DOI:10.32604/iasc.2023.030054

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2023.030054 |  |
| Article |
Opportunistic Routing with Multi-Channel Cooperative Neighbour Discovery
1AVS College of Technology, Salem, 636106, India
2Sona College of Technology, Salem, 636005, India
*Corresponding Author: S. Sathish Kumar. Email: steel.ssk@gmail.com
Received: 17 March 2022; Accepted: 19 April 2022
Abstract: Due to the scattered nature of the network, data transmission in a distributed Mobile Ad-hoc Network (MANET) consumes more energy resources (ER) than in a centralized network, resulting in a shorter network lifespan (NL). As a result, we build an Enhanced Opportunistic Routing (EORP) protocol architecture in order to address the issues raised before. This proposed routing protocol goal is to manage the routing cost by employing power, load, and delay to manage the routing energy consumption based on the flooding of control packets from the target node. According to the goal of the proposed protocol technique, it is possible to manage the routing cost by applying power, load, and delay. The proposed technique also manage the routing energy consumption based on the flooding of control packets from the destination node in order to reduce the routing cost. Control packet exchange between the target and all the nodes, on the other hand, is capable of having an influence on the overall efficiency of the system. The EORP protocol and the Multi-channel Cooperative Neighbour Discovery (MCCND) protocol have been designed to detect the cooperative adjacent nodes for each node in the routing route as part of the routing path discovery process, which occurs during control packet transmission. While control packet transmission is taking place during the routing path discovery process, the EORP protocol and the Multi-channel Cooperative Neighbour Discovery (MCCND) protocol have been designed to detect the cooperative adjacent nodes for each node in the routing. Also included is a simulation of these protocols in order to evaluate their performance across a wide range of packet speeds using Constant Bit Rate (CBR). When the packet rate of the CBR is 20 packets per second, the results reveal that the EORP-MCCND is 0.6 s quicker than the state-of-the-art protocols, according to the findings. Assuming that the CBR packet rate is 20 packets per second, the EORP-MCCND achieves 0.6 s of End 2 End Delay, 0.05 s of Routing Overhead Delay, 120 s of Network Lifetime, and 20 J of Energy Consumption efficiency, which is much better than that of the state-of-the-art protocols.
Keywords: Macro-addressable network; power- and load-aware routing; deterministic and opportunistic routing; gradient routing; multi-channel cooperative neighbor discovery
Among the types of wireless networks, MANETs, which are composed of a large number of mobile nodes that communicate with one another using wireless channels. At the same time, all mobile nodes act as both routers and hosts for the network, which makes them very versatile. It also makes use of peer-to-peer information sharing, which is beneficial since it occurs across several hops. The primary characteristics of these networks are the bandwidth and energy limitations imposed by them and their cooperative nature and complicated structure. There are a variety of applications for these networks, including tactical communication, defense, disaster management, traffic monitoring, and a variety of additional uses [1–4]. However, their dynamic nature [5] makes these networks more susceptible to a broader spectrum of assaults than other networks. When using multihop transmission, it is also common for nodes to be constrained by the amount of energy available to them. Each node will depend on the other nodes to deliver data packets, which will be disseminated across the network [6–8], among other Existing works. The dependability, scalability, flexibility, simplicity of design and execution, sensitivity to failure, and complexity of topology management are only a few of the factors that are taken into account in such routing protocols. Whenever a new route between the origin and destination nodes is discovered, all nodes in a MANET can dynamically connect to those routes in whichever the packets can be fit, regardless of where they are positioned with respect to the origin’s nodes. In most cases, this strategy is known as multipath routing in these types of circumstances. A backup route is often picked from several alternative options when the primary connection fails during data transfer for a variety of reasons. Because of the proposed routing protocol, fault tolerance and route recovery have both been greatly enhanced in recent years. As an alternative, this approach may be used to balance packet flow between several fragmented channels that have been pooled together for convenience. Routes that are disjointed, on the other hand, give the greatest number of aggregated resources, as well as the greatest degree of fault tolerance, are no links between nodes in this arrangement. When it comes to performance, multipath outperforms a single path in the same way [9,10] reduces the lifetime of the node [11] and potentially causes the node to be destroyed. When compared to the AODV protocol [12], the DSR protocol is used by the vast majority of routing strategies [13,14] since it is a small-sized network routing strategy. Comparing DSR to AODV, the efficiency of DSR is higher, making it more suitable for small-sized networks [15]. It was determined which route to take based on how much residual power was there as well as the amount of total transfer energy that was consumed, according to the DSR-ED. Regular electricity, hot electricity, and dangerous electricity were all separated from the rest of the grid’s capacity. Normal Power Consumption is classified based on the following conditions. While this has been accomplished, the node’s overall life has been significantly reduced. So Ali and colleagues [16] created an on-demand Power and Load-Aware Dynamic Source Routing (PLA-DSR) protocol that decreases the amount of power used by a node as well as reduces the number of route discovery activities that must be conducted. To get numerous node-disjoint optimal routes depending on the amount of power and load that each node could handle, a new cost factor was devised for this protocol to obtain several node-disjoint optimum routes. When using dynamic MANET settings, the deterministic routing technique (DSR) was shown to have the highest influence on the reliability of unicast transmission and control overhead, while also having the smallest impact on control overhead. As a result of its observations and conclusions, this article has produced the following significant contributions: EORP protocol communicate to the neighbouring nodes with lesser energy consumption. As part of the routing route discovery process, the EORP-MCCND protocol is used to identify cooperative nearby routers for all of the routers in the routing route while the control packets are being delivered from the source to the destination. This decreased power usage results in an increase in the lifespan of each node during routing, resulting in a reduction in power consumption. The following is the outline for the next parts of the article: a. Introduction Section 2 of this publication contains a thorough discussion of previously completed research in the domain of PLA-based multipath routing in MANET, which are the Existing works. Section 3 begins with a short overview of the approach used in the EORP protocol and carry out the EORP-MCCND protocol in more detail. Section 4 of this publication provides evidence of the effectiveness of various tactics. This section provides a summary of the whole study as well as a discussion of the study’s possible future scope.
Routing Protocol [17] was developed to identify pathways that are both geographically isolated and maximally fragmented at the same time, and this was done to find paths that are both geographically isolated and maximally disjointed. By broadcasting individual packets across a wide range of geographically separated channels, it was feasible to reduce the danger of collisions to the bare minimum. There is, on the other hand, a significant degree of discovering overhead. To distribute load among a large number of distinct routes, the Fibonacci Multipath Load Balancing (FMLB) protocol [18] was designed. This protocol identifies routes that have a limited number of hops and assigns Fibonacci weights to packet exchanges based on the number of hops for each route that is picked in the selection process. The protocol is written in the C++ programming language. However, the number of nodes that are next to one another is the only factor that determines delay rate. Lal and colleagues [19] proposed a routing strategy known as Node-Disjoint Multi-Route (NDMP) for determining the principal path between a data source and a data destination for data transmission. The following is the description of the NDMP routing method: In this NDMP, fraudulent acts were prevented from taking place on the network after the route was hacked because the information at intermediate nodes was erased before backup pathways were identified in this NDMP. The Routing Overhead (RO), on the other hand, was astronomically expensive. It has been proposed [20] that a dispersed strategy be used to seek discontinuous route in Wireless Sensor Networks (WSNs) to overcome the difficulty of k-disjoint path discovery in WSNs. Nodes may broadcast dumpy packets between one-hop nearby nodes, however, at this moment there are no present message formats that may be employed by the network. Despite this, the average EC of this protocol is rather high when compared to other protocols in the same class. According to [21], a twin node-disjoint path routing strategy may be used to improve network reliability and resilience by simultaneously creating all potential node-disjoint routes. This strategy may be used to improve network reliability and resilience by increasing network reliability and resilience. As a result of the enhanced node mobility, a larger than normalized routing burden was observed; nonetheless, the normalized routing load was found to be minimal. Arora [22] suggested a multipath routing approach that was aware of dynamic communication energy and was based on dynamic communication energy for the goal of constructing node-disjoint routes, and this strategy was successful. An adaptive selection of adequate transfer power has been developed to prevent the generation of the greatest amount of intrusion and unnecessary data as a result of control message transmission. A residual power-based, trustworthy multicast routing strategy [23] has been developed that provides a multicast backbone based on node awareness and honest rounding to enhance network strength, and this technique has been used to increase network strength [24]. It was also mentioned that the trustworthy route measure would be used to choose the most effective method of data transmission. The fact remains that when mobility is variable, the network’s efficiency is not taken into consideration. A protocol known as the Adhoc On-Demand Multipath Distance Vector (PE-AOMDV) [25] has been developed that makes use of a new threshold to limit the number of communication channels that may flow through a node at the same time. The threshold is checked for each new request to determine whether or not the maximum number of accessible links has been reached. The rate of packet loss, on the other hand, did not show any improvement over the previous year.
3 Methodology of Communication Protocol
This section provides a high-level description of the EORP and EORP-MCCND protocols, with a focus on their implementation details. The prior PLA-DSR routing technique, for example, was a deterministic routing strategy that often failed to locate adequate pathways in dynamic MANETs with high node mobility, which was a significant drawback. It follows as a result of this that the EORP protocol is created, which makes use of gradient forwarding to decrease control overhead while maintaining high levels of transmission dependability. It uses power consumption, load consumption, and delay as cost indicators to choose the most cost-effective routing route. The source code in this protocol, in contrast to prior protocols, does not simply transfer data; rather, the destination node selects the most appropriate path for data routing. Furthermore, EORP contains the MCCND protocol. The EORP protocol suite also includes the MCCND protocol. As seen in Fig. 1, the overall procedure of the proposed method that has been provided may be seen.
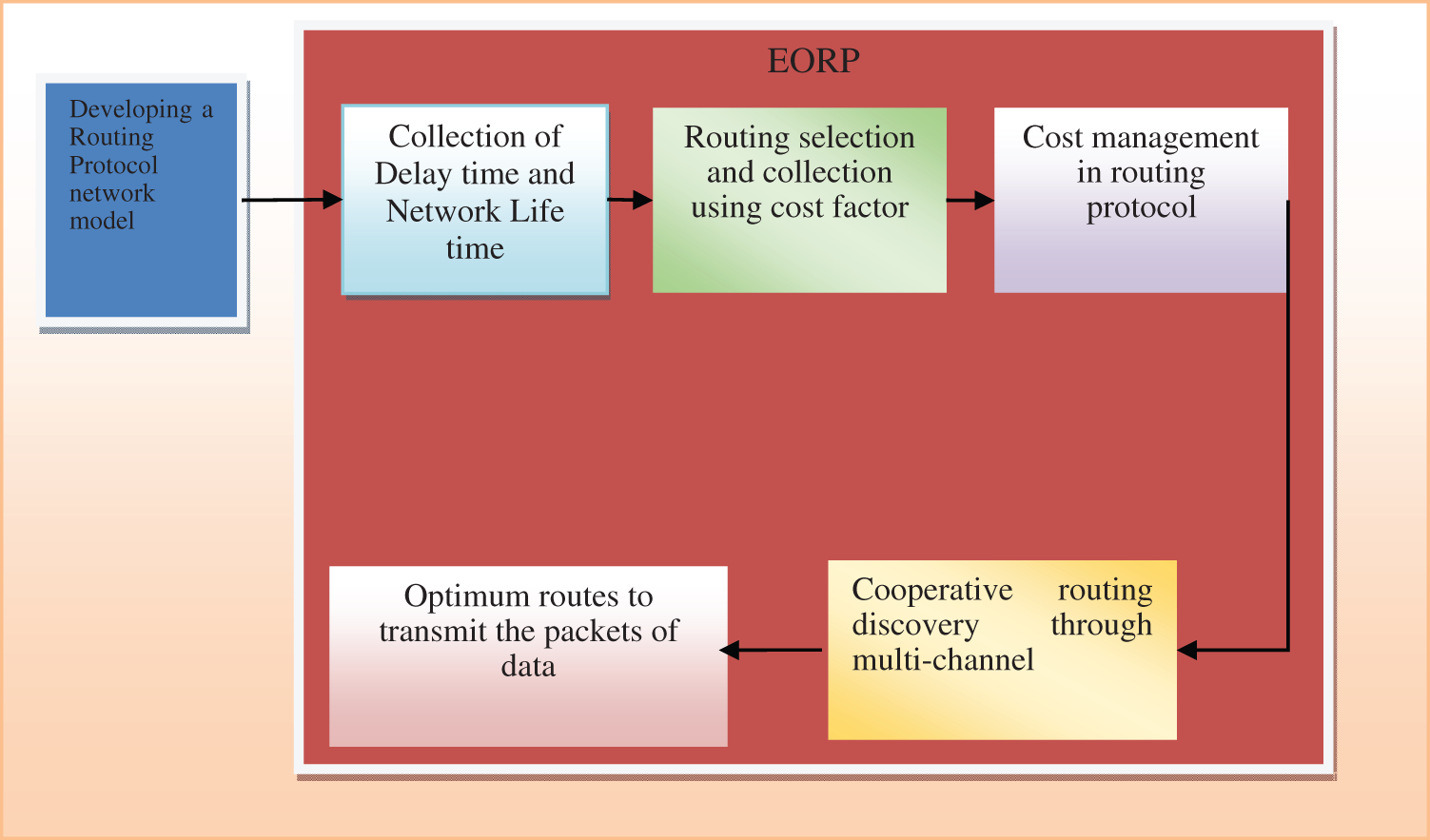
Figure 1: Proposed MANET protocol block diagram
A cost factor was calculated for each node that participated in the path-finding activities and this energy consumption was based on the estimated lifespan of the node in question. This criterion is used to discover which routes are the most productive. The selection of numerous optimal routes from the point of origin to the point of endpoint must be done in such a way that the pathways are trustworthy and reduce the greatest level of mistakes. Origins often have other pathways leading to their destinations, which decreases the likelihood of path-finding activities being initiated and, as a result, reduces the amount of power used by path-finding operations.
When information has to be sent to a particular destination and the origin does not have a cached route to that destination, the on-demand routing mechanism must initiate the path-finding process to discover a route to that destination. As a result, the multipath routing protocol with on-demand routing reduces the amount of power consumed as well as the number of path finding task allocation performed because, in many cases, the origin includes an alternate optimal route to the desired destination, resulting in lower power consumption and fewer path finding task allocation performed in the network.
As an alternative to the development of many routes between source and destination routers, the passage of diverse routes via a limited number of classical routers is also an option. While data flow may be partitioned along such routes, the performance of ordinary nodes along such routes would probably suffer a quick degradation because their data load is often larger than that of the other nodes along the route. In turn, this allows for the beginning of a large number of path-finding activities, as well as the use of extra resources. As network dynamics get more complicated, the chance of a route collapse increases in lockstep with it. Consequently, due to the nature of their mobility behaviour, these ordinary nodes are capable of leaving their 1-hop local transfer zone at any moment. The routing architecture is seen in Fig. 1. In this scenario, the node disjoints between the two optimal routes which has no common nodes. This will prevent the occurrence of the delay in the routing protocol. As a result, the system is unable to divide the work and may save even more energy as a result.
This PLA-DSR protocol, which is dependent on the DSR protocol, incorporates the reactive routing technique into its routing strategy as a component of its overall routing approach. This is performed by transmitting a REQ message to its 1-hop neighbor, which in turn initiates the path-finding procedure on its behalf. Transitional nodes then retransmit the RREQ message with the acknowledgement that the destination would accept it. When the target sends this message, it uses the same route that the source used to deliver the RREQ message. It is referred to as a Route Reply in the industry.
A deterministic routing protocol is a kind of alternative routing protocol in which packets are routed via an existing path to their eventual destination, as opposed to a nondeterministic routing mechanism. Given that it has not collapsed, it can supply dependable and effective data transmission throughout the duration of time that the network has been operational. Even though the route quality in MANET is not continuous and changes often over time, this has the impact of diminishing routing efficiency. Furthermore, when route updates become recurrent in a MANET as a consequence of increased node mobility, the network’s performance may be adversely impacted by the high control overhead associated with the route changes. In the case of MANETs, the development of sophisticated algorithms is necessary for the building and updating of numerous pathways, which involves a high level of processing complexity.
3.2 Improved Opportunistic Routing with Power and Load Aware (EORP) Protocol
According to the findings of this research, PLA should be reliant on opportunistic routing employing gradient forwarding protocol to prevent the problems associated with deterministic routing. The idea of a destination-side routing option is also incorporated in this protocol, which indicates that the routing decision is made by the target nodes themselves. Because it is intended for End-to-End (E2E) packet transmission, this opportunistic routing solution does not rely on a planned routing for End-to-End (E2E) packet transmission. The data is only sent by the source, and the destination decides whether or not to pass it on to the recipient. This is the situation with the new EORP protocol, which was just released. Route variety is used because nodes are intended to send data via a wide number of various routes, resulting in better dependability as a result of the greater amount of dependability. Predictive Modeling of Delay and Network Lifetime. As a result of this, the need of selecting source nodes to increase the likelihood of receiving opportunistic early packets is brought to routing queue. In part, this is due to the large number of accessible source nodes, which reduces the amount of time that the node must spend waiting for a packet to arrive from the source. Taking into consideration several sources, on the other hand, may increase the likelihood that a transfer may fail due to the unreliability of the pathways between the sources and the destination. A threshold for path quality is applied to the path in issue to establish whether or not the route is excellent. Using the highest route quality, the node that has the greatest possibility of properly initiating the transfer with no mistakes has the best chance of succeeding. By choosing the most efficient path, it is expected that the smallest number of transfers will be completed, resulting in the shortest estimated packet delay as well as the lowest amount of energy being used. Because of untrustworthy routes, the flooding data latency of all nodes is a completely arbitrary parameter that may be altered at any moment without affecting the other nodes. When nodes in a distributed system communicate with one another, a method for generating the delay distribution is employed to guide their decision-making process. Those nodes that have a hop count higher than or equal to k are represented as level k nodes in the network. Data packet delays (DPD) are represented by a collection of time ph(i) for level-h nodes during a busy period, where the probability of receiving the data at the time t of the busy period i is represented by qi+1 (k) for the busy period i. Because the origin is continually active, it is conceivable that data that has been delayed will be received by the origin at the beginning of the transmission. Following that, the level h (i) node computes its DPD by comparing it to the DPD of the level h(i)node that is directly above it in the hierarchical order. It is possible to calculate the probability that this level-h + 1 node would be inundated with data during its kth busy period for a given value of DPD of this level-h + 1 node, and its level-h + 1 node with busy periods th (i+1)(k) for each value of k using the following formula:
As seen in this example, the percentage of level-h + 1 node’s busy time that occurs between the times t (h + 1) and t (h) is denoted by n ik (k). The probability that data that enters the level-h node during its ith busy period is received for the first time at the level-h + 1 node during its kth time is given by the equation Ph (i+1) q(1 − q), where I is the number of times data enters the level-h node during its ith busy period and q is the number of times data is received at the level-h + 1 node during its kth time is given by the equation p h (n ik). This means that every single node may compute their DPD be their threshold latency and spread it among their previous hop nodes as a result of making this judgement. When a level-h node X gets a packet during its ith busy period with a delay of th(i). Assuming that the transmission from point A to point B is commenced, the following is the calculation for the Expected Packet Delay (EPD) from point A to point B.:
Eq. (2) defines the variable n ik as the number of Y’s busy periods that occurred between t (h + 1) and t (h) during the period t (h) I, where n it is the number of busy periods that occurred between t (h + 1) and t (h) during the (k). It is necessary to collect and compare the EPD with Y’s Dp to determine if broadcasting or distribution through the power and load-aware optimal nodes is more relevant to make a decision. If the difference between the two is less than or equal to p, it is defined as EPD D p the likelihood that Y nodes before the overlap occurred. When the difference between the two numbers is bigger than p, the probability is defined as EPD D p, where p is the probability threshold. As a consequence, the significance of this package is considerable. It is safe to presume that Y has already accepted this knowledge before learning about the new information as long as EPD is bigger than the likelihood of Dp. Consequently, this information has been considered to be redundant and will not be sent to the next hop Y on the network as a consequence of this determination. Recall that the variable p refers to a control variable that is utilized to maintain a balance between the system’s latency and its power usage. With increasing p, the chance that a packet will be designated as being critical to the operation of the network grows, as shown in Fig. 1. A considerable proportion of packets are delivered opportunistically as a result of the fact that failure is well handled, improving the possibility of getting a packet as soon as feasible. The number of transfers made accessible to persons who use a lot of power is also optimized, which is a considerable benefit in this case. The amount of packets that are delivered by employing power-suboptimal paths to maximize energy efficiency and delay while simultaneously reducing cost is reduced whenever the value of p is decreased. As an example, the Expected Lifetime (EL) of h at time t may be computed as follows:
The anticipated lifespan of h at a given time t is predicted by the Eqs. (3) and (4), which are denoted by the symbol Lt h (t). The symbols E h (t) and ETR h (t) are used to express them in more specific terms. In the following example, the transfer energy required by the symbol P (h, p) in order to transmit a data packet via route T is represented by the symbol P (h, p) (T), while the transfer energy required by the symbol P (h, p) to send a data packet through route T is denoted by the symbol P (h, p) (T). time Amount of time between the current period and final data entry is expressed as a gap; k is the time interval (in seconds) required to calculate the rate, and pkt is the percentage of the current period that has not yet been recorded as data. In computing packet size, the length of a packet is used as the unit of measurement. The rate of current flow prediction refers to the expected rate of current flow in a given situation.
B. Improved Cost and Energy factor Estimation with path Tracking
Energy Packet Delay (F(Ch(t))) is represented by
In order to identify the most cost-effective routes from a variety of available routes that would link a certain origin to the desired destination, this cost factor must be determined. It is becoming more optimum to choose a specific route as the cost associated with that route decreases. When computing the cost factor for a given node. Take, for instance, the route P I which at time t links the origin (S) to the required destination (D) through transitional nodes (n 1-m 2-⋅⋅⋅-n (m − 1), n m), as an example. As a consequence,
C. Path-Quality-based Backoff
It is becoming more optimum to choose a specific route as the cost associated with that route decreases. When computing the cost factor for a given node, the route P I which at time t links the origin (S) to the required destination (D) through transitional nodes (n 1-m 2-⋅⋅⋅-n (m − 1), n m), as an example. As a consequence:
In this way, it ensures that t back off does not become negative and does not go outside of the permissible backoff range. Because of the employment of this component, the danger of a failure is reduced in situations when two or more nodes have similar route quality, hence minimizing the possibility of a failure This results in greater energy efficiency and reduced flooding delay while simultaneously cutting the cost of transmission along the PLA’s best collision-free pathways, as well as decreased flooding delay and higher flooding efficiency.
D. Path Discovery and Routing Cost Management
When constructing the EORP, it is required to include gradient forwarding as well as the newly added routing cost F(C h (t)). When dealing with cost data, this protocol is most often used to inundate it with control packets delivered by the target regularly. The following are some of the most essential components of this cost management strategy, which are given in alphabetical order: When dealing with a high number of diverse sources, a special flooding packet from the target is employed, which is described in detail below. It is only possible to flood a packet flooding zone that is confined to the hop gap between an origin and a destination, and packet flooding zone that is constrained to the hop gap between an origin and a destination if the packet flooding zone is confined to the hop gap between an origin and a destination if the packet flooding zone is confined to the hop gap between an origin and a destination. It is feasible to maintain charges consistent from node to node. It is possible to achieve a regularisation of the cost range at each node by keeping the costs associated with the most effective route constant at each node. PUM (Path Update Message) is an acronym that stands for Path Update Message and is used to refer to a path update message in a path update message. At any time throughout the transmission of this control packet, a route may be changed to suit the situation. It is followed immediately by the transmission of three further control packets. Each of their message structures is shown in Fig. 2 at the relevant positions across the layout. What’s more, no matter how much information is provided in a product information manual (PUM) issued by an originator, it does not include any information concerning fees that must be paid to the target. In this structure, all of these components have been set to their default value of null. Their matching IDs are referred to as the origin ID (Src) and the destination ID (Dest) (Dst). The EPD from the source is sometimes referred to as the arbitrary Sequence Number (PUM-SN), which is an abbreviation (EPD-from-Src). It is possible to identify whether or not PUM has been identified in your system by using the PUM-SN tool. In response to the receipt of a PUM from the source, a clock is started in motion, and a PIM from the destination is ready to be received by its counterpart at the destination. If a PIM does not get the origin before the deadline, it is conceivable that it will miss the origin. After that, a new SN will be created and broadcast to the other PUM, and the operation will be done once again. Whenever a PUM is broadcast to a receiving node, it is critical to verify the PUM-SN at the outset of an operation before continuing with the operation. More than a decade after its introduction, PUM will be removed from the environment and disposed of at a landfill. As a result of this collection and modification of data, the receiver sets the Hop-from-Src parameter on the incoming data stream to one, which causes the PUM-SN to be collected and changed. As a consequence of the t backoff approach, which is discussed below, it is conceivable that the PUM will be sent even if it was not meant for the designated receiver.
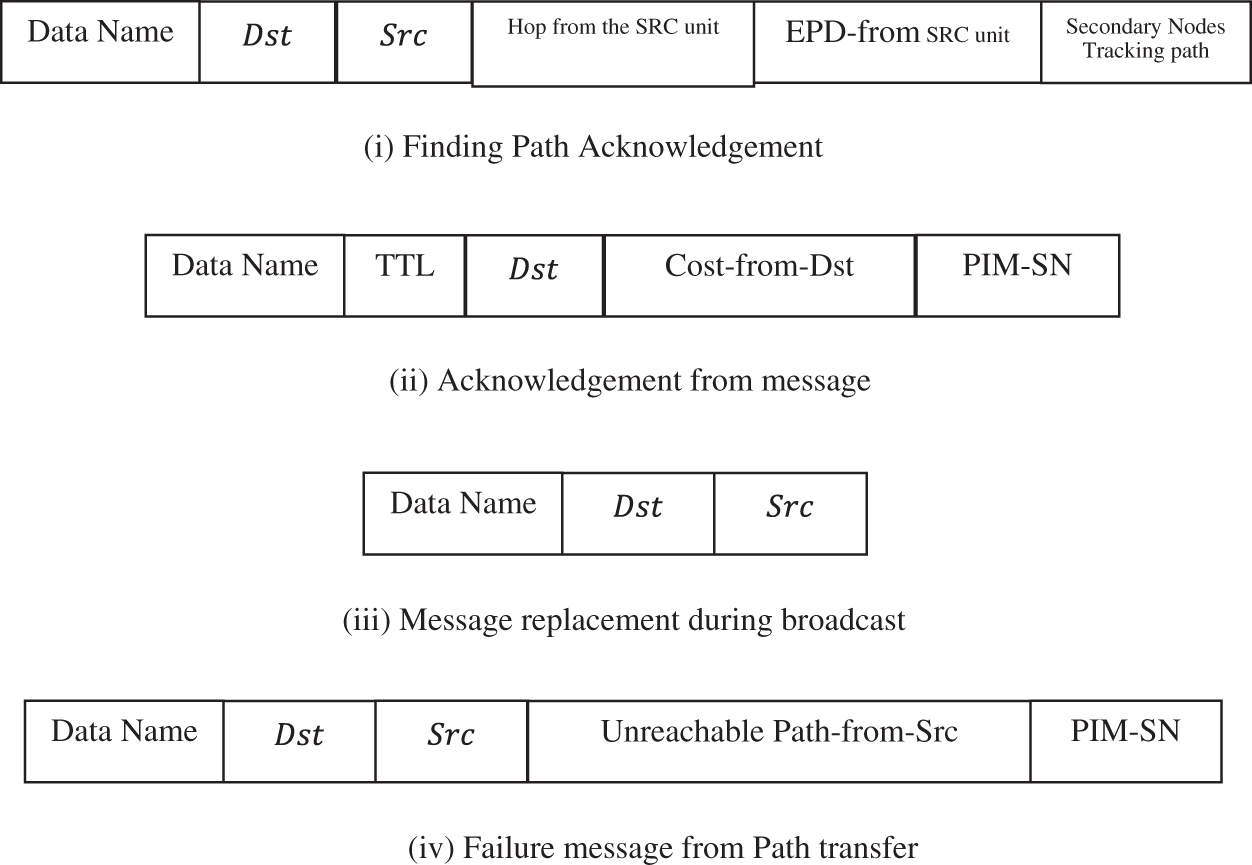
Figure 2: Format of control messages in EORP protocol
It is the receiver’s responsibility to construct an Active Source List (ASL), which is a collection of active traffic sources and their EPDs, to achieve its PUM goal. When the receiver achieves the PUM goal, it creates an Active Source List, which is subsequently utilized to locate further sources (ASL). The ASL is composed of three components: the Src component, the Hop-from-Src component, and the EPD-from-Src component. Using this list, the target will investigate numerous routes to choose many node-disjoint optimal routes, after which it will transmit PIM messages to the source. It is only when the preliminary backoff has been completed that the process of selecting the optimal routes may begin. The hop count and EPD values of routes that have been authorized are used to determine the similarity between routes that have been approved. As a result, it is determined that the main route has the fewest hops and the lowest EPD, and the PIM packet is broadcast back to the source utilizing this major and optimal route as the transmission medium, as shown in Fig. 1. Various factors, such as hop count and EPD values, are used to categorize the various routes that are made accessible to you. In Fig. 3, you can see the steps that a node goes through when it receives an incoming PUM request.
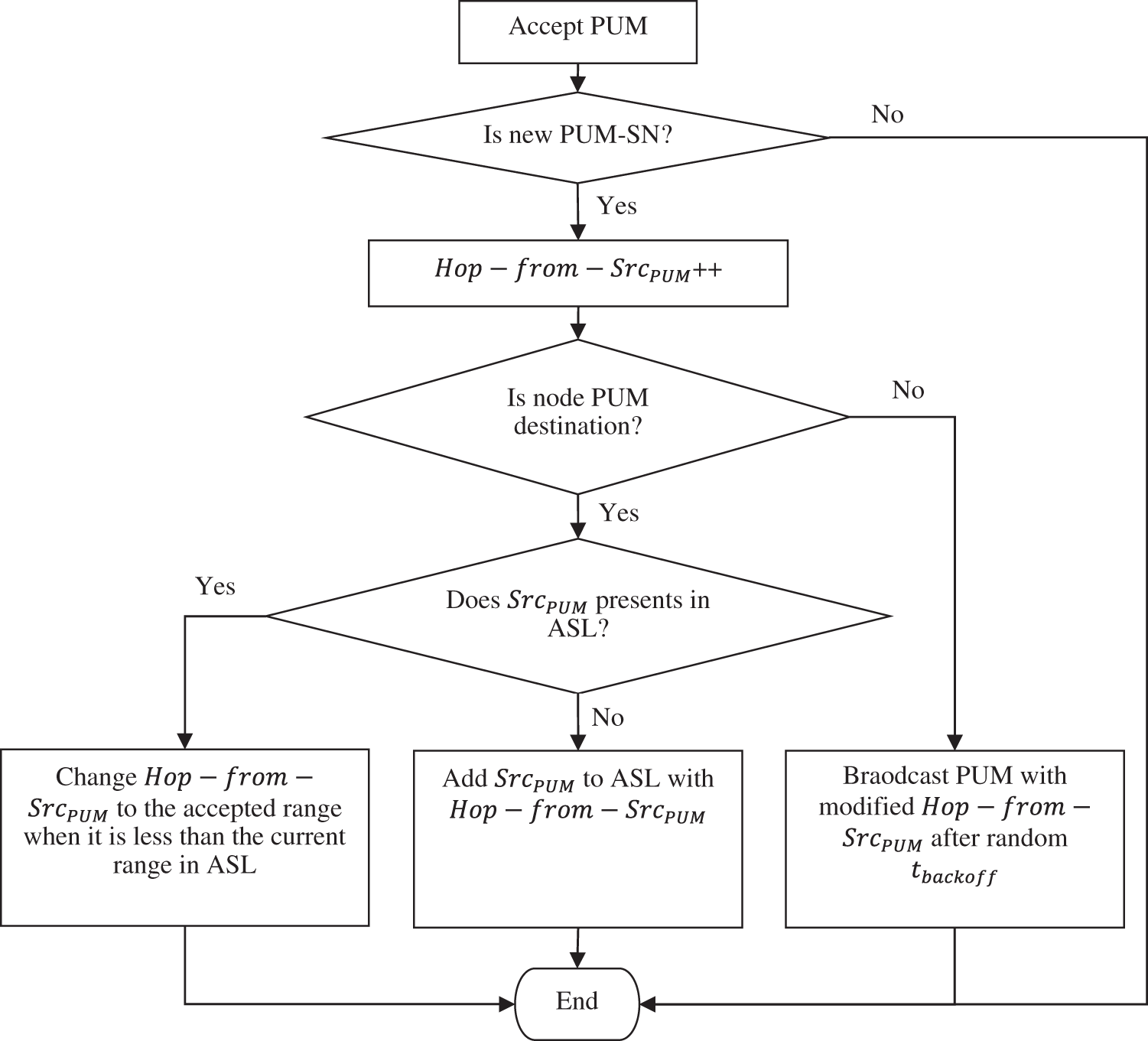
Figure 3: Acknowledgement of received message
When a target has more than one legitimate origin in its ASL, it is usual for the target to bombard the PIMs with requests for its origins and transitional nodes. To establish the true cost of delivering the target, this procedure must be followed. It is possible to configure with a alive timing option that is assigned to the maximum number of hops and the minimum number of EPDs on the ASL. However, even after reducing it by one per PIM, the initial TTL is more than the maximum number of hops permitted by the ASL standard. Due to the use of this technique, PIM floods from even the most distant sources are prevented from reaching their intended destination. Finally, by enabling data to be sent from the origin and transitional nodes to the destination. Fig. 4 depicts the procedures that a node must follow to receive the PIM message.
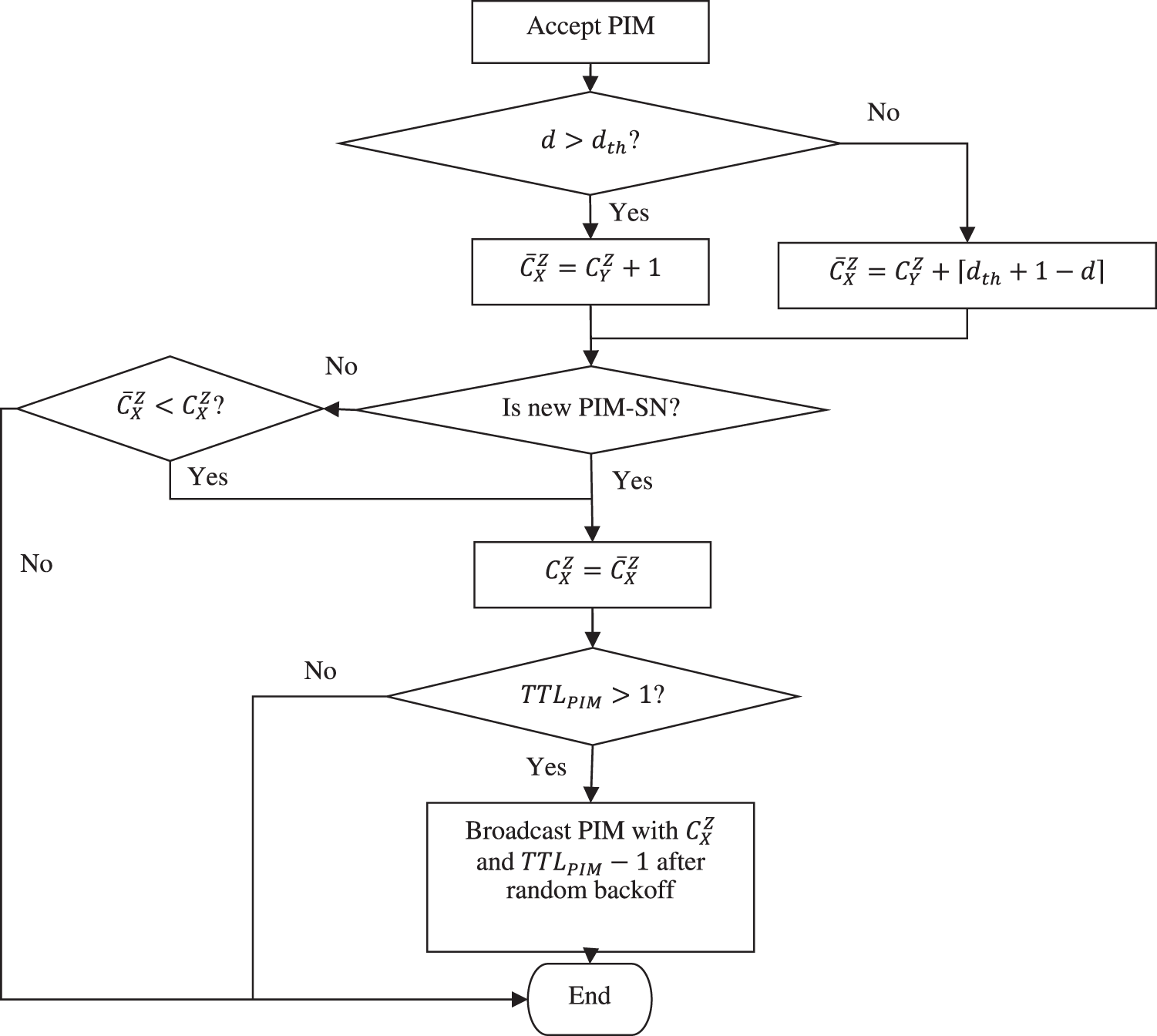
Figure 4: Flowchart of message acknowledgement
The acceptance or rejection of a PIM by a node has an impact on the amount of money it costs to go to the destination. A successful PIM is determined when X receives a PIM from Y.
an is the value that is not larger than an in Eq. (10), and the term d this the delay that is the most significant among the values of a and an. After the transmitting party has calculated C _XZ, the receiver adjusts its cost C _XZC _XZ to reflect the new PIM or the lower cost, as appropriate, after the receiving party has calculated C _XZ. To enhance the likelihood that data will be routed to a node with a lower latency connection to the destination, this strategy is often used in conjunction with other tactics. The routing cost measure is raised by one in the case of a shorter delay route since the hop count for a shorter delay route is larger than the hop count for a long journey. Providing a large number of PIMs with similar sequence numbers to the nodes may also allow them to maintain their optimum price. Due to the fact that an intermediate node with reduced latency may be able to keep routing costs at a much lower level than the costs at which other surrounding nodes must maintain their routing costs, the likelihood of data transfer from this node increases. In addition, the traffic source makes use of the RBEM to tell the target that a packet has been received from the connection’s origin node by the target. Once an RBEM has been received by a receiving device, the associated origin is deleted from the ASL of the receiving device (see below). The cascade of PIMs comes to a halt as soon as the ASL is eliminated from the game. EORP cost management approach can only be used on a network when active end-to-end packet intervals are being carried out on the network as a consequence of the combination of the PUM and RBEM technologies.
E. Path Maintenance
Furthermore, due to the dynamic characteristics of MANET, it is possible to maintain a route between two sites. During transmission, if the path between the origin and the destination is interrupted at any point, a PFM packet will be broadcast to the whole network. After that, the origin looks for backup routes in its cache, which it ultimately locates. After testing all of the backup routes and failing, it is necessary to begin the path-finding procedure for the alternative route.
3.3 EORP with Multi-Channel Cooperative Neighbor Discovery (EORP-MCCND) Protocol
While EORP provides for dependable data transfer, the exchange of control packets (PIM) from the destination to all nodes has the potential to diminish the efficiency of a node’s lifespan by as much as 50%. (see Fig. 1). When the EORP protocol is used in combination with the MCCND protocol, which searches for cooperative nearby nodes on a routing route during the control packet exchange between a remote destination and source node, the challenges described above are solved. Achieved by the use of the finding probability, which represents the likelihood of successful discovery of collaborating neighboring nodes within a random period in the transmission zone. According to the hypothesis given above, it is studied in this protocol if a node has a p percent probability of being in the active mode during a random time and a 1 − p percent chance of being in the inactive mode during a random interval. As a result, while the system is functioning, the system is capable of recognizing cooperative nearby nodes that are in the active state. Aside from that, the possibility of getting a match across all of the other detection channels is taken into account. For simplicity, let us suppose that there are a total of N active nodes in the transfer zone at any one time, with n I active nodes in the transfer zone (out of a total of N nodes). In the case of an unknown interval I and channel k, the solution is identified, and the probability of finding a solution is calculated:
Nodes with a greater possibility of being discovered are referred to as cooperative neighbouring nodes, whilst nodes with a lower likelihood of being discovered are referred to as non-cooperative neighboring nodes once the discovery probability for each node has been calculated. Combining the ASL with this cooperative nearby node list allows the PIM packets to be routed via numerous node-disjoint optimal routes that have been found over the PLA. Because it is not permitted to transmit and receive packets from all nodes regularly, overhead and power consumption on nodes is reduced, resulting in a considerable increase in the number of packets sent and received in a given period.
NS2.35, Network Simulator version 2.35 (NS2.35), are used to simulate and assess the EORP and EORP-MCCND protocols to determine whether or not the protocols in question are effective. Here, we demonstrate how networks that utilize EORP for routing may save energy and send fewer control packets because they identify the cooperative nearby nodes of each network node on the best pathways, resulting in energy and money savings on both sides of the equation. The primary goal of this study is to compare the efficacy of EORP and EORP-MCCND to numerous current approaches, such as DSR, E2NDjMRP [26], and PLA-DSR [16], and others, to identify which is more efficient. As a result, control packets are created at the CBR and sent between the source and destination nodes as needed. In particular, E2E-D, Network Lifetime, EC, and RO are all taken into consideration in the study. There is a list of simulation parameters available on Tab. 1.
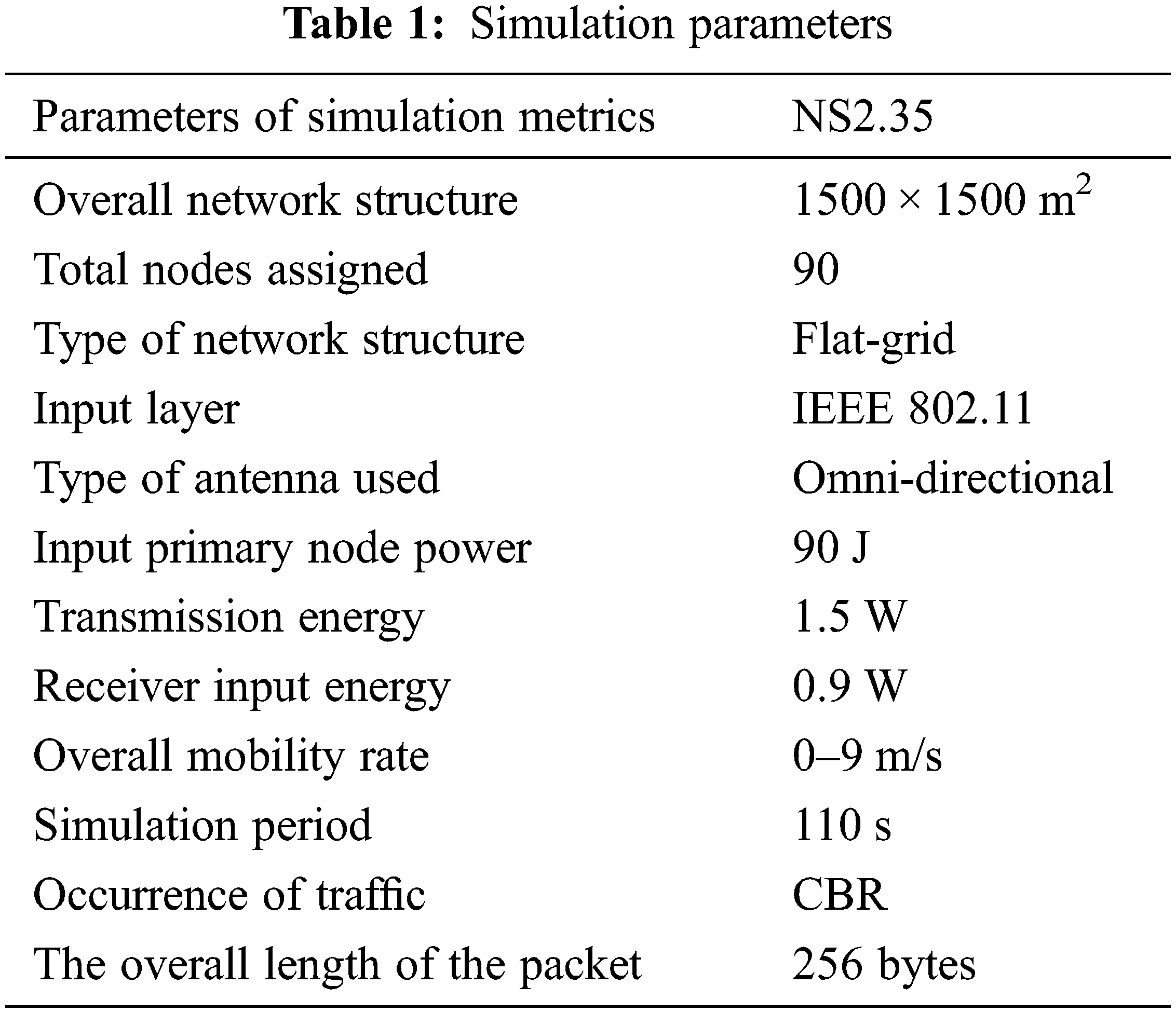
Fig. 5 shows the E2E-D (in seconds) for the DSR, E2NDjMRP, PLA-DSR, EORP, and EORP-MCCND protocols under varied traffic loads (measured in packets per second). As a result, it has been shown that EORP-MCCND decreases the E2E-D when compared to other methods. Take, for example, a packet rate of 20 packets/s for CBR. The E2E-D of EORP-MCCND is 41.7 percent lower than DSR, 38.1 percent lower than E2NDjMRP, 30 percent lower than PLA-DSR, and 9.9 percent lower than EORP protocols. The E2E-D of EORP-MCCND is 45.7 percent lower than that of DSR, 42.42 percent lower than that of E2NDjMRP, and 24.75 percent lower than that of PLA-DSR, and 12.64 percent lower than that of EORP protocols at 12 packets/s. This is because optimal data transfer routes must be found for both cooperative neighboring nodes and numerous node-disjoint pathways.
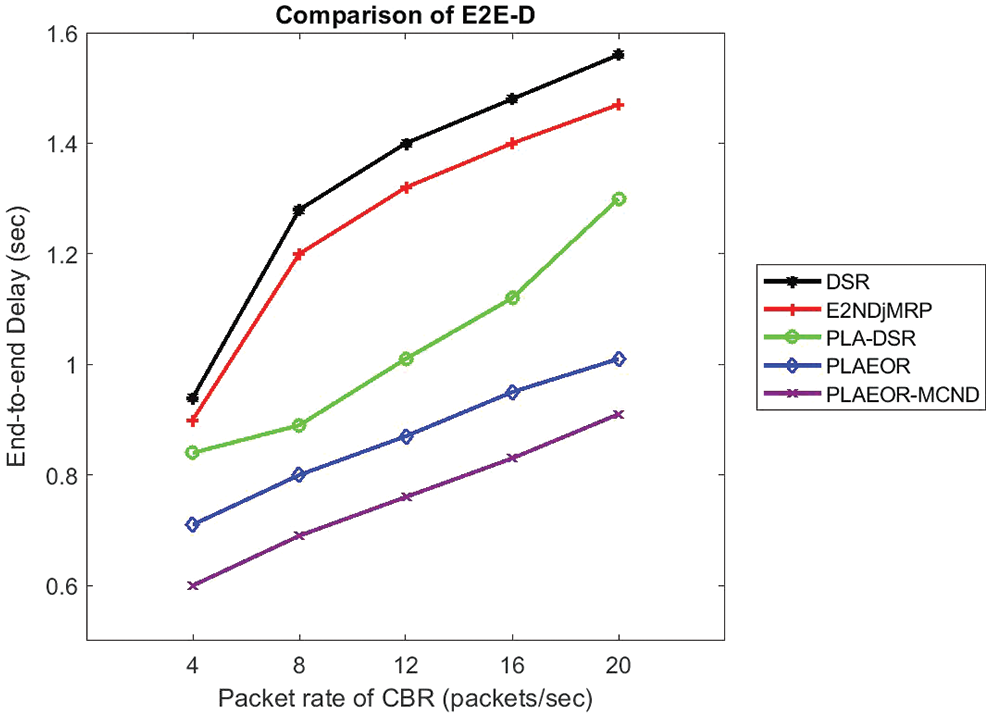
Figure 5: E2E-D vs. packet rate of CBR
It is the amount of power depleted during communication.
Fig. 6 depicts the energy consumption (Energy Consumption) for DSR, E2NDjMRP, PLA-DSR, EORP, and EORP-MCCND when subjected to varying traffic loads (measured in packets/s) under various conditions. According to the results of this research, when compared to the other protocols, the EORP-MCCND therapy lowers Energy Consumption. According to a 20-packet-per-second CBR, the EC of the EORP-MCCND protocol is 41.9 percent lower than the DSR protocol, 34.5 percent lower than the E2NDjMRP protocol, 29.4 percent lower than the PLA-DSR protocol, and 18.2 percent lower than the EORP protocol. If the packet rate of CBR is 20 packets/s, the EC of EORP-MCCND is 41.9 percent lower than DSR, 34.5 percent lower than E2NDjMRP, and 29 percent lower than E2NDjMRP, respectively. Another example is that if the packet rate of the CBR is 12 pakets/s, the EC of EORP-MCCND is 48.15 percent lower than DSR, 42.86 percent lower than E2NDjMRP, 37.78 percent lower than PLA-DSR, and 22.22 percent lower than EORP protocols (see table below). Taking use of the identification of cooperative surrounding nodes, as well as the discovery of numerous node-disjoint optimum paths to transmit data between the origin and the destination, it is feasible to achieve this goal.
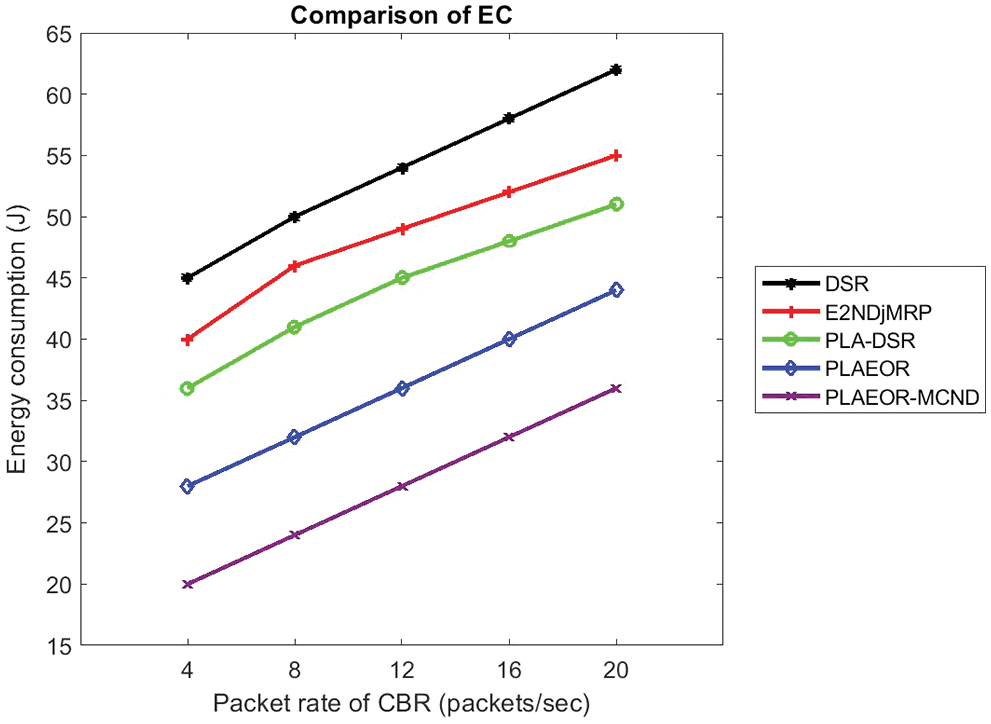
Figure 6: Energy consumption vs. packet rate of CBR
It is the fraction of the overall amount of RREQ and RREP broadcast per data packet.
It is measured in nanoseconds the amount of time it takes for data to be sent between a source and a destination (Network Life). For DSR, E2NDjMRP, PLA-DSR (with and without MCCND), EORP, and EORP-MCCD, the Network Lifetime (seconds) is shown in Fig. 7 under a range of traffic loads (measured in packets/s). This research shows that the EORP-MCCND protocol outperforms all other protocols in terms of extending life while keeping or improving fidelity while maintaining or improving.
Figure 7: Performance metrics of proposed work
While under an EORP-MCCND is 91 s, the life of DSR, PLA, E2NDjMRP, and Proposed EORP is 22, 35, 62, and 79 s, respectively. Similarly, with a traffic load of 12 packets/s, the Network Lifetime of EORP-MCCND is 105 s, but the life of DSR, E2NDjMRP, PLA-DSR, and EORP is 35, 40, 74, and 93 s, respectively, for the same load. As a result, the EORP-MCCND protocol will increase the lifespan of the node by reducing the delay rate, latency, Energy consumption during data transmission.
The EORP protocol was developed in response to the existing routing protocol described in this article, with the routing cost decided by the Energy consumption of all nodes across the network while control messages are flooding between the source and destination nodes. It is possible to avoid sending control packets to every node on a route thanks to the development of the MCCND protocol, which works by detecting the collaborating adjacent nodes of each node along the way. This is significantly less than all other protocols and is significantly less than all other protocols except for one. In congested environments, on the other hand, there is a recurrent collision between nodes throughout the MCCND procedure. Therefore, future studies will focus on preventing traffic collisions and enhancing resource allocation by defining the cost of negotiation between neighbouring nodes to improve network performance.
Acknowledgement: Thank you to Editors and Reviewers.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. D. Kanellopoulos and F. Cuomo, “Recent developments on mobile ad-hoc networks and vehicular ad-hoc networks,” Electronics, vol. 10, no. 4, pp. 1–3, 2021. [Google Scholar]
2. W. Sun, L. Dai, X. Zhang, P. Chang and X. He, “RSOD: Real-time small object detection algorithm in UAV-based traffic monitoring,” in Applied Intelligence, Springer Nature Switzerland AG, pp. 1–16, 2021. https://doi.org/10.1007/s10489-021-02893-3. [Google Scholar]
3. W. Sun, X. Chen, X. Zhang, G. Dai, P. Chang et al., “A multi-feature learning model with enhanced local attention for vehicle re-identification,” Computers Materials & Continua, vol. 69, no. 3, pp. 3549–3561, 2021. [Google Scholar]
4. I. U. Khan, I. M. Qureshi, M. A. Aziz, T. A. Cheema and S. B. H. Shah, “Smart IoT control-based nature inspired energy efficient routing protocol for flying ad hoc network (FANET),” IEEE Access, vol. 8, pp. 56371–56378, 2020. [Google Scholar]
5. M. Kumar and R. Mishra, “An overview of MANET: History, challenges and applications,” Indian Journal of Computer Science and Engineering, vol. 3, no. 1, pp. 121–125, 2012. [Google Scholar]
6. S. S. Dhenakaran and A. Parvathavarthini, “An overview of routing protocols in mobile ad-hoc network,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 3, pp. 251–259, 2013. [Google Scholar]
7. R. Sharma, T. Sharma and A. Kalia, “A comparative review on routing protocols in MANET,” International Journal of Computer Applications, vol. 133, no. 1, pp. 33–38, 2016. [Google Scholar]
8. A. R. Rajeswari, “A mobile Ad hoc network routing protocols: A comparative study,” in Recent Trends in Communication Networks, IntechOpen, United Kingdom, 2020. [Google Scholar]
9. S. Gangwar, “Mobile ad hoc networks: Comparison of multipath routing protocols with unipath routing protocols,” International Journal of Computers & Technology, vol. 5, no. 3, pp. 193–199, 2013. [Google Scholar]
10. B. Sharma, S. Chugh and V. Jain, “Investigation of adaptive multipath routing for load balancing in MANET,” International Journal of Engineering and Advanced Technology, vol. 2, pp. 65–71, 2013. [Google Scholar]
11. H. Jhajj, R. Datla and N. Wang, “Design and implementation of an efficient multipath AODV routing algorithm for MANETs,” in IEEE 9th Annual Computing and Communication Workshop and Conf., >Las Vegas, Nevada United States, pp. 0527–0531, 2019. [Google Scholar]
12. V. Sharma, B. Alam and M. N. Doja, “An improvement in DSR routing protocol of MANETs using ANFIS,” in Applications of Artificial Intelligence Techniques in Engineering, Singapore: Springer, pp. 569–576, 2019. [Google Scholar]
13. D. I. Elewely, M. F. Areed and H. A. Ali, “A proposed routing scheme for power reduction in wireless networks,” International Journal of Engineering and Technology, vol. 3, no. 1, pp. 20–29, 2014. [Google Scholar]
14. F. T. AL-Dhief, N. Sabri, M. S. Salim, S. Fouad and S. A. Aljunid, “MANET routing protocols evaluation: AODV, DSR and DSDV perspective,” in MATEC Web of Conf., EDP Sciences, France, vol. 150, pp. 1–6, 2018. [Google Scholar]
15. X. Zhen and X. Juan, “Energy-aware and delay-aware QoS routing in mobile ad-hoc networks,” in IEEE Int. Conf. on Computational Problem-Solving, Lijiang, China, pp. 511–515, 2012. [Google Scholar]
16. H. A. Ali, M. F. Areed and D. I. Elewely, “An on-demand power and load-aware multi-path node-disjoint source routing scheme implementation using NS-2 for mobile ad-hoc networks,” Simulation Modelling Practice and Theory, vol. 80, pp. 50–65, 2018. [Google Scholar]
17. W. Almobaideen, R. Al-Soub and A. Sleit, “MSDM: Maximally spatial disjoint multipath routing protocol for MANET,” Communications and Network, vol. 5, no. 4, pp. 316–322, 2013. [Google Scholar]
18. Y. Tashtoush, O. Darwish and M. Hayajneh, “Fibonacci sequence based multipath load balancing approach for mobile ad hoc networks,” Ad Hoc Networks, vol. 16, pp. 237–246, 2014. [Google Scholar]
19. C. Lal, V. Laxmi and M. S. Gaur, “A node-disjoint multipath routing method based on AODV protocol for MANETs,” in IEEE 26th Int. Conf. on Advanced Information Networking and Applications, Gwangju, South Korea, pp. 399–405, 2012. [Google Scholar]
20. K. Zhang, G. Yin, Q. Han and J. Lin, “DFDP: A distributed algorithm for finding disjoint paths in wireless sensor networks with correctness guarantee,” International Journal of Distributed Sensor Networks, vol. 10, pp. 1–11, 2014. [Google Scholar]
21. Y. Yu and M. Liang, “A node-disjoint multipath routing protocol in MANETs,” in Int. Conf. on Computer Science and Mechanical Automation, Hangzhou, China, pp. 108–112, 2015. [Google Scholar]
22. B. Arora, “An adaptive transmission power aware multipath routing protocol for mobile ad hoc networks,” Procedia Computer Science, vol. 57, pp. 1242–1248, 2015. [Google Scholar]
23. S. Gopinath and N. Nagarajan, “Energy-based reliable multicast routing protocol for packet forwarding in MANET,” Journal of Applied Research and Technology, vol. 13, no. 13, pp. 374–381, 2015. [Google Scholar]
24. M. Bheemalingaiah, M. M. Naidu, D. S. Rao, and P. Vishvapath, “Energy aware on-demand multipath routing protocol in mobile ad hoc networks,” International Journal of Computer Networks and Wireless Communications, vol. 6, no. 5, pp. 14–33, 2016. [Google Scholar]
25. K. Mounagurusamy and K. Eswaramurthy, “A novel load balancing scheme for multipath routing protocol in MANET,” Journal of Computing and Information Technology, vol. 24, pp. 209–220, 2016. [Google Scholar]
26. S. M. Benakappa and M. Kiran, “An energy-aware node disjoint multipath routing protocol for MANETs with dynamic transmission range adjustment,” in IEEE Int. Conf. on Electrical, Electronics, Communication, Computer, and Optimization Techniques, Mysuru, India, pp. 335–341, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |