 Open Access
Open Access
ARTICLE
Strategic Contracting for Software Upgrade Outsourcing in Industry 4.0
1 College of Mechanical Engineering, Zhejiang University of Technology, Hangzhou, 310014, China
2 Taizhou Research Institute, Zhejiang University of Technology, Taizhou, 318001, China
* Corresponding Author: Cheng Wang. Email:
(This article belongs to the Special Issue: Computing Methods for Industrial Artificial Intelligence)
Computer Modeling in Engineering & Sciences 2024, 138(2), 1563-1592. https://doi.org/10.32604/cmes.2023.031103
Received 14 May 2023; Accepted 06 July 2023; Issue published 17 November 2023
Abstract
The advent of Industry 4.0 has compelled businesses to adopt digital approaches that combine software to enhance production efficiency. In this rapidly evolving market, software development is an ongoing process that must be tailored to meet the dynamic needs of enterprises. However, internal research and development can be prohibitively expensive, driving many enterprises to outsource software development and upgrades to external service providers. This paper presents a software upgrade outsourcing model for enterprises and service providers that accounts for the impact of market fluctuations on software adaptability. To mitigate the risk of adverse selection due to asymmetric information about the service provider’s cost and asymmetric information about the enterprise’s revenues, we propose pay-per-time and revenue-sharing contracts in two distinct information asymmetry scenarios. These two contracts specify the time and transfer payments for software upgrades. Through a comparative analysis of the optimal solutions under the two contracts and centralized decision-making with full-information, we examine the characteristics of the solutions under two information asymmetry scenarios and analyze the incentive effects of the two contracts on the various stakeholders. Overall, our study offers valuable insights for firms seeking to optimize their outsourcing strategies and maximize their returns on investment in software upgrades.Keywords
To lead the new industrial revolution, countries are reviving their manufacturing industry [1,2]. Germany, an old manufacturing powerhouse, stands out by proposing Industry 4.0. Industry 4.0 aims to transform machine-led manufacturing into digital manufacturing by utilizing advanced information technology [3].
In the battle for the digitalization of manufacturing, software as an intermediary link between virtual and real interaction, has injected new energy into R&D, simulation verification, manufacturing, management, sales, and service in the manufacturing industry [4]. With government support, some large manufacturing enterprises have taken the lead in becoming trial sites and integrating software into their manufacturing processes. Siemens, a world-class industrial giant with a presence in home appliances, communications, medical, industrial, and other fields, has been a major beneficiary of software applications in its products and projects. Nowadays, more and more enterprise managers are increasingly aware of the benefits of software in improving efficiency. Moreover, the scope of software applications is no longer limited to internal enterprise operations. Instead, there is a growing interest in using software in the supply chain to achieve cooperation with upstream and downstream enterprises and overcome barriers across all links.
Software development is an ongoing process for enterprises. As market fluctuations occur and enterprise scales expand, software must be upgraded to meet the evolving needs of the business. Software upgrading involves updating the software from a lower version to a higher version. Market trends, industry transformations, or institutional replacements often require enterprises to upgrade or adjust their software. For instance, policies that promote “Internet + E-commerce” marketing models prompt enterprises to successively upgrade software to improve operating efficiency by focusing on procurement and distribution. Moreover, the complexity within the enterprise affects the scale of the enterprises, which is a dynamic process. As the number of employees increases, changes in management methods, technological progress, and adjustments to business chains make it difficult for closed software with single functions and outdated technology to respond quickly to enterprise needs. Upgrading the software to develop more functional services can help enterprises carry out various tasks smoothly and overcome inertia tendencies, thereby increasing enterprise profits [5].
Enterprises have two options for upgrading their software: self-upgrading and outsourcing. When enterprises opt to upgrade their software independently, they typically possess some in-house development capacity, and their internal IT department provides the software upgrade service. In this way, enterprise decision-makers can readily comprehend the software upgrade’s direction, monitor development progress, and enjoy the convenience of the ensuing maintenance, upgrade, and optimization processes. Alternatively, outsourcing involves hiring professional service providers like IBM, Oracle, and Microsoft, who have emerged as software service providers with their professional technology and development capabilities and can provide one-stop software upgrade services to the enterprise.
The distinguishing factor in the context of Industry 4.0 is the emphasis on integration and digitization. Industry 4.0 implementation involves three key dimensions: vertical integration, horizontal integration, and end-to-end integration [6]. Vertical integration focuses on achieving intelligent interconnection and digitization within the production system, primarily through production networking. Horizontal integration aims to achieve intelligent interconnection and digitization between organizations across the entire value network [7]. Lastly, end-to-end integration seeks to achieve intelligent interconnection and digitization throughout all stages of the lifecycle. In short, vertical integration primarily addresses digital integration within an organization. On the other hand, horizontal and end-to-end integration focus on establishing cross-organizational digital networks involving various entities. The method of enterprise software upgrade plays a crucial role in this context. When an enterprise chooses to independently upgrade its software, the upgrade service is typically provided by the enterprise’s IT department, falling under the category of vertical integration. Conversely, when an enterprise outsources the software upgrade to an external service provider, it involves both the enterprise and the service provider, constituting horizontal integration.
The rise of software outsourcing has brought attention to the principal-agent relationship between enterprises and service providers. The principal-agent theory highlights the risk of reverse selection when there is ex-ante information asymmetry and inconsistent interests between parties [8,9]. In the context of software outsourcing, the service provider typically possesses more information about the software upgrade’s capabilities, qualifications, quality, and cost, while the enterprise has greater knowledge of the software’s business value, industry characteristics, and business process. Such information asymmetry can lead to conflicts and damaged interests of one party over the other.
An effective mechanism or contract can address the reverse selection problem that arises due to inconsistent interests and asymmetric information of both parties [10]. In the context of Industry 4.0, the traditional contracts used in software outsourcing may need to be adapted to accommodate the specific characteristics and requirements of digital manufacturing. Unlike traditional manufacturing processes, Industry 4.0 involves a higher level of automation, connectivity, and data exchange, requiring software to be adaptable, scalable, and capable of integrating with various digital technologies and devices. Therefore, the contracts for software upgrade outsourcing in the context of Industry 4.0 should consider these unique aspects and ensure the software’s compatibility and interoperability within the digital manufacturing ecosystem.
The motivating context for this problem is the design of contracts for customized software upgrade supply chain in the Industry 4.0 era, consisting of an enterprise and a service provider. The service provider offers tailored software upgrade services to the enterprise, which faces a diminishing utility of its current software version due to market fluctuations. Given the existence of asymmetric information in software upgrade outsourcing, we adopt a principal-agent model. Within this framework, the agent possesses superior information, while the principal lacks crucial knowledge and assumes the responsibility of contract design. In order to motivate agents to engage in software upgrades, the principal must devise a contract menu that offers multiple options, tailored to each agent type. During the contract design phase, agents reveal their information type by selecting the contract aligned with their characteristics. In the contract execution phase, the service provider delivers the upgrade service to the enterprise at the appropriate time, and in return, the enterprise compensates the provider with the corresponding fee. By solving the equilibrium solutions for different scenarios, we derive software upgrade time and generalize the characteristics of the solutions. Ultimately, this research provides managerial implications for enhancing the efficiency and effectiveness of software upgrade outsourcing contract.
Our paper makes the following contributions: Firstly, we investigate the optimal software upgrade timing decision in response to market fluctuations when a centralized decision is made with full-information. Secondly, we use contracts to address the information asymmetry between the service provider and the enterprise in two scenarios where the former has cost information and the latter has revenue information. Thirdly, we explore the impact of different performance-based contracts on software upgrade timing decisions and profits under information asymmetry. Finally, we compare the equilibrium solutions of using a pay-per-time contract and a revenue-sharing contract under cost and revenue information asymmetry scenarios, respectively, to determine their incentive effects on the parties involved.
This research holds significant importance for both enterprises and service providers operating in the software outsourcing market. By introducing a novel software upgrade outsourcing model that incorporates the influence of market fluctuations on software adaptability, this study presents a valuable decision framework that differs from traditional research perspectives. The proposed pay-per-time and revenue-sharing contracts address the challenges of adverse selection caused by asymmetric information. Through a comparative analysis, the research highlights the characteristics and incentive effects of these contracts on various stakeholders. The findings not only provide a theoretical basis for future research and further exploration of optimal contract design in software outsourcing but also offer practical insights for firms in making informed outsourcing decisions and maximizing their returns on investment. The innovative nature of this research lies in its ability to merge the principles of Industry 4.0 with software upgrade outsourcing, effectively empowering enterprises to optimize their software systems and adapt to the demands of the digital era.
The framework of this paper is as follows: The literature review in Section 2 provides an overview of relevant research. Section 3 outlines the software upgrade outsourcing model between the enterprise and the service provider. In Section 4, we solve for the optimal software upgrade timing strategy under complete information centralized decision-making. Section 5 investigates the impact of two performance-based contracts on optimal software upgrade timing decision-making under incomplete information decentralized decision-making. Finally, Section 6 summarizes our work and findings. The proof process for the Propositions in this paper is detailed in Appendixes A and B.
This section will elaborate on the characteristics of software outsourcing from three perspectives: enterprise software development strategy, software outsourcing objects, and asymmetric information.
Software development strategy in an enterprise can be classified into two categories based on the mode of development: internal development and outsourcing [11]. Enterprises that opt for in-house development typically have a certain level of R&D capability, which enables them to maintain strict control over the direction and progress of software development. In contrast, software outsourcing involves subcontracting part or all of an enterprise’s software project to an external service provider. Software outsourcing can be further divided into full outsourcing and partial outsourcing based on the degree of outsourcing [12,13]. Most enterprises choose software outsourcing to reduce costs, access advanced resources, and focus on their core business. However, software outsourcing also comes with risks, such as loss of control over information systems, hidden costs, and loss of innovation [14].
Research on the economic aspects of enterprise software development strategies dates back to Richmond et al. [15], who explored the impact of different revenue rules on enterprises’ decisions to choose between in-house development or outsourcing, based on a two-stage software development model. Another study by Wang et al. [16] compared the value brought to the company by in-house development and software outsourcing, and determined that in-house R&D would generate more net profit. Early literature analyzed the software development strategies of enterprises, internal development or software outsourcing, mainly from an economic perspective. In contrast, this paper focuses solely on enterprise software outsourcing and aims to achieve the same level of results as in-house R&D through effective contract design.
When enterprises choose to outsource their software, outsourcing can be classified into two types: software development outsourcing and software upgrade outsourcing, based on the specific outsourcing object. Software development outsourcing involves the outsourcing of software development processes to external service providers, who help the enterprise to create software from scratch. Casado-Lumbreras et al. [17] have identified various challenges and opportunities associated with enterprise software development. To address the potential conflicts between the host firm and the outsourcing firm, Bandyopadhyay et al. [18] developed a knowledge-sharing model for software outsourcing teams.
A software upgrade is a newer version of the software that has been developed. Enterprise software upgrades are usually pursued for various reasons, such as reducing operational costs, pursuing new business opportunities, or breaking free from inertia tendencies. When an enterprise decides to outsource software upgrades, the service provider is often the same one that provides software development services. Despite the widespread practice of outsourcing software upgrades, there is relatively little literature on this topic. Pricing is one of the major concerns of enterprises. To price their products, software providers need to consider the attractiveness of both current and future versions. Kornish [19] developed a two-stage game model that demonstrates the existence of an equilibrium pricing strategy if special pricing is applied to consumers who purchase earlier versions. Meanwhile, Bala et al. [20] studied the optimal pricing of new versions by examining the relationship between the magnitude of software product improvements and the structure of equilibrium pricing. Instead of focusing on pricing strategies for new software versions, we explore the adaptability of software and the optimal software upgrade timing strategy.
When enterprises outsource software development, they often face information asymmetry with the external service provider. Existing research categorizes information asymmetry into three types: (1) ex-ante and ex-post information asymmetry based on when it occurs, (2) information type and behavioral information asymmetry based on the content of information, and (3) information asymmetry of the service provider and the outsourcer based on the subject of the information. These three categories of information asymmetry are common in studies related to outsourcing. In the software outsourcing literature, studies typically focus on software value, cost, quality, capability, effort, and other types of information [21–23].
2.2 Adverse Selection Problem and Its Solution
The software upgrade outsourcing relationship between the service provider and the enterprise can be seen as a principal-agent relationship. However, this relationship is characterized by inconsistent interests and information asymmetry, leading to adverse selection [24,25]. Adverse selection occurs when one party in the market uses more information than the other party (such as software value, cost, and agent ability information) to benefit themselves and harm the other party’s interests before the contract is signed [26]. In different fields, research has provided insights to address the adverse selection problem for ex-ante information asymmetry in various contexts.
In their study of carbon capture and storage systems, Cai et al. [27] developed a principal-agent model that addresses the adverse selection problem caused by asymmetric ex-ante information between contracting parties. An interesting aspect of their work is the consideration of a heterogeneous distribution of agent demand with varying levels under each distribution. Many studies focus on the asymmetric information in only one scenario, our paper investigates the adverse selection problem in two scenarios: the service provider’s cost information asymmetry and the enterprise’s revenue information asymmetry.
An effective contract design can solve the adverse selection problem between the contracting parties. Considering that outsourcing investments are irreversible and costs are uncertain, Yao et al. [28] analyzed the issues of when to outsource, how to choose a contract, and how to negotiate an outsourcing contract by building a model.
In the software outsourcing domain, contracts are often incomplete due to unpredictable events in an incomplete contract environment [29]. Time-and-materials (T&M) contracts and fixed-price (FP) contracts are two common types used [30]. T&M contracts have some risk protection and consist of two components: the project development cost and the service provider’s profit. In contrast, fixed-price (FP) contracts have a price cap and are not adjusted once set within the agreed risk range. FP contracts are less efficient for software projects with high uncertainty in software development costs, and are suitable for software projects with low development difficulty and short development time. T&M contracts can be used for relatively difficult software projects, but need to be coupled with project supervision and require enterprises to have relevant software development knowledge. According to Gopal et al. [31], FP contracts make providers more efficient in the software development process and develop higher-quality software.
As software development becomes more complex, contract designers are increasingly considering performance-based contracts (PB) to align the interests of both parties. PB contracts tie the service provider’s revenue to the quality and performance of the software. Revenue-sharing (RS) contracts are the most common type of PB contract, where the revenue generated by the software is shared between the service provider and the enterprise. Contract designers need to select and design contracts based on the specific requirements of software outsourcing projects and incentive goals to achieve the optimal outcome. To address the challenge of monitoring service provider efforts during software development, Huang et al. [32] explored the effect of monitoring on the choice between a time-and-material contract and a revenue-sharing contract. In this paper, we investigate the impact of two performance-based contracts, pay-per-time and revenue-sharing contracts on the optimal software upgrade time.
This section presents the software upgrade outsourcing model between an enterprise and a service provider. The enterprise relies on customized software to generate revenue, but over time, the adaptability of the software decreases due to market fluctuations. The service provider offers software upgrades to the enterprise, aiming to enhance its software’s adaptability. Both parties must make strategic decisions regarding the optimal timing of software upgrades. This section outlines the key elements of the software upgrade outsourcing model.
Software Adaptability Deterioration: The software’s adaptability gradually diminishes as it operates in a changing market environment. Initially, when the software is fully adapted to the current environment, it generates significant revenue per unit time denoted as R, which varies based on the scale of the enterprise. The larger the enterprise, the higher the revenue per unit time that can be generated for the enterprise when the software is fully adapted to the current environment.
However, due to market fluctuations represented by
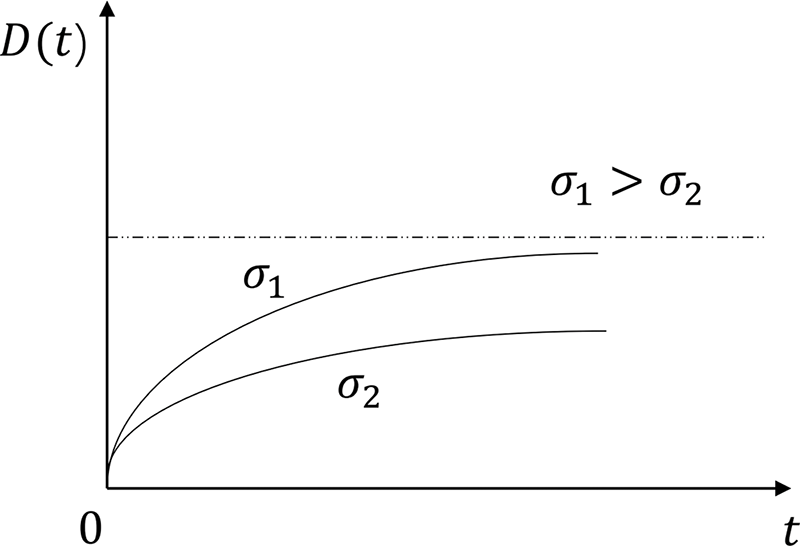
Figure 1: The relationship between the degree of software deviation and upgrade practices and market volatility
where
Enterprise Perspective: The existence of a gap between the existing software version and the version adapted to the current environment hinders enterprises from fully realizing their value, which can result in substantial costs. For instance, in the “Internet + E-commerce” marketing mode, many enterprises have upgraded their software to remain competitive. Failure to take action may lead to the erosion of the enterprise’s original market share by competitors that have adopted “Internet + E-commerce” models, resulting in financial losses. Therefore, the actual revenue P of the enterprise comprises two components: revenue received when the software is fully adapted to the current environment and lost due to the gap between the existing software version and the software version adapted to the current environment. Mathematically, this can be expressed as:
The service provider offers software upgrades to the enterprise, and in return, the enterprise pays the service provider a fee, denoted by T. We assume that the software upgrade provided by the service provider will be successful.
The Service Provider Perspective: The service provider incurs costs associated with software upgrades, comprising fixed costs and variable costs. The fixed costs K represent the resources invested by the service provider, including human resources, for each software upgrade. The variable costs
where
Performance-Based Contracts: In the realm of service contracts, performance-based (PB) contracts are commonly employed to align the agent’s interests with those of the principal. These contracts establish a direct link between the agent’s profits and their performance, thereby incentivizing actions that benefit the principal. Our study focuses on two specific types of PB contracts: pay-per-time contracts and revenue-sharing contracts.
The pay-per-time contract encompasses two key elements: the timing of software upgrades and transfer payments. This contract structure outlines when the software upgrades should take place and determines the corresponding transfer payments to the service provider. On the other hand, the revenue-sharing contract entails a collaborative approach between the enterprise and the service provider, where they jointly partake in the revenue generated by the software. Similar to the pay-per-time contract, this arrangement incorporates considerations regarding the optimal timing of software upgrades. Additionally, it outlines the proportion of revenue that the service provider will receive as part of the transfer.
The existence of unobservable information (the service provider’s cost information/the enterprise’s revenue information) gives rise to the challenge of adverse selection in software upgrade outsourcing contracts. This information asymmetry poses a significant hurdle prior to contract signing. However, despite the inability to directly observe the asymmetric information between the service provider and the enterprise, the party at the information disadvantage in our model can strategically design the contract to gain insights into the information advantage held by the other party.
Assumptions: To simplify the calculation process, our model does not consider the time required for the service provider to develop the new version, the time needed for the enterprise to install the new version, and the impact of market fluctuations on the existing software version during the service provider’s research and development phase.
For a comprehensive understanding of the model, we provide a list of parameters involved and their descriptions in Table 1.
Next, we explore the properties of optimal software upgrade time for outsourcing in two different settings: one with full-information and the other with incomplete information.
4 Benchmark: Centralized Decision with Full-Information
To establish a benchmark, we first analyze the optimal software upgrade timing decision in a centralized decision-making case with full-information. In this scenario, the service provider is treated as a department of the enterprise, and the payment from the enterprise to the service provider is purely monetary. Hence, the problem is to determine the optimal software upgrade time
Proposition 4.1 characterizes the optimal software decision for centralized decision-making with full-information, which is proved in Appendix A.
Proposition 4.1. For centralized decision with full-information, when R ≥ kσ, t∗. takes infinity, indicating that the software does not need to be upgraded during its use. When 0 ≤ R < kσ, the optimal software upgrade time and the optimal expected profits of the system are
Moreover, t∗ and W(t∗) are increasing in R and decreasing in σ.
The optimal software upgrade timing decision for centralized decision with full-information can be divided into two cases. In the first case, where
In the second case, where
Furthermore, for centralized decision-making with full-information, the optimal software upgrade time is delayed as the enterprise scale expands and advanced as market fluctuations increase. Moreover, the expected profits of the system increase with the expansion of the enterprise scale, but decrease with the increase of market fluctuations.
5 Contract Design in the Case of Decentralized Decision with Incomplete Information
In a software upgrade outsourcing relationship, the service provider and enterprise often keep their cost and revenue information private. This lack of transparency can result in adverse selection if the enterprise does not have accurate access to the service provider’s cost information. The service provider may inflate the cost of the software upgrade to secure a higher profit margin before signing the contract. Conversely, if the service provider does not know the true revenue information of the enterprise, the enterprise may under-report its software revenue to gain excess revenue, leading to further adverse selection problems. To address these issues, this section proposes the use of incentive contracts that screen the true information of service providers and enterprises in situations where they have private information. The goal is to achieve the optimal solution in a centralized decision-making environment with full-information.
In this section, we establish the software upgrade outsourcing relationship between the enterprise and the service provider as a principal-agent model, based on the widely-used principal-agent theory. In principal-agent theory, the party possessing private information is referred to as the agent, while the party lacking information is known as the principal.
5.1 Contract Design for the Service Provider with Private Cost Information
As mentioned earlier, the service provider’s costs consist of fixed and variable costs. Fixed costs refer to the human resource costs invested by the service provider, which can be estimated by the enterprise based on the average salary of software developers in the market. Hence, we consider fixed costs as common knowledge between the parties to the contract. On the other hand, variable costs are influenced by the software deviation degree D and the cost coefficient
Assuming that service providers in the market can be categorized into high-cost and low-cost types based on their cost coefficient, denoted by
5.1.1 Pay-Per-Time Contract Offered by the Enterprise
We consider a scenario where the service provider possesses private cost information. In this case, the enterprise offers a pay-per-time contract

Figure 2: The time line using pay-per-time contracts where the service provider has privare cost information
In the contract design stage, the service provider knows its cost type, but the enterprise only has prior beliefs about the likelihood of the service provider’s variable cost coefficient type. The service provider is presented with a contract menu,
In the contract execution stage, the enterprise identifies the cost type of the service provider based on the chosen contract. Once the contract is signed, the service provider delivers the software upgrade service at the agreed-upon time, and the enterprise makes the corresponding payment based on the upgrade time.
In outsourcing agreements, the enterprise’s contract aims to maximize its profits while also satisfying the service provider’s individual rational (IR) and incentive compatibility (IC) constraints. To achieve this, an optimal contract can be formulated as follows:
The individual rationality (IR) constraints, denoted by
Proposition 5.1 describes the optimal menu of a pay-per-time contract provided by the enterprise in the context of asymmetric cost information, as proved in Appendix B.
Proposition 5.1, Under the condition 0 ≤ R < klσ, using pay-per-time contract in the case where the service provider has private cost information, the optimal contract menu designed by the enterprise is
In Proposition 5.1,
In the context of pay-per-time contracts with asymmetric cost information, the optimal software upgrade time for low-cost service providers remains the same as in the case of the centralized decision with full-information, while the optimal software upgrade time for high-cost service providers is distorted downward. Specifically,
This is because, in a centralized decision with full-information, the enterprise can offer contracts that correspond to the cost type of the service provider, and maximize profits by ensuring that both types of service providers receive zero utility. However, when the service provider has private cost information, the enterprise needs to design the contract in a way that allows the high-cost type service provider to receive zero utility, while preventing the low-cost type provider from masquerading as the high-cost type to gain positive utility. In other words, to achieve a separation equilibrium, the enterprise may choose to transfer some information rent to the low-cost type service provider with a cost advantage, so that their profits are equal to those obtained by selecting the high-cost type service provider. In essence, enterprises must carefully craft contracts to effectively differentiate between the two cost types of service providers and maximize their profits accordingly.
5.1.2 Revenue-Sharing Contract Offered by the Enterprise
Next, we consider that when the service provider has private cost information, the enterprise offers a revenue-sharing contract that includes a term

Figure 3: The time line using revenue-sharing contracts where the service provider has privare cost information
The enterprise design a contract menu
Therefore, under the asymmetric cost information of the service provider, the problem of the enterprise is to design the contract menu
Proposition 5.2 characterizes the optimal contract menu and its proof is given in Appendix B.
Proposition 5.2. Under the condition that
By comparing the optimal solutions achieved using the pay-per-time contract, revenue-sharing contract, and centralized decision-making with full-information, we can obtain
where
Eqs. (17)–(18) demonstrate that the optimal software upgrade time for both high and low-cost service providers is the same under both the revenue-sharing and pay-per-time contracts. Likewise, Eqs. (19)–(20) show that the payouts paid to high and low-cost service providers under the revenue-sharing contract are equivalent to the payouts paid under the pay-per-time contract. Therefore, our findings suggest that these two contracts are equivalent in cases where there is asymmetric information about the service providers’ costs.
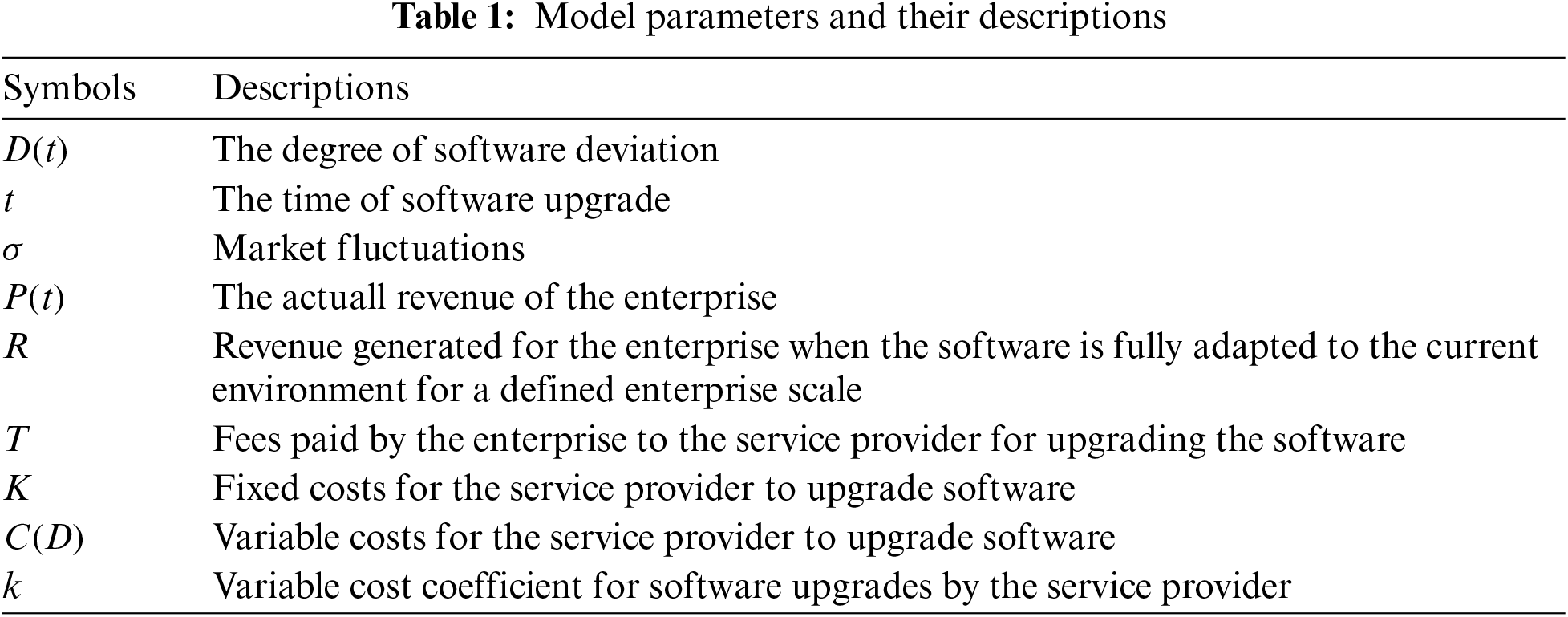
Fig. 4 compares the profits of the enterprise under centralized decision-making with full-information, pay-per-time contract, and revenue-sharing contract when the service provider has private cost information. The profit curves for pay-per-time and revenue-sharing contracts overlap exactly, indicating their equivalence in the presence of asymmetric information about the service provider’s costs. However, due to the need to transfer some information rent to low-cost type service providers, the enterprise’s profits under these contracts are always lower than those under centralized decision-making with full-information, as shown in Fig. 4.
Figure 4: Profits comparison for the enterprise,
5.2 Contract Design for the Enterprise with Private Revenue Information
As previously noted, the revenue generated by the software fully adapting to the current environment is denoted as R, and it is proportional to the scale of the enterprise. However, enterprises of the same scale may have different revenues due to their unique characteristics and industry conditions. We assume that enterprises of the same scale in the market can be classified as either high-revenue or low-revenue types. Let
5.2.1 Pay-Per-Time Contract Offered by the Service Provider
We now explore the use of a pay-per-time contract when the enterprise possesses private revenue information. In contrast to the scenario where the service provider has private cost information, when the enterprise has private revenue information, the service provider designs the contract. This contract has a term

Figure 5: The time line using pay-per-time contracts where the enterprise has privare revenue information
In the contract design stage, before signing the contract, the enterprise is aware of its revenue type, and the revenue generated by the software remains confidential to the enterprise. The service provider designs a contract menu
In the contract execution stage, the service provider determines the revenue information type based on the contract selected by the enterprise. Once the contract is signed, the service provider offers software upgrade services at the agreed-upon time. The enterprise then pays for the upgrade based on the upgrade time.
In this case, we can express the optimal contract menu between the parties as follows:
Proposition 5.3 describes the optimal menu of the pay-per-time contract offered by the service provider when the enterprise has private revenue information, which is proved in Appendix B.
Proposition 5.3. Under the conditions that
Compared with the optimal contract in the case of centralized decision with full-information, the optimal software upgrade time of the high-revenue type enterprise remains unchanged, while the optimal software upgrade time of the low-revenue type enterprise is distorted downward,
The above phenomenon can be attributed to the following reasons: when the enterprise has private revenue information, the service provider can still design the contract such that the low-revenue type enterprise obtains zero utility. However, to prevent the high-revenue type enterprise from gaining positive utility by pretending to be the low-revenue type enterprise, the service provider must eliminate the incentive to imitate. This is achieved by ensuring that high-revenue type enterprises earn the same profit by selecting a contract that matches their type as they would if they imitated low-revenue type enterprises. In other words, the service provider chooses to pay a portion of the information rent to the revenue-advantaged enterprise in order to achieve a separation equilibrium.
5.2.2 Revenue-Sharing Contract Offered by the Service Provider
In the following, we turn to the scenario where the service provider proposes a revenue-sharing contract in the presence of private revenue information held by the enterprise. The terms of the contract are denoted as

Figure 6: The time line using revenue-sharing contracts where the enterprise has privare revenue information
Thus, in the case where the enterprise has private revenue information, the service provider’s problem is to design the optimal contract menu
Proposition 5.4, proved in Appendix B, characterizes the optimal revenue-sharing contract menu offered by the service provider when there is asymmetric revenue information from the enterprise.
Proposition 5.4. Under the condition that
Proposition 5.4 shows that when using a revenue-sharing contract with private revenue information from the enterprise, the optimal software upgrade times for high and low-revenue enterprises are the same as those in the centralized decision case, with “no distortion at either the high or low end (the high-revenue or low-revenue type enterprise)”. Additionally, both high and low-revenue enterprises are required to transfer all revenues to the service provider. These findings suggest that a revenue-sharing contract can achieve the optimal solution in the case of a centralized decision with full-information when there is asymmetric information about the enterprise’s revenues.
The pay-per-time contract and the revenue-sharing contract yield quite different results when the enterprise has private revenue information. The reason is that in a revenue-sharing contract, the service provider treats both high and low-revenue enterprises equally, requiring both types to transfer all revenues. This prevents the high-revenue enterprise from imitating the low-revenue enterprise and obtaining positive profits, leading both types to obtain zero utility. Thus, the enterprise selects the contract that matches its true type regardless of revenue. Therefore, using a revenue-sharing contract under private revenue information achieves the optimal solution in the case of a centralized decision with full-information.
However, under a pay-per-time contract, the service provider values high-revenue enterprises more than low-revenue enterprises. As a result, the service provider takes all the revenue from the low-revenue enterprise and offers information rent to the high-revenue enterprise as an incentive to choose the contract that matches its true type. This leads to a phenomenon known as “no distortion at the high end and downward distortion at the low end,” where the contract is accurate for high-revenue enterprises but distorted for low-revenue enterprises.
Fig. 7 plots the profits of the service provider offering a pay-per-time contract and a revenue-sharing contract when the enterprise has private revenue information. The two curved surfaces in Fig. 7 illustrate that, under the same enterprise scale and market distribution, the blue curved surface is consistently higher than the red curved surface. This indicates that the service provider can generate greater profits by providing a revenue-sharing contract than by providing a pay-per-time contract when the enterprise has private revenue information. The reason for this is that under a pay-per-time contract, the service provider must transfer part of the information rent to the high-revenue enterprise. However, by offering a revenue-sharing contract, the service provider not only avoids the need to transfer information rent but can also achieve the optimal solution similar to the centralized decision with full-information. Thus, when the enterprise has private revenue information, the service provider prefers to choose the revenue-sharing contract.
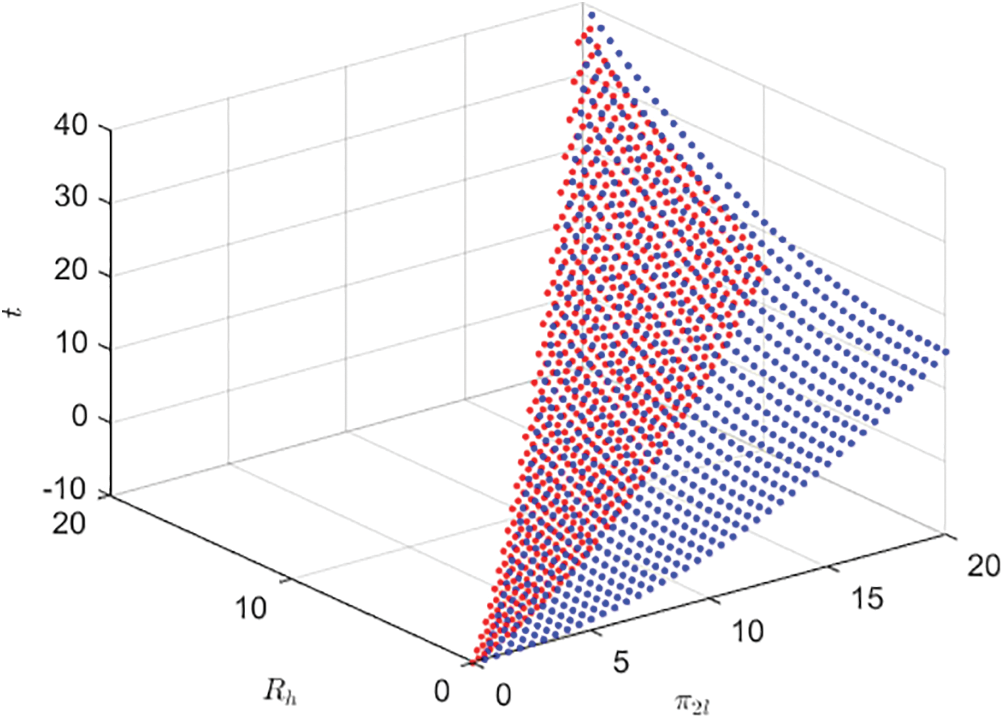
Figure 7: Profits for the service provider under the pay-per-time contracts and revenue-sharing contracts,
5.3 Comparision of Optimal Solutions and Incentive Effect
Table 2 presents the optimal solutions obtained through the pay-per-time and revenue-sharing contracts. These contracts address the adverse selection problem in two scenarios where the service provider has private cost information and the enterprise has private revenue information. Next, we compared the results with those obtained from centralized decision-making with full-information to assess the incentive effects of the contracts.
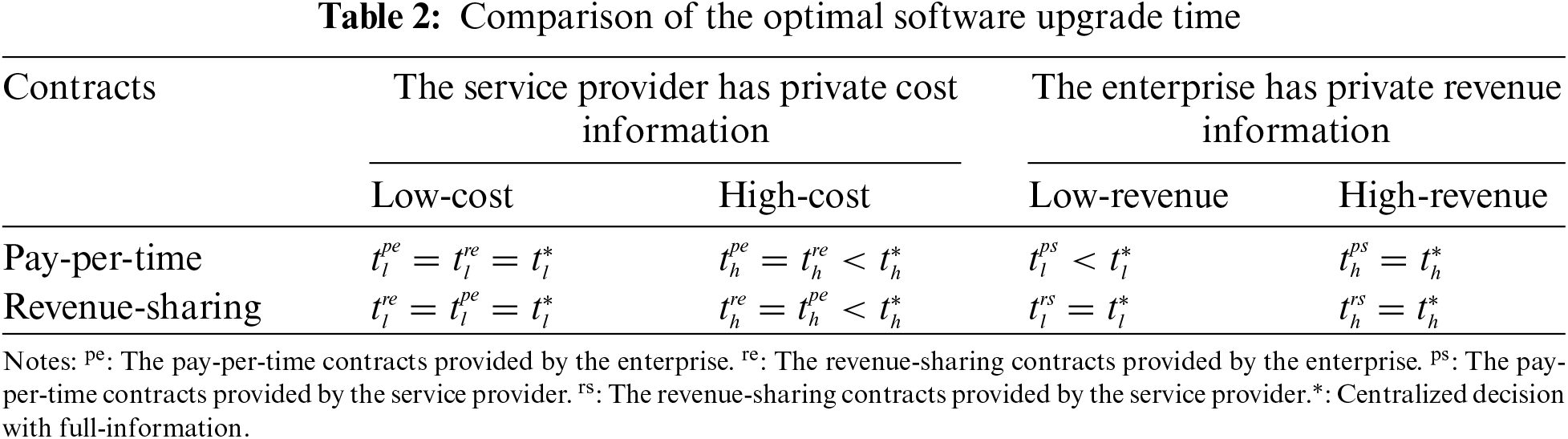
Section 5.1 investigates the impact of contracts on software upgrade decisions when service providers hold private cost information. We found that the pay-per-time and revenue-sharing contracts yield the same optimal solutions under this scenario. That is, both contracts fail to achieve optimal incentives when the service provider is a high-cost type, leading to suboptimal solutions. Only when the service provider is a low-cost type do the pay-per-time and revenue-sharing contracts produce outcomes consistent with the centralized decision-making approach. These findings suggest that both contracts have similar incentive effects on service providers when cost information is asymmetric, but neither can fully achieve optimal incentives.
Section 5.2 examines the impact of contracts on software upgrade decisions when the enterprise has private revenue information. The results show that when the enterprise is a high-revenue type, the optimal solutions for both the pay-per-time and revenue-sharing contracts align with the centralized decision case. However, when the enterprise is a low-revenue type, the pay-per-time contract yields suboptimal solutions, while the revenue-sharing contract maintains optimal incentives. These findings suggest that the revenue-sharing contract provides superior incentives compared to the pay-per-time contract and can achieve optimal results in the presence of asymmetric revenue information about the enterprise.
The comparison of the optimal solutions and incentive effects in different information scenarios provides several managerial insights for software upgrade outsourcing:
Managing Information Asymmetry: Asymmetric information about costs and revenues can significantly impact the outcomes of software upgrade outsourcing. Service providers should strive to improve transparency regarding their cost structure, allowing enterprises to make more informed decisions. Similarly, enterprises should share relevant revenue information with service providers to align incentives and achieve better outcomes.
Contract Design: The choice of contract plays a crucial role in managing information asymmetry and aligning incentives. The revenue-sharing contract proves to be more effective in providing optimal incentives for both low-revenue and high-revenue enterprises. Enterprises should consider adopting revenue-sharing contracts to ensure service providers are motivated to deliver the best outcomes.
Risk Mitigation: Software upgrade outsourcing involves inherent risks associated with market fluctuations and potential losses due to outdated software. Enterprises should carefully assess these risks and develop risk mitigation strategies such as timely upgrades and collaborations with service providers. Effective risk management can help enterprises maintain their market position and competitiveness.
Collaborative Decision-Making: While centralized decision-making with full-information yields optimal solutions, achieving such an ideal scenario may be challenging in practice. However, enterprises and service providers can adopt collaborative decision-making approaches, sharing relevant information and working together to maximize joint profits. Regular communication and collaboration can lead to better outcomes and stronger partnerships.
With the rapid advancement of technology and automation, Industry 4.0 represents the integration of digital technologies and industrial processes, leading to increased efficiency, productivity, and competitiveness. Our research on software upgrade outsourcing aligns with the principles of Industry 4.0 by enabling enterprises to leverage external expertise and resources to optimize their software systems, thereby enhancing their ability to adapt and thrive in the digital era. This paper takes the impact of market fluctuations on software adaptability as an entry point and establishes a software upgrade outsourcing model between the enterprise and the service provider.
In the centralized decision with full-information, the service provider functions as the enterprise’s information technology department, collaborating with the enterprise to optimize the expected profit of the system through joint decision-making. This approach yields the most favorable outcomes for software upgrades. There are two cases to consider when determining the optimal software upgrade time. In the first case, the optimal software upgrade time and expected system profits are contingent upon the scale of the enterprise within a specific range. As the enterprise expands, the optimal upgrade time is delayed, and the system’s expected profits increase. Additionally, the optimal software upgrade time is also affected by market fluctuations. When substantial market fluctuations occur, resulting in decreased revenue and increased software upgrade costs, the system’s expected profits decline, prompting enterprises to opt for earlier software upgrades. In the second case, if the enterprise scale exceeds the aforementioned range, the enterprise will have a continuous increase in profits without software upgrades.
In decentralized decision-making with incomplete information, the enterprise and the service provider operate as two independent entities with inconsistent interests and asymmetric information. To avoid the adverse selection problem arising from the ex-ante asymmetric information about the service provider’s cost and the enterprise’s revenue, this paper proposes a software upgrade outsourcing model based on the principal-agent and uses well-designed contracts to screen the true type of the information superior party. Furthermore, we investigate the impact of pay-per-time and revenue-sharing contracts on the software upgrade timing decision and the profits of both parties. Our findings reveal that, in cases where the service provider has private cost information, the pay-per-time and revenue-sharing contracts are equivalent, and the optimal software upgrade time exhibits characteristics of “no distortion at the high end and downward distortion at the low end” compared to the optimal solution under centralized decision-making with full-information. In the cases where the enterprise has private revenue information, the optimal software upgrade time under the pay-per-time contract demonstrates characteristics of “no distortion at the high end and downward distortion at the low end,” while the optimal software upgrade time under the revenue-sharing contract can achieve the optimal solution under centralized decision-making with full-information, showing “no distortion at either the high or low end.” At this point, the incentive effect of the revenue-sharing contract is superior to that of the pay-per-time contract.
In summary, our proposed framework empowers all parties involved in software upgrade outsourcing contracts to make informed decisions, resulting in improved return on investment and increased operational efficiency. By considering the impact of information asymmetry and market fluctuations, enterprises can strategically determine the optimal software upgrade time and maximize their expected profits. This research contributes to the growing body of knowledge in the field of software upgrade outsourcing contract design and provides certain insights for practitioners and scholars.
Acknowledgement: Authors are very much thankful to the reviewers and Journal Authorities.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors confirm contribution to the paper as follows: supervision: C. W.; draft manuscript preparation: Z. W. Z. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Liu, C., Zheng, P., Xu, X. (2023). Digitalisation and servitisation of machine tools in the era of Industry 4.0: A review. International Journal of Production Research, 61(12), 4069–4101. [Google Scholar]
2. Hussain, M., Memon, T. D., Hussain, I., Memon, Z. A., Kumar, D. (2022). Fault detection and identification using deep learning algorithms in induction motors. Computer Modeling in Engineering & Sciences, 133(2), 435–470. https://doi.org/10.32604/cmes.2022.020583 [Google Scholar] [PubMed] [CrossRef]
3. Oztemel, E., Gursev, S. (2020). Literature review of Industry 4.0 and related technologies. Journal of Intelligent Manufacturing, 31, 127–182. [Google Scholar]
4. Rafferty, C., Smith, R. (2000). Making a prophet. Computer Modeling in Engineering & Sciences, 1(1), 151–159. https://doi.org/10.3970/cmes.2000.001.151 [Google Scholar] [CrossRef]
5. Furneaux, B., Mannina, S., Rieser, L. (2022). Responding to information system obsolescence: Should we upgrade or replace? Journal of Computer Information Systems, 62(2), 372–383. [Google Scholar]
6. Liu, Y., Xu, X. (2017). Industry 4.0 and cloud manufacturing: A comparative analysis. Journal of Manufacturing Science and Engineering, 139(3), 034701. [Google Scholar]
7. Stock, T., Seliger, G. (2016). Opportunities of sustainable manufacturing in Industry 4.0. Procedia CIRP, 40, 536–541. [Google Scholar]
8. Baron, D. P. (1979). The incentive problem and the design of investment banking contracts. Journal of Banking & Finance, 3(2), 157–175. [Google Scholar]
9. Baron, D. P., Holmström, B. (1980). The investment banking contract for new issues under asymmetric information: Delegation and the incentive problem. The Journal of Finance, 35(5), 1115–1138. [Google Scholar]
10. Sappington, D. E. M. (1991). Incentives in principal-agent relationships. Journal of Economic Perspectives, 5(2), 45–66. [Google Scholar]
11. Prikladnicki, R., Audy, J. L. N. (2012). Managing global software engineering: A comparative analysis of offshore outsourcing and the internal offshoring of software development. Information Systems Management, 29(3), 216–232. [Google Scholar]
12. Rajaeian, M. M., Cater-Steel, A., Lane, M. (2017). A systematic literature review and critical assessment of model-driven decision support for it outsourcing. Decision Support Systems, 102, 42–56. [Google Scholar]
13. Lacity, M. C., Khan, S. A., Willcocks, L. P. (2009). A review of the it outsourcing literature: Insights for practice. The Journal of Strategic Information Systems, 18(3), 130–146. [Google Scholar]
14. Kern, T., Willcocks, L. P., Lacity, M. (2002). Application service provision: Risk assessment and mitigation. MIS Quarterly Executive, 1(2), 113–126. [Google Scholar]
15. Richmond, W. B., Seidmann, A., Whinston, A. B. (1992). Incomplete contracting issues in information systems development outsourcing. Decision Support Systems, 8(5), 459–477. [Google Scholar]
16. Wang, E. T., Barron, T., Seidmann, A. (1997). Contracting structures for custom software development: The impacts of informational rents and uncertainty on internal development and outsourcing. Management Science, 43(12), 1726–1744. [Google Scholar]
17. Casado-Lumbreras, C., Colomo-Palacios, R., Ogwueleka, F. N., Misra, S. (2014). Software development outsourcing: Challenges and opportunities in Nigeria. Journal of Global Information Technology Management, 17(4), 267–282. [Google Scholar]
18. Bandyopadhyay, S., Pathak, P. (2007). Knowledge sharing and cooperation in outsourcing projects–A game theoretic analysis. Decision Support Systems, 43(2), 349–358. [Google Scholar]
19. Kornish, L. J. (2001). Pricing for a durable-goods monopolist under rapid sequential innovation. Management Science, 47(11), 1552–1561. [Google Scholar]
20. Bala, R., Carr, S. (2009). Pricing software upgrades: The role of product improvement and user costs. Production and Operations Management, 18(5), 560–580. [Google Scholar]
21. Whang, S. (1992). Contracting for software development. Management Science, 38(3), 307–324. [Google Scholar]
22. Elitzur, R., Gavious, A., Wensley, A. K. (2012). Information systems outsourcing projects as a double moral hazard problem. Omega, 40(3), 379–389. [Google Scholar]
23. Zhang, Z., Xu, X. (2017). Principal agent model based design and outsourcing of information value. Cluster Computing, 20, 67–79. [Google Scholar]
24. Pavlou, P. A., Liang, H., Xue, Y. (2007). Understanding and mitigating uncertainty in online exchange relationships: A principal-agent perspective. MIS Quarterly, 31(1), 105–136. [Google Scholar]
25. Grossman, S. J., Hart, O. D. (1992). An analysis of the principal-agent problem. In: Foundations of insurance economics, pp. 302–340. Dordrecht: Springer Netherlands. [Google Scholar]
26. Ciliberti, F., de Haan, J., de Groot, G., Pontrandolfo, P. (2011). CSR codes and the principal-agent problem in supply chains: Four case studies. Journal of Cleaner Production, 19(8), 885–894. [Google Scholar]
27. Cai, W., Singham, D. I. (2018). A principal–agent problem with heterogeneous demand distributions for a carbon capture and storage system. European Journal of Operational Research, 264(1), 239–256. [Google Scholar]
28. Yao, T., Jiang, B., Young, S. T., Talluri, S. (2010). Outsourcing timing, contract selection, and negotiation. International Journal of Production Research, 48(2), 305–326. [Google Scholar]
29. Banerjee, A. V., Duflo, E. (2000). Reputation effects and the limits of contracting: A study of the indian software industry. The Quarterly Journal of Economics, 115(3), 989–1017. [Google Scholar]
30. Benaroch, M., Lichtenstein, Y., Fink, L. (2016). Contract design choices and the balance of ex ante and ex post transaction costs in software development outsourcing. MIS Quarterly, 40(1), 57–82. [Google Scholar]
31. Gopal, A., Koka, B. R. (2010). The role of contracts on quality and returns to quality in offshore software development outsourcing. Decision Sciences, 41(3), 491–516. [Google Scholar]
32. Huang, H., Hu, M., Xu, H. (2023). Time-and-materials or revenue-sharing? Implications of monitoring for software outsourcing contract. Information & Management, 60(3), 103776. [Google Scholar]
33. Wang, C., Deng, L., Zhou, W. (2022). “We missed you!”: A joint optimization strategy of appointment window and reminder sending. Computers & Industrial Engineering, 169, 108198. [Google Scholar]
Proof of Proposition 4.1. Firstly, the actual revenue function of the enterprise is deformed:
Secondly, convert
Thirdly, the first and second derivatives of
Since
Since D is a monotonically increasing function of
(1) If
(2) If
When
(1) If
(2) If
(3) If
It can be observed that for the centralized decision-making with full-information, the optimal software upgrade time exists and is positive only when the value of R satisfies
Finally, we can substitute
The optimal expected profits of the system are
Calculate the first derivatives of
The first derivatives of
We can observe the molecule
Proof of Proposition 5.1. Suppose the information rent
The information rent of high-cost type service providers is
In cases where the service provider has private cost information, it is common for the low-cost type service provider to imitate the high-cost type service provider. Consequently, it can be deduced that
Although an effective contract can reduce the information rent
The expressions for information rent,
The enterprise aims to design a contract that meets the incentive constraints and minimizes the information rent paid. Thus, it is essential that the constraint
Substitute
According to Eq. (37), it can be solved
Finally, substitute
The value of
(1) If
(2) If
(3) If
The value of
(1) If
(2) If
(3) If
To determine the range of R further, we can compare
By substituting
Take the first derivative of
As a result, the variable cost coefficient has an inverse proportionality relationship with the optimal software upgrade time, which leads to the deduction that
Comparing
Consider using a pay-per-time contract when there is asymmetry in the service provider’s cost information
Proof of Proposition 5.2. Suppose the information rent
The information rent of the high-cost type service provider is
Based on the expressions of information rent
Constraint (55) is tight, meaning that
Similar to the proof of Proposition 5.1, we discuss the three cases of
Proof of Proposition 5.3. Suppose the information rent
The information rent of the high-revenue type enterprise is
According to the expressions of information rent
As mentioned previously, the service provider in a design contract seeks to minimize the payment of information rent in order to maximize its own interests. Hence, constraint (64) is tight, which means that
Then, substituting
Substitute the expression for
Bringing
Similarly, the results of
Proof of Proposition 5.4. Define the information rent
The information rent of the high-revenue type enterprise is
According to the expressions of information rent
To minimize information rent and maximize profits, the service provider aims to design a contract that pays as little information rent as possible. Thus, the constrain (76) is tight. Substituting
Bringing
Bringing
The results for
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools