 Open Access
Open Access
ARTICLE
Trust-Aware AI-Enabled Edge Framework for Intelligent Traffic Control in Cyber-Physical Systems
1 Department of Computer Science, Islamia College Peshawar, Peshawar, 25120, Pakistan
2 College of Computer and Information Sciences, Imam Mohammad Ibn Saud Islamic University (IMSIU), Riyadh, 11432, Saudi Arabia
3 School of Computer Science & IT, Institute of Management Sciences (IMSciences), Peshawar, 25100, Pakistan
4 City University of Science and Information Technology (CUSIT), Peshawar, 25000, Pakistan
* Corresponding Author: Imran Qureshi. Email:
(This article belongs to the Special Issue: Next-Generation Intelligent Networks and Systems: Advances in IoT, Edge Computing, and Secure Cyber-Physical Applications)
Computer Modeling in Engineering & Sciences 2025, 145(3), 4349-4362. https://doi.org/10.32604/cmes.2025.072326
Received 24 August 2025; Accepted 01 December 2025; Issue published 23 December 2025
Abstract
The rapid evolution of smart cities has led to the deployment of Cyber-Physical IoT Systems (CPS-IoT) for real-time monitoring, intelligent decision-making, and efficient resource management, particularly in intelligent transportation and vehicular networks. Edge intelligence plays a crucial role in these systems by enabling low-latency processing and localized optimization for dynamic, data-intensive, and vehicular environments. However, challenges such as high computational overhead, uneven load distribution, and inefficient utilization of communication resources significantly hinder scalability and responsiveness. Our research presents a robust framework that integrates artificial intelligence and edge-level traffic prediction for CPS-IoT systems. Distributed computing for selecting forwarders and analyzing threats across the IoT system enhances stability while improving energy efficiency. In addition, to achieve efficient routing decision-making, the Artificial Bee Colony algorithm is explored to enhance the effective utilization of network resources across IoT systems. Based on the simulation results, the proposed framework achieves remarkable performance in terms of throughput by 38%–41%, packet loss ratio by 30%–33%, security risk mitigation by 35%–37%, and trust level by 41%–44% as compared to existing work.Keywords
IoT networks and edge computing enable rapid development in the automation process, facilitating data collection and processing [1,2]. The real-world system utilizing future-generation technologies not only maintains the observing field but also reduces human efforts in monitoring and controlling the remote environment [3,4]. Recently, many existing systems require consistent and distributed services to achieve reliable and load-balanced approaches integrated with CPS-IoT, enabling timely responses from the requested devices and support for intelligence in smart cities [5,6]. Moreover, due to the dynamic infrastructure, incorporating security and threat analysis is also a significant research challenge [7,8], as well as controlling the massive data traffic generated by interconnected devices [9,10]. Moreover, such issues degrade the performance of sensor-driven applications in terms of scalability and effective load distribution across heterogeneous infrastructure [11,12]. Furthermore, due to the increasing use of battery-powered IoT devices, optimizing energy consumption is a critical research problem for physical systems. Thus, smart cities require an efficient solution for energy scheduling and allocation of network resources [13,14]. Due to the dynamic and inconsistent structure of IoT systems, they are more suspicious in the presence of malicious threats, and are vulnerable to distributed attacks to compromise the data with unauthorized access [15,16]. Most existing approaches cope with network threats, but at the cost of additional overhead and rapidly degrading energy resources. Thus, recently, many researchers have focused on developing reliable and fault-tolerant network solutions to address privacy and trustworthiness issues [17,18]. Such a system should be able to tackle faulty requests for connections and provide robust authentication and verifiable strategies to permit only authorized devices to access resources and sensitive data. Moreover, lightweight encryption/decryption must be designed to prevent against potential threats and mitigate multifaceted communication holes [19,20]. It has been observed that most IoT-CPS systems require resource optimization and trustworthiness approaches, necessitating the development of energy efficiency and threat analysis solutions. Therefore, our research aims to provide a framework with traffic-based analysis for route selection, considering edge-level local processing with realistic parameters and environmental conditions. In this research, we introduce a framework for a T-CPS environment by integrating trusted and load-balanced devices with the collaboration of edge-level intelligence. The trust computation enhances consistency among vehicles and reduces network traffic by effectively managing threats and malicious behavior.
i. Firstly, by exploring the Artificial Bee Colony algorithm, a distributed computing approach is employed to optimize resource usage while transmitting transportation data in smart cities.
ii. Secondly, the proposed framework is trained to analyze device behavior and identify abnormal traffic resulting from malicious activities.
iii. Lastly, only authentic data can be analyzed and processed by the trusted edges for issuing connected requests to devices.
The article is organized as follows: Related work is explained in Section 2, Section 3 explains the functionalities of the proposed framework, the experimental setup and results analysis are discussed in Section 4, and at the end, this research study is concluded in Section 5.
IoT networks enable many smart communication systems for Cyber-Physical communication, advancing automation and real-time data management [21,22]. Unlike cloud networks, edge computing provides access to resources near the source device, enabling rapid data processing for real-time analysis. It improves response time and increases device performance in critical applications by reducing latency and overhead [23,24]. These systems enhance task computation effectiveness by distributing the load across intermediate devices, improving system resilience in critical infrastructure against communication failures [25,26]. In [27], the authors propose an adaptive routing protocol to control energy usage in end-user devices. It utilizes a link quality prediction method to cluster network objects and route data based on the movement of these objects. The protocol introduced the NHARSO algorithm [28] to determine optimal paths between cluster heads and base stations in IoT-enabled Wireless Sensor Networks (IWSNs), addressing issues related to sensing, residual energy, and communication. The selection of optimal cluster heads not only increases the network lifetime but also efficiently utilizes the energy consumption of the devices.
In [29], authors have proposed an energy-efficient multilevel secure routing (EEMSR) protocol, which aims to cluster the network for efficient resource management and energy efficiency. It also decreases the overhead on the devices and supports the communication system with a prolonged network lifetime. Moreover, multiple factors are explored for trust, including data perception, fusion, and communication trust, to provide security and protect the system against threats. An Artificial Intelligence-based Energy-aware Intrusion Detection and Secure Routing model is proposed in [30] for Industrial Wireless Sensor Networks. Its aim is to establish a secure IoT network with minimal additional energy consumption in the network structure. In addition, the proposed model integrates intrusion detection with a game strategy-based decision mechanism to provide an energy-aware ad hoc on-demand distance vector algorithm with authentic and reliable routing.
Authors in [31] integrate software-defined networking (SDN) and blockchain technology to address the challenges of energy efficiency and security research. Consequently, a novel energy protocol combined with a cluster structure was proposed to develop a secure and blockchain-enabled SDN controller architecture for IoT networks. Because it uses public and private blockchains for peer-to-peer (P2P) communication between IoT devices and SDN controllers, eliminating Proof-of-Work, the distributed trust architecture is suitable for resource-constrained IoT devices. The study [32] introduces a modified AntHocNet in the FANET routing protocol, aiming to provide optimal data forwarders for route establishment using ant colony optimization (ACO). The data forwarders are rotated to maintain the constructed paths and enhance the system’s efficacy. The result analysis significantly enhanced the energy efficiency of the network, resulting in a long-run stable period. Table 1 outlines the existing research challenges in most related work, along with the inclusion of major functionalities of the proposed framework.
In this section, we present the details of our proposed framework along with its algorithms.
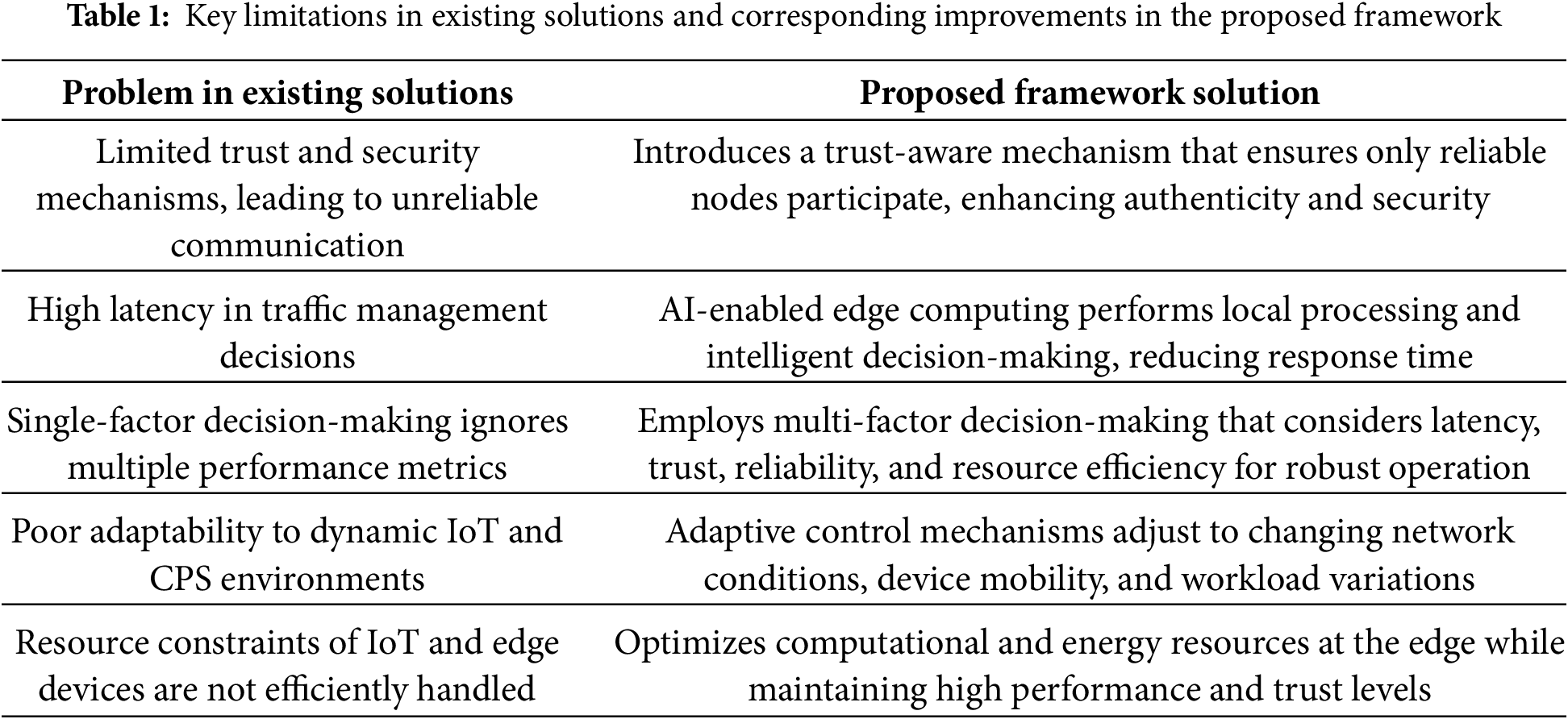
Graph initialization, communication optimization, and trust integration are the three main phases of the proposed framework, as depicted in Fig. 1. Such an environment consists of IoT sensors that sense objects and send the collected data to the edges for local processing. The integration of intelligence is another key feature of the proposed framework, supported by a trust-driven approach. It not only identifies malicious devices but also enhances security for T-CPS through mutual authentication. The proposed framework assumes the following assumptions for realistic Cyber-Physical IoT Systems.
Figure 1: T-CPS enabled communication architecture for IoT-based Trusted systems
• Network devices in T-CPS are resource-constrained in terms of energy, transmission power, and memory, requiring efficient communication mechanisms.
• CPS-IoT environments are dynamic and may experience unreliable connectivity, mobility, and varying communication reliability.
• Edge devices possess sufficient computational resources for distributed processing and task offloading from constrained nodes.
• Source and destination devices are initially trusted, while intermediate nodes may be malicious; hence, trust-based mechanisms are employed for secure communication.
Initially, a connected graph G is formed using nodes V and edges E. Edges denote the communication links. In the proposed framework, we explore the Artificial Bee Colony [33] based optimization to cope with the transmission of transportation data among vehicles. Moreover, edges are not selected based on cost and are randomly selected to construct initial routes for disseminating data in the Transportation Cyber-Physical System (T-CPS). Such a mechanism manages the traffic load in a balanced order and reduces device congestion. Node
where
where
where
Eq. (5) defines the latency metric to compute the communication delay in vehicles and enhances the trust level in a crucial environment with rapid response.
Eq. (6) computes the node reliability based on the behavior and consistency of vehicles. In such a case, the trust in vehicle
where:
•
•
•
•
•
Eq. (7) defines the edge selection process by integrating a trust evaluation mechanism.
where
where:
•
•
•
Fig. 2 shows the working flow of the proposed framework using IoT architecture for the T-CPS environment. It evaluates real-time capture data and generates an optimal decision-making system using the Artificial Bee Colony algorithm. Weighted methods are explored to incorporate multiple parameters, such as communication cost, link dependability, and trust, allowing agents to select the most reliable forwarders with the highest reliability and trust levels. Such decisions are less likely to be erroneous. Thus, our proposed framework optimizes and controls IoT traffic while ensuring efficient resource management and secure computations across associated devices. The generated decision is also adaptively updated based on traffic and network conditions. To achieve secure, more authentic IoT-based communication, the proposed trustworthy techniques are depicted in Fig. 3. In the proposed framework, the trust score plays a crucial role in promptly identifying malicious devices. The deployed edges are treated as agents and select communication routes with higher trusted scores, thereby introducing a more stable T-CPS communication system that efficiently utilizes network resources. If any lower-rated devices are selected as forwarders, they are marked as invalid for further data transmission. All devices are assigned a trust score based on their behavior, which changes dynamically over time. Moreover, the lightweight security methods make it able to attain the integrity and less congested the bounded constraint devices. Our layer-based trust management offers more reliable and resilient communication channels over the CPS environment.
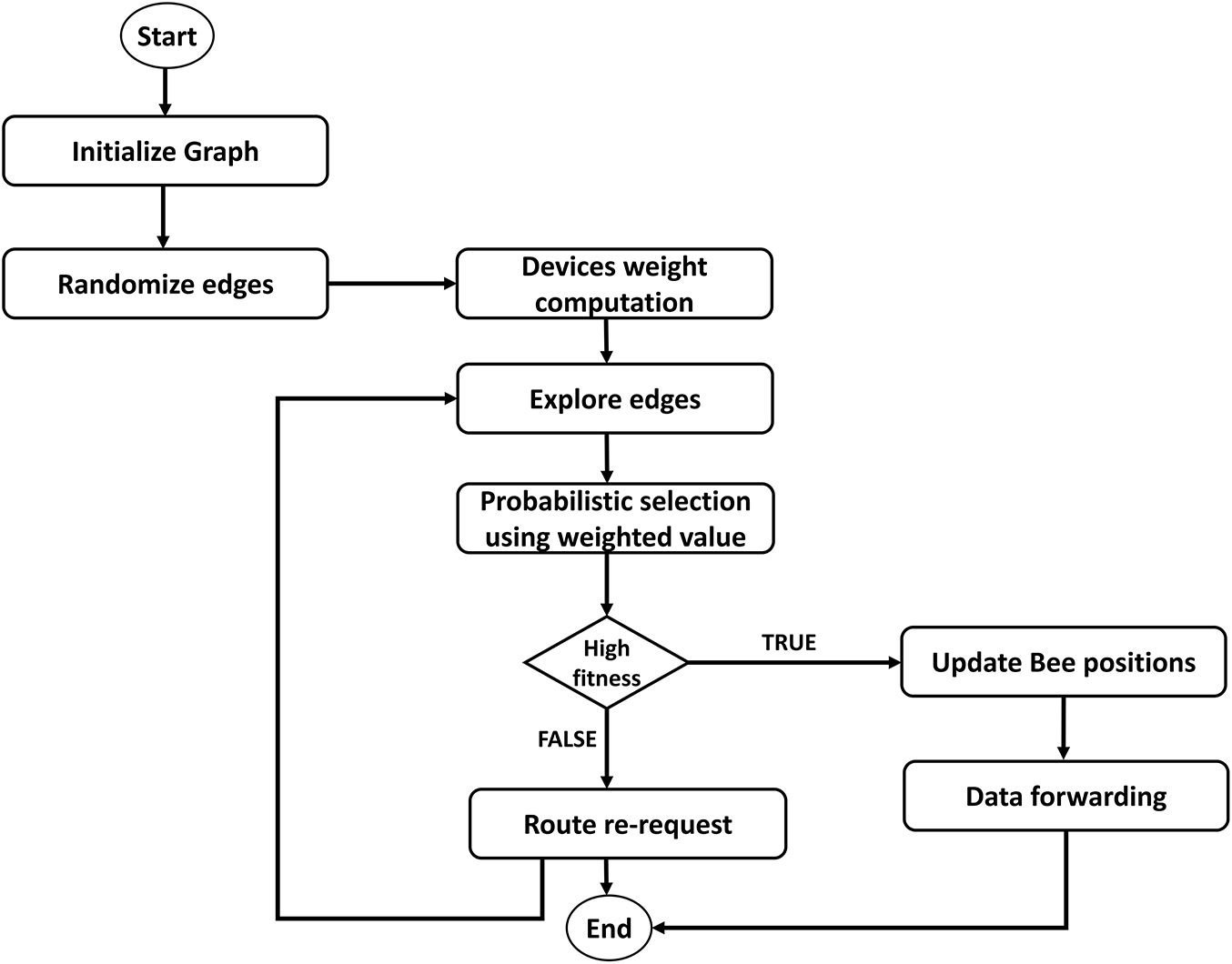
Figure 2: Flowchart for real-time data dissemination using network edges in CPS system
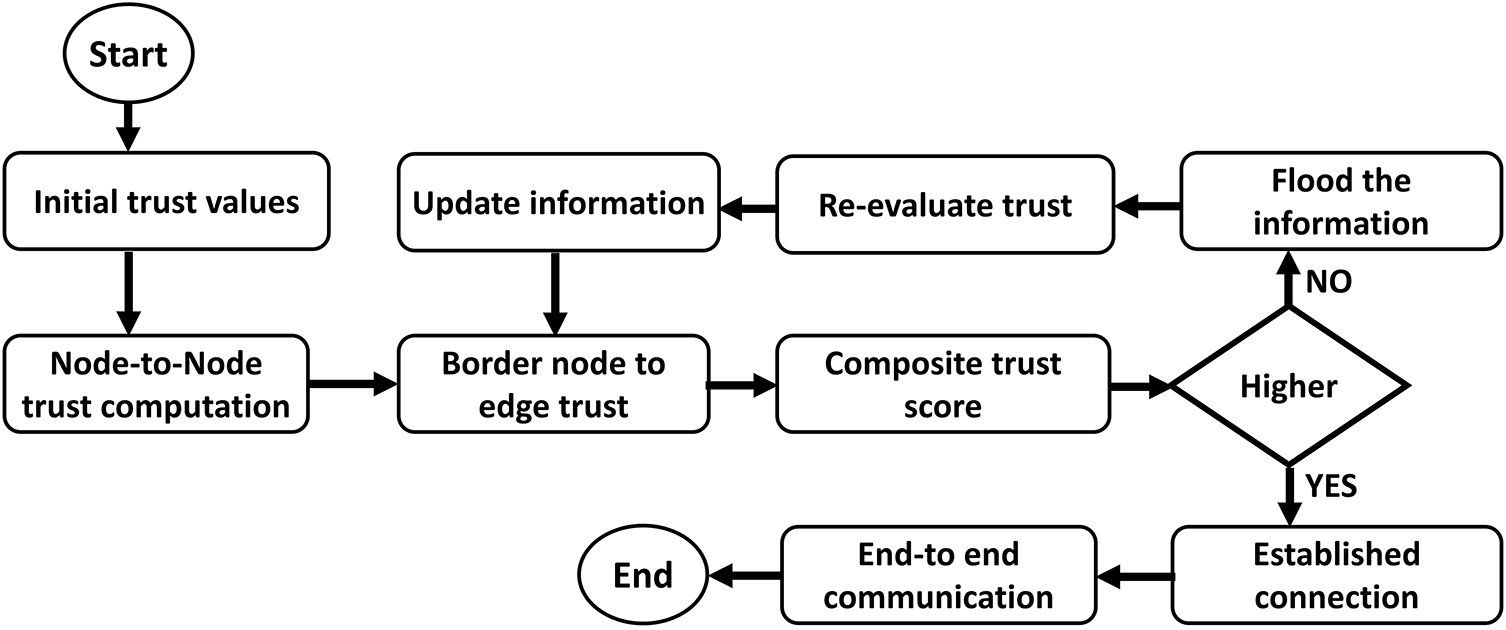
Figure 3: Flowchart for trust-aware communication and adaptive routing in T-CPS
Algorithm 1 illustrates the developed procedures for optimized decision-making, trust computation, and route maintenance using edge-level processing.
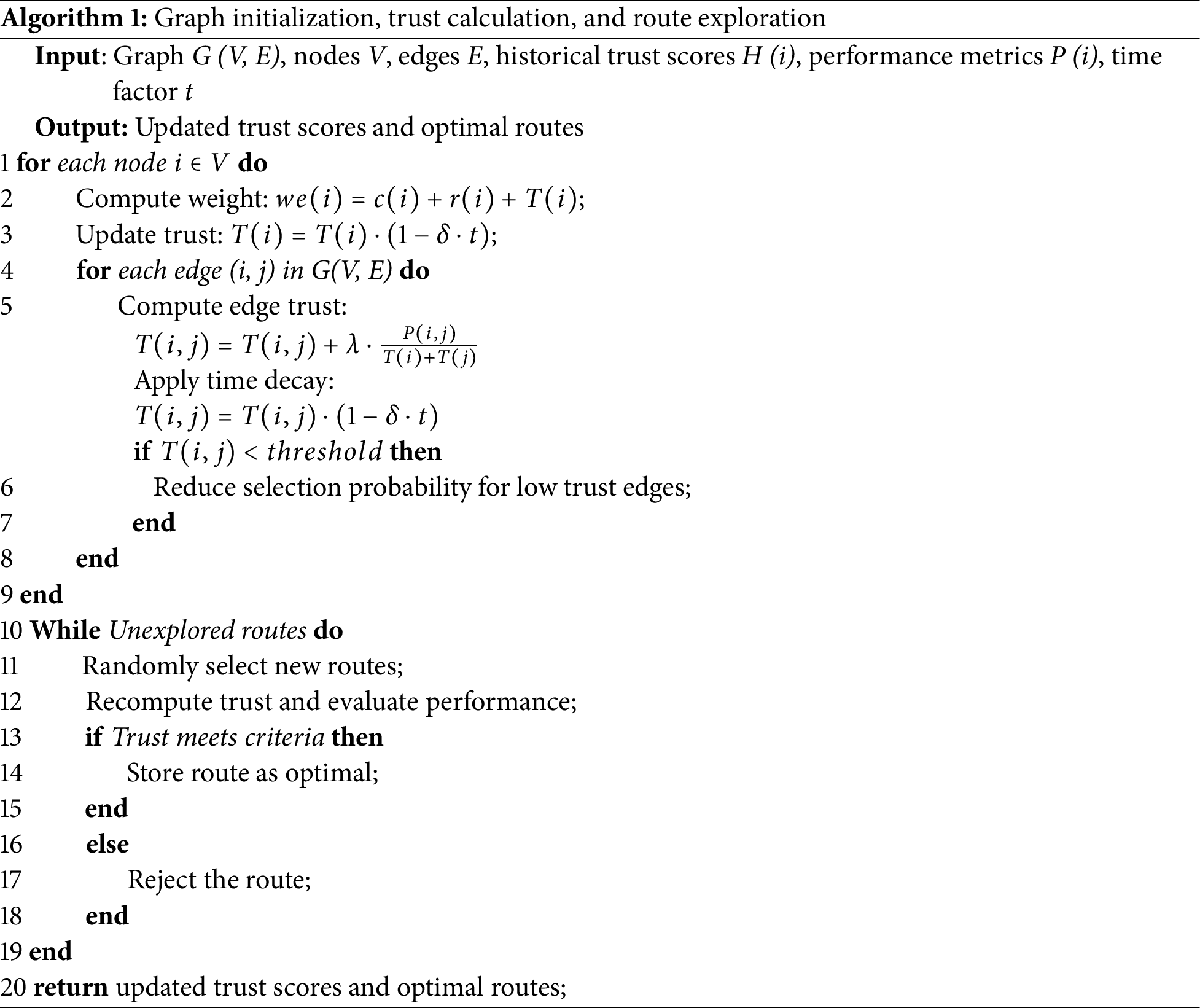
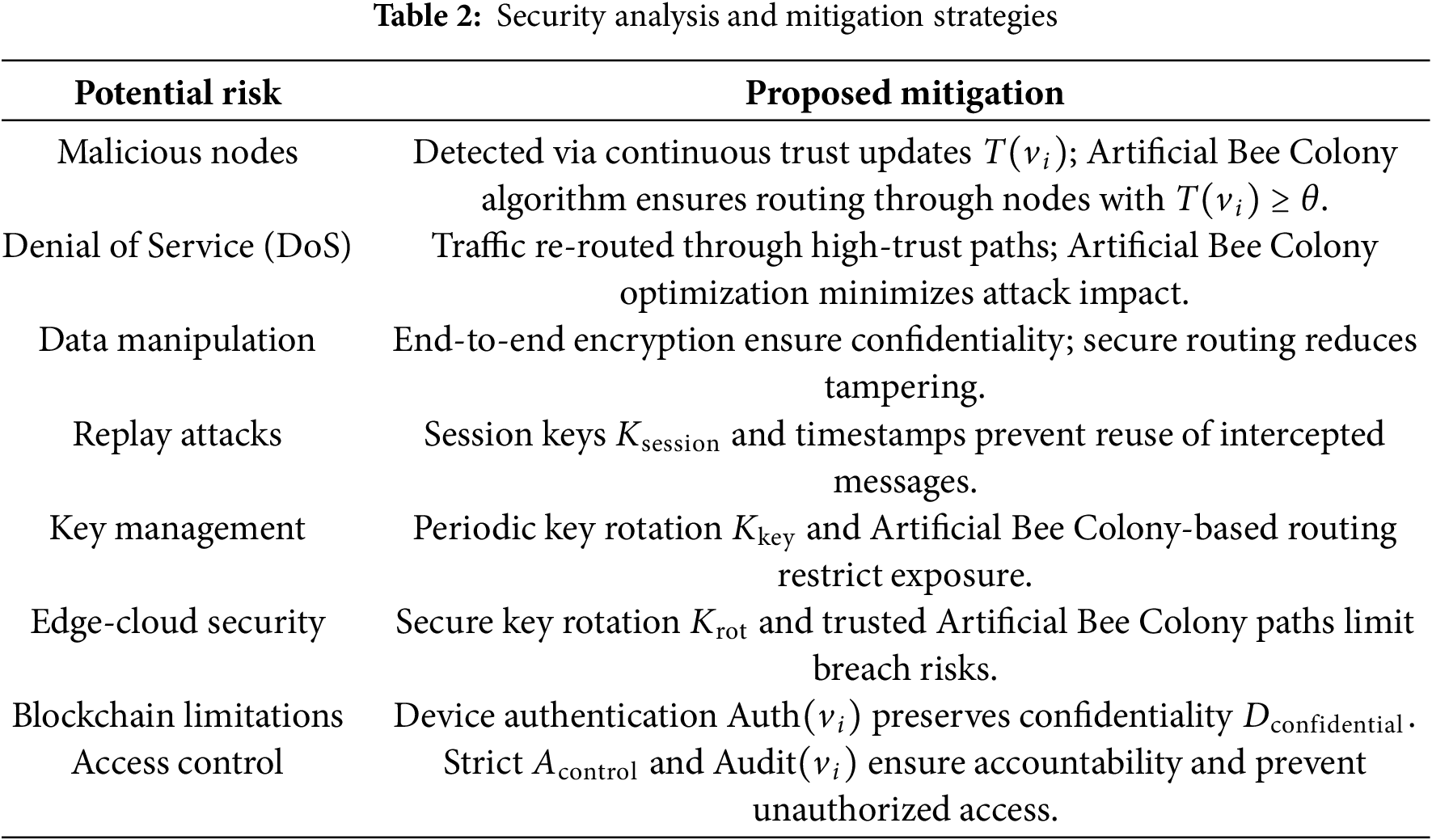
Table 2 describes the proposed security methods while addressing potential attacks in IoT networks to guarantee a reliable T-CPS environment with trustworthiness.
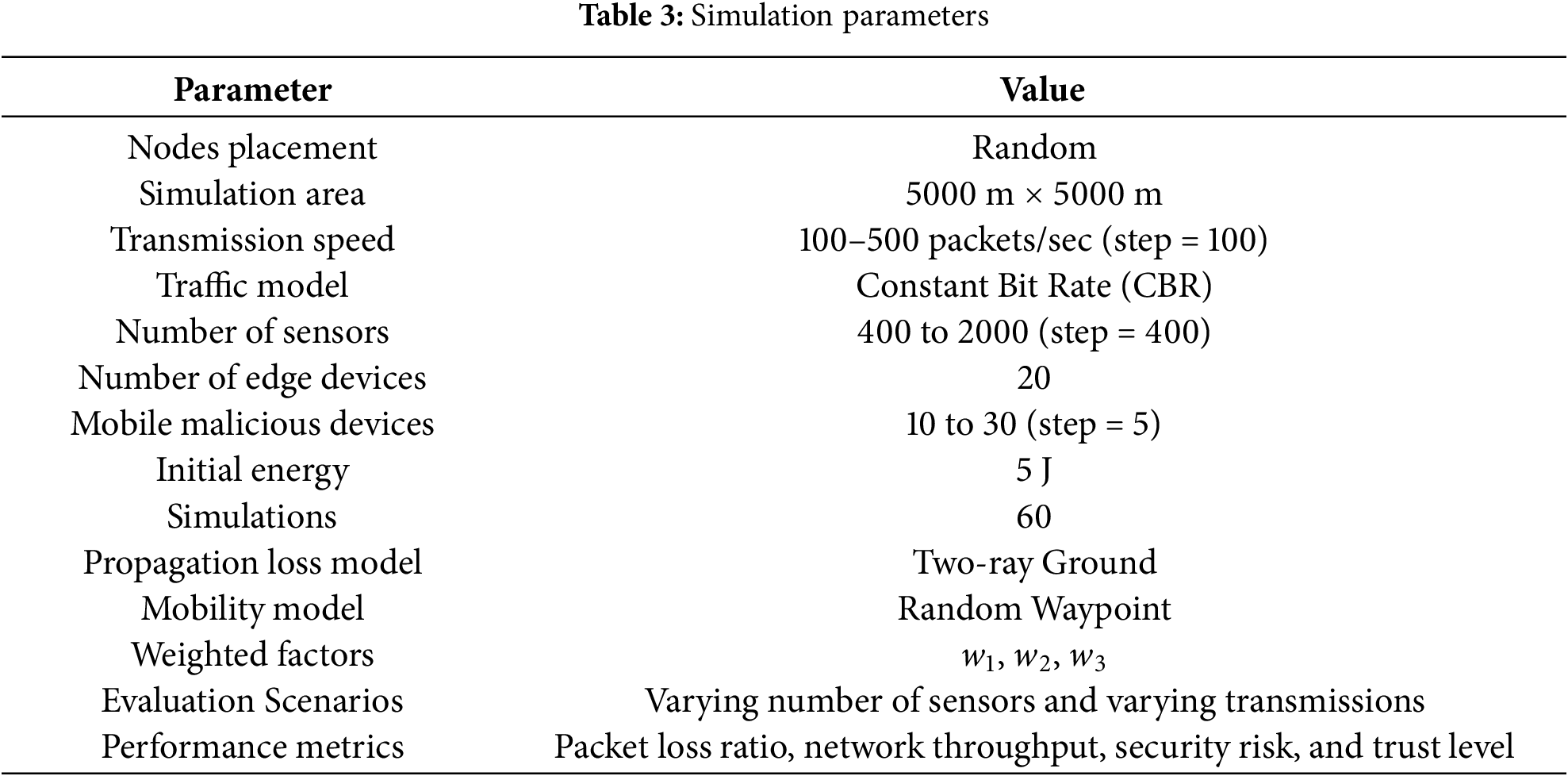
This section presents the performance evaluation of the proposed framework with related studies in terms of varying sensors and transmission data. The deployed environment consists of sensors, edge nodes, and sink nodes, all of which are connected to the cloud system. Simulation parameters with their default values are declared in Table 3.
We compared the performance of the packet drop ratio of the proposed framework with existing approaches, as depicted in Figs. 4 and 5. The proposed framework reduced the packet drop ratio by an average of 32% and 37% under varying numbers of sensors and transmission data. This is due to integrating the Artificial Bee Colony algorithm, which is used to select more reliable communication links and efficiently manage network resources. Moreover, the proposed framework provides stable paths by computing link interference parameters, thereby enhancing data reception and reducing the probability of network congestion. The proposed trusted mechanisms mitigated malicious traffic and prevented false requests from devices, thus improving the overall management of transportation traffic and stabilizing the real-time environment of CPS.
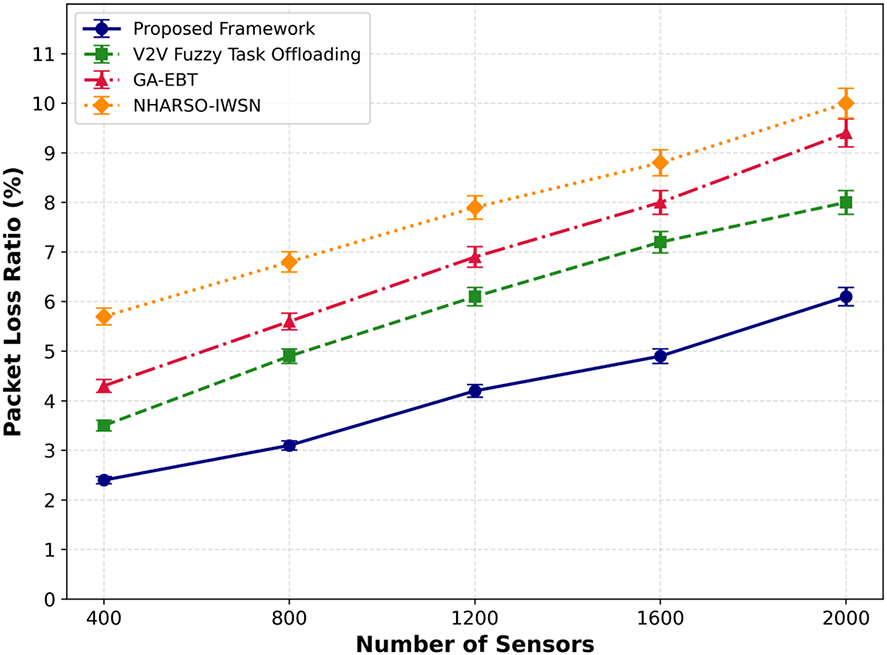
Figure 4: Performance of proposed framework with V2V fuzzy task offloading, GA-EBT, and NHARSO-IWSN for packet loss rate under varying number of sensors
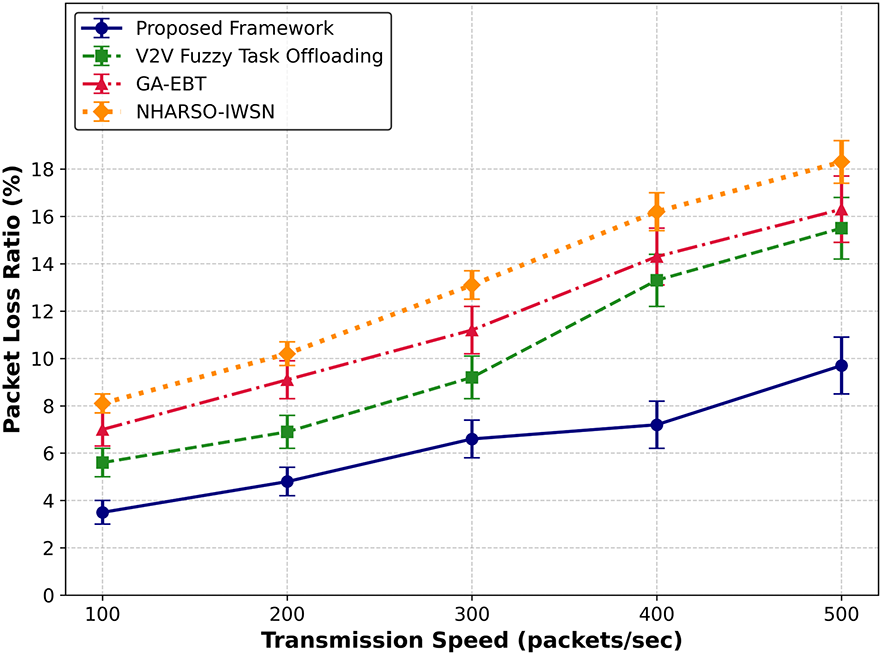
Figure 5: Performance of proposed framework with V2V fuzzy task offloading, GA-EBT, and NHARSO-IWSN for packet loss rate under varying transmissions
The network throughput of the proposed framework is evaluated against existing approaches, as shown in Figs. 6 and 7. The experimental results indicate that our framework improves average network throughput by 40% and 45% under varying numbers of sensors and data transmission scenarios, respectively. The initial route selection leverages a weighted objective function that incorporates device history, performance metrics, and decayed trust values, thus providing uniform contribution for each parameter. It also reduces the load on the selected forwarders through balancing strategies. In addition, the dual-level trust enables T-CPS not to send sensor data for further processing via wireless links that are compromised or inauthentic.
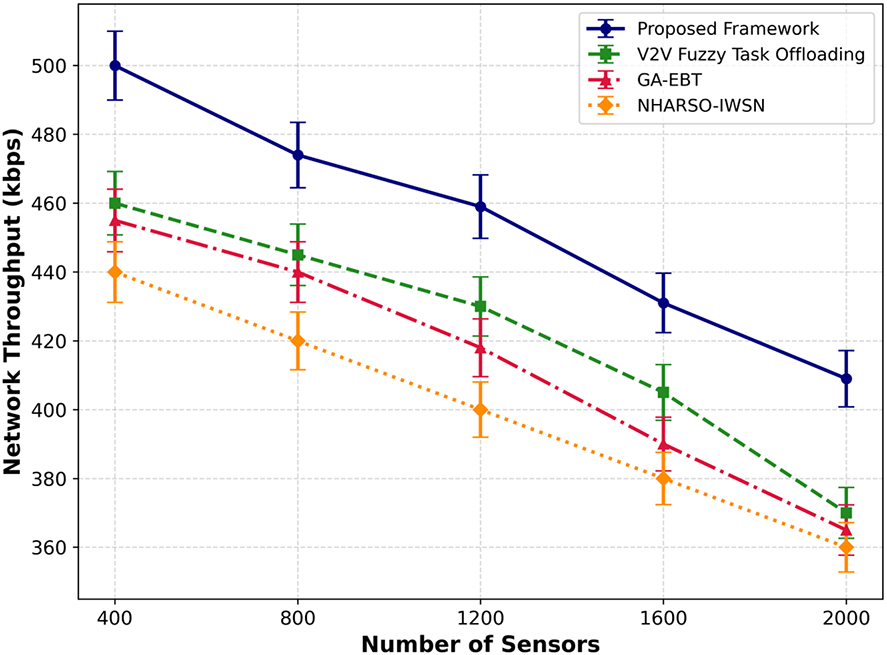
Figure 6: Performance of proposed framework with V2V fuzzy task offloading and GA-EBT for network throughput under varying number of sensors
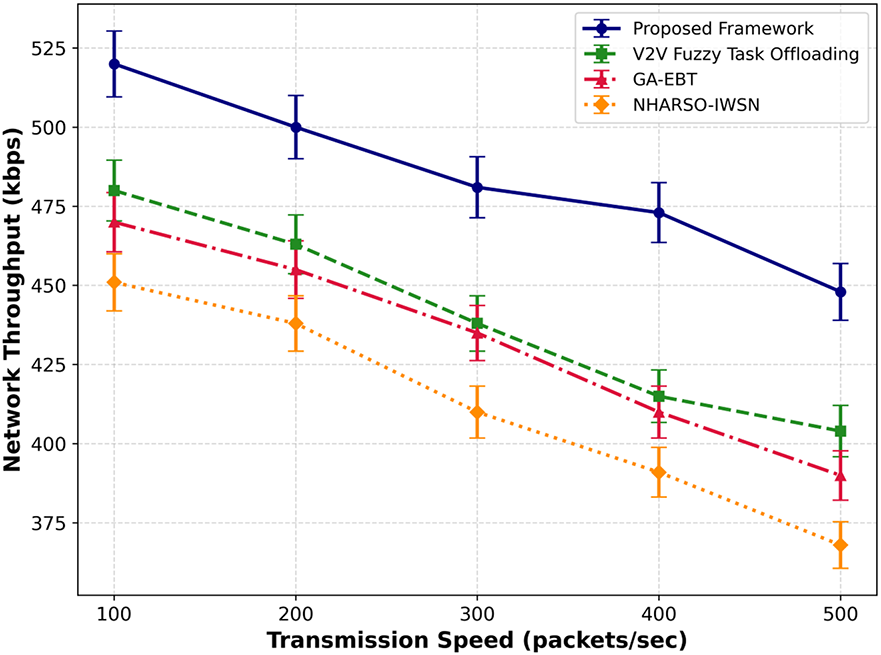
Figure 7: Performance of proposed framework with V2V fuzzy task offloading, GA-EBT, and NHARSO-IWSN for network throughput under varying transmissions
The security risk performance of the proposed framework, compared with existing approaches, is illustrated in Figs. 8 and 9 under varying sensors and transmission data. Upon comparison, it was discovered that the proposed framework effectively improved the protection of T-CPS against threats by an average of 34% and 39%, respectively, by identifying malicious devices and routing traffic only over the more trusted links. This is due to the combination of multiple parameters that enable secure data forwarders to maintain a reliable history in terms of data computation and association with neighboring nodes. The edges continuously monitor the border nodes, and if any malicious activity is detected based on communication behavior, the edges mark the transmission as compromised and record the information in log files. Furthermore, the resilient and incoming transportation data is verified using historical information, which is later sent to the cloud system. The proposed framework offers lightweight computing and minimizes unnecessary resource consumption by imposing a minimal overhead on transportation devices.
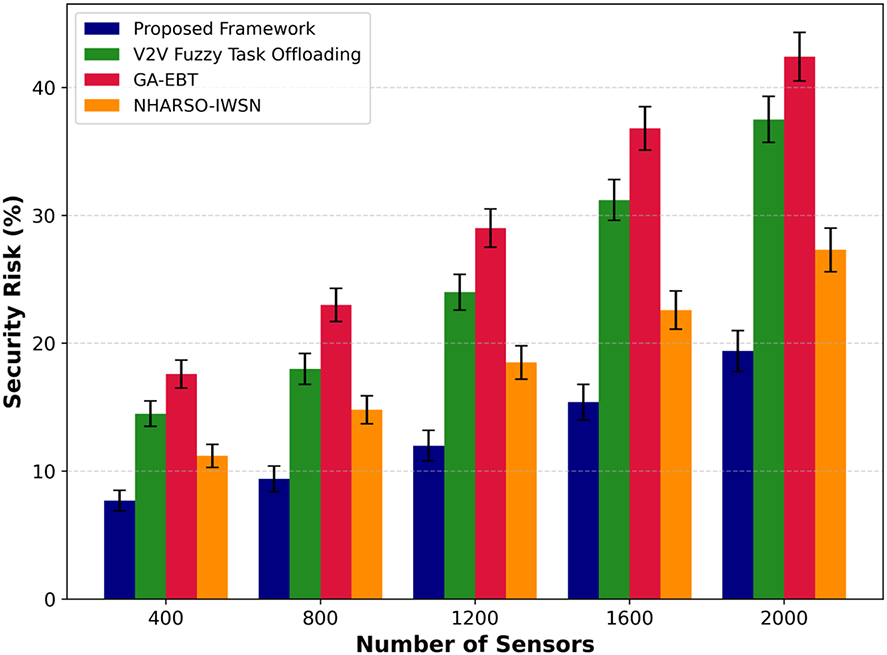
Figure 8: Performance of proposed framework with V2V fuzzy task offloading, GA-EBT, and NHARSO-IWSN for security risk under varying number of sensors
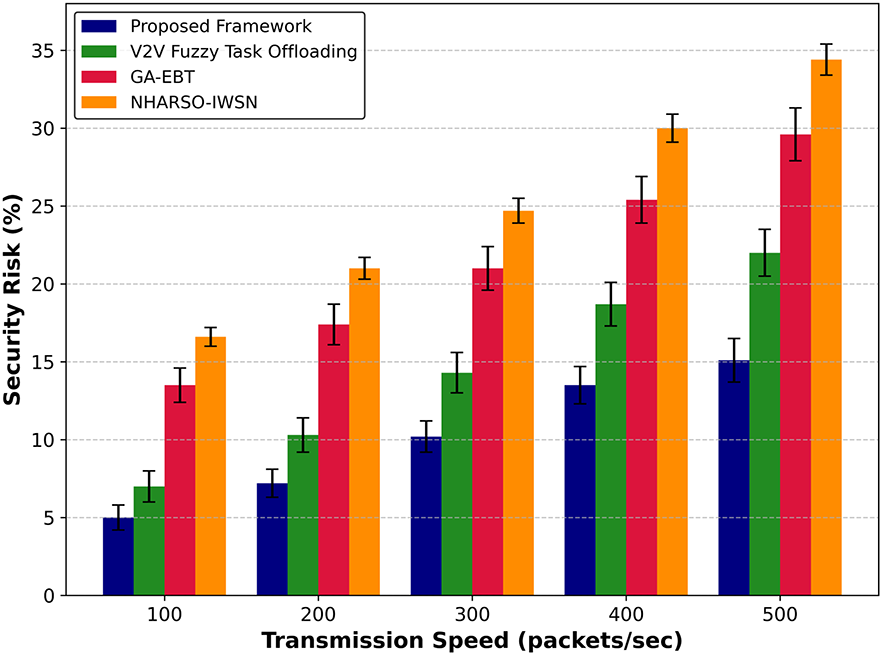
Figure 9: Performance of proposed framework with V2V fuzzy task offloading, GA-EBT, and NHARSO-IWSN for security risk under varying transmissions
In Figs. 10 and 11, the performance of the proposed framework and existing approaches is compared to evaluate trust levels under varying sensor and transmission data. Based on the results analysis, it was found that the proposed framework improved the performance by an average of 43% and 48% for prediction trust levels. By leveraging intelligence in decision-making, the proposed framework reduces device overhead and actively identifies threats through a multi-level trusted mechanism. Moreover, the Artificial Bee Colony algorithm provides more reliable, long-term communication paths for data routing, avoiding communication holes while accounting for multiple factors and environmental conditions.
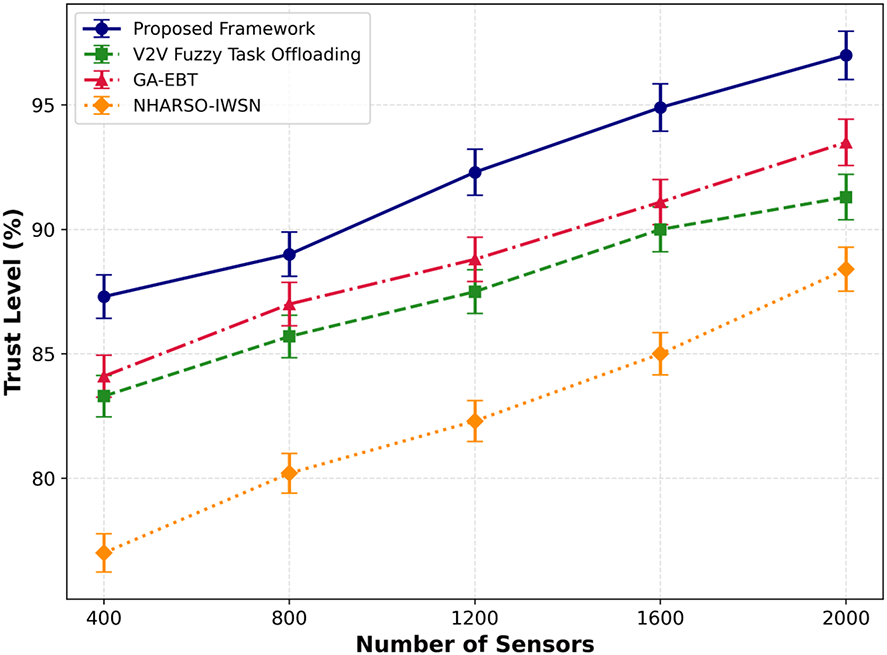
Figure 10: Performance of proposed framework with V2V fuzzy task offloading, GA-EBT, and NHARSO-IWSN for trust level under varying number of sensors
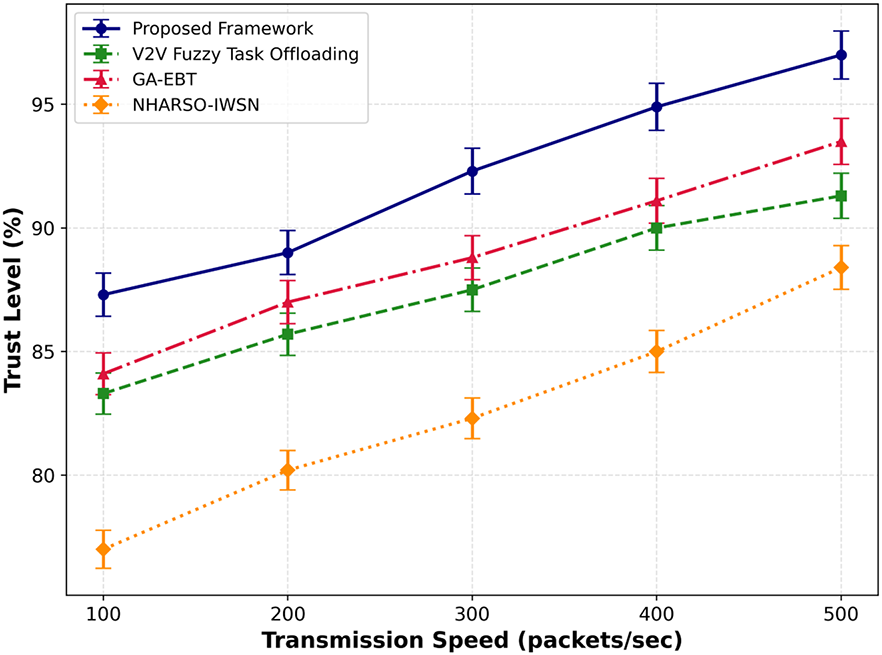
Figure 11: Performance of proposed framework with V2V fuzzy task offloading, GA-EBT, and NHARSO-IWSN for trust level varying transmissionss
In recent decades, emerging technologies with IoT systems have enabled real-time data processing and management for the formulation of smart cities. On the other hand, edge computing provides local processing and enables real-time traffic analysis for transportation networks. However, some solutions still lack intelligent decision-making, leading to additional energy consumption in the communication system. Moreover, threat analysis is another crucial component that is often overlooked in most existing approaches. Our proposed framework optimizes the decision-making strategies using the Artificial Bee Colony algorithm and integrates the multi-level trust detection against threats. Additionally, the distributed computing in the proposed framework reduces communication gaps through its load-balancing approach, thereby enhancing the vehicles’ efficacy. However, based on the results, it was noted that our proposed framework lacks scalability as the vehicle increases in size, resulting in additional computational cost. Thus, in future work, we plan to introduce SDN controllers to enhance flexibility and minimize the connection disturbance in heterogeneous CPS-IoT systems.
Acknowledgement: The authors would like to acknowledge the support by the Deanship of Scientific Research at Imam Mohammad Ibn Saud Islamic University (IMSIU) (grant number IMSIU-DDRSP2504).
Funding Statement: This work was supported and funded by the Deanship of Scientific Research at Imam Mohammad Ibn Saud Islamic University (IMSIU) (grant number IMSIU-DDRSP2504).
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Khalid Haseeb, Imran Qureshi; data collection: Naveed Abbas, Muhammad Ali, Muhammad Arif Shah; analysis and interpretation of results: Muhammad Ali, Muhammad Arif Shah, Qaisar Abbas; draft manuscript preparation: Khalid Haseeb, Imran Qureshi, Naveed Abass. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: All data generated or analyzed during this study are included in this published article.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. Abkenar FS, Ramezani P, Iranmanesh S, Murali S, Chulerttiyawong D, Wan X, et al. A survey on mobility of edge computing networks in IoT: state-of-the-art, architectures, and challenges. IEEE Commun Survs Tutor. 2022;24(4):2329–65. [Google Scholar]
2. Andriulo FC, Fiore M, Mongiello M, Traversa E, Zizzo V. Edge computing and cloud computing for internet of things: a review. Informatics. 2024;11:71. [Google Scholar]
3. Ahmed SF, Alam MSB, Hoque M, Lameesa A, Afrin S, Farah T, et al. Industrial Internet of Things enabled technologies, challenges, and future directions. Comput Electr Eng. 2023;110:108847. doi:10.1016/j.compeleceng.2023.108847. [Google Scholar] [CrossRef]
4. Abdulhussain SH, Mahmmod BM, Alwhelat A, Shehada D, Shihab ZI, Mohammed HJ, et al. A comprehensive review of sensor technologies in IoT: technical aspects, challenges, and future directions. Computers. 2025;14(8):342. doi:10.3390/computers14080342. [Google Scholar] [CrossRef]
5. Ullah I, Noor A, Nazir S, Ali F, Ghadi YY, Aslam N. Protecting IoT devices from security attacks using effective decision-making strategy of appropriate features. J Supercomput. 2024;80(5):5870–99. doi:10.1007/s11227-023-05685-3. [Google Scholar] [CrossRef]
6. Kato T, Fukumoto N, Sasaki C, Tagami A, Nakao A. Challenges of CPS/IoT network architecture in 6G era. IEEE Access. 2024;12(1):62804–17. doi:10.1109/access.2024.3395363. [Google Scholar] [CrossRef]
7. Mei Q, Xiong H, Chen YC, Chen CM. Blockchain-enabled privacy-preserving authentication mechanism for transportation CPS with cloud-edge computing. IEEE Trans Eng Manag. 2022;71(37):12463–74. doi:10.1109/tem.2022.3159311. [Google Scholar] [CrossRef]
8. Bhansali A, Patra RK, Divakarachari PB, Falkowski-Gilski P, Shivakanth G, Patil SN. CNN-CLFFA: support mobile edge computing in transportation cyber physical system. IEEE Access. 2024;12:21026–37. doi:10.1109/access.2024.3361837. [Google Scholar] [CrossRef]
9. Mohammed A. Cybersecurity in Smart Cities: as cities become smarter, new vulnerabilities arise. Research can focus on securing IoT devices, smart infrastructure, and privacy concerns associated with smart city data. Pioneer Res J Comput Sci. 2024;1(1):75–82. doi:10.4018/979-8-3373-3326-7.ch003. [Google Scholar] [CrossRef]
10. Escolar AM, Wang Q, Calero JMA. Enhancing honeynet-based protection with network slicing for massive Pre-6G IoT Smart Cities deployments. J Netw Comput Appl. 2024;229(8):103918. doi:10.1016/j.jnca.2024.103918. [Google Scholar] [CrossRef]
11. Trigka M, Dritsas E. Edge and cloud computing in smart cities. Future Internet. 2025;17(3):118. doi:10.3390/fi17030118. [Google Scholar] [CrossRef]
12. Babar M, Khan MS, Din A, Ali F, Habib U, Kwak KS. Intelligent computation offloading for IoT applications in scalable edge computing using artificial bee colony optimization. Complexity. 2021;2021(1):5563531. doi:10.1155/2021/5563531. [Google Scholar] [CrossRef]
13. Reddy KHK, Luhach AK, Kumar VV, Pratihar S, Kumar D, Roy DS. Towards energy efficient Smart city services: a software defined resource management scheme for data centers. Sustain Comput Inform Syst. 2022;35(2):100776. doi:10.1016/j.suscom.2022.100776. [Google Scholar] [CrossRef]
14. Sun Z, Yang H, Li C, Yao Q, Teng Y, Zhang J, et al. A resource allocation scheme for edge computing network in smart city based on attention mechanism. ACM Trans Sens Netw. 2024;4(2):22. doi:10.1145/3650031. [Google Scholar] [CrossRef]
15. Alzaabi FR, Mehmood A. A review of recent advances, challenges, and opportunities in malicious insider threat detection using machine learning methods. IEEE Access. 2024;12:30907–27. doi:10.1109/access.2024.3519957. [Google Scholar] [CrossRef]
16. Siwakoti YR, Bhurtel M, Rawat DB, Oest A, Johnson R. Advances in IoT security: vulnerabilities, enabled criminal services, attacks, and countermeasures. IEEE Internet Things J. 2023;10(13):11224–39. doi:10.1109/jiot.2023.3252594. [Google Scholar] [CrossRef]
17. Chunduri V, Alsaadi M, Gupta S, Ahanger TA, Gopi A, Alghayadh FY, et al. Blockchain-based secure trust management scheme for internet of vehicles over cyber-physical system. IEEE Trans Intell Transp Syst. 2024;26(9):14067–76. doi:10.1109/tits.2024.3485481. [Google Scholar] [CrossRef]
18. Rehman A, Haseeb K, Alruwaili FF, Ara A, Saba T. Autonomous and intelligent mobile multimedia cyber-physical system with secured heterogeneous IoT network. Mobile Netw Appl. 2024;29(3):876–85. doi:10.1007/s11036-024-02329-5. [Google Scholar] [CrossRef]
19. Ozaif M, Mustajab S, Alam M. Exploration of secured data transmission in internet of things: a survey. In: 2024 IEEE international conference on computing, power and communication technologies (IC2PCT); 2024 Feb 9–10; Greater Noida, India. p. 106–12. doi:10.1109/ic2pct60090.2024.10486716. [Google Scholar] [CrossRef]
20. Jha AV, Appasani B, Khan MS, Zeadally S, Katib I. 6G for intelligent transportation systems: standards, technologies, and challenges. Telecommun Syst. 2024;86(2):241–68. doi:10.1007/s11235-024-01126-5. [Google Scholar] [CrossRef]
21. Ryalat M, ElMoaqet H, AlFaouri M. Design of a smart factory based on cyber-physical systems and Internet of Things towards Industry 4.0. Appl Sci. 2023;13(4):2156. doi:10.3390/app13042156. [Google Scholar] [CrossRef]
22. Zhang K, Shi Y, Karnouskos S, Sauter T, Fang H, Colombo AW. Advancements in industrial cyber-physical systems: an overview and perspectives. IEEE Trans Ind Inform. 2022;19(1):716–29. doi:10.1109/tii.2022.3199481. [Google Scholar] [CrossRef]
23. Rodrigues TK, Suto K, Nishiyama H, Liu J, Kato N. Machine learning meets computation and communication control in evolving edge and cloud: challenges and future perspective. IEEE Commun Surv Tutor. 2019;22(1):38–67. [Google Scholar]
24. Firouzi F, Jiang S, Chakrabarty K, Farahani B, Daneshmand M, Song J, et al. Fusion of IoT, AI, edge-fog–cloud, and blockchain: challenges, solutions, and a case study in healthcare and medicine. IEEE Internet Things J. 2022;10(5):3686–705. doi:10.36227/techrxiv.20369043.v1. [Google Scholar] [CrossRef]
25. Luo Q, Hu S, Li C, Li G, Shi W. Resource scheduling in edge computing: a survey. IEEE Commun Surv Tutor. 2021;23(4):2131–65. [Google Scholar]
26. Avan A, Azim A, Mahmoud QH. A state-of-the-art review of task scheduling for edge computing: a delay-sensitive application perspective. Electronics. 2023;12(12):2599. doi:10.3390/electronics12122599. [Google Scholar] [CrossRef]
27. Foko Sindjoung ML, Velempini M, Kengne Tchendji V. ARPMEC: an adaptive mobile edge computing-based routing protocol for IoT networks. Cluster Comput. 2024;27(7):9435–50. doi:10.1007/s10586-024-04450-2. [Google Scholar] [CrossRef]
28. Sharma P, Sharma M, Singh R, Kumar V, Agarwal R, Malik PK. NHARSO-IWSN: a Novel hybridized adaptive-network-based fuzzy inference system with reptile search optimization algorithm-based routing protocol for internet of things-enabled wireless sensor networks. IEEE Trans Consumer Electron. 2024;70(3):6293–302. doi:10.1109/tce.2024.3418845. [Google Scholar] [CrossRef]
29. Zhang Y, Ren Q, Song K, Liu Y, Zhang T, Qian Y. An energy-efficient multilevel secure routing protocol in IoT networks. IEEE Internet Things J. 2021;9(13):10539–53. doi:10.1109/jiot.2021.3121529. [Google Scholar] [CrossRef]
30. Aruchamy P, Gnanaselvi S, Sowndarya D, Naveenkumar P. An artificial intelligence approach for energy-aware intrusion detection and secure routing in internet of things-enabled wireless sensor networks. Concurr Comput. 2023;35(23):e7818. doi:10.1002/cpe.7818. [Google Scholar] [CrossRef]
31. Yazdinejad A, Parizi RM, Dehghantanha A, Zhang Q, Choo KKR. An energy-efficient SDN controller architecture for IoT networks with blockchain-based security. IEEE Trans Services Comput. 2020;13(4):625–38. doi:10.1109/tsc.2020.2966970. [Google Scholar] [CrossRef]
32. Khan IU, Qureshi IM, Aziz MA, Cheema TA, Shah SBH. Smart IoT control-based nature inspired energy efficient routing protocol for flying ad hoc network (FANET). IEEE Access. 2020;8:56371–8. doi:10.1109/access.2020.2981531. [Google Scholar] [CrossRef]
33. Kaya E, Gorkemli B, Akay B, Karaboga D. A review on the studies employing artificial bee colony algorithm to solve combinatorial optimization problems. Eng Appl Artif Intell. 2022;115(3):105311. doi:10.1016/j.engappai.2022.105311. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools