 Open Access
Open Access
ARTICLE
Designing Pair of Nonlinear Components of a Block Cipher over Gaussian Integers
1 Department of Mathematics, Quaid-I-Azam University, Islamabad, 45320, Pakistan
2 Escuela de Matemáticas y Estadística, Universidad Pedagógica y Tecnológica de Colombia, Tunja, 150003, Columbia
* Corresponding Author: Muhammad Sajjad. Email:
Computers, Materials & Continua 2023, 75(3), 5287-5305. https://doi.org/10.32604/cmc.2023.035347
Received 17 August 2022; Accepted 24 October 2022; Issue published 29 April 2023
Abstract
In block ciphers, the nonlinear components, also known as substitution boxes (S-boxes), are used with the purpose of inducing confusion in cryptosystems. For the last decade, most of the work on designing S-boxes over the points of elliptic curves has been published. The main purpose of these studies is to hide data and improve the security levels of crypto algorithms. In this work, we design pair of nonlinear components of a block cipher over the residue class of Gaussian integers (GI). The fascinating features of this structure provide S-boxes pair at a time by fixing three parameters. But the prime field dependent on the Elliptic curve (EC) provides one S-box at a time by fixing three parameters and . The newly designed pair of S-boxes are assessed by various tests like nonlinearity, bit independence criterion, strict avalanche criterion, linear approximation probability, and differential approximation probability.Keywords
Cryptography was widely used in military, diplomatic, and government applications until the 1970s. In the 1980s, the telecommunications and financial industries installed hardware cryptographic devices. The mobile phone system was the first cryptographic application in the late 1980s. Nowadays, everyone uses cryptographic applications in their daily lives. Our daily lives are commonly dependent on the secure transmission of information and data. Online shopping, cell phone messages and calls, ATMs, electronic mail, facsimile, wireless media, and data transfer over the internet all require a system to maintain the secrecy and integrity of private information. In an antagonistic environment, cryptography provides a way for everyone to communicate securely. Cryptography plays a major role in the security of data. Encryption of a message ensures that the meaning is concealed in it so that someone who reads the message cannot understand anything out of it unless people crack the message [1].
In cryptography, the S-box plays a major role in maintaining safe communication. In 1949, Shannon proposed the concept of an S-box. In creating confusion in data, S-boxes play a key role. According to Shannon, hiding the relationship between the key and cipher text is known as confusion, while hiding the statistical relationship between plain text and cipher text is known as diffusion. In other words, the plain text's non-uniformity in the distribution of individual letters should be redistributed into the cipher text's non-uniformity in the distribution of much larger structures, which is significantly much harder to detect [2].
In literature, for creating confusion very well-known S-boxes are available in data and information, such as data encryption standard (DES), advanced encryption standard (AES), affine power affine, Gray, Skipjack,
A brief description of the latest cryptosystem is approved for general use by the National Institute of Standards and Technology (NIST). It is called the Advanced Encryption Standard (AES) and was adopted, effective May 26, 2002, as the official Federal Information Processing Standard (FIPS) to be used by all U.S. government organizations to protect sensitive information. It is also expected to be used by other organizations, institutions, and individuals all over the world. The enciphering algorithm in AES was designed by two Belgian cryptographers, Dr. Joan Daeman and Dr. Vincent Rijmen. It was given the name Rijndael (pronounced “rhine dahl”). The basic structure of the Rijndael algorithm is that of an iterated block cipher, but with some additional features. Before considering the Rijndael algorithm, we will move towards an iterated block cipher which is present in [4].
For creating confusion on data, for the construction of S-boxes, many researchers used different schemes with algebraic and statistical structures. The authors proposed S-boxes over the permutation of the symmetric group in [5]. The construction of S-boxes over the action of the quotient of a modular group by using a secure scheme is given in [6]. The construction of the S-box based on the subgroup of the Galois field is given in [7]. The author proposed a strong encryption scheme by using a modified Chebyshev map, AES S-boxes, and a symmetric group of permutations [8].
In [9], the authors proposed a new scheme for the construction of the S-box based on the linear fractional transformation (LFT) and permutation function. In [10], the author proposed S-box over the Mobius group and finite field. The author proposed S-box on a nonlinear chaotic map in [11]. The authors proposed S-boxes over the second coordinate of EC in [12]. Adnan et al. [13], designed the construction of a non-linear component of block cipher by means of a chaotic dynamical system and symmetric group. In [14], the author constructed cyclic codes over quaternion integers, these quaternion structures can be helpful for the construction of S-boxes.
An S-box generator is appropriate for cryptographic purposes if it can efficiently make highly dynamic S-boxes with good cryptographic properties or tests like nonlinearity, bit independence criterion, strict avalanche criterion, linear approximation probability, and differential approximation probability. The key contributions of our proposed study are given below:
• Propose an algorithm to generate pair of S-boxes by the cyclic group over the residue class of Gaussian integers.
• Security Analysis.
• The advantages of the proposed algorithm over GI with some of the existing algorithms over EC.
This paper is structured as follows: Basic definitions, cyclic group over the residue class of Gaussian integers, and some fundamental results are elaborated in Section 2. The scheme of the pair of new S-boxes is proposed in Section 3. Analysis of the proposed S-boxes including nonlinearity, bit independence criterion, strict avalanche criterion, linear approximation probability, and differential approximation probability investigated in Section 4. The comparison of the proposed S-boxes with some of the existing S-boxes are given in Section 5. Conclusions and future directions are given in Section 6.
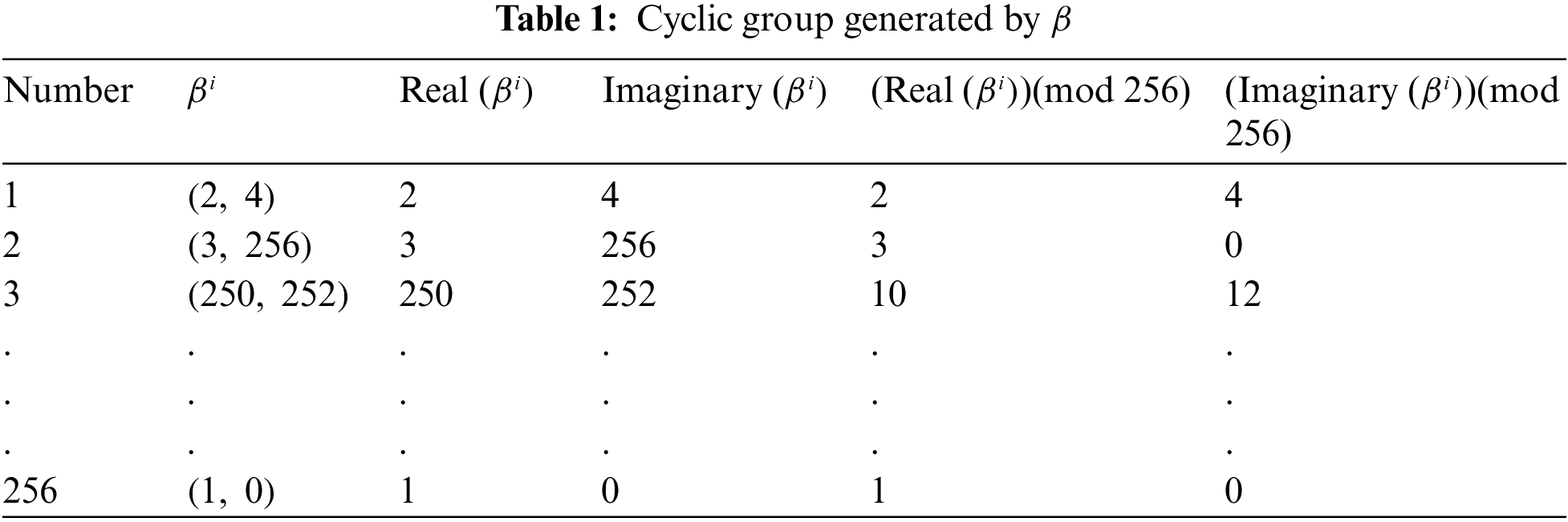
This section provides the key concepts and basic findings that will be used in the study of upcoming sections. First of all, we recall the definition of Gaussian integers, cyclic group over a residue class of Gaussian integers, and some fundamental results.
Gaussian Integers
By following [[15], Section 2], Gaussian integers are a subset of complex numbers which have integers as real and imaginary parts;
1.
2. Multiplicative identity is 1.
3.
Let
A Gaussian integer has only two parts, one is the scalar part
Addition of two Gaussian Integers
Let
Multiplication of two Gaussian Integers
Let
Theorem: In [[15], Section 2], the set of natural numbers for each odd rational prime
Theorem: In [[16], Theorem 6.3], if the norm of a Gaussian integer
Definition: In [[17], Section 2], let
Then,
Where
Theorem: In [[17], Theorem 7.12], let h be a Gaussian prime, and the number of Gaussian integers modulo h is the norm of
Theorem: In [[17], Theorem 2], If c and d are two relatively prime integers, then
3 Redesign of Pair of n × n S-Boxes Over Gaussian Integers
Numerous procedures can be used to generate confusion in a security system. S-box is one of the most efficient techniques in modern cryptosystems. The S-boxes are generally constructed through the class of GI, which is the multiplicative cyclic group. Consequently, there is a good choice to design a variety of S-boxes over the residue class of GI, which provides a marvelous perspective for secure and consistent cryptosystems. The following steps are helpful for the construction of S-boxes over the residue class of GI (Multiplicative cyclic group);
Step 1: Construct a cyclic group of order
Step 2: Separate real and imaginary parts of the cyclic group constructed in Step 1.
Step 3: Apply modulo
Step 4: Select the first
Step 5: Apply permutation through affine mapping as
where
Step 6: Get a pair of S-boxes.
3.1 Pair of 4 × 4 S-Boxes Over the Residue Class of GI
Let
Select the first 16 non-repeated elements from the last two columns of Table 1, then apply the affine permutation mapping,


3.2 Pair of 8 × 8 S-Boxes Over the Residue Class of GI
Let
Select the first 256 non-repeated elements from the real part of Table 4. Then apply the affine permutation map

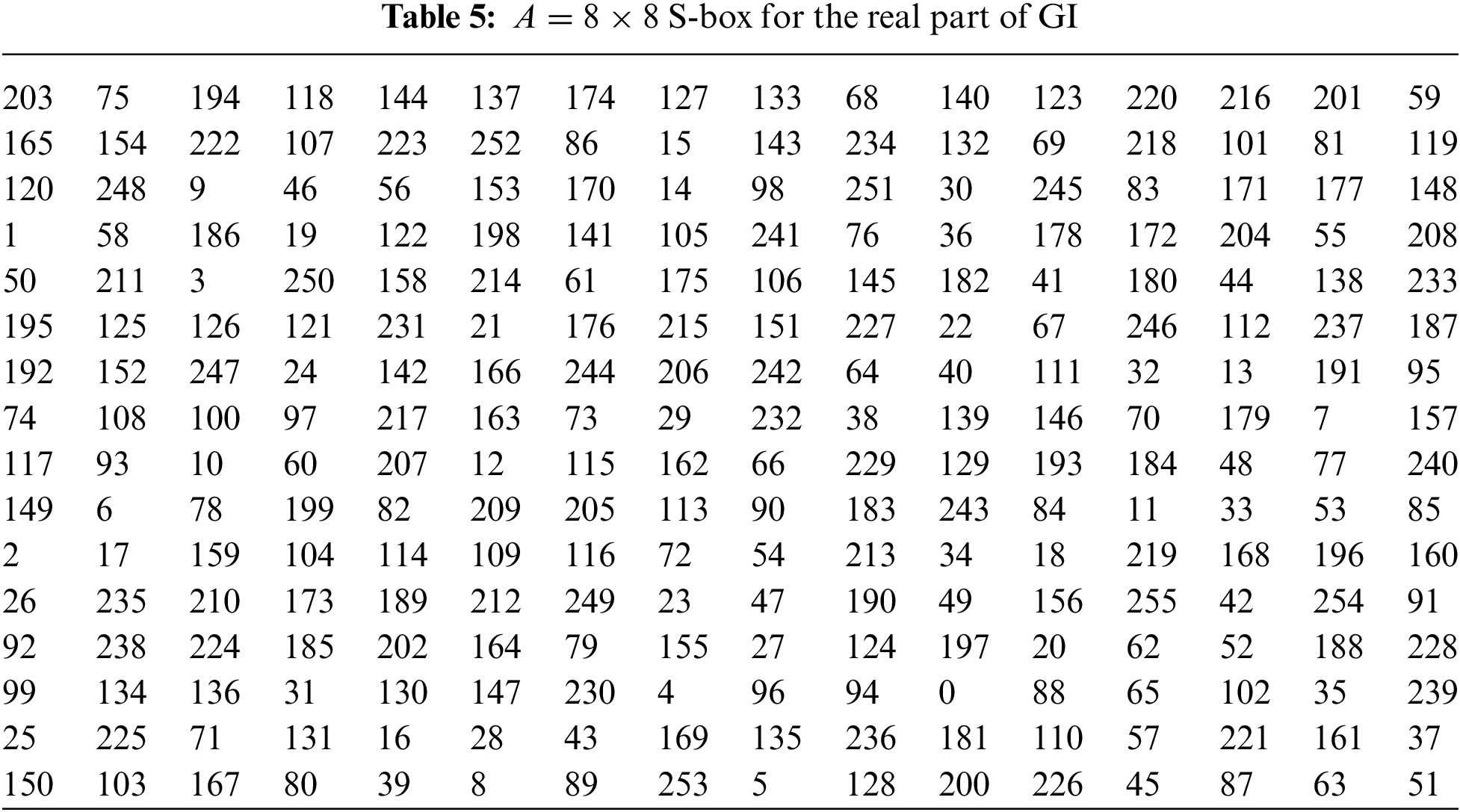
Select the first 256 non-repeated elements from the imaginary part of Table 4. Then apply the affine permutation map
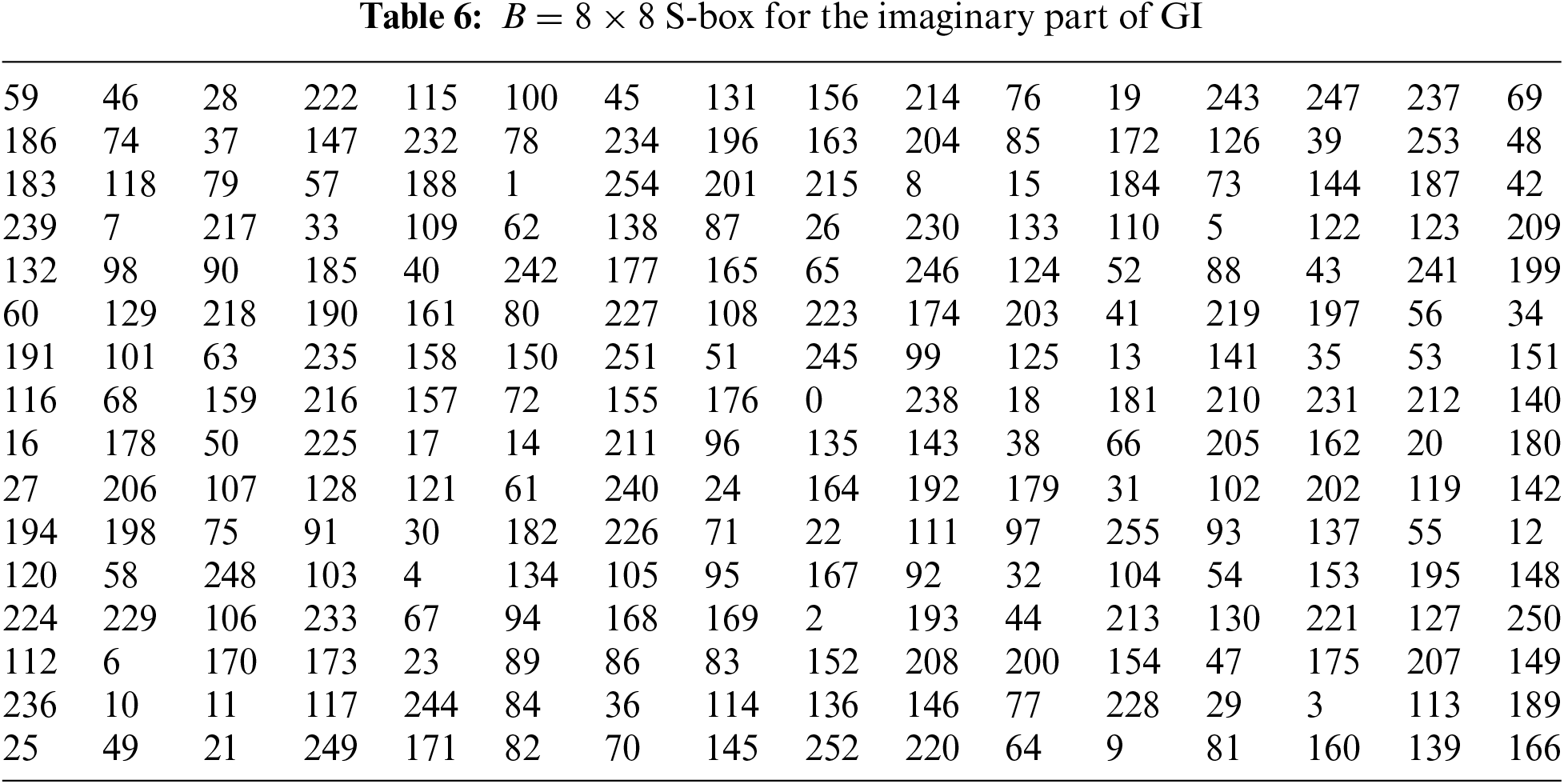
3.3 Pair of 8 × 8 S-Boxes Over the Residue Class of GI
Let


The S-boxes
The Inverse S-box of A is defined by the map
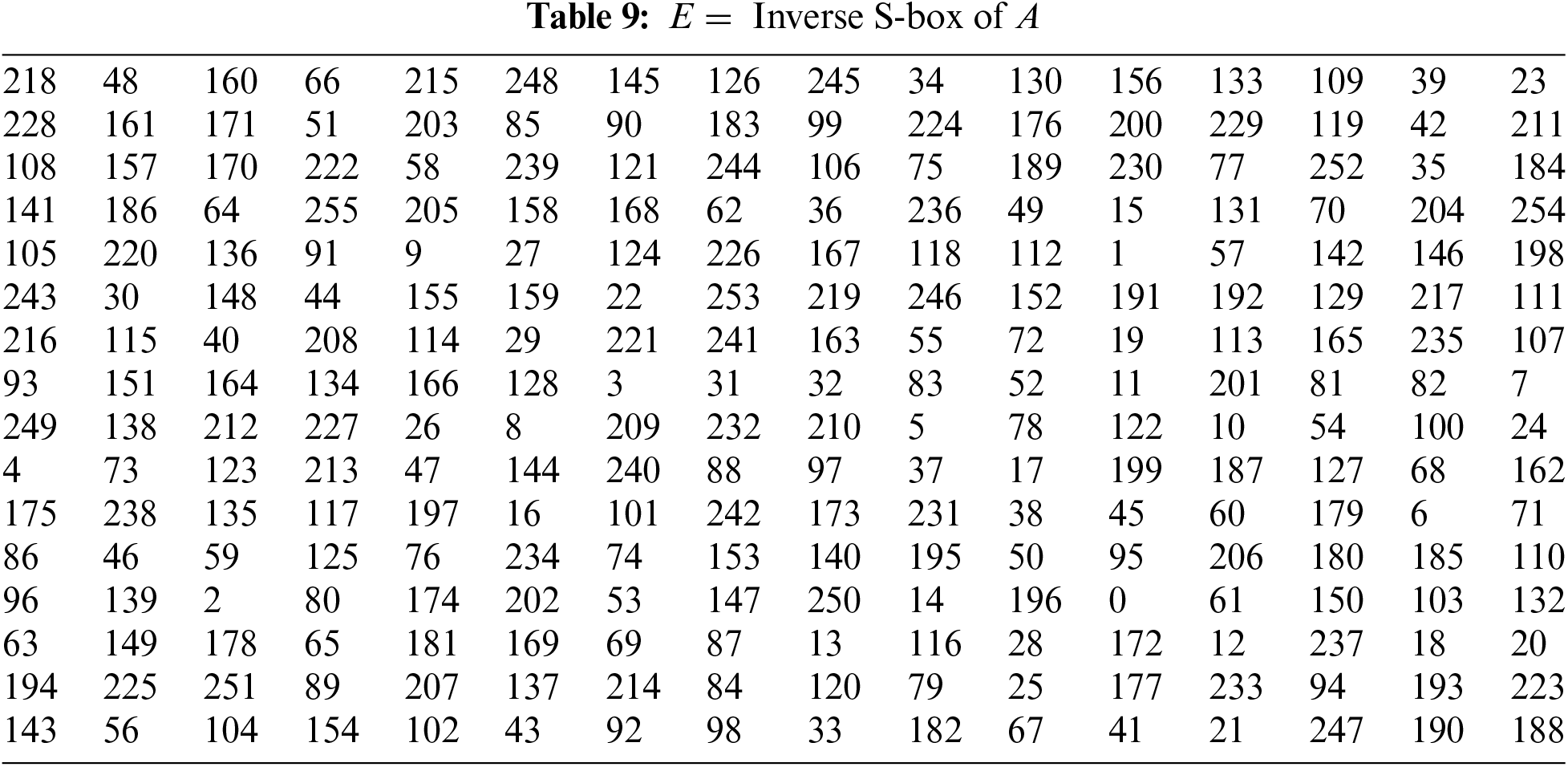
The inverse S-box of B is defined by the map

The inverse S-box of C for the real part of GI is given in Table 11.
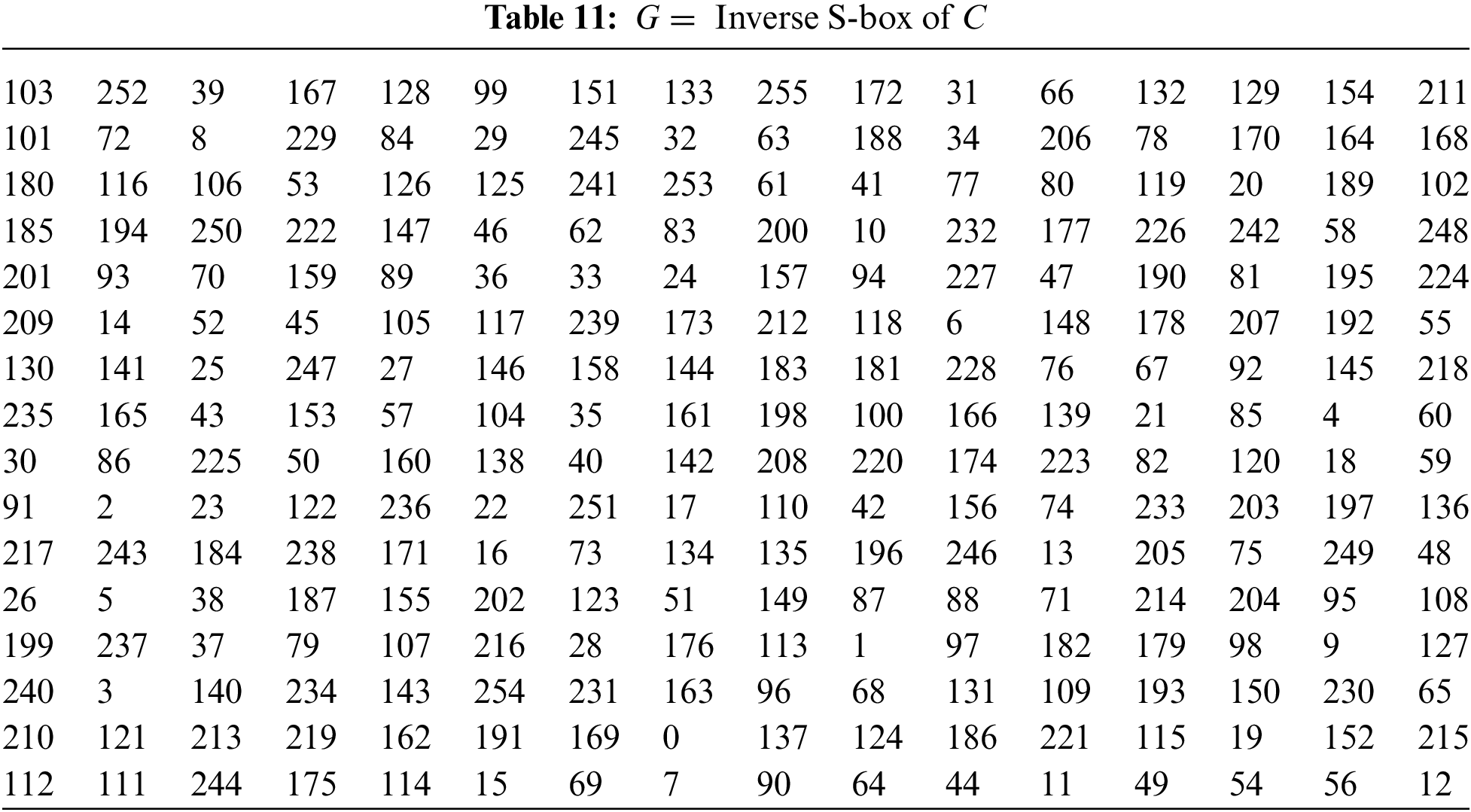
The inverse S-box of D for the imaginary parts of GI is given in Table 12.

In this section, we will present some useful analyses of the proposed S-box like as; Nonlinearity, bit independence criterion, strict avalanche criterion, linear approximation probability, and differential approximation probability.
The NL of a Boolean function can be defined as the distance between the function and the set of all affine functions. In other words, we can say that; Non-linearity is the number of bits that must be changed in the truth table of a Boolean function to reach the closest affine function. The upper bound of NL for the S-box is
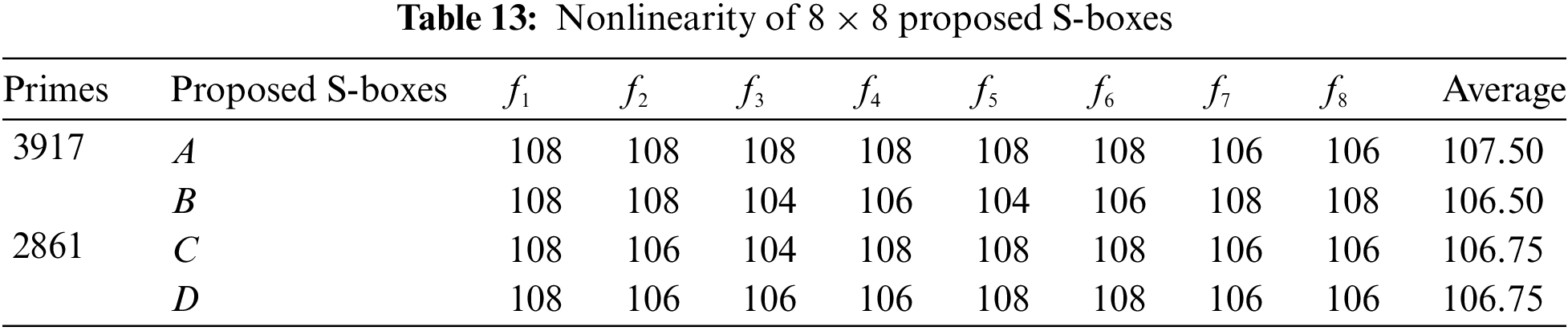
The maximum nonlinearity of all proposed S-boxes
4.2 Bit Independence Criterion (BIC)
The output BIC was also first introduced by Webster and Tavares, which is explained in [18], which is another desirable property for any cryptographic design. It means that all the avalanche variables should be pair-wise independent for a given set of avalanche vectors generated by the complementing of a single plaintext bit. The average value of BIC is
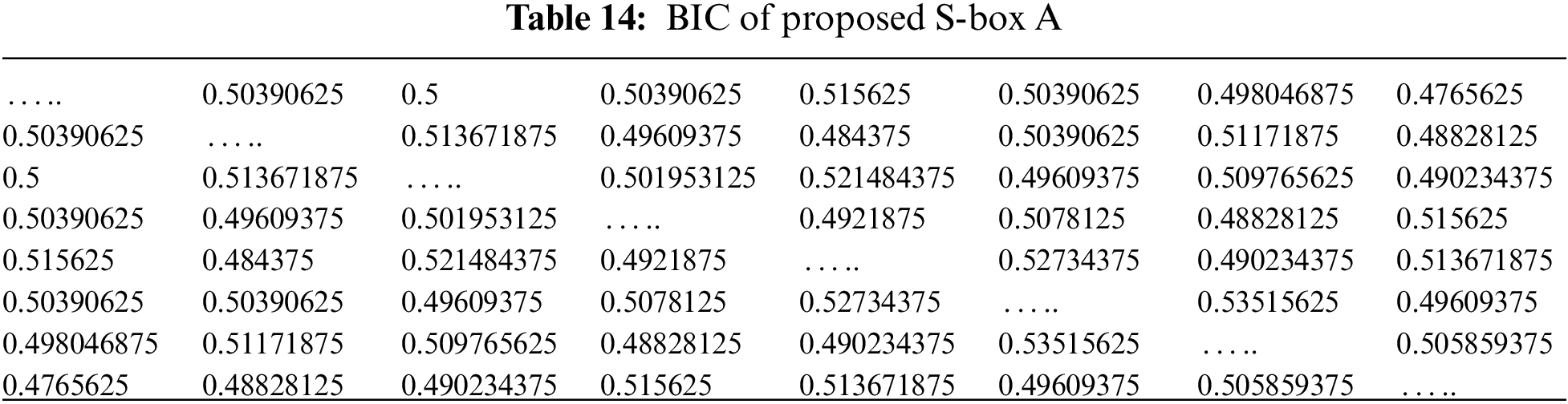
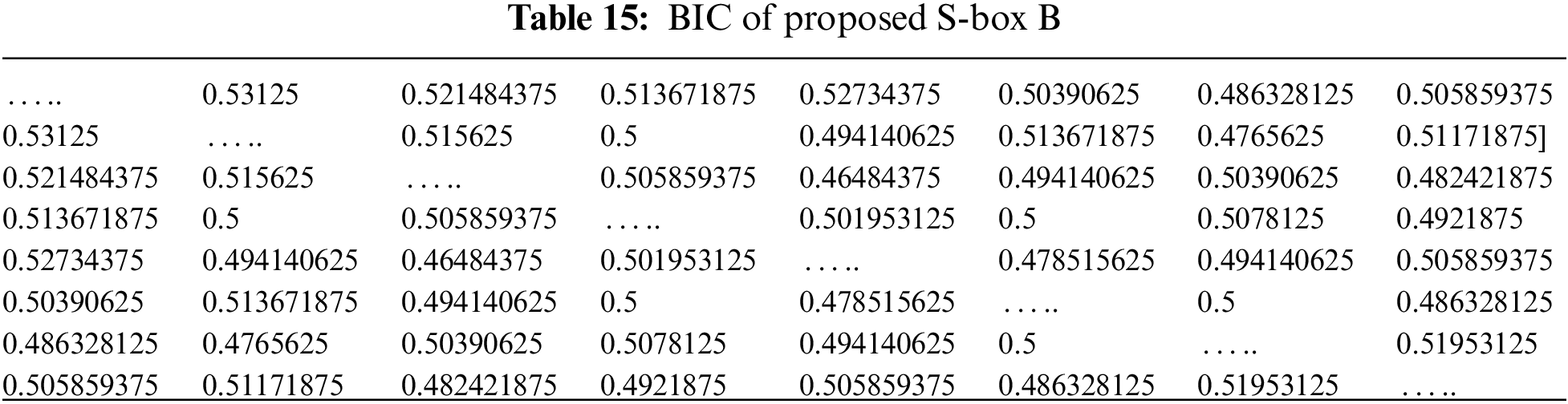
The maximum (Max), average (Ave), and minimum (Min) BIC values of proposed S-boxes (
4.3 Linear Approximation Probability (LAP)
LAP is the maximum value of the imbalance of an event. The parity of the input bits selected by the mask
where
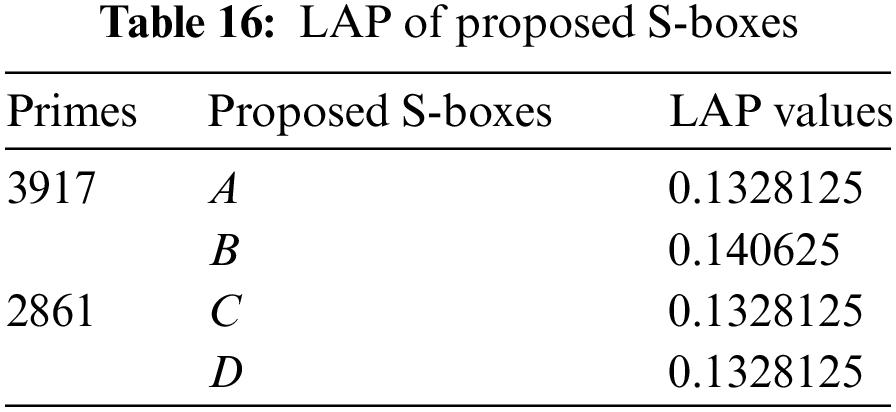
4.4 Differential Approximation Probability (DAP)
The nonlinear transformation S-box should ideally have differential uniformity. An input differential
The DAP results of proposed S-boxes
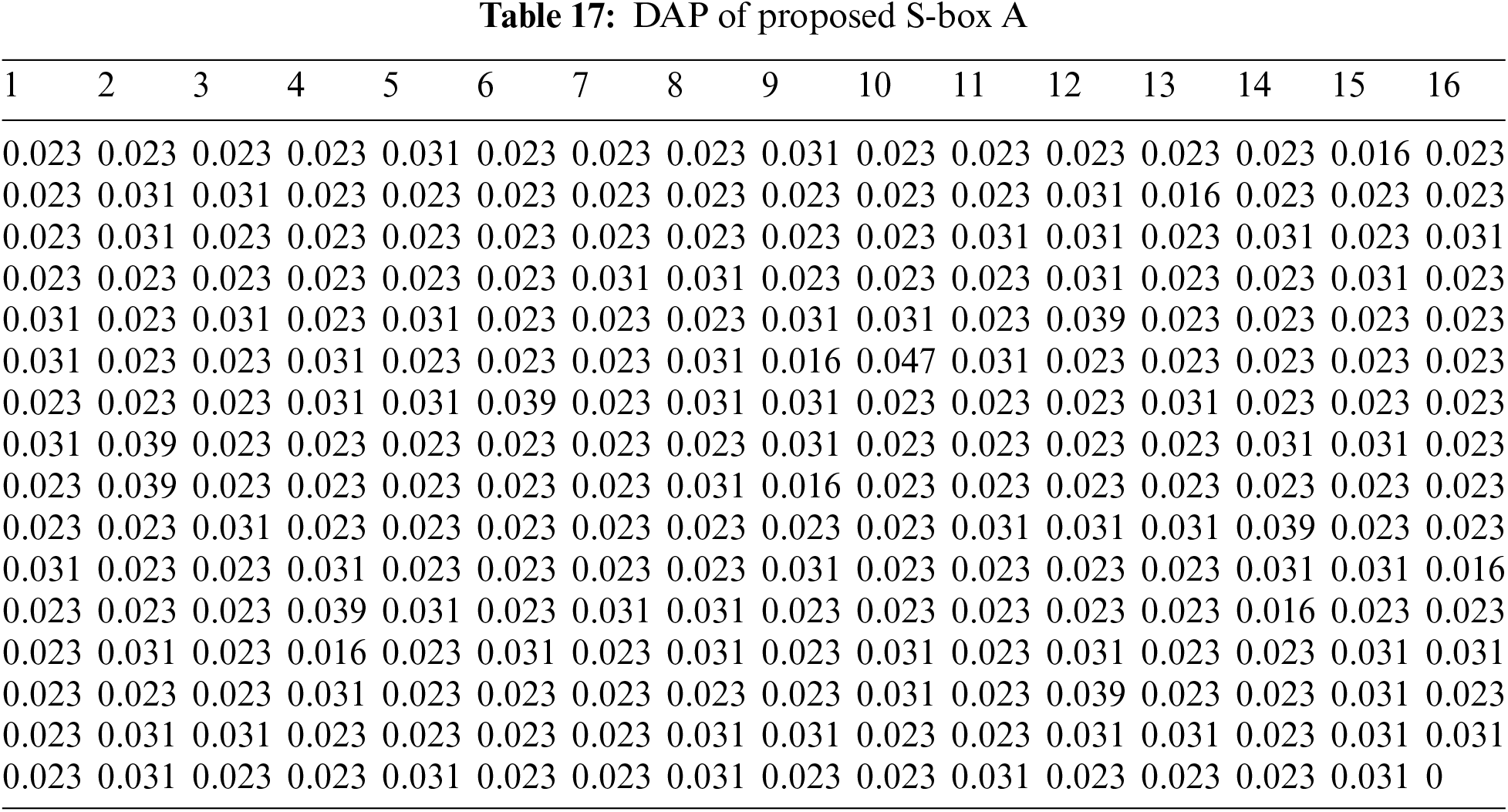
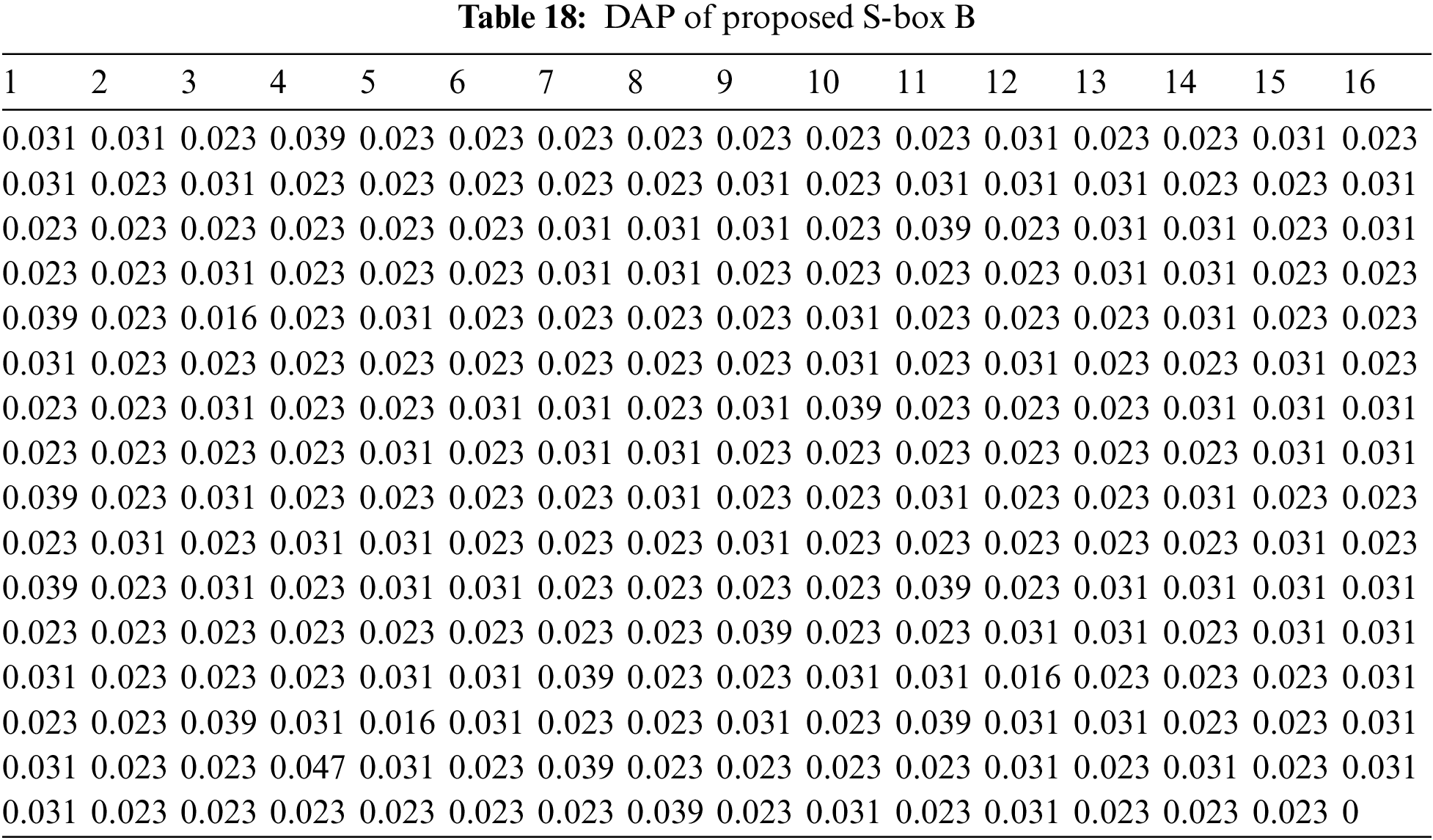
The Max. DAP values of proposed S-boxes
4.5 Strict Avalanche Criterion (SAC)
An S-box satisfies SAC if a single bit changes on the input results in a change on half of the output bits. Note that when S-box is used to build an S-P network, then a single change on the input of the network causes an avalanche of changes. The SAC results of the proposed S-boxes
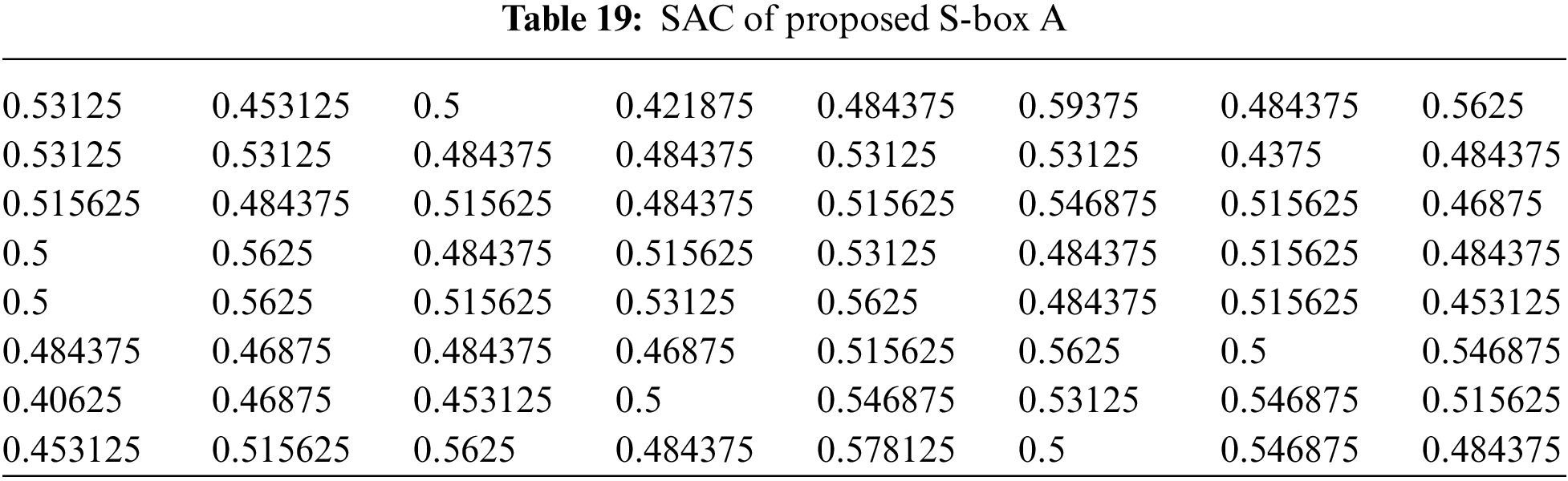
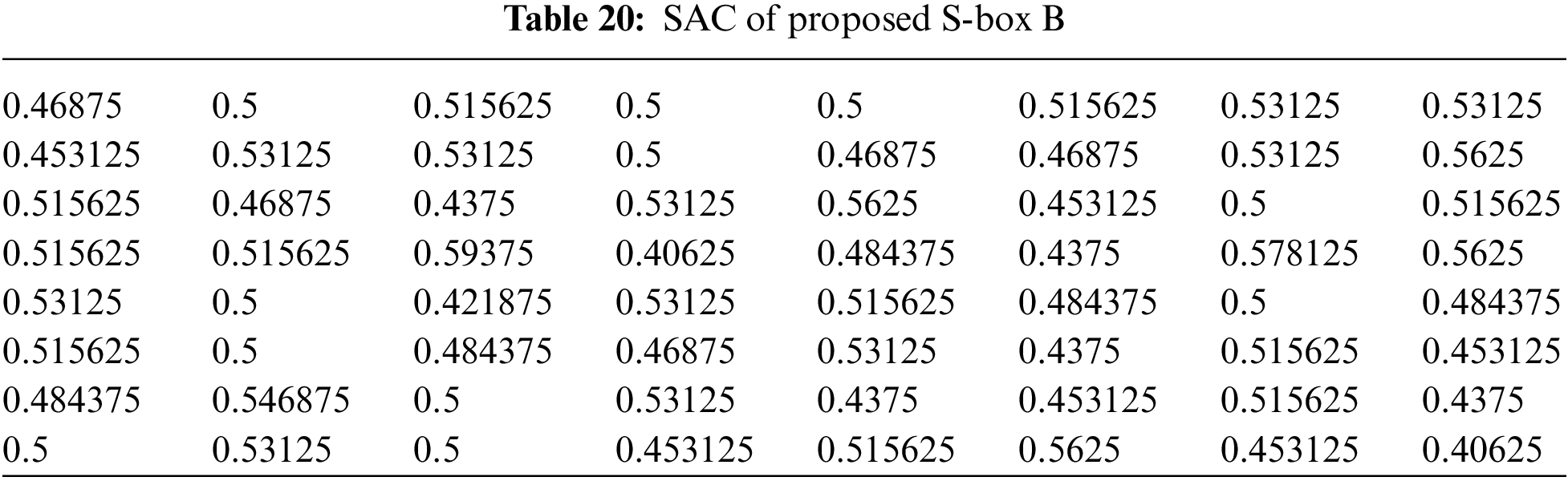
The Max SAC values of proposed S-boxes
The former tests are applied on well-known S-boxes over EC presented in [19,20] to compare with the proposed S-boxes
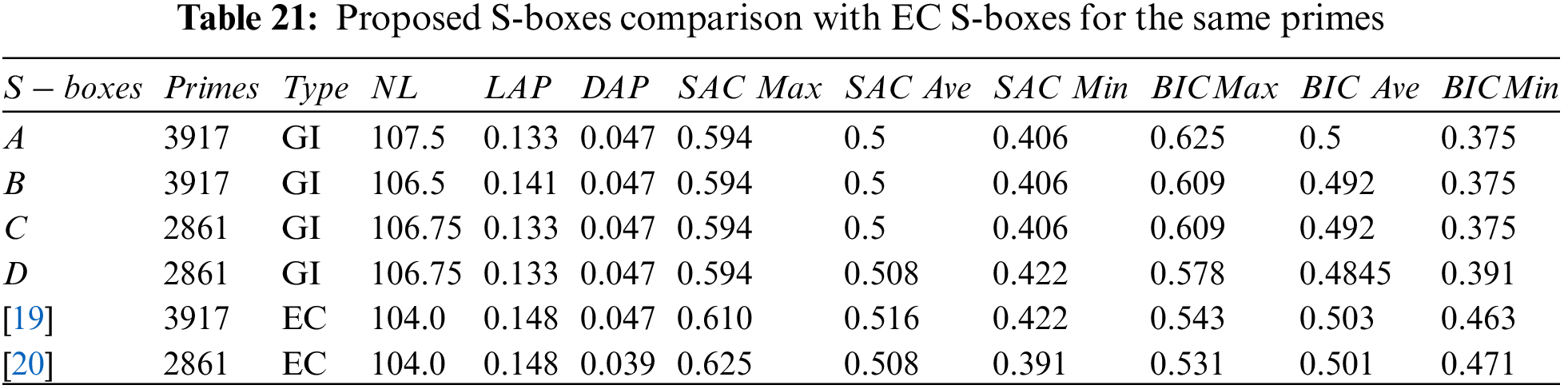
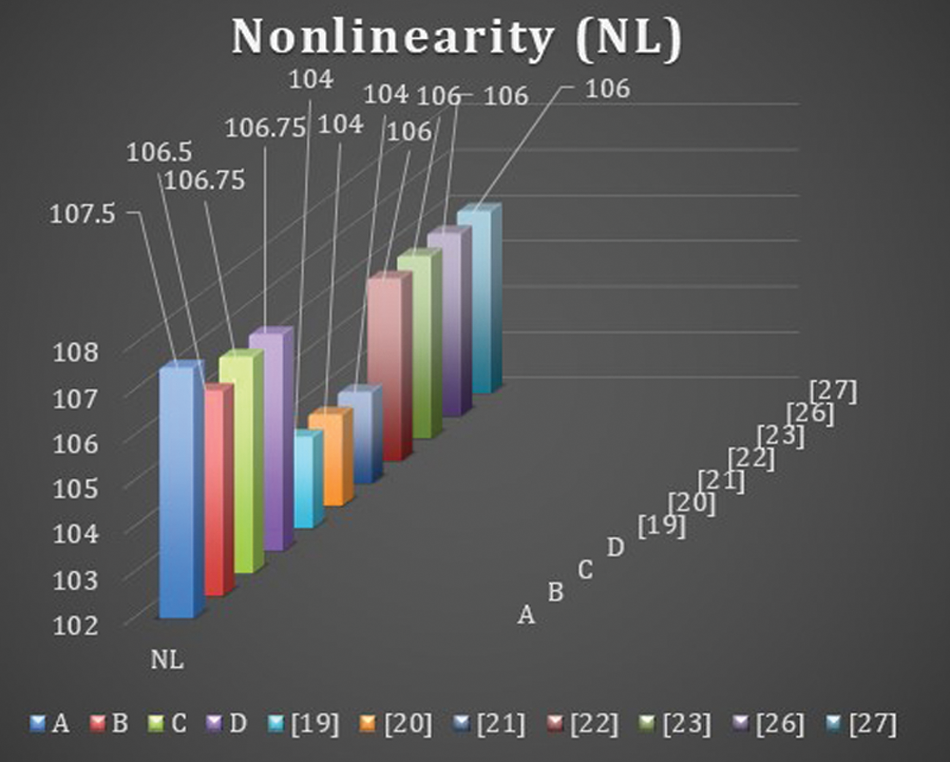
Figure 1: Nonlinearity
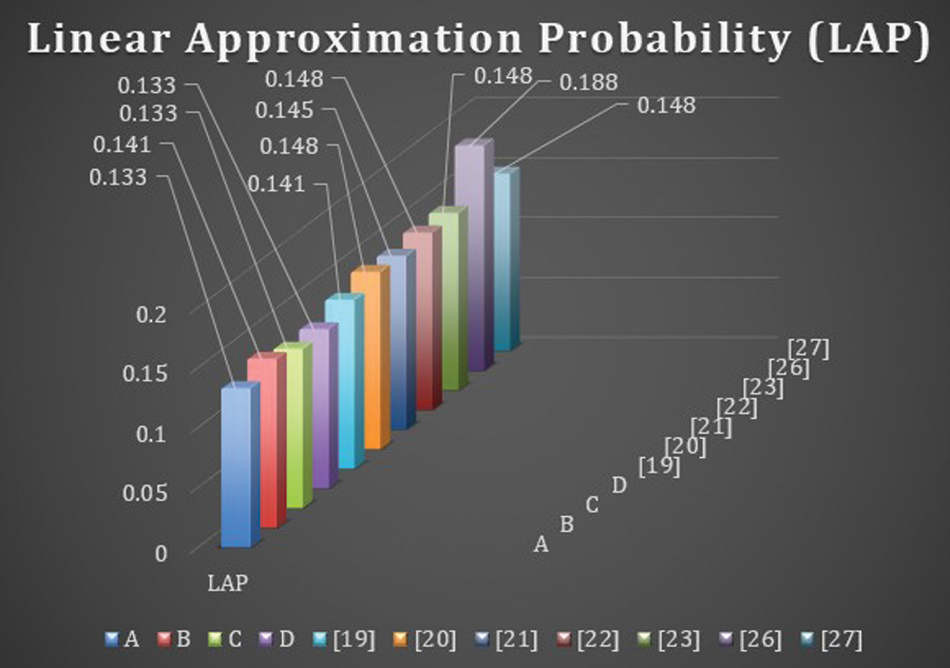
Figure 2: Linear approximation probability
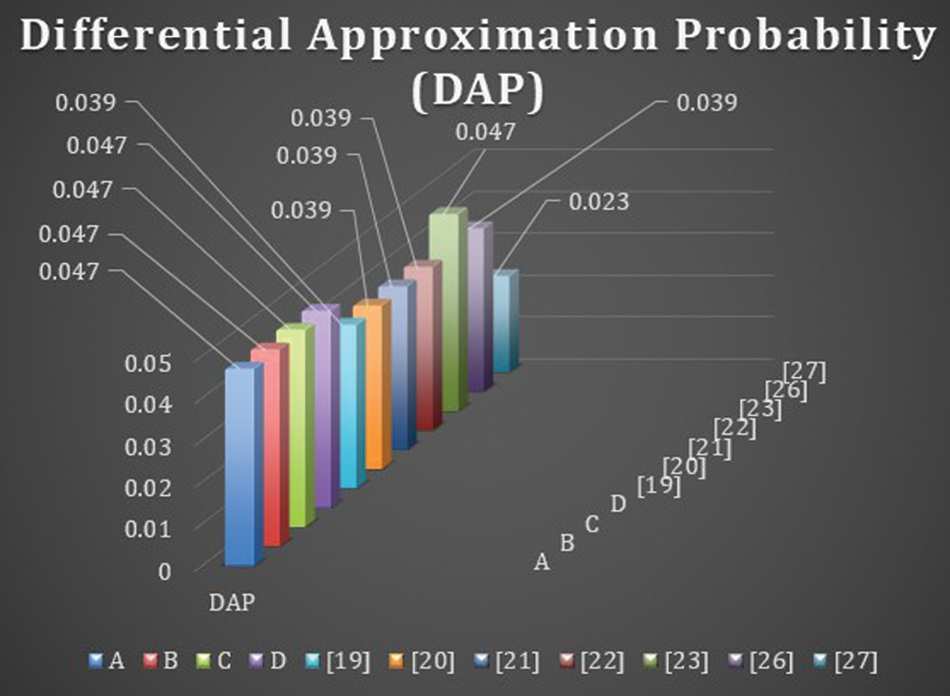
Figure 3: Differential approximation probability
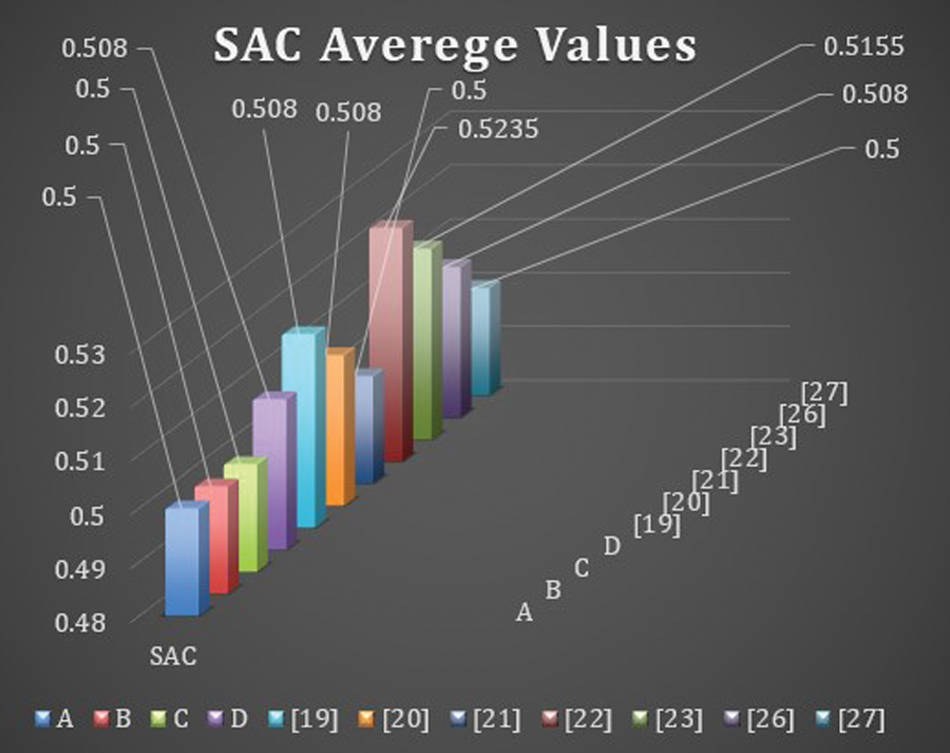
Figure 4: SAC average values
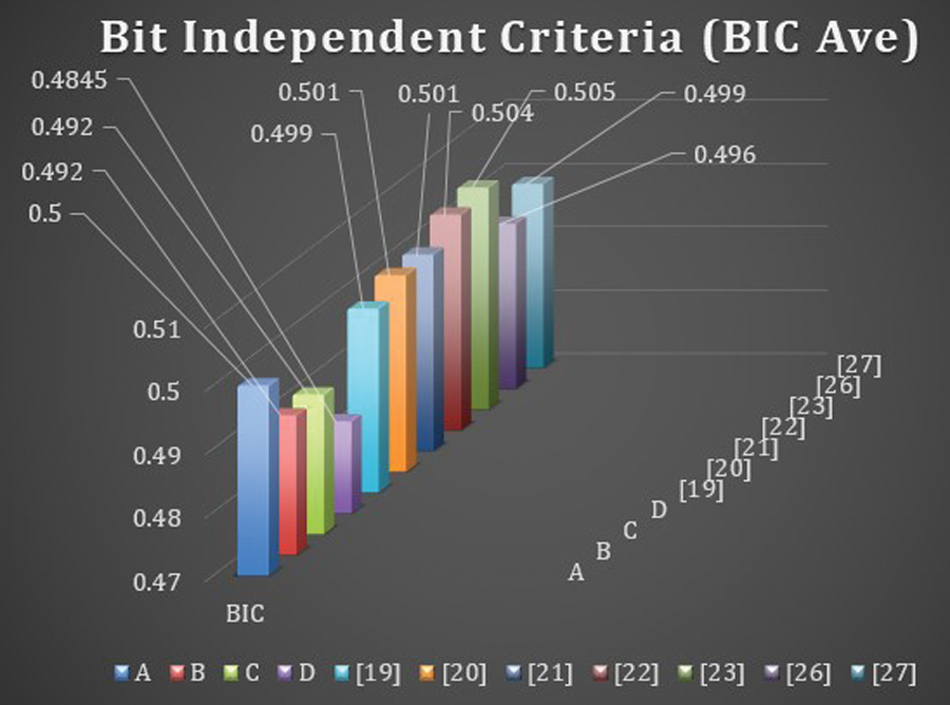
Figure 5: Bit independent criteria
Similarly, the comparison of S-boxes over EC presented in [19–27] with the proposed S-boxes
It is observed that the value of nonlinearity of the proposed S-boxes is better than with EC S-boxes. The fascinating features of the proposed technique by using affine mapping provide S-boxes pair at a time by fixing three parameters
6 Conclusion and Future Directions
A novel S-box construction technique is presented in this article. The fascinating features of the proposed technique by using affine mapping provide S-boxes pair at a time by fixing three parameters
The proposed S-boxes over the residue class of GI can be extended to the S-boxes over the residue class of quaternion and octonion integers. Furthermore, we can use these structures in watermarking and image encryption.
Funding Statement: The third author is supported by Minciencias Convocatoria 891.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. K. Ruohonen, “Mathematical cryptology,” Lecture Notes, vol. 1, no. 1, pp. 1–138, 2010. [Google Scholar]
2. C. E. Shannon, “Communication theory of secrecy systems,” The Bell System Technical Journal, vol. 28, no. 4, pp. 656–715, 1949. [Google Scholar]
3. M. M. Hoobi, “Strong triple data encryption standard algorithm using nth degree truncated polynomial ring unit,” Journal of Science, vol. 3, no. 3, pp. 1760–1771, 2017. [Google Scholar]
4. A. Fathy, I. F. Tarrad, H. F. A. Hamed and A. I. Awad, “Advanced encryption standard algorithm, issues and implementation aspects,” in Int. Conf. on Advanced Machine Learning Technologies and Applications, Berlin, Heidelberg, Springer, vol.12, no. 2, pp. 516–523, 2012. [Google Scholar]
5. A. Anees and Y. P. P. Chen, “Designing secure substitution boxes based on permutation of symmetric group,” Neural Computing and Applications, vol. 2, no. 11, pp. 7045–7056, 2020. [Google Scholar]
6. I. Shahzad, Q. Mushtaq and A. Razaq, “Construction of new S-box using action of quotient of the modular group for multimedia security,” Security and Communication Networks, vol. 19, no. 1, pp. 1–13, 2019. [Google Scholar]
7. T. Shah and A. Qureshi, “S-box on subgroup of galois field,” Cryptography, vol. 3, no. 2, pp. 1–9, 2019. [Google Scholar]
8. I. Hussain, A. Anees, A. H. Alkhaldi, M. Aslam, N. Siddiqui et al., “Image encryption based on Chebyshev chaotic map and S8 S-boxes,” Optica Applicata, vol. 49, no. 2, pp. 317–330, 2019. [Google Scholar]
9. L. C. N. Chew and E. S. Ismail, “S-box construction based on linear fractional transformation and permutation function,” Symmetry, vol. 12, no. 5, pp. 826–842, 2020. [Google Scholar]
10. B. Arshad, N. Siddiqui, Z. Hussain and M. E. U. Haq, “A novel scheme for designing secure substitution boxes (S-boxes) based on mobius group and finite field,” Wireless Personal Communications, vol. 135, no. 124, pp. 3527–3548, 2022. [Google Scholar]
11. I. Hussain, T. Shah, M. A. Gondal and H. Mahmood, “A novel image encryption algorithm based on chaotic maps and GF (28) exponent transformation,” Nonlinear Dynamics, vol. 72, no. 1, pp. 399–406, 2013. [Google Scholar]
12. U. Hayat, N. A. Azam and M. Asif, “A method of generating 8× 8 substitution boxes based on elliptic curves,” Wireless Personal Communications, vol. 101, no. 1, pp. 439–451, 2018. [Google Scholar]
13. A. Javeed, T. Shah and A. Ullah, “Construction of non-linear component of block cipher by means of chaotic dynamical system and symmetric group,” Wireless Personal Communications, vol. 112, no. 1, pp. 467–480, 2020. [Google Scholar]
14. M. Sajjad, T. Shah, M. M. Hazzazi, A. R. Alharbi and I. Hussain, “Quaternion integers based higher length cyclic codes and their decoding algorithm,” Computers, Materials & Continua, vol. 73, no. 1, pp. 1177–1194, 2022. [Google Scholar]
15. G. Davidoff, P. Sarnak and A. Valette, “Elementary number theory, group theory, and ramanujan graphs,” Cambridge University Press, vol. 55, no. 1, pp. 45–80, 2003. [Google Scholar]
16. K. Conrad, “The Gaussian integers,” Preprint, Paper Edition, vol. 10, no. 2, pp. 1–13, 2018. [Google Scholar]
17. K. Huber, “Codes over Gaussian integers,” IEEE Transactions on Information Theory, vol. 40, no. 1, pp. 207–216, 1994. [Google Scholar]
18. M. I. Haider, A. Ali, D. Shah and T. Shah, “Block cipher's nonlinear component design by elliptic curves: An image encryption application,” Multimedia Tools and Applications, vol. 80, no. 3, pp. 4693–4718, 2021. [Google Scholar]
19. U. Hayat and N. A. Azam, “A novel image encryption scheme based on an elliptic curve,” Signal Processing, vol. 155, no. 1, pp. 391–402, 2019. [Google Scholar]
20. G. Dresden and W. M. Dymàčcek, “Finding factors of factor rings over the Gaussian integers,” The American Mathematical Monthly, vol. 112, no. 7, pp. 602–611, 2005. [Google Scholar]
21. N. Siddiqui, A. Naseer and M. E. U. Haq, “A novel scheme of substitution-box design based on modified pascal’s triangle and elliptic curve,” Wireless Personal Communications, vol. 116, no. 4, pp. 3015–3030, 2021. [Google Scholar]
22. N. A. Azam, U. Hayat and I. Ullah, “Efficient construction of a substitution box based on a mordell elliptic curve over a finite field,” Frontiers of Information Technology & Electronic Engineering, vol. 20, no. 10, pp. 1378–1389, 2019. [Google Scholar]
23. U. Hayat, N. A. Azam, H. R. G. Ruiz, S. Naz and L. Batool, “A truly dynamic substitution box generator for block ciphers based on elliptic curves over finite rings,” Arabian Journal for Science and Engineering, vol. 46, no. 9, pp. 8887–8899, 2021. [Google Scholar]
24. B. Collard and F. X. Standaert., “Experimenting linear cryptanalysis,” in Advanced Linear Cryptanalysis of Block and Stream Ciphers, 1st ed., vol. 1. Du Levant 3, B-1348, Louvain-la-Neuve, Belgium: IOS Press, pp. 1–28, 2011. [Google Scholar]
25. E. Biham and A. Shamir, “Differential cryptanalysis of DES-like cryptosystems,” Journal of Cryptology, vol. 4, no. 1, pp. 3–72, 1991. [Google Scholar]
26. N. A. Azam, U. Hayat and I. Ullah, “An injective S-box design scheme over an ordered isomorphic elliptic curve and its characterization,” Security and Communication Networks, vol. 80, no. 3, pp. 220–229, 2018. [Google Scholar]
27. I. Ullah, U. Hayat and M. D. Bustamante, “Image encryption using elliptic curves and rossby/drift wave triads,” Entropy, vol. 22, no. 4, pp. 454–473, 2020. [Google Scholar] [PubMed]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools