 Open Access
Open Access
ARTICLE
Adaptive Reversible Visible Watermarking Based on Total Variation for BTC-Compressed Images
1 School of Computer Science, Hunan First Normal University, Changsha, 410205, China
2 Hunan Provincial Key Laboratory of Informationization Technology for Basic Education, Changsha, 410205, China
3 Department of Applied Mathematics and Statistics, College of Engineering and Applied Sciences, Stony Brook University, NY 11794, USA
* Corresponding Author: Hengfu Yang. Email:
Computers, Materials & Continua 2023, 74(3), 5173-5189. https://doi.org/10.32604/cmc.2023.034819
Received 28 July 2022; Accepted 22 September 2022; Issue published 28 December 2022
Abstract
Few previous Reversible Visible Watermarking (RVW) schemes have both good transparency and watermark visibility. An adaptive RVW scheme that integrates Total Variation and visual perception in Block Truncation Coding (BTC) compressed domain, called TVB-RVW is proposed in this paper. A new mean image estimation method for BTC-compressed images is first developed with the help of Total Variation. Then, a visual perception factor computation model is devised by fusing texture and luminance characteristics. An adaptive watermark embedding strategy is used to embed the visible watermark with the effect of the visual perception factor in the BTC domain. Moreover, a lossless embedding method of the encrypted visible watermark is exploited to deter illegal watermark removal. The visible watermark can be removed since the visual perception factor and the estimated mean image remain unchanged before and after watermark embedding. Extensive experiments validate the superiority of the proposed algorithm over previous RVW schemes in BTC in terms of the visual quality of watermarked images and watermark visibility, and it can achieve a good balance between transparency and watermark visibility.Keywords
Visible watermarking is an important branch of digital watermarking techniques and has been widely concerned by experts in information security [1,2]. Unlike invisible watermarking [3–6], visible watermarking embeds a visual copyright pattern into the host visual media translucently and protect the copyright of multimedia data in a visually recognizable way. So, visible watermarks are used to instantly prevent misuse of visual media by providing visual copyright notice [7–10]. The visible watermarking technique can be classified into irreversible and Reversible Visible Watermarking (RVW) according to whether the original image can be recovered. So far, many irreversible visible watermarking algorithms have been reported in the literature [11–15]. However, in some specific applications such as medical imagery, remote sensing, and law enforcement, any permanent visual overlaying on the host media by visible watermarking is not acceptable. In these scenarios, RVW is needed because authorized users want to access original high-definition visual media data. In RVW, the embedded visible watermark can be easily recognized by human eyes, and authorized users can obtain original multimedia data by removing the visible watermark superimposed on the host multimedia [16,17]. An example of RVW is: in a medical imaging system, for convenience of efficient management of massive patient's medical images, a visible watermark with patient's basic personal information is required to overlay into the medical image translucently. But authorized doctors should be admitted to access original medical image data for the need of medical diagnostics. So, the visible watermark is required to be removable by authorized users. Another application of RVW is: In remote sensing or military imagery applications, in order not to expose image details to the public, a visible watermark is asked to be translucently embedded into the region of interest in original images. since these remote sensing images and military images are very difficult to obtain and each pixel is very vital to the final image analysis and judgment. In this case, original images are needed for accurate image analysis. Thus, the RVW scheme is required here.
Early lossless watermarking or reversible watermarking schemes mainly focus on invisible watermarking techniques [18–21]. During the past decades, researchers have studied various RVW schemes [22–26]. General RVW algorithms (also called removable visible watermarking and lossless visible watermarking) should satisfy some basic requirements including watermark visibility, transparency, robustness, reversibility, and security [27–29].
In recent years, as a powerful and widely used communication medium, digital images have been widely used on the Internet and in some image processing applications. They are increasingly playing an important role in our daily life. At the same time, copyright infringements of digital images on the Internet become a serious problem with the rapid dissemination of digital images. Compared with the irreversible visible watermarking scheme, reversible visible watermarking techniques provide a more effective solution to deter copyright infringement because of the reversibility of original images. Due to the simplicity of Block Truncation Coding (BTC) image compression, RVW schemes based on BTC have been proposed to enhance the practicability, but few of these RVW schemes can obtain high transparency and visual quality of the visible watermark. To further obtain satisfactory visual quality and good watermark visibility of watermarked images, a new RVW scheme suitable for BTC-compressed images is developed. The total variation image inpainting method is adopted to get a mean image unaffected by watermark embedding for reversibility. A new visual perception computation model dependent on BTC codes of the mean image is used for adaptive visible watermark embedding to obtain a good visual quality of watermarked images.
This paper is organized as follows. In Section 2 related works are discussed. Section 3 gives a brief introduction to BTC coding and total variation image inpainting. Section 4 describes the proposed RVW scheme. Experiments are given in Section 5. Section 6 concludes the paper.
As an effective method for copyright protection of digital images on the Internet, the Reversible Visible Watermarking (RVW) technique has received more and more attention from researchers all over the world. Several RVW techniques have been proposed in the past [22–24]. The concept of reversible visible watermarks was first proposed by IBM in 1997 [26]. In 2006, Hu et al. [25] proposed a reversible visible watermarking algorithm based on lossless data compression. It reversibly hides the payload containing two reconstruction data packets for recovering the watermark region and the non-watermark region in the non-watermark region. Furthermore, the specially designed user key guarantees unauthorized users cannot remove the visible watermark. Yip et al. [17] designed two lossless visible watermarking algorithms by using bijective intensity mapping function and circular pixel shift, respectively. To improve the visibility of the watermark in the high variance region, Tsai et al. [30] proposed a reversible visible watermarking algorithm by mapping pixel values of the original image to a small range to generate a visible watermarked image. To achieve the ‘lossless’ property, lossless compression and reversible data embedding are employed to losslessly embed some side information into the visible watermarked image. Yang et al. [31] proposed an RVW scheme that overlaps the watermark onto a user-specified region of the original image under the control of human visual system-based scaling factors. To achieve reversibility, the reconstruction packet containing the difference image between the original image and its approximate version is losslessly hidden in the non-watermark region. Tsai et al. [32] proposed a secure reversible visible watermarking method that designs a pixel mapping function to superpose translucently a binary watermark image on the host image. This method uses lossless data hiding to embed the recovery data and hash value for original image recovery and image authentication, respectively. Liu et al. [33] designed a generic framework of the lossless visible watermark by the use of deterministic one-to-one compound mappings of image pixel values. The compound mappings are reversible which makes the lossless recovery of original images possible. Zhang et al. [34] developed a lossless data-hiding method based on the difference value shift, and then it is applied to implement a reversible visible watermarking scheme by losslessly embedding some additional data about the watermark and the host image. Qi et al. [9] proposed a reversible visible image watermarking scheme based on the Human Visual System (HVS) which losslessly embeds a visible watermark into a region of interest (ROI) of the original image by the use of the difference expansion method. During watermark embedding, the Visual Effect Factor (VEF) based on HVS is computed by the estimated watermarked and non-watermarked blocks within the neighborhood of each block and used to adaptively adjust the pixel values. The above-mentioned RVW schemes embed the visible watermark into the spatial domain [9,17,27,30–34]. Generally speaking, their robustness has not as good as that of transform-based RVW methods. Hu et al. [35] proposed a user-key-dependent removable visible watermarking system in the wavelet domain in 2006. It embeds the visible watermark into low-frequency subbands and high-frequency subbands, respectively. The user-key-controlled pre-watermarking template makes unauthorized watermark removal almost impossible. Under the action of the wavelet coefficient Contrast Sensitive Function (CSF), Chang et al. [36] proposed an RVW algorithm by combining Discrete Wavelet Transform (DWT) and vector quantization. But the watermark removal requires some additional information such as the original watermark, the codebook, the DWT, and CSF. Ying et al. [37] proposed a removable visible watermarking scheme in the Discrete Cosine Transform (DCT) domain. The adaptive scaling and embedding factors are computed according to the features of the host image and the preprocessed watermark. The preprocessed watermark is adaptively embedded into the host image. The key controlled preprocessed watermark design can deter the illegal removal of the visible watermark. Lin et al. [38] proposed a DWT-based removable visible watermark mechanism by adopting the subsampling technique. The watermark strength is computed by the pair pool generated by the individual user key and the watermark is embedded into low-frequency sub-bands. The key-dependent random pairs generation ensures that only authorized users with the correct key can remove the visible watermark to restore the host image. Rangel-Espinoza et al. [8] proposed a removable visible watermarking scheme in the DCT domain based on a dual watermark technique. The visible watermark is adaptively and translucently embedded into the host image. Moreover, lossless hiding of the original watermark in an invisible manner based on the Quantization Index Modulation-Dither Modulation (QIM-DM) technique ensures that it can prevent illegal visible watermark removal. Lin et al. [39] proposed an RVW algorithm in the DCT domain that generates a lossless visible watermark by modifying the DCT coefficients of an image to generate a lossless visible watermark. It improves security against visible watermark removable attacks by using a random permutation matrix to factorize the transformation. RVW schemes in the compressed domain are more practical than those of RVW methods in the spatial domain and transform domain. Yang et al. proposed a removable visible watermarking algorithm in Block Truncation Coding (BTC) domain [40]. It computes the embedding factors according to the features of the predicted image and the visible watermark is embedded into two quantization levels of BTC codes. The embedding of an encrypted watermark prevents illegal watermark removal. Mohammad et al. [41] proposed an AMBTC-based reversible visible watermarking scheme that embeds a visible watermark into BTC codes of the original image by using adaptive pixel circular shift operation. The stability of visual perception factors ensures that it can remove the visible watermark from the watermarked image. Due to the simplicity of BTC, embedding the visible watermark into BTC codes of digital images is becoming more and more necessary and attractive. But previous RVW algorithms did not take full of advantage of human perception.
In the proposed RVW method, Absolute Moment BTC (AMBTC) is adopted. AMBTC is presented by Lema et al. [42] and preserves the higher mean and lower mean of an image sub-block.
In the encoding phase, the image with size M × N is divided into non-overlapping sub-blocks with size s × s. Let
Pixels in the image block are then classified into two ranges of values. The higher area contains these pixels whose pixel values are greater than or equal to the block mean value
where q stands for the number of pixels whose values are greater than or equal to the mean value.
Taking
3.2 Total Variation Image Inpainting
In 2002, Chan and Shen presented an image inpainting model based on Total Variation (TV). Fig. 1 shows a diagram of TV-based image inpainting, where D is an inpainting area with piecewise smooth boundary Γ, and the fixed closed domain E in the complement
underfitting constraint on E.
where
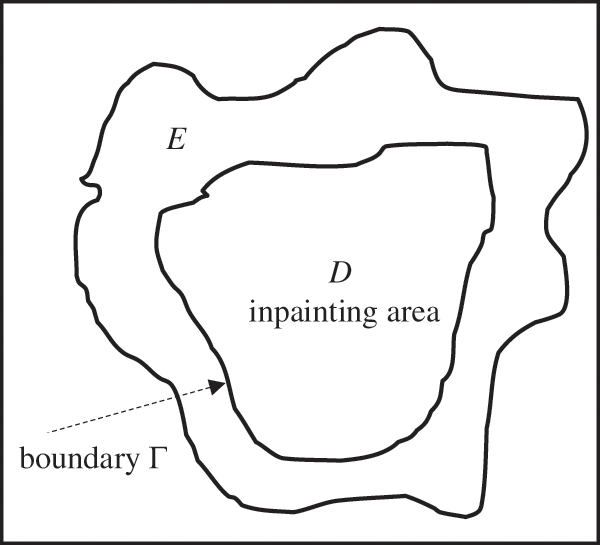
Figure 1: The TV image inpainting model
Assume that
The constrained optimization problem in Eq. (6) can be transformed into an unconstrained one by using the Lagrange multiplier method.
where λ is the Lagrange multiplier. The Euler–Lagrange equation for the energy functional
For all
Given a target pixel O and its four adjacent pixels E, N, W, S. Let e, n, w, s denote the corresponding four virtual midway points.
Let
where
The Gauss-Jacobi iteration method is adopted, at each step k,
4 Proposed Reversible Visible Watermarking Scheme
The proposed TVB-RVW scheme includes two subroutines: watermark embedding and watermark removal. In the watermark embedding process, TV-based mean image estimation and visual perceptual factor computation are first carried out. Then the visible watermark embedding and lossless data hiding of the encrypted watermark are subsequently executed. The watermark removal process consists of visible watermark extraction and original image recovery. Fig. 2 illustrates the schematic diagram of the proposed TVB-RVW scheme.
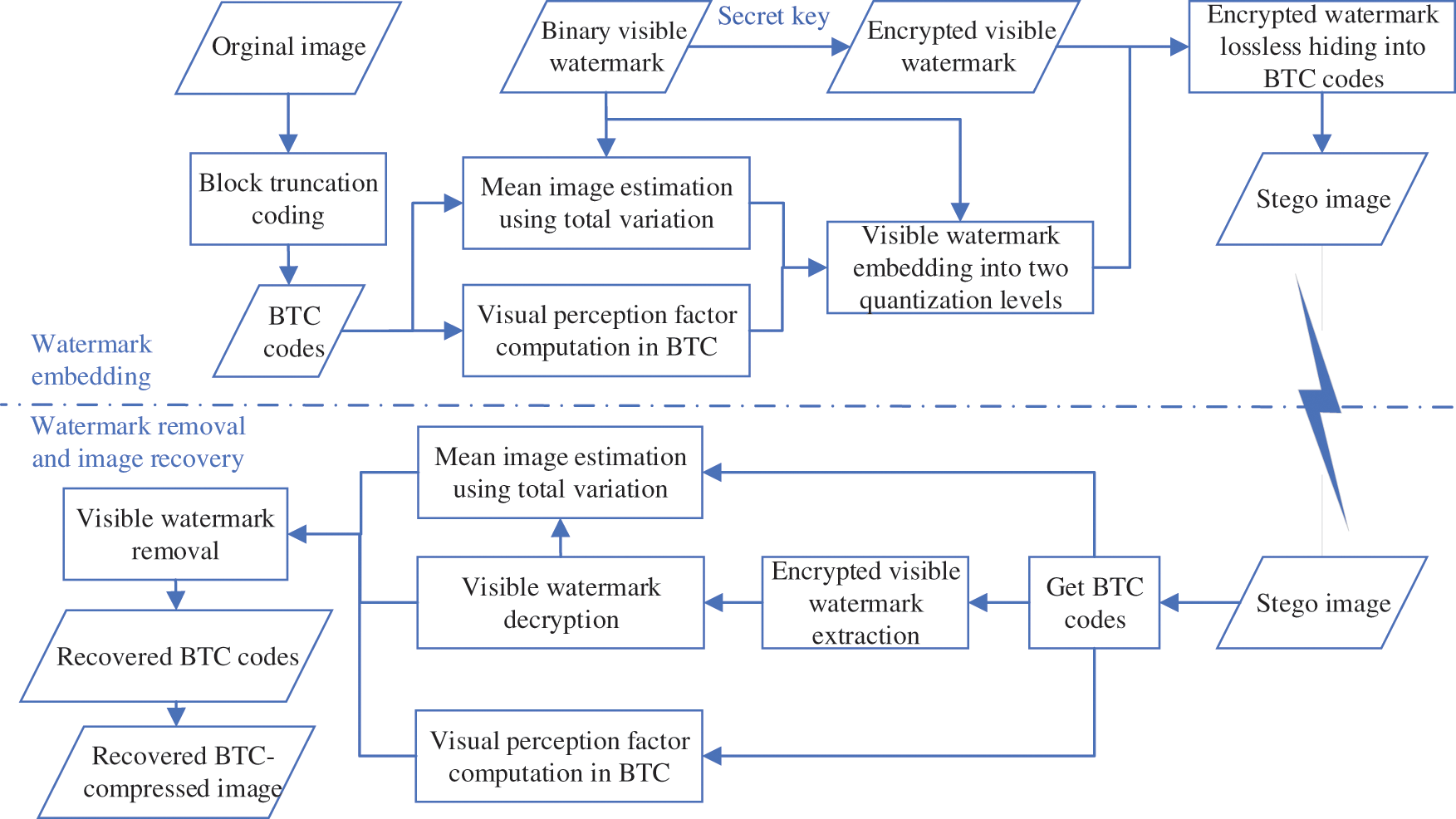
Figure 2: Block diagram of the proposed TVB-RVW scheme
A visible watermark is embedded into BTC codes by adaptively adjusting the quantization levels. TV-based mean image estimation and visual perception factor computation ensure reversibility, and encrypted watermark embedding can keep unauthorized users from removing the visible watermark.
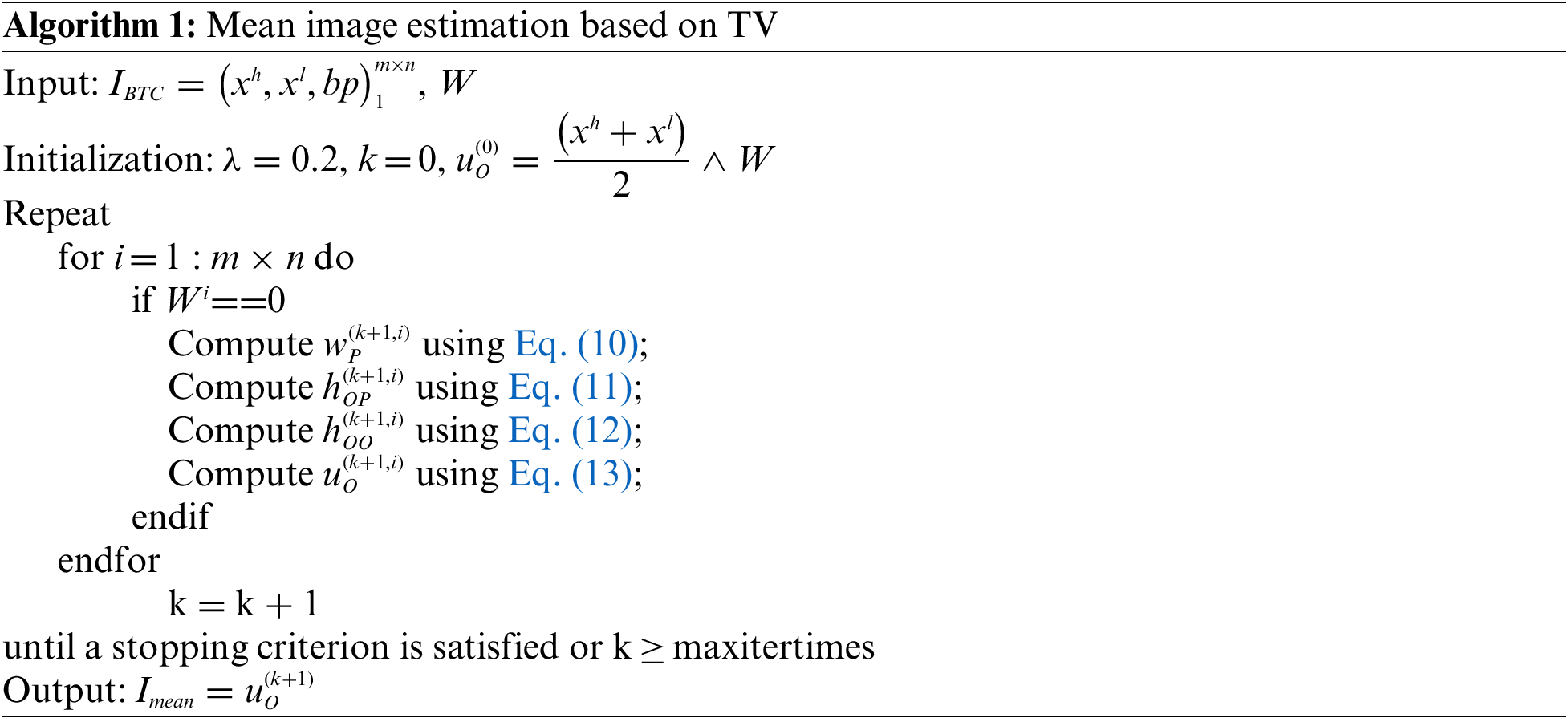
4.1.1 Mean Image Estimation Using Total Variation
To achieve reversibility, an estimated version of the original image needs to be generated which is not affected by watermark embedding. Applying the image inpainting method based on total variation to obtain the estimated mean image, we have Algorithm 1.
4.1.2 Visual Perception Factor Computation
To adaptively embed a visible watermark into the BTC compressed image, a visual perception factor computation model in the BTC domain is developed. First, given the ith image sub-block
The number of bit transitions depicts the texture characteristics of the image sub-block. So, it can be used as a texture factor
Similarly, calculate the luminance characteristics of the ith sub-block based on the bit-plane by
where
The visual perception factor for the ith sub-block can be gotten by integrating the texture and luminance characteristics. It can be written as
Given an interval
The detailed procedures are depicted in Algorithm 2.

4.1.3 Visible Watermark Embedding
To obtain a good visual quality of the watermarked image, the visible watermark is adaptively embedded into the BTC codes with the effect of visual perception factors. Given watermark weight
where
The detailed visible watermark embedding procedure is described in Algorithm 3.

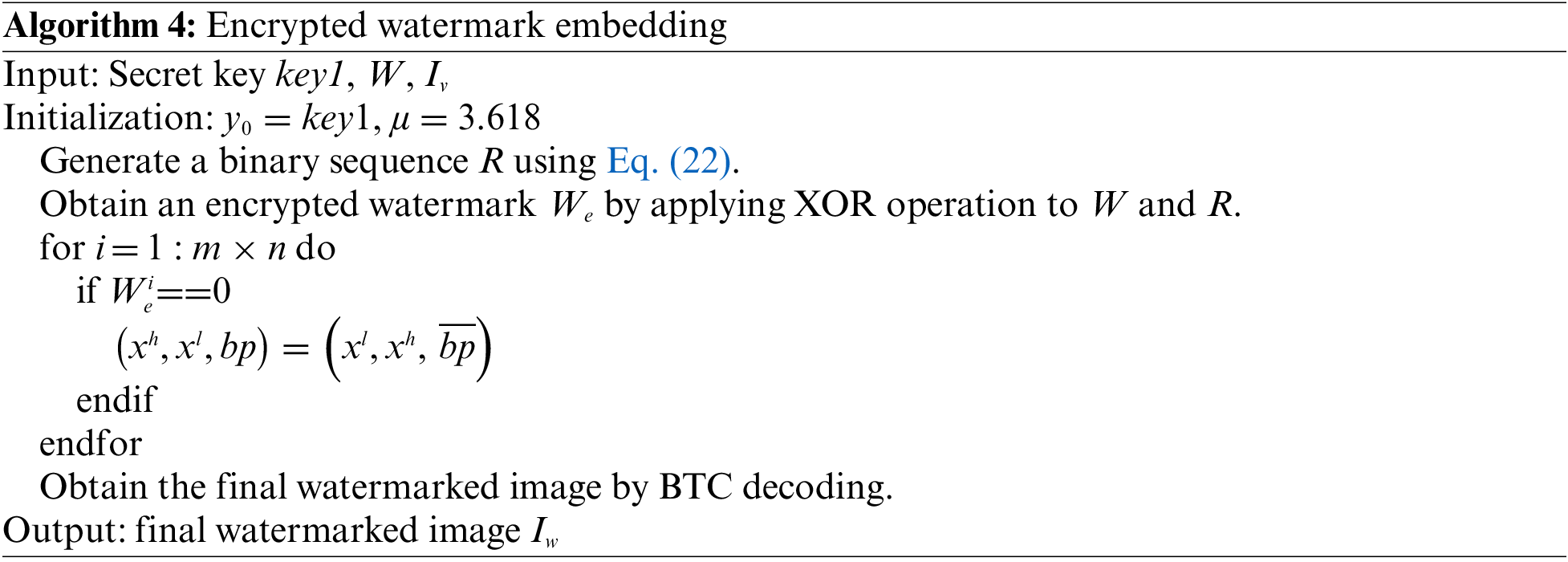
4.1.4 Lossless Data Hiding of Encrypted Visible Watermark
To prevent unauthorized users from removing the visible watermark, the encrypted watermark is further losslessly hidden into the BCT codes. Given the initial condition and the bifurcation parameter μ, the chaotic logistic map shown as follows can be used to encrypt the watermark signal.
where, the bifurcation parameter μ should be chosen from the half-open interval (3.599456, 4].
Subsequently, we can use Algorithm 4 to embed the encrypted watermark by employing the lossless data hiding method.
In the watermark removal phase, we first extract the visible watermark, and then remove it and recover the original BTC compressed image. the main steps are listed below.
(1) Extract encrypted watermark signal
(2) Get the visible watermark by decrypting the encrypted watermark with the secret key.
(3) Produce the estimated mean image
(4) Remove the visible watermark (see Algorithm 5) and obtain a recovered BTC-compressed image (see Algorithm 6). The watermark removal approach can be written as
4.2.1 Visible Watermark Extraction
Given the user secret key, the proposed scheme can extract the visible watermark from the watermarked image. The detailed strategy is illustrated in Algorithm 5.

The same mean image can be generated based on the watermarked image with the visible watermark

In this section, the TVB-RVW scheme is evaluated by a series of experiments on several aspects such as the visual quality of the watermarked image, watermark visibility, robustness, and security. These experiments are conducted on some 512 × 512 × 8bits test images which range from fairly smooth images to highly textured ones. The visible watermark is a binary image with the size of 128 × 128 as shown in Fig. 3a. Figs. 3b–3d shows some BTC test images referred to as “Lena”, “jet”, “Baboon”, respectively. In the experiments, the parameter

Figure 3: Visible watermark and some test images
Peak Signal to Noise Ratio (PSNR) values are adopted to evaluate the transparency of the BTC-compressed watermarked images produced by the TVB-RVW scheme. Figs. 4a–4c illustrate the watermarked images for some BTC-compressed images, referred to as “Lena”, “jet”, “Baboon”, respectively. From Fig. 4, one can observe that the watermarked images have satisfactory visual quality, which preserves the visual perceptual content of original BTC-compressed images very well.
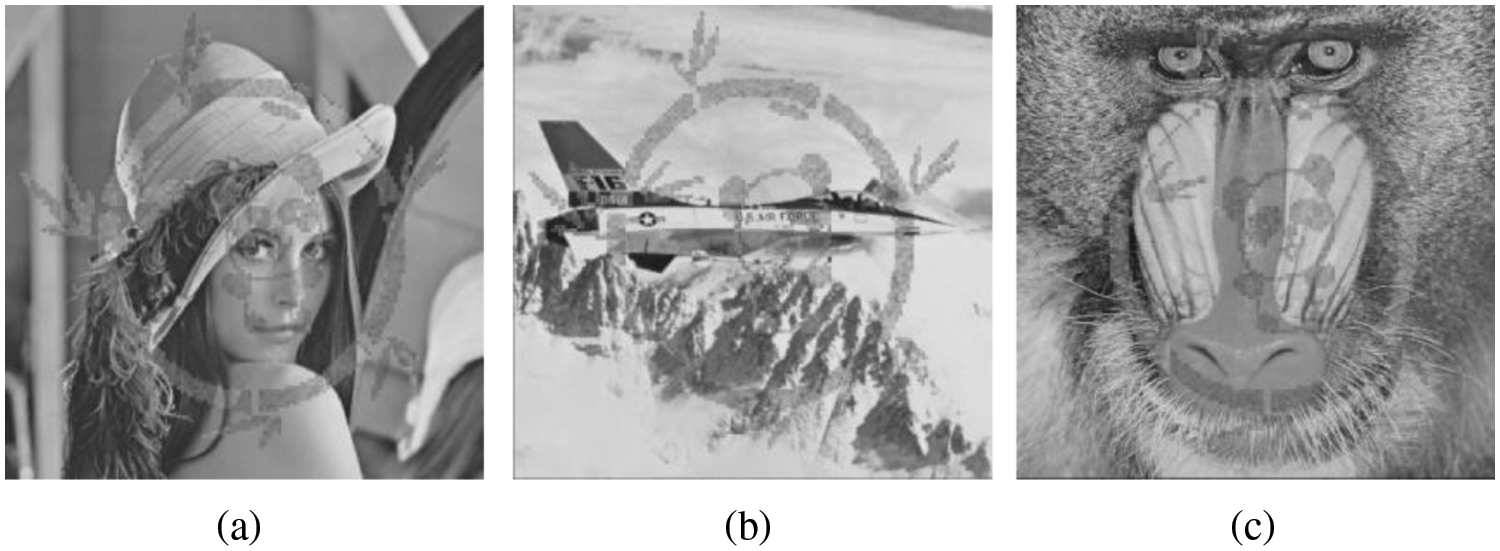
Figure 4: Watermarked images
Watermark visibility is one of the important attributions of visible watermarking techniques. Good watermark visibility means high contrast of the watermark content as well as the satisfactory visual quality of watermarked images. Simply, one can judge roughly the watermark visibility by observing watermark images produced by the TVB-RVW scheme as shown in Fig. 4. The visible watermark is translucent and adaptive to the content of host images with various texture types. Moreover, Fig. 5 illustrates the difference images of the original BTC-compressed images and corresponding watermarked images. To provide a good visual effect, the difference images are magnified by 10 times. From Fig. 5, it can be noticed that the watermark strength is adaptive to the perceptual content of images.
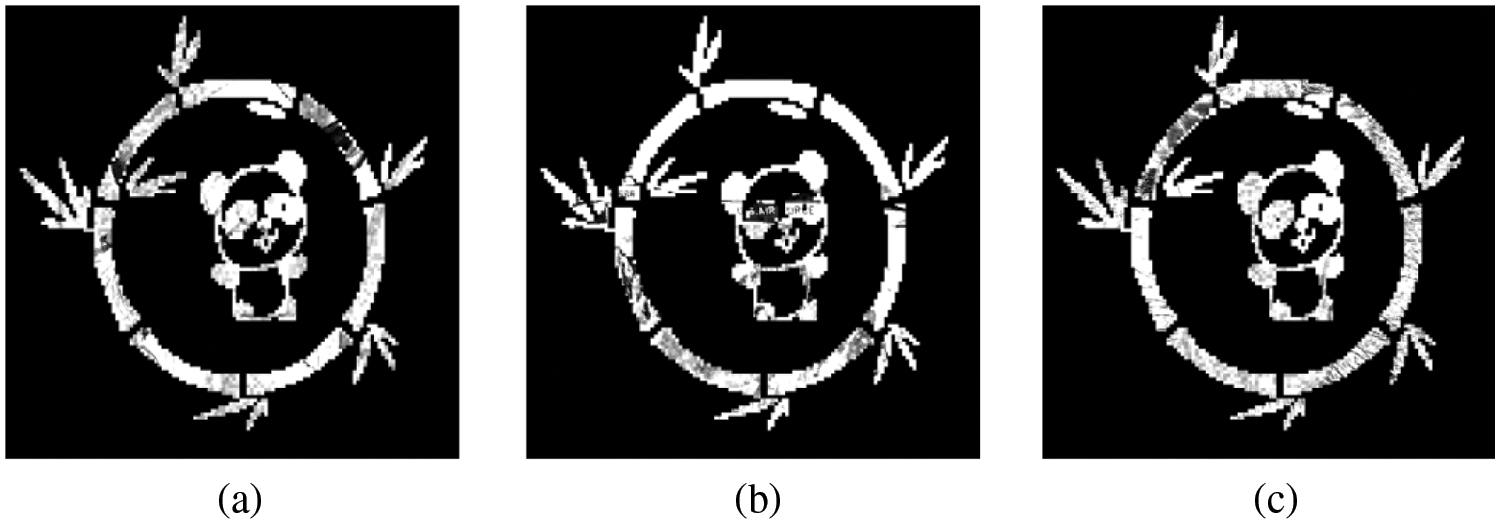
Figure 5: Difference images between original BTC-compressed images and watermarked images
Fig. 6 illustrates these attacked experimental results for the Lena BTC-compressed image. It can be observed that one can recognize the visible watermark clearly from the attacked watermarked images. According to the experiments, these above-mentioned signal processing attacks cannot completely delete the superimposed visible watermark. So, it can be concluded that the proposed TVB-RVW scheme is robust against common signal processing attacks.

Figure 6: Robustness against common signal processing attacks. histogram equalization, Laplacian sharpening, 5 × 5 median filtering
The PSNR values (dB) of recovery images are shown in Table 1. The average PSNR value for illegal removal and legal removal is 17.33 and 58.91 dB, respectively. The PSNR values for illegal removal are much lower than those for legal removal. This shows that illegal removal results for different types of images have poor visual quality and unauthorized users cannot completely delete the visible watermark by illegal watermark removal.
In this section, the visibility, robustness, and security results were compared with the results from the previous RVW methods, referred to as RVWBCM [40] and Mohammad et al.'s method [41]. For a fair comparison, all the algorithms were embedded with the same visible watermark. To more effectively compare the visibility of different visible watermarking schemes, an objective measurement called Normalized Energy (NE) [40] is adopted to evaluate the visibility. Table 2 shows the visibility results of different RVW schemes on different test images. According to Table 2, it can be seen that the watermarked images generated by the TVB-RVW algorithm have relatively higher visibility than existing RVW schemes based on BTC.
Furthermore, Fig. 7 depicts the joint transparency and visibility experimental results under various RVW methods. The transparency vs. visibility curve of the TVB-RVW is on the top right corner of Fig. 7 One can notice that the proposed TVB-RVW scheme outperforms other BTC-based RVW schemes in terms of comprehensive transparency vs. visibility performance. This is partly because those optimal visual perception factors are computed in BTC compressed domain.
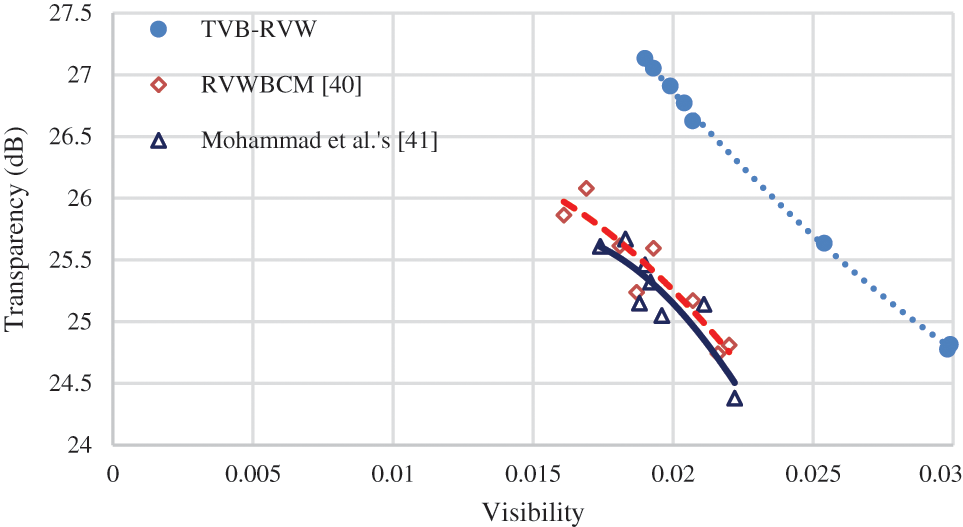
Figure 7: PSNR values vs. watermark visibility under various algorithms
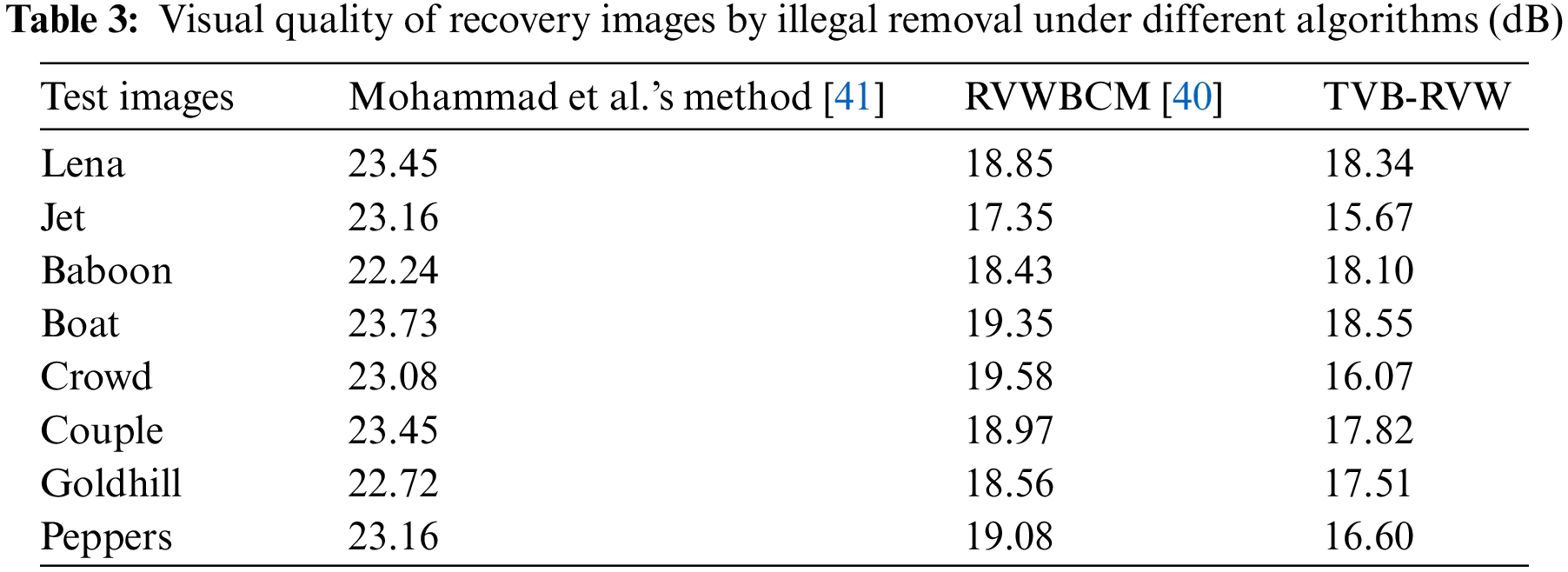
Finally, the visual quality of illegal removal results generated by different RVW algorithms has been measured by PSNR values. The corresponding experimental results of illegal removal are illustrated in Table 3. The TVB-RVW has the lowest PSNR values of illegal removal results than those of existing RVW approaches. It implies that unauthorized users cannot completely remove the visible watermark and the presented RVW scheme performs better in security.
In this paper, a novel RVW algorithm suitable for BTC-compressed images is proposed. A mean image estimation method based on total variation is presented to achieve reversibility. To achieve adaptive embedding, a visual perception factor computation model based on the bit-planes of BTC codes is developed. The visible watermark can be completely removed by authorized users because the visual perception factors remain unchanged before and after watermark embedding. Subsequently, the lossless embedding strategy of the encrypted watermark ensured its security. The proposed scheme has higher imperceptibility and visibility than existing BTC-based RVW schemes. It can be applied for copyright protection of digital visual media on the Internet. Future works will extend the scheme to other different types of images by employing visual computing in the compressed domain and weighted total variation.
Funding Statement: This work was supported in part by the National Natural Science Foundation of China under Grant 61872408, the Natural Science Foundation of Hunan Province under Grant 2020JJ4238, the Social Science Foundation of Hunan Province under Grant 19YBA098, and the Research Fund of Hunan provincial key laboratory of informationization technology for basic education under Grant 2015TP1017.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. D. Zhang, G. Yang, F. Li, J. Wang and A. K. Sangaiah, “Detecting seam carved images using uniform local binary patterns,” Multimedia Tools and Applications, vol. 79, no. 13, pp. 8415–8430, 2020. [Google Scholar]
2. F. Zhu, Y. Ren, Q. Wang and J. Xia, “Preservation mechanism of network electronic records based on broadcast-storage network in urban construction,” Journal of New Media, vol. 1, no. 1, pp. 27–34, 2019. [Google Scholar]
3. Z. Xia, X. Wang, B. Han, Q. Li, X. Wang et al., “Color image triple zero-watermarking using decimal-order polar harmonic transforms and chaotic system,” Signal Processing, vol. 180, pp. 107864, 2021. [Google Scholar]
4. D. Liu, Q. Su, Z. Yuan and X. Zhang, “A blind color digital image watermarking method based on image correction and eigenvalue decomposition,” Signal Processing: Image Communication, vol. 95, pp. 116292, 2021. [Google Scholar]
5. I. K. Yeo and H. J. Kim, “Generalized patchwork algorithm for image watermarking,” Multimedia Systems, vol. 9, no. 3, pp. 261–265, 2003. [Google Scholar]
6. L. Xiang, W. Wu, X. Li and C. Yang, “A linguistic steganography based on word indexing compression and candidate selection,” Multimedia Tools and Applications, vol. 77, no. 21, pp. 28969–28989, 2018. [Google Scholar]
7. R. Thanki, S. Borra, V. Dwivedi and K. Borisagar, “A RONI based visible watermarking approach for medical image authentication,” Journal of Medical Systems, vol. 41, no. 9, pp. 143, 2017. [Google Scholar]
8. K. Rangel-Espinoza, E. Fragoso-Navarro, C. Cruz-Ramos, R. Reyes-Reyes, M. Nakano-Miyatake et al., “Adaptive removable visible watermarking technique using dual watermarking for digital color images,” Multimedia Tools and Applications, vol. 77, no. 11, pp. 13047–13074, 2018. [Google Scholar]
9. W. Qi, G. Yang, T. Zhang and Z. Guo, “Improved reversible visible image watermarking based on HVS and ROI-selection,” Multimedia Tools and Applications, vol. 78, no. 7, pp. 8289–8310, 2019. [Google Scholar]
10. E. Fragoso-Navarro, K. Rangel-Espinoza, M. Nakano-Miyatake, M. Cedillo-Hernandez and H. Perez-Meana, “Seam carving based visible watermarking robust to removal attacks,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 7, pp. 4499–4513, 2022. [Google Scholar]
11. B. -B. Huang and S. -X. Tang, “A contrast-sensitive visible watermarking scheme,” IEEE Multimedia, vol. 13, no. 2, pp. 60–66, 2006. [Google Scholar]
12. Y. Hu and S. Kwong, “Wavelet domain adaptive visible watermarking,” Electronics Letters, vol. 37, no. 20, pp. 1219–1220, 2002. [Google Scholar]
13. H. Santoyo-Garcia, E. Fragoso-Navarro, R. Reyes-Reyes, G. Sanchez-Perez and H. Perez-Meana, “An automatic visible watermark detection method using total variation,” in Proc. Int. Workshop on Biometrics & Forensics, Coventry, UK, pp. 1–5, 2017. [Google Scholar]
14. C. Y. Weng, Y. H. Zhang, L. C. Lin and S. -J. Wang, “Visible watermarking images in high quality of data hiding,” Journal of Supercomputing, vol. 66, no. 2, pp. 1033–1048, 2013. [Google Scholar]
15. N. Wang, Z. Li, X. Cheng and Z. Li, “Diffusion weighted image reversible visible watermarking algorithm based on support vector regression,” in Proc. 14th IEEE Int. Conf. on Signal Processing (ICSP), Beijing, China, pp. 1144–1148, 2018. [Google Scholar]
16. W. Qi, S. Guo, Y. Liu, X. Wang, and Z. Guo, “Research on reversible visible watermarking algorithms based on vectorization compression method,” The Computer Journal, vol. 65, no. 5, pp. 1320–1337, 2022. [Google Scholar]
17. S. Yip, O. C. Au, C. Ho and H. Wong, “Lossless visible watermarking,” in Proc. 2006 IEEE Int. Conf. on Multimedia and Expo, Toronto, ON, Canada, pp. 853–856, 2006. [Google Scholar]
18. S. Yi and Y. Zhou, “Separable and reversible data hiding in encrypted images using parametric binary tree labeling,” IEEE Transactions on Multimedia, vol. 21, no. 1, pp. 51–64, 2019. [Google Scholar]
19. W. Zhang, H. Wang, D. Hou and N. Yu, “Reversible data hiding in encrypted images by reversible image transformation,” IEEE Transactions on Multimedia, vol. 18, no. 8, pp. 1469–1479, 2016. [Google Scholar]
20. X. Zhang, “Reversible data hiding with optimal value transfer,” IEEE Transactions on Multimedia, vol. 15, no. 2, pp. 316–325, 2013. [Google Scholar]
21. X. Wang, X. Li and Q. Pei, “Independent embedding domain based two-stage robust reversible watermarking,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 30, no. 8, pp. 2406–2417, 2019. [Google Scholar]
22. Z. Xu, L. Li and G. Xie, “Research on reversible visible watermarking technique,” in Proc. Information and Business Intelligence, Berlin, Heidelberg, pp. 91–98, 2012. [Google Scholar]
23. P. L. A. Merlin, V. Rajamani and V. E. Jayanthi, “Architecture design and field programmable gate array implementation of removable visible image watermarking for digital camera images using a private key,” Journal of Imaging Science and Technology, vol. 58, no. 6, pp. 60502-1–60502-10(102014. [Google Scholar]
24. Y. L. Wang and W. H. Tsai, “Lossless visible watermarking for copyright protection of H.263 videos," in Proc. 2006 19th IPPR Conf. on Computer Vision, Graphics and Image Processing, Madurai, India, pp. 820–824, 2006. [Google Scholar]
25. Y. Hu and B. Jeon, “Reversible visible watermarking and lossless recovery of original images,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 16, no. 11, pp. 1423–1429, 2006. [Google Scholar]
26. F. Mintzer, J. B. Lotspiech and N. Morimoto, “Safeguarding digital library contents and users: Digital watermarking,” 1997. [Online]. Available: http://www.dlib.org/dlib/december97/ibm/12lotspiech.html. [Google Scholar]
27. Y. Hu and B. Jeon, “Reversible visible watermarking technique for images,” in Proc. 2006 Int. Conf. on Image Processing, Atlanta, GA, USA, pp. 2577–2580, 2006. [Google Scholar]
28. E. Fragoso-Navarro, M. Cedillo-Hernández, M. Nakano-Miyatake, A. Cedillo-Hernández and H. M. Pérez-Meana, “Visible watermarking assessment metrics based on just noticeable distortion,” IEEE Access, vol. 6, pp. 75767–75788, 2018. [Google Scholar]
29. S. P. Mohanty, K. R. Ramakrishnan and M. S. Kankanhalli, “A DCT domain visible watermarking technique for images,” in Proc. 2000 IEEE Int. Conf. on Multimedia and Expo, New York, NY, USA, vol. 2, pp. 1029–1032, 2000. [Google Scholar]
30. H. Tsai and L. Chang, “A high secure reversible visible watermarking scheme,” in Proc. Int. Conf. on Multimedia and Expo, Beijing, China, pp. 2106–2109, 2007. [Google Scholar]
31. Y. Yang, X. Sun, H. Yang, C. Li and R. Xiao, “A contrast-sensitive reversible visible image watermarking technique,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 19, no. 5, pp. 656–667, 2009. [Google Scholar]
32. H. M. Tsai and L. W. Chang, “Secure reversible visible image watermarking with authentication,” Signal Processing: Image Communication, vol. 25, no. 1, pp. 10–17, 2010. [Google Scholar]
33. T. -Y. Liu and W. -H. Tsai, “Generic lossless visible watermarking−A new approach,” IEEE Transactions on Image Processing, vol. 19, no. 5, pp. 1224, 2010. [Google Scholar]
34. X. Zhang, S. Wang and G. Feng, “Reversible visible watermarking with lossless data embedding based on difference value shift,” Intelligent Automation and Soft Computing, vol. 17, no. 2, pp. 233–243, 2011. [Google Scholar]
35. Y. Hu, S. Kwong and J. Huang, “An algorithm for removable visible watermarking,” IEEE Trans. Circuits Syst. Video Technol., vol. 16, no. 1, pp. 129–133, 2006. [Google Scholar]
36. C. -C. Chang, C. -C. Lin and K. -M. Li, “A removable visible watermark for digital images,” Journal of Computers, vol. 21, no. 3, pp. 37–49, 2010. [Google Scholar]
37. Y. Ying, X. Sun, H. Yang and C. T. Li, “Removable visible image watermarking algorithm in the discrete cosine transform domain,” Journal of Electronic Imaging, vol. 17, no. 3, pp. 033008-1–033008-11, 2008. [Google Scholar]
38. P. Y. Lin, Y. H. Chen, C. C. Chang and J. S. Lee, “Contrast-adaptive removable visible watermarking (CARVW) mechanism,” Image and Vision Computing, vol. 31, no. 4, pp. 311–321, 2013. [Google Scholar]
39. Y. K. Lin, C. H. Yang and J. T. Tsai, “More secure lossless visible watermarking by DCT,” Multimedia Tools and Applications, vol. 77, pp. 8579–8601, 2018. [Google Scholar]
40. H. Yang and J. Yin, “A secure removable visible watermarking for BTC compressed images,” Multimedia Tools and Applications, vol. 74, no. 6, pp. 1725–1739, 2015. [Google Scholar]
41. N. Mohammad, X. Sun, H. Yang, J. Yin, G. Yang et al., “Lossless visible watermarking based on adaptive circular shift operation for BTC-compressed images,” Multimedia Tools and Applications, vol. 76, pp. 13301–13313, 2017. [Google Scholar]
42. M. Lema and O. Mitchell, “Absolute moment block truncation coding and its application to color images,” IEEE Transactions on Communications, vol. 32, no. 10, pp. 1148–1157, 1984. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools