented, which extended the life of the network. The density function of energy, function of motion performance, and function of adaptive adjustment collaborated to improve cluster head self-adaptability, equalize network capacity, minimize data latency, and extend network life span. The suggested model outperforms the previous model in energy consumption for 500 to 2500 nodes, consuming 17.60%, 23.52%, 11.87% and 15.26% less energy. In future work, the optimization-based algorithms can be used in energy-saving targets.
Acknowledgement: The authors express their gratitude to Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R323), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Funding Statement: Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R323), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest: The authors declare that there is no conflict of interests regarding the publication of the paper.
1. W. Qian, K. Bai, L. Zhou, Z. Hu, Y. Jin et al., “A cluster-based energy optimization algorithm in wireless sensor networks with mobile sink,” Sensors, vol. 21, no. 7, pp. 2523–2533, 2021. [Google Scholar]
2. M. B. Poolan, “Lifetime centric load balancing mechanism in wireless sensor network based IoT environment,” International Journal of Electrical & Computer Engineering, vol. 1, no. 3, pp. 2088–8708, 2021. [Google Scholar]
3. J. Wang, Z. Zhang, F. Xia, W. Yuan and S. Lee, “An energy efficient stable election-based routing algorithm for wireless sensor networks,” Sensors, vol. 13, no. 3, pp. 14301–14320, 2013. [Google Scholar]
4. H. Cheng, L. Tao and X. Zhang, “A fast and efficient broadcast protocol with a mobile sink node in asynchronous wireless sensor networks,” IEEE Access, vol. 7, no. 12, pp. 92813–92824, 2019. [Google Scholar]
5. A. Zahhad, M. Ahmed, S. M. Sabor and N. Sasaki, “Mobile sink based adaptive immune energy efficient clustering protocol for improving the lifetime and stability period of wireless sensor networks,” IEEE Sensor, vol. 15, no. 4, pp. 4576–4586, 2015. [Google Scholar]
6. W. R. Heinzelman, A. Chandrakasan and H. Balakrishnan, “Energy efficient communication protocol for wireless microsensor networks,” in Proc. 33rd Annual Hawaii Int. Conf. on System Sciences, Maui, USA, pp. 1–10, 2000. [Google Scholar]
7. X. Jia, J. Ning, X. Lou, T. Peng, Q. Zhou et al., “Improvement of LEACH protocol for WSN,” in Proc. 9th Int. Conf. on Fuzzy Systems and Knowledge Discovery, Chongqing, China, pp. 2174–2177, 2012. [Google Scholar]
8. O. Younis and S. Fahmy, “A hybrid, energy efficient, distributed clustering approach for ad hoc sensor networks,” IEEE Transactions on Mobile Computing, vol. 3, no. 4, pp. 366–379, 2004. [Google Scholar]
9. G. Smaragdakis, I. Matta and A. Bestavros, A stable election protocol for clustered heterogeneous wireless sensor networks. Boston, USA: Boston University Computer Science Department, pp. 1–12, 2004. [Google Scholar]
10. Y. Liao, H. Qi and W. Li, “Load balanced clustering algorithm with distributed self-organization for wireless sensor networks,” IEEE Sensors Journal, vol. 13, no. 5, pp. 1498–1506, 2013. [Google Scholar]
11. F. Wang, S. Wu, K. Wang and X. Hu, “Energy efficient clustering using correlation and random update based on data change rate for wireless sensor networks,” IEEE Sensors Journal, vol. 16, no. 13, pp. 5471–5480, 2016. [Google Scholar]
12. S. Kumar, “Compartmental modeling of opportunistic signals for energy efficient optimal clustering in WSN,” IEEE Communications Letters, vol. 22, no. 1, pp. 173–176, 2018. [Google Scholar]
13. M. M. Alam, M. A. Razzaque, M. M. Rashid and C. S. Hong, “Energy aware QoS provisioning for wireless sensor networks: Analysis and protocol,” Journal of Communications and Networks, vol. 11, no. 4, pp. 390–405, 2009. [Google Scholar]
14. X. Liu and P. Zhang, “Data drainage: A novel load balancing strategy for wireless sensor networks,” IEEE Communications Letters, vol. 22, no. 1, pp. 125–128, 2018. [Google Scholar]
15. S. Hu and G. Li, “Fault tolerant clustering topology evolution mechanism of wireless sensor networks,” IEEE Access, vol. 6, no. 3, pp. 28085–28096, 2018. [Google Scholar]
16. M. Azharuddin and P. K. Jana, “PSO based approach for energy-efficient and energy balanced routing and clustering in wireless sensor networks,” Soft Computing, vol. 21, no. 22, pp. 6825–6839, 2017. [Google Scholar]
17. S. Kumar, A. Verma, P. R. Gautam, A. Dayal and A. Kumar, “The load balancing of optimizing leach clustering algorithm with mobile sink and rendezvous nodes,” in Proc. 5th IEEE Uttar Pradesh Section Int. Conf. on Electrical, Electronics and Computer Engineering (UPCON), Gorakhpur, India, pp. 1–6, 2018. [Google Scholar]
18. X. Fu and X. He, “Energy balanced data collection with path-constrained mobile sink in wireless sensor networks,” International Journal of Electronics and Communications, vol. 127, no. 3, pp. 153504, 2020. [Google Scholar]
19. R. Zhang, J. Pan, J. Liu and D. Xie, “A hybrid approach using mobile element and hierarchical clustering for data collection in WSNs,” in Proc. IEEE Wireless Communications and Networking Conf. (WCNC), New Orleans, LA, USA, pp. 9–12, 2015. [Google Scholar]
20. C. Zhu, S. Wu, G. Han, L. Shu and H. Wu, “A tree cluster-based data-gathering algorithm for industrial WSNs with a mobile sink,” IEEE Access, vol. 3, no. 2, pp. 381–396, 2015. [Google Scholar]
21. P. Kuila and P. K. Jana, “Energy efficient clustering and routing algorithms for wireless sensor networks: Particle swarm optimization approach,” Engineering Applications of Artificial Intelligence, vol. 33, no. 3, pp. 127–140, 2014. [Google Scholar]
22. M. Azharuddin and P. K. Jana, “PSO based approach for energy-efficient and energy-balanced routing and clustering in wireless sensor networks,” Soft Computing, vol. 21, no. 22, pp. 6825–6839, 2017. [Google Scholar]
23. R. S. Y. Elhabyan and M. C. E. Yagoup, “Two tier particle swarm optimization protocol for clustering and routing in the wireless sensor network,” Applications, vol. 52, no. 10, pp. 116–128, 2015. [Google Scholar]
24. S. K. Gupta and P. K. Jana, “Energy efficient clustering and routing algorithms for wireless sensor networks: GA based approach,” Wireless Personal Communications, vol. 83, no. 3, pp. 2403–2423, 2015. [Google Scholar]
25. T. Amgoth and P. K. Jana, “An energy aware routing algorithm for wireless sensor networks,” Computers & Electrical Engineering, vol. 41, no. 8, pp. 357–367, 2015. [Google Scholar]
26. B. Baranidharan and B. Santhi, “DUCF: Distributed load balancing unequal clustering in wireless sensor networks using Fuzzy approach,” Applied Soft Computing, vol. 40, no. 7, pp. 495–506, 2016. [Google Scholar]
27. A. A. Ari, B. O. Yenke, N. Labraoui and D. Irepran, “A power efficient cluster based routing algorithm for wireless sensor networks: Honeybees swarm intelligence based approach,” Journal of Network and Computer Applications, vol. 69, no. 6, pp. 77–97, 2016. [Google Scholar]
28. N. Sabor, M. Abozahhad, S. Sasaki and S. M. Ahmed, “An unequal multi hop balanced immune clustering protocol for wireless sensor networks,” Applied Soft Computing, vol. 43, no. 4, pp. 372–389, 2021. [Google Scholar]
29. K. Thangaramya, K. Kulothungan, R. Logambigai, M. Selvi, S. Ganapathy et al., “Energy aware cluster and neuro-fuzzy based routing algorithm for wireless sensor networks in IoT,” Computer Networks, vol. 151, no. 5, pp. 211–223, 2019. [Google Scholar]
30. P. Jiang, Y. Feng, F. Wu, S. Yu and H. Yu, “Dynamic layered dual cluster heads routing algorithm based on krill herd optimization in UWSNs,” Sensors, vol. 16, no. 9, pp. 1379, 2016. [Google Scholar]
31. M. Abdel Basset, D. El-Shahat, K. Deb and M. Abouhawwash, “Energy-aware whale optimization algorithm for real-time task scheduling in multiprocessor systems,” Applied Soft Computing, vol. 93, no. 3, pp. 106349, 2020. [Google Scholar]
32. M. Abdel Basset, R. Mohamed, M. Abouhawwash, K. Ripon Chakrabortty and J. Michael, “EA-MSCA: An effective energy-aware multi-objective modified sine-cosine algorithm for real-time task scheduling in multiprocessor systems: Methods and analysis,” Expert Systems with Applications, vol. 173, no. 4, pp. 114699, 2021. [Google Scholar]
33. M. Abdel Basset, R. Mohamed and M. Abouhawwash, “Balanced multi-objective optimization algorithm using improvement based reference points approach,” Swarm and Evolutionary Computation, vol. 60, no. 3, pp. 100791, 2021. [Google Scholar]
34. H. Seada, M. Abouhawwash and K. Deb, “Multiphase balance of diversity and convergence in multiobjective optimization,” IEEE Transactions on Evolutionary Computation, vol. 23, no. 3, pp. 503–513, 2019. [Google Scholar]
35. M. Abouhawwash and A. M. Alessio, “Multi objective evolutionary algorithm for PET imagereconstruction: Concept,” IEEE Transactions on Medical Imaging, vol. 40, no. 8, pp. 2142–2151, 2021. [Google Scholar]
36. M. Abouhawwash, “Hybrid evolutionary multi objective optimization algorithm for helping multi-criterion decision makers,” International Journal of Management Science and Engineering Management, vol. 16, no. 2, pp. 94–106, 2021. [Google Scholar]
37. M. Abouhawwash and K. Deb, “Reference point based evolutionary multi-objective optimization algorithms with convergence properties using KKTPM and ASF metrics,” Journal of Heuristics, vol. 27, no. 12, pp. 575–614, 2021. [Google Scholar]
38. M. Abouhawwash, K. Deb and A. Alessio, “Exploration of multi-objective optimization with genetic algorithms for PET image reconstruction,” Journal of Nuclear Medicine, vol. 61, no. 4, pp. 572, 2020. [Google Scholar]
39. M. Abdel Basset, N. Moustafa, R. Mohamed, O. Elkomy and M. Abouhawwash, “Multi-objective task scheduling approach for fog computing,” IEEE Access, vol. 9, no. 3, pp. 126988–127009, 2021. [Google Scholar]
40. M. Abouhawwash, “Hybrid evolutionary multi-objective optimization algorithm for helping multi criterion decision makers,” International Journal of Management Science and Engineering Management, Taylor&Francis, vol. 16, no. 2, pp. 94–106, 2021. [Google Scholar]
41. S. T. Suganthi, A. Vinayagam, V. Veerasamy, A. Deepa, M. Abouhawwash et al., “Detection and classification of multiple power quality disturbances in microgrid network using probabilistic based intelligent classifier,” Sustainable Energy Technologies and Assessments, vol. 47, no. 4, pp. 101470, 2021. [Google Scholar]
42. N. Mittal, H. Singh, V. Mittal, S. Mahajan, A. K. Pandit et al., “Optimization of cognitive radio system using self-learning salp swarm algorithm,” Computers, Materials & Continua, vol. 70, no. 2, pp. 3821–3835, 2022. [Google Scholar]
43. Z. B. Zhou, C. Du, L. Shu, G. Hancke, J. Niu et al., “An energy balanced heuristic for mobile sink scheduling in hybrid WSNs,” IEEE Transactions on Industrial Informatics, vol. 12, no. 3, pp. 28–40, 2015. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |