 Open Access
Open Access
ARTICLE
Electricity Carbon Quota Trading Scheme based on Certificateless Signature and Blockchain
1 College of Computer Science and Engineering, Northwest Normal University, Lanzhou, 730070, China
2 Institute of China Telecom Wanwei, China Telecom Wanwei Information Technology Co., Ltd., Lanzhou, 730030, China
3 College of Big Data and Internet, Shenzhen Technology University, Shenzhen, 518118, China
4 Key Laboratory of Cryptography and Data Analytics, Northwest Normal University, Lanzhou, 730070, China
* Corresponding Author: Runze Diao. Email:
(This article belongs to the Special Issue: The Bottleneck of Blockchain Techniques: Scalability, Security and Privacy Protection)
Computer Modeling in Engineering & Sciences 2024, 138(2), 1695-1712. https://doi.org/10.32604/cmes.2023.029461
Received 20 February 2023; Accepted 22 May 2023; Issue published 17 November 2023
Abstract
The carbon trading market can promote “carbon peaking” and “carbon neutrality” at low cost, but carbon emission quotas face attacks such as data forgery, tampering, counterfeiting, and replay in the electricity trading market. Certificateless signatures are a new cryptographic technology that can address traditional cryptography’s general essential certificate requirements and avoid the problem of crucial escrow based on identity cryptography. However, most certificateless signatures still suffer from various security flaws. We present a secure and efficient certificateless signing scheme by examining the security of existing certificateless signature schemes. To ensure the integrity and verifiability of electricity carbon quota trading, we propose an electricity carbon quota trading scheme based on a certificateless signature and blockchain. Our scheme utilizes certificateless signatures to ensure the validity and nonrepudiation of transactions and adopts blockchain technology to achieve immutability and traceability in electricity carbon quota transactions. In addition, validating electricity carbon quota transactions does not require time-consuming bilinear pairing operations. The results of the analysis indicate that our scheme meets existential unforgeability under adaptive selective message attacks, offers conditional identity privacy protection, resists replay attacks, and demonstrates high computing and communication performance.Keywords
More than forty percent of all carbon emissions in China are produced by the electric power industry, making it a significant sector. In addition, according to a report by Ember, a UK-based independent climate think tank, carbon emissions from the power industry reached a new peak in 2021, rising by 778 million tons annually. According to research, limiting carbon emissions in the electricity industry is essential for achieving an early carbon emissions peak [1].
Carbon emissions are considered a commodity in carbon trading, which uses a market mechanism to raise the price of carbon emissions to regulate and lower them and to foster low-carbon, sustainable development. Government departments assign carbon emission quotas [2–4] to each firm in accordance with predetermined guidelines to attain the objectives of “carbon peaking” and “carbon neutrality”. Suppose the actual carbon emissions of an enterprise are higher than the initial quota allocated by the government. If an enterprise’s actual carbon emissions exceed the initial quota assigned by the government, the enterprise must acquire the additional quota on the carbon trading market. Using energy-saving and emission-reduction technologies, if an enterprise’s actual carbon emissions are lower than the government-allocated quota, it can sell and trade the excess carbon quota to generate revenue. Fig. 1 depicts the carbon quota trading procedure between two businesses.

Figure 1: Overview of carbon quota trading
Blockchain technology has the characteristics of immutability and transaction traceability, providing technical support for the realization of secure and trusted carbon quota trading. Zhang et al. [5] established a carbon quota trading model with blockchain technology to ensure the fairness of carbon quota allocation. Zhu et al. [6] proposed a multi-energy primary energy storage optimization configuration model based on blockchain to improve energy self-sufficiency. Ji et al. [7] designed an electricity carbon rights trading mechanism based on an alliance chain to improve the market returns of all participants. Yuan et al. [8] used blockchain technology to build a carbon emission data-sharing platform to realize the traceability and sharing of carbon trading. However, these schemes still suffered from complex key management and low transaction efficiency.
Certificateless signatures maintain the advantages of identity-based cryptographic systems without vital public certificates and can ensure the integrity, identity authentication, and nonrepudiation of carbon quota trading. Electricity carbon quota trading scheme based on certificateless signature and blockchain offers several advantages:
Efficiency: Traditional carbon quota trading requires the involvement of government regulatory bodies for verification and approval, which is time-consuming and costly. However, Certificateless signature and blockchain-based scheme eliminates the need for certificate verification and enables fast, automated transaction verification and settlement, reducing intermediaries and increasing transaction efficiency.
Security: The scheme based on certificateless signature uses digital signatures to verify information authenticity, while blockchain technology ensures the immutability of transaction records, guaranteeing transaction safety and reliability.
Decentralization: The blockchain-based scheme does not require a centralized platform as an intermediary; all transactions are recorded on the blockchain, enhancing transaction transparency and traceability while removing intermediaries.
Compared to traditional schemes, the proposed Electricity Carbon Quota Trading Scheme based on Certificateless Signature and Blockchain has the following advantages:
1. Traditional schemes rely on third-party certificate authorities for identity verification, adding extra time and expense. But the certificateless public key cryptography-based scheme is decentralized and does not require certificate verification, thus enabling faster transactions.
2. The use of digital signature verification ensures transactional authenticity and integrity, while blockchain technology enforces immutability, guaranteeing transaction safety and reliability.
3. Traditional schemes require businesses to purchase a fixed number of carbon quotas. By contrast, the certificateless signature and blockchain-based scheme allow for instantaneous carbon quota trading, making it more flexible.
4. Traditional schemes require payment of multiple types of fees and costs, while the certificateless signature and blockchain-based solution can reduce transaction costs.
In conclusion, the electricity carbon quota trading scheme based on certificateless signature and blockchain provides greater efficiency, security, and decentralization compared to traditional schemes. Researchers have presented several certificateless signature techniques [9–11] in recent years. The user’s private key is divided into two pieces for the certificateless signature: a secret value chosen randomly by the user and a partial private key derived by the semi-trusted key generation center (KGC). For the security of certificateless signature schemes, attackers are divided into two categories: one is the attacker that imitates malicious users, usually known as the first type of attacker A1. It can launch public key replacement attacks and mastering user secret values but is unaware of KGC’s master key. The KGC attacker is an additional type of attacker that mimics malicious attacks. It is usually called the second type of attacker A2. It has access to the master key of the KGC, but it is prohibited from launching public key replacement attacks and cannot determine the user’s secret value. Mei et al. [12] suggested a certificateless signature scheme that enables conditional privacy protection; however, signature verification efficiency might be improved. Deng et al. [13] proposed a new certificateless signature scheme, but it could not resist replay attacks and did not consider anonymity. To solve these problems, Wang et al. [14] proposed an undocumented signature scheme that supports anonymity and traceability (referred to as Wang et al.’s scheme). Wang et al. [15] have presented a novel blockchain-based smart car carbon emission cap-and-trade system. The proposed system employs a dual-chain architecture, wherein the data chain is utilized to chronicle the data collated from automobiles to guarantee the dependability of the data, thereby ensuring correctness of the carbon emission calculation outcomes. Luo et al. [16] have proposed a carbon quota trading scheme for power generation based on blockchain technology, which integrates lightweight certificateless signature technology and smart contracts to realize an automated carbon quota trading mechanism. However, we find that Wang et al.’s scheme has security defects and cannot resist signature forgery attacks launched by two types of attackers.
Our contributions: To ensure the integrity and identity authentication of electricity carbon quota trading, we propose a scheme of electricity carbon quota trading based on the blockchain and certificateless signatures. The main work is as follows:
(1) We evaluate the security of Wang et al.’s scheme and present two types of forgery attacks.
(2) Aiming at the security defects of Wang et al.’s scheme, we propose an improved certificateless signature scheme.
(3) We suggest an improved signature method and blockchain technology-based trading scheme to make electric carbon quota trading tamper-proof and traceable.
(4) A security study demonstrates that our scheme has low computing and communication costs, provides anonymity and traceability of power enterprise identification, and can withstand forgery and replay attacks.
Let
A bilinear map
(1) Bilinear: For any
(2) Nonregressive:
(3) Validity: There is an effective algorithm to calculate
Computational Diffie Hellman (CDH) problem: Given a tuple
Definition 1 The CDH hypothesis is said to be valid if there is no polynomial-time algorithm that can solve the CDH issue with a nonnegligible probability [8].
Discrete Logarithms (DL) Problem: Given a tuple
Definition 2 The DL hypothesis is said to be true if there is no polynomial-time algorithm that can solve the DL problem with a nonnegligible probability [11].
The central objective of our security model is to comprehensively address the security challenges related to carbon emission quotas in the electricity trading market. Specifically, the proposed model strives to prevent various types of malicious attacks, such as data falsification, tampering, forgery, and replay attacks.
To overcome the limitations imposed by traditional cryptography’s reliance on fundamental certification requirements and avoid critical custody issues based on identity-based cryptography, a certificate-free signature scheme has been proposed as a feasible solution. The proposed certificate-free signature scheme is highly secure and efficient, aimed at ensuring the validity and non-repudiation of all transactions involved in carbon emission quota trading. In addition, blockchain technology has been deployed to achieve the immutability and traceability of all power carbon quota transactions. This scheme provides conditional identity privacy protection, enhances defense against replay attacks, and has high computational and communication performance.
In response to the security vulnerabilities of Wang et al.’s scheme, we propose the security model for our scheme and divide the adversaries of the certificate-free signing scheme into two categories:
A2: These are adversaries who launch forged attacks against malicious KGCs. As malicious KGCs, they not only know the main secret key of KGC and partial private key
3 Security Analysis of Wang et al.’s Scheme
This section focuses mostly on reviewing the certificateless signature scheme proposed by Wang et al. [14], analyzing its security, and presenting the related enhancement scheme.
3.1 Wang et al.’s Scheme Description
The certificateless signature of Wang et al.’s scheme consists of the six methods listed below:
(1) System establishment: Given a security parameter
① Select bilinear groups
② Select random number
③ Select three hash functions
④ Expose the system parameter
(2) Pseudonym generation: The user whose real identity is
After receiving
(3) Generation of partial private keys: The KGC generates partial private keys for users with the alias
① Select a random number
② Calculate
③ Calculate partial private key
④ Send
(4) Public/private key generation: After receiving
(5) Signature generation: For message
① Randomly select
② Select a timestamp
③ Calculate
④ Output a signature
(6) Signature verification: The verifier goes through the following motions to ensure that
① Check the freshness of
② Calculate
③ Verify equation
The verifier accepts the signature if the aforementioned equation is true; otherwise,
The relevant process of the Wang et al.’s scheme is shown in Fig. 2.
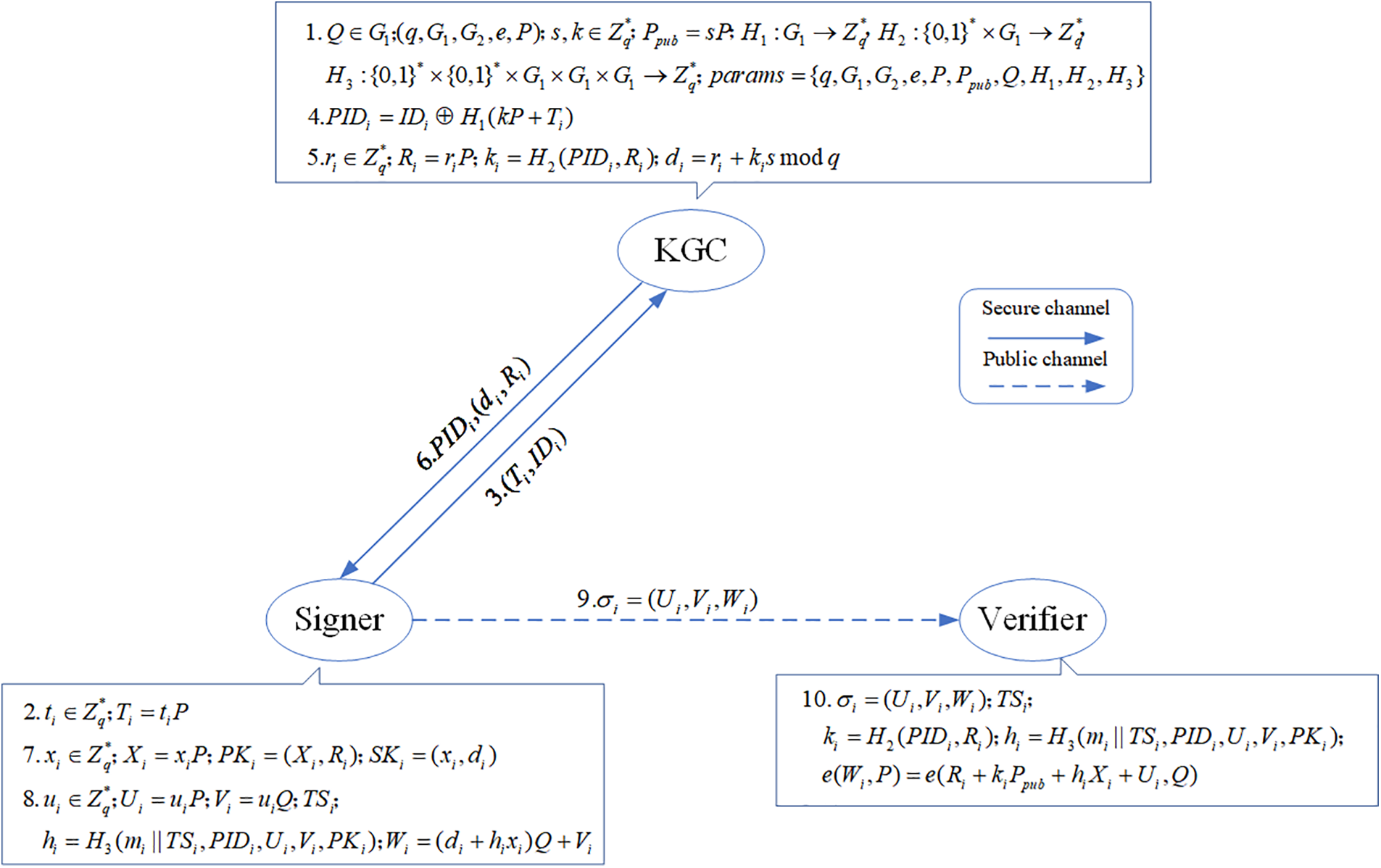
Figure 2: Wang et al.’s scheme
3.2 Forgery Attack of Wang et al.’s Scheme
Here are the specific steps for the two forgery attacks that Wang et al.’s scheme cannot resist.
(1) Forgery attack by malicious users: Let
① Calculate
② Select
③ Select message
④ Calculate
⑤ Output
The following verifies the legitimacy of
The given reasoning demonstrates that
(2) Forgery attack of malicious KGC: Let A2 be the second type of attacker against Wang et al.’s scheme. A2 selects a target user and obtains its pseudonym
① Select a random number
② Select
③ Select message
④ Calculate
⑤ Output
The following verifies the legitimacy of the signature forged by A2:
The given reasoning demonstrates that
3.3 Improved Certificateless Signature Scheme
To address the security flaws of Wang et al.’s scheme, we provide an enhanced certificateless signing scheme below. The cyclic group of the elliptic curve is chosen to improve the communication performance of the updated scheme. The specific description is as follows:
(1) System establishment: The KGC performs the following actions to produce system parameters and master keys based on security parameter
① Select an elliptic curve cyclic group
② Select a random number
③ Select four hash functions:
④ Expose system parameter
(2) Kana generation: This algorithm is the same as Wang et al.’s scheme.
(3) Partial private key generation: This algorithm is the same as Wang et al.’s scheme, but the only difference is that the value of
(4) Public/private key generation: This algorithm is the same as Wang et al.’s scheme.
(5) Signature generation: For message
① Randomly select
② Select a timestamp
③ Calculate
④ Output signature
(6) Signature verification: The verifier performs the following steps to check the validity of
① Check the freshness of
② Calculate
③ Verify equation
If the above formula is true, the verifier accepts the signature; otherwise, it rejects
The related process of the Improved certificateless signature scheme is shown in Fig. 3.
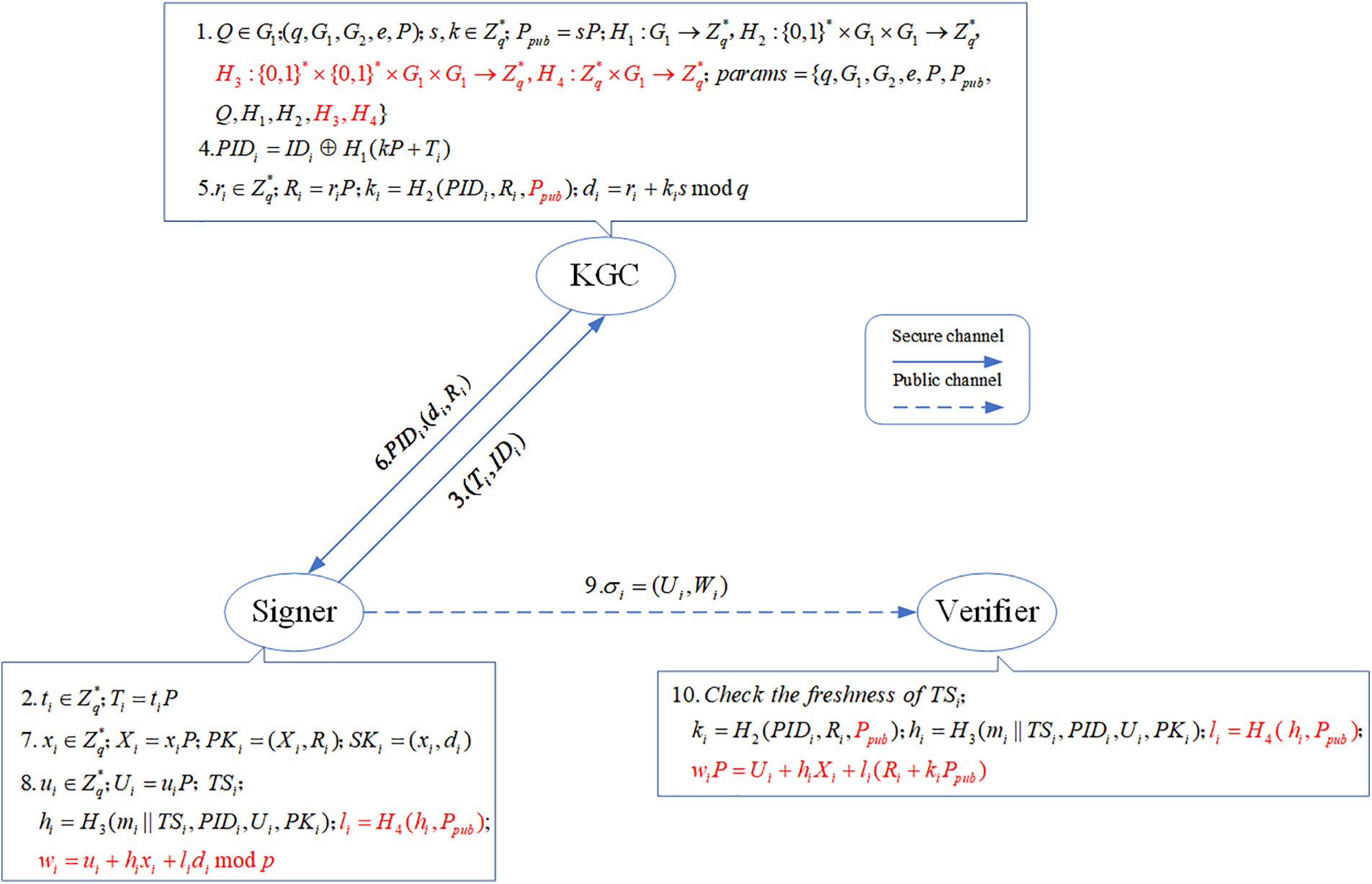
Figure 3: Improved certificateless signature scheme
In the hash value
4 Electricity Carbon Quota Trading Scheme Based on Certificateless Signature and Blockchain
Based on the improved certificateless signing scheme and blockchain technology presented in Section 3.3, we propose and analyze a secure and effective power carbon quota trading scheme.
The carbon quota trading model proposed in this paper is shown in Fig. 4, including six participants: the environmental protection management department (EPMD), quota seller enterprise (QSE), blockchain network (BN), quota buyer enterprise (QBE), audit department (AD), and distributed storage hash table (DSHT).
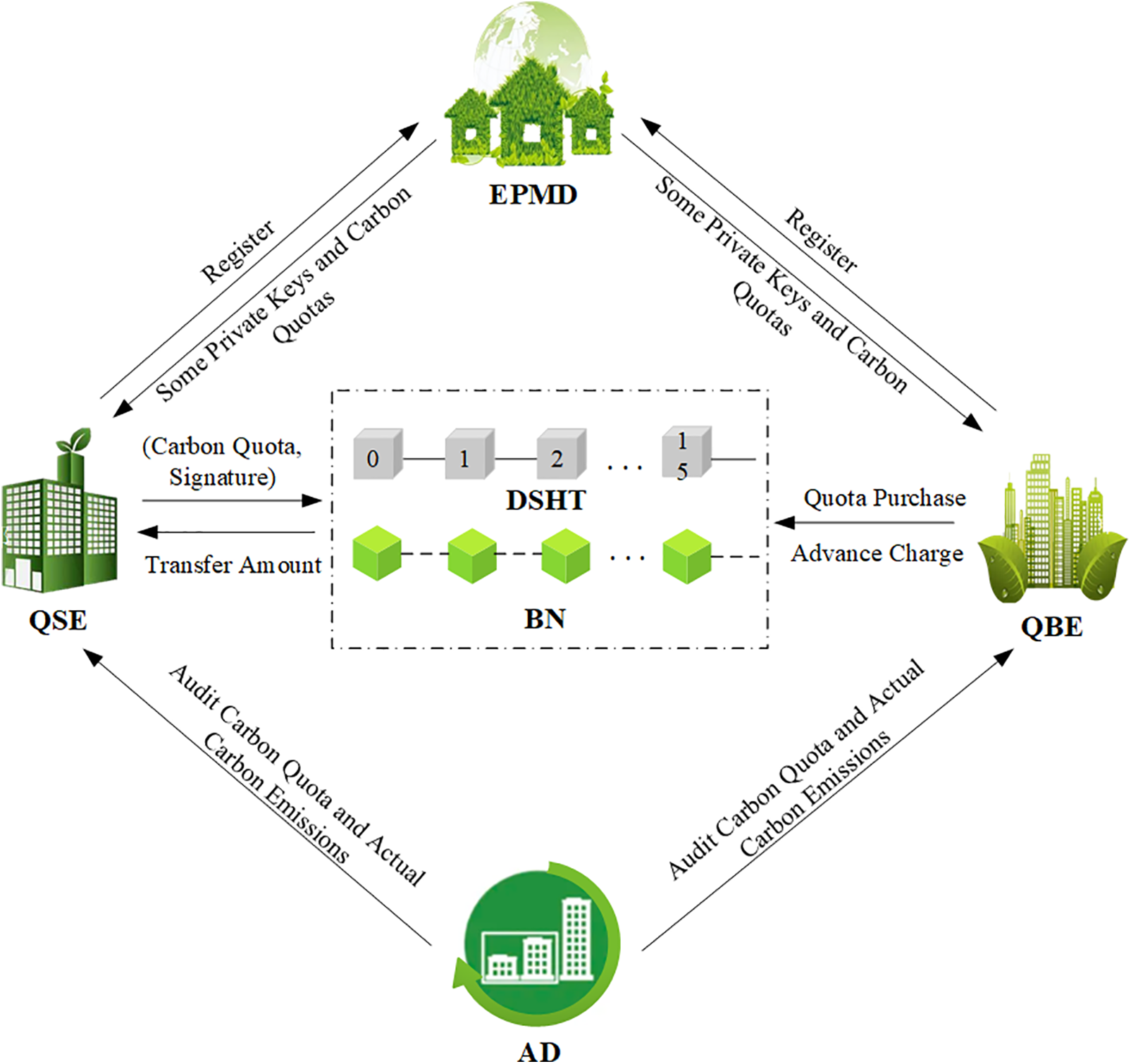
Figure 4: System model
(1) EPMD: Mainly responsible for system initialization, maintenance of the blockchain network, and distribution of some private keys and initial carbon quotas of power enterprises.
(2) QSE: Power enterprises with surplus carbon quotas sign the carbon quota to be sold and then publish it to the blockchain network for trading.
(3) BN: This network is mainly accountable for processing the storage and transaction requests of power carbon quota transactions and validating transaction legitimacy.
(4) QBE: Power enterprises with insufficient carbon quotas purchase carbon quotas through the blockchain network and pay transaction costs to the seller enterprises.
(5) AD: Mainly audits electric power enterprise carbon emission quotas and actual carbon emissions and assists the environmental protection management department in resolving transaction disputes.
(6) DSHT: Mainly stores relevant data on electric power enterprises and carbon quota transactions. Essentially, it is a distributed storage space that divides the data into several small pieces, gives them to different clients for storage, and then uses the storage address to read the data.
(1) System initialization: The environmental management department runs the system establishment algorithm of the improved certificateless signature scheme described in Section 3.3 and sets
(2) Enterprise registration: The power enterprise whose real identity is
After receiving
① Verify the identity information of
② Save
③ Select a random number
④ Calculate
⑤ Calculate the partial private key
⑥ Allocate the initial carbon emission quota
⑦ Send
⑧ Publish a correctly registered transaction
After receiving
(3) Quota sale: For the surplus electric power carbon emission quota
① Execute the signature generation process outlined in Section 3.3 of the enhanced certificateless signature scheme and generate the signature
② Publish on the blockchain a transaction
(4) Quota purchase: When the enterprise with the pseudonym
① Check the freshness of
② Find the cred
③ Perform the signature verification procedure described in Section 3.3 of the improved certificateless signature scheme. If
④ If
⑤ Send
⑥ In enterprise credit pool
⑦ The enterprises of both parties shall go through the relevant carbon quota transfer filing formalities in the environmental protection management department and terminate the carbon quota transaction.
(5) Dispute arbitration: If there is a dispute regarding the electric carbon emission quota

Figure 5: The interactions between blockchain and entities
5 Security and Performance Analysis
Based on the methods in [10,14], Theorem 1 and Theorem 2 prove that our proposed scheme can resist signature forgery attacks from malicious users and malicious KGCs.
Theorem 1 If the DL hypothesis is true, our scheme is unfakable for the first type of attacker.
Proof: If the first type of attacker C forges a valid signature of our scheme, then the DL problem can be solved by constructing an Algorithm C as the challenger. Given an instance of a DL problem
(1) System initialization: C sets
(2) Query: C creates 5 blank initialized tables
①
②
③
④
⑤ Public key query: When
• If
• If
⑥ Secret value query: When
⑦ Partial private key query: When
⑧ Public key replacement query: When
⑨ Signature query: When
(3) Forgery: After a finite number of the above queries,
Therefore,
Nevertheless, the DL problem is difficult to solve in polynomial time, indicating that
Theorem 2 If the LD hypothesis is valid, our scheme is unforgeable for the second type of attacker.
The proving procedure for Theorem 2 is comparable to that of Theorem 1. Because the second sort of attacker has access to the KGC’s master key, partial private key queries and public key replacement queries are no longer conducted.
(1) Anonymity: The real identity
(2) Traceability: When there is a dispute in an enterprise-issued energy carbon quota transaction, the environmental protection management department looks up
(3) Integrity, authenticity, and nonrepudiation: The power carbon quota transaction issued by the enterprise of the seller must be appended with signature
(4) Resist replay attack: When the buyer’s enterprise purchases the electricity carbon quota, it checks the freshness of the transaction through timestamp
Tables 1 and 2 exhibit the performance and function comparisons between our scheme and published schemes [10,11,14]. Reference [18] evaluated the operation time of cryptographic operations, where


As seen in Tables 1 and 2, Figs. 6, and 7, compared with other schemes [10,11,14], our scheme has the minimum time cost in generating and verifying signatures and the shortest signature length. Our scheme introduces the use of blockchain technology to eliminate intermediaries and improve the efficiency, transparency, and traceability of carbon quota trading in the electricity industry.

Figure 6: Comparison of computational overhead
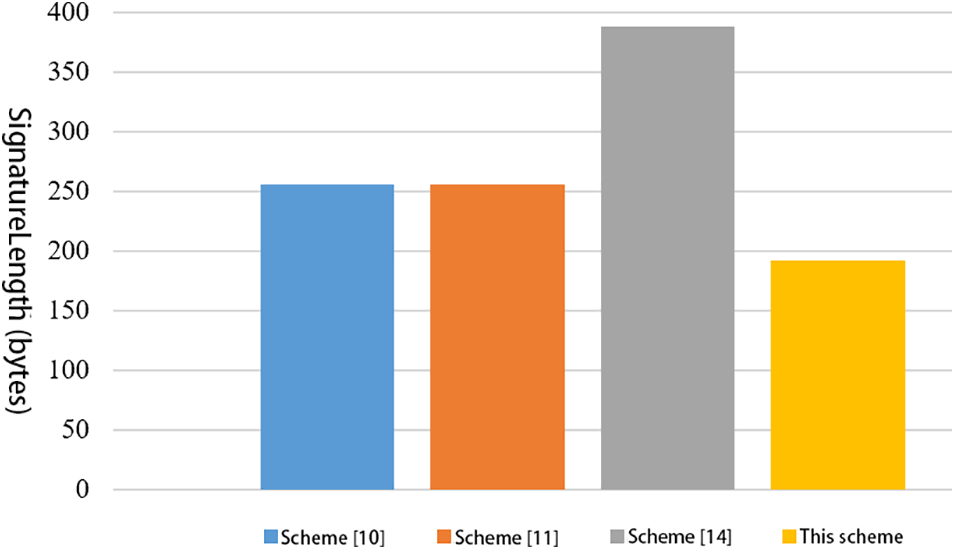
Figure 7: Comparison of signature length
The experimental environment for building the blockchain is Intel(R) Xeon(R) Gold 6133 2.50 GHz with Ubuntu Server 22.04 LTS 64-bit operating system, and the underlying platform for the blockchain is Hyperledger Fabric. The experiment simulated the generation of 1,000 to 5,000 user data entries, and tested the time it takes to upload the user data to the blockchain and the time it takes to retrieve the data from the blockchain. The specific test results are shown in Figs. 8 and 9.

Figure 8: User data upload time

Figure 9: User data return time
The test results show that as the amount of user data increases, the upload time slightly increases and the efficiency decreases slightly, but this decrease is within an acceptable range compared to the significant increase in data volume. When retrieving user data, the blockchain needs to run a consensus algorithm to disclose data to the nodes, and the degree of impact on time varies depending on the consensus algorithm used, so the retrieval time is slightly lower than the upload time.
We propose an efficient electricity carbon emission quota trading scheme based on an improved certificateless signature scheme and blockchain technology. Ensure the integrity and security of the transaction by signing without the certificate, and using the blockchain to store the transaction data to improve the anti-tampering and traceability of the power carbon quota transaction.
Our scheme provides conditional privacy protection, not only to protect the identity privacy of power enterprises but also to track the real identity of power enterprises that issue disputed transactions. However, our scheme does not consider the confidentiality of transaction data. Therefore, we plan to design a power carbon quota trading scheme based on blockchain and encryption technology in the future.
Acknowledgement: The authors wish to express their appreciation to the reviewers for their helpful suggestions which greatly improved the presentation of this paper.
Funding Statement: This research was supported by the National Fund Project No. 62172337, National Natural Science Foundation of China (No. 61662069) and China Postdoctoral Science Foundation (No. 2017M610817).
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Xiaodong Yang, Runze Diao; data collection: Tao Liu, Haoqi Wen; analysis and interpretation of results: Tao Liu, Haoqi Wen. Haoqi Wen; draft manuscript preparation: Xiaodong Yang, Runze Diao. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data used to support the study's findings are included in the paper.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Lin, B., Zhou, Y. (2021). Does the internet development affect energy and carbon emission performance. Sustainable Production and Consumption, 28(6), 1–10. [Google Scholar]
2. Wang, R., Cheng, S., Zuo, X., Liu, Y. (2022). Optimal management of multi-stakeholder integrated energy system considering dual incentive demand response and carbon trading mechanism. International Journal of Energy Research, 46(5), 6246–6263. [Google Scholar]
3. Zhang, L., Li, S., Nie, Q., Hu, Y. (2022). A two-stage benefit optimization and multi-participant benefit-sharing strategy for hybrid renewable energy systems in rural areas under carbon trading. Renewable Energy, 189, 744–761. [Google Scholar]
4. Wang, X. Q., Su, C. W., Lobont, O. R., Li, H., Nicoleta-Claudia, M. (2022). Is China’s carbon trading market efficient? Evidence from emissions trading scheme pilots. Energy, 245, 123240. [Google Scholar]
5. Zhang, Y., Wu, Q., Hu, W. (2023). Carbon quota trading model based on quantum blockchain. Journal of Systems & Management, 32(2), 300–307. [Google Scholar]
6. Zhu, X., Fu, Q., Wen, H., Zhong, Y., Su, Z. et al. (2020). Optimal allocation model of multi-energy entity energy storage from the perspective of blockchain. Electric Power Automation Equipment, 40(8), 47–56. [Google Scholar]
7. Ji, B., Liu, Y., Zhu, L. (2020). Design of carbon emission permit trading mechanism in power industry based on consortium blockchain. Huadian Technology, 42(8), 32–40. [Google Scholar]
8. Yuan, L., Li, D. (2020). Carbon emission mechanism design based on blockchain technology. Cyberspace Security, 11(2), 111– 117. [Google Scholar]
9. Liu, Y., Wang, D., Wang, Z., Duan, R. (2020). Efficient revocable certificateless signature scheme for cloud computing. Computer Engineering and Design, 41(9), 2442–2446. [Google Scholar]
10. Wang, D., Teng, J. (2018). Probably secure certificate less aggregate signature algorithm for vehicular ad hoc. Network Journal of Electronics & Information Technology, 40(1), 11–17. [Google Scholar]
11. Xu, Z., He, D., Kumar, N., Choo, K. R. (2020). Efficient certificateless aggregate signature scheme for performing secure routing in VANETs. Security and Communication Networks, 2020(2), 1–12. [Google Scholar]
12. Mei, Q., Xiong, H., Chen, J., Yang, M., Kumari, S. et al. (2020). Efficient certificateless aggregate signature with conditional privacy preservation in IoV. IEEE Systems Journal, 15(1), 245–256. [Google Scholar]
13. Deng, L., Ning, B., Jiang, Y. (2020). A lightweight certificateless aggregation signature scheme with provable security in the standard model. IEEE Systems Journal, 14(3), 4242– 4251. [Google Scholar]
14. Wang, H., Wang, L., Zhang, K., Li, J., Luo, Y. (2022). A conditional privacy-preserving certificateless aggregate signature scheme in the standard model for VANETs. IEEE Access, 10, 15605–15618. [Google Scholar]
15. Wang, Y., Li, L., Zhang, Y., Zhao, B. (2022). STRICTs: A blockchain-enabled smart emission cap restrictive and carbon permit trading system. Applied Energy, 306, 117848. https://doi.org/10.1016/j.apenergy.2022.117848 [Google Scholar] [CrossRef]
16. Luo, J., Han, M., Wang, J. (2020). A blockchain-based electricity carbon quota trading scheme with lightweight certificateless signature. IEEE Access, 8, 222830–222840. [Google Scholar]
17. Bagherzandi, A., Cheon, J. H., Jarecki, S. (2008). Multi signatures secure under the discrete logarithm assumption and a generalized forking lemma. Proceedings of the 15th ACM Conference on Computer and Communications Security (CCS’08), pp. 449–458. New York, NY, USA, Association for Computing Machinery. [Google Scholar]
18. Cui, J., Wu, D., Zhang, J., Xu, Y., Zhong, H. (2019). An efficient authentication scheme based on semi-trusted authority in VANETs. IEEE Transactions on Vehicular Technology, 68(3), 2972–2986. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools