DOI:10.32604/cmc.2022.019591

| Computers, Materials & Continua DOI:10.32604/cmc.2022.019591 |  |
| Article |
Multi-Factor Authentication for Secured Financial Transactions in Cloud Environment
1IFET College of Engineering, Villupuram, 605108, Tamilnadu, India
2University College of Engineering-Tindivanam, Tindivanam, 604001, Tamilnadu, India
*Corresponding Author: D. Prabakaran. Email: dprabakaranmtech@gmail.com
Received: 19 April 2021; Accepted: 03 June 2021
Abstract: The rise of the digital economy and the comfort of accessing by way of user mobile devices expedite human endeavors in financial transactions over the Virtual Private Network (VPN) backbone. This prominent application of VPN evades the hurdles involved in physical money exchange. The VPN acts as a gateway for the authorized user in accessing the banking server to provide mutual authentication between the user and the server. The security in the cloud authentication server remains vulnerable to the results of threat in JP Morgan Data breach in 2014, Capital One Data Breach in 2019, and many more cloud server attacks over and over again. These attacks necessitate the demand for a strong framework for authentication to secure from any class of threat. This research paper, propose a framework with a base of Elliptical Curve Cryptography (ECC) to perform secure financial transactions through Virtual Private Network (VPN) by implementing strong Multi-Factor Authentication (MFA) using authentication credentials and biometric identity. The research results prove that the proposed model is to be an ideal scheme for real-time implementation. The security analysis reports that the proposed model exhibits high level of security with a minimal response time of 12 s on an average of 1000 users.
Keywords: Cloud computing; elliptical curve cryptography; multi-factor authentication; mel frequency cepstral coefficient; privacy protection; secured framework; secure financial transactions
Virtual Private Network (VPN) is an emerging technology that turns out to be vital among IT professions, research persons, and the common public in terms of employing the data resources through the cloud server. In this modern digital era, the common public utilizes the cloud resources [1] in the form of online financial transactions and as per the survey by Pew report and American Life project, 51% of users stated that they utilize cloud computing due to its easiness and convenience in accessing the resources. The Virtual Private Network has multiple distinct attributes like elasticity, metered services, broad network access, on-demand self-service, resource pooling, measured service, etc. One noteworthy application of cloud computing is digital financial transaction using desktop or portable devices like smart phone, laptops, etc. through a cloud server, that drives the economy to scale exponentially. The digital financial transactions [2] are executed by accessing the banking server through a third-party cloud service provider, which provides access by consigning session key on prosperous verification of authentication credentials. The cloud computing in parallel to its notorious advantages also face weak security [3] as it is vulnerable to the attacks [4] introduced by Hackers. Some of the highlighted cyber financial attacks were, RBS World pay Hack (Atlanta, 2008), National City Bank breach (United States, 2010), U.S Federal Reserve bank of Cleveland breach (United States, 2010), Global Payments breach (United States, 2011), Brazilian payments system Attack (Brazil, 2012), JP Morgan Chase Data Breach (United States, 2014), Equifax hack (United States, 2017), City Union Bank SWIFT Attack (India, 2018), Mexican Bank Theft (Mexico, 2018), State Bank of Mauritius (Mauritius, 2018), SBI Breach (India, 2019), Paypal Accounts linked to Google pay abused (United States & Germany, 2020). The hackers target the security credentials by introducing multitudinous means of attacks like Man-in-the-Middle attack, impersonation attack [5], session hijack [6], secure socket layer attack, Denial of Service (DoS) attack [7], eavesdropping [8], password discovery attack and had succeeded in gaining access to the database resources with the authentication credentials earned illegitimately. The Deloitte- India Banking Fraud Survey, edition II, states that 54% of banking attacks were succeeded by hackers in executing the pre-mentioned attacks. Besides, the Quick Heal annual report 2017 mentions that hackers introduce attacks through range of vulnerabilities like Trojan, infectors, worm, Potentially Unwanted Application (PUA), adware, Ransomware. Research has been accelerated in this domain to clear the pit fall of weak security in cloud computing. Despite abundant research and results, the authentication policy [9] prevails weaker and lacks mutual authentication between the user device and cloud authentication servers. The cloud-based authentication server is a multi-cloud server, provide session key to the user on successful affirmation of the authentication process. The hacker manages to gain the session by cracking the authentication verification system. The feeble authentication paves a path to the breach of communication channel security and the integrity of the transmitted data was compromised. The severity of this concern is the motivation for this research work, and its benefaction to resolving this issue is spotlighted as follows.
1.1 Beneficence of the Research Work
i) This research work proposes a novel framework with Multi-Factor Authentication (MFA) system to strengthen the security using a low entropy password, individual unique biometrics for authentication.
ii) The influx of Multi-Factor Authentication (MFA) inhibits the hackers from attacking the session by encrypting the credentials and session key by Elliptical Curve Cryptography (ECC).
iii) This system magnifies the security for third party transactions in the cloud network by preferring voice recognition as an imperative parameter along with customary credentials that include the user name and low entropy password.
iv) The motive for the preference of voice recognition over different biometrics was these metrics follow image recognition system which can be duplicated whereas the voice recognition has the least possibility of duplication and most recent mobile devices embeds voice sensors for the authentication process.
1.2 Organization of This Research Work
The research paper is organized as follows: Section 2 illustrates the recent research works related to the issues aforementioned in Section 1.1, Section 3 narrates the architecture and the algorithms of the proposed framework followed by the security analysis of the proposed work is done in Section 4. Subsequently in Section 5, the evaluation of proposed system is performed and Section 6 concludes the proposed model.
Plentiful researchers had introduced several policies to implement a secure authentication process and to thwart hackers from succeeding in their attempt of accessing the cloud resources.
Garg et al. [10] proposed and evaluated a mobile phone-based authentication with a session key agreement approach that provides strong authentication services to SOCKS V5 protocol. This proposed protocol is applicable for mobile devices and employs International Mobile Subscriber Identity (IMSI) number to provide an individual’s unique identification. Xie et al. [11] proposed a novel dynamic ID-based anonymous two-factor authenticated key exchange protocol. The proposed model addresses multi-factor authentication and prevents vulnerabilities like a lost-smart-card-attack, offline dictionary attack, lack of forward secrecy. It supports smart card revocation and password update without centralized storage. Soares et al. [12] depicts a system that supersedes the ATM cards and PINs by the physiological biometric fingerprint and iris authentication. The feature of One-Time Password (OTP) affords confidentiality to the users and unfastens the user from reviving PINs. Hafizul Islam et al. [13] recommended a scheme of maintaining a password table in the server which has weak security against server masquerade attack, insider attack and hence backslides to sustain security. Tao et al. [14] proposed an intricate face authentication task on the devices with limited resources; the emphasis is largely on the reliability and applicability of the system. Both theoretical and practical considerations are taken. The final system has achieved an equal error rate of 2% under challenging testing protocols. Preeti et al. [15] presented a strong security protocol of three-factor remote authentication system to provide better security and is much complex in terms of performance and cost. Hafizul Islam [16] designed a protocol that offers computation cost-efficient and robust three-party Password-based Authentication Key Exchange (3-PAKE). The key confirmation is done using extended chaotic maps and smart card. The protocol has proved to be secure in the random oracle model and is certified through simulation of Automated Validation of Internet Security Protocols and Applications (AVISPA) software tic maps and smartcard.
The following are the gaps identified on the existing system through the literature survey are:
i) Lack of stringent authentication scheme to secure the session key.
ii) Complex Protocols with high computational cost and is vulnerable to attacks.
iii) The fragile authentication policies, benefits the attackers masquerade the verification process.
3.1 Preliminaries of Proposed Scheme
The practice of pairing among the factors of two cryptographic groups to the third group with a mapping
where, G1, G2, and GT are the additive cyclic groups of prime order “q”.
The pairing based cryptography satisfies the following properties:
1. The bilinearity property:
2. The non-degeneracy policy:
3. The existence of efficient algorithm for the computation of bilinear pairing function “e”.
The notations in the Tab. 1 are used to describe the process throughout the paper.
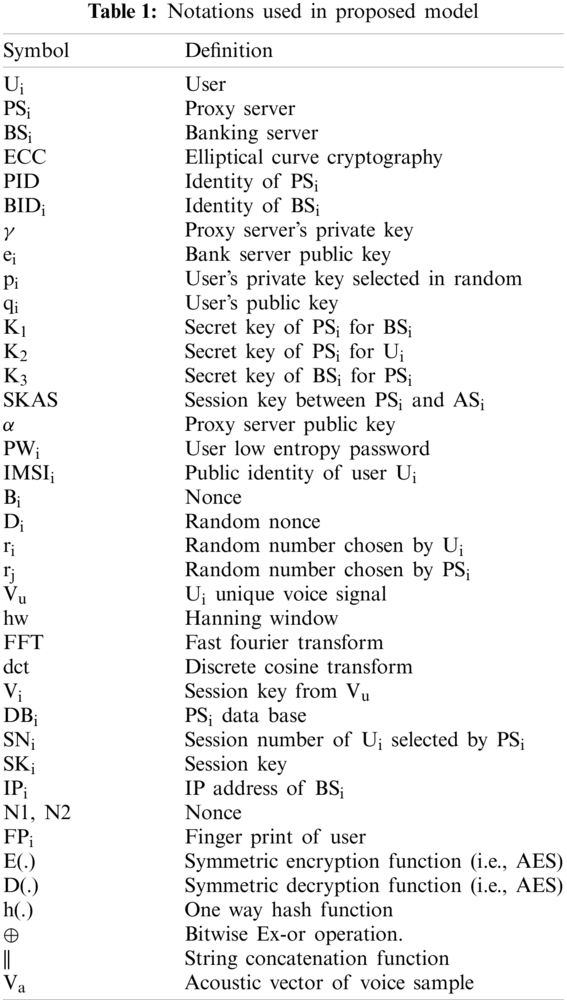
The aim to design the proposed model that provides a secure platform for the users in performing secured banking transactions using their mobile devices. The proposed model is composed of components namely mobile device, authentication server, banking server, and the user with valid low entropy password and biometric identity. This system has an elasticity of extending with multiple users and multiple banking servers. This model composed of five phases that take account of registration, user verification, voice coefficient extraction phase using MFCC, session key generation, and shielded transaction phase. Fig. 1 illustrates the system architecture of the proposed model. In this proposed model, the user Ui accesses the BSi by registering the low entropy password and biometric identity especially the user’s voice which is unique. The former has to register themselves to the authentication server using a low entropy password and International Mobile Subscriber Identity (IMSI) number while the later register with the authentication server by generating a key pair.

Figure 1: System architecture of proposed model
The user Ui login with password and biometric identity say individual’s voice with the authentication server. The authentication server in turn fetches the IMSI of the user device and verifies the digital signature for proper authentication to provide ticket to user the same that received from banking server.
3.2 Algorithm for Registration and Key Agreement Using Elliptical Curve Cryptography
In the Fig. 2, Registration and Key agreement phase were mentioned as registration which involves user’s mobile device (Ui), banking server (BSi) and the authentication server (ASi). This phase performs two process namely registration and key agreement process where the former is secured as the entire process is performed offline whereas the later uses Elliptical Curve Cryptography (ECC) [17] to generate the session key. The Fig. 2 characterizes the registration process of user Ui and banking server BSi with the authentication server in multi cloud ASi.

Figure 2: Message flow diagram- registration phase
The algorithm for registration and key agreement is illustrated in Tab. 2.

The registration and key agreement algorithm is a notarization algorithm involving generation of private key and public key of banking server BSi and user device Ui. The banking server generates the secret key k3 and transmits over the secure channel.
3.3 Algorithm for User Verification
This phase involves user Ui, authentication server ASi and banking server BSi that performs user authentication and credential verification process to provide a secure session key. In the Fig. 3, the authentication process between the user Ui and the authentication server ASi is illustrated. In this phase, the Ui provides low entropy password and the individual unique voice to prove its identity authentication process. The voice has been processed by incorporating Mel Frequency Cepstral Coefficient (MFCC) [18] algorithm.

Figure 3: Message flow diagram- user verification phase
The algorithm for user verification is exemplified in Tab. 3.
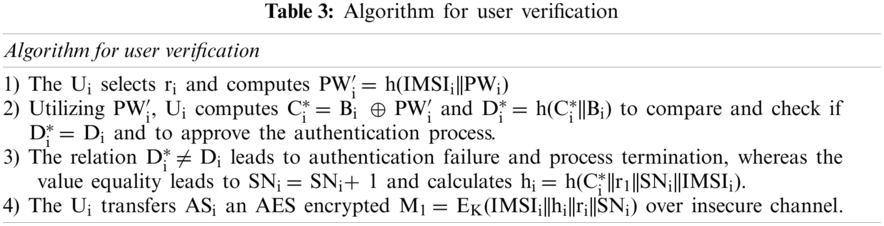
The user provides its password, which undergoes authentication check and on successful verification, the user device sends login message to authentication server for authentication process for the grant of session key to the user.
Algorithm for Voice Coefficient Extraction Using Mel Frequency Cepstrum Coefficient (MFCC)
The voice Vu of the Ui acts as the major credential and is recorded through the Ui device. The Vu express the Ui gender, emotion and ease the identification process of Ui. Several voice feature extraction algorithms like Linear Predictive Coefficients (LPC), Mel Frequency Cepstral Coefficients (MFCC) and Relative Spectra filtering of log domain coefficients (RASTA) were in practice, among which the Mel Frequency Cepstral Coefficient (MFCC) algorithm provides better accuracy [19], low error rate, high recognition rate, and faster response subject to utilization of self data set. The MFCC provides better Vu coefficients Vi and is well aligned as of human ear’s perception that cannot exceed the frequency limit of 1 KHz. The Fig. 4 elucidates the process implicated by MFCC algorithm in extracting the voice coefficients.

Figure 4: Message flow diagram- session key generation phase
The MFCC technique involves pre-emphasis, sampling and windowing process, performing Fast Fourier Transform (FFT), Mel filter bank, performing discrete cosine transform to produce mel coefficients. The MFCC algorithm is executed in MATLAB R2013a version and for the reason that is simpler and creation of better coefficients; the MFCC is implemented in this proposed system to create credentials for authentication process.
The user gratifying the authentication process utilizes session key and providing valid biometric finger print, access BSi to perform successful transaction. The MFCC accepts the Ui voice input Vi recorded through microphone is continuous in time and is represented as v(t). The algorithm for the voice coefficient extraction using Mel Frequency Cepstrum Coefficient (MFCC) is illustrated in Tab. 4.

3.5 Algorithm for Session Key Generation
This phase involves Ui, ASi and BSi to issue secure session key based on successful verification of credentials as the process continuation to authentication checking of authorized Ui. The Fig. 4, depicts that the session key generation followed by the request for ticket by the user Ui to the bank server BSi through authentication server ASi. The bank server issues the session key on successful verification of authentication and the ticket is forwarded to user Ui through the authentication server ASi.
On reception of message M2, the algorithm for session key generation is executed as per illustrated in Tab. 5.

Algorithm for Shielded Transaction Phase
This phase involves Ui and BSi to perform a shielded transaction between the Ui and BSi as the session key is issued and confirmed to grant a secure transaction. The Fig. 5, illustrates the shielded transaction between the user Ui and banking server BSi. The user Ui sends the fingerprint minutiae to the banking server and on successful verification the shielded transaction is granted to the user Ui.
1)The Ui on applying the unique FPi extracts the features FPi = Minutiae ( ) to encrypt MSG = Evi(FPi||N1||ESKAS(BIDi||N2)) to BSi.
2)The BSi decrypts Dkey(MSG) to acquire (FPi||N1||ESKAS(BIDi||N2) and DSKAS(ESKAS(BIDi ||N2) to test BIDi ! = BIDi and N2! = N2 leads to termination of transaction while the amend leads to establishment of session and extraction of N1 to execute a successful transaction in triumph of FPi == FPi ∗.

Figure 5: Message flow diagram- shielded transaction phase
On successful clearance of authentication process, the authentication server connects the user device with banking server to perform the transaction in a shielded mode.
We put forward that our proposed model has much merits and can defy multiple security threats.
4.1 Theorem 1. The Proposed Model Provides Tough Anonymity Against Man-in-the-Middle Attack
Proof: This type of attack, the attacker attempts to alter the communication between Ui, ASi and BSi. In this case, the proposed system is resistive against this attack as the key q, K1, K2 were generated in offline mode. The IMSIi identity acts as a key to receive information from ASi and BSi which is unique and is stored in DBi of ASi in offline mode. Hence the possibility of extracting the IMSIi information is very low in this system. Also the ASi sends {α, Bi, Di, SNi} over offline mode, even on breaking this information, the attacker feels hard to crack the information as the pi is private to the Ui. The threat to M1-M6 were decrypted with {K, Bi, Di, SNi} were stored in Ui resists the attack hardly and has a least probability of success in attack.
The message M1: M1 = EK(IMSIi||hi||ri||SNi); M2: M2 = Eβ(h2||R||SNj||IMSIi); M3: M3 = (Fi||h(IMSIi||BIDi)); M4:M4 = EKi(PID||N1); M5: M5 = EK((PID||N1||BIDi||N2||SKAS); M6: M6 = ESKAS(BIDi||N2).
Let we consider, that hacker tends to know the IMSIi of user Ui, and the entire message content through the successful execution of Man in the Middle attack, the hacker needs to know the key “k, β” which were the private keys generated by the ASi for BSi and User device Ui.
4.2 Theorem 2. The Proposed Model Withstands Stolen Sim-Card Attack
Proof: The Ui stores the confidential information {K, Bi, Di, SNi} vital for decryption of M1-M6 face a threat of data disclosure on stolen sim card attack. Any attacker on having the confidential stored information and the sim card can involve in man-in-the-middle attack. The proposed model highly withstands stolen sim card attack, as the SKi is generated on verification of Vi extracted from Vu which is unique to each user. Without generation of SKi, the stolen sim card and details have no more active in associative with the actions of attacker. Furthermore, SNi is invalidated without Vi = MFCC(dct) and this system is invulnerable to stolen sim card attack.
Consider the user device Ui has been lost or stolen by hacker to have an authorized access by an unauthorized user using the device Ui and with IMSIi.
M1: M1 = EK(IMSIi||hi||ri||SNi); M2: M2 = Eβ(h2||R||SNj||IMSIi); M3: M3 = (Fi||h(IMSIi||BIDi));
M4: M4 = EKi(PID||N1); M5: M5 = EK((PID||N1||BIDi||N2||SKAS); M6: M6 = ESKAS(BIDi||N2).
The hacker, knowing the IMSIi information is not sufficient to gain the session key illegally as he need to know the other parameters like.
4.3 Theorem 3. The Proposed Model Provides Rigid Secrecy Against Password Guessing Attack
Proof: In this type of attack, the attacker employs cryptanalytic techniques and attempts all probabilities of password against PWi. The attacker gains PWi related information from DBi for the successful guessing of exact PWi but cannot be able to identify the decryption keys {K, Bi, Di, SNi} which was shared offline among Ui and ASi. The proposed system involves {PWi, Vi, FPi} for successful authentication whereas the later two credentials is highly essential for generating and sharing of SKi. The {Vi, FPi} and biometric sets that are not available in any directories. Thus the attacker even though succeeded in password guessing was blind in {Vi, FPi} flops in generation of SKi that proves the proposed system is highly resistive to password guessing attack.
Consider the hacker succeeds in guessing the low entropy password of User Ui.
M1: M1 = EK(IMSIi||hi||ri||SNi); M2: M2 = Eβ(h2||R||SNj||IMSIi); M3: M3 = (Fi||h(IMSIi||BIDi));
M4: M4 = EKi(PID||N1); M5: M5 = EK((PID||N1||BIDi||N2||SKAS); M6: M6 = ESKAS(BIDi||N2),
The hacker fails in decrypting any of message M1-M6 as it needs information about SNi, BIDi, PID, SKAS which still a short fall for the hacker to succeed in gaining unauthorized access.
4.4 Theorem 4. The Proposed Model Counters Known-Key Attack
Proof: Let’s consider that the attacker hacks the session key, tends to acquire the session illegally leads to failure attempt. The system proves to be rigid against any sort of attacks as the authentication process relies on multiple keys {γ, pi, K1; K2, K3} and is still secure that the final access grant relies on user’s voice print Vi and finger print FPi. The fact that the attacker manages to know the key value, the proposed model not only relies on cryptographic keys but also utilize PWi, Vi = MFCC(dct) and Finger print FPi = Minutiae( ). These credentials are essential for the computation and grant of SKi to the known Ui. Hence the proposed model is highly rigid towards the known key attack.
M1: M1 = EK(IMSIi||hi||ri||SNi); M2: M2 = Eβ(h2||R||SNj||IMSIi); M3: M3 = (Fi||h(IMSIi||BIDi));
M4: M4 = EKi(PID||N1); M5: M5 = EK((PID||N1||BIDi||N2||SKAS); M6: M6 = ESKAS(BIDi||N2)
Let us consider the hacker encounters with known key attack and is aware of secret keys k, β and can decrypt the message M1 to obtain the session number SNi . To obtain SNi, the user has to undergo successful authentication check with low entropy password, IMSIi and minutiae matching confirmation process. Hence the known key attack proves to be insufficient to gain the illegal access of session key SKi.
4.5 Theorem 5. The Proposed Model Discards Parallel Session Attack and Insider Attack
Proof: The Parallel session attack and the Insider attack in the cloud environment is, the attacker tends to grab the session illegally by gaining information about the keys {γ, pi, K1; K2, K3}. The proposed model engross {α, Bi, Di, SNi} keys which are computed within Ui and were shared in offline mode, which the parallel session attacker is not aware of remains fail in decrypting ((PID||N1||BIDi||N2||SKAS)) and gaining the session to perform transaction. Hence the proposed system discards the parallel session attack and insider attack.
4.6 Theorem 6. The Proposed Model Rebuff Denial of Service (DoS) Attack
Proof: The attacker introduce Denial of service attack in the cloud environment to make the service unavailable to the Ui by flooding the target network with superfluous traffic intends to overload the network. The proposed model is highly resistive to this attack, the ASi exercise N1, N2 value which were time bounded. The session establishment SKi transmits ((PID||N1||BIDi||N2||SKAS)) and the N1 and N2 were time bounded exceeding which the transaction is terminated. Thus the proposed model strongly rebuffs the denial of service attack.
M1: M1 = EK(IMSIi||hi||ri||SNi); M2: M2 = Eβ(h2||R||SNj||IMSIi); M3: M3 = (Fi||h(IMSIi||BIDi));
M4: M4 = EKi(PID||N1); M5: M5 = EK((PID||N1||BIDi||N2||SKAS); M6: M6 = ESKAS(BIDi||N2)
The Denial of Service (DoS) attack proves to be unsuccessful as the half completed request will exhaust due to the nonce value encrypted in all message M1-M6.
4.7 Theorem 7. The Proposed Model Proves Rigid Against Authentication Server Attack or MITC Attack
Proof: The attacker tends to attack the authentication server ASi rather than performing other attacks to gain illegal access of a single user. The authentication server attack on becoming success, ease the attacker to gain the access of all the sessions that the authentication server acts as gateway. The proposed model proves highly rigid against the authentication server attack or insider attack as the system possess multi factor authentication system that includes low entropy password, feature extracted from voice print, IMSI identity of authenticated user’s device and user finger print noted as {PWi, Vi, IMSIi, FPi}. The attacker in the authentication server ASi may illegally gain information of {PWi, Vi, IMSIi} as all these secure credentials were verified and communicated through authentication server which is already compromised. The user’s finger print FPi is the final authentication credential that is passed over channel directly to banking server BSi where the MiTC attack proves inefficient in gaining the fingerprint FPi information.
In this section, we analyzed the proposed system in terms of efficiency and effectiveness based on the key size and strength. The parameters considered for the analysis are the length of IMSIi, length of low entropy password PWi, random numbers and message digest M1-M6 against computing time represented in milli seconds. We had chosen key words of multiple lengths ranges from 160–512 bits to perform the experiment of measuring the efficiency of our proposed system. The Fig. 6 illustrates the response of computational time with respect to the key length in bits. For clarity, the IMSIi, random numbers were numerical value whereas the PWi is composed of alphanumerical and special characters. To calculate the actual key length, we convert the key to numerical format as follows
The weight of PWi created by the Ui is determined by converting the PWi into an equivalent ASCII code. From Fig. 6, it is evident that the increase in key length directly drives computational time proportionally and to achieve a least computational time the summation of key length of PWi, ri, ri, messages (M1-M6) must be short that attenuates the strong security against various attacks.

Figure 6: Comparison of key length with computation time
It is reasonable to select PWi, ri, ri, M1-M6 of average length means neither short nor too long such that to achieve computational time at customary range. In our proposed model, we chose the key length to be 256 bits based on outcome of system analysis. The computation time in the proposed system is classified into three phases namely user login phase, ASi authentication phase and BSi authentication phase. The proposed system transmits {M1, M2, M3, M4, M5, M6} between the entities to authenticate the user and this message is of {1024 + 1024 + 128 + 128 + 1024 + 128} = 3456 bits which is lesser when compared to the reference model considered in this system. This makes the system to compute faster and to authenticate the user at faster rate such that it is more secured as it consumes least time which is not sufficient for any hacker to perform brute force attack. The proposed system provides high level of security as it involves user’s unique biometric identities namely user voice coefficient and fingerprint along with the low entropy password to authenticate the right user.
As explained earlier, the MFCC algorithm employed here performs hamming window to extract the Mel frequency coefficients from unique voice sample Vi which has high response towards all range of frequencies. The Fig. 7 depicts the feature point extraction from the voice print Vu. The hamming window detects and corrects the discontinuities in the start and end of voice sample to obtain the accurate Mel coefficients from the Vi.

Figure 7: MFCC feature point extraction
In the proposed system, the nonce period is 60 s and from the Fig. 8, it is clear that the proposed system utilize maximum of 12 s to respond for 1000 user requests. Hence the proposed system is proven to be highly robust against Denial of Service attack.

Figure 8: Comparison of number of user request with request response time
The authentication verification and secured transmission in the cloud network is a biggest challenge for which our proposed model, identity based secured transmission using MFCC algorithm provides better results and withstand various types of attacks in cloud environment. Our proposed system is efficient that proves its rigidity against any attacks and afford secured session key and mutual authentication to perform secure transmission over insecure network. As the protocol provides session key security, this protocol supports efficient practical applications in cloud network. The system has a capability of enhancing the security feature by safeguarding the credentials in authentication server database DBi be the future development to provide strong protection against any attack in particular the Man in the Cloud (MiTC) attack.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. P. Lula, O.Dospinescu, D. Homocianu and N. A. Sireteanu, “An advanced analysis of cloud computing concepts based on the computer science ontology,” Computers, Materials & Continua, vol. 66, no. 3, pp. 2425–2443, 2021. [Google Scholar]
2. Y. Ren, C. Wang, Y. Chen, M. C. Chuah and J. Yang, “Signature verification using critical segments for securing mobile transactions,” IEEE Transactions on Mobile Computing, vol. 19, no. 3, pp. 724–739, 2020. [Google Scholar]
3. J. Luna, A. Taha, R. Trapero and N. Suri, “Quantitative reasoning about cloud security using service level agreements,” IEEE Transactions on Cloud Computing, vol. 5, no. 3, pp. 457–471, 2017. [Google Scholar]
4. R. Shyamala and D. Prabakaran, “A survey on security issues and solutions in virtual private network,” International Journal of Pure and Applied Mathematics, vol. 119, no. 15, pp. 3115–3122, 2018. [Google Scholar]
5. P. N. Brown, H. P. Borowski and J. R. Marden, “Security against impersonation attacks in distributed systems,” IEEE Transactions on Control of Network Systems, vol. 6, no. 1, pp. 440–450, 2019. [Google Scholar]
6. Q. Hu, B. Du, K. Markantonakis and G. P. Hancke, “A session hijacking attack against a device-assisted physical-layer key agreement,” IEEE Transactions on Industrial Informatics, vol. 16, no. 1, pp. 691–702, 2020. [Google Scholar]
7. Z. Tan, A. Jamdagni, X. He, P. Nanda, R. P. Liu et al., “Detection of denial-of-service attacks based on computer vision techniques,” IEEE Transactions on Computers, vol. 64, no. 9, pp. 2519–2533, 2015. [Google Scholar]
8. Y. Han, L. Duan and R. Zhang, “Jamming-assisted eavesdropping over parallel fading channels,” IEEE Transactions on Information Forensics and Security, vol. 14, no. 9, pp. 2486–2499, 2019. [Google Scholar]
9. K. Fan, H. Li, W. Jiang, C. Xiao and Y. Yang, “Secure authentication protocol for mobile payment,” Tsinghua Science and Technology, vol. 23, no. 5, pp. 610–620, 2018. [Google Scholar]
10. R. Garg, M. Gupta, R. Amin, K. Patel, S. H. Islam et al., “Design of secure authentication protocol in socks V5 for VPN using mobile phone,” in Int. Conf. on Trends in Automation, Communications and Computing Technology, Bangalore, India, pp. 1–6, 2015. [Google Scholar]
11. Q. Xie, D. S. Wong, G. Wang, X. Tan, K. Chen et al., “Provably secure dynamic ID-based anonymous two-factor authenticated key exchange protocol with extended security model,” IEEE Transactions on Information Forensics and Security, vol. 12, no. 6, pp. 1382–1392, 2017. [Google Scholar]
12. J. Soares and A. N. Gaikwad, “Fingerprint and iris biometric controlled smart banking machine embedded with GSM technology for OTP,” in Int. Conf. on Automatic Control and Dynamic Optimization Techniques, Pune, India, pp. 409–414, 2016. [Google Scholar]
13. S. K. Hafizul Islam, G. P. Biswas and K. K. Raymond Choo, “Cryptanalysis of an improved smartcard based remote password authentication scheme,” International Journal for Information Sciences, vol. 3, no. 1, pp. 35–40, 2014. [Google Scholar]
14. Q. Tao and R. Veldhuis, “Biometric authentication system on mobile personal devices,” IEEE Transactions on Instrumentation and Measurement, vol. 59, no. 4, pp. 763–773, 2010. [Google Scholar]
15. C. Preethi and H. Om, “Cryptanalysis and extended three-factor remote user authentication scheme in multi-server environment,” Arabian Journal for Science and Engineering, vol. 42, no. 2, pp. 765–786, 2017. [Google Scholar]
16. S. K. Hafizul Islam, “Design and analysis of a three party password-based authenticated key exchange protocol using extended chaotic maps,” International Journal of Information Sciences, vol. 312, pp. 104–130, 2015. [Google Scholar]
17. W. Pan, F. Zheng, Y. Zhao, W. Zhu and J. Jing, “An efficient elliptic curve cryptography signature server with gpu acceleration,” IEEE Transactions on Information Forensics and Security, vol. 12, no. 1, pp. 111–122, 2017. [Google Scholar]
18. J. Jensen and Z. Tan, “Minimum mean-square error estimation of Mel-frequency cepstral features—A theoretically consistent approach,” IEEE/ACM Transactions on Audio, Speech, and Language Processing, vol. 23, no. 1, pp. 186–197, 2015. [Google Scholar]
19. D. Prabakaran and R. Shyamala, “A review on performance of voice feature extraction techniques,” in 3rd Int. Conf. on Computing and Communications Technologies, Chennai, Tamilnadu, India, pp. 221–231, 2019. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |