 Open Access
Open Access
ARTICLE
IECC-SAIN: Innovative ECC-Based Approach for Secure Authentication in IoT Networks
1Mathematics, Computer Science and Applications TEAM, Abdelmalek Essaâdi University, ENSA, Tangier, 90000, Morocco
2 National School of Applied Sciences, Sultan Moulay Slimane University, Beni Mellal, 23000, Morocco
3 Department of Library and Information Science, Fu Jen Catholic University, New Taipei City, 242062, Taiwan
4 Department of Computer Science and Information Engineering, Asia University, Taichung City, 413, Taiwan
* Corresponding Author: Cheng-Chi Lee. Email:
Computer Modeling in Engineering & Sciences 2025, 144(1), 615-641. https://doi.org/10.32604/cmes.2025.067778
Received 12 May 2025; Accepted 26 June 2025; Issue published 31 July 2025
Abstract
Due to their resource constraints, Internet of Things (IoT) devices require authentication mechanisms that are both secure and efficient. Elliptic curve cryptography (ECC) meets these needs by providing strong security with shorter key lengths, which significantly reduces the computational overhead required for authentication algorithms. This paper introduces a novel ECC-based IoT authentication system utilizing our previously proposed efficient mapping and reverse mapping operations on elliptic curves over prime fields. By reducing reliance on costly point multiplication, the proposed algorithm significantly improves execution time, storage requirements, and communication cost across varying security levels. The proposed authentication protocol demonstrates superior performance when benchmarked against relevant ECC-based schemes, achieving reductions of up to 35.83% in communication overhead, 62.51% in device-side storage consumption, and 71.96% in computational cost. The security robustness of the scheme is substantiated through formal analysis using the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool and Burrows-Abadir-Needham (BAN) logic, complemented by a comprehensive informal analysis that confirms its resilience against various attack models, including impersonation, replay, and man-in-the-middle attacks. Empirical evaluation under simulated conditions demonstrates notable gains in efficiency and security. While these results indicate the protocol’s strong potential for scalable IoT deployments, further validation on real-world embedded platforms is required to confirm its applicability and robustness at scale.Keywords
The exponential growth in Information and Communication Technology (ICT) has revolutionized the way we interact with and utilize data, facilitating seamless connectivity and empowering myriad applications across various sectors [1]. Central to this evolution is the Internet of Things (IoT), a paradigm that interconnects countless devices, enabling efficient automation, enhanced productivity, and enriched service delivery in both consumer and industrial contexts [2]. From smart homes that adjust environments based on occupant behavior to industrial sensors that optimize manufacturing processes in real-time, the IoT not only has streamlined operations but also has elevated standards of living and service provision [3].
However, this rapid digitization has been paralleled by a surge in cybersecurity threats, amplifying concerns about data integrity, privacy breaches, and system vulnerabilities. Cryptography emerges as a cornerstone in mitigating these risks, offering robust mechanisms to secure sensitive information and communications. The IoT Threat Report 2023 by Securelist, backed by Kaspersky, underscores the importance of effective authentication mechanisms in the IoT space, revealing a 30% surge in attacks and over 1.5 billion incidents in the first half of 2023 [4]. This highlights the critical need for robust security measures to protect data exchanges across potentially insecure networks.
For instance, IoT authentication ensures that only authorized devices can communicate and access resources within a network. This authentication process hinges significantly on the efficiency and security of cryptographic protocols. Elliptic curve cryptography has emerged as a pivotal solution, offering superior performance advantages with shorter key lengths compared to traditional cryptographic methods. ECC’s ability to provide equivalent security with smaller key sizes reduces computational overhead, making it particularly well-suited for resource-constrained IoT devices [5].
Against this backdrop, this paper presents a novel IoT authentication approach based on our previously proposed mapping and reverse operations [6] on elliptic curves over prime fields. We select NIST curves (192, 256, 384, 521) for their efficient arithmetic and low resource requirements [7]. It is worth noting that we also go beyond the 521-bit security level to demonstrate the scalability of our approach. Unlike existing benchmarks that rely heavily on point multiplication and suffer from significant performance degradation as security increases, our method maintains efficiency even at higher security levels. Our method focuses on optimizing authentication speed across varying key sizes, surpassing conventional point multiplication techniques that often bottleneck ECC-based systems [8]. Furthermore, we conduct a comprehensive security evaluation using AVISPA and BAN logic, supported by informal proofs against potential attacks. Through empirical assessments covering storage, communication, and computational costs, we demonstrate the efficiency and effectiveness of our proposed system in real-world scenarios.
The Internet of Things (IoT) heavily depends on wireless networks for data collection by authorized users. Typically, communication happens between a central platform and various terminal nodes, where the platform sends commands to the nodes to gather and transmit data back. Mutual authentication between the platform and terminal nodes is crucial to ensure network security. Without this, unauthorized individuals could exploit the network for data theft or malicious activities. Moreover, terminal nodes need to authenticate themselves to other nodes to prevent unauthorized access, which could disrupt the network and deceive both the platform and legitimate nodes [9]. Therefore, mutual identity authentication is vital for maintaining the security of IoT systems. In scenarios where processing power and memory are constrained, ECC as a form of public key cryptography, is particularly suitable. ECC offers an efficient solution for secure communication in resource-limited environments, making it a viable option for enhancing IoT security [10].
The various ECC-based authentication schemes proposed in the literature utilize different methods, such as time-stamp techniques and certificate-based mutual authentication. However, certificate-based methods can be costly, as they require additional computational resources for servers and users to authenticate each other’s identities. In contrast, the authors in [11] proposed an ECC-based authentication and key agreement scheme specifically for IoT environments. Their protocol facilitates secure communication between embedded devices and cloud servers by providing mutual authentication, allowing both the user and server to negotiate encryption keys collaboratively. They assert that their scheme meets all necessary security requirements and offers robust resistance to various well-known IoT attacks.
Despite the author’s claim, studies in [12–15] identified significant security flaws and structural issues in their protocol. These issues include the failure of mutual authentication, ambiguity in session key establishment, vulnerability to offline password guessing, and susceptibility to insider and traceability attacks. In response, each of these researchers proposed enhanced protocols, asserting that their improvements effectively address the identified vulnerabilities and fulfill the necessary security requirements. Further advancements include the work in [16], which proposed an anonymous authentication scheme that integrates a password validator to defend against known temporary information and DoS attacks. This scheme showcased ECC’s potential in fortifying IoT devices against sophisticated attacks while maintaining a lightweight footprint. Another significant contribution is from [17] proposed a novel lightweight anonymous authentication protocol (LAAP) to meet security and efficiency requirements. This protocol uses ECC and dynamic pseudonyms to prevent traceable attacks caused by fixed identity identification and employs symmetric encryption to optimize the server’s search for anonymous device information, reducing the time complexity from O(n) to O(1). Very recently, the authors in [18,19] proposed a mutual authentication scheme based on ECC and the U-Quark light hash function, which is known for its collision resistance. This approach not only retains the essential security features of ECC but also enhances performance, making it well-suited for the IoT environment. Despite continuous efforts, designing a resource-efficient and secure ECC-based authentication protocol for IoT edge devices remains a significant challenge. Similarly, in 2024, the authors in [6] proposed an innovative hash-based technique that embeds messages into an elliptic curve (EC) points before encryption, using a random parameter and a shared secret point from the generated through elliptic curve Diffie–Hellman protocol. The method’s security was evaluated against various attack models, and its complexity and sensitivity were analyzed. A tag ensures message integrity, and the scheme meets criteria such as the strict avalanche criterion and linear complexity. Comprehensive analysis confirmed its effectiveness in maintaining data security and integrity. Another recent study, the authors in [20] proposed a two-factor authentication protocol for IoT-enabled Wireless Sensor Networks (WSNs), integrating ECC with a fuzzy verifier to enhance both security and usability in resource-constrained environments. Instead of relying on traditional deterministic password hashes, their scheme employs a fuzzy verifier approach, introducing randomness that enhances resistance to common attacks while preserving authentication reliability. Formal security validation using the Real-or-Random model and comparative analysis confirmed the scheme’s efficiency, achieving a computation cost of 8.9569 ms, outperforming existing protocols in both performance and protection metrics. In a related contribution, the authors in [21] designed an authentication protocol optimized for military Internet of Drones (IoD) scenarios, addressing the need for secure, real-time communication under resource constraints. Their approach leverages Elliptic Curve Cryptography and independently managed session keys across various communication links to contain potential breaches and reduce computational load. To further strengthen security, the protocol integrates trust anchors, group key exchanges, and position verification techniques, ensuring resistance to attacks such as replay and denial-of-service. In 2025, the authors in [22] introduced a lightweight authentication protocol specifically designed for the Internet of Medical Things (IoMT), addressing both security and user privacy in resource-constrained medical environments. Their approach ensures secure communication between body-connected devices while preserving patient confidentiality, and it is formally verified using the AVISPA tool. By leveraging smaller key sizes and efficient cryptographic techniques, the proposed protocol achieves 5 to 6 times greater computational efficiency compared to conventional methods such as ElGamal and Rivest–Shamir–Adleman (RSA), while resisting common threats found in existing schemes. Building on the work proposed in [6], we introduce a novel ECC-based mutual authentication protocol for IoT environments. Our protocol is designed to provide lightweight communication with reduced computational and storage costs while maintaining strong security properties. The security of our protocol has been formally verified using AVISPA and BAN logic, chosen based on a survey of 40 authentication protocols, which revealed that
3 Elliptic Curves Cryptography and Secure Embedding Approach
This section provides essential background on ECC required to understand the proposed scheme. It covers key concepts such as point multiplication, solving modular quadratic equations, and data embedding into elliptic curve points.
3.1 Introduction to Elliptic Curve Cryptography over Prime Fields
Elliptic Curve Cryptography uses the algebraic structure of elliptic curves over finite fields for secure communication. An elliptic curve over a prime field
where
3.1.1 Points on Elliptic Curves
Points on the elliptic curve
1. Point Addition: Given two points P and Q, their sum R = P + Q is another point on the curve. The point −P denotes the symmetric of P and verifies
2. Point Doubling: Doubling a point P results in another point
3. Point Multiplication (PM): Multiplying a point P by an integer
A generator point G is a specific point on the elliptic curve used to generate all or almost all other points in the elliptic curve group through repeated addition. Table 1 describes various elliptic curve parameters used in alongside this paper.

Comprehensive details on ECC can be found in [24].
3.2 Modular Quadratic Equation
The proposed mapping and reverse mapping operations require solving a modular quadratic equation of the form
with discriminant
If
3.3 Elliptic Curve Embedding Approach
In this section, we explore a secure method for embedding information into elliptic curves, originally proposed in [6], and it is applied in a novel way to support efficient and secure authentication. The approach focuses on integrating data within the curve’s structure while ensuring robust security measures. Upon establishing an agreement between the server and the device on the elliptic curve domain parameters, as detailed in the forthcoming setup phase Section 4.1, we define
which converts a given element
Once a solution
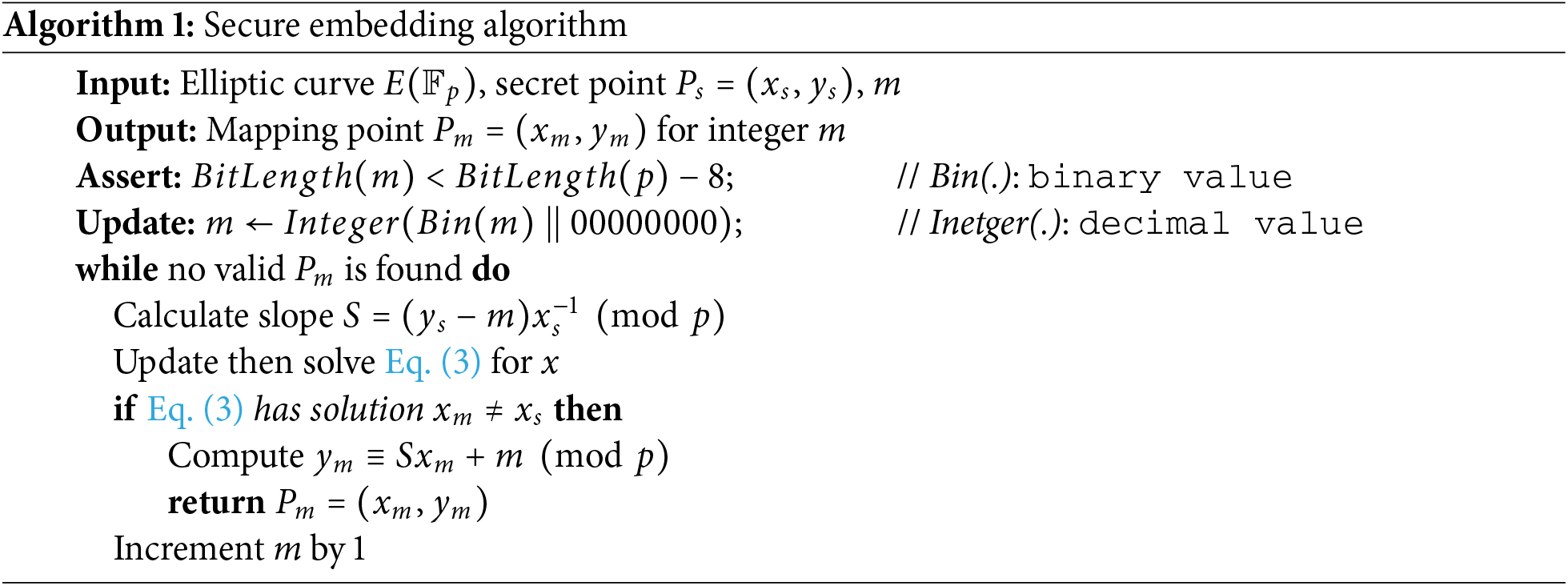
Now we explore how to reverse the mapping process. This method complements the secure embedding approach detailed previously, ensuring that the original integer
Given the shared elliptic curve
The reverse mapping process follows these steps:
1. Slope Calculation: The slope S of the line passing through the points
2. Computing
3. Removing the Last 8 Bits: Convert
The algorithm for this reverse mapping approach is detailed in Algorithm 2.
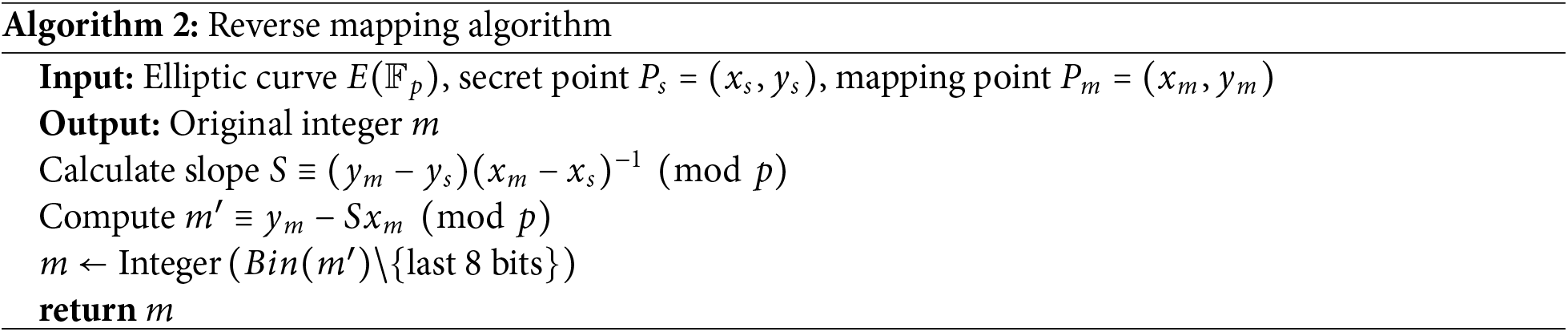
Our protocol consists of four main phases: the setup phase, the registration phase, the login phase, and the authentication phase. Implemented using the Charm framework, it employs elliptic curve cryptography for secure key exchange and authentication. Data transmission from the embedded devices D and the server is assumed to occur over a secure channel during the registration phase. In the following, we detail each phase and the corresponding steps involved in the protocol execution as depicted in Fig. 1. The parameters used in our protocol and their corresponding definitions are listed in Table 2.

Figure 1: Proposed ECC-based authentication scheme for IoT.

In the setup phase, both the server and the device agree on an elliptic curve to use, such as the standardized NIST curve prime192v1. In the proposed method, we specifically use elliptic curves defined over prime fields with characteristics greater than or equal to 5. The domain parameters for the chosen elliptic curve are detailed in Table 1.
In the Registration Phase, the device
The server then stores the values
4.3 Login and Authentication Phase
The authentication phase involves mutual verification between the device and the server through a sequence of cryptographic operations and exchanges of various values.
During the Login and Authentication Phases, the device
The device then sends
Additionally, the server updates its counter (
The server then sends
If
and sends
where
If
and derives the session key:
By adhering to these carefully structured steps, our ECC-based authentication protocol ensures robust mutual authentication between IoT devices and the central server, capitalizing on the computational efficiency and security strengths of elliptic curve cryptography.
5 Security Analysis and Performance Analysis of the Elliptic Curve Embedding Approach
In this section, we delve into the rigorous evaluation of the security and performance aspects of our proposed Elliptic Curve Embedding Approach (ECEA) for IoT authentication. Our approach builds upon the foundation laid by our previously proposed ElGamal ECC-based encryption [6], leveraging its inherent security properties and extending them to authenticate IoT devices securely.
Lemma 1. Let
Proof: Let
On the other hand, suppose there exists a point
Theorem 1. Let
Proof: Consider G to be the generator point of
where
As discussed in [6], the embedding approach successfully encodes a message (integer
To demonstrate the authentication system’s sensitivity to small changes in its inputs, ensuring security through significant variations in authentication parameters, we set an initial ID as a random number, then created 10 different

Figure 2: Normalized Data Pathways in Device-Server Communication during Authentication Protocol

Figure 3: Comparative Analysis of Execution Times for Cryptographic Operations: Mapping, Reverse, Multiplication, Addition
The computational overhead, assessed across the NIST elliptic curve with various key sizes compared to secp192r1 as illustrated in Table 3, which highlights how the execution time growth ratio for reverse and mapping operations remains manageable yet notably faster compared to the substantial growth observed with point multiplication. This disparity leads to slower authentication processes when relying on point multiplication. Conversely, our proposed mapping operations maintain a more linear growth pattern, ensuring efficiency even as key sizes increase.

Additionally, we compared the computational cost of point multiplication and our embedding algorithm on the NIST curve secp192r1. Point multiplication using the double-and-add algorithm requires up to 23,857 field operations with affine coordinates and 2500 with mixed coordinates (Jacobian and affine), reduced to 718 using the Fixed-Base Comb method, which trades off the storage of approximately 30 points [24]. In contrast, our embedding approach, which involves solving the quadratic Eq. (3) using the square root of the discriminant
Note that the previously established comparison is motivated by the fact that all ECC-based authentication schemes rely on point multiplication as a core operation. While these schemes successfully enhance performance and security compared to those leveraging other cryptographic techniques like RSA, the point multiplication operation remains the most computationally intensive aspect. Our proposed embedding scheme is designed to offer improved performance while maintaining high security.
The findings show that our method is particularly suitable for reducing computational complexity in elliptic curve cryptographic applications, such as authentication, in resource-constrained IoT environments. By maintaining a delicate balance between security and performance while addressing the scalability challenges posed by larger key sizes, our method is well-suited for deployment in these environments.
6 Threat Model and Assumptions
This section outlines the security assumptions, attacker capabilities, and environmental constraints considered in the design of the proposed authentication protocol for IoT environments. We target typical IoT scenarios, where devices operate in open and potentially untrusted settings, often with limited computational, memory, and energy resources.
We assume that an adversary has full control over the communication channel between the device and the server. This includes the ability to intercept, eavesdrop, replay, inject, or alter transmitted messages. The adversary may act passively (observing protocol flows) or actively (modifying or forging messages). However, the adversary cannot break standard cryptographic assumptions, such as the collision resistance of SHA-256 or the intractability of the Elliptic Curve Discrete Logarithm Problem (ECDLP) over ECC-256. Moreover, it is assumed that the adversary cannot access the secure internal memory of honest IoT devices.
A stronger adversarial model is also considered, in which long-term secrets from the server side may become exposed. In such a setting, the focus shifts to assessing whether past session keys remain confidential. These assumptions are particularly relevant for environments that require session-level security guarantees even under partial compromise.
The IoT devices are assumed to be constrained in terms of processing power and storage, and the initial registration phase is performed in a trusted and secure environment. Communications take place over insecure and asynchronous wireless networks. To maintain freshness and prevent replay without requiring strict time synchronization, we assume the use of a monotonically increasing counter (cpt) shared between the device and server. The server is trusted and possesses sufficient computational capacity to manage authentication requests from numerous devices simultaneously. This threat model establishes the foundation upon which the protocol’s security properties—such as resistance to replay, impersonation, and man-in-the-middle attacks—will be rigorously evaluated in the subsequent formal and informal analysis sections.
7 Security Analysis of the Proposed Authentication
In this section, we aim to rigorously demonstrate the resilience of our proposed secure ECC-based authentication scheme against a range of prevalent attacks targeting the Internet of Things (IoT). To accomplish this, we will employ both informal and formal security analysis methodologies. Specifically, we will leverage the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool and Burrows–Abadi–Needham (BAN) logic to thoroughly validate and verify our scheme’s security properties. Through these methods, we will comprehensively assess the scheme’s ability to withstand potential security threats.
7.1 Informal Security Analysis
This subsection provides an informal security analysis of our authentication scheme, demonstrating its resilience against several common threats: replay attacks, impersonation attacks, and man-in-the-middle attacks. Additionally, we discuss how the scheme ensures Perfect Forward Secrecy. We will show how our scheme effectively mitigates these threats, ensuring robust and secure authentication.
Threat: Tracking a specific IoT device over multiple sessions.
Mitigation: In the logging and authentication phases, it is essential for the server to identify which device is attempting to log in, enabling the authentication process based on the corresponding data of that identity. Some existing schemes [16] transmit the hash value of the device ID (
Effectiveness: Ensures unlinkability and anonymized authentication.
Threat: Recovering past session keys after long-term key compromise.
Mitigation: The proposed authentication protocol ensures resilience against attacks targeting perfect forward secrecy (PFS) by protecting past session keys even if long-term keys are compromised. The protocol uses a unique random value
Effectiveness: Achieves strong session isolation and confidentiality over time.
Threat: Reusing previously captured messages to gain unauthorized access.
Mitigation: Our authentication scheme is secured against replay attacks through the use of a counter (
Effectiveness: Replay attempts are rejected due to counter mismatch.
Threat: An attacker impersonates a legitimate device or server.
Mitigation: In our scheme, an attacker cannot impersonate either the device or the server due to the reliance on specific cryptographic values and session-specific information. To impersonate the device, the attacker would need the legitimate user’s
Effectiveness: Prevents both client-side and server-side impersonation through cryptographic binding of session-specific secrets.
7.1.5 Man-in-the-Middle Attack
Threat: Intercepting, modifying, or forging messages between device and server.
Mitigation: A Man-in-the-Middle (MitM) attack occurs when an attacker secretly intercepts and possibly alters the communication between two parties to gain unauthorized access or manipulate the data. For MitM attacks, the scheme’s use of random values and counters ensures that each session is unique and secure. During the exchange, the counter
Effectiveness: Ensures message integrity and authenticity under active adversary conditions.
As shown in Table 4, the comparative analysis of the proposed scheme with other relevant schemes demonstrates comprehensive security coverage, outperforming other schemes in several critical areas. This comprehensive security performance underlines the effectiveness and robustness of theproposed scheme in various attack scenarios.
This subsection demonstrates the formal security analysis of the proposed methods utilizing the AVISPA tool and BAN Logic.
The Automated Validation of Internet Security Protocols and Applications tool is a comprehensive framework designed to rigorously assess network protocol security against well-known attack vectors. In our evaluation, we explicitly analyzed the resilience of the proposed protocol against Man-in-the-Middle (MITM) attacks, replay attacks, interception, and message modification attacks.
Utilizing the High-Level Protocol Specification Language (HLPSL), AVISPA allows for precise specification of protocol participants’ actions and interactions. HLPSL, a role-based language, enables detailed specification of the behavior and roles of protocol entities. This high-level description is translated into an Intermediate Format (IF), which serves as the input for AVISPA’s backend analyzers. This translation is essential for systematically analyzing the protocol’s security properties.
The backend of the AVISPA tool comprises four main components, each using different methodologies to analyze the protocol. These are the SAT-based Model-Checker (SATMC), which uses satisfiability-solving techniques; the Tree-Automata-based Protocol Analyzer (TA4SP), which employs tree automata; the On-the-Fly Model-Checker (OFMC), which performs dynamic analysis; and the Constraint Logic-based Attack Searcher (CL-AtSe), which uses constraint-solving techniques to identify potential attacks. For protocols involving XOR operations, such as ours, OFMC and CL-AtSe are particularly suitable, as SATMC and TA4SP do not support XOR operations.
The AVISPA tool produces an Output Format (OF) that provides a detailed security analysis of the protocol. A result indicating that the protocol is SAFE confirms its robustness against specified attacks, such as MITM and replay attacks, thereby validating the protocol’s security properties.
In our proposed protocol, we utilized HLPSL to define the protocol’s roles, environment, and security objectives as depicted in Fig. 4. This includes specifying the actions and interactions of each participant, setting up instances of each role, constructing the entire protocol session, and establishing goals such as confidentiality to ensure sensitive information remains protected, and authentication to verify the legitimacy of the data exchanged between entities.

Figure 4: HLPSL Code Specification for our proposed authentication protocol analyzed by the AVISPA tool.
The security goals are integral to the protocol’s design and are articulated using HLPSL constructs such as secrecy and authentication. These constructs ensure that secret values remain undisclosed and unauthorized access to sensitive information is prevented, while also validating the legitimacy of the entities involved.
As illustrated in Fig. 5, the OFMC and CL-AtSe backends verified that the protocol is SAFE under the specified analysis conditions. The OFMC backend’s statistics demonstrate its efficiency by detailing the parse time, search time, visited nodes, and search depth. Meanwhile, the CL-AtSe backend provides metrics on the number of analyzed and reachable states. These results indicate that our protocol has undergone a comprehensive analysis and has been deemed secure against the potential threats evaluated by the AVISPA tool.
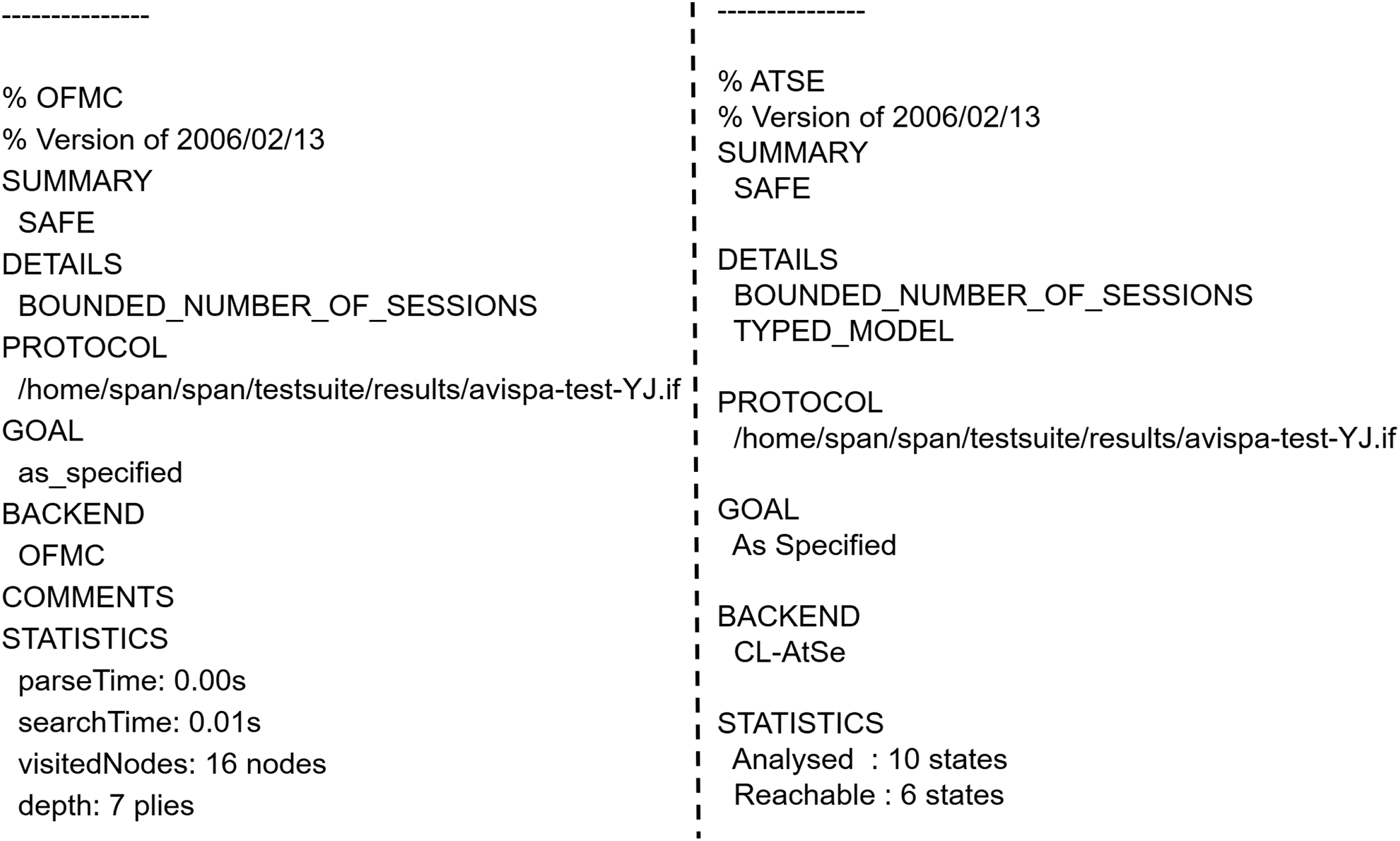
Figure 5: Analysis result of OFMC and CL AtSc security checkers on our protocol.
To complement the automated validation, we employed BAN logic to formally reason about the mutual authentication, session key establishment, and message integrity properties of our protocol.
We present the constructs and primary postulates of BAN logic in Tables 5 and 6, respectively.

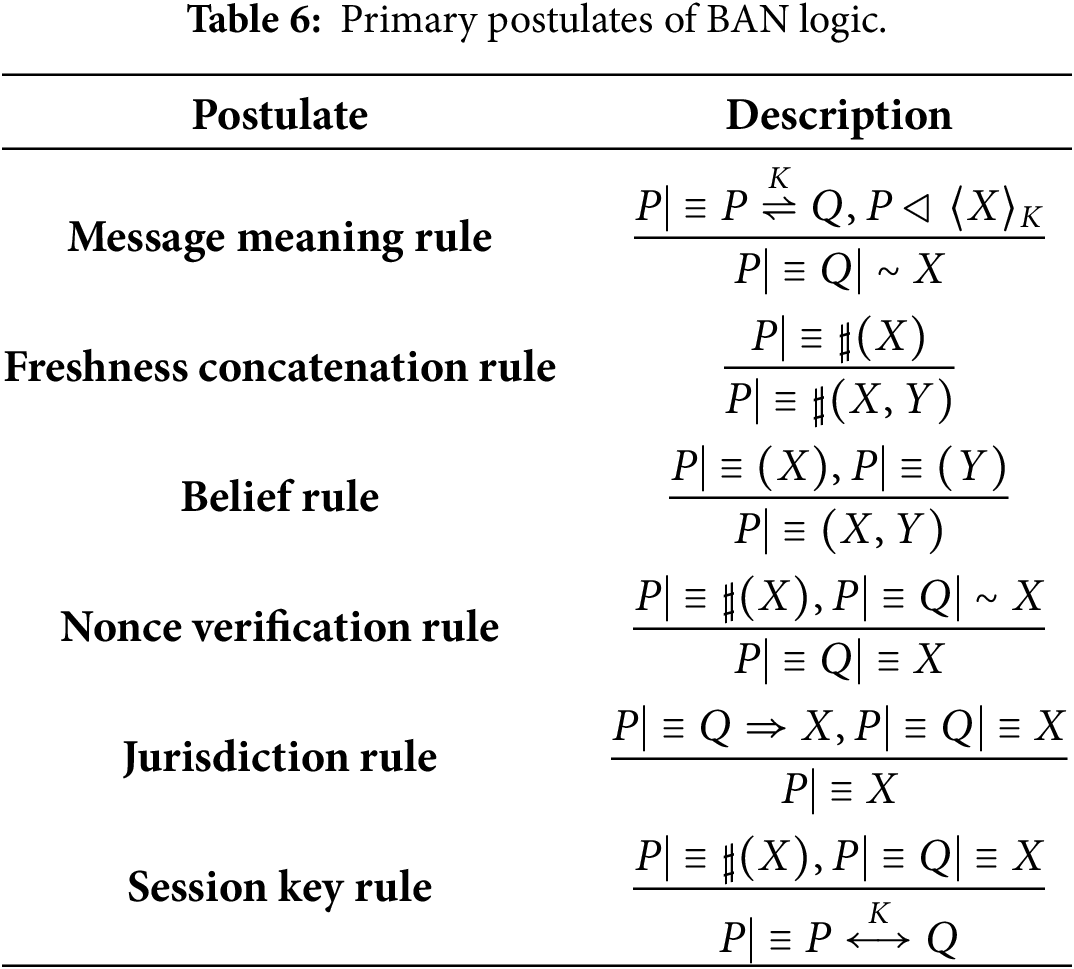
The process to prove the authentication protocol using BAN logic is as follows:
1. Define the goals, which need to be achieved by the authentication system.
2. The proposed authentication protocol should be idealized in the formal language of BAN logic.
3. Set the initial state of the protocol by mentioning the various assumptions.
4. Apply BAN logic constructs and postulates to prove or achieve the goals set in the first step.
The proof of the proposed authentication protocol using BAN logic is described as follows:
Goals:
—The idealized form of the authentication phase of the proposed protocol is given by:
—The following are the assumptions made to achieve the defined goals:
—The above-mentioned postulates and assumptions are applied to the idealized form: M1 and M2 to achieve the defined goals as follows.
M1:
According to the assumption A1 and the freshness concatenation rule:
Using the assumptions A4, A6, and the message meaning rule:
Using the assumptions A5 and A9 and the jurisdiction rule:
M2:
Using the assumptions A2, A3, and the nonce verification rule:
According to the session key rule:
From the goal definition:
This completes the proof. The BAN logic analysis confirmed that both communication parties can trust the established session key and are mutually authenticated, reinforcing the results obtained through AVISPA. This dual-layer verification provides strong assurance of the protocol’s ability to withstand critical security threats in IoT environments.
The proposed ECC-based authentication protocol was rigorously evaluated to assess its computational efficiency, communication overhead, storage requirements, and security robustness. To ensure consistency and rigor in the evaluation, the proposed protocol employs a 256-bit elliptic curve (ECC-256) alongside SHA-256 for cryptographic operations. The selection of SHA-256 is based on recommendations from NIST, which highlight its suitability for IoT environments due to its optimal balance between computational efficiency and cryptographic strength, particularly in resource-constrained devices. Although NIST has not deprecated SHA-256 in favor of SHA-3—both being considered secure—SHA-256 remains the most practical and efficient option for the majority of current IoT deployments [29]. Similarly, all relevant recent protocols included in the comparative analysis were standardized to use ECC-256 and SHA-256. When evaluating computational complexity, lightweight operations such as exclusive OR (XOR) and string concatenation were excluded.
The results presented here were obtained following the implementation of the protocols on a system with the following specifications as shown in Table 7: Ubuntu 16 and Python 2.6 in a virtual machine (VM) adapted to the Charm framework. Web sockets were employed for communication between the embedded device D and the server S. All experiments were conducted on a MacBook Air with a 1.6 GHz Intel i5 processor, 8 GB of RAM, running macOS 12.2. Notably, all experiments were performed on a single core of the processor.
In our analysis of the computation cost, we define the execution times of various cryptographic operations as follows:
•
•
•
•
•
•
Our experimental findings indicate the following execution times for

Based on the comparison Table 8, our proposed protocol demonstrates a significant improvement in computational efficiency relative to other recent protocols. With a total computation overhead of 92.22 ms, our protocol is markedly more efficient than those listed in the comparison. Specifically, it achieves a reduction of approximately 61.1% compared to the average total computation cost of the other protocols.
The registration phase of our protocol incurs a cost of 47.53 ms, which is more efficient compared to some other protocols. Notably, the efficiency gains are particularly evident in the login and authentication phase, where our protocol’s computation overhead is only 44.68 ms, significantly lower than that of other protocols. For example, the protocol by [16] has a computation cost of 316.3012 ms, and Ref. [15] shows 256.0705 ms for the same phase.
This reduction is primarily attributable to our protocol’s design, which incorporates only a single point multiplication
This efficiency is further illustrated in Fig. 6, which shows that our protocol achieves the lowest computation overhead values in both the registration and authentication phases. This reduced overhead is crucial for time-sensitive applications, as it enables faster and more responsive authentication processes. In comparison, other schemes exhibit higher computation overheads, which can result in delays or increased resource consumption. Thus, the streamlined design of our protocol not only improves computational efficiency but also makes it a more optimal choice compared to existing solutions.
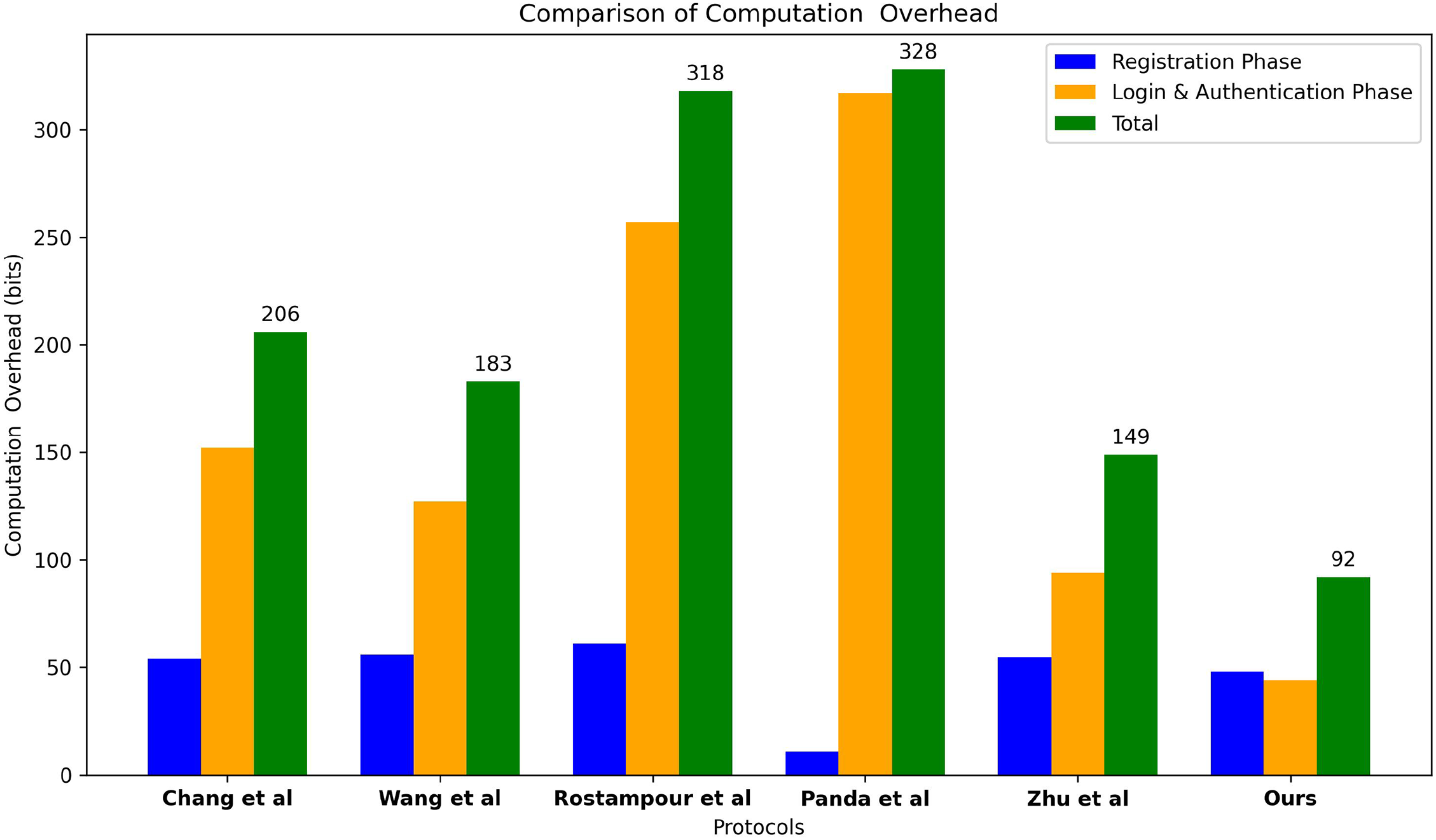
Figure 6: Performance comparison of different schemes in terms of computational overheads: Chang et al. [12], Wang et al. [13], Rostampour et al. [15], Panda and Chattopadhyay [16], and Zhu et al. [17].
The communication overhead was assessed by measuring the size of the authentication messages exchanged between IoT devices and the server during the registration, login, and authentication phases. In our proposed authentication protocol, the data transmitted between the device and the server consists of three types of messages:
1. Registration Phase:The message
•
2. Login and Authentication Phase: Two messages are transmitted:
• —
• —
The total communication overhead for both phases is the sum of the sizes of all transmitted messages:
Based on the comparison Table 9, our proposed protocol exhibits superior performance in terms of communication overhead compared to other recent protocols. Specifically, our protocol achieves the lowest registration phase communication overhead, totaling 672 bits. This is notably more efficient than the protocol by [13], which has a registration phase overhead of 768 bits.
In the login and authentication phase, our protocol’s communication overhead is 1792 bits, which aligns with the protocol size presented by [17]. However, our protocol achieves a lower total communication overhead of 2464 bits, compared to 3072 bits in theirs. This represents a reduction of approximately 19.8% in total communication cost when compared to the protocol by [17].
Overall, the reduced registration phase overhead and competitive login and authentication phase size contribute to the lower total communication cost of our protocol. This reduction in message size is critical for IoT environments, where bandwidth and energy efficiency are of utmost importance as illustrated in Fig.7, making our protocol a more efficient choice relative to existing solutions.
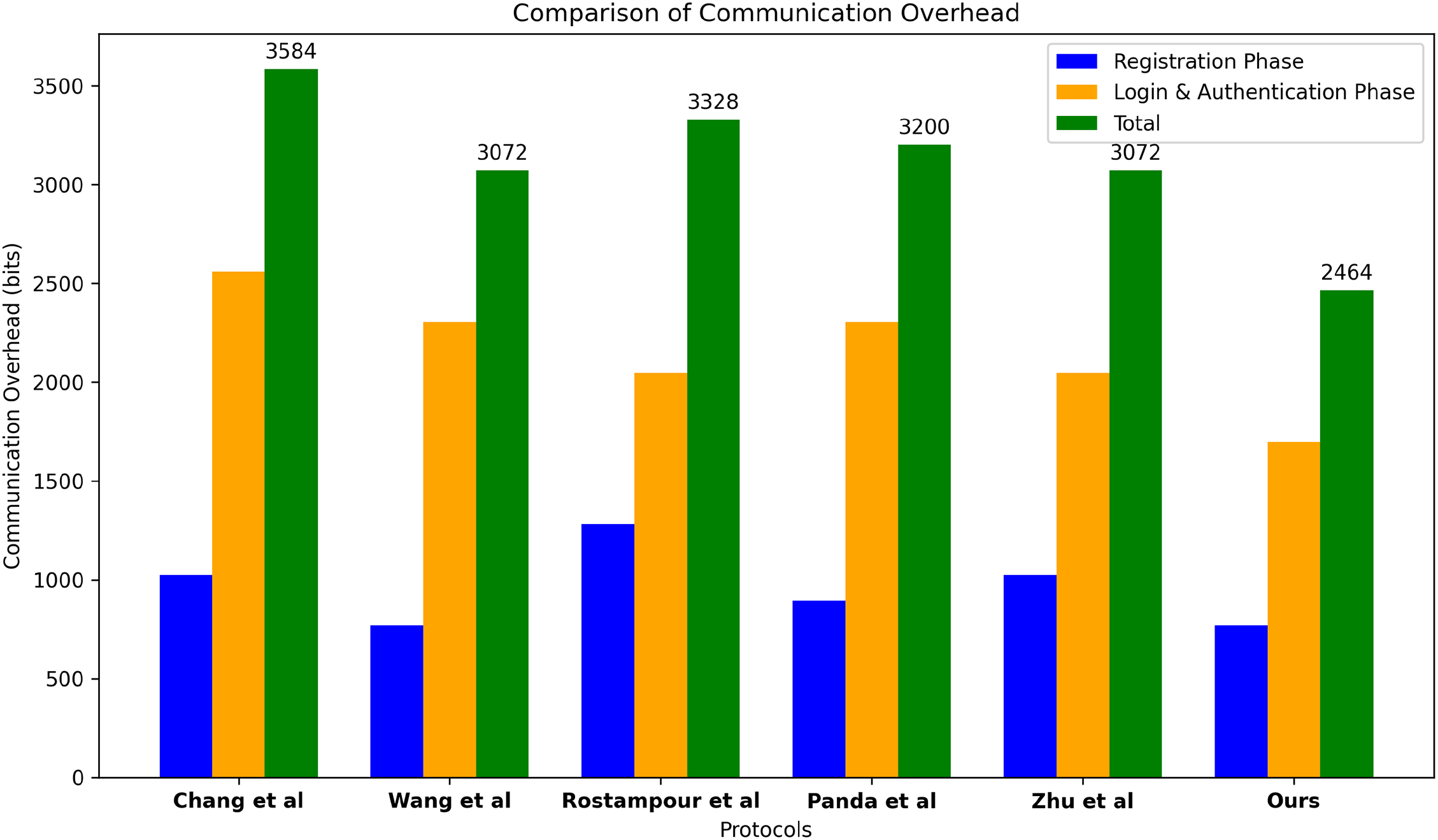
Figure 7: performance of different schemes in terms of communication overheads: Chang et al. [12], Wang et al. [13], Rostampour et al. [15], Panda and Chattopadhyay [16], and Zhu et al. [17].
For our proposed protocol, the storage cost is analyzed in two phases: the registration phase and the login and authentication phase.
1. Registration Phase:
- Device: During the registration phase, the device stores the identity ID (160 bits) and the value of
- Server: Concurrently, the server stores the values of
2. Login and Authentication Phase:
- Device: In this phase, the device temporarily stores the values of
- Server: The server temporarily stores the values
The overall total storage cost for both the device and the server across all phases is 5056 bits.
However, in the relevant literature [13,16,17], the focus is typically on the storage cost of the device rather than the server, due to the limited memory capacity of IoT devices compared to the vast storage resources of cloud servers. Therefore, to ensure a fair and accurate comparison with other protocols, we consider only the device’s storage cost in our analysis. The detailed results, highlighting the device’s storage requirements, are presented in Table 10.

As shown in Fig. 8, our proposed protocol offers notable improvements in device storage overhead compared to other recent protocols, both during the registration and login/authentication phases. The reduction in storage requirements is critical for IoT devices, where memory capacity is typically limited. This efficiency allows our protocol to effectively minimize storage usage while maintaining robust security and functionality
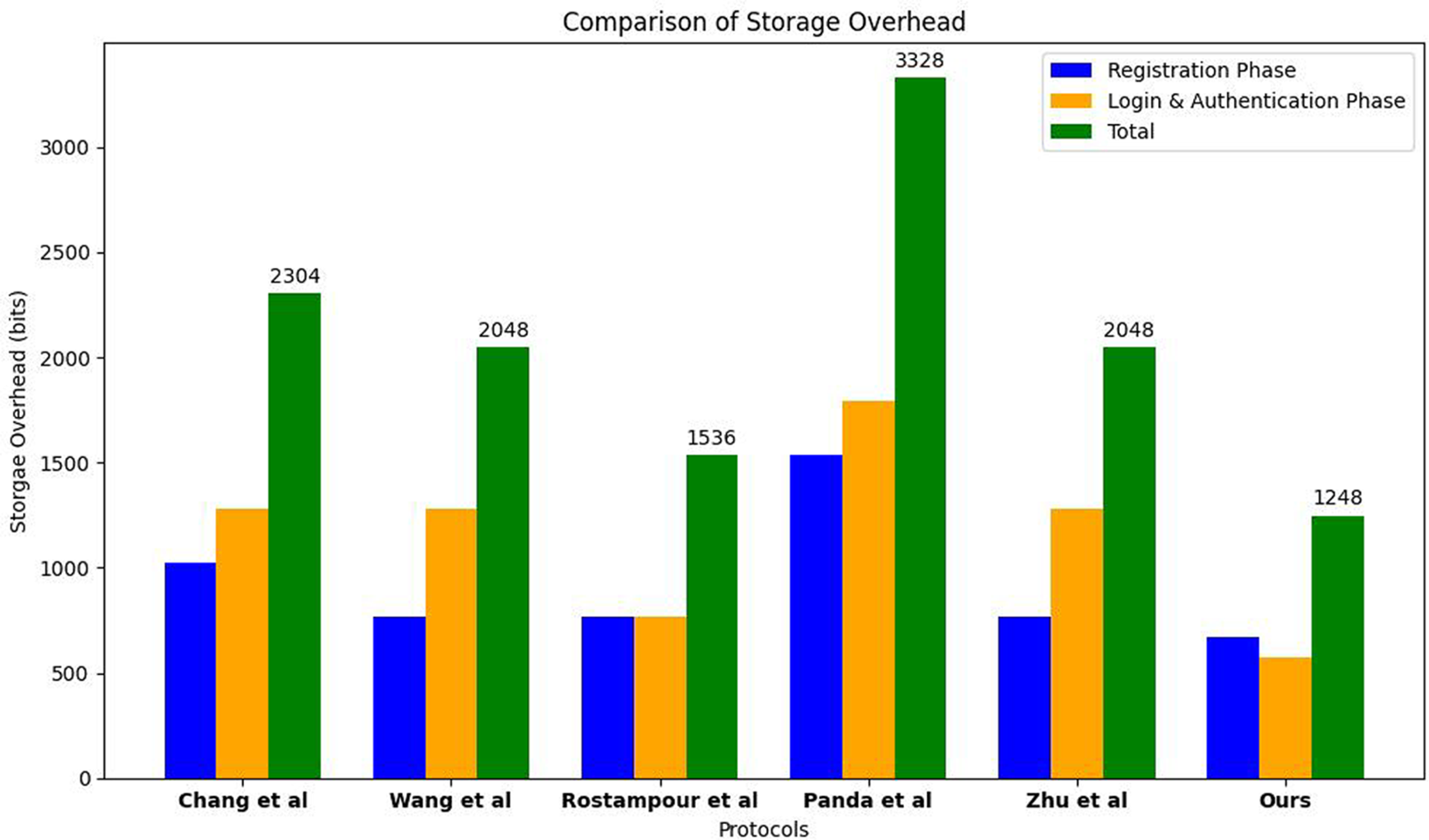
Figure 8: performance of different schemes in terms of device storage overheads: Chang et al. [12], Wang et al. [13], Rostampour et al. [15], Panda and Chattopadhyay [16], and Zhu et al. [17].
The evaluation of our proposed authentication protocol highlights its significant advantages in both security and lightweight performance compared to existing protocols. By effectively reducing communication, computation, and storage overheads, our scheme not only ensures robust protection against a variety of attacks but also maintains user anonymity and service availability. These attributes make it particularly well-suited for secure authentication in practical deployment scenarios.
Furthermore, the protocol’s efficiency in resource-constrained environments, achieved through substantial reductions in overheads, underscores its practicality. This balance of security and performance positions our protocol as an optimal solution for applications where both resource efficiency and strong security measures are critical, making it a superior choice for modern authentication needs.
This article introduces a novel ECC-based authentication protocol for IoT designed to enhance security while optimizing performance. Through the application of ECC, our protocol achieves superior security with reduced computational, communication, and storage overheads. A thorough security analysis, conducted both informally and formally using AVISPA and BAN logic, confirms the protocol’s resilience against various attacks.
Our performance evaluation underscores the protocol’s efficiency, demonstrating significantly lower computational, communication, and storage costs compared to existing relevant authentication protocols. These findings highlight that our protocol is not only secure but also highly practical for real-world applications, particularly in IoT environments where resource constraints are a significant concern.
Future work will focus on applying our authentication protocol in real-world scenarios to validate its practical effectiveness and reliability. Additionally, we aim to extend our protocol for integration with blockchain technology, leveraging its decentralized nature to further enhance security and trust in various applications. By continually refining and adapting our approach, we aim to advance secure and efficient authentication mechanisms in an increasingly interconnected digital landscape.
Acknowledgement: Not applicable.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors confirm contribution to the paper as follows: Conceptualization, Younes Lahraoui and Jihane Jebrane; methodology, Younes Lahraoui and Jihane Jebrane; software, Younes Lahraoui and Jihane Jebrane; validation, Younes Lahraoui, Jihane Jebrane, Youssef Amal, Saiida Lazaar and Cheng-Chi Lee; formal analysis, Younes Lahraoui and Jihane Jebrane; investigation, Younes Lahraoui, Jihane Jebrane; writing—original draft preparation, Younes Lahraoui, Jihane Jebrane; writing—review and editing, Younes Lahraoui, Jihane Jebrane, Youssef Amal, Saiida Lazaar and Cheng-Chi Lee; funding acquisition, Cheng-Chi Lee. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Chauhan A, Sharma A, Sikhwal OP. Opportunities created by digital technology and increased data. ECS Trans. 2022;107(1):8071–8076. doi:10.1149/10701.8071ecst. [Google Scholar] [CrossRef]
2. Sharma J, Sangwan A, Singh RP. A review on evolving domains of internet of things: architecture, applications, and technical challenges. Int J Commun Syst. 2023;36(18):e5613. doi:10.1002/dac.5613. [Google Scholar] [CrossRef]
3. Zanella A, Bui N, Castellani A, Vangelista L, Zorzi M. Internet of things for smart cities. IEEE Internet Things J. 2014;1(1):22–32. doi:10.1109/JIOT.2014.2306328. [Google Scholar] [CrossRef]
4. Securelist. IoT threat report 2023. 2023. [cited 2025 Jun 20]. Available from: https://securelist.com/iot-threat-report-2023/110644/. [Accessed June 20, 2025]. [Google Scholar]
5. Zhang L, Tang S, Luo H. Elliptic curve cryptography-based authentication with identity protection for smart grids. PLoS One. 2016;11(3):e0151253. doi:10.1371/journal.pone.0151253. [Google Scholar] [PubMed] [CrossRef]
6. Lahraoui Y, Lazaar S, Amal Y, Nitaj A. Securing data exchange with elliptic curve cryptography: a novel hash-based method for message mapping and integrity assurance. Cryptography. 2024;8(2):23. doi:10.3390/cryptography8020023. [Google Scholar] [CrossRef]
7. Brown M, Hankerson D, López J, Menezes A. Software implementation of the NIST elliptic curves over prime fields. In: Naccache D, editor. Lecture notes in computer science. Topics in cryptology—CT-RSA 2001. Vol. 2020. Berlin/Heidelberg: Springer; 2001. p. 250–65. doi:10.1007/3-540-45353-9_19. [Google Scholar] [CrossRef]
8. Verri Lucca A, Mariano Sborz GA, Leithardt VRQ, Beko M, Albenes Zeferino C, Parreira WD. A review of techniques for implementing elliptic curve point multiplication on hardware. J Sensor Actuator Networks. 2021;10(1):3. doi:10.3390/jsan10010003. [Google Scholar] [CrossRef]
9. Zhao G, Si X, Wang J, Long X, Hu T. A novel mutual authentication scheme for internet of things. In: Proceedings of the 2011 International Conference on Modelling, Identification and Control; Shanghai, China; 2011. p. 563–6. doi:10.1109/ICMIC.2011.5973767. [Google Scholar] [CrossRef]
10. Ferrag MA, Maglaras LA, Janicke H, Jiang J, Shu L. Authentication protocols for internet of things: a comprehensive survey. Secur Commun Netw. 2017;2017(4):562953. doi:10.1155/2017/6562953. [Google Scholar] [CrossRef]
11. Kalra S, Sood SK. Secure authentication scheme for IoT and cloud servers. Pervasive Mob Comput. 2015;24(1):210–23. doi:10.1016/j.pmcj.2015.08.001. [Google Scholar] [CrossRef]
12. Chang CC, Wu HL, Sun CY. Notes on ‘secure authentication scheme for IoT and cloud servers’. Pervasive Mob Comput. 2017;38(15):275–8. doi:10.1016/j.pmcj.2015.12.003. [Google Scholar] [CrossRef]
13. Wang KH, Chen CM, Fang W, Wu TY. A secure authentication scheme for internet of things. Pervasive Mob Comput. 2017;42(15):15–26. doi:10.1016/j.pmcj.2017.09.004. [Google Scholar] [CrossRef]
14. Kumari S, Karuppiah M, Das AK, Li X, Wu F, Kumar N. A secure authentication scheme based on elliptic curve cryptography for IoT and cloud servers. J Supercomput. 2018;74(4):6428–53. doi:10.1007/s11227-017-2048-0. [Google Scholar] [CrossRef]
15. Rostampour S, Safkhani M, Bendavid Y, Bagheri N. ECCbAP: a secure ECC-based authentication protocol for IoT edge devices. Pervasive Mob Comput. 2020;67(2018):101194. doi:10.1016/j.pmcj.2020.101194. [Google Scholar] [CrossRef]
16. Panda PK, Chattopadhyay S. A secure mutual authentication protocol for IoT environment. J Reliab Intell Environ. 2020;6(2):79–94. doi:10.1007/s40860-020-00098-y. [Google Scholar] [CrossRef]
17. Zhu X, Ren Z, He J, Ren B, Zhao S, Zhang P. LAAP: lightweight anonymous authentication protocol for IoT edge devices based on elliptic curve. Wirel Commun Mob Comput. 2022;2022(1):8768928. doi:10.1155/2022/8768928. [Google Scholar] [CrossRef]
18. Jebrane J, Lazaar S. ILAPU-Q: an improved lightweight authentication protocol for IoT based on U-quark hash function. Recent Adv Comput Sci Commun. 2024;17(2):78–87. doi:10.2174/0126662558274597231204114801. [Google Scholar] [CrossRef]
19. Jebrane J, Lazaar S. An enhanced and verifiable lightweight authentication protocol for securing the internet of medical things (IoMT) based on CP-ABE encryption. Int J Inf Secur. 2024;1(1):1–15. doi:10.1007/s10207-024-00906-z. [Google Scholar] [CrossRef]
20. Sudhakar T, Praveen R, Natarajan V. An efficient ECC and fuzzy verifier based user authentication protocol for IoT-enabled WSNs. Sci Rep. 2025;15(1):9974. doi:10.1038/s41598-025-16694-3. [Google Scholar] [CrossRef]
21. Choe H, Kang D. ECC-based authentication protocol for military internet of drones (IoDa holistic security framework. IEEE Access. 2025;13(1):21503–21519. doi:10.1109/ACCESS.2025.3536014. [Google Scholar] [CrossRef]
22. Samal K, Sunanda SK, Jena D, Patnaik S. A lightweight privacy preservation authentication protocol for IoMT using ECC based blind signature. Int J Eng Bus Manag. 2025;17(4):1–13. doi:10.1177/18479790251318538. [Google Scholar] [CrossRef]
23. Sabbry NH, Levina AB. An optimized point multiplication strategy in elliptic curve cryptography for resource-constrained devices. Mathematics. 2024;12(6):881. doi:10.3390/math12060881. [Google Scholar] [CrossRef]
24. Hankerson D, Vanstone S, Menezes A. Guide to elliptic curve cryptography. New York, NY: Springer Professional Computing; 2004. doi:10.1007/b97644, 978-0-387-95273-4 [Google Scholar] [CrossRef]
25. Szepieniec A. On the use of the Legendre symbol in symmetric cipher design. Cryptology ePrint Archive, Paper 2021/984. 2021. [cited 2025 Jun 20]. Available from: https://eprint.iacr.org/2021/984. [Google Scholar]
26. Webster AF, Tavares SE. On the design of S-Boxes. In: Lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformaticsVol. 218. LNCS; 1986. doi:10.1007/3-540-39799-X_41. [Google Scholar] [CrossRef]
27. Kam L, Davida G. Structured design of substitution-permutation encryption networks. IEEE Trans Comput. 1979;28(10):747–53. doi:10.1109/TC.1979.1675242. [Google Scholar] [CrossRef]
28. Adiguzel-Goktas E, Ozdemir E. Square root computation in finite fields; 2024. arXiv:2206.07145. [Google Scholar]
29. Dang Q. NIST special publication 800-107 revision 1: recommendation for applications using approved hash algorithms. Natl Inst Stand Technol. 2017. doi:10.6028/NIST.SP.800-107r1. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools